DOI:10.32604/cmc.2021.019051

| Computers, Materials & Continua DOI:10.32604/cmc.2021.019051 |  |
| Article |
An Efficient Lightweight Authentication and Key Agreement Protocol for Patient Privacy
1Department of Computer Engineering, Ferdowsi University of Mashhad, Mashhad, 9177948974, Iran
2Department of Informatics, Faculty of Science and Technology, Universitas Alazhar Indonesia, Jakarta, 12110, Indonesia
*Corresponding Author: Rahmat Budiarto. Email: rahmat.budiarto@uai.ac.id
Received: 29 March 2021; Accepted: 30 April 2021
Abstract: Tele-medical information system provides an efficient and convenient way to connect patients at home with medical personnel in clinical centers. In this system, service providers consider user authentication as a critical requirement. To address this crucial requirement, various types of validation and key agreement protocols have been employed. The main problem with the two-way authentication of patients and medical servers is not built with thorough and comprehensive analysis that makes the protocol design yet has flaws. This paper analyzes carefully all aspects of security requirements including the perfect forward secrecy in order to develop an efficient and robust lightweight authentication and key agreement protocol. The secureness of the proposed protocol undergoes an informal analysis, whose findings show that different security features are provided, including perfect forward secrecy and a resistance to DoS attacks. Furthermore, it is simulated and formally analyzed using Scyther tool. Simulation results indicate the protocol’s robustness, both in perfect forward security and against various attacks. In addition, the proposed protocol was compared with those of other related protocols in term of time complexity and communication cost. The time complexity of the proposed protocol only involves time of performing a hash function Th, i.e.,: O(12Th). Average time required for executing the authentication is 0.006 seconds; with number of bit exchange is 704, both values are the lowest among the other protocols. The results of the comparison point to a superior performance by the proposed protocol.
Keywords: Authentication; key agreement protocol; tele-medical; Scyther; perfect forward secrecy
With the rapid development and advancement of information technology, new Internet-based services have emerged, such as online banking, online medicine, and online training. Since all of these services utilize the potentially insecure environment of the Internet, the disclosure of important and sensitive information is a major concern for users.
Medical online service is one of the most sensitive Internet-based services, in which patient medical records are stored in databases and transmitted over the Internet. These records contain confidential information on patient illness and treatment. To take advantage of telemedicine, patients must register with a medical provider. After the initial registration process, whenever telemedicine services are accessed, the user and the server must authenticate to each other. If each party confirms the other party’s identity, the two can reach a key agreement and exchange their messages through the shared key.
When Internet-based communications are not secure, it is very possible that an unauthorized party disclosures patient information and resulting violation of patient’s privacy. To address this issue, many research works have focused on the security and authentication of telecommunications protocols [1–6]. Nevertheless, the proposed protocols are still lack of perfect forward secrecy feature. This research work attempts to address the issue and come up with a robust and efficient lightweight authentication and key agreement protocol for patient privacy in network communications by considering perfect forward secrecy. A robust protocol should be developed based on comprehensive analysis and evaluation on the security requirements. Thus, this work begins with investigating the existing relevant protocols to reveal the flaws and strengths then design the protocol in such a way to avoid the flaws.
The article is organized as follows. Section 2 reviews previous studies and Section 3 analyzes the Mehmood et al. [7] protocol. Section 4 proposes a secure and efficient protocol for authentication and key exchange which is resistant to various attacks. Section 5 deals with the security analysis of the introduced protocol, while Section 6 presents formal analysis using Scyther tool [8]. Then, Section 7 compares the proposed protocol with similar ones in terms of time complexity. Finally, Section 8 provides conclusion and discusses future work.
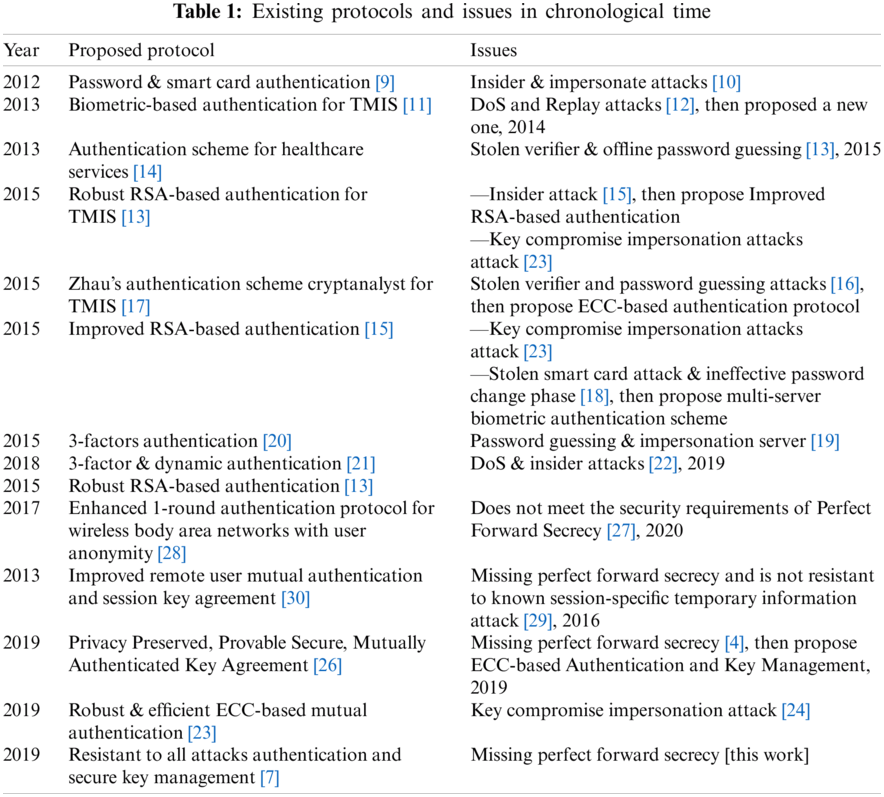
In 2012, Wu et al. [9] introduced a “password and smart card” authentication protocol. However, in the same year, Debiao et al. [10] revealed that the Wu et al. protocol was not resistant to “insider and impersonation” attacks and so they introduced an improved protocol. Tan et al. [11] proposed a biometric-based authentication protocol for Telecare medical information system (TMIS), claiming it was resistant to all attacks and could meet various security needs. Finding that the Tan et al. [11] protocol was not immune to DoS and replay attacks, Arshad and Arshad et al. [12] introduced a new three-factor biometric-based protocol. In 2015, Giri et al. [13] demonstrated that the Khan et al. [14] protocol was not resistant to the Stolen-verifier attack and off-line password guessing attack and then developed an RSA encryption-based validation protocol to ward off this attack. When studying the Giri et al. [13] protocol in 2015, Amin et al. [15] discovered that it was vulnerable to insider and password guessing attacks and, thus, could not meet the security requirement of anonymity. In the same year, Arshad et al. [16] demonstrated that the Muhaya protocol [17] was not resistant to the Stolen-verifier attack and off-line password guessing attack and unable to meet the “perfect forward secrecy” security requirement, so Arshad et al. proposed an Elliptic-curve cryptography (ECC)-based authentication scheme for TMIS, in which the user is anonymous.
Chaudhry et al. [18] evaluated Amin and Biswas protocol [19] and reported its lack of resistance to stolen smart card attacks and an ineffective password change phase. They further improved the protocol.
Jiang et al. [19] examined the three-factor authentication protocol proposed by Lu et al. [20] and declared it to be vulnerable to password guessing and user and server impersonation attacks. After making enhancements to the three-factor protocol, they provided a more viable solution to the security issues proposed by Lu et al. [20]. Zhang et al. [21] presented a three-factor plan for medical service authentication, by then, Aghili et al. [22], showed to be at risk of DoS and insider attacks.
At the same time, Ostadsharif et al. [23] reviewed the protocols presented in [13,15] and found they were not resistant to key compromise impersonation attacks. In addressing this, they introduced a new protocol for authentication and key agreement between patients and medical practitioners. Later, Kumari et al. [24] reported that the protocol of Ostadsharif et al. [25] still failed to resist key compromise impersonation attacks. Furthermore, Khatoon et al. [26] presented a physician and medical practitioner authentication protocol, which Amintoosi et al. [4] reviewed the same year, concluding that its security did not provide perfect forward secrecy and was open to known-session-specific temporary information attacks.
Ravanbakhsh et al. [2] then came up with an interesting scheme for authentication and key agreement in telemedicine, which, although their design had several advantages, but their design could not meet the “perfect forward secrecy” and is not resistant to “known session-specific temporary information attack”. Sowjanya et al. [27] examined the plan proposed by Li et al. [28] and concluded that the plan [28] has shortcomings such as not meeting the security requirements of Perfect Forward Secrecy. Also, He et al. [29] states that the plan in their other article [30] unable to meet the “perfect forward secrecy” security requirement Lastly, He et al. introduced a protocol for remote patient and physician authentication and claimed that it was resistant to all attacks and met various security requirements. The present study, nevertheless, proves that this protocol does not satisfy the security demands of perfect forward secrecy. Tab. 1 summarizes existing protocols and their issues in chronological time.
3 Analyzing the Weaknesses of the Mehmood et al.’s Protocol
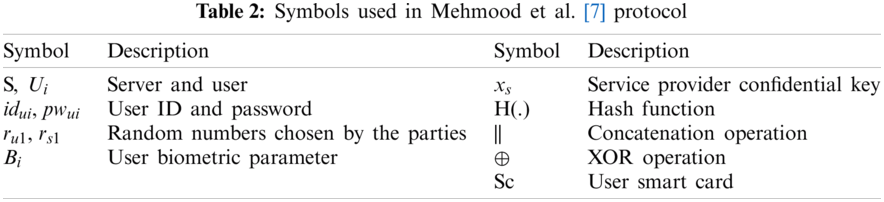
This section briefly reviews the protocol by Mehmood et al. [7] and analyzes the weaknesses of its security. Authentication and key authentication protocols usually include three phases: registration, authentication, and password change. According to Fig. 1, in the registration phase, the communication channel between the two channel entities is assumed to be secure. Furthermore, the parties communicate through a secure channel or in person. During the login and authentication process (Fig. 2), the channel is considered unsafe and the attacker can listen to the channel. Tab. 2 provides the symbols employed in Mehmood et al.’s protocol.

Figure 1: Registration phase of Mehmood et al. [7] protocol

Figure 2: Authentication phase of Mehmood et al. [7] protocol
Mehmood et al. [7] presented a protocol for two-way authentication of patients and medical servers, declaring that it was resistant to most attacks and fulfilled various security needs. This section, however, proves that this protocol does not provide perfect forward secrecy and is vulnerable to DoS attacks.
The security system of Perfect Forward Secrecy assumes that an attacker should not be able to access the session key even if long term parameters, such as the server’s secret key, are compromised. However, if such a breach occurs in Mehmood et al.’s protocol, the attacker can, in fact, obtain the session key. To explain the matter, one can suppose that the attacker has the secret key of the server. Because parameter
Furthermore, due to the relationship
When the user sends the first message to the server, the initial action taken before authentication is decryption, which is a demanding operation. During this strain on the server, the attacker can repeatedly send the message, thus keeping the server extremely busy and unable to respond to requests.
4 A Secure and Efficient Protocol for Authentication and Key Exchange
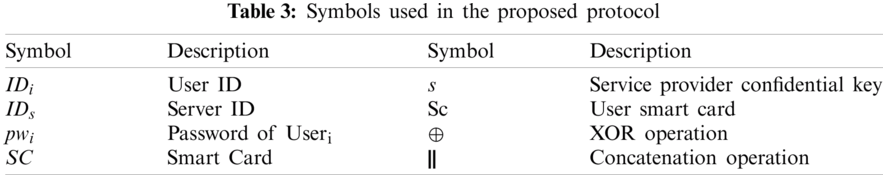
In order to address the drawbacks of Mehmood et al. [7] protocol, this work introduces a secure and efficient ECC-based protocol for authentication and key exchange. This scheme features registration, authentication, key agreement, and password update stages, for which a detailed description will be provided. Tab. 3 presents the symbols utilized in the proposed protocol.
As seen in Fig. 3, during the registration process, the patient selects his/her own ID (
Compute
Compute
Selects random number
Compute
Compute
Compute

Figure 3: Registration phase of the proposed protocol
4.2 Login and Authentication Phase
In this phase, the patient and server authenticate each other, after which the patient can log into the server. As presented in Fig. 4, during the login and authentication stage of the proposed protocol, the patient inserts his/her smart card into the card reader and enters the correct ID and password. Initially, through the following relationships, the smart card is verified as belonging to the patient in question and, therefore, not stolen.
Enters his/her
Compute
Compute
Compute
Check
Compute
Compute

Figure 4: Login and authentication phase of the proposed protocol
At this point, parameter
As soon as it receives the patient’s message, the server checks for its freshness. Possessing its own secret key, the server obtains parameter
Compute
Compute
Compute
Check
Now, the server selects the timestamp (
As soon as it receives the server’s message, the patient checks for its freshness. After creating the session key from the following relationship, the patient authenticates the received message to verify its authenticity and identity. In this manner, the login and authentication phase of the proposed protocol finishes.
Compute
Compute
Check
In this phase, the patient can securely change his/her password. To do so, the patient first enters the password (
Compute
Compute
Compute
Check
At this point, the patient enters the new password (
Compute
Compute
Compute
Compute
5 Security Analysis of the Proposed Protocol
The security parameters of the proposed protocol are discussed in the following sections.
According to Nikooghadam et al. [31], the security measure of Perfect Forward Secrecy assumes that an attacker cannot obtain the session key even if the secret key of one of the parties is disclosed or if long term parameters are exposed. In the proposed protocol, the session key is equal to
In anonymity, it is presumed that the attacker cannot access the identity of the parties if it intercepts all messages transmitted on the public channel. In the proposed protocol, even if the attacker hears all messages transmitted on the public channel, it will not be able to obtain the parties’ IDs.
In the replay attack, the attacker is assumed to intercept an old message from the public channel and send it to the parties after a period of time. In the proposed protocol, such attack does not occur due to the use of time stamps and random parameters.
A DoS attack occurs when a substantial operation, such as scalar multiplication, is performed by one of the two entities. The proposed protocol would not experience such an attack as no considerable jobs are undertaken, such as decoding or scalar multiplication.
Due to the two-way authentication between the patient and server, impersonation is not possible. One can consider the scenario in which the attacker sends fake parameters, i.e.,:
5.6 Server Impersonation Attack
Since there is a session key within the
In the insider attack, it is assumed that the attacker is on the server side and intends to acquire the user password. Consequently, in the registration stage, the proposed protocol does not send the patient’s password directly to the server. Therefore, the password is sent to the service provider in the form of
The assumption of the password guessing attack is that the user password cannot be guessed even if the attacker intercepts all the messages transmitted on the public channel. Because the user password is in the format of
5.9 Known-Session-Specific Temporary Information Attack
In this attack, it is presumed that the attacker cannot obtain nor construct the session key, even if it acquires random parameters. Furthermore, in the session key, there are long term parameters, such as
The stolen-verifier attack assumes that it is not possible for the attacker to access the session key if it has acquired the parameters within the server memory or the smart card. In the proposed protocol, since the server’s memory is tamper-proof, such parameters cannot be stolen. In addition, since there are no important parameters inside the smart card, the attacker cannot obtain the session key by stealing it.
6 Formal Security Analysis with Scyther
Scyther [8] is a powerful and effective tool for analyzing and identifying potential attacks and security protocol vulnerabilities. This official tool automatically analyzes protocol and scrutinizes its behavior when faced with most possible attacks. Implementation code Scyther tool is shown in Fig. 5.
Fig. 6 provides the output of the proposed protocol review by Scyther, i.e.,:
— The Niagree feature ensures the parties in communication are confident that messages are securely transmitted and in correct order between them.
— The Nisynch feature makes sure that messages exchanged between parties cannot be decrypted and resent.
— The Alive feature guarantees that the protocol steps are approved by the parties in communication.
— The Weakagree feature sees to it that the protocol does not impersonate.
— The secret property also ensures that the relevant parameter remains safe.
As shown in Fig. 6, the proposed authentication protocol provides all of the above features.

Figure 5: Implementation code of Scyther

Figure 6: Evaluation of proposed protocol by Scyther tool [8]
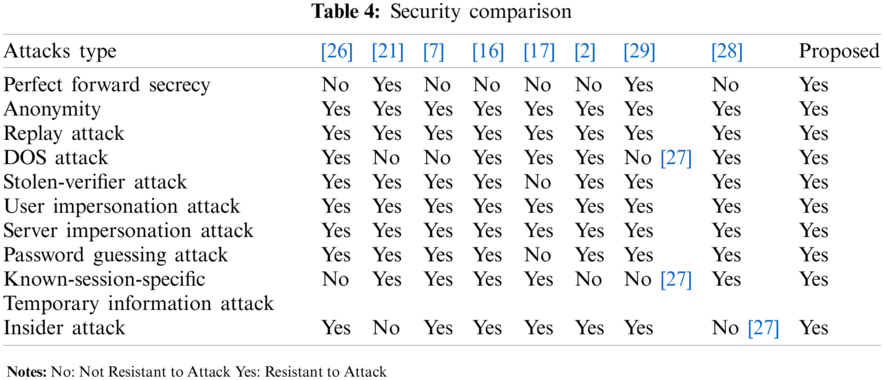
According to the material presented and evaluated by the usage of the Scyther tool, Tab. 4 compares the security of the proposed protocol with that of other similar protocols. Based on the information in this table, the proposed protocol is resistant to various attacks and meets various security requirements.
7 Analysis and Validation Using BAN Logic
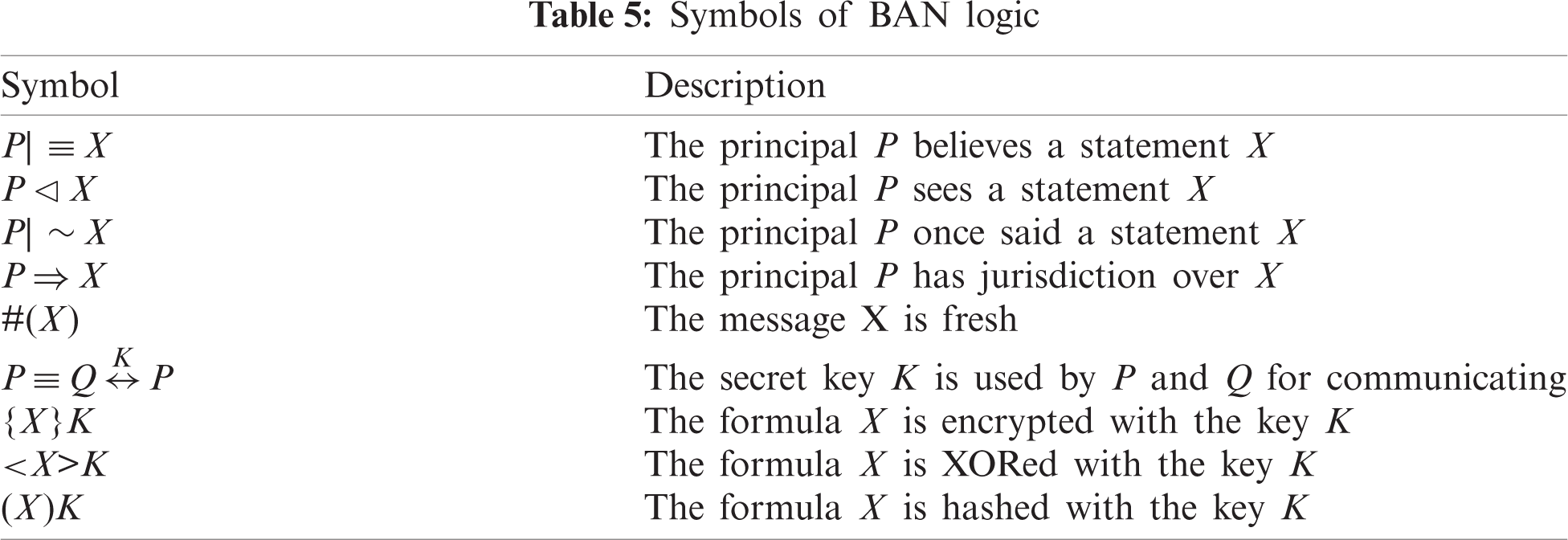
In this section, we analyze and validate our proposed design using BAN logic. The logical assumptions and rules of the Burrows–Abadi–Needham (BAN) logic, as well as the security objectives and ideal forms, are defined in (1) to (6). The symbols used are shown in Tab. 5.
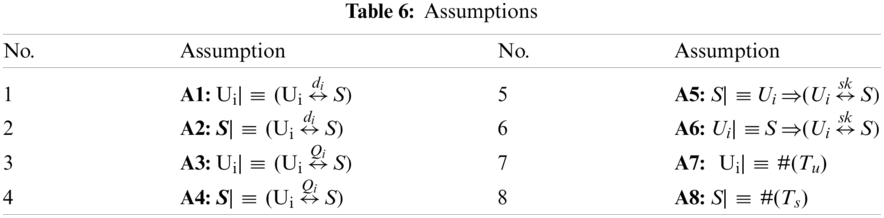
Some assumptions are shown in Tab. 6.
Goals are as follows:
S| ≡ (
Idealized forms are as follows:
Message 1:
Message 2: S →
Based on the assumptions and logical rules of BAN logic, we analyze the ideal form of the proposed protocol as follows: According to the Message 1, we can obtain the following:
R1: S ⊵ (
Based on the assumption A2, and after applying the H rule to R1, R2 can be deduced as:
R2: S| ≡
Based on the assumption A7, and after applying the nonce verification rule H to R2, R3 can be deduced as:
R3: S| ≡
Based on the Message 2, R4 can be deduced as:
R4:
Based on the assumption A4, and after applying the H rule to R4, R5 can be deduced as:
R5:
Based on the applying the nonce verification rule to R5, R6 can be deduced as:
R6:
Based on the assumptions A1, A3, A6, and the session key sk = h (
R
Based on the assumption A5, and after applying the jurisdiction rule to R7, R8 can be deduced (which is Goal1) as:
Based on the R3, assumptions A2, A4 and the session key sk = h (
R
Based on the assumption A6, and after applying the jurisdiction rule to R9, R10 can be deduced (which is Goal2) as:
R10: S| ≡ (
8 Analysis and Comparison of the Proposed Protocol’s Time Complexity with Other Similar Protocols
Based on research work by He et al. [30] the computation time of a fuzzy extraction operation, the time of performing a hash function, the time of performing symmetric encryption/decryption, the time of performing ECC point multiplication, the time of performing ECC point addition operation, and the time of modular exponentiation operation is 0.063075, 0.0005, 0.0087, 0.063075, 0.000262, and 0.522 s, respectively and the symbol for each are listed in the Tab. 7. Furthermore, for the communication cost, we have considered the size of an identifier or timestamp to be 32 bits, a nonce to be 64 bits, an EC point to be 320 bits, and a hash output to be 256 bits.
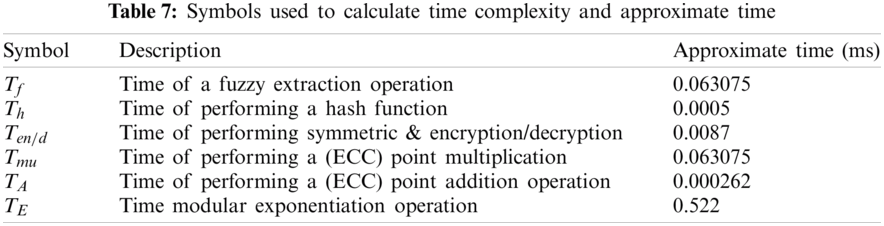
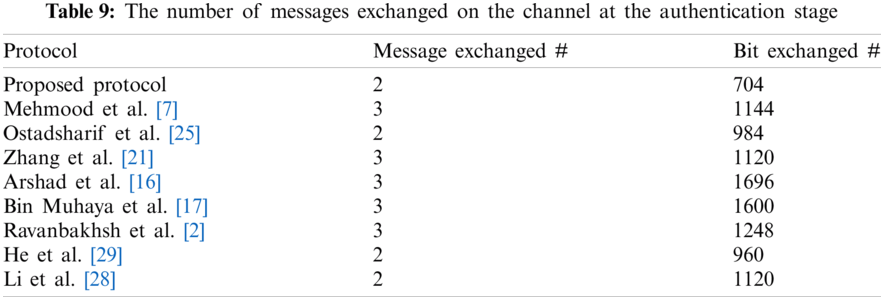
As exhibited in Tabs. 8 and 9, the proposed protocol performs better than or closer to similar protocols in the past. The importance of this issue is apparent when the proposed protocol is able to meet security requirements with less complexity than of most similar protocols.
Having done revealing flaws in perfect forward secrecy and preventing DoS attacks of authentication and key agreement scheme proposed by Mehmood et al, this work has proposed a secure and ultra-lightweight protocol for medical services communication. The proposed protocol was analyzed in term of secureness and performance during the authentication stage was measured. Formal analysis using Scyther tool proves its robustness against various attacks, and demonstrates its ability to provide various security features. During the authentication stage, measurement results showed that the proposed protocol outperforms other existing protocol and achieves a satisfactory computational time and less number of bits in the exchanged messages. Telemedicine provides easy and secure access to patient information by physicians and access to the large number of specialist physicians needed by patients, even patients in remote and underprivileged areas, while saving time and money.
As future work, the proposed protocol can be implemented hardware-wise using the ARM and FPGA programming languages and the Cortex-M3 Microcontroller board, and the results can be reviewed.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. O. Mir and M. Nikooghadam, “A secure biometrics based authentication with key agreement scheme in telemedicine networks for e-health services,” Wireless Personal Communication, vol. 83, no. 4, pp. 2439–2461, 2015. [Google Scholar]
2. N. Ravanbakhsh and M. Nazari, “An efficient improvement remote user mutual authentication and session key agreement scheme for e-health care systems,” Multimedia Tools and Applications, vol. 77, no. 1, pp. 55–88, 2016. [Google Scholar]
3. A. Ostad-Sharif, D. Abbasinezhad-Mood and M. Nikooghadam, “An enhanced anonymous and unlinkable user authentication and key agreement protocol for TMIS by utilization of ECC,” International Journal of Communication Systems, vol. 32, no. 5, pp. e3913, 2019. [Google Scholar]
4. H. Amintoosi and M. Nikooghadam, “A novel provably-secure ECC-based authentication and key management protocol for telecare medical information systems,” in Proc. of 9th Int. Conf. on Computer and Knowledge Engineering, Mashhad, Iran, pp. 85–90, 2019. [Google Scholar]
5. N. Radhakrishnan and M. Karuppiah, “An efficient and secure remote user mutual authentication scheme using smart cards for telecare medical information systems,” Informatics in Medicine Unlocked, vol. 16, no. 2, pp. 100092, 2019. [Google Scholar]
6. M. Safkhani and A. Vasilakos, “A new secure authentication protocol for telecare medicine information system and smart campus,” IEEE Access, vol. 7, pp. 23514–23526, 2019. [Google Scholar]
7. Z. Mehmood, A. Ghani, G. Chen and A. S. Alghamdi, “Authentication and secure key management in e-health services: A robust and efficient protocol using biometrics,” IEEE Access, vol. 7, pp. 113385–113397, 2019. [Google Scholar]
8. C. J. F. Cremers, “Scyther-semantics and verification of security protocols,” Ph.D. Thesis. Eindhoven University of Technology, 2006. [Google Scholar]
9. Z.-Y. Wu, Y.-C. Lee, F. Lai, H.-C. Lee and Y. Chung, “A secure authentication scheme for telecare medicine information systems,” Journal of Medical Systems, vol. 36, no. 3, pp. 1529–1535, 2010. [Google Scholar]
10. H. Debiao, C. Jianhua and Z. Rui, “A more secure authentication scheme for telecare medicine information systems,” Journal of Medical Systems, vol. 36, no. 3, pp. 1989–1995, 2011. [Google Scholar]
11. Z. Tan, “An efficient biometrics-based authentication scheme for telecare medicine information systems,” Networks, vol. 2, no. 3, pp. 200–204, 2013. [Google Scholar]
12. H. Arshad and M. Nikooghadam, “Three-factor anonymous authentication and key agreement scheme for telecare medicine information systems,” Journal of Medical Systems, vol. 38, no. 12, pp. 1, 2014. [Google Scholar]
13. D. Giri, T. Maitra, R. Amin and P. D. Srivastava, “An efficient and robust RSA-based remote user authentication for telecare medical information systems,” Journal of Medical Systems, vol. 39, no. 145, pp. 770, 2014. [Google Scholar]
14. M. K. Khan and S. Kumari, “An authentication scheme for secure access to healthcare services,” Journal of Medical Systems, vol. 37, no. 4, pp. 201, 2013. [Google Scholar]
15. R. Amin and G. P. Biswas, “An improved RSA based user authentication and session key agreement protocol usable in TMIS,” Journal of Medical Systems, vol. 39, pp. 1–14, 2015. [Google Scholar]
16. H. Arshad, V. Teymoori, M. Nikooghadam and H. Abbassi, “On the Security of a two-factor authentication and key agreement scheme for telecare medicine information systems,” Journal of Medical Systems, vol. 39, no. 8, pp. 1, 2015. [Google Scholar]
17. F. T. Bin Muhaya, “Cryptanalysis and security enhancement of Zhu’s authentication scheme for telecare medicine information system,” Security and Communication Networks, vol. 8, no. 2, pp. 149–158, 2014. [Google Scholar]
18. S. A. Chaudhry, M. T. Khan, M. K. Khan and T. Shon, “A multiserver biometric authentication scheme for TMIS using elliptic curve cryptography,” Journal of Medical Systems, vol. 40, no. 11, pp. article–no. 230, 2016. [Google Scholar]
19. Q. Jiang, Z. Chen, B. Li, J. Shen, L. Yang et al., “Security analysis and improvement of bio-hashing based three-factor authentication scheme for telecare medical information systems,” Journal of Ambient Intelligence and Humanized Computing, vol. 9, no. 4, pp. 1061–1073, 2017. [Google Scholar]
20. Y. Lu, L. Li, H. Peng and Y. Yang, “An enhanced biometric-based authentication scheme for telecare medicine information systems using elliptic curve cryptosystem,” Journal of Medical Systems, vol. 39, no. 32, pp. 1, 2015. [Google Scholar]
21. L. Zhang, Y. Zhang, S. Tang and H. Luo, “Privacy protection for e-health systems by means of dynamic authentication and three-factor key agreement,” IEEE Transactions on Industrial Electronics, vol. 65, no. 3, pp. 2795–2805, 2018. [Google Scholar]
22. S. F. Aghili, H. Mala, M. Shojafar and P. Peris-Lopez, “LACO: Lightweight three-factor authentication, access control and ownership transfer scheme for e-health systems in IoT,” Future Generation Computer Systems, vol. 96, no. 1, pp. 410–424, 2019. [Google Scholar]
23. A. Ostad-Sharif, D. Abbasinezhad-Mood and M. Nikooghadam, “A robust and efficient ECC-based mutual authentication and session key generation scheme for healthcare applications,” Journal of Medical Systems, vol. 43, no. 10, pp. 175, 2018. [Google Scholar]
24. S. Kumari, P. Chaudhary, C.-M. Chen and M. K. Khan, “Questioning key compromise attack on Ostad-Sharif et al.’s authentication and session key generation scheme for healthcare applications,” IEEE Access, vol. 7, pp. 39717–39720, 2019. [Google Scholar]
25. A. Ostad-Sharif, M. Nikooghadam and D. Abbasinezhad-Mood, “Design of a lightweight and anonymous authenticated key agreement protocol for wireless body area networks,” International Journal of Communication Systems, vol. 32, no. 12, pp. e3974, 2019. [Google Scholar]
26. S. Khatoon, S. M. M. Rahman, M. Alrubaian and A. Alamri, “Privacy-preserved, provable secure, mutually authenticated key agreement protocol for healthcare in a smart city environment,” IEEE Access, vol. 7, pp. 47962–47971, 2019. [Google Scholar]
27. K. Sowjanya, M. Dasgupta and S. Ray, “An elliptic curve cryptography based enhanced anonymous authentication protocol for wearable health monitoring systems,” International Journal of Information Security, vol. 19, no. 1, pp. 129–146, 2019. [Google Scholar]
28. X. Li, J. Peng, S. Kumari, F. Wu, M. Karuppiah et al., “An enhanced 1-round authentication protocol for wireless body area networks with user anonymity,” Computers & Electrical Engineering, vol. 61, pp. 238–249, 2017. [Google Scholar]
29. D. He, S. Zeadally, N. Kumar and J.-H. Lee, “Anonymous authentication for wireless body area networks with provable security,” IEEE Systems Journal, vol. 11, no. 4, pp. 2590–2601, 2017. [Google Scholar]
30. D. He, N. Kumar, M. Khan and J. Lee, “Anonymous two-factor authentication for consumer roaming service in global mobility networks,” IEEE Transactions on Industrial Electronics, vol. 59, no. 4, pp. 811–817, 2013. [Google Scholar]
31. M. Nikooghadam and H. Amintoosi, “Perfect forward secrecy via an ECC-based authentication scheme for SIP in VoIP,” Journal of Supercomputer, vol. 76, no. 4, pp. 3086–3104, 2019. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |