DOI:10.32604/cmc.2021.018549

| Computers, Materials & Continua DOI:10.32604/cmc.2021.018549 |  |
| Article |
A Lightweight Certificate-Based Aggregate Signature Scheme Providing Key Insulation
Department of Software Convergence in Soonchunhyang University, Asan-si, 31538, Korea
*Corresponding Author: Im-Yeong Lee. Email: imylee@sch.ac.kr
Received: 12 March 2021; Accepted: 16 April 2021
Abstract: Recently, with the advancement of Information and Communications Technology (ICT), Internet of Things (IoT) has been connected to the cloud and used in industrial sectors, medical environments, and smart grids. However, if data is transmitted in plain text when collecting data in an IoT-cloud environment, it can be exposed to various security threats such as replay attacks and data forgery. Thus, digital signatures are required. Data integrity is ensured when a user (or a device) transmits data using a signature. In addition, the concept of data aggregation is important to efficiently collect data transmitted from multiple users (or a devices) in an industrial IoT environment. However, signatures based on pairing during aggregation compromise efficiency as the number of signatories increases. Aggregate signature methods (e.g., identity-based and certificateless cryptography) have been studied. Both methods pose key escrow and key distribution problems. In order to solve these problems, the use of aggregate signatures in certificate-based cryptography is being studied, and studies to satisfy the prevention of forgery of signatures and other security problems are being conducted. In this paper, we propose a new lightweight signature scheme that uses a certificate-based aggregate signature and can generate and verify signed messages from IoT devices in an IoT-cloud environment. In this proposed method, by providing key insulation, security threats that occur when keys are exposed due to physical attacks such as side channels can be solved. This can be applied to create an environment in which data is collected safely and efficiently in IoT-cloud is environments.
Keywords: Internet of things; certificate-based aggregate signature; key insulation; cloud; lightweight; physical attack
Recent developments in Information and Communications Technology (ICT), the Internet of Things (IoT) have facilitated industrial “smartization”; smart factories and smart industries that link the real and virtual worlds via Cyber Physical Systems (CPS). A CPS processes tasks and information of the physical world in virtual space using IoT and other networks, and continuously adapts to changes without human intervention. If a CPS is to function well, the nature of the IoT environment is important because many physical things must be connected to sensors and communication devices. In an IoT-cloud environment, data is collected from IoT devices and stored safely in the cloud, whereby legitimate users can access the cloud and check the data. It is currently mainly used in Industrial Internet of Things (IIoT) environments such as manufacturing, transportation, and energy fields, as well, as medical environments and smart homes [1–3]. However, if sensors transmit plain text, data forgery and replay attacks are possible. In particular, millions of dollars worth of assets could be at risk if communications are not secured in large network systems such as IIoT environments [4].
To solve this problem, a lightweight cryptography technology is required to provide data confidentiality, and a digital signature technology that ensures the integrity of the data generated by a sensor device in an IoT environment is necessary. A sensor signs all messages and passes them (through a gateway) to the cloud as shown in Fig. 1. A user verifies the signature, ensuring message integrity. In an IoT environment, users can receive safe services only when the integrity of data collected from all devices is ensured. In addition, in an environment where large-scale data is collected such as IIoT, the concept of aggregation is important to efficiently distribute data.
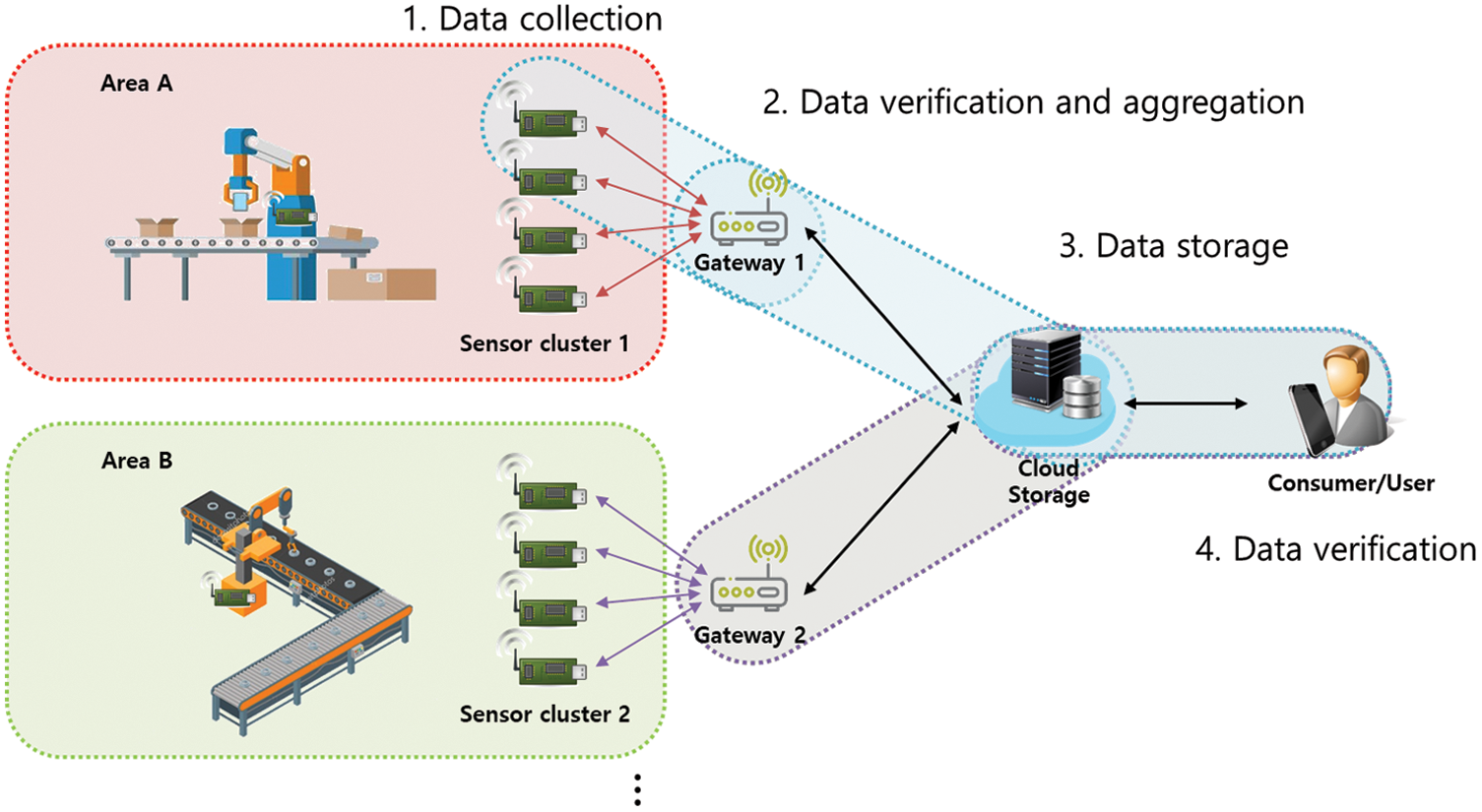
Figure 1: Data signing and verification process in the IoT-cloud (e.g., smart factory)
However, among previously studied aggregate signature methods, there are many methods that create aggregate signatures using pairing operations. This is inefficient. The computational burden rises as the number of signatories increases. An early digital signature method used a Public Key Infrastructure (PKI) encryption system. This was followed by signature and aggregate signature methods employing Identity-Based Cryptography (IBC), Identity-Based Signatures (IBS), Identity-Based Aggregate Signatures (IBAS), and Certificateless Cryptography (CLC). However, both the IBC and CLC methods pose key escrow and/or key distribution problems [5–7]. To solve these problems, Certificate-Based Signatures (CBS) and Certificate-Based Aggregate Signatures (CB-AS) have been proposed, and studies are being conducted to ensure they meet a number of security requirements, such as data integrity, non-repudiation, and resistance to the forgery of signatures.
In this paper, we analyze CB-AS and propose a new lightweight CB-AS scheme for IoT-cloud environments. Specifically, this proposed method is an efficient CB-AS method that provides key insulation, and the contribution of the paper is as follows: 1) The signature cannot be forged by an attacker. 2) In order to solve the key exposure problem due to physical attacks such as side-channel attacks, key insulation is applied to continuously update the signature keys generated in the sensor devices. 3) The size of the entire signature is reduced in group environments, such as IIoT, by a gateway collecting and aggregating signed messages from multiple sensor devices. The final verifier can verify the signatures for multiple messages with one verification, and this provides integrity and non-repudiation functions for messages. 4) Since it is performed using pairing-free operations in the signature generation, aggregation, and verification steps, the operation efficiency is high compared to the aggregate signature methods proposed using pairings.
The proposed scheme in this paper focuses on integrity rather than confidentiality of data. It will be applicable to a sensor device network environment that safely collects data continuously in real time in an IIoT environment that has been expanded to an IoT-cloud environment. The paper is structured as follows. Section 2 deals with related studies and explains the CBS and CB-AS constructs, security threats, and previously studied key insulation and CB-AS systems. Section 3 introduces the security requirements of Certificate-Based Key Insulated Aggregate Signatures (CB-KIAS). Section 4 describes our method in detail. Section 5 analyzes the security and efficiency of the method, and Section 6 is the conclusion.
This section describes the Elliptic Curve Discrete Logarithm Problem (ECDLP), digital signatures, and key insulation. It also reviews studies on CB-AS.
Elliptic curve encryption is a public key encryption method using the fact that the discrete logarithm problem on the elliptic curve is difficult. Compared to conventional public key cryptography, the same security can be obtained with fewer bits, encryption is processed at a high speed, and key management is easy because a short key is used. Therefore, it is widely used in IoT and other lightweight environments. The elliptic curve for elliptic curve encryption is a set of solutions (X, Y) of the equation
A digital signature is a method of verifying one’s identity in a network, and generally uses cryptographic technology related to Public Key Cryptography (PKC). When a message is signed with the sender’s private key and transmitted, the receiver uses the sender’s public key to verify the validity of the signature. This provides a non-repudiation function via the signed message, that can prove that a message has been transmitted from the sender and provides the signer’s authentication and message integrity.
Digital signatures started from PKC based signatures and have evolved into various types of signatures such as IBS, Certificateless Signature (CLS), and CBS, and research on signatures that aggregate many signatures into one signature is also being conducted [9–12]. PKC is a security technology that utilizes public key cryptography and can provide various functions such as signing and authentication. However, since PKC uses a certificate to verify a user’s public key, there is a storage problem for the certificate and overhead for management such as distribution, verification, and revocation.
Therefore, Shamir developed an IBS. In IBS the public key is a user identifier, eliminating the certificate management overhead [13–15]. However, a key escrow problem occurs because all users require private keys [16–18].
To solve this problem, Gentry et al. (2003) developed a (CBC) scheme that combined the advantages of the PKC and IBC. A user creates a public/private key pair and receives a certificate with an identity and a public key from a trusted Certification Authority (CA). The CBC certificate serves as a private (secret) key for the user. Signing and decryption are performed employing the user’s certificate and private key simultaneously. Thus, the key escrow problem caused by the Key Generation Center (KGC) issuance of keys to each IBS owner is solved, and certificate management (problematic with the earlier PKC schemes) is simplified. Additionally, public key verification overload is eliminated. There are CBS and CB-AS techniques using CBC [19–26].
In signature-based methods, the private key used in signing must be absolutely secure. If this key is exposed, there are several security threats to the smart factory of Fig. 1. Assuming that the attacker has exposed a key by physically attacking a sensor in the factory, the attacker can use that key to forge a message and signature from the sensor. This can trigger errors in manufacturing and the entire system could stop. This is fatal in a large, interconnected environment such as a smart factory or other IIoT. It is essential to safely manage and store the private keys, and among the various methods to do this is key insulation technology.
Key insulation was introduced by Dodis in 2002. Users update their private keys using a physically secure device termed a Helper (Fig. 2) [27]. Each user creates a public key, a private key, and a temporary secret key for initial signature. After that, the helper takes the user’s public key, creates key, known as an update key, that can be used for period t, and sends it to the user. With the received update key, the user updates the existing signature key with a signature key that can be used for period t. Then, the Helper issues a new key to be used during the following period, t′. The IBC, CBC, and CLS methods use key insulation methods to solve the problem of key exposure [28–31].
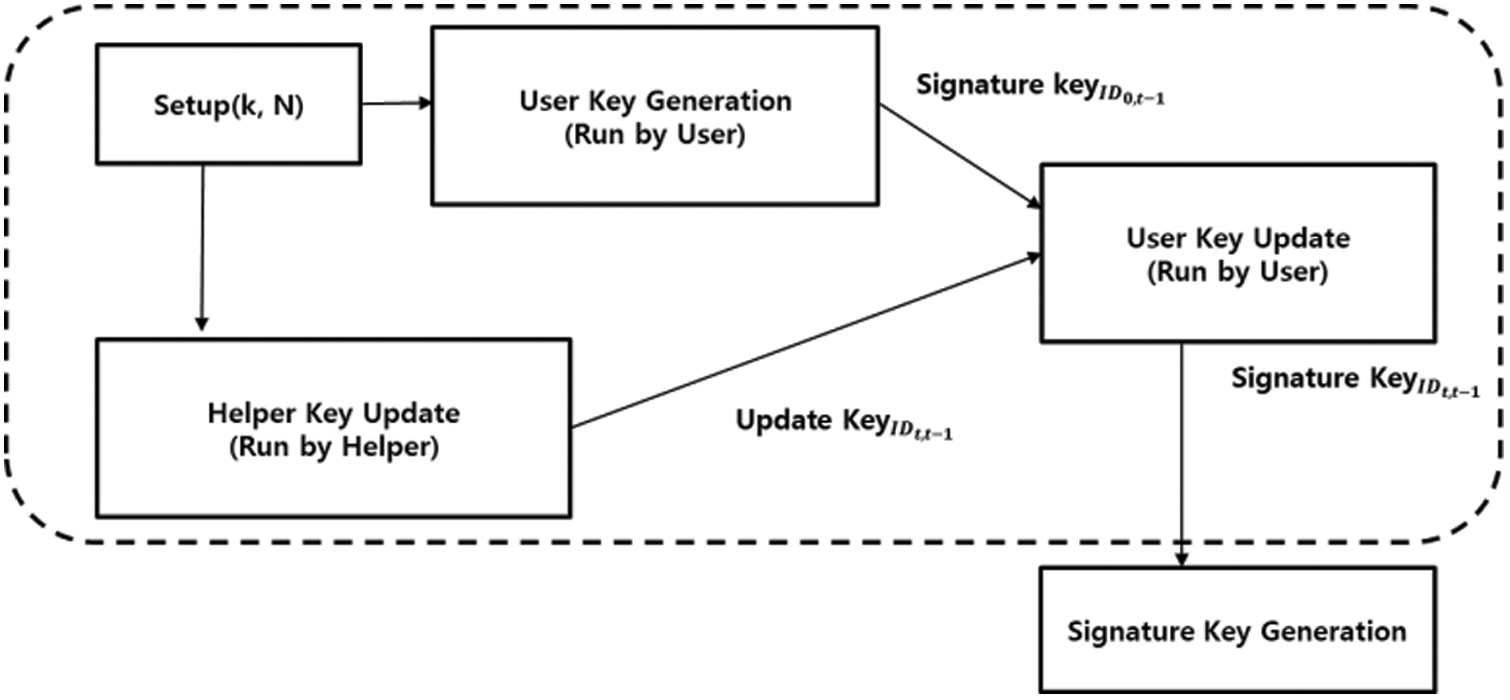
Figure 2: Signature key generation structure using key insulation
2.4 Certificate-Based Aggregate Signatures (CB-AS)
A CBS is a signature for a single message. The CB-AS method collects multiple messages and creates an aggregated signature. In CBS, if multiple senders transmit data, a signature is generated for each message. Thus, the number of signatures increases as the number of signatories rises, and the verifier must check all signatures. CB-AS aggregates the multiple signatures into one. Sender public keys are used for verification, but all signatures are verified together. This reduces verification and memory overheads, computing cost, and bandwidth. Many pairing-free-based CB-AS methods have been applied in IIoT environments such as smart factories [23–26].
Fig. 3 is a diagram showing the basic structure of CB-AS. The CB-AS method features a CBS that first registers a sensor with a CA and then issues a certificate. In general, the technique features seven phases. The Setup and Certificate Generate (CertGen) phases are performed by the CA. During Setup, the public parameters and a master CA key are created. In the CertGen phase, when a user requests, a certificate corresponding to the user ID and public key is generated and transmitted. In the Key Generate (KeyGen) phase, the user (signatory) generates a public/private key pair and then a signature for messages using the certificate, the public and private keys, and his/her identity. In the Sign phase, the user signs the message and sends it to the gateway, which verifies the message and signature. Messages and signatures from multiple signatories are aggregated into one by the gateway and transmitted to cloud storage. The verifier checks all messages and the aggregated signature [23–26].
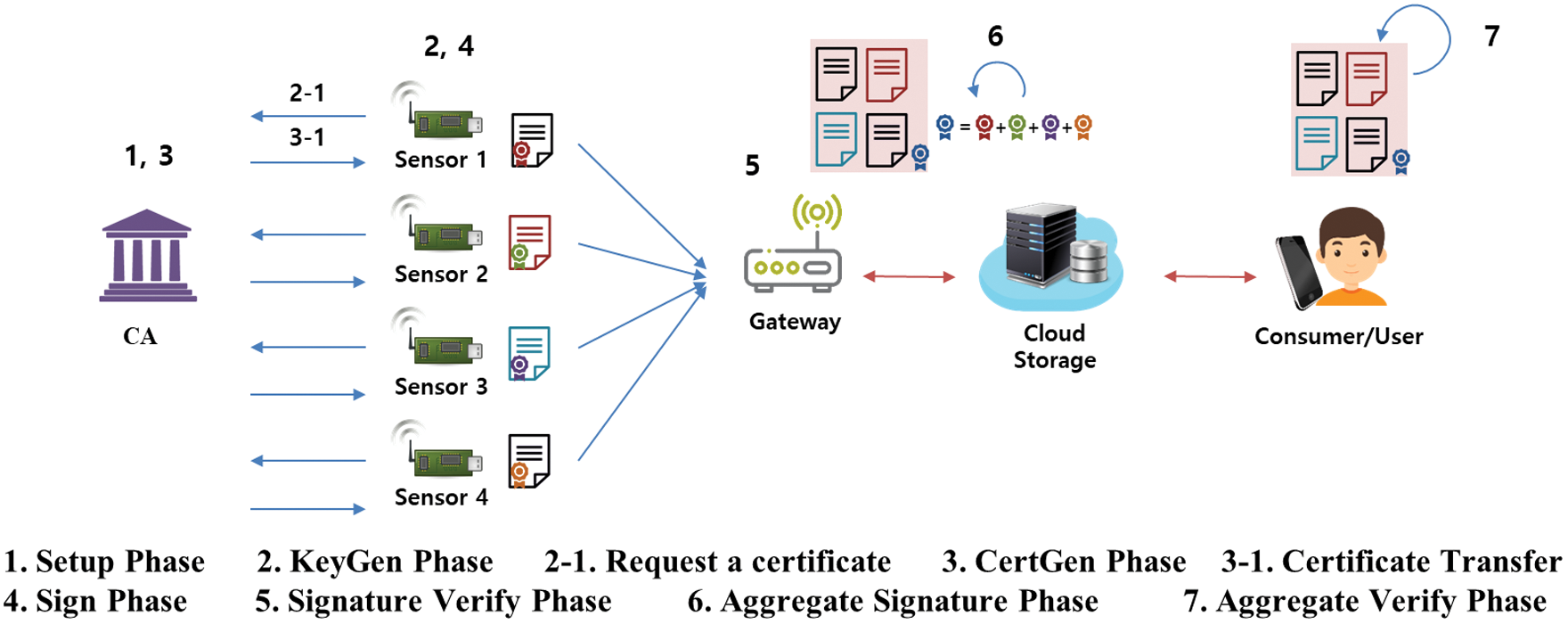
Figure 3: Structure of certificate-based aggregate signature
The CB-AS method is vulnerable to forgery of messages and signatures. The public CB-PKC key can be authenticated via a certificate, but an attacker may substitute the public key of another user. A public key replacement attack on a CBS may forge the signature that device (A) sends to device (B) and replace the public key of device (A) (which is open for signature verification) with a public key generated by the attacker. Such an attack is possible because the substituted public key of the attacker, which can bypass verification of a signature generated using the private key of device (A), cannot be authenticated as the public key of device (A). In addition, the CA can forge the signature of device (A) using a certificate [25–27].
The security model of CB-AS must counter two types of attacks. The two models are similar to games in which competent attackers
Security Attack Type I, Adversary A1
In Security Attack Type I, II, an attack is performed based on the CB-KIAS model, which provides a key insulation function.
It is possible to use the oracle to query Setup, KeyGen, PublicKeyReplace, CertGen, Signature Key and SignGen (depending on the competence of
–AI has never requested ID′ through the Signature Key oracle.
–AI has never requested
–
Definition 1. In CB-AS Attack Type I, if there is no attacker
Security Attack Type II, Adversary A2
–
–
Definition 2. In CB-KIAS Attack Type II, it is existentially impossible to engage in forgery in the absence of an attacker
2.5 Analysis of Existing CB-AS Schemes
CB-AS was first proposed by Gentry in 2003, and recently proposed CB-AS schemes have many efficient methods that do not use pairing operations. Tab. 1 shows existing CBS, IBAS, and CB-AS methods that have been studied as well as the proposed method. The Li et al. [32] scheme solves the problem of key exposure due to physical attack by using a certificate-based signature using a key insulation technique. However, since it uses a pairing operation, there is a disadvantage in that the computational amount is high, and in 2017, Lu et al. [30] raised the problem that the signature could be forged by a malicious CA in the Li et al. scheme. This is because some (e.g.,

Xiong et al. [22] proposed an efficient CBS scheme that does not use a pairing operation. As a feature, a key insulation technique is applied to solve the security threats that occur when the key is exposed by a physical attack. The system affords high computational efficiency in lightweight IoT environments. However, as it lacks an aggregation function, it is necessary to individually verify all data from multiple sensors.
The Reddy et al. [29] scheme and the Shen et al. [11] scheme employ identity-based aggregate signatures, but only the Reddy et al. scheme features key insulation. Since both methods use pairing, and the larger the number of signatures, the higher the amount of computation. Also, since IBS allow the KGC to create a user’s key, curiously, a key escrow issue can arise from KGC. To solve the key escrow problem, use need to create their own keys for signing.
The methods of the Chen et al. [24] scheme and the Verma et al. second method feature CB-AS. Either can be used in IoT and IIoT environments because computation is efficient (pairing is not employed). However, key insulation is not provided. Xiong et al. showed that one of the methods of Verma et al. was susceptible to public key replacement attack and signature forgery by a malicious CA. As in Attack Type I in 2.4.2, assuming that the attacker A1 tries to forge a valid signature on all messages
Xiong et al. [31] proposed a second method. It is a CB-KIAS proposed to solve the signature forgery problem occurring in the Verma et al. method discussed above. This Xiong et al. method includes both the aggregation function and key insulation function required by this proposed scheme. However, since a pairing operation is used, there is a disadvantage considering the amount of operations increase according to the number of signatures when generating signatures, verifying signatures, and verifying aggregated signatures.
The goal of our proposed method is to provide overall operational efficiency by not using a pairing operation unlike the second Xiong et al. method. In addition, we will solve the problem of forged signatures due to the attacks presented in Section 2.4.2, and respond to security threats that occur when keys are exposed due to physical attacks through periodic key updates in a key insulation method.
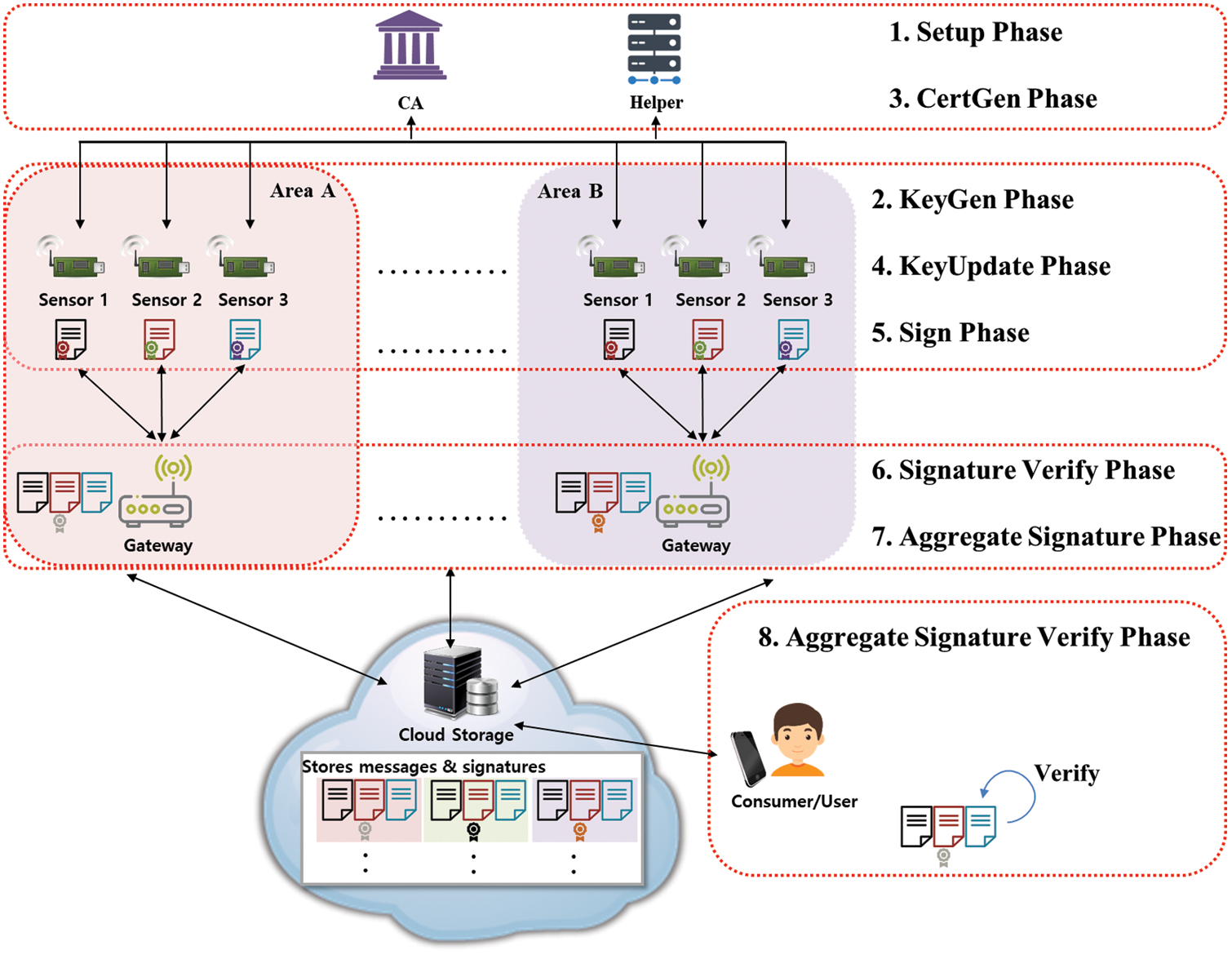
Figure 4: Scenario of the proposed scheme
In this paper, we propose a certificate-based aggregate signature scheme that provides key insulation for secure data collection and processing through sensor networks in IoT-cloud environments. Fig. 4 is a schematic diagram of the scenario of this proposed method. In a network environment connected to a virtual CPS space, sensors generate data, sign messages, and send them to a gateway. Each gateway serves as an aggregator that verifies, collects, and aggregates data from multiple sensors and stores the information in the cloud. A user who wants to check the aggregated data can download the information and perform a single verification. The CA initially registers each sensor and issues certificates when requested. The Helper creates and updates (partial) keys for each sensor. The proposed scheme satisfies the security requirements for signature forgery prevention and non-repudiation of signatures. Aggregate signatures based on pairing-free operations can reduce the size of signatures in storage and reduce the amount of verification computations for validators. In addition, when a sensor device generates a signature key, a key insulation method is applied to periodically update the key used for signatures. This can prevent a security threat that may occur due to the exposure of the sensor key due to a physical attack such as a side-channel attack.
The system parameters are:
The eight phases of our scheme include a KeyUpdate key insulation process and the seven phases of the CB-AS listed in Section 2.4.1.
4.3 Description of the Proposed Scheme
Setup is performed by entering the security parameter K into the CA, and the public key
Sensor IDi selects a random value
The CA receives
The CA transmits the certificate to the sensor and sends the registered sensor information to the Helper via a secure channel.
The KeyUpdate phase is divided into three steps. First, when the Helper sends a temporary value for signing key generation to the sensor device, the device creates a temporary key for signing. The second step is for the Helper to generate and transmit an update value udskIDi, t that the sensor uses to update the signature key of the sensor device. Finally, the sensor takes the received update value and updates the signature key,
Helper key update step: The Helper generates the update value udskIDi, t employing the user information received from the CA and transmits it to the sensor.
Sensor signature key update: The sensor receives udskIDi, t from the Helper and can update the existing temporary signature key TSKIDi, t −1 to TSKIDi, t as follows. (The TSKIDi, t key can be used for time t.)
The sensor signs message
Step 1. The sensor device calculates
Step 2. The value required for signature is generated as follows and the signature is output.
The gateway receives signed messages from sensors and verifies the signatures using IDi, DPKIDi,
4.3.7 Aggregate Signature Phase
When messages are received from multiple sensors, the gateway performs verification, and then aggregates messages with valid signatures. Signed messages received from n sensors are collected under one signature. Aggregation can be expressed as in Eq. (14), where W is the signature of message (
4.3.8 Aggregate Signature Verify Phase
Users who wish to check aggregated messages download them from the cloud. Then the users verify the validity of the aggregated signature W using
In this section, we will identify whether the proposed method meets the data integrity, forgery resistance, and key leakage resilience requirements from Section 3.
Attacker
An IoT environment requires efficient computation. In a network environment in which many sensor devices participate in communications, the system is required to work without problems using low-performance devices with either Elliptic Curve Cryptography (ECC) or paring-free based lightweight cryptographic operations rather than heavy cryptographic operations using on Rivest–Shamir–Adleman (RSA) and pairing operations. In the aggregation process, as the number of messages and signatures increases, the total time for signature, aggregation, and verification increases in direct proportion. In this proposed method, pairing operations are not used. Compared to other pairing-free methods, ECC-based elliptic curve addition and multiplication operations are efficiently applied to reduce the total operation time, and the amount of calculation is more efficient than the pairing operations applied in the existing Xiong et al. [31] scheme. In addition, compared to the Chen et al. and Reddy et al. methods, which do not use pairing operations, as shown in Tab. 2, the computational efficiency is high, and the computational amount is similar to the Verma et al. methods. For the simulation environment of this proposed method and the existing methods, Windows 10 was used, running on an Intel i5-4690 processor with 3.50 GHz clock rate and 8 GB of memory. The ECC implementation used a Koblitz elliptic curve

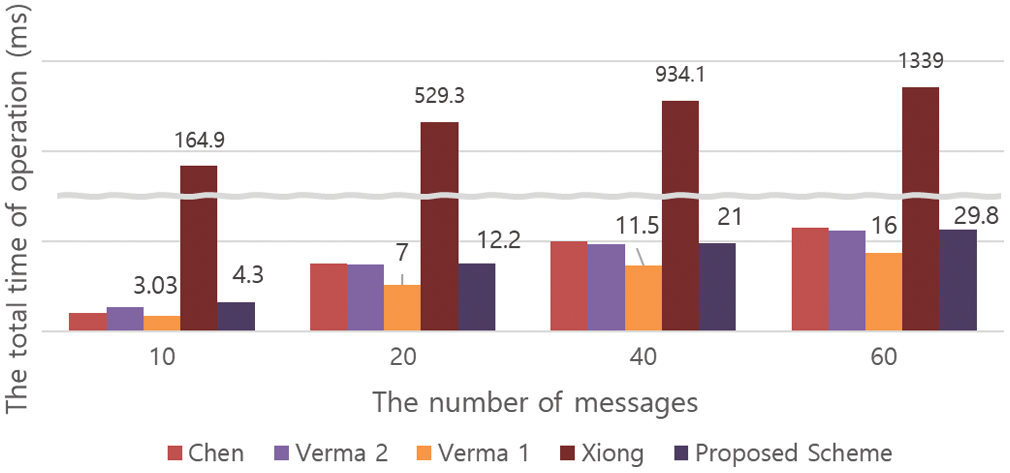
Figure 5: Comparison of total computation time between the proposed scheme and existing schemes
The proposed scheme is a certificate-based aggregate signature scheme that provides key insulation for secure and efficient data collection and provision in IoT-cloud environments. As a feature of this proposed scheme, signatures cannot be forged by an attacker, and the signature keys generated in the sensor devices are continuously updated by applying a key insulation technique to solve the key exposure problem caused by physical attacks such as side-channels attacks. In addition, the aggregate signature function allows the signatures of messages received from multiple sensor devices to be aggregated into one signature, thereby reducing the total size of the signature. Additionally, the final verifier can verify the signature of multiple messages with a single verification. This provides integrity and reliability for messages, and can be used in environments such as IIoT. Finally, since it is performed using pairing-free operations in the signature generation, aggregation, and verification phases, the operation efficiency is high compared to CB-AS methods proposed using pairings (Tab. 2).
For future research, it is necessary to study signcryption that can add data encryption for the confidentiality of data transmitted in the IoT environment. In particular, research on weight reduction to reduce the amount of computations performed in each phase for efficient communication between IoT devices should also be conducted.
Funding Statement: This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (NRF-2019R1A2C1085718) and was supported by the Soonchunhyang University Research Fund.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. M. Zolanvari, M. A. Teixeira, L. Gupta, K. M. Khan and R. Jain, “Machine learning-based network vulnerability analysis of industrial internet of things,” IEEE Internet of Things Journal, vol. 6, no. 4, pp. 6822–6834, 2019. [Google Scholar]
2. J. W. Jang, S. Kwon, S. Kim, J. Seo, J. Oh et al., “Cybersecurity framework for IIoT-based power system connected to microgrid,” KSII Transactions on Internet and Information Systems, vol. 14, no. 5, pp. 2221–2235, 2020. [Google Scholar]
3. M. M.Sha and M. P. Rahamathulla, “Cloud-based healthcare data management framework,” KSII Transactions on Internet and Information Systems, vol. 14, no. 3, pp. 1014–1025, 2020. [Google Scholar]
4. A. R. Sadeghi, C. Wachsmann and M. Waidner, “Security and privacy challenges in industrial internet of things,” in 2015 52nd ACM/EDAC/IEEE Design Automation Conf., San Francisco, CA, USA, pp. 1–6, 2015. [Google Scholar]
5. W. Diffie and M. Hellman, “New directions in cryptography,” IEEE Trans. Inf. Theory, vol. 22, no. 6, pp. 644–654, 1976. [Google Scholar]
6. A. Shamir, “Identity-based cryptosystems and signature schemes,” in Workshop on the Theory and Application of Cryptographic Techniques, Berlin, Heidelberg: Springer, pp. 47–53, 1984. [Google Scholar]
7. S. S. Al-Riyami and K. G. Paterson, “Certificateless public key cryptography,” in Int. Conf. on the Theory and Application of Cryptology and Information Security, Berlin, Heidelberg: Springer, pp. 452–473, 2003. [Google Scholar]
8. N. Koblitz, “Elliptic curve cryptosystems,” Mathematics of computation, vol. 48, no. 177, pp. 203–209, 1987. [Google Scholar]
9. D. Boneh, C. Gentry, B. Lynn and H. Shacham, “Aggregate and verifiably encrypted signatures from bilinear maps,” in Int. Conf. on the Theory and Applications of Cryptographic Techniques, Berlin, Heidelberg: Springer, pp. 416–432, 2003. [Google Scholar]
10. K. A. Shim, “An ID-based aggregate signature scheme with constant pairing computations,” Journal of Systems and Software, vol. 83, no. 10, pp. 1873–1880, 2010. [Google Scholar]
11. L. Shen, J. Ma, X. Liu, F. Wei and M. Miao, “A secure and efficient id-based aggregate signature scheme for wireless sensor networks,” IEEE Internet of Things Journal, vol. 4, no. 2, pp. 546–554, 2016. [Google Scholar]
12. X. Yang, R. Liu, M. Wang and G. Chen, “Identity-based aggregate signature scheme in vehicle ad-hoc network,” in 2019 4th Int. Conf. on Mechanical, Control and Computer Engineering, IEEE, pp. 1046–10463, 2019. [Google Scholar]
13. F. Hess, “Efficient identity-based signature schemes based on pairings,” in Int. Workshop on Selected Areas in Cryptography, pp. 310–324, 2002. [Google Scholar]
14. H. Du and Q. Wen, “An efficient identity-based short signature scheme from bilinear pairings,” in Int. Conf. on Computational Intelligence and Security, pp. 725–729, 2007. [Google Scholar]
15. I. Ali, T. Lawrence and F. Li, “An efficient identity-based signature scheme without bilinear pairing for vehicle-to-vehicle communication in VANETs,” Journal of Systems Architecture, vol. 103, no. 8, pp. 101692, 2020. [Google Scholar]
16. P. Kumar, S. Kumari, V. Sharma, A. K. Sangaiah, J. Wei et al., “A certificateless aggregate signature scheme for healthcare wireless sensor network, sustainable computing,” Informatics and Systems, vol. 18, pp. 80–89, 2018. [Google Scholar]
17. L. Zhang and F. Zhang, “A new certificateless aggregate signature scheme,” Computer Communications, vol. 32, no. 6, pp. 1079–1085, 2009. [Google Scholar]
18. L. Deng, Y. Yang, Y. Chen and X. Wang, “Aggregate signature without pairing from certificateless cryptography,” Journal of Internet Technology, vol. 19, no. 5, pp. 1479–1486, 2018. [Google Scholar]
19. J. Li, X. Huang, Y. Mu, W. Susilo and Q. Wu, “Certificate-based signature: Security model and efficient construction,” in European Public Key Infrastructure Workshop, Berlin, Heidelberg: Springer, pp. 110–125, 2007. [Google Scholar]
20. J. Li, X. Huang, Y. Zhang and L. Xu, “An efficient short certificate-based signature scheme,” Journal of Systems & Software, vol. 85, no. 2, pp. 314–322, 2012. [Google Scholar]
21. J. Zhang, “On the security of a certificate-based signature scheme and its improvement with pairings,” in Int. Conf. on Information Security Practice and Experience, Berlin, Heidelberg: Springer, pp. 47–58, 2009. [Google Scholar]
22. H. Xiong, S. Wu, J. Geng, E. Ahene, S. Wu et al., “A pairing-free key-insulated certificate-based signature scheme with provable security,” KSII Transactions on Internet and Information Systems, vol. 9, no. 3, pp. 1246–1259, 2015. [Google Scholar]
23. X. Ma, J. Shao, C. Zuo and R. Meng, “Efficient certificate-based signature and its aggregation,” in Int. Conf. on Information Security Practice and Experience, Cham: Springer, pp. 391–408, 2017. [Google Scholar]
24. J. N. Chen, Q. S. Chen and F. M. Zou, “Certificate-based aggregate signature scheme without bilinear pairings,” Journal of Information Hiding and Multimedia Signal Processing, vol. 7, no. 6, pp. 1330–1336, 2016. [Google Scholar]
25. G. K. Verma, B. B. Singh, N. Kumar and V. Chamola, “CB-CAS: Certificate-based efficient signature scheme with compact aggregation for industrial internet of things environment,” IEEE Internet of Things Journal, vol. 7, no. 4, pp. 2563–2572, 2019. [Google Scholar]
26. G. K. Verma, B. B. Singh, N. Kumar and O. Kaiwartya, “PFCBAS: Pairing free and provable certificate-based aggregate signature scheme for the e-healthcare monitoring system,” IEEE Systems Journal, vol. 14, no. 2, pp. 1704–1715, 2019. [Google Scholar]
27. Y. Dodis, J. Katz, S. Xu and M. Yung, “Key-insulated public key cryptosystems,” in Int. Conf. on the Theory and Applications of Cryptographic Techniques, Berlin, Heidelberg: Springer, pp. 65–82, 2002. [Google Scholar]
28. G. Hanaoka, Y. Hanaoka and H. Imai, “Parallel key insulated public key encryption,” in Int. Workshop on Public Key Cryptography, Berlin, Heidelberg: Springer, pp. 105–122, 2006. [Google Scholar]
29. P. V. Reddy and P. V. S. S. N. Gopal, “Identity-based key-insulated aggregate signature scheme,” Journal of King Saud University-Computer and Information Sciences, vol. 29, no. 3, pp. 303–310, 2017. [Google Scholar]
30. Y. Lu, J. Li and J. Shen, “Weakness and improvement of a certificate-based key-insulated signature in the standard model,” The Computer Journal, vol. 60, no. 12, pp. 1729–1744, 2017. [Google Scholar]
31. H. Xiong, Y. Hou, X. Huang and S. Kumari, “Certificate-based parallel key-insulated aggregate signature against fully chosen-key attacks for industrial internet of things,” IEEE Internet of Thing Journal, Early Access, pp. 1–14, 2020. [Google Scholar]
32. J. Li, H. Du and Y. Zhang, “Certificate-based key-insulated signature in the standard model,” The Computer Journal, vol. 59, no. 7, pp. 1028–1039, 2016. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |