DOI:10.32604/cmc.2021.014305

| Computers, Materials & Continua DOI:10.32604/cmc.2021.014305 |  |
| Article |
A Novel Hybrid Clustering Based Transmission Protocol for Wireless Body Area Networks
1Research Scholar, Computer Science and Engineering, Uttarakhand Technical University (UTU), Dehradun, India
2Computer Science and Engineering, Maharaja Agrasen Institute of Technology, New Delhi, India
3School of Computer & Systems Sciences, Jawaharlal Nehru University (JNU), Delhi, India
4College of Engineering Roorkee, UTU, Dehradun, India
5Department of Information Technology, KIET Group of Institutions, Ghaziabad, India
*Corresponding Author: Neelam Sharma. Email: sharmaneelam2@gmail.com
Received: 12 September 2020; Accepted: 01 November 2020
Abstract: Wireless sensor networks are a collection of intelligent sensor devices that are connected to one another and have the capability to exchange information packets amongst themselves. In recent years, this field of research has become increasingly popular due to the host of useful applications it can potentially serve. A deep analysis of the concepts associated with this domain reveals that the two main problems that are to be tackled here are throughput enhancement and network security improvement. The present article takes on one of these two issues namely the throughput enhancement. For the purpose of improving network productivity, a hybrid clustering based packet propagation protocol has been proposed. The protocol makes use of not only clustering mechanisms of machine learning but also utilizes the traditional forwarding function approach to arrive at an optimum model. The result of the simulation is a novel transmission protocol which significantly enhances network productivity and increases throughput value.
Keywords: Forwarding function; wireless sensor networks; WSNs; WBANs; energy characteristics; clustering; hybrid mechanism; dissipated energy; network stability
Wireless sensor networks, in particular wireless body area networks have become an increasingly popular topic of research and inquiry in the past few years. This is both because of their capabilities and the implications of their application results. Wireless body area networks or WBANs for short may be defined as an assembly of smart sensor devices which gather meaningful information and are suitably linked to each other so as to communicate amongst themselves and thereby transmit the information collected.
This area of research has become quite popular in the recent years because of the host of applications of this technology. WBANs can be used in the healthcare industry for remote health monitoring, in the agriculture industry to boost crop production, and in the entertainment industry to enhance user experience. Thus, there is an increasing need to make these networks more resourceful and secure.
The two main needs of the hour in this sector of research therefor are the network transmission and packet security as well as the throughput enhancement. The present article focuses on one of these problems namely the throughput enhancement. The network throughput is a measure of the efficiency and capability of the network. Thus, enhanced throughput directly implies improved network capability and resourcefulness.
In order to enhance the network throughput, the article proposes a novel mechanism for transmission of packets within a wireless sensor network. The proposed algorithm makes use of a combination of the machine learning approach of clustering as well as a traditional forwarding function. With the new approach, the network was found to perform significantly better than its predecessors and the throughout value was also found to be greater as compared to previously proposed mechanisms.
The article is divided into ten sections in total. The current introduction chapter serves as the first section. The second section provides a brief overview of previously used transmission protocols. The third section introduces the previously proposed protocols that are relevant in context of the present work. The fourth section provides a detailed account of the proposed protocol. The fifth section compares the placements and usage of the network sensor nodes of the proposed model with those of its predecessors. In the sixth section, a description of the simulation environment and the parameters considered is provided. The seventh section highlights the performance superiority using graphical simulations. The eighth section concludes the research findings. The ninth section is dedicated to address the bridged gap by the medium of the present article and the tenth section is dedicated to the references.
Some of the notable packet transmission protocols proposed previously have been listed and explained in brief here.
Quwaider et al. [1] suggested a protocol that is equipped to deal with variations in the network. In their protocol, all the nodes are able of putting away data packets, and a store and forward mechanism is utilized to extend the likelihood of a specific data packet reaching the sink node. Following this, a self-organization protocol for body area networks was proposed by Wattyene et al. [2] to limit the transmission of data from the sensor nodes to the sink directly.
Nabi et al. [3] proposed a protocol based on the transmission power adaptation methodology. A store and forward plan was also incorporated along with the TPA method. Javaid et al. [4,5] proposed a mobility supporting, threshold-based, energy-efficient, multi-hop protocol termed M-ATTEMPT. This mechanism provides mobility of the nodes at the cost of throughput and the added expenditure of relay nodes.
Nadeem et al. [6] proposed the SIMPLE protocol wherein each node is aware of the neighboring node’s as well as the sink’s positions. With the purpose of saving energy, a multi-hop protocol is employed here. A cost function is calculated by the sink at the beginning of each transmission cycle to select a forwarder node.
Neelam Sharma et al. [7] improved upon the simple protocol by proposing a new cost function calculation methodology. In the protocol proposed by them, the transmission mechanism remains similar to that proposed by Nadeem et al., the cost function however is calculated on the basis of dissipated energy instead of the residual energy. This increases network throughput and stability.
Chuang et al. [8] proposed a transmission protocol that utilizes the concept of cluster head announcement delay and a new cluster head selection approach. The clustering approach utilizes a random declaration delay design which chooses the node with the shortest declaration delay as the cluster head of its region to decide the cluster topology. The clustering approach moreover includes a novel energy-classifying strategy which classifies all sensor nodes into several levels according to the genuine situation of the network to extend its scalability.
Chowdhury et al. [9] proposed a scheme named Energy Balanced Distributed Clustering Protocol (EBDCP) that ensures to transmit the sensed data to the base station inside the tour deadline with the help of a mobile sink. For this reason, a productive sojourn point assurance algorithm has moreover been utilized.
In this protocol, for each transmission rounds, a cost function is calculated for each of the nodes in the network. The node with the minimum value of this cost function is chosen as the forwarder node. The cost function in case of the SIMPLE protocol is calculated on the basis of the residual energy of each node and its distance from the sink node [10].
The E2 protocol as proposed by Neelam Sharma et al. [7] utilizes a method of packet propagation which uses the dissipated energy of the nodes in place of the residual energy. At the beginning of each transmission cycle, a forwarder is chosen from the available nodes on the bases of the forwarding function which considers the dissipated energy and the distance from the central node for each node. The node with the minimum value of this forwarding function is chosen as the forwarder for that transmission cycle and each of the nodes transmits its data to the forwarder which then sends it to the sink node [9].
5 Proposed Hybrid Clustering Based Protocol
The hybrid clustering based protocol, or the HC protocol is a packet transmission protocol that’s based on the principles of both K implies clustering and the dissipated energy based forwarding function as proposed by Neelam Sharma et al. [7]. The protocol eliminates the concept of a sink node and uses cluster heads obtained by the K means algorithm to transmit data packets directly to the base station.
5.1 Proposed Protocol Mechanism
At the beginning of each transmission cycle, all of the nodes in the network broadcast an information packet that constitutes integral data such as their energy levels, positions on the host etc. This packet is sent not only to all the other nodes in the network but also to the base station. The base station, because it possesses the relevant computing abilities, uses the data obtained to apply the K-means clustering algorithm on the network nodes to segment them into groups [10–13]. Once this is done, information about each group’s cluster head and cluster labels of each node are sent back to the sensor network.
Thus, each node now has a relevant cluster label and an associated cluster head. All the nodes in a particular group transmit their data packets to their corresponding cluster heads. These cluster heads then transmit the data packets directly to the base station. The process is then repeated again for the next transmission round. If at any point, the energy of a cluster’s head is found to be lower than a predefined threshold value, the traditional forwarding function approach is applied to that cluster. In other words, the forwarding function as proposed by Neelam Sharma et al. [7] in their protocol E2 is applied to all the nodes as classified under that cluster and a forwarder is chosen. Once this is done, all the nodes in that cluster transmit their data packets to this forwarder which then directly transmits this data to the base station. As can be inferred from the above explanation of the network’s runtime simulation, any concept of a sink node has been completely eliminated.
5.2 Transmission Model Employed
In the simulations that were run to test the effectiveness of the proposed HC protocol, the radio model for transmission of nodes was employed.
A first order radio model was considered and its corresponding energy equations were used to calculate the real time battery values for each of the nodes for clustering or forwarder selection for a given transmission round [14,15]. These equations can be summarized as follows in Eqs. (1)–(3):
These equations were integrated into the simulation algorithms to obtain the relevant results. In accordance with these, the energy consumed during transmission depends upon the transmission energy factor, the transmission channel loss factor, packet size, and the distance from the receiver. Similarly, the energy consumed during receiving is based on the receiving energy, the amplification factor before relay to base station, size of the packet, as well as the loss and distance to base station factors [16–18].
5.3 Scheduling of Data Packets
A time division multiple access scheduling protocol is used to manage the transmission of packets between the nodes, the cluster heads, as well as the base station. Each of the cluster heads, after segmentation, set up dedicated time slots for each of its fellow cluster members and accepts packets from them in accordance with this time slot’s schedule.
Similarly, when each cluster head is done collecting data from its cluster of nodes, the base station assigns a dedicated time slot to each cluster head and thus, the information from the cluster heads are transmitted to the base station. When they are not forwarding or receiving any data, or in case they do not have any data to transmit or receive, nodes in the sensor network switch to their idle states. This switch ensures that maximum energy saving takes place.
5.4 An Overview of the Clustering Algorithm Used
The proposed transmission protocol makes use of both machine learning concepts such as the K-means clustering algorithm as well as more traditional approaches like the forwarding function based on dissipated energy. The clustering algorithm used in the HC protocol is the K-means clustering algorithm. The K-means algorithm is one of the most widely used and uncomplicated clustering approaches employed. In this algorithm, the value of K, which designates the total number of required clusters has to be prespecified. Depending upon the value of K as well as the attributes associated with each data point, each object in the list is segmented and assigned a cluster label. This clustering algorithm is a type of partitioning algorithm that clusters data unsupervised based on the similarity of the data points, which in the present case are the nodes, to each other.
K-means tries to minimize the intra-cluster distances and maximize the inter cluster distances. The Euclidean distance between each data point is determined and used as this distance metric. The limitation of this algorithm is that it is highly susceptible to local convergence. To overcome this problem and obtain optimum results, the algorithm is run multiple times. For the present HC protocol, the K-means algorithm was run about 12 times with 3 as the value of K for each transmission round to obtain optimum results.
The sensor network simulations were run in python 3.6 in the Jupiter labs environment. At the beginning of each transmission cycle, the status of each node as broadcasted by the system were used to cluster them using the K means algorithm. As a consequence of this, the cluster heads were determined which then transmitted the data to the base station. In case the energy of the cluster head was found to be less than a predefined threshold value, the traditional forwarder approach was applied to that entire cluster to obtain the relay node that would transmit the data to the base station. Thus in this approach the entire concept of a sink node was eliminated. The algorithm of the simulation is given below and flow chart is illustrated in Fig. 1.
The algorithm of the proposed HC Protocol (ROUTING PHASE):
IN EACH ROUND:
a) From skikitlearn. Cluster import K-Means.
b) Create a K-means object.
c) Create a data frame of all the node characteristics i.e., RE, x & y coordinates, status etc.
d) Feed the above data frame into the K means using the fit function.
e) Use the object to obtain cluster labels and heads.
f) Check if the energy of any cluster head is less than threshold. If it is apply the E2 protocol forwarding approach as follows:
def calcffE2(node, sink):
distance = euclidean_distance(node, sink)
if node.E == 0.5:
ff = 1/(distance*node.E*node.E)
else:
de = 0.5 − node.E #dissipated energy; ff = 1/(distance*de*de)
return ff
g) The cluster nodes and heads transmit the data to their destination in accordance with the simulation energy equations as follows:
def updating_in_case_normal(self):
d = euclidean_distance(self, sinky)
self.E = self.E
− ((ETX)*(4000) + Emp*3.38*4000*(ma.pow(d, 3.38)))
def updating_in_case_forwarder(self):
d = euclidean_distance(self, sinky)
self.E = self.E((ETX + ERX + EDA)*(4000) + Emp*3.38*4000*(ma.pow(d, 3.38)))
h) Check if any node has become dead as follows and update the alive node list:
for node in new_list:
if node.E < = 0:
new_list.remove(node)
dead = dead + 1

Figure 1: The flow chart of the simulation algorithm
6 Nodes Location in the Proposed Protocol (HC Protocol)
A diagrammatic representation of node distribution in the host is presented for both the HC protocol as well as SIMPLE and E2 is shown in Fig. 2.

Figure 2: Node distribution in E2 and SIMPLE as well as HC protocol
The image to the extreme left illustrates the node distribution in the network in case of the SIMPLE and E2 protocols. In both of these, a forwarder node was chosen based on the results of a forwarding function. The node with the minimum value of this function was chosen as the forwarder for that transmission round. All the nodes in the network then transmitted their data packets to this forwarder which in turn sent this information to the sink. The sink then created a cumulative packet and sent it to the base station.
In the network simulations of both of these protocols, a total of nine nodes were deployed which formed the sensor network. Out of these, two nodes were the glucose and ECG nodes that directly communicated with the sink without the intervention of a forwarder, one node was the sink which combined all data packets and sent them to the forwarder, and the rest of the six nodes were normal sensor nodes out of which a novel forwarder was chosen for each transmission cycle.
In Fig. 2, the picture to the right represents the distribution of nodes in the body of the host in case of the proposed HC protocol. As can be seen from the image, there exist nine nodes in total all of which have the same identical task. For each transmission round, the K means clustering algorithm finds segmented groups and their corresponding cluster heads. These cluster heads collect data from their cluster member nodes and then relay the packet directly to the base station, thereby eliminating the need of a dedicated sink node.
In case at any point the energy of any of the cluster heads is found to be less than a predefined threshold value, the traditional forwarding function as proposed by the E2 protocol is applied to that cluster and a forwarder is chosen that sends the sensed data to the base station directly.
7 Simulation Environment and Parameters Considered
The term hardware specifications, here, is used to refer to the energy value and other factors associated with the sensor nodes that are used to create the network. All of the energy factors that have been used in the radio transmission model described in the preceding section, depend upon the hardware used and its energy specifications.
In the proposed model, the characteristics of two transceivers were considered for simulation purposes. These were the Nordic nRF 2410A which is a single chip, low power transceiver and the Chipcon CC2420.
Both of these devices have the same bandwidth which is about 2.4 GHz. The typical parameters associated with these and those utilized during network simulation are listed below in Tab. 1. There are three main parameters on which the proposed HC protocol is based. The first one is the throughput. The throughput of any wireless network is a measure of the efficiency of that network and gives a quantitative measure of the data flow volume. Here, the throughput parameter has been used to measure the overall performance of the protocol and is measured as a ratio of the packets transmitted to the number of the transmission cycles.

The second parameter is the dissipated energy. The traditional forwarding function that has been integrated into the protocol is based upon the network energy and distance from destination node. Thus, the node energy plays an important role in the proposed protocol. Just like the E2 protocol, the proposed HC protocol considers the dissipated node energy to make the forwarder selection for optimized results.
The third parameter is the K value to be considered in the K-Means clustering algorithm. This value determines the number of clusters that will be produced as a result of the application of the algorithm. The value of 3 is chosen for the current protocol. The network to which the proposed and previously proposed protocols were applied was created and simulated in python 3.6 in the Jupyter labs environment.
In the below Fig. 3, representation of the network nodes after application of clustering as well as the information flow has been provided. The orange colored rectangle is the base station which is the penultimate transceiver for the current HC protocol. In the simulation, nine nodes were considered in total. Out of these, one node was assigned to dedicatedly collect ECG readings from the host and another to dedicatedly collect glucose readings. Each of these nine nodes was subjected to clustering using the proposed algorithm.

Figure 3: Schematic representation of node topology in simulation
As a consequence of the application of the clustering algorithm, 3 clusters were produced during each transmission round along with the corresponding cluster heads. In the image above the nodes with different colors, namely, pink, blue, and green represent the nodes belonging to the three different clusters. The nodes with yellow outlines are the cluster heads for the given group. During the time of transmission, each of the nodes of a given cluster transmit their data packets to the cluster heads which at that point compile these and send them off to the base station. The plan of sending of these data packets is governed by the TDMA protocol.
The main parameter considered is the energy of the nodes. The SIMPLE protocol uses the concept of residual energy and distance from the sink to calculate the forwarding function for each node. The node with the least value of this function is chosen as the forwarder for that transmission cycle.
The E2 protocol uses the concept of dissipated energy and the distance from sink to calculate the forwarding function. The node with the least value of the forwarding function is chosen as the forwarder for that round and transmits the collected information to the sink.
The current protocol HC uses a hybrid approach instead. For each round, the K means algorithm is used to find the segmented groups and cluster heads. The cluster heads are used as forwarders for associated group and transmit directly to the base station. In case of lower than threshold energy, the forwarder as employed in the E2 protocol is used to choose the forwarder of associated cluster.
The following Tab. 2 tabulates the forwarding functions used by both the proposed protocol as well as those considered for comparison namely the E2 and SIMPLE protocol.
8 Graphical Analysis of Simulation Results
In this section, the results of the sensor network simulation have been presented in a graphical manner to demonstrate the improved network output results in case of the novel proposed protocols. Comparison and analysis are performed on the basis of multiple parameters such as the number of packets reaching the destination, the number of dead nodes, network energy, number of rounds etc. The results of the comparative analysis are detailed in the following sections.

8.1 Network Residual Energy vs. the Number of Rounds
A graph of the network residual energy vs. the number of rounds has been plotted for all three of the protocols being considered in Fig. 4. Here, the residual network energy refers to the sum total of the residual energies of all the nodes in the network during a particular round. The number of rounds, here, refers to the number of the transmission cycles for packet transmission considered.
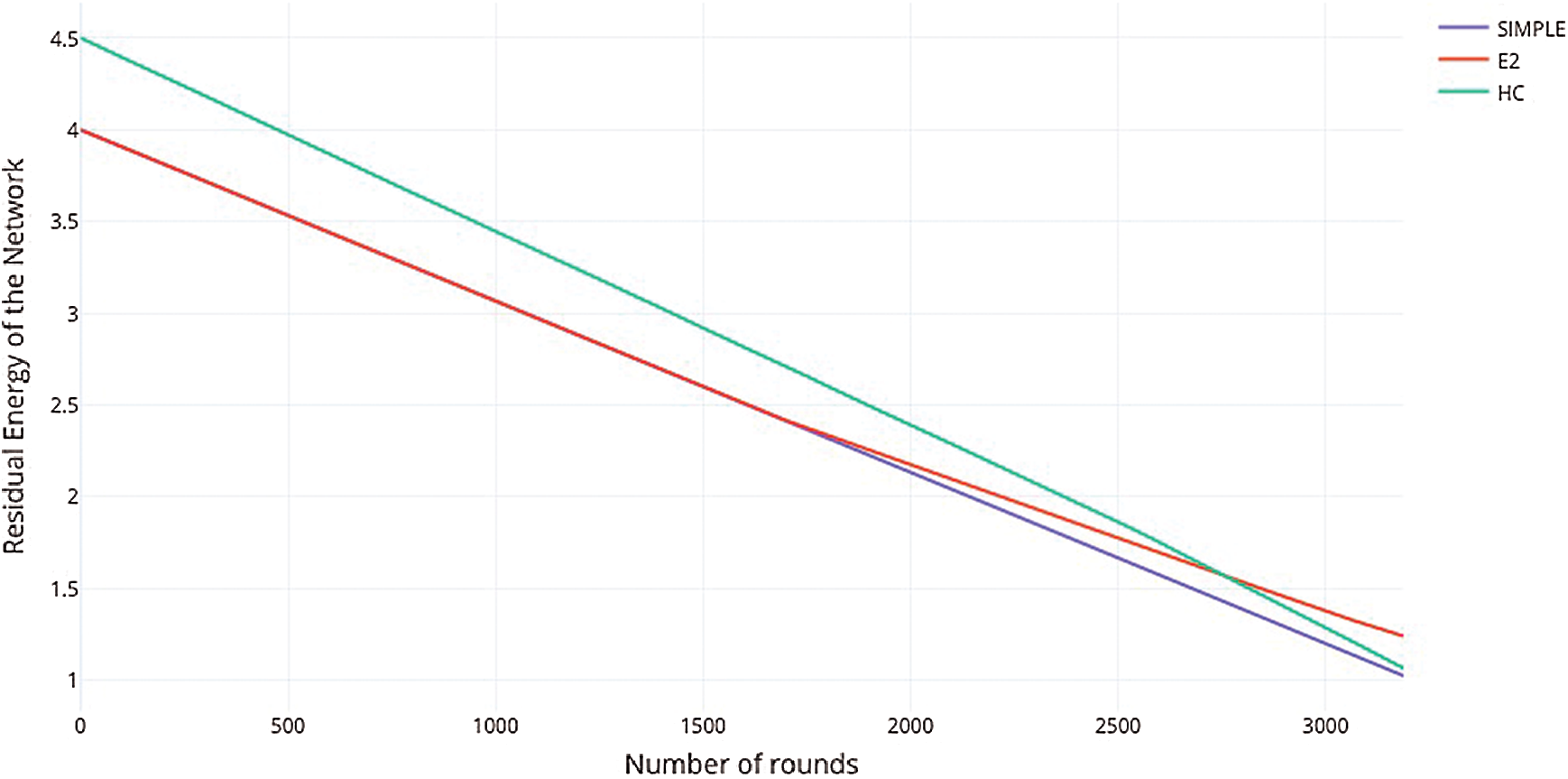
Figure 4: Residual energy vs. number of rounds
As can be seen from the Fig. 4 above, the residual energy of the network for the proposed HC protocol is greater than those of the E2 and the SIMPLE protocol at the beginning of the transmission cycles. This is because even though, the same number of nodes were employed in both the simulations, the number of nodes working dedicatedly as a part of sensor network is greater in case of the HC protocol due to the elimination of the concept of sink.
Furthermore, up until somewhere around 2750 rounds, the residual energy of the network for the HC protocol is greater than both the previously proposed ones indicating smoother and more stabilized energy consumption characteristics. After the 2750 round mark, the residual energy of the network for the HC protocol reduces more rapidly as compared to the E2 protocol. Its performance in this regard, however, remains better than the SIMPLE protocol during the entire course of the simulation run.
8.2 Number of Dead Nodes vs. the Number of Rounds
A graph of the number of dead nodes in the network during simulation run vs. the total number of rounds in the simulation has been shown in Fig. 5. Here, the number of dead nodes refers to all those nodes in the network who have run out of energy and are no longer sensing or transmitting any data. The number of rounds, as usual, is the total number of transmission cycles in the simulation.
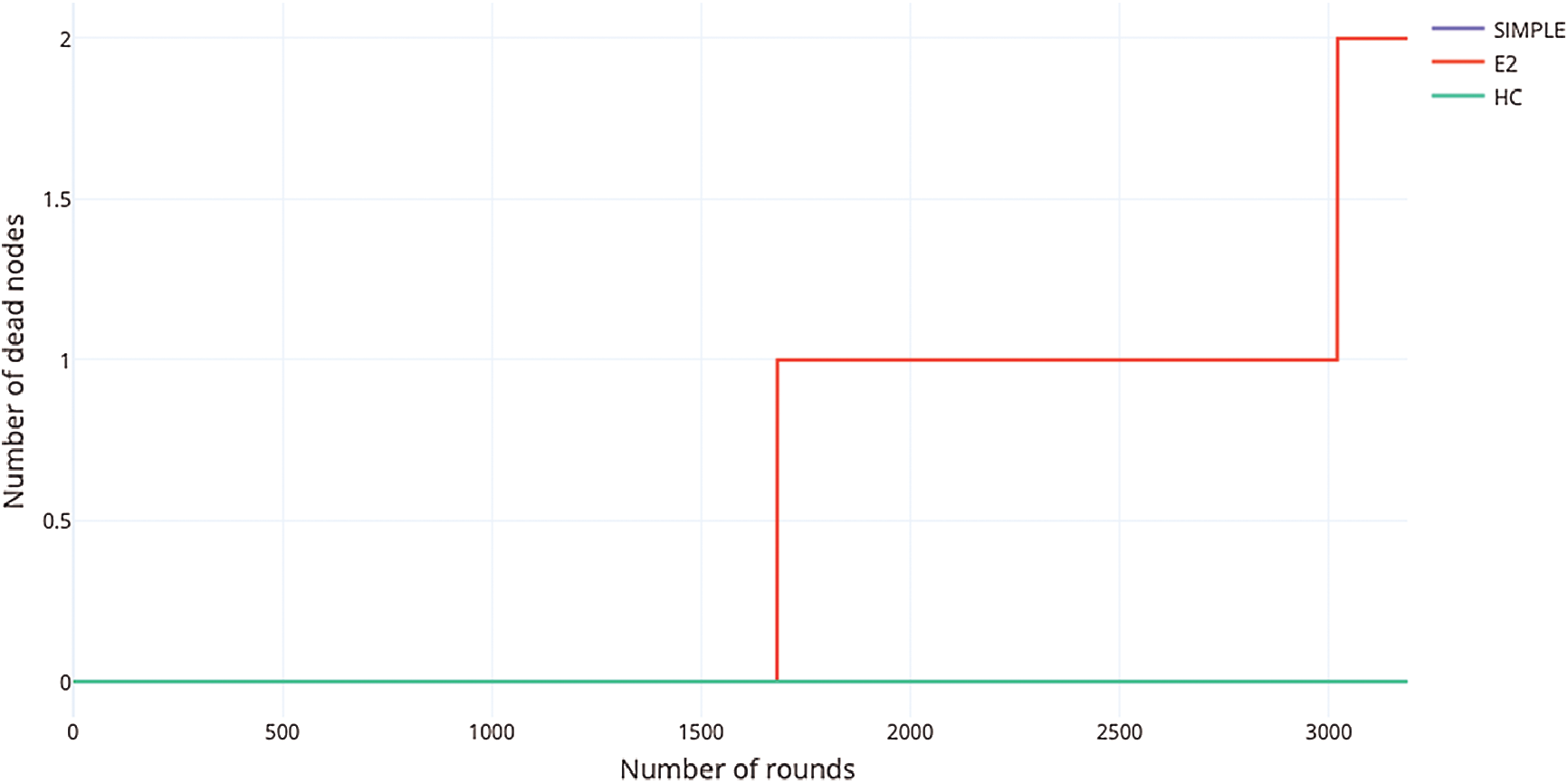
Figure 5: Number of dead vs. the number of rounds
From the above plot it can be seen that for the course of the simulation run, the number of dead nodes in case of the HC protocol remained zero up until the 3190th round mark. This is an indicator of stable energy consumption characteristics. Similarly, in the case of the SIMPLE protocol, the number of dead nodes till about 3190 rounds remains zero. In contrast to this in case of the E2 protocol, the number of dead nodes increases at around the 1700th round mark and then increases to become two at the 3000th round mark.
8.3 Packets to Destination vs. Number of Rounds
A plot of the packets to destination versus the total number of rounds has been shown in Fig. 6. Here, the packets to destination is the total number of information packets that reached the penultimate receiver without attenuation or distortion. This receiver is the sink node in case of the SIMPLE and E2 protocol and the base station in case of the HC proposed protocol. The number of rounds has its usual meaning.
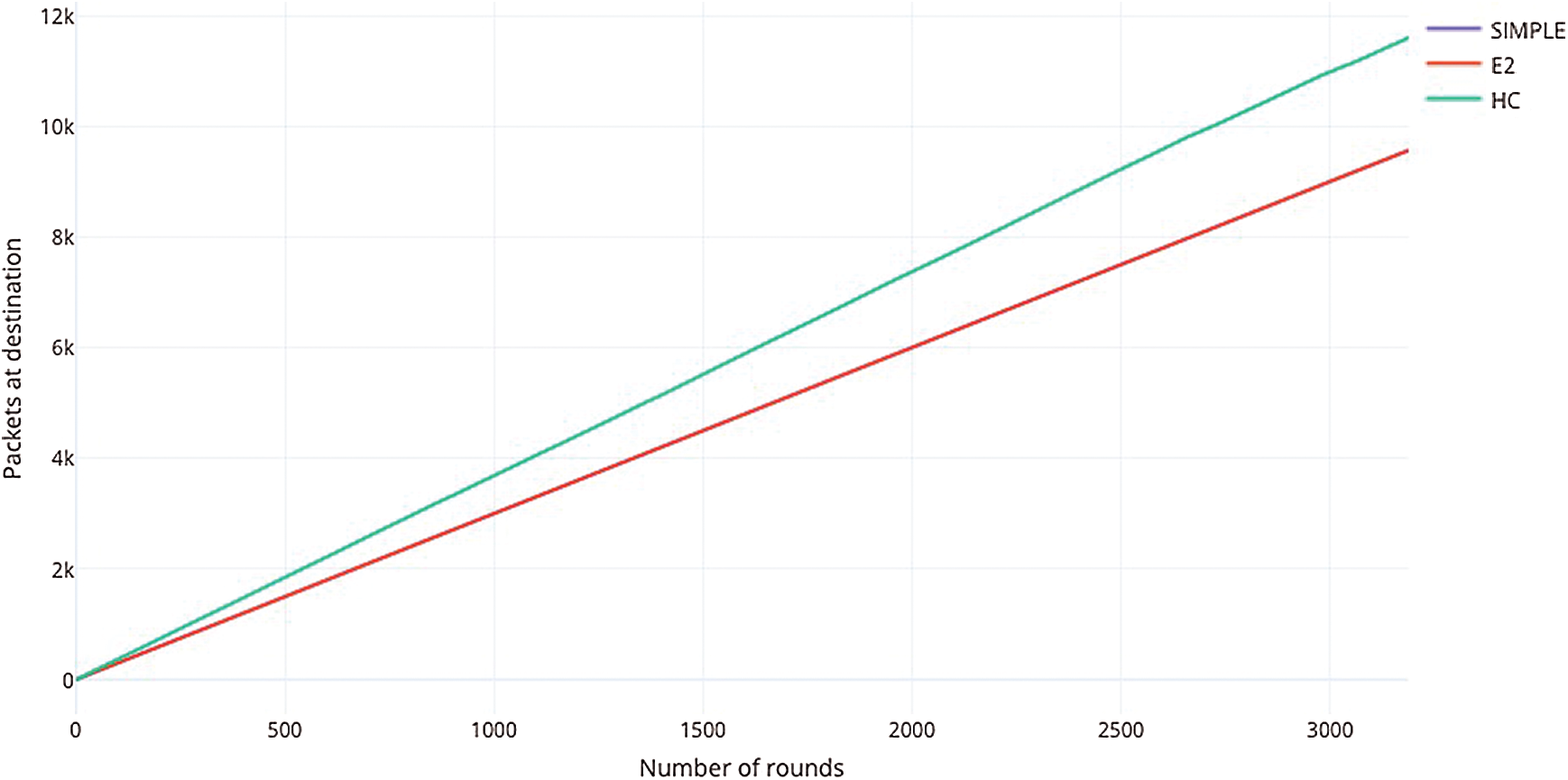
Figure 6: Packets at destination vs. the number of rounds
As can be seen from the graph, the characteristics of both E2 and SIMPLE protocol are almost identical and thus their characteristic lines overlap in the plot. On the contrary, the performance of the proposed HC protocol is better at every data point form the beginning till the end of the simulation indicating better transmission efficiency and a greater overall information volume that is being transmitted.
8.4 Network Throughput and Comparison
Network throughput in case of wireless networks may be defined as the rate of flow of information packets across different nodes in the network. It serves as an indicator of the total volume of the meaningful information reaching the destination transceiver.
In the present case, we calculate the throughput for both the previously proposed as well as the current protocol as a measure of the total number of packets at the destination in proportion to the number of transmission cycles. The plot of the same for all three of the considered protocols is shown in Fig. 7.
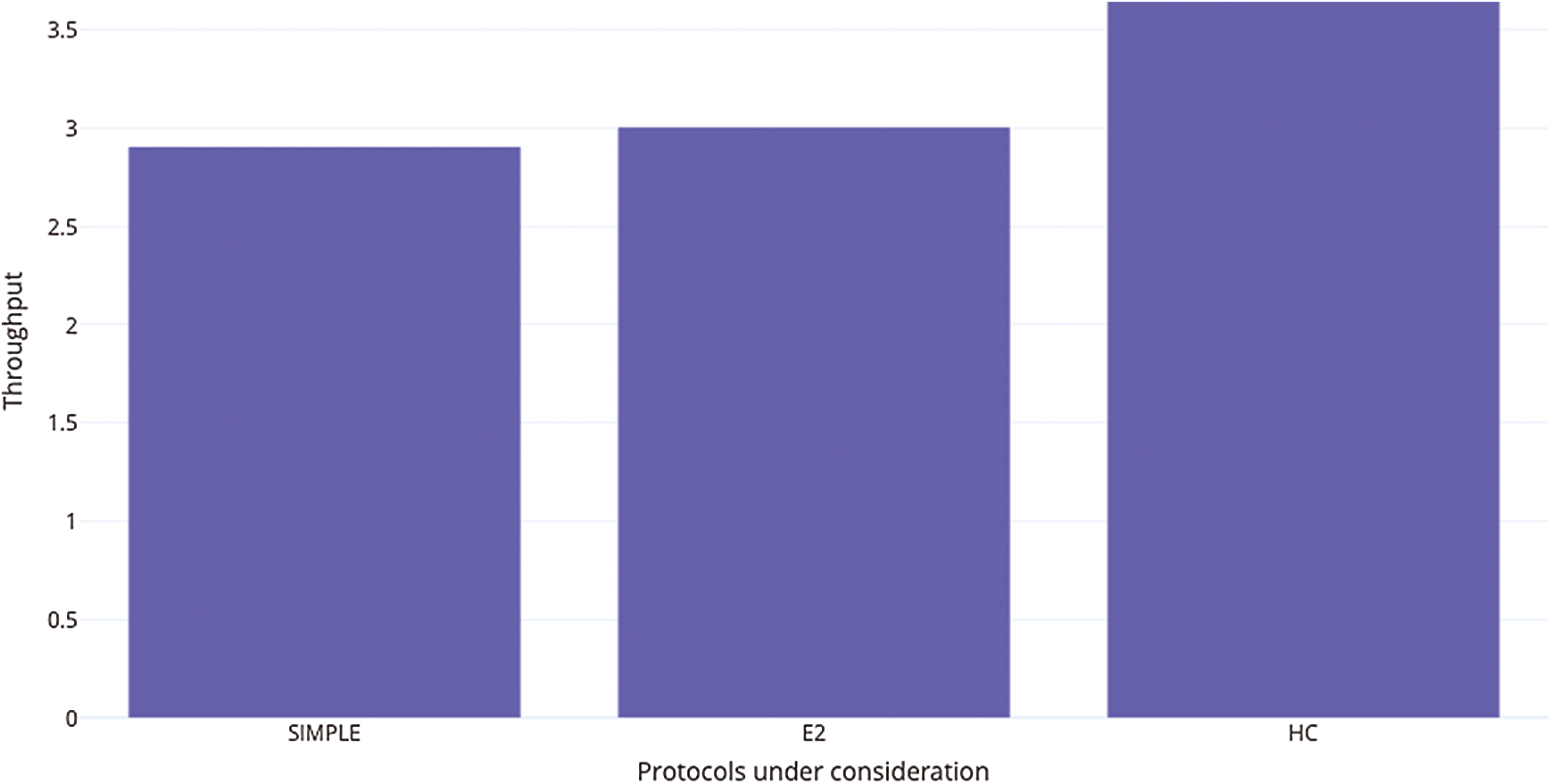
Figure 7: A plot of throughputs for compared protocols
As is clear from the above Fig. 7, the throughput is better for the HC protocol as compared to the two previously proposed protocols. The performance of the proposed E2 protocol is found to be approximately 25.5% better than the SIMPLE protocol and about 23.3% better than the E2 protocol.
On the basis of the discussions and findings illustrated in the preceding sections, the following conclusions can be drawn:
• The HC protocol proposes a novel packet transmission mechanism that makes use of both clustering machine learning algorithms as well as traditional forwarding function approaches.
• The performance of the HC protocol is found to be enhanced as compared to its predecessors by factors of 23–25% on average.
• The improved performance is due to better network resource utilization leading to increased packet transmission efficiency.
Due to the host of applications it offers, WSN as a field of technology has become increasingly popular in the recent past. As stated in Section 1, one of the main problems concerning this technology is the enhancement of the energy characteristic.
Most of the protocols that try to solve this issue propose cost functions or forwarding functions that utilize the energy characteristics of the network nodes and their distances from the sink. A heterogeneous network architecture is used therein where one of the network nodes functions explicitly as the sink node and does not sense and transmit any useful information.
The proposed model tries to bridge this inefficiency gap by introducing a clustering-based transmission protocol. In this mechanism, each of the network nodes collects useful information. At each transmission cycle, the clustering algorithm is applied, and cluster heads are chosen, which then directly transmit to the base station.
The novel approach used enhances the stability of the network. It also tries to prolong the network lifetime by introducing the traditional forwarding function based on a previously proposed E2 protocol so as to minimize the energy consumption in case a node’s energy become less than a pre-fixed threshold value.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. M. Quwaider and S. Biswas, “On-body packet routing algorithms for body sensor networks,” in First Int. Conf. on Networks and Communications, Chennai, India, pp. 171–177, 2009. [Google Scholar]
2. T. Watteyne, I. Augé-Blum, M. Dohler and D. Barthel “Anybody: A self-organization protocol for body area networks,” in ICST 2nd Int. Conf. on Body Area Networks, Florence, Italy, Article No. 6, 2007. [Google Scholar]
3. M. Nabi, T. Basten, M. Geilen, M. Blagojevic and T. Hendriks, “A robust protocol stack for multi-hop wireless body area networks with transmit power adaptation,” in Fifth Int. Conf. on Body Area Networks, Corfu Island, Greece, pp. 77–83, 2010. [Google Scholar]
4. N. Javaid, M. Yaqoob, M. Khan, M. Y. Khan, M. A. Javaid et al., “Analyzing delay in wireless multi-hop heterogeneous body area networks,” Research Journal of Applied Sciences, Engineering and Technology, vol. 7, no. 1, pp. 123–136, 2013. [Google Scholar]
5. N. Javaid, I. Israr, M. A. Khan, A. Javaid, S. H. Bouk et al., “Analyzing medium access techniques in wireless body area networks,” Research Journal of Applied Sciences, Engineering and Technology, vol. 7, no. 3, pp. 603–613, 2014. [Google Scholar]
6. Q. Nadeem, N. Javaid, S. N. Mohammad, M. Y. Khan, S. Sarfraz et al., “SIMPLE: Stable increased-throughput multi-hop protocol for link efficiency in broadband and wireless computing,” in Eighth Int. Conf. on Broadband and Wireless Computing, Communication and Applications, Compiegne, France, pp. 221–226, 2013. [Google Scholar]
7. N. Sharma, K. Singh and B. M. Singh, “An enhanced-simple protocol for wireless body area networks,” Journal of Engineering Science and Technology, vol. 13, no. 1, pp. 196–210, 2018. [Google Scholar]
8. P. J. Chuang, S. H.Yang and C. S. Lin, Energy-efficient clustering in wireless sensor networks in Algorithms and Architectures for Parallel Processing, Lecture Notes in Computer Science, Springer, Heidelberg, 2009. [Google Scholar]
9. S. Chowdhury and C. Giri, “Energy and network balanced distributed clustering in wireless sensor network,” Wireless Personal Communication, vol. 10, no. 5, pp. 1083–1098, 2019. [Google Scholar]
10. M. M. Alam and E. B. Hamida, “Surveying wearable human assistive technology for life and safety critical applications: Standards, challenges and opportunities,” Sensors, vol. 14, no. 5, pp. 9153–9209, 2014. [Google Scholar]
11. S. Adibi, Mobile Health: A Technology Road Map. 5, Berlin, Germany: Springer, pp. 95–107, 2015. [Google Scholar]
12. S. Yu, W. Zhou, S. Guo and M. Guo, “A feasible IP traceback framework through dynamic deterministic packet marking,” IEEE Trans. Computer, vol. 65, no. 5, pp. 1418–1427, 2015. [Google Scholar]
13. T. S. Le, “Mohhybrid: Multi-channel mac protocol for wbans with inter-wban interference mitigation,” Sensors, vol. 18, no. 5, pp. 1373–1384, 2018. [Google Scholar]
14. Y. Li, J. Liu, B. Cao and C. Wang, “Joint optimization of radio and virtual machine resources with uncertain user demands in mobile cloud computing,” IEEE Trans. Multimedia, vol. 20, no. 9, pp. 2427–2438, 2018. [Google Scholar]
15. N. Sharma and N. Pathak, “Elemental modularity design in smart phones,” International Journal of Engineering and Advanced Technology, vol. 9, no. 1, pp. 7001–7007, 2019. [Google Scholar]
16. Y. Li, S. Xia, M. Zheng, B. Cao and Q. Liu, “Lyapunov optimization based trade-off policy for mobile cloud offloading in heterogeneous wireless networks,” IEEE Trans on Cloud Computing, vol. 20, no. 9, pp. 2440–2454, 2019. [Google Scholar]
17. M. Ghamari, B. Janko, R. S. Sherratt, W. Harwin, R. Piechockic et al., “A survey on wireless body area networks for e-healthcare systems in residential environments,” Sensors, vol. 16, no. 6, pp. 831–846, 2016. [Google Scholar]
18. S. A. Salehi, A. Razzaque, I. Tomeo-Reyes and N. Hussain, “EEE 802.15.6 standard in wireless body area networks from a healthcare point of view,” in 22nd Asia-Pacific Conf. on Communications, Yogyakarta, pp. 523–528, 2016. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |