DOI:10.32604/cmc.2021.017968

| Computers, Materials & Continua DOI:10.32604/cmc.2021.017968 |  |
| Article |
Probabilistic and Hierarchical Quantum Information Splitting Based on the Non-Maximally Entangled Cluster State
1School of Information Science and Technology, North China University of Technology, Beijing, 100144, China
2Information Security Center, State Key Laboratory of Networking and Switching Technology, Beijing University of Posts and Telecommunications, Beijing, 100876, China
3Muroran Institution of Technology, Muroran, 050-8585, Japan
4State Key Laboratory of Public Big Data, College of Computer Science and Technology, Guizhou University, Guiyang, 550025, China
*Corresponding Author: Yu-Ling Chen. Email: Ylchen3@gzu.edu.cn
Received: 19 February 2021; Accepted: 31 March 2021
Abstract: With the emergence of classical communication security problems, quantum communication has been studied more extensively. In this paper, a novel probabilistic hierarchical quantum information splitting protocol is designed by using a non-maximally entangled four-qubit cluster state. Firstly, the sender Alice splits and teleports an arbitrary one-qubit secret state invisibly to three remote agents Bob, Charlie, and David. One agent David is in high grade, the other two agents Bob and Charlie are in low grade. Secondly, the receiver in high grade needs the assistance of one agent in low grade, while the receiver in low grade needs the aid of all agents. While introducing an ancillary qubit, the receiver’s state can be inferred from the POVM measurement result of the ancillary qubit. Finally, with the help of other agents, the receiver can recover the secret state probabilistically by performing certain unitary operation on his own qubit. In addition, the security of the protocol under eavesdropping attacks is analyzed. In this proposed protocol, the agents need only single-qubit measurements to achieve probabilistic hierarchical quantum information splitting, which has appealing advantages in actual experiments. Such a probabilistic hierarchical quantum information splitting protocol hierarchical is expected to be more practical in multipartite quantum cryptography.
Keywords: Cluster state; hierarchical quantum information splitting; probabilistic; non-maximally entangled states
Quantum information splitting, one of the core contents of quantum information science, means that secret information is split in some way and each sub-secret is managed by different agents. Only legal agents can work together to recover secret information. The concept of quantum information splitting and quantum state sharing [1,2] was first proposed by Hillery, Buzek & Berthiaume, who used the three-particle GHZ state and four-particle GHZ state to implement the information splitting scheme. Later, for the first time Cleve, Gottesman & Lo proposed (k, n) threshold quantum secret sharing scheme to distribute information. There are n agents in Gottesman’s scheme, and at least k agents are needed to recover the secret state. Quantum information splitting not only achieves absolute security in quantum communication, but also plays an extremely important role in protecting quantum information in the related region [3–8].
Quantum information splitting is possible if using a non-maximally entangled quantum source. In this condition, the success rate is probabilistic. Hence, this kind of protocol is referred to as probabilistic quantum information splitting protocol (PQIS). In the references [9–12], there have been some PQIS schemes with non-maximally entangled states. Besides, Gottesman pointed out a more general QIS protocol [13] in 2000, known as hierarchical quantum information splitting protocol (HQIS), which includes a hierarchy among agents in QIS protocol. That is to say, there is a hierarchy of the authorities for different agents. It has been shown that shares of the secret should be combined to recover the original secret state. In the references [14–16], Wang et al. had taken use of the
Researchers have focused on the diversity of feasible entangled states, which could realize probabilistic HQIS protocol, such as GHZ states [17], W states [18–19], six-qubit states [20], and so on. However, those states are maximally entangled states that are widely studied, while non-maximally entangled states that have relatively little research are more suitable and practical to achieve the protocol. In 2001, Raussendorf et al. [21] had proven a great use of a non-maximally four-qubit cluster state
In this work, a novel probabilistic hierarchical quantum information splitting protocol (probabilistic HQIS) is designed to teleport an arbitrary one-qubit secret state
In the protocol, something needs to be noticed. First, the shared quantum source and secret state are both uncertain and probabilistic. So, the receiver can only recover the secret state probabilistically under the cooperation of other agents. Apart from sender Alice’s Bell measurement, the other agents Bob, Charlie and David only need to perform single-qubit measurement on his own qubit while one of them could recover the secret state. Second, for the sake of the secret state’s recovery, the receiver often needs to entangle one or more auxiliary qubits with the receiver’s qubits in the probabilistic schemes. In the protocol, after introducing one auxiliary qubit m, the receiver can infer the state of his own qubit through the measurement results of the auxiliary qubit m. As a result, the receiver could recover the secret state by performing appropriate unitary operations on his own particle. Finally, it is important to note that the states of qubit m are not orthogonal. Based on non-distinguishability of non-orthogonal states, if the two quantum states are nonorthogonal, they cannot be completely precisely distinguished. However, there exists a more general type of measurement than the projective measurements, which is known as positive operator-valued measure (POVM). POVM provides a useful way to distinguish between nonorthogonal states. Hence, it’s feasible and essential to introduce POVM to measure qubit m.
2 Probabilistic and Hierarchical Quantum Information Splitting via a Non-Maximally Entangled Four-Qubit Cluster State
We assume the particle 1, 2, 3 and 4 are entangled via a four-qubit cluster state owned by Alice, Bob, Charlie and David separately. Without loss of generality, if the high grade’s agent David wants to recover the original secret state, then he needs the aid of one agent in low grade. If Bob or Charlie informs David the measurement result of his own qubit through the classical channel, David would infer the state of his qubit by POVM and recover the secret state through appropriate unitary operations. However, when the low grade’s agent, let’s say Bob, he should obtain the cooperation of all other agents to recover the secret. Only if both Charlie and David informs their measurement results to Bob, can Bob recover the secret state through unitary operations on his own qubit.
Assume that the sender Alice wants to teleport an arbitrary one-qubit secret state
where the coefficients
where the coefficients a and b are both arbitrary complex numbers satisfying
As shown in Fig. 1, Alice owns the secret qubit x and particle 1. Before teleporting the secret state, Alice splits the secret information into three pieces and distributes each piece to different agents so that any agent cannot recover the secret state alone.
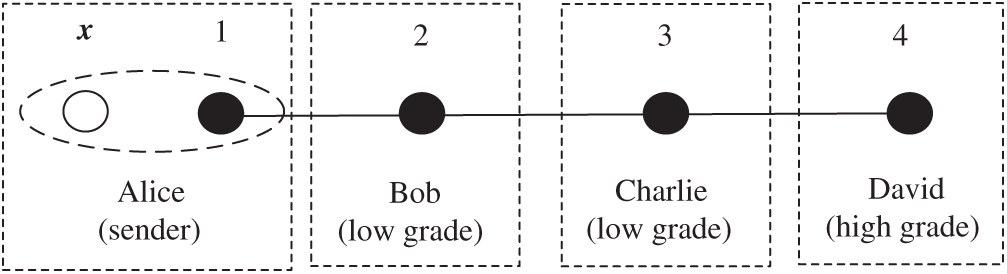
Figure 1: Four agents and their own particles, authorities
Then the whole system can be expressed as
Now, Alice needs to perform a joint measurement on her particles x and 1 by using
After Alice informs her measurement result, the states of the other three would collapse into the following four possible outcomes:
If the measurement result of Alice is
It’s important to note that only the authorized agent can recover the secret state
2.1 High Grade’s Agent Recovers the Secret State
In the protocol, there is only one agent David in high grade. Suppose David is the receiver, we rewrite
Next, Bob or Charlie needs to perform Z-basis measurement on their particle. No matter what Alice’s measurement result is, the measurement results of Bob and Charlie are always correlated. So only one agent is needed to perform single-qubit measurement. Hence, David can recover the secret state by certain unitary operation with the help of Bob or Charlie.
Suppose Alice and Bob’s measurement results are
At last, David performs a unitary operation
Table 1: David’s unitary operations needed according to Alice’s and Bob’s measurement results
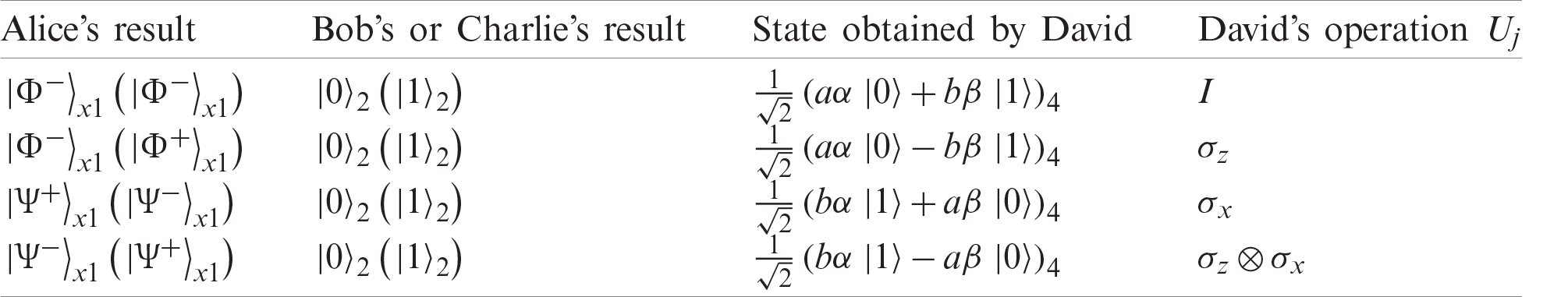
However, the state obtained by David is slightly different from the original secret state
Then David needs to perform a controlled-NOT operation
where
Hence, they cannot be differentiated deterministically by usual projection measurement. To distinguish the two states of particle m with the certain success probability, David needs to perform an POVM on the auxiliary particle m. POVM provides the ability to distinguish non-orthogonal states. Just as its name implies, POVM consists of a set of positive operators denoted by
where
Note that
for all
The probabilities of obtaining the value of
Similarly,
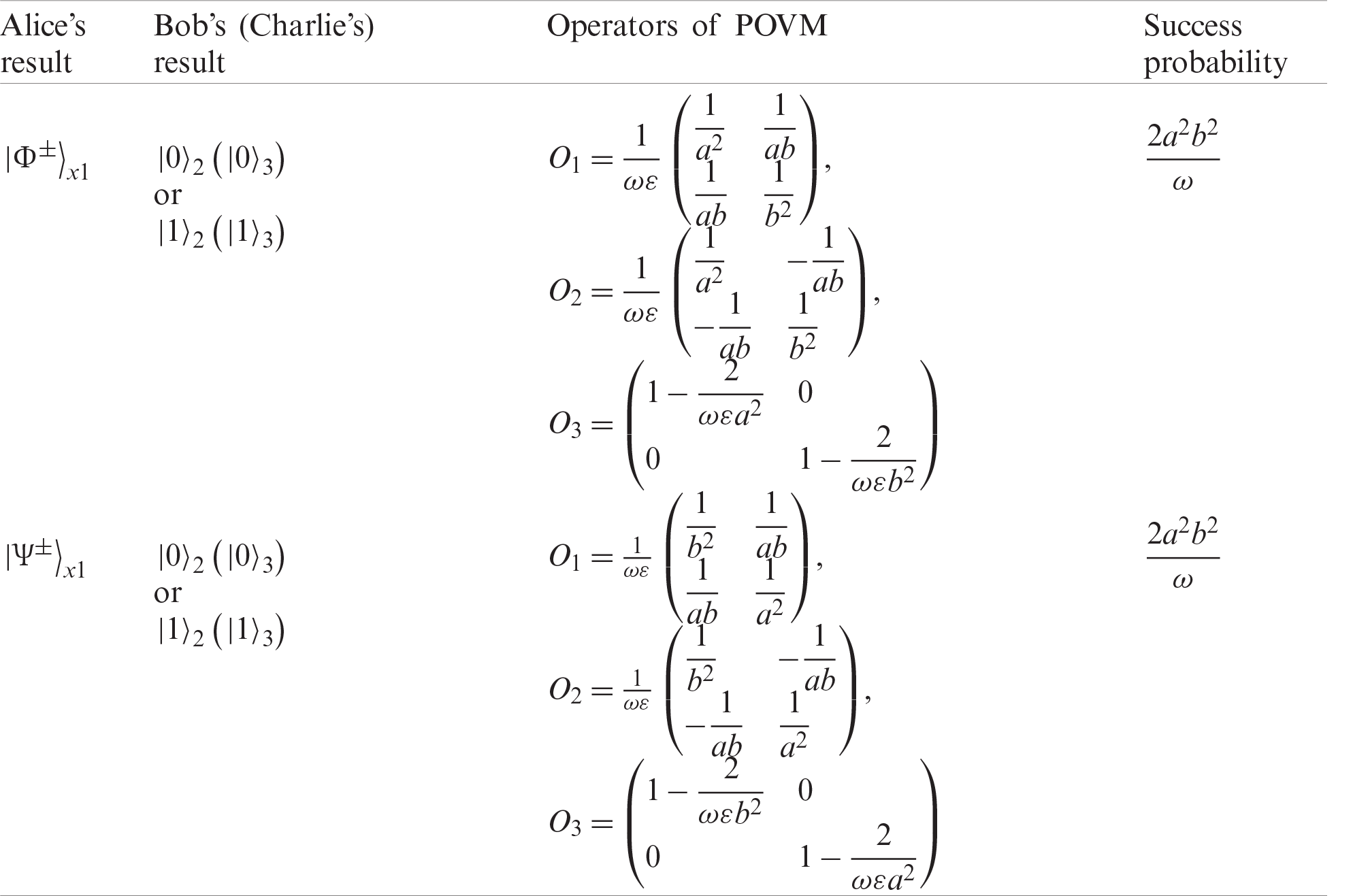
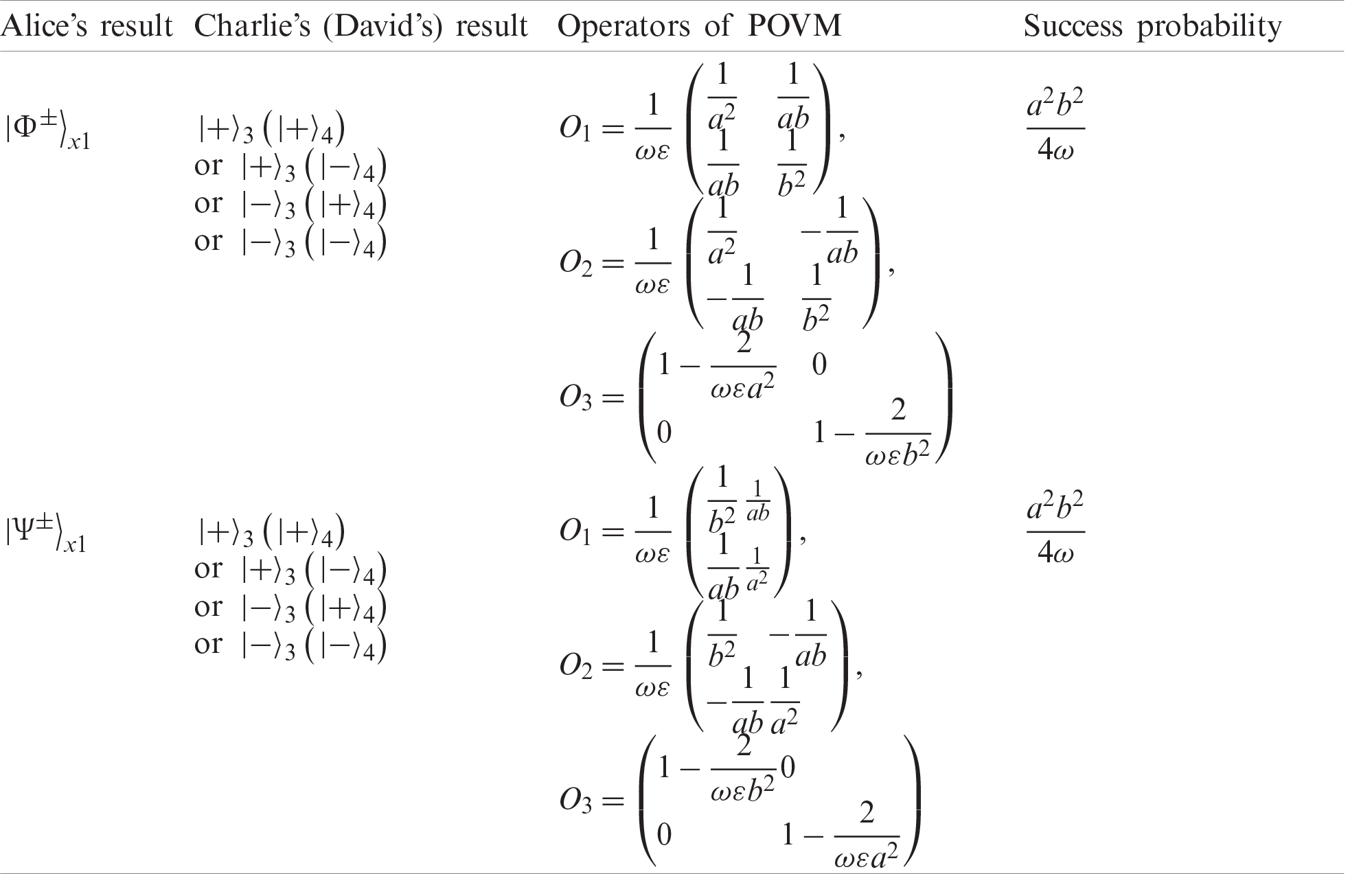
As shown above, David can obtain the state of qubit m with the probability
Once the state of particle m is measured, the state of particle 4 is also determined. Consequently, David can get the secret state through appropriate local unitary operations on his particle 4. From Eq. (17), it is obvious that the state of David’s particle 4 is
Up to now, we only consider the success probability when Alice and Bob’s measurement results are
Table 2: The success probability of the corresponding measurement results via POVM
2.2 Low Grade’s Agent Recovers the Secret State
Now, we consider the agent in low grade (Bob or Charlie) to recover the secret state. In this case, the agent in low grade needs the cooperation of all agents. Since Bob and Charlie have the same authority, they have the same recovery process. What follows is the process of Bob’s recovering the secret state
To help Bob recover the original secret state, Charlie and David need to measure their own particle in the X-basis. Then Bob can recover the secret state by certain unitary operation
Table 3: Bob’s unitary operations needed according to others’ measurement results
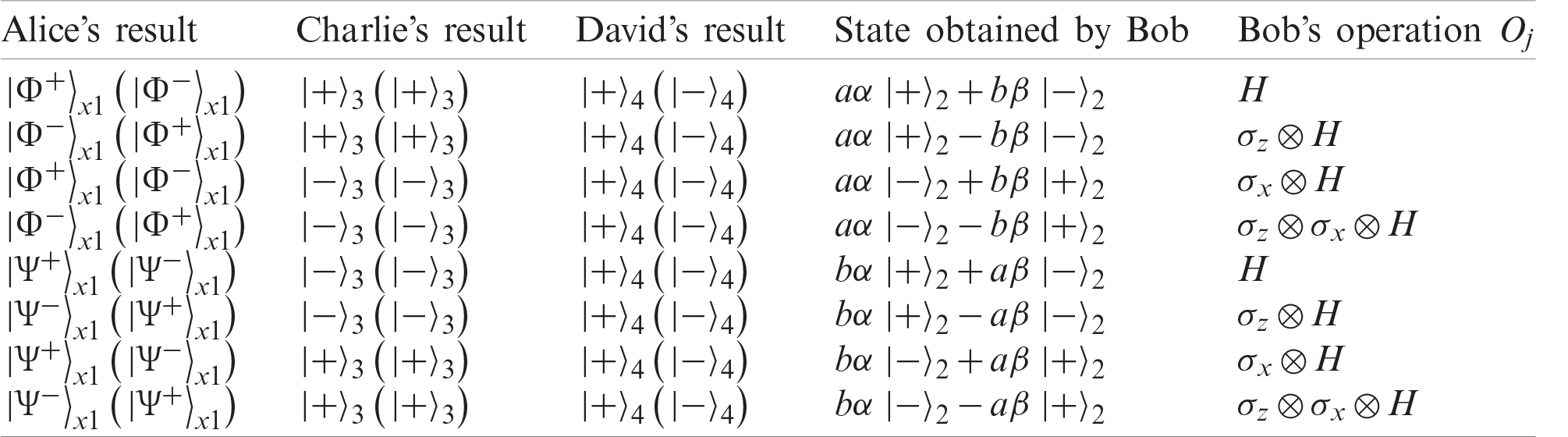
As shown in Tab. 3, after performing operations on Bob’s particle 2, the states of the particle 2 can be
Just as proposed in case 1, Bob needs to introduce an auxiliary qubit m in state
Then, Bob needs to perform a CNOT operation
where
Because the permutation of Bob’s particle 2 and Charlie’s particle 3 cannot change the quantum source, Bob and Charlie are in
Table 4: The success probability of the corresponding measurement results via POVM
Assume there is an attacker named Eve, he attempts to steal the secret information from the four legitimate agents Alice, Bob, Charlie and David. So, there are two ways of eavesdropping: intercept-measure-resend attack and entanglement attack.
For the former, Eve would intercept and measure the qubits sent by Alice in a random basis. Then Eve resends fake qubits to the other legitimate agents to disturb the secret’s recovery. But Eve would introduce abnormal error rates of the process inevitably. Hence, the intercept-measure-resend attack can be detected, and the teleportation of the secret state should be aborted. If the quantum channel is noiseless, then the error rate is equal to 0. In this scenario, the state of Eve’s system and the original system is a simply separable state, or product state, which means there is neither quantum nor classical correlation between these two systems. Therefore, Eve cannot gain any information from the original quantum state.
For the latter, during the distribution of particle 2, 3, 4, Eve entangles an ancillary qubit e with the quantum source
In summary, there are some merits in the paper. First of all, the shared quantum source, a non-maximally entangled four-qubit cluster state, is robust against quantum decoherence. It’s obvious that the generation and preservation of four-qubit non-maximally entangled states is easier than maximally six-qubit states, which has an attractive advantage in the experimental realization. The symmetry of cluster states helps the expansion of HQIS protocol. Then the secret state is arbitrary, which means the strong applicability and generality of the proposed protocol. What’s more, each agent has different grades so that there exists a hierarchy in the protocol. The receiver cannot recover the secret state successfully only if the cooperation of the other agents. Together with the non-maximally quantum source, the receiver could recover the secret state in a certain success probability. In other words, non-maximally quantum source and hierarchy of the protocol help expand the research scope of usual QIS protocols. In addition, only by single-qubit measurements can the receiver recover the secret state, which brings convenience to experimental realization.
Funding Statement: This work is supported by the NSFC (Grant Nos. 92046001, 61571024, 61671087, 61962009, 61971021), the Open Foundation of Guizhou Provincial Key Laboratory of Public Big Data (Grant Nos. 2018BDKFJJ018, 2019BDKFJJ010, 2019BDKFJJ014), the Open Research Project of the State Key Laboratory of Media Convergence and Communication, Communication University of China, China (Grant No. SKLMCC2020KF006), the High-quality and Cutting-edge Disciplines Construction Project for Universities in Beijing (Internet Information, Communication University of China), and the Fundamental Research Funds for the Central Universities (Grant No. 2019XD-A02), the Scientific Research Foundation of North China University of Technology, the Fundamental Research Funds for the Beijing Municipal Education Commission and JSPS KAKENHI Grant Number JP20F20080.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. M. Hillery, V. Bužek and A. Berthiaume, “Quantum secret sharing,” Physical Review A, vol. 59, no. 3, pp. 1829–1834, 1999. [Google Scholar]
2. R. Cleve, D. Gottesman and H. K. Lo, “How to share a quantum secret,” Physical Review Letters, vol. 83, no. 3, pp. 648–651, 1999. [Google Scholar]
3. G. Xu, K. Xiao, Z. Li, X. Niu and M. Ryan, “Controlled secure direct communication protocol via the three-qubit partially entangled set of states,” Computers, Materials & Continua, vol. 58, no. 3, pp. 809–827, 2019. [Google Scholar]
4. Z. Dou, G. Xu, X. Chen and K. Yuan, “Rational non-hierarchical quantum state sharing protocol,” Computers, Materials & Continua, vol. 58, no. 2, pp. 335–347, 2019. [Google Scholar]
5. Z. G. Qu, S. Y. Chen and X. J. Wang, “A secure controlled quantum image steganography algorithm,” Quantum Information Processing, vol. 19, no. 380, pp. 1–25, 2020. [Google Scholar]
6. Z. Qu, S. Wu, W. Liu and X. Wang, “Analysis and improvement of steganography protocol based on bell states in noise environment,” Computers, Materials & Continua, vol. 59, no. 2, pp. 607–624, 2019. [Google Scholar]
7. V. S. Naresh and S. Reddi, “Multiparty quantum key agreement with strong fairness property,” Computer Systems Science and Engineering, vol. 35, no. 6, pp. 457–465, 2020. [Google Scholar]
8. X. B. Chen, Y. R. Sun, G. Xu and Y. X. Yang, “Quantum homomorphic encryption scheme with flexible number of evaluator based on (k, n)-threshold quantum state sharing,” Information Sciences, vol. 501, no. 1, pp. 172–181, 2019. [Google Scholar]
9. G. Gordon and G. Rigolin, “Generalized quantum-state sharing,” Physical Review A, vol. 73, no. 6, pp. 062316, 2006. [Google Scholar]
10. C. M. Bai and Y. M. Li, “Probabilistic quantum information splitting based on the non-maximally entangled four-qubit state,” International Journal of Theoretical Physics, vol. 55, no. 3, pp. 1658–1667, 2016. [Google Scholar]
11. J. Wu, “Symmetric and probabilistic quantum state sharing via positive operator-valued measure,” International Journal of Theoretical Physics, vol. 49, no. 2, pp. 324–333, 2010. [Google Scholar]
12. J. Y. Peng and Z. W. Mo, “Hierarchical and probabilistic quantum state sharing with a nonmaximally four-qubit cluster state,” International Journal of Quantum Information, vol. 11, no. 1, pp. 1350004, 2013. [Google Scholar]
13. D. Gottesman, “Theory of quantum secret sharing,” Physical Review A, vol. 61, no. 4, pp. 313, 2000. [Google Scholar]
14. X. W. Wang, L. X. Xia, Z. Y. Wang and D. Y. Zhang, “Hierarchical quantum-information splitting,” Optics Communications, vol. 283, no. 6, pp. 1196–1199, 2010. [Google Scholar]
15. X. W. Wang, D. Y. Zhang, S. Q. Tang and L. J. Xie, “Multiparty hierarchical quantum-information splitting,” Journal of Physics B: Atomic, Molecular and Optical Physics, vol. 44, no. 3, pp. 35505, 2011. [Google Scholar]
16. X. W. Wang, D. Y. Zhang, S. Q. Tang, X. G. Zhan and K. M. You, “Hierarchical quantum information splitting with six-photon cluster states,” International Journal of Theoretical Physics, vol. 49, no. 11, pp. 2691–2697, 2010. [Google Scholar]
17. X. H. Li, P. Zhou, C. Y. Li, H. Y. Zhou and F. G. Deng, “Efficient symmetric multiparty quantum state sharing of an arbitrary m-qubit state,” Journal of Physics B: Atomic, Molecular and Optical Physics, vol. 39, no. 8, pp. 1975–1983, 2006. [Google Scholar]
18. H. Yuan, Y. M. Liu, W. Zhang and Z. J. Zhang, “Optimizing resource consumption, operation complexity and efficiency in quantum-state sharing,” Journal of Physics B: Atomic, Molecular and Optical Physics, vol. 41, no. 14, pp. 145506, 2008. [Google Scholar]
19. Z. Y. Xue, P. Dong, Y. M. Yi and Z. L. Cao, “Quantum state sharing via the GHZ state in cavity QED without joint measurement,” International Journal of Quantum Information, vol. 4, no. 5, pp. 749–759, 2006. [Google Scholar]
20. S. Choudhury, S. Muralidharan and P. K. Panigrahi, “Quantum teleportation and state sharing using a genuinely entangled six-qubit state,” Journal of Physics A: Mathematical and Theoretical, vol. 42, no. 11, pp. 115303, 2009. [Google Scholar]
21. R. Raussendorf and H. J. Briegel, “A one-way quantum computer,” Physical Review Letters, vol. 86, no. 22, pp. 5188–5191, 2001. [Google Scholar]
22. S. Muralidharan and P. K. Panigrahi, “Perfect teleportation, quantum-state sharing, and superdense coding through a genuinely entangled five-qubit state,” Physical Review A, vol. 77, no. 3, pp. 1, 2008. [Google Scholar]
23. P. Agrawal and B. Pradhan, “Task-oriented maximally entangled states,” Journal of Physics A: Mathematical and Theoretical, vol. 43, pp. 23, 2010. [Google Scholar]
24. M. Q. Bai and Z. W. Mo, “Hierarchical quantum information splitting with eight-qubit cluster states,” Quantum Information Processing, vol. 12, no. 2, pp. 1053–1064, 2013. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |