DOI:10.32604/cmc.2021.014966

| Computers, Materials & Continua DOI:10.32604/cmc.2021.014966 |  |
| Article |
Cogent and Energy Efficient Authentication Protocol for WSN in IoT
1Department of CS & IT, University of Azad Jammu and Kashmir, Muzaffarabad, 13100, Pakistan
2Birla Institute of Technology, Mesra, Jharkhand, 814142, India
3Raptor Interactive (Pty) Ltd., Eco Boulevard, Witch Hazel Ave, Centurion, 0157, South Africa
4The School of Computer Science and Engineering, Kyungpook National University, Daegu, 41566, Korea
*Corresponding Author: Anand Paul. Email: paul.editor@gmail.com
Received: 29 October 2020; Accepted: 02 February 2021
Abstract: Given the accelerating development of Internet of things (IoT), a secure and robust authentication mechanism is urgently required as a critical architectural component. The IoT has improved the quality of everyday life for numerous people in many ways. Owing to the predominantly wireless nature of the IoT, connected devices are more vulnerable to security threats compared to wired networks. User authentication is thus of utmost importance in terms of security on the IoT. Several authentication protocols have been proposed in recent years, but most prior schemes do not provide sufficient security for these wireless networks. To overcome the limitations of previous schemes, we propose an efficient and lightweight authentication scheme called the Cogent Biometric-Based Authentication Scheme (COBBAS). The proposed scheme is based on biometric data, and uses lightweight operations to enhance the efficiency of the network in terms of time, storage, and battery consumption. A formal security analysis of COBBAS using Burrows–Abadi–Needham logic proves that the proposed protocol provides secure mutual authentication. Formal security verification using the Automated Validation of Internet Security Protocols and Applications tool shows that the proposed protocol is safe against man-in-the-middle and replay attacks. Informal security analysis further shows that COBBAS protects wireless sensor networks against several security attacks such as password guessing, impersonation, stolen verifier attacks, denial-of-service attacks, and errors in biometric recognition. This protocol also provides user anonymity, confidentiality, integrity, and biometric recovery in acceptable time with reasonable computational cost.
Keywords: Internet of things; wireless sensor networks; authentication; Burrows–Abadi–Needham logic; fuzzy extractor; elliptic curve cryptography
The core purpose of the Internet of things (IoT) is a convergence of the physical and digital worlds. On the IoT, a set of sensors is attached to a thing (object or device) from which sensors collect various data and transmit it to a central system via a public network. The central system organizes data and extracts results before sending it to an authorized recipient. Consequently, an authorized user can remotely connect with that object or thing. Statistics show that the IoT market is continuously growing. By 2019, the IoT market growth was 212 billion US dollars, and in 2020, it is expected to reach up to 248 billion US dollars [1]. Moreover, the number of connected devices is expected to reach 100 billion by 2030. There are many examples of IoT, such as smart cities, smart homes, industry and building automation systems, and health care systems. A wireless sensor network (WSN) embedded in a building/home provides services such as heat control, air conditions, refrigerator, and lighting control, security and surveillance. Conventional cryptographic algorithms may not be practicable for WSN or IoT due to insufficient computational and storage resources of remote sensor systems. Furthermore, traditional password-based protocols can be vulnerable because they are easily breakable, especially by social engineering. In the IoT, a user registers on a network themselves to acquire data from the sensors. This registration is performed by a gateway node; after successful registration, a user may be able to access secret information. During the registration or login phase, an intruder can easily obtain data and secret information because this information is transmitted through public networks. In such situations, an efficient, lightweight, and intelligent scheme is required to ensure the security of wireless sensors. To ensure that communication between a user and sensor nodes remains secure, various authentication schemes have been proposed over the last decades; however, most of these schemes fail to provide sufficient security for practical applications and future development. In this study, we propose an authentication scheme using light operations, providing a higher level of security than previously proposed related schemes.
For the analysis of the proposed scheme, we use the Dolev–Yao model [2], which is based on the assumption that an adversary can attack at any time and at any level. In the login and authentication phase, an adversary can steal the password or impersonate a legal user or node. Similarly, an adversary can repudiate and change the content of a message. An attacker can also send fake messages to the gateway and sensor nodes, and involve the nodes in useless tasks. All the above threats are considered in the proposed protocol. We have relied on hashing and encryption algorithms for security. This protocol also uses ECC and RC5 to protect networks from attackers. The contributions of this research are briefly summarized below.
• A detailed analysis of recent biometric-based authentication schemes, highlighting their limitations, is presented, particularly a cryptanalysis of the scheme proposed by Riaz et al. [3].
• A new scheme named Cogent Biometric-Based Authentication Scheme (COBBAS) is proposed that provides sufficient security and lightweight operations, enhancing the network efficiency in terms of communication and computational overload.
• Time stamps have been used in the majority of existing schemes to ensure data freshness. Because a time stamp requires clock synchronization between the user’s mobile device or PC and a WSN, it is an unreasonable way to ensure data freshness. COBBAS uses a nonce value instead of a time stamp to ensure data freshness.
• The authenticity of the proposed scheme is formally analyzed using Burrows–Abadi–Needham (BAN) logic. Moreover, the Automated Validation of Internet Security Protocols and Applications (AVISPA) tool is used to demonstrate that the proposed scheme is secure.
• Informal security analysis of COBBAS is performed to check its protection against various cybersecurity attacks.
• The efficiency of the proposed scheme in terms of time and computational cost is also compared with recent existing schemes.
In the remaining paper, Section 2 provides a comprehensive literature review of prior schemes. The detailed work of the Secure User Biometric Based Authentication Scheme (SUBBASe) and its limitations are presented in Section 3. The proposed scheme is explained in Section 4. The results, including formal and informal analyses, are presented in Section 5. Section 6 concludes.
To ensure the security of WSNs, many password-based authentication schemes have been proposed over the last few decades [4–13]. More recently, Jian Jun et al. [14] proposed a biometric authentication scheme consisting of four phases: registration, login, authentication, and password change. As transmitted messages are not encrypted in this scheme, if an unauthorized user obtains control over a sensor node, he/she can easily capture all the information stored on that sensor node. In this scheme, secure channels are not provided; thus, it has major problems with data confidentiality and integrity.
Khan and Alghathbar’s (K-A) scheme [10] is a password-based authentication scheme; however, it is defenseless against non-repudiation and mutual authentication between the user and gateway node. Yuan modified the K-A scheme to remove these weaknesses in their protocol [15]. In addition, Das proposed a scheme that consists of a registration phase, login, authentication, and a key agreement phase. His scheme resists insider attacks, online password-guessing attacks, and biometric key-guessing attacks. The author passwords, smart cards, and user biometrics for authentication. Hence, this authentication scheme depends on three factors [16].
To address the weaknesses of Yuan’s scheme, Wei et al. [17] proposed a scheme that suffers from many vulnerabilities such as the misuse of biometrics, stolen smart card attacks, gateway node impersonation attacks, and a lack of session key establishment. Wei et al. proposed a three-phase scheme that removed some of the weaknesses of the Yuan scheme. Similarly, Wu et al. [18] identified the weaknesses in Das’ scheme; i.e., it is defenseless against offline password-guessing and de-synchronization attacks. To improve Das’ scheme, Wu et al. proposed a two-step registration phase of user registration and sensor node registration. In this scheme, they provide a secure mechanism against insider, offline password-guessing, user forgery, and gateway forgery attacks.
Park et al. [19] proposed a three-factor authentication scheme. This scheme draws its efficiency from the use of elliptic curve cryptography and a fuzzy extractor. Maurya et al. [20] proposed another fuzzy extractor-and ECC-based scheme consisting of four phases. However, Maurya’s scheme was inefficient with regard to computation time.
Kang et al. [21] proposed a scheme to address the problems of a lack of user anonymity and offline password-guessing attacks in previous schemes. Their analysis shows that their scheme provides a high level of security without the need for time synchronization. The Bi-Phase Authentication Scheme (BAS) [22] was proposed to improve Wong et al. [6] scheme. BAS consists of initial and final authentication phases, and uses special hardware called Full Function Devices (FFDs) and Reduced Function Devices (RFDs). BAS has several weaknesses; for instance, the protocol requires extra hardware, message confidentiality is not considered, and a session key is not established after user authentication.
To address the weaknesses of the BAS scheme, the SUBBASe was proposed in [3]. SUBBASe provides mutual authentication and network defense against several common security attacks such as stolen verifier attacks, message confidentiality, replay attacks, guessing attacks, and network traffic attacks. However, it suffers from security vulnerabilities such as biometric recognition errors, user anonymity issues, perfect forward secrecy, and gateway node impersonation attacks. To overcome the vulnerabilities of SUBBASe, Riaz et al. [23] proposed a scheme with two phases. The first phase was “Registration” and the second was “Login and Authentication.” This scheme overcomes the weaknesses of SUBBASe, removes biometric recognition errors, and ensures user anonymity. However, it still suffers from gateway node impersonation attacks and Sybil attacks. In addition, these schemes use a time stamp to ensure data freshness. Because the time stamp requires clock synchronization between a user’s mobile device or PC and the WSN, this timestamp is not a practical way to ensure data freshness.
Authentication in WSNs has attracted considerable research attention in the domain of IoT and smart homes. In 2019, Shin et al. [24] proposed a smart card-based authentication scheme for smart homes. Their scheme consists of five phases, but takes considerable time to complete its run. Lightweight three-factor authentication schemes have been proposed for IoT and 5G in [25,26] respectively.
All these schemes require smart cards to store user biometric information and provide authentication. These schemes provides desirable attributes for IoT environments, and authors’ shows that the computation and communication costs of their proposed scheme are suitable for extremely low-cost IoT devices. However, the need for smart cards was removed using the scheme proposed in [27]. Biometric and smartcard-based authentication schemes have been proposed for health care in [28,29]. A stream-based authentication mechanism, using key authorization infrastructure, specifically addressing security concerns of multi-homing sub-aqueous big data networks was presented in [30]. A novel Fractal-Based Authentication Technique was proposed by implementing a Sierpinski triangle in [31]. Their scheme reduces the probability of password guessing, and provides security against attacks such as shoulder surfing. To reduce energy consumption in IoT, a game-based mechanism was suggested in [32], and an electoral system was proposed in [33]. These schemes select the most appropriate cluster heads or community heads to enhance the efficiency of a network. Human activity recognition in home automation systems is an emerging topic addressed in [34]. Their scheme provides an efficient technique to observe human behavior within a smart home. The study of human behaviors can also be helpful in designing authentication mechanisms.
All these schemes are valuable additions to IoT systems; however, they also suffer from several security threats. To overcome the flaws in these schemes, we propose a scheme called “COBBAS.” It not only provides sufficient security, but also uses nonce values instead of time stamps to ensure data freshness. Furthermore, this scheme removes biometric recognition errors using fuzzy extraction. The authenticity of the proposed scheme is formally analyzed using BAN logic. Moreover, the AVISPA tool is used to prove that the proposed scheme is secure.
In this section, we first provide a brief description of the details of SUBBASe [3], and then, conduct a security analysis to explain its vulnerabilities. For convenience, the notations used in this paper are given in Tab. 1.
Table 1: Notations used in SUBBASe and proposed scheme
This scheme has two phases. In the first phase, the user enrolls themselves with the network, which is called the enrollment phase. The second is an authentication phase where the user is authenticated by a trusted node, and the required information is provided to the user.
Before deployment, each node in the network is preloaded with the following information: ID of sensor node and secret value xo. We describe both phases and security weaknesses below.
a) In the enrollment phase, the user registers with the network. The user imprints their biometric data, and calculates its hash value. Then, the user inputs IDi and sends it to a trusted node, i.e., IDi and Ai.
b) The trusted node receives the value from the user and calculates s, which is a hash value of the IDi of a user and a secret xo, i.e., s = h(IDi||xo). Then, the trusted node sends this value to the user.
a) In this phase, the user imprints finger Bi and calculates the hash value of biometric A
b) After receiving a message from the user, the sensor node calculates the time interval if T1 − T0 ¿
c) The trusted node receives the message and checks the time stamp if T3 − T2 ¿
d) The sensor node first verifies the timestamp; if condition T5 − T4 ¿
e) The user verifies the time stamp if T7 − T6
In SUBBASe, the IDi of the user is sent on public network without encryption. In the enrollment phase, the user inputs his/her IDi, imprints his/her biometric Bi, calculates Ai, which is the hash of Bi, and sends it to the trusted node (TN). Similarly, in the authentication phase, the user imprints finger Bi and calculates the hash value of biometric A
3.3.2 Biometric Recognition Error
A hash function returns a different value even if a single bit changes in input. Conversely, biometric input contains various noise and cannot reproduce 100% identical output over multiple access attempts. In the enrollment phase, the users imprint their biometric Bi and calculate its hash value Ai. Moreover, in the authentication phase, the user again imprints finger Bi and calculates the hash value of biometric A
The session keys perform a crucial role in security. Moreover, sensor nodes have limited computational resources. The SUBBASe session key (sk) is created by the sensor node through the following operations; the sensor node computes s = h(IDi||xo) to calculate sk = h(IDi||T6||s). Then, the sensor node and user will use this key as a session key for the ongoing session. ESK(d) represents the encryption of the required user information. Session key sk is calculated using parameters IDi, T6, and s. As we know that IDi is not encrypted, the adversary can easily obtain it. Similarly, s = h(IDi||xo) also depends on IDi and xo. In other words, the session key only depends on IDi, xo, and T6, which is not efficient. Moreover, the calculation of hash values by a sensor node is not efficient in terms of the computational load. This task can instead be performed by a trusted node that has high computational capacity.
In proposed scheme, the following information is preloaded onto the network nodes.
• The node ID
• A secret value xo
The secret value xo is shared among the user, sensor node (SN), and gateway node (GN). The login and authentication phases are performed by both the sensor and gateway nodes. Two types of devices are used in WSNs, namely FFDs and RFDs. In this scheme, an FFD acts as an authenticator, whereas an RFD continuously manages communication among the devices. In this scheme, the fingerprint of a user is collected, and a random string is generated using a fuzzy extractor. The collection of fingerprints does not require special hardware, because a user can easily imprint his/her biometric on his/her personal tablet or PC to login into the network. COBBAS uses SHA-256 to perform a one-way hash function. It uses RC5 with a key size of 20 bytes, as this size is the most suitable for resource-constrained devices. The phases of the proposed scheme are described below.
In the registration phase, the user is registered with the network. The steps are briefly discussed below.
a) The user inputs his/her IDi, password PW, and biometric Bi using a tablet or PC. The user computes
b) The gateway node calculates the authentication measures using the received values. The gateway node calculates Ni, which will be used by the gateway node to authenticate the user during the login and authentication phase. Si is used for user anonymity, and Mi is used by the sensor node to authenticate the gateway node in the login and authentication phase. The gateway node broadcasts M2, which comprises the following values (Ni,Si,Mi), to the user and sensor node.
c) The gateway node broadcasts the above parameters to the user and all nodes in the network. After this step, the registration phase is complete. Fig. 1 describes the process of registration.

Figure 1: Registration phase of proposed scheme
4.2 Login and Authentication Phase
The steps included in login and authentication phase are given below.
a) The user again enters his/her IDi and password PW*, and imprints his/her biometric
b) The gateway node first verifies the user as IDi = ID
c) The sensor node first verifies the gateway node and user by comparing Mi = M
d) The user calculates Ci with the help of Di, Ci =
e) The user sends an acknowledgment to the sensor node to ensure mutual authentication as (N
f) The sequence of message exchanges in the login and authentication phases are shown in Fig. 2.

Figure 2: Login and authentication phases of proposed scheme
5.1 Formal Security Analysis Using BAN Logic
COBBAS provides mutual authentication between the sensor node and user. In this section, we prove this using BAN logic [35]. The postulates of BAN logic are described, and the formal proof of the proposed scheme, which comprises “Assumptions,” “Messages,” “Goals,” and “Analysis” parts, is given below. The basic symbols used for BAN logic are described in Tab. 2.
Table 2: Notations and symbols used in BAN logic

Rule 1: Message meaning rule:
Rule 2: Nonce verification rule:
Rule 3: Belief rule
Rule 4: Freshness rule:
Rule 5: Jurisdiction rule:
Rule 6: Seeing rule:
The message exchange of COBBAS in idealized form is given below.
Message 1: U
Message 2: GN
Message 3: SN
Message 4: U
To ensure secure operation, the proposed protocol should meet the following security goals.
Goal 1: U|
Goal 2: SN |
Goal 3: U|
Goal 4 : SN|
To proceed with the proof, following assumptions are made.
Assumption 1: U |
Assumption 2: GN |
Assumption 3: GN |
Assumption 4: SN |
Assumption 5: SN |
Assumption 6: U |
Assumption 7: U |
Assumption 8: SN |
Step 1: From Message 1,
Step 2: From the message meaning rule and Assumption 2
GN |
Step 3: From Message 2,
Step 4: From the message meaning rule and Assumption 4
SN |
Step 5: From Message 3,
Step 6: From the message meaning rule and Assumption 6
U |
Step 7: From Message 4,
Step 8: From the message meaning rule and Assumption 5
SN |
Step 9: From Step 6, the freshness rule, and Assumption 7,
Step 10: From Step 6 and the second seeing rule,
Step 11: From Step 8, the freshness rule, and Assumption 8,
Step 12: From Step 8 and the second seeing rule,
Step 13: From Steps 6 and 9, the nonce verification rule, and Assumption 7,
Step 14: From the nonce verification rule, Assumption 8, and Steps 8 and 11,
Key freshness is vital to security protocols. The results of Step 9, i.e., Eq. (10), prove that the user trusts the freshness of the key shared between the user and sensor node. Similarly, from Step 11 Eq. (12), it is clear that the sensor node also believes that the key shared between itself and the user is fresh. Moreover, Step 10 shows that the user believes that he/she and the sensor node share the same secret key (Goal 1). Step 12 verifies that the sensor node also believes that it shares the same secret key with the user (Goal 2). Steps 13 and 14 verify that the user believes that the sensor node believes that the user and sensor node share the same secret key and vice versa (Goals 3 and 4).
5.2 Formal Security Analysis with AVISPA
AVISPA is an automated protocol validation tool. This tool uses high-level protocol specification language (HLPSL) [36]. AVISPA provides a suite of applications for building and analyzing formal models of security protocols written in HLPSL.
In this section, it is proven that the proposed scheme is safe against intruder attacks. The session key generated by the sensor node is safely received by the user. HLPSL is a role-based language. In the proposed scheme, three entities are involved: user (U), gateway node (GN), and sensor node (SN). The roles of these entities are described in the HLPSL code in Figs. 3–5, respectively.

Figure 3: Role specification of user in HLPSL

Figure 4: Role specification of gateway in HLPSL

Figure 5: Role specification of sensor node
Once the basic roles have been defined, we need to define a composed role and session role (Fig. 6) to integrate them so that several roles can be executed together. Lastly, the environment role is defined in Fig. 7, which contains “intruder knowledge” and “goal section.”

Figure 6: Role session

Figure 7: Environment and goals in HLPSL
The results of the AVISPA analysis, using on-the-fly model-checker (OFMC) and attack search (AtSeE) backends to ensure the security of the proposed protocol, are shown in Figs. 8 and 9. To estimate its security against a replay attack, the OFMC checks whether a legitimate entity can execute the protocol by searching for a passive adversary. Moreover, the OFMC checks whether the proposed protocol is secure against the man-in-the-middle attack using the Dolev–Yao model.

Figure 8: Simulation results with OFMC

Figure 9: Simulation results with ATSE
The OFMC backend takes 0.04 s to visit eight nodes. The replay attack and Dolev–Yao model checks were performed successfully, showing that the proposed protocol is safe against replay and man-in-the-middle attacks. Figs. 7–9 show the goals section and simulation results.
This section presents the security analysis of COBBAS with a focus on the shortcomings of previous authentication mechanisms, i.e., user anonymity, integrity, and biometric recognition error. It also provides an in-depth analysis of how the proposed scheme is resilient against various security attacks.
The proposed scheme ensures the user’s anonymity because of the shared secret xo. The user calculates a variable Yi, which is XOR with IDi and Ni. Here, Ni was shared by the gateway node during the registration phase. Then, the user calculates
In this scheme, the user sends Na, a nonce value, to the gateway node. A nonce is the number generated by a node or user for one session only. These variables cannot be used in the next section. The nonce Na sent from the user will be received by the sensor node. The sensor node encrypts Na and sends it to the user. The user receives the values and other data with his/her generated nonce. This confirms that the message has not been replayed.
The proposed scheme avoids biometric recognition errors using a fuzzy extractor. When the user inputs his/her biometric Bi using a tablet or computer, the protocol first calculates Ri and Pfe using the fuzzy extractor, where Ri is a random string that represents Bi and Pfe is a helping string.
Gen(Bi) = (Ri, Pfe)
When the user wants to login to the network again, the fuzzy extractor calculates
Rep(B
The advantage of a fuzzy extractor is that, if there is a small difference between Bi and
The integrity of a scheme is established if an adversary cannot alter the contents of a transmitted message. In this scheme, integrity is ensured using hash functions. The IDi of the user is sent as
Previously proposed schemes using smart cards or biometrics required special hardware. To use smart cards, a card reader is necessary. In this scheme, the user imprints his/her biometrics on his/her tablet or PC to login to the network. Hence, special hardware is not required in this scheme.
An insider attack is launched by an adversary through an authorized system. It is difficult to identify and protect against insider attacks.
In this scheme, this type of attack is not beneficial for the attacker because of one-way hashing. All the information that is sent is calculated using a one-way hash function.
5.3.7 Password-Guessing Attack
The proposed scheme resists password-guessing attacks because the user imprints his/her personal biometrics for logging in. The password is encrypted with a one-way hash function. Even the gateway node does not know the original password. Hence, it is difficult for an adversary to obtain the original password or biometric imprint of the user.
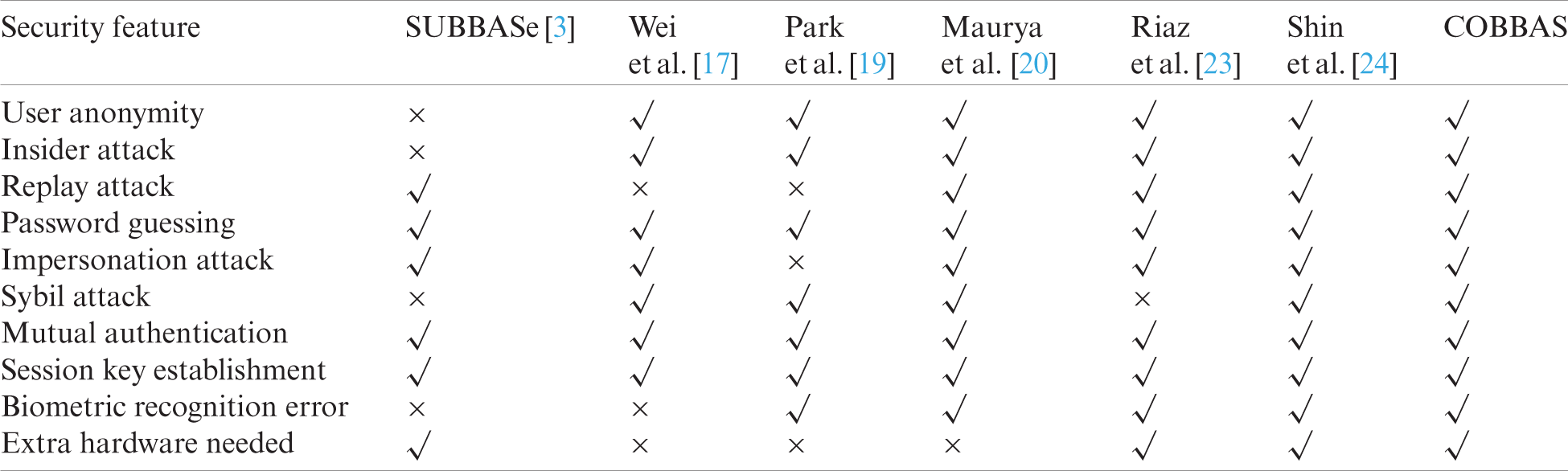
Tab. 3 compares the proposed scheme with previous related schemes based on various security features. It clearly shows that the proposed scheme provides mutual authentication and session key establishment, and is robust to biometric recognition error.
Table 3: Comparison of security features with related schemes
5.4 Performance Analysis of COBBAS
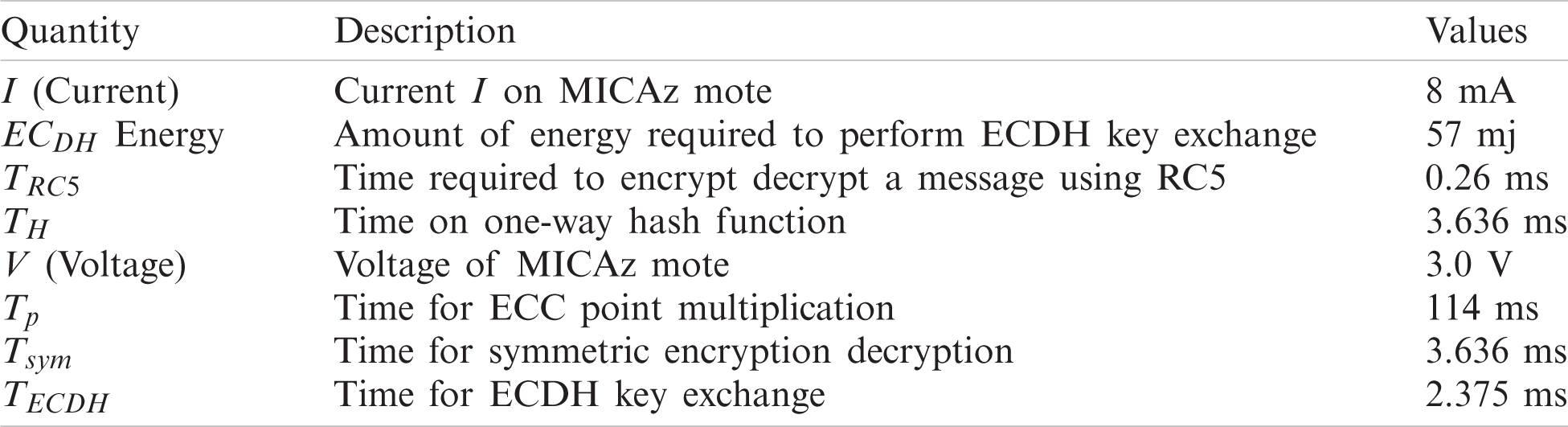
MICAz motes were used to evaluate the time utilization and energy consumption of the COBBAS protocol on sensor nodes.
The results are then compared with the related schemes proposed by Wei et al. [17], Maurya et al. [20], Shin et al. [24], Park et al. [19], SUBBASe [3], and Riaz et al. [23]. The time and energy consumed by the related schemes were also calculated for the MICAz motes. The MICAz mote is constructed using second-and third-generation sensor node technology by Crossbow Technology USA [37]. MICAz motes can measure biometric pressure and seismic waves, and are equipped with humidity, light, and temperature sensors [38].
The current I on the MICAz mote is 8 mA, and its voltage is 3 V [20]. The total energy required for elliptic-curve Diffie-Hellman (ECDH) key exchange is 57 mJ [3]. Therefore, the time required for key exchange can be calculated by:
57 = 3
t = 2.375 ms (i.e., TECDH)
where E is the energy consumed, V is the voltage of the node, I is the current in mA, and t is the time required for key exchange. Therefore, the time required for one ECDH key exchange (TECDH) on the MICAz mote is 2.375 ms. In addition, the computational cost for the fuzzy extractor is lesser than the cost of hashing [17]. Therefore, for simplicity, we assumed the same values for both operations. The time for the one-way hash function (TH) was 3.636 [24]. Here, TRC5 denotes the time required to perform one RC5 encryption or decryption on the MICAz mote. On the MICAz mote, execution time for one RC5 encryption or decryption was 0.26 ms [3]. Moreover, the time for symmetric key encryption/decryption cost is one hash function [3]. Therefore, we assumed that the time for symmetric key encryption decryption (Tsym) on the MICAz mote was 3.636 ms. The computational times on the MICAz mote for different cryptographic operations is given in Tab. 4
Table 4: Execution time and energy consumption on sensor node
According to [24], the execution time of a one-way hash function (T’H) on a PC is 2.58
Table 5: Execution time on PC/device

In this section, the proposed scheme and existing schemes are compared in terms of time consumption. We have compared only the login and authentication phases of COBBAS with previous schemes because registration and password updates are not used frequently. Tab. 6 summarizes the time analysis.
Table 6: Comparison of time consumption with related schemes
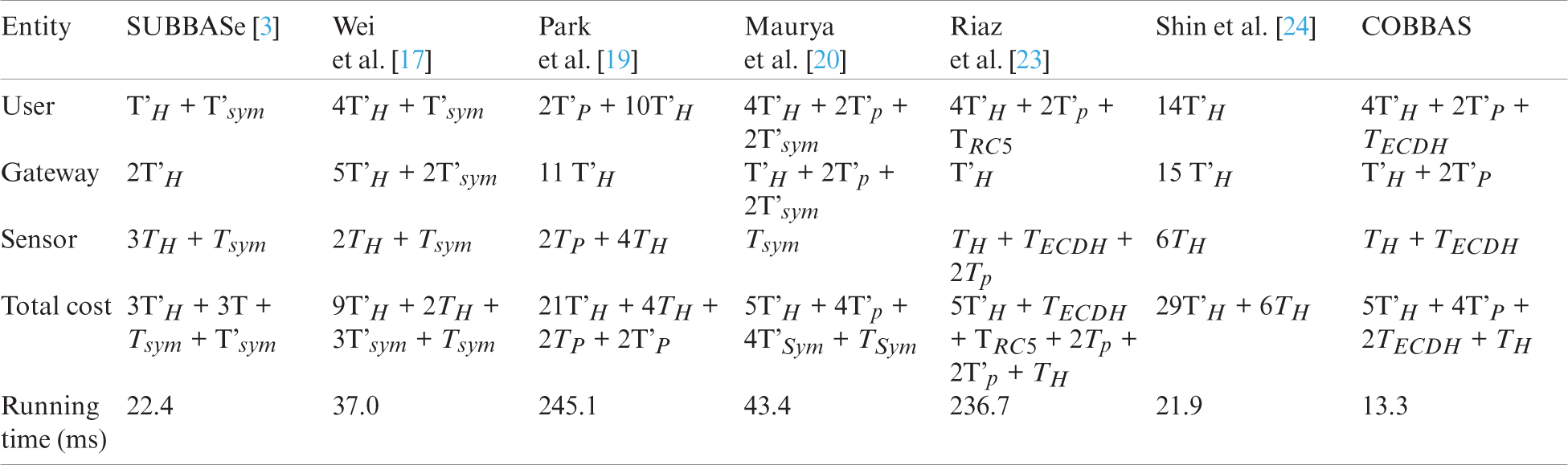
Tab. 6 shows that the times required for Maurya et al. [20] scheme, Wei et al. [17] scheme, Park et al. [19] scheme, Shin et al. [24] scheme, Riaz et al. [23] scheme, and SUBBASe [3] were 43.4, 37.0, 245.1, 21.9, 236.7, and 22.4 ms, respectively. The time required for the COBBAS scheme was 13.3 ms. The authentication time of the proposed scheme is much faster than that of the current schemes. Moreover, this comparison shows that the proposed scheme outperforms and provides a higher level of security, even with light computation.
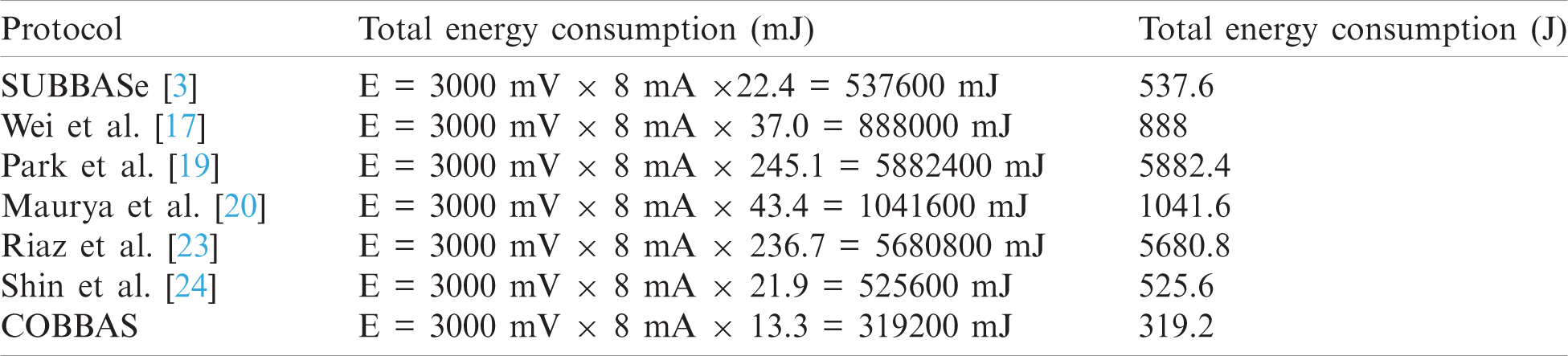
The authentication process is completed by exchanging several messages among the entities involved in the network. During this process, energy is consumed by the sensor node. This section compares the energy consumption of the proposed scheme with related schemes. We measured the energy consumed by the proposed protocol and related schemes on the MICAz mote. The energy is calculated with the help of Eq. 16. The energy consumed by each protocol for one node’s authentication is given in Tab. 7. This table shows the energy consumed by SUBBASe [3], Wei et al. [17], Park et al. [19] Maurya et al. [20], Riaz et al. [23] and Shin et al. [24] schemes are 537.6, 888, 5882.4, 1041.6, 5680.8, and 525.6 J, respectively. The energy consumed by the proposed method was only 319.2 J, which shows that the proposed scheme is efficient compared to related schemes in terms of energy input.
Table 7: Comparison of energy consumption with related schemes
In this study, we analyzed various studies related to authentication mechanisms in recent years. To overcome the flaws in previous schemes, we proposed an efficient authentication scheme, comprising only two phases using simple and lightweight computations. The COBBAS scheme protects WSNs from different types of attacks, and provides user anonymity along with biometric error recovery. The mutual authentication of the proposed scheme was proved using BAN logic. In addition, AVISPA analysis proved that the proposed scheme is safe from intruder-based interventions. Furthermore, an informal security analysis showed that COBBAS provides better security than previous schemes with reasonable resource utilization. Additionally, its computational cost and energy consumption are believed to be suitable for resource-constrained networks. Moreover, the proposed scheme is energy efficient, and provides a higher level of security than related proposed schemes.
Funding Statement: This project was funded by the National Research Foundation of Korea. Grant Number: 2020R1A2C1012196.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. Statista Research Department, “Global IoT end-user spending worldwide 2017–2025,” January, 2021. [Online]. Available: https://www.statista.com/statistics/976313/global-iot-market-size/. [Google Scholar]
2. D. Dolev and A. C. Yao, “On the security of public key protocols,” IEEE Transactions on Information Theory, vol. 29, no. 2, pp. 198–208, 1983. [Google Scholar]
3. R. Riaz, S. S. Rizvi, S. Shokat, S. J. Kwon and N. A. Gillani, “SUBBASE: An authentication scheme for wireless sensor network based on user biometric,” Wireless Communication and Mobile Computing, vol. 2019, no. 11, pp. 1–11, 2019. [Google Scholar]
4. R. Watro, D. Kong, S. F. Cuti, C. Gardiner, C. Lynn et al., “TinyPK: Securing sensor networks with public key technology,” in Proc. of the 2nd ACM Workshop on Security of Ad Hoc and Sensor Networks, New York, USA, 2004. [Google Scholar]
5. M. L. Das, “Two-factor user authentication in wireless sensor networks,” IEEE Transaction on Wireless Communication, vol. 3, no. 3, pp. 1086–1090, 2009. [Google Scholar]
6. K. H. Wong, Y. Zheng, J. Cao and S. Wang, “A dynamic user authentication scheme for wireless sensor networks,” in IEEE Int. Conf. on Sensor Networks, Ubiquitous, and Trustworthy Computing, Taichung, 2006. [Google Scholar]
7. H. R. Tseng, R. H. Jan and W. Yang, “A robust password-based authentication scheme for heterogeneous sensor networks,” Communication of IICM Taiwan, vol. 11, no. 3, pp. 1–13, 2008. [Google Scholar]
8. T. Chen and W. Shih, “A robust mutual authentication protocol for wireless sensor networks,” Electronics and Telecommunications Research Institute, vol. 32, no. 5, pp. 704–712, 2010. [Google Scholar]
9. T. H. Lee, “Simple dynamic user authentication protocols for wireless sensor network,” in Second Int. Conf. on Sensor Technologies and Applications, Cap Esterel, 2008. [Google Scholar]
10. M. K. Khan and K. Alghathbar, “Cryptanalysis and security improvements of two factor user authentication in wireless sensor network,” Sensors, vol. 10, no. 3, pp. 2450–2459, 2010. [Google Scholar]
11. S. G. Yoo, K. Y. Park and J. Kim, “A security-performance-balanced user authentication scheme for wireless sensor network,” International Journal of Distributed Sensor Networks, vol. 8, no. 3, pp. 382810, 2012. [Google Scholar]
12. P. Kumar, A. Gurtov, M. Ylianttila, S. Lee and H. Lee, “A strong authentication with user privacy for wireless sensor networks,” Electronics and Telecommunications Research Institute, vol. 35, no. 5, pp. 889–899, 2013. [Google Scholar]
13. S. Yu, J. Lee, K. Lee, K. Park and Y. Park, “Secure authentication protocol for wireless sensor networks in vehicular communication,” Sensors, vol. 18, no. 10, pp. 3191, 2018. [Google Scholar]
14. J. Yuan, C. Jiang and J. Zuowen, “A biometric based user authentication for wireless sensor networks,” Wuhan University Journal of Natural Sciences, vol. 15, no. 3, pp. 272–276, 2010. [Google Scholar]
15. J. J. Yuan, “An enhanced two-factor user authentication in wireless sensor network,” Telecommunication Systems, vol. 55, no. 1, pp. 105–113, 2014. [Google Scholar]
16. A. K. Das, “A secure and robust temporal credential-based three-factor user authentication scheme for wireless sensor networks,” Peer-to-Peer Networking and Applications, vol. 9, no. 1, pp. 223–244, 2016. [Google Scholar]
17. F. Wei, J. Ma, Q. Jiang, J. Shen and C. Ma, “Cryptanalysis and improvement of an enhanced two-factor user authentication scheme in wireless sensor network,” Information Technology and Control, vol. 45, no. 1, pp. 62–70, 2016. [Google Scholar]
18. F. Wu, L. Xu, S. Kumari and X. Li, “An improved and provably secure three-factor user authentication scheme for wireless sensor network,” Peer-to-Peer Networking and Applications, vol. 11, no. 1, pp. 1–20, 2018. [Google Scholar]
19. Y. Park and Y. Park, “Three-factor user authentication and key agreement using elliptic curve cryptosystem in wireless sensor networks,” Sensors, vol. 16, no. 12, pp. 2123, 2016. [Google Scholar]
20. A. K. Maurya and V. Sastry, “Fuzzy extractor and elliptic curve based efficient user authentication protocol for wireless sensor networks and internet of things,” Information-An International Interdisciplinary Journal, vol. 8, no. 4, pp. 136, 2017. [Google Scholar]
21. D. Kang, J. Jung, H. Kim, Y. Lee and D. Won, “Efficient and secure biometric based user authenticated agreement scheme with anonymity,” Security and Communication Network, vol. 2018, no. 12, pp. 1–14, 2018. [Google Scholar]
22. R. Riaz, T. S. Chung, S. S. Rizvi and N. Yaqub, “BAS: The biphase authentication scheme for wireless sensor network,” Security and Communication Networks, vol. 2017, no. 3, pp. 1–10, 2017. [Google Scholar]
23. R. Riaz, S. S. Rizvi, M. Shaheen and S. J. Kwon, “Enhanced biometric based user authentication scheme for wireless sensor networks using fuzzy extractor and elliptic curve cryptography,” Journal of Information Communication and Technologies, vol. 2016, pp. 1–14, 2020. [Google Scholar]
24. S. Shin and T. Kwon, “A lightweight three-factor authentication and key agreement scheme in wireless sensor networks for smart homes,” Sensors, vol. 19, no. 9, pp. 2012, 2019. [Google Scholar]
25. H. Lee, D. Kanga, J. Ryu, D. Wo, H. Kim et al., “A three-factor anonymous user authentication scheme for internet of things environments,” Journal of Information Security and Applications, vol. 52, pp. 102494, 2020. [Google Scholar]
26. S. Shin and T. Kwon, “A privacy-preserving authentication, authorization, and key agreement scheme for wireless sensor networks in 5g-integrated internet of things,” IEEE Access, vol. 8, pp. 67555–67571, 2020. [Google Scholar]
27. M. Wazid, A. K. Das, S. Shetty, J. J. Rodrigues and Y. Park, “LDAKM-EIoT: Lightweight device authentication and key management mechanism for edge-based iot deployment,” Sensors, vol. 19, no. 24, pp. 5539, 2019. [Google Scholar]
28. B. D. Deebak, F. Al-Turjman, M. Aloqaily and O. Alfandi, “An authentic-based privacy preservation protocol for smart e-healthcare systems in IoT,” IEEE Access, vol. 7, pp. 99, 2019. [Google Scholar]
29. Z. Ali, A. Ghani, I. Khan, S. A. Chaudhry, S. H. Islam et al., “A robust authentication and access control protocol for securing wireless healthcare sensor networks,” Journal of Information Security and Applications, vol. 52, no. 4, pp. 102502, 2020. [Google Scholar]
30. N. M. F. Qureshi, I. F. Siddiqui, A. Abbas, A. K. Bashir, C. S. Nam et al., “Streambased authentication strategy using iot sensor data,” Wireless Personal Communications, vol. 116, pp. 1217–1229, 2020. [Google Scholar]
31. A. Ali, H. Rafique, T. Arshad, M. A. Alqarni, S. H. Chauhdary et al., “A fractal-based authentication technique using sierpinski triangles in smart devices,” Sensors, vol. 19, no. 3, pp. 678, 2019. [Google Scholar]
32. M. Sohail, S. Khan, R. Ahmad, D. Singh and J. Lloret, “Game theoretic solution for power management in iot-based wireless sensor networks,” Sensors, vol. 19, no. 18, pp. 3835, 2020. [Google Scholar]
33. D. Singh, G. U. Rehman, A. Ghani, M. Zubair and M. I. Saeed, “SOS: Socially omitting selfishness in IoT for smart and connected communities,” International Journal of Communication System, pp. e4455, 2020. [Google Scholar]
34. D. Singh, M. Kaur, G. Kaur, P. K. Sharma and A. Jolfaei, “Binary cuckoo search metaheuristic-based supercomputing framework for human behavior analysis in smart home,” Journal of Supercomputing, vol. 76, no. 4, pp. 2479–2502, 2020. [Google Scholar]
35. Y. Zhou, L. Yu, S. Pan and Z. Wang, “BAN logic analysis method based on yahalom protocol,” Revista de la Facultad de Ingenieria, vol. 31, pp. 134–142, 2016. [Google Scholar]
36. The team AVISPA, “A Beginner’s Guide to Modelling and Analysing Internet Security Protocols,” Retrieved May 15, 2019, [Online]. Available: http://www.avispaproject.org/package/tutorial.pdf. [Google Scholar]
37. M. Johnson, M. Healy, P. v. Ven, M. J. Hayes, J. Nelson et al., “A comparative review of wireless sensor network mote technologies,” in IEEE SENSORS, 2009 Conf., Canterbury 8013, New Zealand, 2009. [Google Scholar]
38. R. P. Narayanan, T. V. Sarath and V. V. Vineeth, “Survey on motes used in wireless sensor networks: Performance & parametric analysis,” Wireless Sensor Network, vol. 8, no. 4, pp. 51–60, 2016. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |