DOI:10.32604/cmc.2021.016260

| Computers, Materials & Continua DOI:10.32604/cmc.2021.016260 |  |
| Article |
An Efficient Impersonation Attack Detection Method in Fog Computing
1Engineering Research Center of Intelligent Perception and Autonomous Control, Faculty of Information Technology, Beijing University of Technology, Beijing, 100124, China
2Faculty of Computer Science and Engineering, Ghulam Ishaq Khan Institute of Engineering Sciences and Technology, Topi, 23460, Pakistan
3Department of Electronics Engineering, FICT, Balochistan University of Information Technology, Engineering and Management Sciences, Quetta, 87300, Pakistan
4Department of Computer Science, Namal Institute, Mianwali, 42200, Pakistan
*Corresponding Author: Shanshan Tu. Email: sstu@bjut.edu.cn
Received: 28 December 2020; Accepted: 28 January 2021
Abstract: Fog computing paradigm extends computing, communication, storage, and network resources to the network’s edge. As the fog layer is located between cloud and end-users, it can provide more convenience and timely services to end-users. However, in fog computing (FC), attackers can behave as real fog nodes or end-users to provide malicious services in the network. The attacker acts as an impersonator to impersonate other legitimate users. Therefore, in this work, we present a detection technique to secure the FC environment. First, we model a physical layer key generation based on wireless channel characteristics. To generate the secret keys between the legitimate users and avoid impersonators, we then consider a Double Sarsa technique to identify the impersonators at the receiver end. We compare our proposed Double Sarsa technique with the other two methods to validate our work, i.e., Sarsa and Q-learning. The simulation results demonstrate that the method based on Double Sarsa outperforms Sarsa and Q-learning approaches in terms of false alarm rate (FAR), miss detection rate (MDR), and average error rate (AER).
Keywords: Fog computing; double Sarsa; attack detection; physical layer key security
Due to the growth of the Internet of Things (IoT) and mobile devices, many applications are sensitive to bandwidth and perceived latency [1,2]. Besides, the processing of these applications requires higher computation and communication costs [3]. In IoT, interconnected things generate a large amount of data. The data is usually processed in the cloud, prone to severe network congestion and load [4,5]. This is highly problematic, especially for the overall performance of time-sensitive applications and services. In particular, the recently developed 5G wireless networks have a higher demand for bandwidth, computing resource, security, and delay [6–9]. To address the problems mentioned above, fog computing was introduced to facilitate the computing, networking, and storage operations between end-users and cloud data centers. The added fog layer is located between the cloud and end-users. The primary function of fog computing is to process IoT data locally, thereby bringing the convenience of data storage, calculation, and transmission. It has the characteristics of low latency, location awareness, and large-scale IoT applications support [4]. However, due to its additional and unique features, it is faced with communication and data security issues.
In FC, most of the devices are connected wirelessly [10]. As a result, due to the wireless transmission medium’s broadcast characteristics, there is a security risk in communication between fog nodes and end-users [11]. For example, the attackers may pretend to be legitimate fog nodes or end-users, thereby sending signals to other nodes so that the receivers may receive wrong signals. To prevent the attack from disguised attackers and ensure the wireless network’s security in FC, both parties need to use a common key for encrypted transmission. Therefore, we propose the fusion of physical layer security (PLS) technologies based on the key generation and reinforcement learning algorithm to detect impersonation attacks.
On the one hand, PLS protects the information by exploiting the communications medium’s intrinsic characteristics or principles and is a promising wireless security technique [12]. Thus, we employ physical layer key generation technology based on PLS. Unlike traditional cryptography methods with computational complexity, it can provide real-time, non-distribution key generation means for both communicating parties with channel coding, pre-coding, signal processing, etc. On the other hand, reinforcement learning is the training of machine learning algorithms to help make a sequence of decisions. In this scheme, a user learns to achieve a goal in an uncertain and potentially complex environment via trial and error [13]. The learning is based on a game-like situation where the users obtain rewards through continuous interaction with the environment and attain the optimal strategies [14]. Thus, we propose a detection method with a Double Sarsa algorithm to defend against impersonation attacks. The proposed detection method based on Double Sarsa [14] utilizes the channel state information (CSI). It can obtain the optimal test threshold value to detect impersonation attacks in the dynamic environment. The main contributions of this work are summarized below.
• We investigate to tackle the impersonation attacks between fog nodes and legitimate end-users in fog computing (FC). For this purpose, we apply a reinforcement learning algorithm to detect the impersonation attacks.
• We formulate a zero-sum game between the illegitimate node (fog node or end user) and receiver. We obtain the optimal threshold value to detect impersonation attacks by establishing a hypothesis test based on channel state information (CSI) at the receiving end.
• We validate the performance of the proposed method by comparing with Sarsa and Q-learning in false alarm rate (FAR), miss detection rate (MDR), and average error rate (AER) based on a test threshold value. We find out that the FAR, MDR, and AER are decreased significantly as the experiments progress based on the appropriate threshold value with the proposed method. This shows that our proposed technique has a better detection capability.
The rest of the paper is organized as follows. In Section 2, we discuss the related work. Sections 3 and 4 describe our proposed system and proposed method, respectively. Section 5 presents the performance evaluation of our proposed method. Finally, the paper is concluded in Section 6.
Key generation technology exploits the randomness and reciprocity of wireless channels. In recent years, this approach is widely studied by many researchers. Zhang et al. [15] presented a survey of the key generation technologies related to the wireless channels. An information theory secret key generation (SKG) method is proposed in [16] for time-division duplexing (TDD) based orthogonal frequency-division multiplexing (OFDM) systems over multipath fading channels. In [17], the authors proposed a novel key generation scheme for wireless sensor networks, achieving a high key reconciliation rate. The authors in [18] developed an algorithm to protect the keys secret from eavesdropper and non-trusted selected relays, which improves the secret key generation rate (SKGR). FC cannot be considered fully secure, and it is faced with security vulnerabilities. To deal with this problem, different approaches have been proposed in the literature. Huang et al. [19] proposed an access tree structure and attribute-based signature technology in FC to implement ciphertext updating and computing outsourcing. To ensure the end-to-end security of IoT devices at the fog layer, Abbas et al. [20] proposed a novel fog security service based on two cryptographic schemes, i.e., identity-based encryption and identity-based signature. Tian et al. [21] proposed a three-layer storage framework to prevent an attack from the inside of the cloud server and protect data privacy. However, the traditional security methods are not suitable in a dynamic environment. These conventional methods have no self-learning ability and cannot make timely adjustments according to the changing environment, which causes difficulty in optimization.
Besides, reinforcement learning algorithms have been used by researchers to improve wireless network security. For instance, Xiao et al. [22] proposed a spoofing detection scheme based on Q-learning to detect spoofing attacks in wireless networks, and the efficiency of the proposed strategy is improved. In [23], the authors applied a Q-learning algorithm with reinforcement learning to detect the impersonation attacks, enhancing detection accuracy. However, these methods mentioned above only used one Q-table, which may make large changes in the threshold and slow convergence. Our proposed can solve the problem with two Q-tables, and the optimum test threshold value is obtained for each other’s estimation errors. It has better performance in detecting impersonation attacks in FC security.
This section illustrates the impersonation attack model and the security model based on the key generation. First, we discuss the system architecture to consider legitimate and illegitimate users. Then, a key generation model is presented to discuss the process of secret keys.
As depicted in Fig. 1, we consider a three-layer system architecture model of the FC network, including the cloud layer, fog layer, and end-user layer. The fog layer is composed of fog nodes, which can be computers, smartphones, etc. The end-user layer includes end-user devices and IoT devices. In this regard, let consider there are
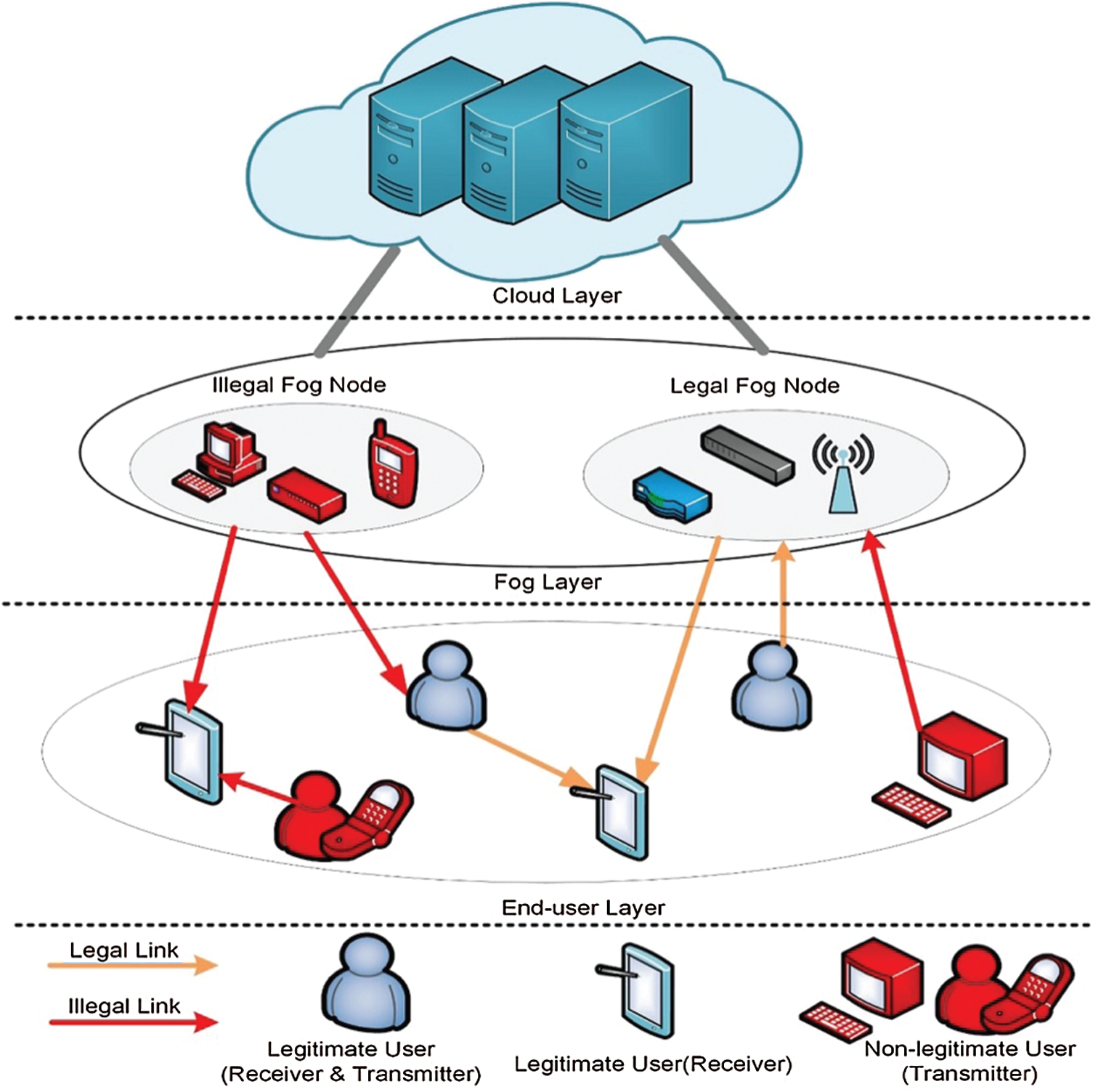
Figure 1: Impersonation attack network model
The fog nodes are used to provide computing, storage, and communication. They provide temporary storage and real-time analysis for terminal devices’ data and send their data summary to the cloud. Illegal users pretend to be legitimate users to enjoy the fog node’s services or pretend to be legal fog nodes to offer false services to end-users. These non-legitimate users (fog nodes or end-user nodes) claim to be legitimate and launch attacks on other network nodes. Consequently, it causes the wireless communication link between fog nodes and end-users’ insecure.
As mentioned in the previous section, the purpose is to generate a random and secure key for secure communication between fog nodes and end-users [24]. Therefore, we exploit the physical layer channel parameter, i.e., CSI, to generate the secret keys. The proposed key generation model is depicted in Fig. 2. In this model, we assume that the fog nodes and the end-users communicate in a time division duplex (TDD) mode. First, both parties send training signals to each other in a time slot. Based on the received signals, they will estimate the channel and measure the channel parameter. As the attacker may launch an attack at any time, the signal transmitted by the channel may be non-legitimate. The detection step is introduced to identify the legitimacy of the received signals. If the signal is non-legitimate, the two sides continue to transmit training signals to extract CSI.
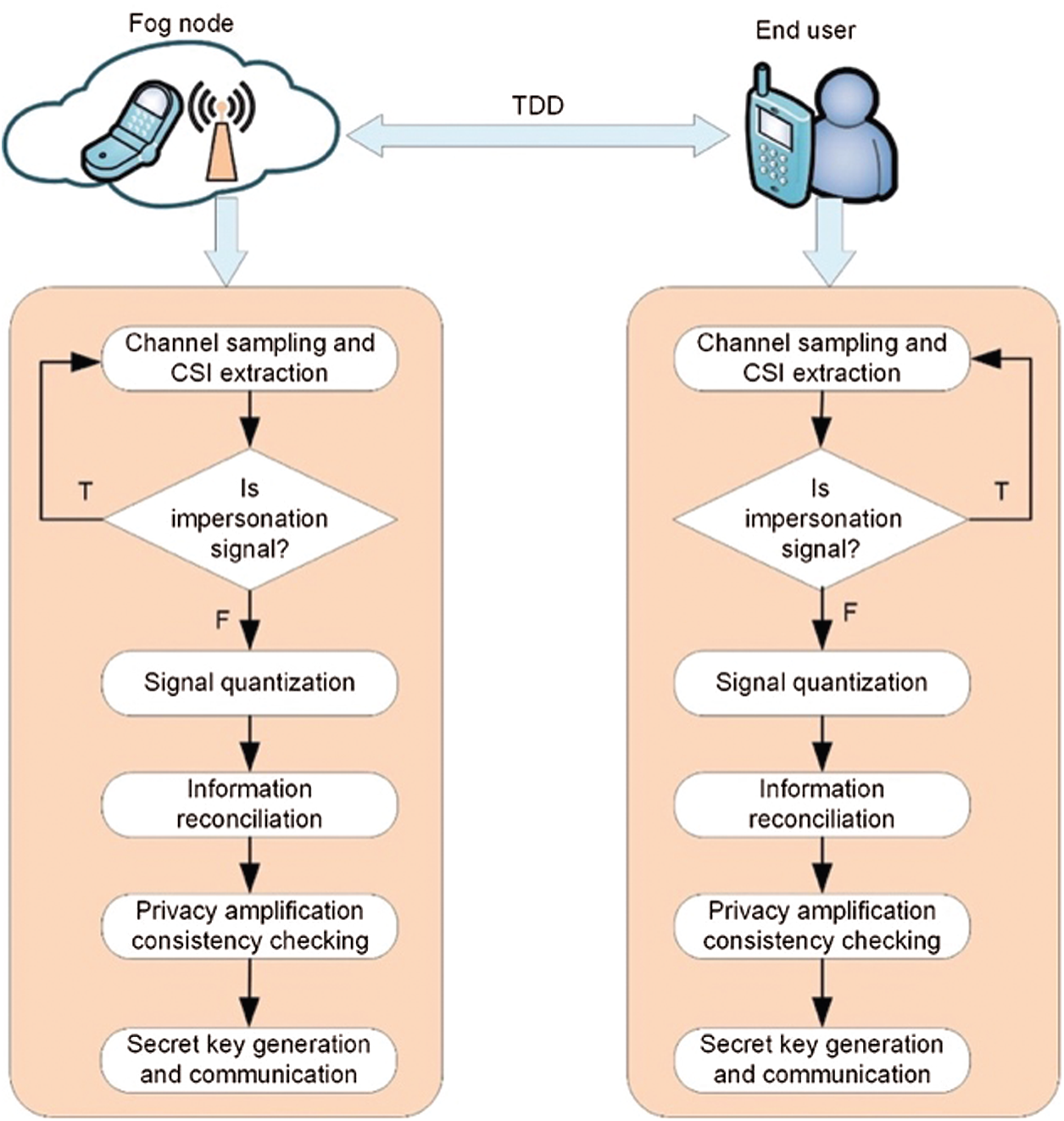
Figure 2: Security model based on key generation
Alternatively, the quantization step is performed to get the initial key bit sequence. The information reconciliation is then employed to correct mismatch bits and privacy amplification consistency checking to ensure the agreed key sequence security. After these steps, both parties’ common and secure secret key sequence is generated for secure communications. In this way, the communication between the fog node and the end-user node is coarse-grained detected, which reduces the communication and calculation overhead.
According to the models presented in the previous section, we establish the hypothesis test at the receiver. We then exploit the zero-sum game and the Double Sarsa algorithm [14] to present the proposed method.
For the hypothesis test, the fog node and the end-user send training signals to each other in the channel sampling stage. The receiving end estimates its related CSI and extracts the signal’s channel vector after receiving each signal. The channel vector of the signal accepted by the receiving end is called the channel record. The channel vector and the channel record are used to determine the sender’s legitimacy. The hypothesis test is built at the receiving end to detect the attack. The channel gain of each received training signal is sampled and estimated at the receiving end. Let
Where
•
•
Due to wireless channels’ spatial decorrelation, the CSIs of each legitimate node, attacker, and malicious nodes are different [25] but can be determined uniquely. As a result, if
The symbol
The value of the test threshold has a certain relationship with the detection accuracy. The false alarm rate (FAR) is high for a small threshold value, while a large threshold value results in a high miss detection rate (MDR). The FAR represents the probability that a legal signal sent by a legitimate node is detected as an illegitimate signal. The MDR represents the probability that an illegitimate signal is detected as a legal signal. Based on the hypothesis test, the FAR and MDR are calculated as below [23].
The AER is the probability of error in detecting impersonation attacks, which is given by
Where
•
• n is the relative change rate of channel gain;
•
•
4.2 Methodology of Impersonation Detection
Based on the impersonation attack model presented in Section 3.1, the interactions between an illegitimate node and a receiver can be considered a zero-sum game [26]. The probability that an illegitimate node sends an illegal signal is pk. The set of illegitimate signals sent by illegitimate nodes is
Where
• l1 is the gain of receiving legal signals, l2 is the gain of refusing illegal signals;
• r1 is the cost of receiving illegal signals, r2 is the cost of refusing legal signals;
•
Therefore, according to the zero-sum game, the utility at the receiving end is as follows.
In (10), the illegitimate nodes and the receivers play games in the static environment. However, the practical fog computing environment is dynamic. Specifically, the mobility of fog nodes and terminals can cause changes in the wireless channel, and the change rate has a particular impact on the key generation rate (KGR). In the dynamic scenario, it is difficult for the receiver to recognize the training signal’s legitimacy. Double Sarsa algorithm in reinforcement learning can be used to find out the optimal strategy with insufficient information in a dynamic environment [14,28].
In reinforcement learning, there are several important constants. First, the discount rate is used to control the proportion of current and future rewards. For the large value, the agent pays much attention to future rewards. However, for a small value, the agent focuses on the current rewards. Next is learning efficiency. For high efficiency, a large proportion of results are obtained with new attempts and vice versa. In Double Sarsa algorithm [14], two Q-tables are used to compensate for each other’s estimation errors. A small change in the Q-value can determine a steady policy and increase the reward. The receiver evaluate the T training signals sent by transmitter in each time slot via the hypothesis test. Meanwhile, the receiver employs the
In the Double Sarsa algorithm, aiming at reducing the impact of estimation errors and converging to the optimal Q value, the update rule of two Q-tables is given by
Where
•
•
•
•
Aiming to get an optimal action and maximize the utility, the proposed method to resist impersonation attack is described in Algorithm 1. We initialize some parameters, then judge the legitimacy of training signals according to the test threshold. Finally, we find the optimum test threshold value based on the Double Sarsa algorithm to detect impersonation attacks.
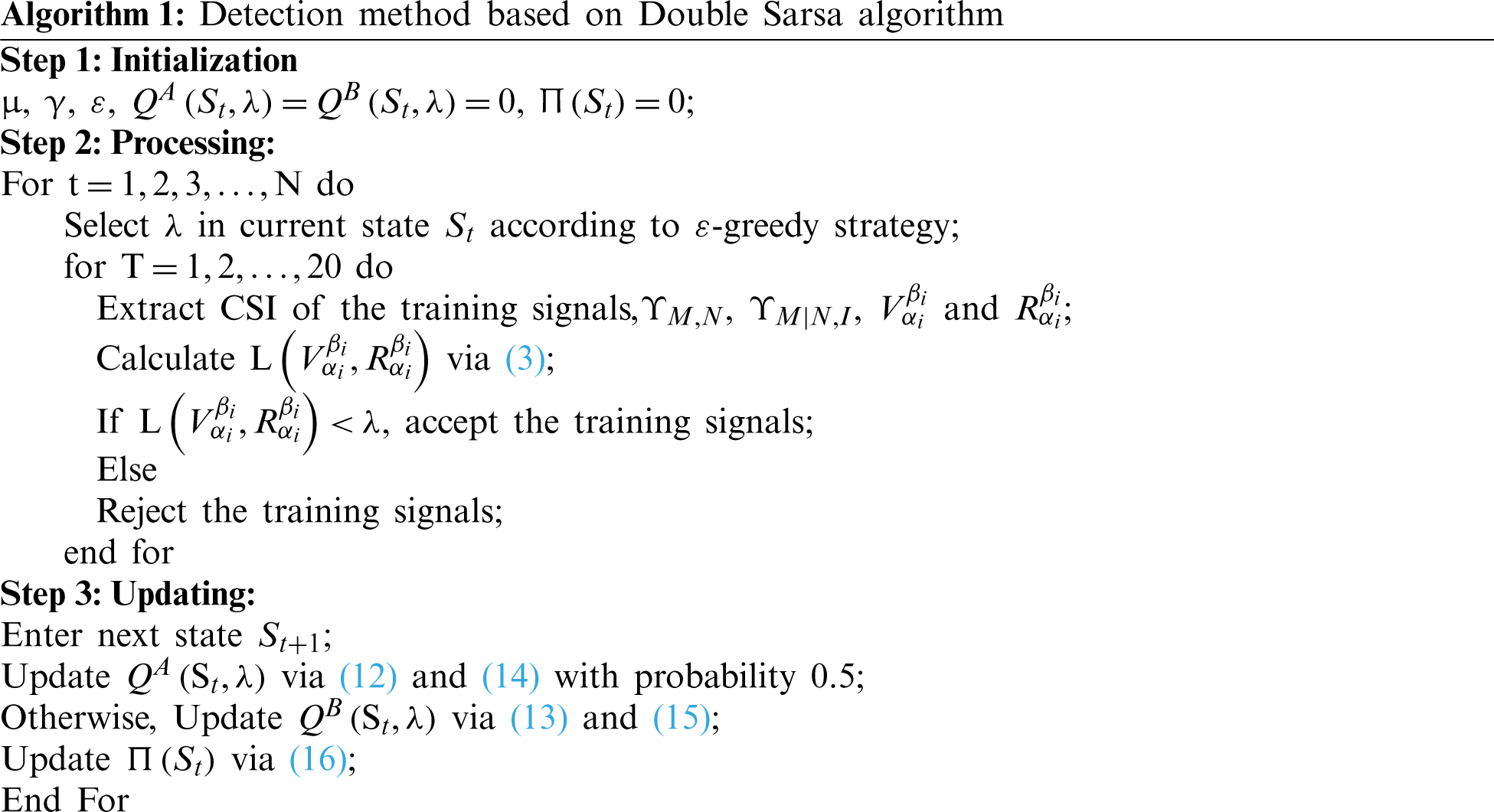
In this section, to assess the proposed method’s performance, we set four indicators, such as the utility at the receiver, FAR, MDR, and AER. And three different methods are compared for preventing impersonation attacks in 500 experiment trails.
5.1 Performance Metrics and Initial Parameters
In this study, we set the experimental environment as a space of
Table 1: List of symbols and names for parameters
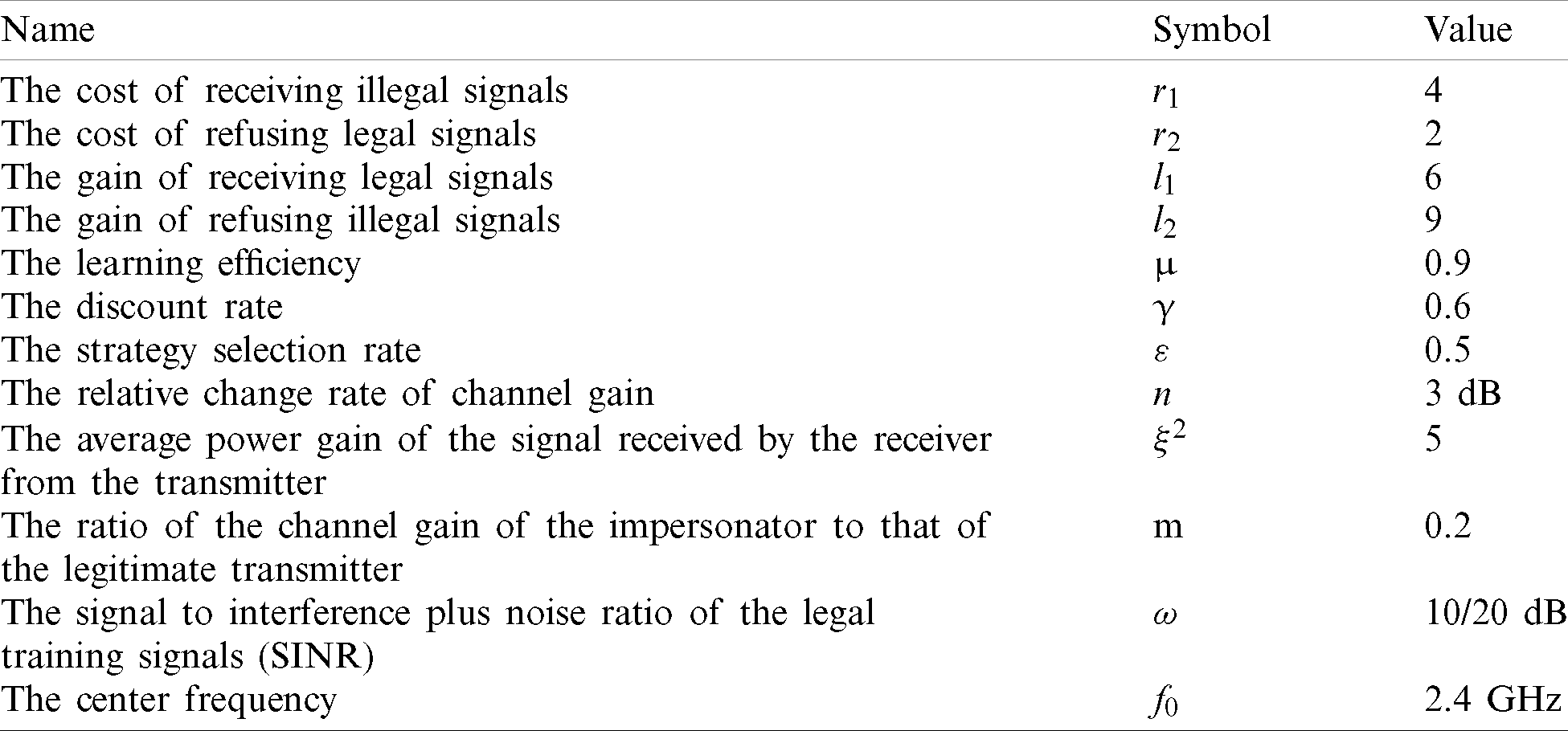
To improve the detection accuracy at the receiving end, we analyze the performance of the proposed method under the four indicators by changing the value of
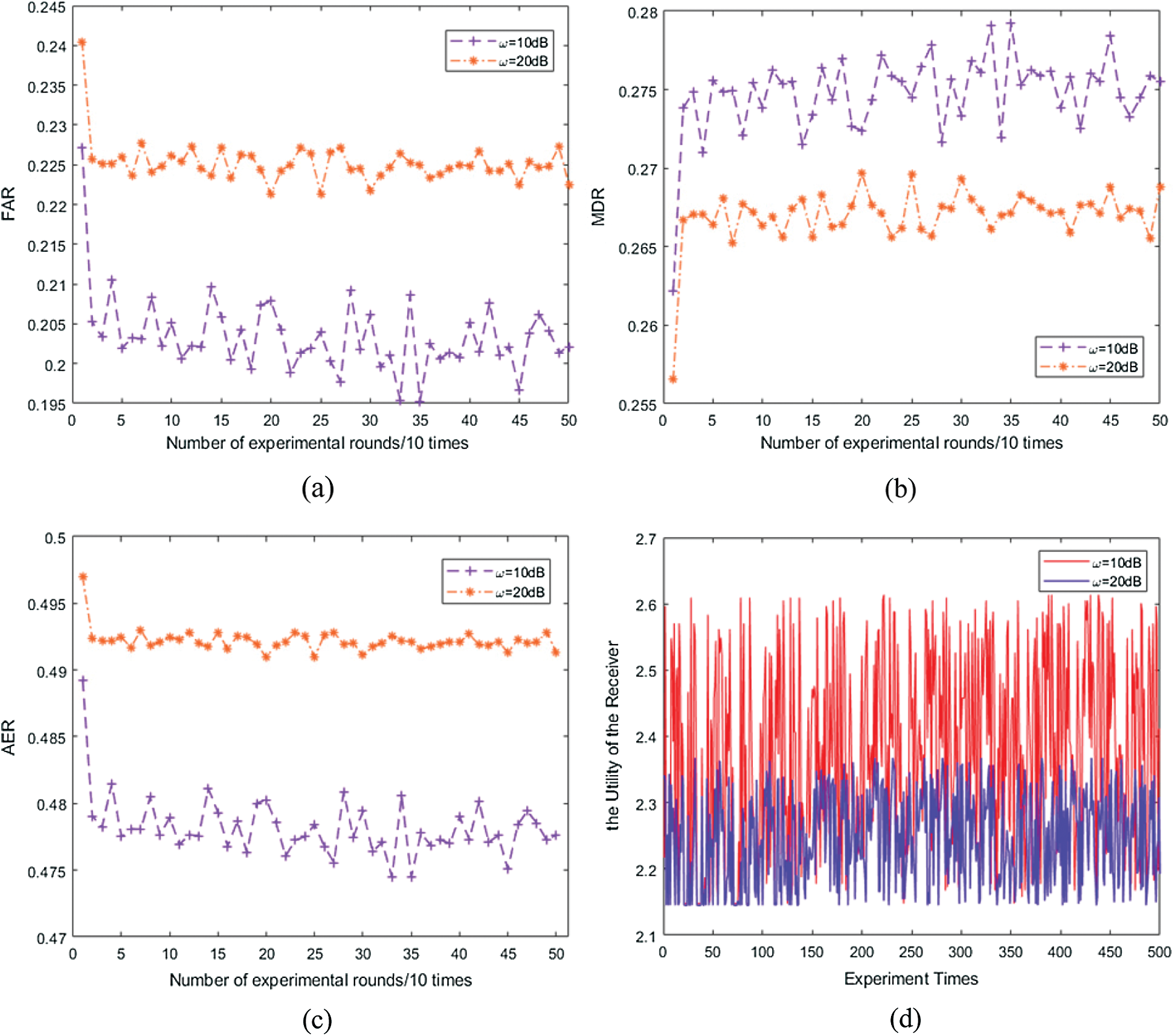
Figure 3: Average impersonation detection performance in the experiments. (a) False alarm rate (FAR). (b) Miss detection rate (MDR). (c) Average error rate (AER). (d) Utility of the receiver
In addition, as the detection error rate decreases correspondingly, the average utility of the receiver decreases with
Table 2: FAR, MDR, AER and the average utility with
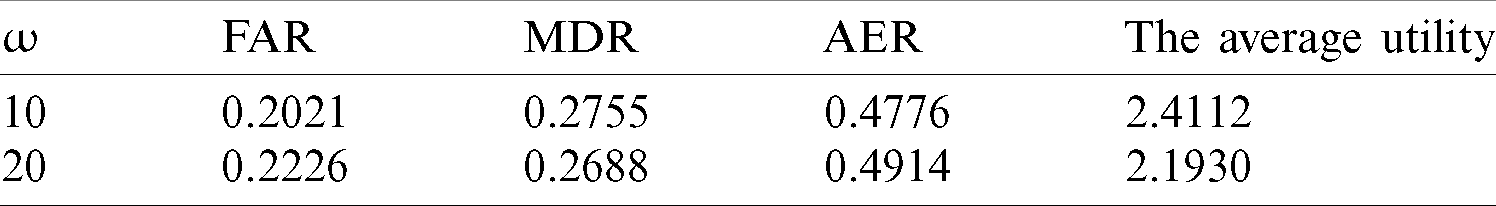
Fig. 4 depicts the comparison of FAR of three algorithms for 500 iterations. It can be seen that the FAR of these three algorithms reduces at the start. The proposed method gradually stabilizes after 100 iterations. As the iterations continue, the three methods are roughly kept within a constant range. The proposed method is stable at 20.0%–20.2%. Because the receiving end knows nothing about the channel and gradually gets understanding as the experiment goes on. The optimal
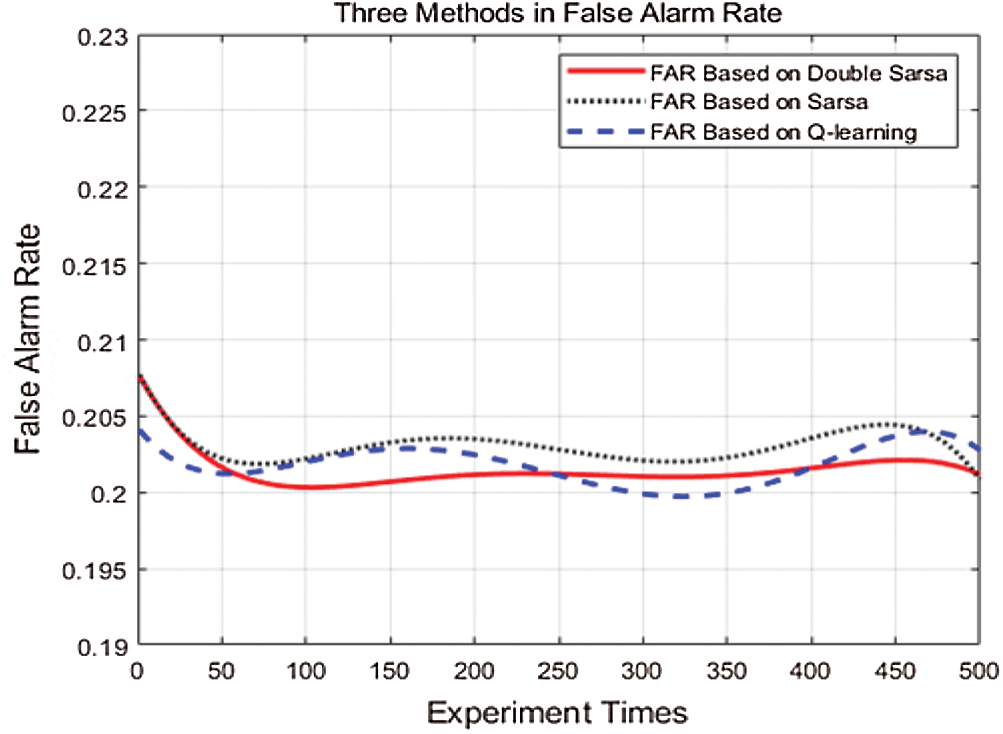
Figure 4: Comparison of double Sarsa, Sarsa, Q-learning for false alarm rate (FAR)
Fig. 5 describes the MDR of the three algorithms. Because the receiving end has no idea of the system details. The initial Q-table value is all zero, and the threshold at the beginning of the experiment is small. During continuous training, the threshold gradually increases. According to Eq. (7), the MDR value of three methods increases first. As the threshold reaches the optimum gradually, the change range of MDR value is getting smaller. Besides, the channel fading also affects the value, so it fluctuates slightly. The MDR of the proposed method is steady at about 27.6%, with the experiment is iterated 500 times. Compared with the Sarsa-based method, the MDR of the Double Sarsa-based method is decreased by 5.5% and by an average of 5.8% compared with the Q-learning-based method. Furthermore, Double Sarsa uses two Q-value tables to compensate for errors each other and prevent large changes in the threshold value, so it is more stable than the other two methods. The proposed method increases the probability of illegitimate signals being ignored so that the communication quality between fog nodes and end-users is improved.
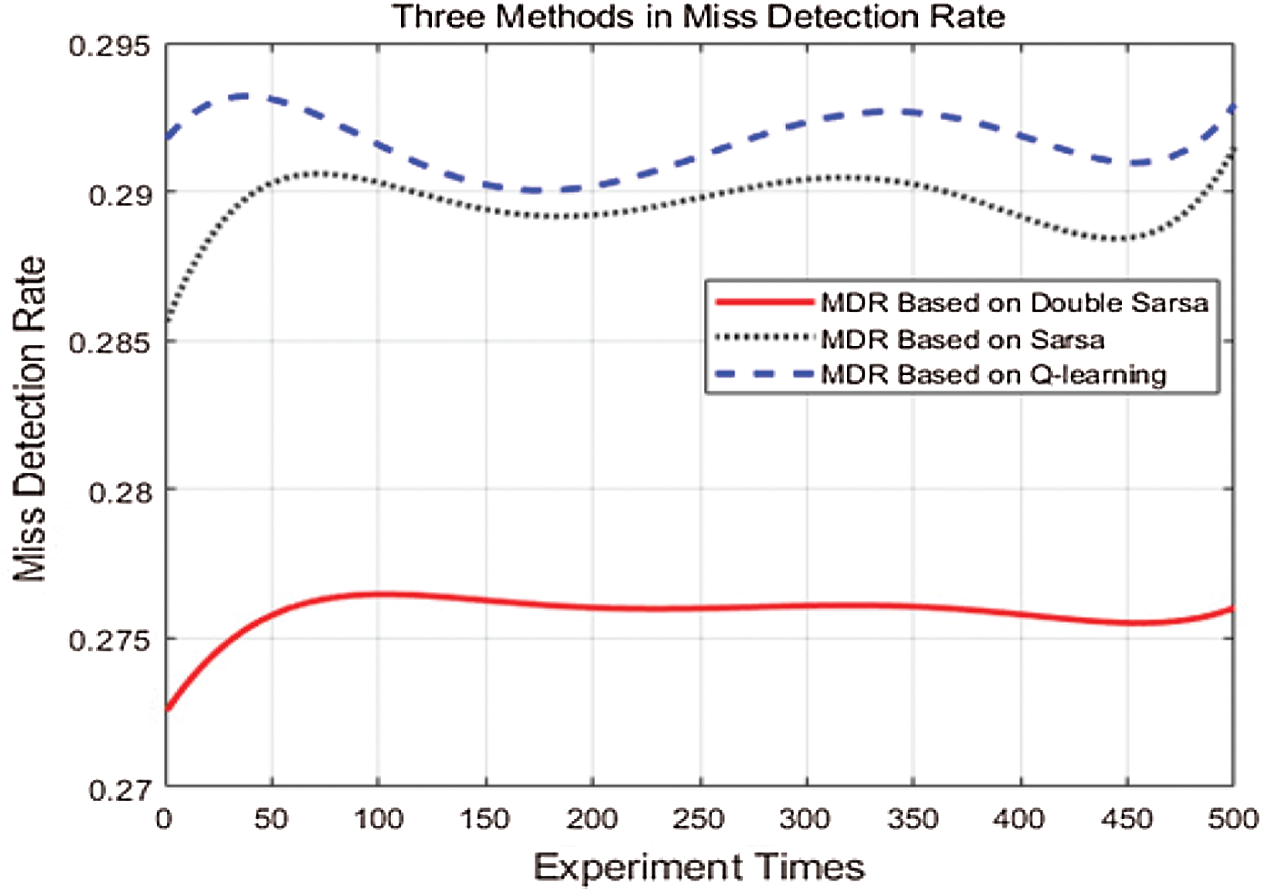
Figure 5: Comparison of double Sarsa, Sarsa, Q-learning for miss detection rate (MDR)
As shown in Fig. 6, we compare the average error rate of detection attacks under three algorithms. All three methods have a downward trend in the early period of the experiment and then stabilizes. This is because the receiver has a better understanding of the channel after receiving a large number of training signals and can use accumulated experience to choose the optimal threshold for detection. At the same time, the AER value eventually stabilizes at a constant within range for the channel’s characteristics. AER based on the Double Sarsa algorithm is lower than the other two algorithms. When the experiment is carried out 500 times, the AER of the proposed method is stable at about 47.72%, which is less than the Q-learning-based method by 3.0% and by 3.1% Sarsa-based method. In addition, our proposed method converges more slowly because two Q tables are used to update alternately. Therefore, considering the overall performance, the proposed method has lower FAR, MDR and AER, and it can detect attack behavior more accurately in balanced exploration and utilization, which can improve the security of FC.
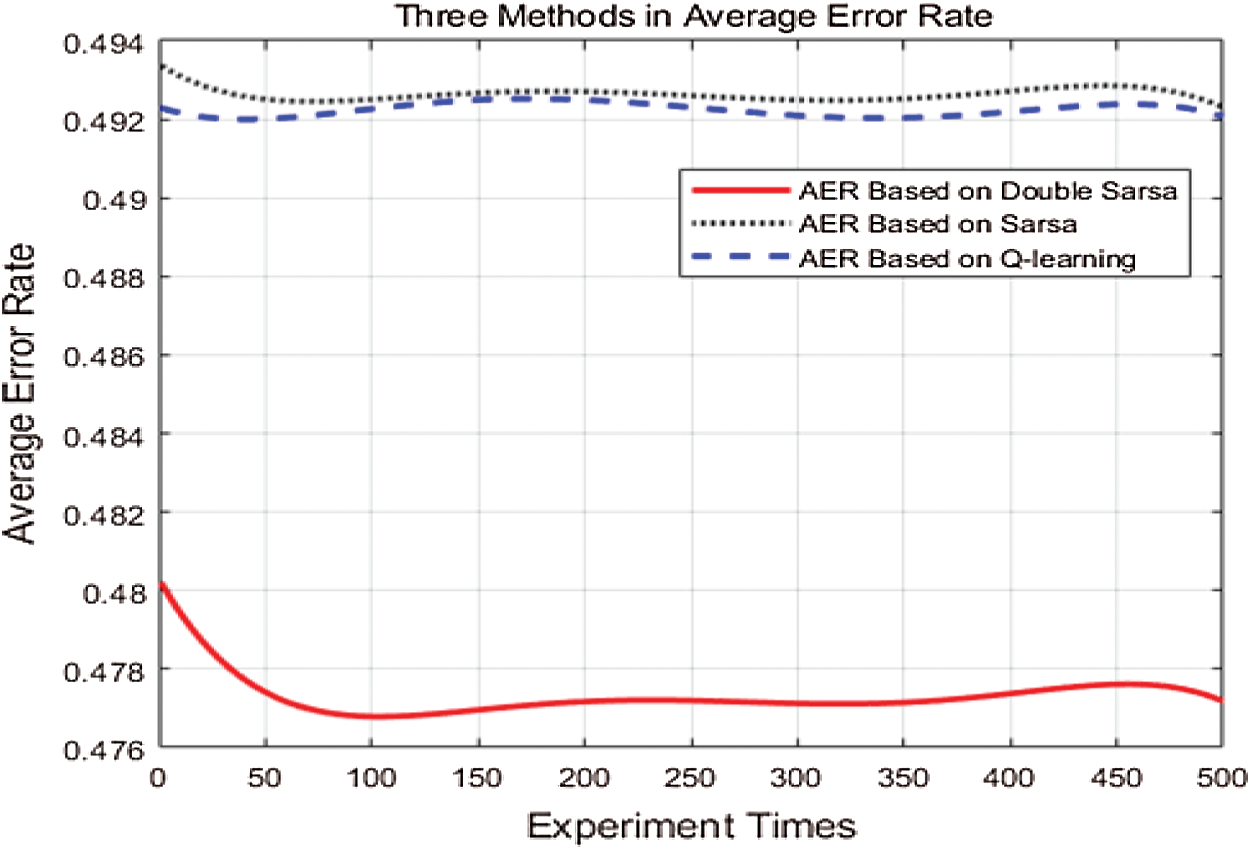
Figure 6: Comparison of double Sarsa, Sarsa, Q-learning for average error rate (AER)
In this paper, we proposed an impersonation attack detection method based on the Double Sarsa algorithm in FC. First, the impersonation attack model and the key generation model based on PLS are built. Then, the hypothesis test is established at the receiver. Next, the zero-sum game between illegitimate nodes and receivers is designed to calculate utility. Double Sarsa algorithm with reinforcement learning is used to choose the optimal test threshold to detect malicious users’ impersonation attacks. The experimental results illustrate that the proposed method can reduce the FAR, MDR, and AER. Comparing with the Sarsa algorithm and Q-learning algorithm, the performance gain of the proposed method is proved. The proposed method in this study can protect the FC environment more effectively. In the future, reinforcement learning and deep learning will be combined to study and solve the fog computing environment’s security problem.
Funding Statement: This work was supported by Natural Science Foundation of China (61801008), The China National Key R&D Program (No. 2018YFB0803600), Scientific Research Common Program of Beijing Municipal Commission of Education (No. KM201910005025) and Chinese Postdoctoral Science Foundation (No. 2020M670074).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. K. H. Abdulkareem, M. A. Mohammed, S. S. Gunasekaran, M. N. Al-Mhiqani, A. A. Mutlag et al. (2019). , “A review of fog computing and machine learning: Concepts, applications, challenges, and open issues,” IEEE Access, vol. 7, pp. 153123–153140. [Google Scholar]
2. L. Xu, C. Xu, Z. Liu, Y. Wang and J. Wang. (2019). “Enabling comparable search over encrypted data for IoT with privacy-preserving,” Computers, Materials & Continua, vol. 60, no. 2, pp. 675–690. [Google Scholar]
3. P. Bellavista, J. Berrocal, A. Corradi, S. K. Das, L. Foschini et al. (2019). , “A survey on fog computing for the internet of things,” Pervasive and Mobile Computing, vol. 52, pp. 71–99. [Google Scholar]
4. J. Ni, K. Zhang, X. Lin and X. S. Shen. (2017). “Securing fog computing for internet of things applications: Challenges and solutions,” IEEE Communications Surveys & Tutorials, vol. 20, no. 1, pp. 601–628. [Google Scholar]
5. M. De Donno, K. Tange and N. Dragoni. (2019). “Foundations and evolution of modern computing paradigms: Cloud, IoT, edge, and fog,” IEEE Access, vol. 7, pp. 150936–150948. [Google Scholar]
6. M. Waqas, Y. Niu, Y. Li, M. Ahmed, D. Jin et al. (2020). , “A comprehensive survey on mobility-aware D2D communications: Principles, practice and challenges,” IEEE Communications Surveys & Tutorials, vol. 22, no. 3, pp. 1863–1886. [Google Scholar]
7. N. Hassan, K. L. A. Yau and C. Wu. (2019). “Edge computing in 5G: A review,” IEEE Access, vol. 7, pp. 127276–127289. [Google Scholar]
8. D. Kim and S. Kim. (2020). “Network-aided intelligent traffic steering in 5G mobile networks,” Computers, Materials & Continua, vol. 65, no. 1, pp. 243–261. [Google Scholar]
9. K. Shaque, B. A. Khawaja, F. Sabir, S. Qazi and M. Mustaqim. (2020). “Internet of things (IoT) for next-generation smart systems: A review of current challenges, future trends and prospects for emerging 5G-IoT scenarios,” IEEE Access, vol. 8, pp. 23022–23040. [Google Scholar]
10. R. K. Naha, S. Garg, D. Georgakopoulos, P. P. Jayaraman, L. Gao et al. (2018). , “Fog computing: Survey of trends, architectures, requirements, and research directions,” IEEE Access, vol. 6, pp. 47980–48009. [Google Scholar]
11. Y. Wu, A. Khisti, C. Xiao, G. Caire, K. K. Wong et al. (2018). , “A survey of physical layer security techniques for 5G wireless networks and challenges ahead,” IEEE Journal on Selected Areas in Communications, vol. 36, no. 4, pp. 679–695. [Google Scholar]
12. N. Wang, P. Wang, A. Alipour-Fanid, L. Jiao and K. Zeng. (2019). “Physical layer security of 5G wireless networks for IoT: Challenges and opportunities,” IEEE Internet of Things Journal, vol. PP, no. 99, pp. 1. [Google Scholar]
13. H. Zhang, K. Zheng, X. Wang, S. Luo and B. Wu. (2020). “Strategy selection for moving target defense in incomplete information game,” Computers, Materials & Continua, vol. 62, no. 2, pp. 763–786. [Google Scholar]
14. M. Ganger, E. Duryea and W. Hu. (2019). “Double Sarsa and double expected Sarsa with shallow and deep learning,” Journal of Data Analysis and Information Processing, vol. 4, no. 4, pp. 159–176. [Google Scholar]
15. J. Zhang, T. Q. Duong, A. Marshall and R. Woods. (2016). “Key generation from wireless channels: A review,” IEEE Access, vol. 4, pp. 614–626. [Google Scholar]
16. Y. Peng, P. Wang, W. Xiang and Y. Li. (2017). “Secret key generation based on estimated channel state information for TDD-OFDM systems over fading channels,” IEEE Transactions on Wireless Communications, vol. 16, no. 8, pp. 5176–5186. [Google Scholar]
17. K. Moara-Nkwe, Q. Shi, G. M. Lee and M. H. Eiza. (2018). “A novel physical layer secure key generation and refreshment scheme for wireless sensor networks,” IEEE Access, vol. 6, pp. 11374–11387. [Google Scholar]
18. M. Waqas, M. Ahmed, Y. Li, D. Jin and S. Chen. (2018). “Social-aware secret key generation for secure device-to-device communication via trusted and non-trusted relays,” IEEE Transactions on Wireless Communications, vol. 17, no. 6, pp. 3918–3930. [Google Scholar]
19. Q. Huang, Y. Yang and L. Wang. (2017). “Secure data access control with ciphertext update and computation outsourcing in fog computing for internet of things,” IEEE Access, vol. 5, pp. 12941–12950. [Google Scholar]
20. N. Abbas, M. Asim, N. Tariq, T. Baker and S. Abbas. (2019). “A mechanism for securing IoT-enabled applications at the fog layer,” Journal of Sensor and Actuator Networks, vol. 8, no. 1, pp. 16. [Google Scholar]
21. T. Wang, J. Zhou, X. Chen, G. Wang, A. Liu et al. (2018). , “A three-layer privacy preserving cloud storage scheme based on computational intelligence in fog computing,” IEEE Transactions on Emerging Topics in Computational Intelligence, vol. 2, no. 1, pp. 3–12. [Google Scholar]
22. L. Xiao, Y. Li, G. Han, G. Liu and W. Zhuang. (2016). “PHY-layer spoofing detection with reinforcement learning in wireless networks,” IEEE Transactions on Vehicular Technology, vol. 65, no. 12, pp. 10037–10047. [Google Scholar]
23. S. Tu, M. Waqas, S. Rehman, M. Aamir, O. Rehman et al. (2018). , “Security in fog computing: A novel technique to tackle an impersonation attack,” IEEE Access, vol. 6, pp. 74993–75001. [Google Scholar]
24. J. Zhang, S. Rajendran, Z. Sun, R. Woods and L. Hanzo. (2020). “Physical layer security for the internet of things: Authentication and key generation,” IEEE Wireless Communications, vol. 26, no. 5, pp. 92–98. [Google Scholar]
25. N. Aldaghri and H. Mahdavifar. (2020). “Physical layer secret key generation in static environments,” IEEE Transactions on Information Forensics and Security, vol. 15, pp. 2692–2705. [Google Scholar]
26. J. R. Riehl and M. Cao. (2018). “A centrality-based security game for multihop networks,” IEEE Transactions on Control of Network Systems, vol. 5, no. 4, pp. 1507–1516. [Google Scholar]
27. Z. Ma and A. Leijon. (2011). “Bayesian estimation of beta mixture models with variational inference,” IEEE Transactions on Pattern Analysis & Machine Intelligence, vol. 33, no. 11, pp. 2160–2173. [Google Scholar]
28. H. Zhang, K. Zheng, X. Wang, S. Luo and B. Wu. (2020). “Strategy selection for moving target defense in incomplete information game,” Computers, Materials & Continua, vol. 62, no. 2, pp. 763–786. [Google Scholar]
29. M. Waqas, S. Tu, S. Rehman, Z. Halim, S. Anwar et al. (2020). , “Authentication of vehicles and road side units in intelligent transportation system,” Computers, Materials & Continua, vol. 64, no. 1, pp. 359–371. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |