DOI:10.32604/cmc.2021.016058

| Computers, Materials & Continua DOI:10.32604/cmc.2021.016058 |  |
| Article |
Systematic Analysis of Safety and Security Risks in Smart Homes
1Department of Accounting and Information Systems, College of Business and Economics, Qatar University, Doha, Qatar
2Department of Computer Science, University of Swabi, Swabi, Pakistan
3School of Software, University of Technology Sydney, Sydney, Australia
4Department of Finance & Economics, College of Business & Economics, Qatar University, Doha, Qatar
*Corresponding Author: Habib Ullah Khan. Email: habib.khan@qu.edu.qa
Received: 21 December 2020; Accepted: 11 February 2021
Abstract: The revolution in Internet of Things (IoT)-based devices and applications has provided smart applications for humans. These applications range from healthcare to traffic-flow management, to communication devices, to smart security devices, and many others. In particular, government and private organizations are showing significant interest in IoT-enabled applications for smart homes. Despite the perceived benefits and interest, human safety is also a key concern. This research is aimed at systematically analyzing the available literature on smart homes and identifying areas of concern or risk with a view to supporting the design of safe and secure smart homes. For this systematic review process, relevant work in the most highly regarded journals published in the period 2016–2020 (a section of 2020 is included) was analyzed. A final set of 99 relevant articles (journal articles, book sections, conference papers, and survey papers) was analyzed in this study. This analysis is focused on three research questions and relevant keywords. The systematic analysis results and key insights will help researchers and practitioners to make more informed decisions when dealing with the safety and security risks of smart homes, especially in emergency situations.
Keywords: Smart buildings; IoT; smart homes; systematic literature review; prototype model
During the last decade, Internet of Things (IoT)-enabled smart applications have been increasingly integrated into our daily life and related activities, e.g., healthcare, home, manufacturing, and transportation [1]. These applications are connected through the Internet to enhance and facilitate the way we live, work, and play [2]. The IoT-enabled smart home is one of the important areas discussed in this paper [2]. A smart home has technologies that facilitate sensing and monitoring of people and home appliances. In short, smart homes are used to monitor and control home-facing operations and their continuous adaptation. In the last few years, concepts from smart homes have been applied to other areas, such as smart healthcare systems [3], energy systems [4], security and emergency management systems [5], and comfort and entertainment systems [6].
A smart living environment’s automatic transformation mechanism is controlled by the arguing system, which is considered the brain of the smart living architectures. The smart home arguing system (SHAS) is used to make accurate decisions ensuring the security, safety, and comfort of the inhabitants and their surroundings. Keeping this in mind, researchers have intensively explored and studied multiple artificial intelligence (AI)-based systems and their uses for ambient-assisted living (AAL) systems. However, no systematic mechanism has been proposed that investigates the decision support systems (DSS) incorporated in smart living environments. Chan et al. [7] and Calvaresi et al. [8] reviewed smart living environments. Others, including Zaidan et al. [9] and Brand et al. [10], studied smart homes from single application domain perspectives, such as IoT-based communication components, and privacy concerns of IoT components in living environments. Furthermore, Wilson et al. [11] reported on smart home residents and their uses of the underlying infrastructure from socio-technical perspectives. To the best of our knowledge, there is a lack of comprehensive systematic literature review of the current context of human safety and security in smart homes.
In this paper, a systematic literature review (SLR) is presented that examines the aforementioned domain of smart homes from the following perspectives:
• Determine the main goal of smart living systems;
• Deliver new understanding and new knowledge about human safety in a rapidly evolving smart built environment;
• Identify and characterize the key features and requirements of smart living to ensure safety and security during emergencies;
• Catalogue the tools and features that provide the abilities to monitor, collect, and process real-time human sensors, and build data for efficient and effective decision making.
The rest of this paper is organized as follows. In Section 2, the proposed SLR process adapted for literature search and analysis is described. SLR results are reported and discussed in Section 3. The limitations of the proposed research work are outlined in Section 4, followed by conclusions and directions of planned future work in Section 5.
SLR is a well-known process used to identify and evaluate available research work relevant to a particular subject or event of interest. SLR aims to present a fair evaluation of a particular research topic using a rigorous, trustworthy, and auditable methodology [12]. SLR studies are reported in many fields, e.g., networking PMIPV6 domains [13] and healthcare Big Data analytics [14]. The main reasons for performing a SLR are the following:
• To explore and summarize the existing research work on a particular technology;
• To find the gaps in the available technology that will ultimately lead to future investigations.
In the proposed research work, the SLR process is conducted by following the guidelines suggested by Kitchenham et al. [15,16]. The proposed review process protocol is depicted in Fig. 1 and consists of three main phases: (1) planning the review process, (2) performing the review process, and (3) reporting the results of the review process. All these steps are illustrated in detail in Fig. 1.
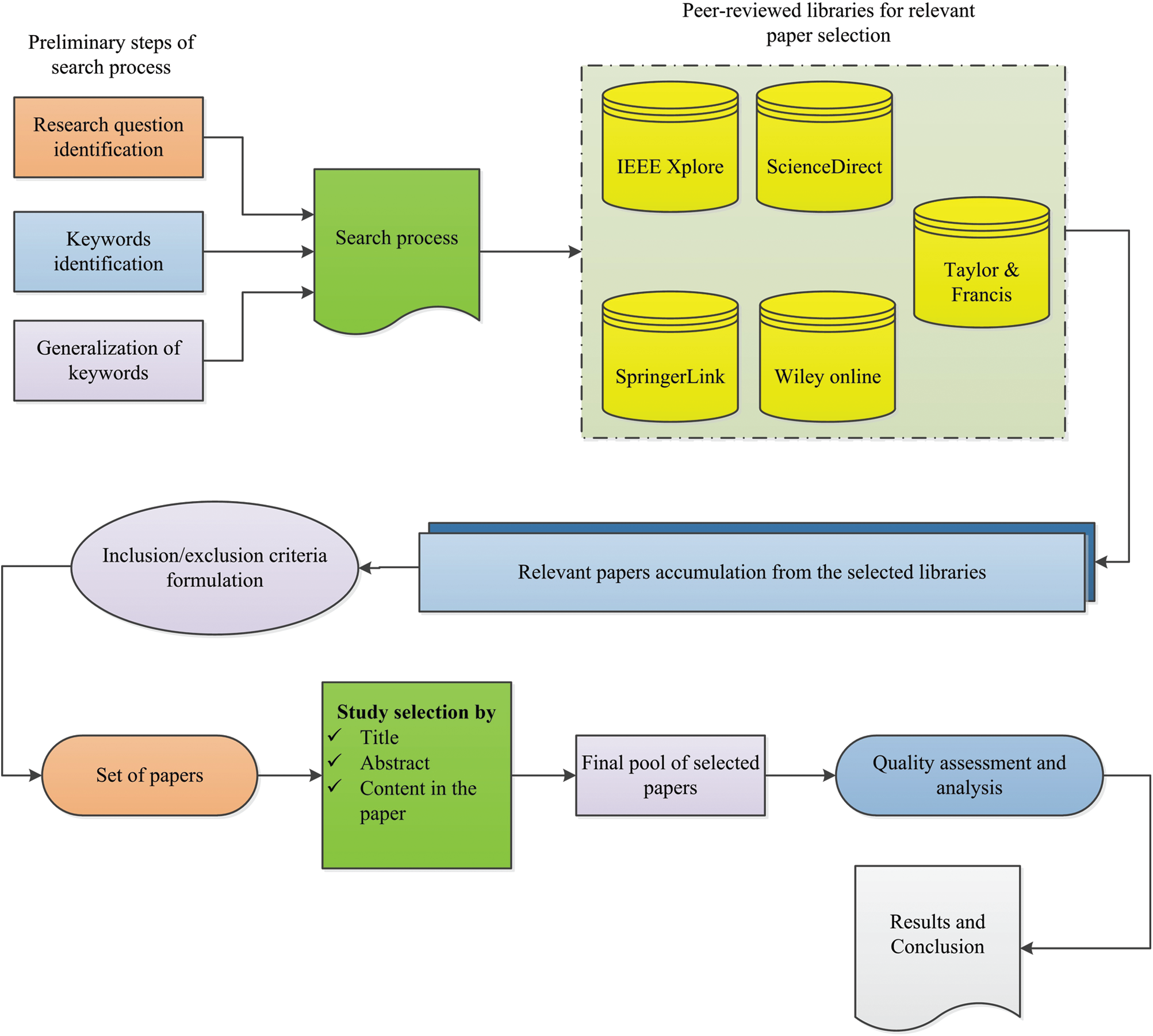
Figure 1: Research protocol of the proposed SLR work
The proposed systematic review process is performed using the guidelines provided by Kitchenham [16,17]. Based on these guidelines, researchers must explore the existing evidence on a topic of interest and determine the need for a review process. Furthermore, the study outlines the key pre-review activities: formulation of the research questions, identification of the keywords and query formulation, selection of the peer-reviewed online digital libraries for the accumulation of the relevant primary articles for the review process, and the inclusion/exclusion criteria. Accordingly, the present systematic review was performed due to recent increasing research interest in smart homes and living environments. It is noted that there is a lack of systematic literature review study in the specific context of smart home safety and security risks, particularly during emergency situations.
2.1.1 Research Question Formulation
As discussed earlier, research question formulation is an essential activity in conducting a SLR. For defining the most relevant research questions, the Goal-Questions-Metrics approach of Van Solingen et al. [18] was followed, and, consequently, the three research questions given in Tab. 1 were formulated.
2.1.2 Identification of Keywords and Query Formulation
After formulating the research questions, the next and most important activity of the SLR was to identify keywords and formulate a search query to systematically select the most relevant articles from the selected online digital libraries. Keywords and the search query are shown in Tab. 2.
Table 2: Keywords and query for search process

2.1.3 Online Digital Library Selection
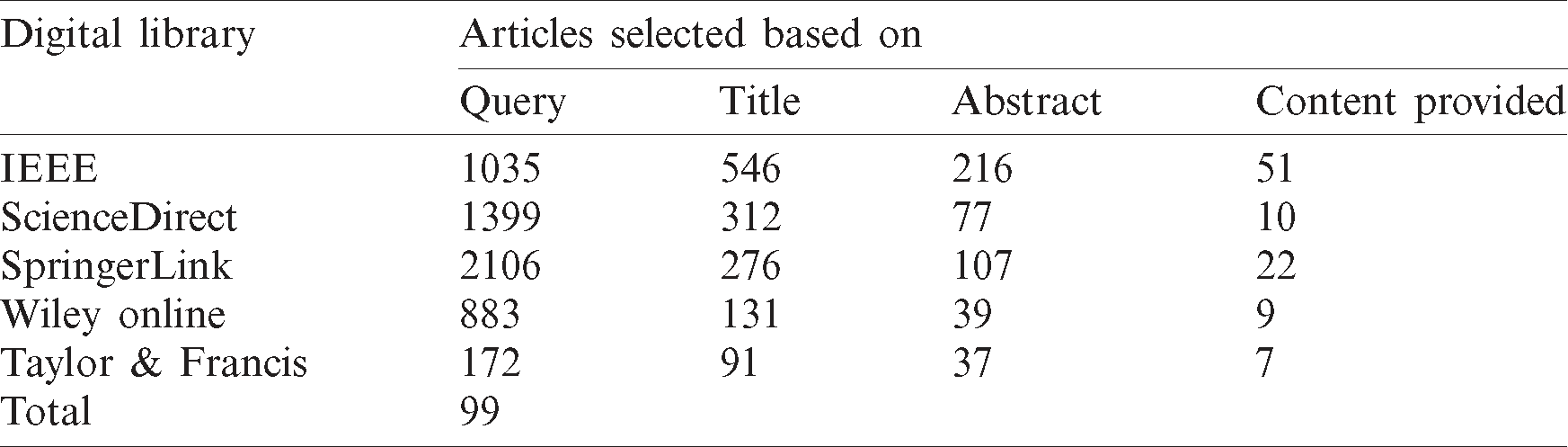
The five well-known online digital libraries shown in Tab. 3 were selected to identify relevant research.
Table 3: Online digital libraries selected for article accumulation

The primary articles were selected and downloaded from these digital libraries based on the defined query. After downloading, these papers were further analyzed and explored to remove the redundant and irrelevant papers, if any. Irrelevant papers, i.e., those that did discuss smart buildings or smart homes, were removed. The finalized primary articles were then merged into a single set or directory. These are the papers that address at least one of the research questions. In summary, 99 research articles were selected as most relevant primary research articles for the purpose of the present SLR study.
2.1.4 Inclusion/Exclusion Criteria
Defining inclusion/exclusion criteria is the most challenging job in a SLR research process. As the main activity of the process, it ensures the selection of the most relevant primary articles for the final pool of papers for further quality assessment. Tab. 4 presents the inclusion/exclusion criteria of the primary studies relevant to the aforementioned proposed research questions.
Table 4: Inclusion/exclusion criteria

The selected primary research articles were thoroughly checked and analyzed by all the authors to ensure research validity and avoid any possible omission. Significant attention is given to the last three questions, which are defined for the inclusion of a paper in this study. A voting mechanism was considered for this step. If more than half of the authors agreed to the inclusion of the paper, then the paper was added to the final set of the most relevant articles; otherwise, the paper was excluded. This voting mechanism is based on the paper’s title, abstract, and contents presented in the research article itself. A summary of the overall inclusion process is shown in Tab. 5. A final pool of 99 relevant primary articles was selected for the assessment process.
Table 5: Selection of the primary studies for final pool
After performing the preliminary steps of selecting the online digital libraries, identifying research questions, selecting keywords, and determining inclusion/exclusion criteria, the next phase was to perform the review using the research protocol selected as shown in Fig. 1. This activity includes defining final pool selection, data synthesis, monitoring, and quality assessment processes. All of these steps are discussed in detail in the following subsections.
2.3 Final Pool of Relevant Articles
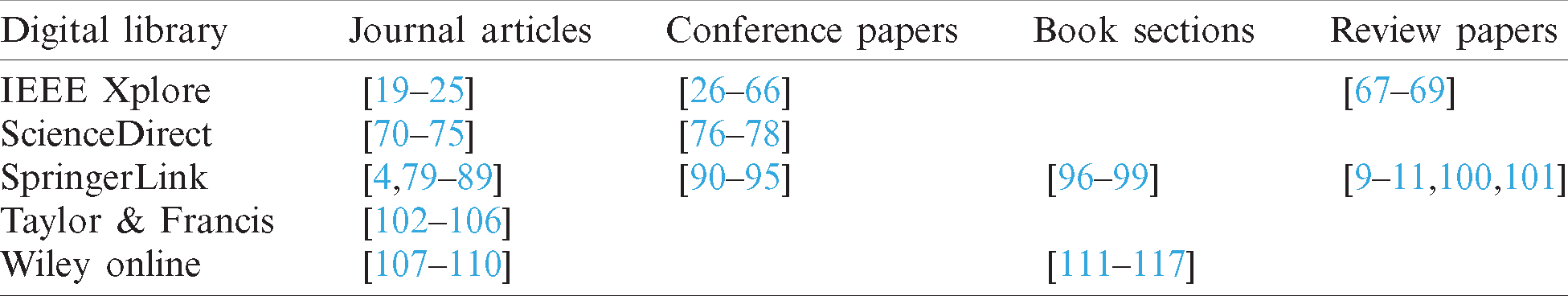
After sorting the selected digital libraries for the relevant primary articles and performing the inclusion/exclusion process, a final set of 99 relevant articles were selected for SLR. The final pool of papers includes workshop papers, conference proceedings, book sections, journal articles, and review/survey articles. Tab. 6 presents details of the selected finalized pool of research articles.
Table 6: Evolution of final set of relevant papers
The mapping of paper sources is shown in Fig. 2, from which it is concluded that IEEE Xplore contains more papers when compared to other sources. This may reflect the interest of researchers to publish their research work in IEEE Xplore.
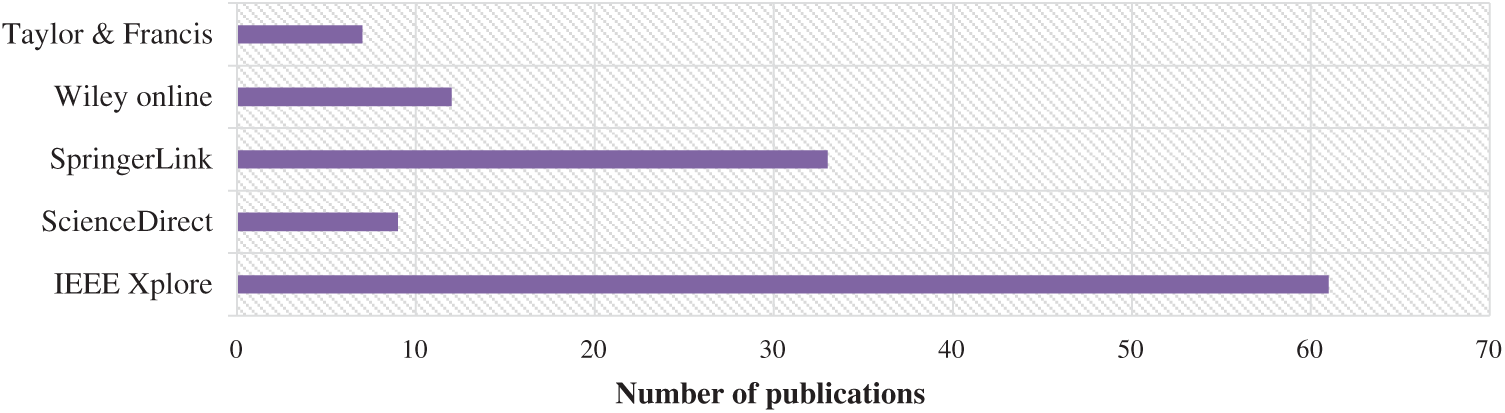
Figure 2: Contribution of each library in the final set of relevant papers
The final paper set was also sorted based on year and publication sources. It is observed that the number of publications increases with the passage of time, which may reflect the growing interest among the research community in the proposed area of research. Fig. 3 shows the sorting results.
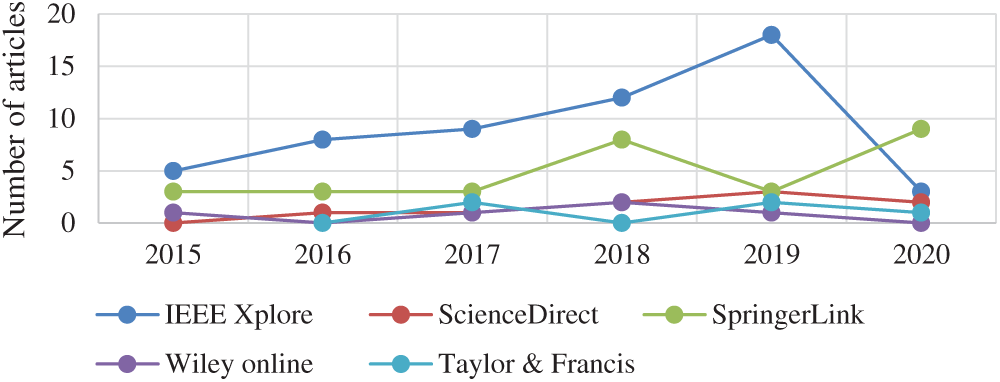
Figure 3: The Sorting Results
Furthermore, the final set of relevant papers was sorted based on digital library, reference list, type of paper, and publication year, as depicted in Fig. 4. In the figure, the outer shell represents the references to the primary articles, the medium shell the paper type, and the most-inner-shell date of publication.
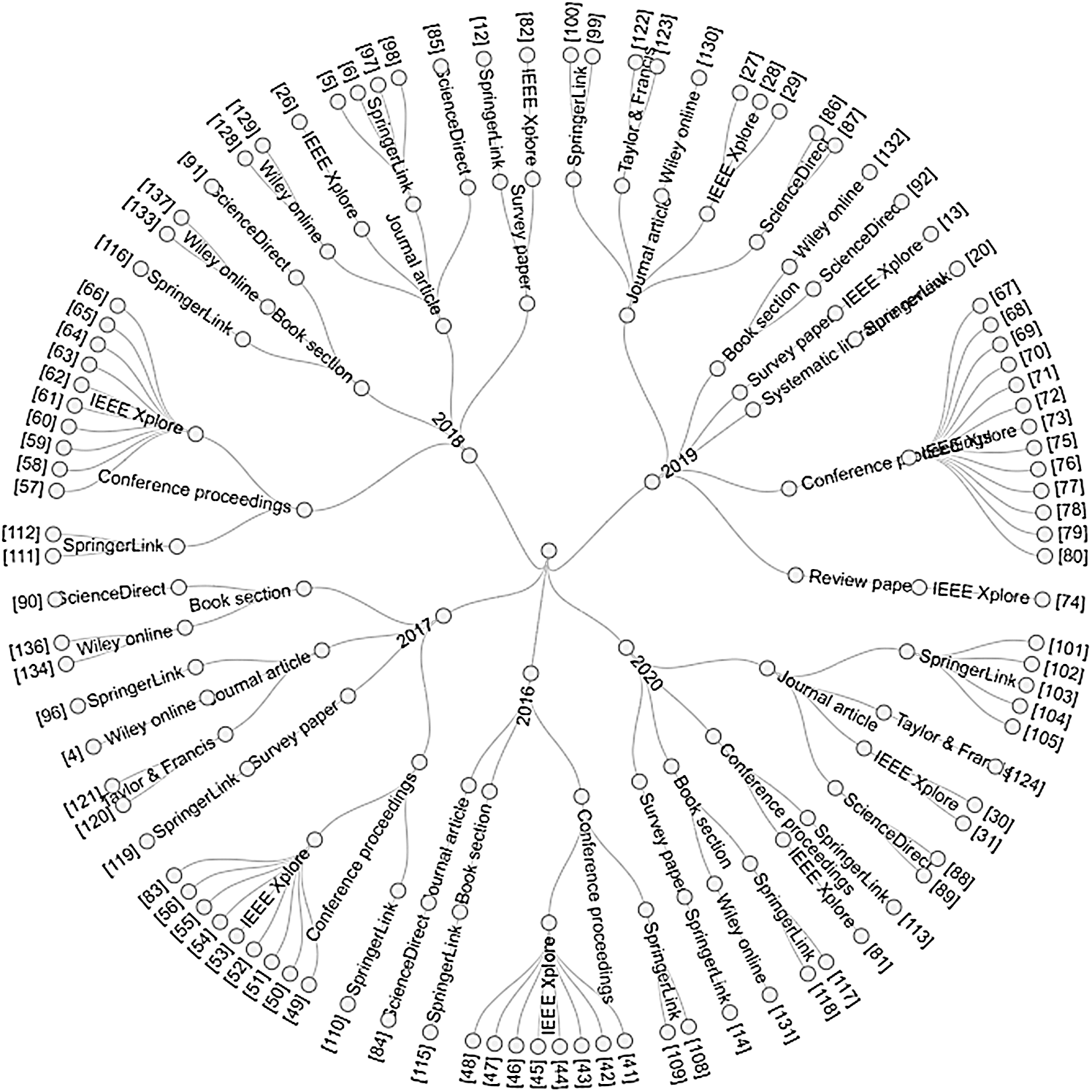
Figure 4: Evolution of the final selected papers
The quality of the selected relevant articles was assessed using the criteria defined in the SLR protocol. The set of relevant articles was reviewed and assessed against each of the research questions and corresponding criteria (QC) listed in Tab. 7.
Table 7: Quality criteria for assessment process

This assessment ensured the quality of each selected paper for SLR. Furthermore, weights were assigned to all research questions based on the following criteria:
• 0 if a paper has no information for the selected research question;
• 0.5 if a paper has a piece of partial but satisfactory information about a research question;
• 1 if a paper contains a full and complete description for the research question.
After performing the quality assessment, the most relevant articles were determined, as shown in Fig. 5.
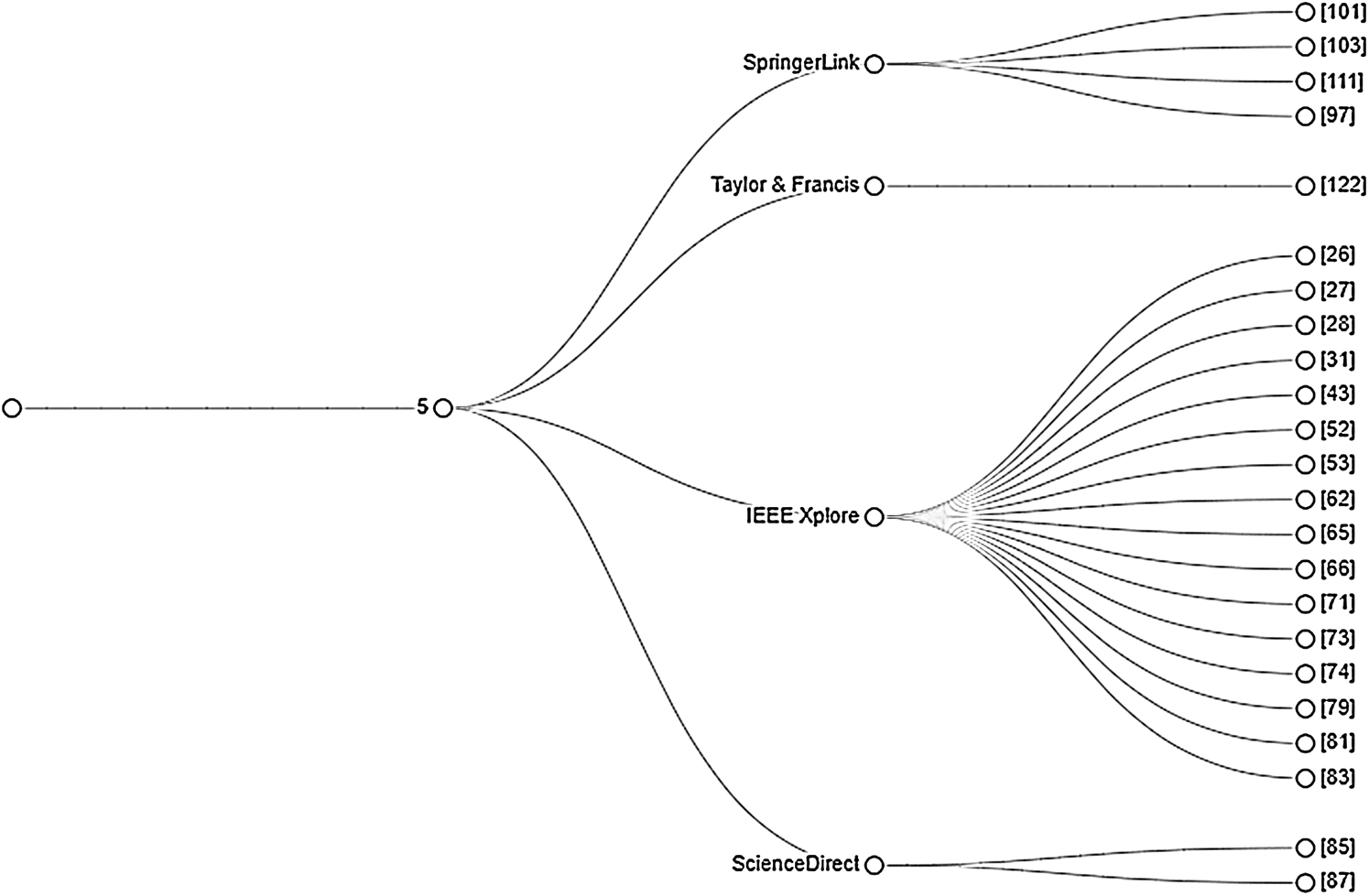
Figure 5: Most relevant research articles
Each subsection below provides details of each related research question formulated for the present SLR research work.
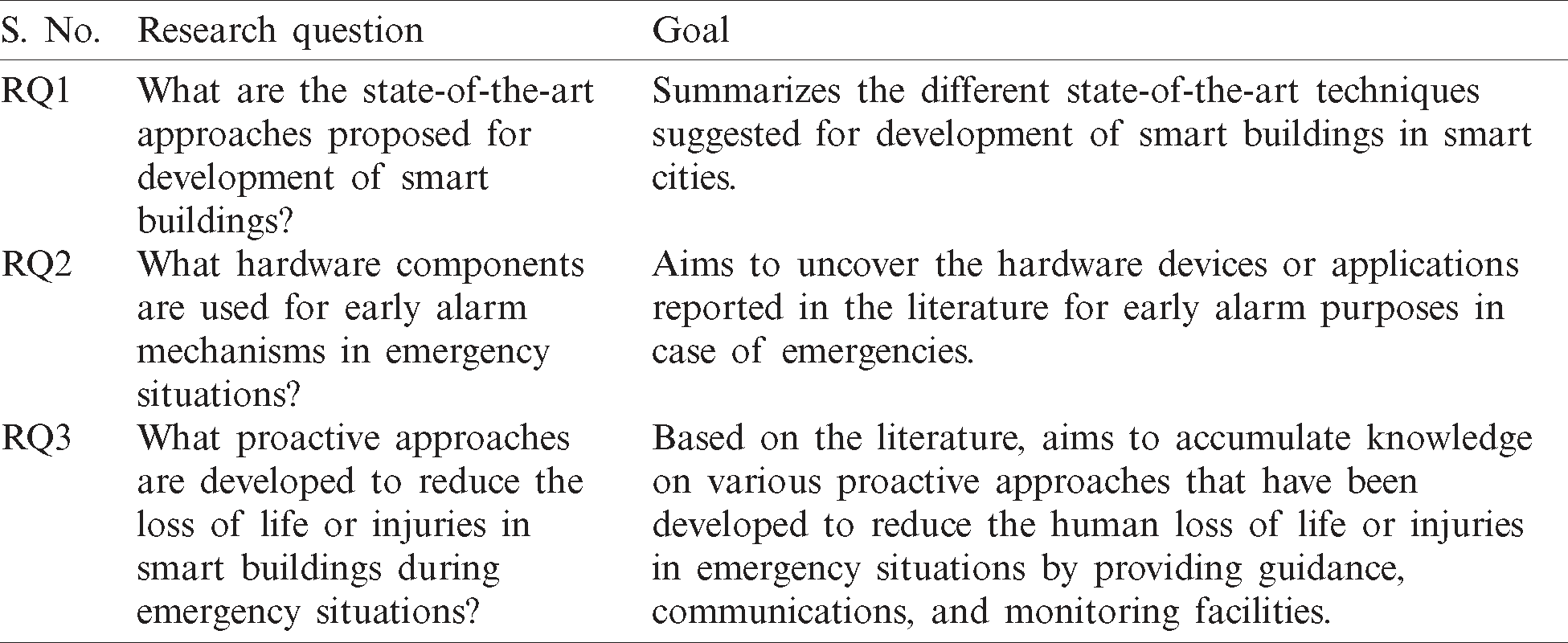
3.1 RQ1-What are State-of-the-Art Approaches Proposed for Development of Smart Buildings?
Responses to this question were used to synthesize the literature from 2016 to 2020 in which the approaches for developing smart building architectures were discussed. Tab. 8 outlines the different approaches proposed for smart building architectures.
Table 8: List of approaches proposed for smart building architectures
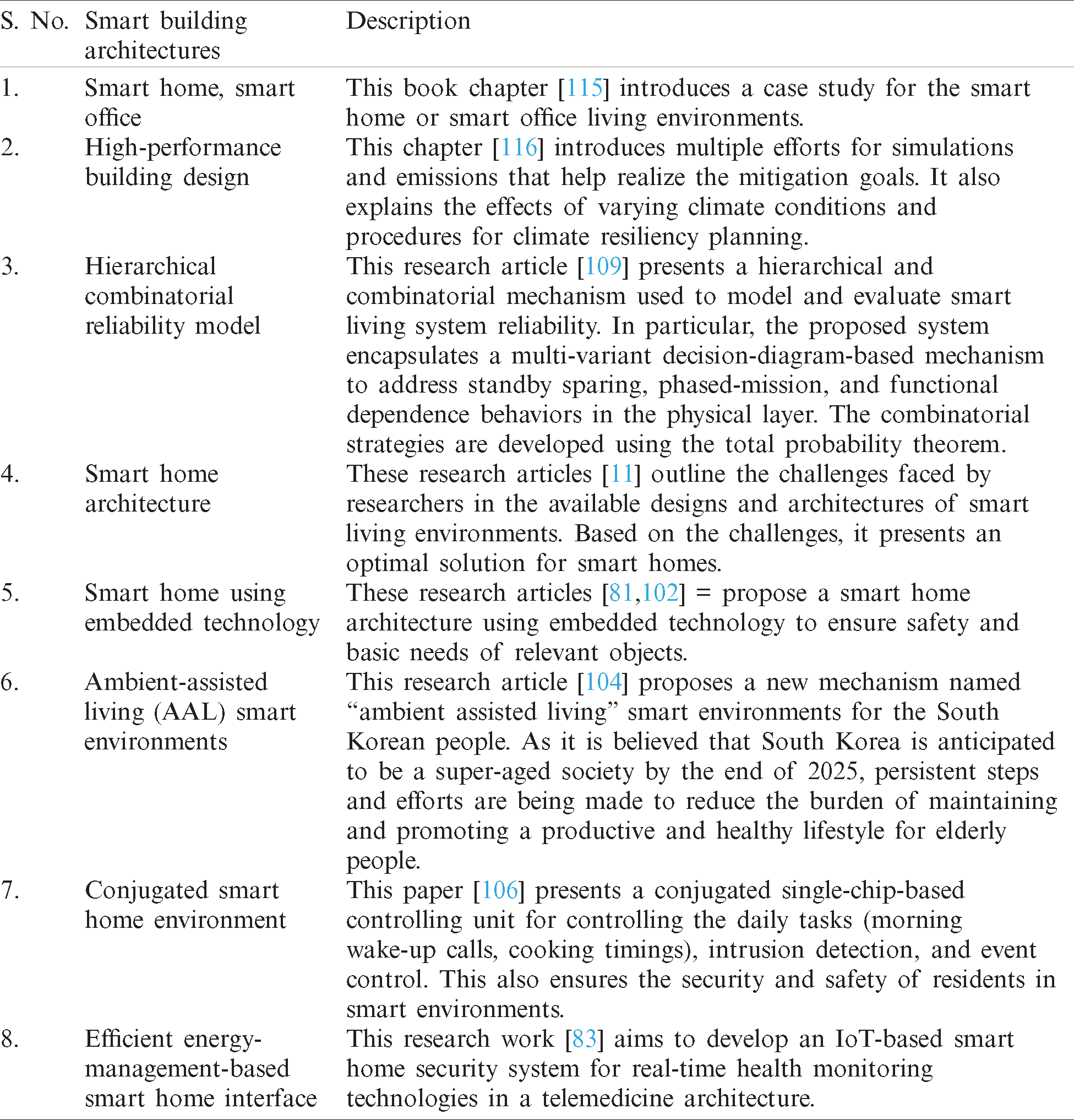
3.2 RQ2-What Hardware Components are Used for Early Alarm Mechanism in Emergency Situations?
Smart homes or smart living environments are developed to facilitate living with high standards and resiliency in normal and emergency situations. Tab. 9 lists multiple hardware devices or applications that are proposed for early alarm purposes during emergency situations.
Table 9: List of hardware components used for early alarm purposes

3.3 RQ3-What Proactive Approaches are Developed to Reduce Loss of Life or Injuries in Smart Buildings During Emergency Situations?
Smart living environments have been developed to ensure human healthcare and security, but concerns or emergency situations exist that must be addressed, such as short circuits, other fire issues, and earthquakes, that may adversely impact smart living environments. The present SLR study uncovered a number of approaches, which are listed in Tab. 10.
Table 10: List of proactive approaches to counter emergency situations

The limitations of the proposed research work are the following.
• Only five digital libraries were selected for SLR. However, these libraries provide broader coverage for peer-reviewed and high-quality research articles.
• A specific range of years (2016–2020 (a portion of 2020 was included in the review process) was selected for SLR. This was done to ensure the inclusion of recent trends and studies relevant to the current context of smart homes. This is also important to set the further research options based on the recent work reported in the present study.
• Google Scholar is another informal source of literature and was thus omitted from the present SLR since the focus was on the systematic selection of only peer-reviewed articles.
• Papers that contain the word “smart home” in their title were excluded, but their contents were not meaningful or relevant to the research questions posed. In other words, papers only containing definitions were omitted from the present study.
During the past decade, IoT devices have provided state-of-the-art and smart applications for humans. These applications range from smart urban management to smart transportation management devices, smart healthcare devices, smart electrical and home devices, and many others. One of the most inspiring applications is smart homes that aim to support contemporary human living needs. Among the major concerns and challenges of researchers are the security and safety of smart homes. Embedding security in IoT-based applications has been identified as an opportunity to realize the vision of smart and energy-efficient homes and buildings. To address this problem, a SLR was performed to investigate the available literature published in the period 2016–2020 (a portion of 2020 was included in the systematic mapping). This was achieved using the SLR guidelines provided by Kitchenham [16,17].
Five different peer-reviewed online digital libraries were used for sourcing primary research articles. A total of 99 relevant articles (journal articles, book sections, conference proceedings, and survey papers) were identified for analysis and assessment purposes. This systematic synthesis and analysis of the existing research work will serve as a knowledgebase for researchers and designers interested in designing safe and secure smart homes of the future. Furthermore, the results from this SLR will inform the community about recent research trends in smart homes, which are important for formulating future research options.
Acknowledgement: This publication was supported by Qatar University Internal Grant No. IRCC-2020-009. The findings achieved herein are solely the responsibility of the authors.
Funding Statement: The author(s) received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. S. Naoui, M. E. Elhdhili and L. A. Saidane. (2019). “Lightweight and secure password based smart home authentication protocol: LSP-SHAP,” Journal of Network and Systems Management, vol. 27, no. 4, pp. 1020–1042. [Google Scholar]
2. G. Lindsay, B. Woods and J. Corman. (2016). Smart Homes and the Internet of Things, Washington, D.C., United States: Atlantic Council. [Google Scholar]
3. N. Falcionelli, P. Sernani, A. Brugués, D. N. Mekuria, D. Calvaresi et al. (2019). , “Indexing the event calculus: Towards practical human-readable personal health systems,” Artificial Intelligence in Medicine, vol. 96, no. 4, pp. 154–166. [Google Scholar]
4. J. Yu, N. Lee, C. S. Pyo and Y. S. Lee. (2018). “WISE: Web of object architecture on IoT environment for smart home and building energy management,” Journal of Supercomputing, vol. 74, no. 9, pp. 4403–4418. [Google Scholar]
5. M. Schneps-Schneppe, A. Maximenko, D. Namiot and D. Malov. (2012). “Wired smart home: Energy metering, security, and emergency issues,” in 2012 IV Int. Congress on Ultra Modern Telecommunications and Control Systems, St. Petersburg, Russia, pp. 405–410, . https://doi.org/10.1109/ICUMT.2012. 6459700. [Google Scholar]
6. J. R. Velasco, I. Marsá-Maestre, A. Navarro, M. A. López-Carmona and A. J. de Vicente et al. (2005). , “Location-aware services and interfaces in smart homes using multiagent systems,” PSC, vol. 5, pp. 104–110. [Google Scholar]
7. M. Chan, D. Estève, C. Escriba and E. Campo. (2008). “A review of smart homes—Present state and future challenges,” Computer Methods and Programs in Biomedicine, vol. 91, pp. 55–81. [Google Scholar]
8. D. Calvaresi, D. Cesarini, P. Sernani, M. Marinoni, A. F. Dragoni et al. (2017). , “Exploring the ambient assisted living domain: A systematic review,” Journal of Ambient Intelligence and Humanized Computing, vol. 8, no. 2, pp. 239–257. [Google Scholar]
9. A. A. Zaidan, B. B. Zaidan, M. Y. Qahtan, O. S. Albahri, A. S. Albahri et al. (2018). , “A survey on communication components for IoT-based technologies in smart homes,” Telecommunication Systems, vol. 69, no. 1, pp. 1–25. [Google Scholar]
10. D. Brand, F. D. DiGennaro Reed, M. D. Morley, T. G. Erath and M. D. Novak. (2020). “A survey Assessing privacy concerns of smart-home services provided to individuals with disabilities,” Behavior Analysis in Practice, vol. 13, no. 1, pp. 11–21. [Google Scholar]
11. C. Wilson, T. Hargreaves and R. Hauxwell-Baldwin. (2015). “Smart homes and their users: A systematic analysis and key challenges,” Personal and Ubiquitous Computing, vol. 19, no. 2, pp. 463–476. [Google Scholar]
12. B. Kitchenham. (2004). “Procedures for performing systematic reviews,” Keele, UK: Keele University, vol. 33, pp. 1–26. [Google Scholar]
13. A. Hussain, S. Nazir, S. Khan and A. Ullah. (2020). “Analysis of PMIPv6 extensions for identifying and assessing the efforts made for solving the issues in the PMIPv6 domain: A systematic review,” Computer Networks, vol. 179, pp. 107366. [Google Scholar]
14. S. Nazir, S. Khan, H. U. Khan, S. Ali, I. García-Magariño et al. (2020). , “A comprehensive analysis of healthcare big data management, analytics and scientific programming,” IEEE Access, vol. 8, pp. 95714–95733. [Google Scholar]
15. S. Keele. (2007). “Guidelines for performing systematic literature reviews in software engineering,” Technical Report, Ver. 2.3 EBSE Technical Report. [Google Scholar]
16. B. Kitchenham, R. Pretorius, D. Budgen, O. P. Brereton, M. Turner et al. (2010). , “Systematic literature reviews in software engineering---A tertiary study,” Information and Software Technology, vol. 52, no. 8, pp. 792–805. [Google Scholar]
17. B. Kitchenham and S. Charters. (2007). “Guidelines for performing systematic literaturereviews in software engineering,” in Evidence-Based Software Engineering, Boca Raton, Florida: Chapman & Hall/CRC. [Google Scholar]
18. R. Van Solingen, V. Basili, G. Caldiera and H. D. Rombach. (2002). “Goal question metric (GQM) approach,” Encyclopedia of Software Engineering, vol. SE-14, pp. 758. [Google Scholar]
19. S. Ntalampiras, I. Potamitis and N. Fakotakis. (2011). “Probabilistic novelty detection for acoustic surveillance under real-world conditions,” IEEE Transactions on Multimedia, vol. 13, no. 4, pp. 713–719. [Google Scholar]
20. S. Chiou and Z. Liao. (2018). “A real-time, automated and privacy-preserving mobile emergency-medical-service network for informing the closest rescuer to rapidly support mobile-emergency-call victims,” IEEE Access, vol. 6, pp. 35787–35800. [Google Scholar]
21. S. Khatoon, S. M. M. Rahman, M. Alrubaian and A. Alamri. (2019). “Privacy-preserved, provable secure, mutually authenticated key agreement protocol for healthcare in a smart city environment,” IEEE Access, vol. 7, pp. 47962–47971. [Google Scholar]
22. S. A. Shah, D. Z. Seker, M. M. Rathore, S. Hameed, S. B. Yahia et al. (2019). , “Towards disaster resilient smart cities: Can internet of things and big data analytics be the game changers?,” IEEE Access, vol. 7, pp. 91885–91903. [Google Scholar]
23. D. Shin, K. Yun, J. Kim, P. V. Astillo, J. Kim et al. (2019). , “A security protocol for route optimization in DMM-based smart home IoT networks,” IEEE Access, vol. 7, pp. 142531–142550. [Google Scholar]
24. X. Luo, L. Yin, C. Li, C. Wang, F. Fang et al. (2020). , “A lightweight privacy-preserving communication protocol for heterogeneous IoT environment,” IEEE Access, vol. 8, pp. 67192–67204. [Google Scholar]
25. M. Wazid, A. K. Das, V. Odelu, N. Kumar and W. Susilo. (2020). “Secure remote user authenticated key establishment protocol for smart home environment,” IEEE Transactions on Dependable and Secure Computing, vol. 17, no. 2, pp. 391–406. [Google Scholar]
26. R. Aburukba, A. R. Al-Ali, N. Kandil and D. AbuDamis. (2016). “Configurable ZigBee-based control system for people with multiple disabilities in smart homes,” in 2016 Int. Conf. on Industrial Informatics and Computer Systems, Sharjah, United Arab Emirates, pp. 1–5, . https://doi.org/10.1109/ICCSII.2016.7462435. [Google Scholar]
27. E. Bajramovic, K. Waedt, A. Ciriello and D. Gupta. (2016). “Forensic readiness of smart buildings: Preconditions for subsequent cybersecurity tests,” in 2016 IEEE Int. Smart Cities Conf., Trento, Italy, pp. 1–6, . https://doi.org/10.1109/ISC2.2016.7580754. [Google Scholar]
28. S. Escolar, D. Villa, F. J. Villanueva, R. Cantarero and J. C. López. (2016). “An adaptive emergency protocol for people evacuation in high-rise buildings,” in 2016 IEEE Symp. on Computers and Communication, Messina, Italy, pp. 364–371, . https://doi.org/10.1109/ISCC.2016.7543767. [Google Scholar]
29. R. S. Ransing and M. Rajput. (2015). “Smart home for elderly care, based on Wireless Sensor Network,” in 2015 Int. Conf. on Nascent Technologies in the Engineering Field, Navi Mumbai, India, pp. 1–5, . https://doi.org/10.1109/ICNTE.2015.7029932. [Google Scholar]
30. P. Gupta and J. Chhabra. (2016). “IoT based smart home design using power and security management,” in 2016 Int. Conf. on Innovation and Challenges in Cyber Security, Greater Noida, India, pp. 6–10, . https://doi.org/10.1109/ICICCS.2016.7542317. [Google Scholar]
31. X. Hong, C. Yang and C. Rong. (2016). “Smart home security monitor system,” in 2016 15th Int. Symp. on Parallel and Distributed Computing, Fuzhou, pp. 247–251, . https://doi.org/10.1109/ISPDC.2016.42. [Google Scholar]
32. J. Nicklas, M. Mamrot, P. Winzer, D. Lichte, S. Marchlewitz et al. (2016). , “Use case based approach for an integrated consideration of safety and security aspects for smart home applications,” in 2016 11th System of Systems Engineering Conf., Kongsberg, Norway, pp. 1–6, . https://doi.org/10.1109/SYSOSE. 2016.7542908. [Google Scholar]
33. S. Al Salami, J. Baek, K. Salah and E. Damiani. (2016). “Lightweight encryption for smart home,” in 2016 11th Int. Conf. on Availability, Reliability and Security, Salzburg, Austria, pp. 382–388, . https://doi.org/10.1109/ARES.2016.40. [Google Scholar]
34. S. Dharur, C. Hota and K. Swaminathan. (2017). “Energy efficient IoT framework for smart buildings,” in 2017 Int. Conf. on I-SMAC (IoT in Social, Mobile, Analytics and CloudPalladam, India, pp. 793–800, . https://doi.org/10.1109/I-SMAC.2017.8058288. [Google Scholar]
35. R. Fischer, K. Lamshöft, J. Dittmann and C. Vielhauer. (2017). “Advanced issues in wireless communication security: Towards a security-demonstrator for smart-home environments,” in 2017 Int. Carnahan Conf. on Security Technology, Madrid, Spain, pp. 1–6, . https://doi.org/10.1109/CCST.2017.8167864. [Google Scholar]
36. D. Geneiatakis, I. Kounelis, R. Neisse, I. Nai-Fovino, G. Steri et al. (2017). , “Security and privacy issues for an IoT based smart home,” in 2017 40th Int. Convention on Information and Communication Technology, Electronics and Microelectronics, Opatija, pp. 1292–1297, . https://doi.org/10.23919/MIPRO.2017.7973622. [Google Scholar]
37. J. E. Hachem, T. A. Khalil, V. Chiprianov, A. Babar and P. Aniorte. (2017). “A model driven method to design and analyze secure architectures of systems-of-systems,” in 2017 22nd Int. Conf. on Engineering of Complex Computer Systems, Fukuoka, pp. 166–169, . https://doi.org/10.1109/ICECCS.2017.31. [Google Scholar]
38. M. Hajjem, H. Bouziri, E. Talbi and K. Mellouli. (2017). “Intelligent indoor evacuation guidance system based on ant colony algorithm,” in 2017 IEEE/ACS 14th Int. Conf. on Computer Systems and Applications, Hammamet, Tunisia, pp. 1035–1042, . https://doi.org/10.1109/AICCSA.2017.47. [Google Scholar]
39. S. Krishnan, M. S. Anjana and S. N. Rao. (2017). “Security considerations for IoT in smart buildings,” in 2017 IEEE Int. Conf. on Computational Intelligence and Computing Research, Coimbatore, India, pp. 1–4, . https://doi.org/10.1109/ICCIC.2017.8524450. [Google Scholar]
40. M. A. Raja, G. R. Reddy and Ajitha. (2017). “Design and implementation of security system for smart home,” in 2017 Int. Conf. on Algorithms, Methodology, Models and Applications in Emerging Technologies, Chennai, India, pp. 1–4, . https://doi.org/10.1109/ICAMMAET.2017.8186705. [Google Scholar]
41. D. A. R. Wati and D. Abadianto. (2017). “Design of face detection and recognition system for smart home security application,” in 2017 2nd Int. Conf. on Information Technology, Information Systems and Electrical Engineering, Yogyakarta, Indonesia, pp. 342–347, . https://doi.org/10.1109/ICITISEE.2017.8285524. [Google Scholar]
42. T. Adiono, S. Harimurti, B. A. Manangkalangi and W. Adijarto. (2018). “Design of smart home mobile application with high security and automatic features,” in 2018 3rd Int. Conf. on Intelligent Green Building and Smart Grid, Yilan, Taiwan, pp. 1–4, . https://doi.org/10.1109/IGBSG.2018.8393574. [Google Scholar]
43. S. K. Bhoi, S. K. Panda, B. N. Padhi, M. K. Swain, B. Hembram et al. (2018). , “FireDS-IoT: A fire detection system for smart home based on IoT data analytics,” in 2018 Int. Conf. on Information Technology, pp. 161–165. [Google Scholar]
44. M. Botticelli, L. Ciabattoni, F. Ferracuti, A. Monteriù, S. Pizzuti et al. (2018). , “A smart home services demonstration: Monitoring, control and security services offered to the user,” in 2018 IEEE 8th Int. Conf. on Consumer Electronics, Berlin, pp. 1–4. [Google Scholar]
45. E. Ertugrul, U. Kocaman and O. K. Sahingoz. (2018). “Autonomous aerial navigation and mapping for security of smart buildings,” in 2018 6th Int. Istanbul Smart Grids and Cities Congress and Fair, Istanbul, Turkey, pp. 168–172, . https://doi.org/10.1109/SGCF.2018.8408966. [Google Scholar]
46. V. Haţegan, V. T. Dădarlat, A. Peculea and E. Cebuc. (2018). “Secure and extensible smart home template,” in 2018 17th RoEduNet Conf.: Networking in Education and Research, Cluj-Napoca, Romania, pp. 1–6, . https://doi.org/10.1109/ROEDUNET.2018.8514145. [Google Scholar]
47. C. C. Li, P. Wu, H. Wang, E. T. H. Chu and J. W. S. Liu. (2018). “Building/environment data/information system for fine-scale indoor location specific services,” in 2018 IEEE 2nd Int. Conf. on Fog and Edge Computing, Washington, DC, USA, pp. 1–8, . https://doi.org/10.1109/CFEC.2018.8358731. [Google Scholar]
48. P. K. Madupu and B. Karthikeyan. (2018). “Automatic service request system for security in smart home using IoT,” in 2018 Second Int. Conf. on Electronics, Communication and Aerospace Technology, Coimbatore, India, pp. 1413–1418, . https://doi.org/10.1109/ICECA.2018.8474684. [Google Scholar]
49. S. Pawar, V. Kithani, S. Ahuja and S. Sahu. (2018). “Smart home security using IoT and face recognition,” in 2018 Fourth Int. Conf. on Computing Communication Control and Automation, Pune, India, pp. 1–6, . https://doi.org/10.1109/ICCUBEA.2018.8697695. [Google Scholar]
50. L. Rafferty, F. Iqbal, S. Aleem, Z. Lu, S. Huang et al. (2018). , “Intelligent multi-agent collaboration model for smart home IoT security,” in 2018 IEEE Int. Congress on Internet of Things, San Francisco, CA, USA, pp. 65–71, . https://doi.org/10.1109/ICIOT.2018.00016. [Google Scholar]
51. Y. Wang, H. Lv, Q. Zhang, P. Wang, D. Yan et al. (2018). , “Research on smart home security system based on bp neural network information fusion,” in 2018 Chinese Automation Congress, Xi'an, China, pp. 1381–1384, . https://doi.org/10.1109/CAC.2018.8623606. [Google Scholar]
52. Y. N. Aung and T. Tantidham. (2019). “Ethereum-based emergency service for smart home system: Smart contract implementation,” in 2019 21st Int. Conf. on Advanced Communication Technology, PyeongChang, Korea (Southpp. 147–152, . https://doi.org/10.23919/ICACT.2019.8701987. [Google Scholar]
53. T. Chaurasia and P. K. Jain. (2019). “Enhanced smart home automation system based on internet of things,” in 2019 Third Int. Conf. on I-SMAC (IoT in Social, Mobile, Analytics and CloudPalladam, India, pp. 709–713, . https://doi.org/10.1109/I-SMAC47947.2019.9032685. [Google Scholar]
54. B. Cui, Z. Lan and X. Bai. (2019). “Research on role-based access control in IPv6 smart home,” in 2019 IEEE 9th Int. Conf. on Electronics Information and Emergency Communication, Beijing, China, pp. 205–208, . https://doi.org/10.1109/ICEIEC.2019.8784596. [Google Scholar]
55. H. Hsu, G. Jong, J. Chen and C. Jhe. (2019). “Improve IoT security system of smart-home by using support vector machine,” in 2019 IEEE 4th In. Conf. on Computer and Communication Systems, Singapore, pp. 674–677, . https://doi.org/10.1109/CCOMS.2019.8821678. [Google Scholar]
56. K. Karimi and S. Krit. (2019). “Smart home-smartphone systems: Threats, security requirements and open research challenges,” in 2019 Int. Conf. of Computer Science and Renewable Energies, Agadir, Morocco, pp. 1–5, . https://doi.org/10.1109/ICCSRE.2019.8807756. [Google Scholar]
57. V. Krundyshev and M. Kalinin. (2019). “Prevention of false data injections in smart infrastructures,” in 2019 IEEE Int. Black Sea Conf. on Communications and Networking, Sochi, Russia, pp. 1–5, . https://doi.org/10.1109/BlackSeaCom.2019.8812786. [Google Scholar]
58. V. Nguyen, H. Nguyen, Q. Huynh, N. Venkatasubramanian and K. Kim. (2019). “A scalable approach for dynamic evacuation routing in large smart buildings,” in 2019 IEEE Int. Conf. on Smart Computing, Washington, DC, USA, pp. 292–300, . https://doi.org/10.1109/SMARTCOMP.2019.00065. [Google Scholar]
59. U. Osisiogu. (2019). “A review on cyber-physical security of smart buildings and infrastructure,” in 2019 15th Int. Conf. on Electronics, Computer and Computation, Abuja, Nigeria, pp. 1–4, . https://doi.org/10.1109/ICECCO48375.2019.9043207. [Google Scholar]
60. E. Pramunanto, M. Muhtadin and W. Febrian. (2019). “Integrated smart safety home system based on wireless sensor network and internet of things as emergency preventive efforts in settlement areas,” in 2019 Int. Conf. on Computer Engineering, Network, and Intelligent Multimedia, Surabaya, Indonesia, pp. 1–7, . https://doi.org/10.1109/CENIM48368.2019.8973328. [Google Scholar]
61. H. Qusa, H. Allam, F. Younus, M. Ali and S. Ahmad. (2019). “Secure smart home using open security intelligence systems,” in 2019 Sixth HCT Information Technology Trends (ITT), New York, US: IEEE, pp. 12–17. [Google Scholar]
62. S. Ramapatruni, S. N. Narayanan, S. Mittal, A. Joshi and K. Joshi. (2019). “Anomaly detection models for smart home security,” in 2019 IEEE 5th Int. Conf. on Big Data Security on Cloud, IEEE Int. Conf. on High Performance and Smart Computing and IEEE Int. Conf. on Intelligent Data and Security, Washington, DC, USA, pp. 19–24, . https://doi.org/10.1109/BigDataSecurity-HPSC-IDS.2019.00015. [Google Scholar]
63. J. Tang and Q. Jia. (2019). “A simulation platform for sensing system selection for occupant distribution estimation in smart buildings,” in 2019 IEEE 15th Int. Conf. on Automation Science and Engineering, Vancouver, BC, Canada, pp. 985–990, . https://doi.org/10.1109/COASE.2019.8843129. [Google Scholar]
64. T. Tantidham and Y. N. Aung. (2019). “Emergency service for smart home system using ethereum blockchain: System and architecture,” in 2019 IEEE Int. Conf. on Pervasive Computing and Communications Workshops, Kyoto, Japan, pp. 888–893, . https://doi.org/10.1109/PERCOMW.2019.8730816. [Google Scholar]
65. V. Zhmud, A. Liapidevskiy, H. Roth and J. Nosek. (2019). “The concept of a smart home: Security, additional features and augmented reality,” in 2019 Int. Multi-Conf. on Industrial Engineering and Modern Technologies, Vladivostok, Russia, pp. 1–8, . https://doi.org/10.1109/FarEastCon.2019.8933841. [Google Scholar]
66. A. K. Ray and A. Bagwari. (2020). “IoT based Smart home: Security aspects and security architecture,” in 2020 IEEE 9th Int. Conf. on Communication Systems and Network Technologies, Gwalior, India, pp. 218–222, . https://doi.org/10.1109/CSNT48778.2020.9115737. [Google Scholar]
67. V. Subbarao, K. Srinivas and R. S. Pavithr. (2019). “A survey on internet of things based smart, digital green and intelligent campus,” in 2019 4th Int. Conf. on Internet of Things: Smart Innovation and Usages, Ghaziabad, India, pp. 1–6, . https://doi.org/10.1109/IoT-SIU.2019.8777476. [Google Scholar]
68. X. Feng, Y. Wang, L. Jiang, Y. Huang and T. Li. (2018). “A survey on internet of things security based on smart home,” in 2018 5th Asia-Pacific World Congress on Computer Science and Engineering, Nadi, Fiji, pp. 84–91, . https://doi.org/10.1109/APWConCSE.2018.00022. [Google Scholar]
69. W. Ali, G. Dustgeer, M. Awais and M. A. Shah. (2017). “IoT based smart home: Security challenges, security requirements and solutions,” in 2017 23rd Int. Conf. on Automation and Computing, Huddersfield, UK, pp. 1–6, . https://doi.org/10.23919/IConAC.2017.8082057. [Google Scholar]
70. A. Jacobsson, M. Boldt and B. Carlsson. (2016). “A risk analysis of a smart home automation system,” Future Generation Computer Systems, vol. 56, no. 1, pp. 719–733. [Google Scholar]
71. H. M. Do, M. Pham, W. Sheng, D. Yang and M. Liu. (2018). “RiSH: A robot-integrated smart home for elderly care,” Robotics and Autonomous Systems, vol. 101, no. 3, pp. 74–92. [Google Scholar]
72. N. Akatyev and J. I. James. (2019). “Evidence identification in IoT networks based on threat assessment,” Future Generation Computer Systems, vol. 93, no. 8, pp. 814–821. [Google Scholar]
73. P. Bhoyar, P. Sahare, S. B. Dhok and R. B. Deshmukh. (2019). “Communication technologies and security challenges for internet of things: A comprehensive review,” AEU International Journal of Electronics and Communications, vol. 99, no. 4, pp. 81–99. [Google Scholar]
74. D. D. Furszyfer Del Rio, B. K. Sovacool, N. Bergman and K. E. Makuch. (2020). “Critically reviewing smart home technology applications and business models in Europe,” Energy Policy, vol. 144, pp. 111631. [Google Scholar]
75. P. P. Ray, D. Dash and N. Kumar. (2020). “Sensors for internet of medical things: State-of-the-art, security and privacy issues, challenges and future directions,” Computer Communications, vol. 160, no. 3, pp. 111–131. [Google Scholar]
76. L. Vadillo Moreno, M. L. Martín Ruiz, J. Malagón Hernández, M. Á. Valero Duboy and M. Lindén. (2017). “Chapter 14-The role of smart homes in intelligent homecare and healthcare environments,” In: C. Dobre, C. Mavromoustakis, N. Garcia, R. Goleva, G. Mastorakis (Eds.)Ambient Assisted Living and Enhanced Living Environments, Oxford, United Kingdom: Butterworth-Heinemann, pp. 345–394. [Google Scholar]
77. L. J. Fennelly and M. A. Perry. (2018). “150 things you should know about security,” In: L. J. Fennelly, M.~A. Perry (Eds.)150 Things You Should Know About Security, 2nd ed., Oxford, United Kingdom: Butterworth-Heinemann, pp. 1–218. [Google Scholar]
78. R. Saini and D. Mishra. (2019). “Chapter 4---Privacy-aware physical layer security techniques for smart cities,” In: D. B. Rawat, K. Z. Ghafoor (Eds.)Smart Cities Cybersecurity and Privacy, Amsterdam, Netherlands: Elsevier, pp. 39–56. [Google Scholar]
79. W. M. Kang, S. Y. Moon and J. H. Park. (2017). “An enhanced security framework for home appliances in smart home,” Human-Centric Computing and Information Sciences, vol. 7, no. 1, pp. 6. [Google Scholar]
80. M. Amiribesheli and H. Bouchachia. (2018). “A tailored smart home for dementia care,” Journal of Ambient Intelligence and Humanized Computing, vol. 9, no. 6, pp. 1755–1782. [Google Scholar]
81. E. Park, S. Kim, Y. Kim and S. J. Kwon. (2018). “Smart home services as the next mainstream of the ICT industry: Determinants of the adoption of smart home services,” Universal Access in the Information Society, vol. 17, no. 1, pp. 175–190. [Google Scholar]
82. H. Xu, L. König, D. Cáliz and H. Schmeck. (2018). “A generic user interface for energy management in smart homes,” Energy Informatics, vol. 1, no. 1, pp. 55. [Google Scholar]
83. M. Talal, A. A. Zaidan, B. B. Zaidan, A. S. Albahri, A. H. Alamoodi et al. (2019). , “Smart home-based IoT for real-time and secure remote health monitoring of triage and priority system using body sensors: Multi-driven systematic review,” Journal of Medical Systems, vol. 43, no. 3, pp. 42. [Google Scholar]
84. X. Wei, T. Wang and C. Tang. (2019). “Throughput Analysis of smart buildings-oriented wireless networks under jamming attacks,” Mobile Networks and Applications, vol. 18, no. 8, pp. 2611. [Google Scholar]
85. D. R. dos Santos, M. Dagrada and E. Costante. (2020). “Leveraging operational technology and the Internet of things to attack smart buildings,” Journal of Computer Virology and Hacking Techniques, . https://doi.org/10.1007/s11416-020-00358-8. [Google Scholar]
86. N. Guhr, O. Werth, P. P. H. Blacha and M. H. Breitner. (2020). “Privacy concerns in the smart home context,” SN Applied Sciences, vol. 2, no. 2, pp. 247. [Google Scholar]
87. S. Naoui, M. E. Elhdhili and L. Azouz Saidane. (2020). “Novel enhanced LoRaWAN framework for smart home remote control security,” Wireless Personal Communications, vol. 110, no. 4, pp. 2109–2130. [Google Scholar]
88. S. Naoui, M. E. Elhdhili and L. A. Saidane. (2020). “Collaborative and verifiable key derivation protocol for smart home security: CV-KDP,” Information Technology and Management, vol. 21, no. 2, pp. 115–129. [Google Scholar]
89. P. Tsoutsa, P. Fitsilis, L. Anthopoulos and O. Ragos. (2020). “Nexus services in smart city ecosystems,” Journal of the Knowledge Economy, vol. 18, no. 5/6, pp. 1. [Google Scholar]
90. F. McCreary, A. Zafiroglu and H. Patterson. (2016). “The contextual complexity of privacy in smart homes and smart buildings,” in HCI in Business, Government, and Organizations: Information Systems, Cham: Springer, pp. 67–78. [Google Scholar]
91. J. R. C. Nurse, A. Atamli and A. Martin. (2016). “Towards a usable framework for modelling security and privacy risks in the smart home,” in Human Aspects of Information Security, Privacy, and Trust, Cham: Springer, pp. 255–267. [Google Scholar]
92. R. Chowdhury, H. Ould-Slimane, C. Talhi and M. Cheriet. (2017). “Attribute-based encryption for preserving smart home data privacy,” in Enhanced Quality of Life and Smart Living, Cham: Springer, pp. 185–197. [Google Scholar]
93. M. Buf, B. Guerra and M. Manso. (2018). “Smart devices for automated emergency calls,” in Interoperability, Safety and Security in IoT, Cham: Springer, pp. 27–37. [Google Scholar]
94. P. K. Sharma, B. W. Kwon and J. H. Park. (2018). “DSS-SL: Dynamic signage system based on SDN with LiFi communication for smart buildings,” in Advances in Computer Science and Ubiquitous Computing, Singapore: Springer, pp. 805–810. [Google Scholar]
95. P. S. Ramya and D. Nandan. (2020). “Analysis of security issues and possible solutions in the internet of things for home automation system,” in Soft Computing: Theories and Applications, Singapore: Springer, pp. 825–836. [Google Scholar]
96. V. Varadharajan and S. Bansal. (2016). “Data security and privacy in the internet of things (IoT) environment,” In: Z. Mahmood (Ed.)Connectivity Frameworks for Smart Devices: The Internet of Things from a Distributed Computing Perspective, Cham: Springer International Publishing, pp. 261–281. [Google Scholar]
97. M. Manso, B. Guerra, C. Carjan, E. Sdongos, A. Bolovinou et al. (2018). , “The application of telematics and smart devices in emergencies,” In: R. Gravina, C. E. Palau, M. Manso, A. Liotta, G. Fortino (Eds.)Integration, Interconnection, and Interoperability of IoT Systems, Cham: Springer International Publishing, pp. 169–197. [Google Scholar]
98. R. M. Aileni, G. Suciu, M. Serrano, R. Maheswar and C. A. Valderrama Sakuyama. (2020). “The perspective of smart dust mesh based on ioee for safety and security in the smart cities,” In: S. Rani, R. Maheswar, G. R. Kanagachidambaresan, P. Jayarajan (Eds.)Integration of WSN and IoT for Smart Cities, Cham: Springer International Publishing, pp. 151–179. [Google Scholar]
99. R. T. Kreutzer and M. Sirrenberg. (2020). “Fields of application of artificial intelligence—Energy sector, smart home, mobility and transport,” in Understanding Artificial Intelligence: Fundamentals, Use Cases and Methods for a Corporate AI, Cham: Springer International Publishing, pp. 195–210. [Google Scholar]
100. D. N. Mekuria, P. Sernani, N. Falcionelli and A. F. Dragoni. (2019). “Smart home reasoning systems: A systematic literature review,” Journal of Ambient Intelligence and Humanized Computing, vol. 12, no. 9, pp. 2265. [Google Scholar]
101. J. Dahmen, D. J. Cook, X. Wang and W. Honglei. (2017). “Smart secure homes: A survey of smart home technologies that sense, assess, and respond to security threats,” Journal of Reliable Intelligent Environments, vol. 3, no. 2, pp. 83–98. [Google Scholar]
102. H. Ai and T. Li. (2017). “A smart home system based on embedded technology and face recognition technology,” Intelligent Automation & Soft Computing, vol. 23, no. 3, pp. 405–418. [Google Scholar]
103. J. E. Kim, T. Barth, G. Boulos, J. Yackovich, C. Beckel et al. (2017). , “Seamless integration of heterogeneous devices and access control in smart homes and its evaluation,” Intelligent Buildings International, vol. 9, no. 1, pp. 23–39. [Google Scholar]
104. D. Choi, H. Choi and D. Shon. (2019). “Future changes to smart home based on AAL healthcare service,” Journal of Asian Architecture and Building Engineering, vol. 18, no. 3, pp. 190–199. [Google Scholar]
105. R. Mulcahy, K. Letheren, R. McAndrew, C. Glavas and R. Russell-Bennett. (2019). “Are households ready to engage with smart home technology?,” Journal of Marketing Management, vol. 35, no. 15, 16, pp. 1370–1400. [Google Scholar]
106. M. C. Chiu, W. D. Lai and C. M. Chiu. (2020). “A smart home system with security and electrical appliances,” Journal of Information and Optimization Sciences, vol. 56, no. 4, pp. 1–17. [Google Scholar]
107. B. Mbarek, A. Meddeb, W. Ben Jaballah and M. Mosbah. (2017). “A secure electric energy management in smart home,” International Journal of Communication Systems, vol. 30, no. 17, pp. e3347. [Google Scholar]
108. S. Sicari, A. Rizzardi, D. Miorandi and A. Coen-Porisini. (2018). “Securing the smart home: A real case study,” Internet Technology Letters, vol. 1, no. 3, pp. e22. [Google Scholar]
109. G. Zhao, L. Xing, Q. Zhang and X. Jia. (2018). “A hierarchical combinatorial reliability model for smart home systems,” Quality and Reliability Engineering International, vol. 34, no. 1, pp. 37–52. [Google Scholar]
110. F. Ghasemi, A. Rezaee and A. M. Rahmani. (2019). “Structural and behavioral reference model for IoT-based elderly healthcare systems in smart home,” International Journal of Communication Systems, vol. 32, no. 12, pp. e4002. [Google Scholar]
111. A. Ali, M. Ahmed, M. Imran and H. A. Khattak. (2020). “Security and privacy issues in fog computing,” in Fog Computing: Theory and Practice, New York, US: IEEE, pp. 105–137. [Google Scholar]
112. M. Wills. (2019). “Network and communications security,” in The Official (ISC)2 SSCP CBK Reference, Mountain View, California, United States, California, United States: Coursera, pp. 467–647. [Google Scholar]
113. P. Spachos and K. Plataniotis. (2018). “Environmental monitoring for smart buildings,” in Transportation and Power Grid in Smart Cities, Communication Networks and Services, pp. 327–354. [Google Scholar]
114. S. Wendzel, J. Tonejc, J. Kaur, A. Kobekova, H. Song et al. (2017). , “Cyber security of smart buildings,” in Security and Privacy in Cyber-Physical Systems, Wiley, pp. 327–351. [Google Scholar]
115. H. F. Rashvand and J. M. A. Calero. (2012). “Smart home, smart office,” in Distributed Sensor Systems: Practice and Applications, Hoboken, New Jersey, United States: Wiley, pp. 189–219. [Google Scholar]
116. S. Gunasingh, N. Wang, D. Ahl and S. Schuetter. (2017). “Climate resilience and the design of smart buildings,” In: H. Song, R. Srinivasan, T. Sookoor and S. Jeschke (Eds.)Smart Cities: Foundations, Principles, and Applications, pp.~641–667, . https://doi.org/10.1002/9781119226444.ch22. [Google Scholar]
117. S. Kolhe, S. Nagpal, P. Makwana and C. Bhatt. (2018). “Smart home: Personal assistant and baby monitoring system,” in Emerging Technologies for Health and Medicine: Virtual Reality, Augmented Reality, Artificial Intelligence Internet of Things, Robotics, Industry 4.0, pp. 259–284. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |