[BACK]
Computers, Materials & Continua
DOI:10.32604/cmc.2021.015597 |  |
| Article | |
An End-to-End Authentication Scheme for Healthcare IoT Systems Using WMSN
Shadi Nashwan*
Department of Computer Science, College of Computer and Information Sciences, Jouf University, Sakaka, 42421, Saudi Arabia
*Corresponding Author: Shadi Nashwan. Email: shadi_nashwan@ju.edu.sa
Received: 29 November 2020; Accepted: 25 January 2021
Abstract: The healthcare internet of things (IoT) system has dramatically reshaped this important industry sector. This system employs the latest technology of IoT and wireless medical sensor networks to support the reliable connection of patients and healthcare providers. The goal is the remote monitoring of a patient’s physiological data by physicians. Moreover, this system can reduce the number and expenses of healthcare centers, make up for the shortage of healthcare centers in remote areas, enable consultation with expert physicians around the world, and increase the health awareness of communities. The major challenges that affect the rapid deployment and widespread acceptance of such a system are the weaknesses in the authentication process, which should maintain the privacy of patients, and the integrity of remote medical instructions. Current research results indicate the need of a flexible authentication scheme. This study proposes a scheme with enhanced security for healthcare IoT systems, called an end-to-end authentication scheme for healthcare IoT systems, that is, an E2EA. The proposed scheme supports security services such as a strong and flexible authentication process, simultaneous anonymity of the patient and physician, and perfect forward secrecy services. A security analysis based on formal and informal methods demonstrates that the proposed scheme can resist numerous security-related attacks. A comparison with related authentication schemes shows that the proposed scheme is efficient in terms of communication, computation, and storage, and therefore cannot only offer attractive security services but can reasonably be applied to healthcare IoT systems.
Keywords: Healthcare IoT systems; wireless medical sensor networks; mutual authentication service; anonymity service; perfect forward secrecy service; COVID-19
1 Introduction
The main goal of internet of things (IoT) healthcare systems is the remote monitoring of the physiological data of patients by physicians to make their lives safer and more comfortable [1–4]. A patient’s physiological data can be collected remotely using specific sensors when the patient is away from a healthcare center, such as electrical activity of the brain, blood pressure, heartbeat, body temperature, blood sugar, pedometer readings, and respiratory signs [5]. These sensitive data are transmitted to physicians, who can provide immediate and continuous health advice, especially during an emergency, such as during the coronavirus disease 2019 (COVID-19) pandemic [6]. Furthermore, healthcare IoT systems can enable the reduction of the number of healthcare centers and cover shortages in remote areas. Healthcare IoT systems can increase the health awareness of communities at a lower cost. In an IoT healthcare system, communications between service providers and patients can be achieved through the internet [7–10]. The communication technology used in most such systems is a wireless medical sensor network (WMSN) [11–13], which enables a reliable wireless connection between provider communication devices and sensor nodes of patients [14,15].
There are two security challenges to the deployment and acceptance of such technology: data privacy of patients and integrity of medical instructions. An unauthorized party could access the sensitive data collected by sensor nodes, with consequences such as loss of jobs or health insurance.
An unauthorized party could modify messages to deliver the wrong order or advice to patients, such as to update the dose pumped by an electronic insulin device [16,17]. Unauthorized access to messages transferred between system nodes is the primary source of weakness, and unauthorized access to sensor nodes may lead to inconsistent or fabricated medical reports. Restricted capabilities of the sensor nodes themselves can cause other types of weaknesses.
Many security attacks exploit these weaknesses, such as smartcard loss attacks; patient and physician anonymity attacks; sensor node spoofing; patient and physician impersonation; and replay, insider, desynchronization, and man-in-the-middle attacks [18–30]. Therefore, WMSN security requires significant improvement.
1.1 Security Requirements of Healthcare IoT Systems
To determine the security requirements of a healthcare IoT system, authentication must be accomplished through an integral unit. Requirements include the following [18–29].
• A lightweight cryptographic function should be used at the patient node to achieve fast and secure mutual authentication with WMSN nodes;
• Mutual authentication is required not only between WMSN nodes and physician nodes but among all communication nodes using different cryptographic techniques;
• Authentication should detect both random and malicious alterations of authentication messages without effecting the communication data rate;
• With anonymity service becoming increasingly important, authentication should hide identities of physician nodes and all communication nodes;
• Authentication should support perfect forward secrecy for long-term keys of communication nodes such that an unauthorized party cannot disclose previous authentication session keys.
1.2 Architecture of Healthcare IoT Systems
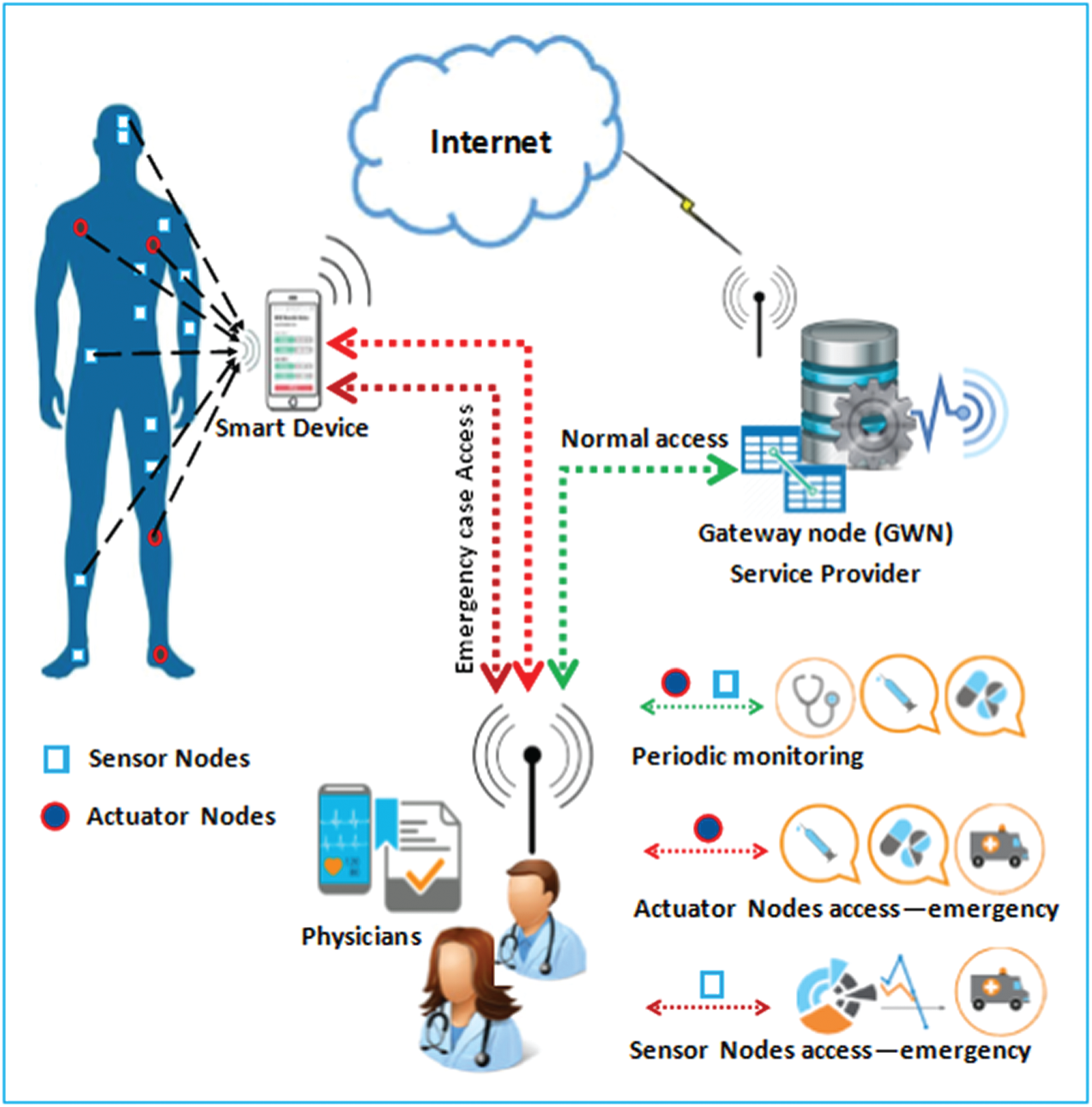
A healthcare IoT system must prevent unauthorized access to sensitive patient data and medical instructions, so a high priority in the design of the authentication scheme should be given for the malicious modifications. We propose a model architecture to monitor patient medical status using WMSN. Fig. 1 shows its main components.

Figure 1: The healthcare IoT system architecture using WMSN
WMSN nodes are either sensor or actuator nodes. Sensor nodes can sense the physiological data of patients and send regular data reports to smart devices such as electroencephalogram, heartbeat, pulse rate, pedometer, breathing, vision, glucose level, and temperature sensors [24,30]. Actuator nodes receive medical instructions from a physician though a patient’s smart device to carry out actions such as for insulin pumps, drug delivery, and brain and muscle stimulators [13,31].
A patient’s smart device node should be able to store and transmit physiological data captured by sensor nodes, including on-demand and emergency sensor data [20]. Sensor nodes periodically send captured data to the smart device, which forwards it directly to the gateway node (GWN) though the internet. Therefore, the smart device must be able to compute the lightweight cryptographic functions to communicate with sensor nodes and GWN node.
The GWN node is the heart of the authentication process, providing registration stages to providers and patient smart devices. It coordinates authentication and key agreement (AKA) execution between all authentication nodes. The physician gathers a patient’s physiological data indirectly from the GWN node to analyze it and monitor the patient’s physical condition.
The physician node is represented by a physician’s monitoring device that collects the physiological data of a patient, either indirectly from the GWN node during periodic monitoring, or directly from the patient’s smart device node during an emergency. The physician can diagnose the medical state of the patient and send medical instructions to actuator nodes for treatment.
WMSN nodes suffer from restrictions such as memory space and computational capability. Moreover, the connection takes place through low frequencies with WMSN nodes. Thus, the communication cost is proportional to the distance between the WMSN node and other nodes in the system.
The proposed architecture eliminates this obstacle. The physician node can connect to WMSN nodes through the patient’s smart device to collect physiological data in an emergency, allowing real-time gathering of data from the patient’s smart device [18].
1.3 Related Work
With increasing demand for healthcare IoT systems, numerous authentication schemes have been proposed to ensure data privacy and integrity of medical instructions. We highlight some schemes proposed for healthcare IoT systems using WMSN.
Kumar et al. [32] proposed an authentication scheme for WMSN to monitor the vital signs of a patient while preventing various security attacks. He et al. [33] claimed that this scheme was vulnerable to attacks such as password guessing, insider attacks, and cannot be achieved the user anonymity service, and suggested an improved scheme. This scheme cannot defeat attacks such as password guessing [34–36]. Li et al. [34] improved on this with an authentication scheme for WMSN applications to preserve user anonymity, using smartcard concepts and hash functions.
Das et al. [37] presented a secure and anonymous user authentication scheme based on smartcard concepts for healthcare applications using WMSN. Srinivas et al. [38] pointed out that the scheme of Li et al. [34] was vulnerable to stolen smartcard attack, insider attack, and user impersonation attack, and proposed a scheme claimed to resist all known attacks. Wu et al. [39] identified security weaknesses in the scheme of Srinivas et al. [38], such as offline password guessing attack.
Amin et al. [40] suggested an anonymity and robust mutual authentication scheme they claimed was more robust than other schemes. Ali et al. [41] showed that the scheme suffers from user offline password guessing, identity guessing, user impersonation, insider, and session key attacks.
Shuai et al. [42] noted that Wu et al. [39] and Ali et al. [41] cannot support perfect forward secrecy service nor resist a desynchronization attack, and proposed a scheme for healthcare systems using WMSN to solve these weaknesses. Fotouhi et al. [43] showed that Srinivas et al. [38] cannot support sensor anonymity and untraceability, nor resist an offline guessing attack, and claimed that Wu et al. [39] and Amin et al. [40] cannot support perfect forward secrecy or sensor anonymity and untraceability services.
It can be observed that none of the above schemes supports end-to-end authentication between all communication nodes of a system
1.4 Motivations and Contributions
The healthcare IoT system is especially important in developing countries to achieve economic growth, as it can reduce the number and expense of healthcare centers, and enable patients to consult physicians from around the world. A healthcare IoT system can increase the health awareness of communities, especially during crises such as the COVID-19 pandemic. An authentication scheme by integrate the healthcare IoT system with WMSN technology can make it more secure and widely accepted.
The main contributions of this paper are as follows. An architecture of the healthcare IoT system using WMSN is introduced, including the main authentication nodes and the communication flow. An authentication scheme for healthcare IoT systems using WMSN is proposed. Security verification based on BAN logic is used to verify mutual authentication between nodes. An informal, comparative security analysis shows how the proposed scheme can resist all types of attacks. A comparative performance analysis demonstrates the scheme’s applicability.
1.5 Organization of This Paper
The remainder of this paper is organized as follows. Section 2 describes the proposed authentication scheme. Formal verification using BAN logic and an informal security analysis of the proposed scheme are described in Section 3. A performance analysis is presented in Section 4. We provide our conclusions in Section 5.
2 Proposed Authentication Scheme
An end-to-end authentication scheme for healthcare IoT systems using WMSN is proposed, which is based on the one-way hash function and symmetric cryptographic techniques.
2.1 Preliminaries
We address preliminaries such as scheme structure, notation, assumptions, and design requirements.
2.1.1 Scheme Structure
The proposed scheme has four types of authentication nodes; physician nodes (Pi), GWNs, WMSN nodes the physician must access (Sk), and smart device nodes (SDj).
The scheme has 10 phases: physician node registration, smart device node registration, WMSN node registration, physician login authentication, patient login authentication, patient password change, physician password change, WMSN node authentication, and long- and short-term authentication.
2.1.2 Notation and Abbreviations
Notation and abbreviations are listed in Tab. 1.
Table 1: Notation and abbreviations of proposed authentication scheme

2.1.3 Assumptions
We list the vulnerability assumptions used in the security analysis of the proposed authentication scheme.
• An adversary can recover the smartcard information of a physician node, and of the patient based on power consumption methods [44,45].
• An adversary can modify, intercept, capture, reroute, and retransmit authentication messages between all communication nodes where communication channels are considered unsecured and unreliable during authentication.
• An adversary can act as a legitimate smart device of a patient or physician node.
• The GWN node is considered a trusted communication node between the smart device of the physician node and the smart device node of the patient.
• Registration phases are accomplished directly through secure and reliable channels with the GWN node.
2.1.4 Design Requirements
We introduce the security requirements used to design the proposed authentication scheme.
• AKA concepts are utilized in all authentication phases. Therefore, communication nodes will mutually and securely authenticate each other to set up a reliable channel and exchange patient data after each authentication session between WMSN and physician nodes.
• Dynamic anonymity is used in authentication to hide the actual identities of patient’s smart device and physician nodes. Therefore, communication nodes use a different identity in each authentication session, and an adversary cannot track or masquerade patients or service provider workers.
• A robust integrity mechanism is used in all authentication phases to detect modifications in authentication messages exchanged between communication nodes. Hence, an adversary cannot alter these messages.
• Lightweight symmetric cryptography is used in long- and short-term authentication to encrypt and decrypt authentication parameters with high entropy. Thus, an adversary cannot guess these parameters in polynomial time. Consequently, physiological data exchanged between communication nodes remain confidential, and only physician nodes can receive it.
• One-way hash functions are used in long- and short-term authentication to derive the long-term session keys. Therefore, an adversary cannot disclose the current session keys nor disclose previous session keys.
2.2 Proposed Scheme Description
The proposed authentication scheme deploys a set of hash and symmetric cryptographic functions; its steps are described using the notation and abbreviations in Tab. 1.
2.2.1 Physician Node Registration Phase
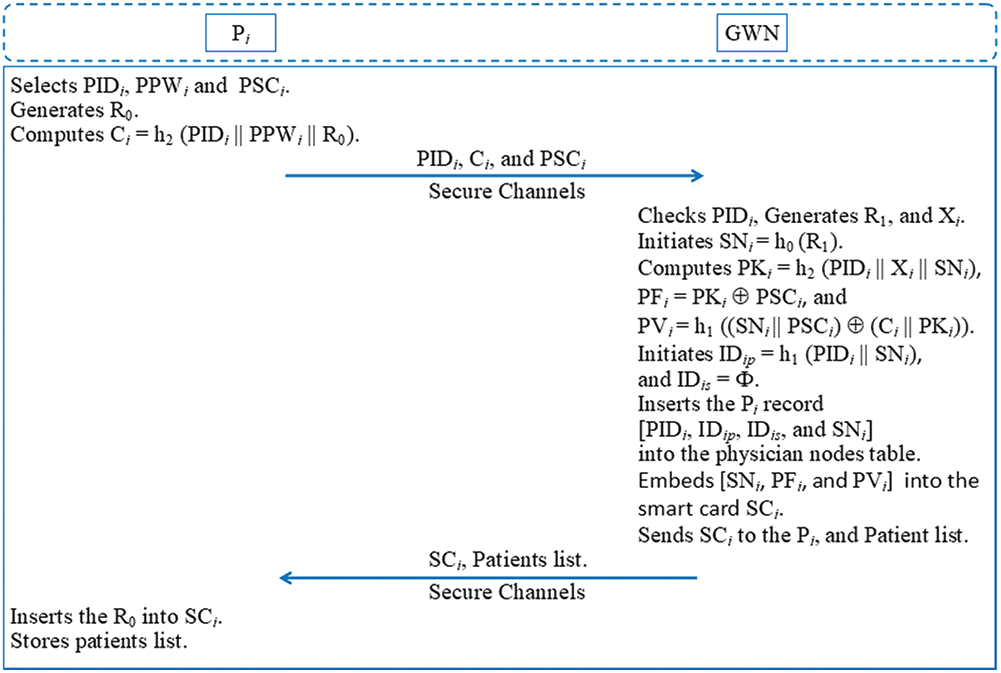
A new physician wanting to access the physiological data collected by the WMSN nodes through the smart device of a patient, whether for periodic monitoring or an emergency, must first register in the GWN node using his/her monitoring device. Fig. 2 shows the physician node registration phase, whose steps are as follows.

Figure 2: Physician node registration phase
Step 1: A new physician node (Pi) selects identity number (PIDi), password (PPWi), and security code (PSCi) according to the system specifications. Pi generates a random number (R0), and computes Ci=h2(PIDi∥PPWi∥R0). Pi sends a registration request message {PIDi, Ci, and PSCi} to the GWN node through a secure communication channel.
Step 2: In response to the Pi request, the GWN node verifies the existence of the identity (PIDi) in the physicians table, which contains the data of physicians that have already registered. If it exists, then the GWN node rejects the registration request message {M1}, and asks Pi to select an unrepeated identity (PIDi). Otherwise, the GWN node generates a random number (R1) and secret key (Xi), whose value is saved securely and separately.
The GWN node initiates the session number SNi=h0(R1), and computes PKi=h1(PIDi∥Xi), PFi=(PKi⊕ PSCi) and PVi=h1((SNi∥PSCi)⊕ (Ci∥PKi)). The GWN node initiates the pseudonym identities IDip=h1(PIDi∥SNi) and IDis=Φ, where Φ has the null value. The GWN node inserts the record of Pi in the physician node table [PIDi, IDip, IDis, and SNi]. The GWN node embeds the authentication parameters [SNi, PFi, and PVi] in a new smartcard (SCi), and connects the new physician with his/her patients through a specific table. The GWN node initiates the session counter (C0ij = 0), and returns SCi and his/her list of patients [SIDj, and C0ij] to Pi via a secure communication channel.
Step 3: Pi receives SCi and inserts R0. Pi separately and securely stores the list of patients.
2.2.2 Smart Device Registration Phase
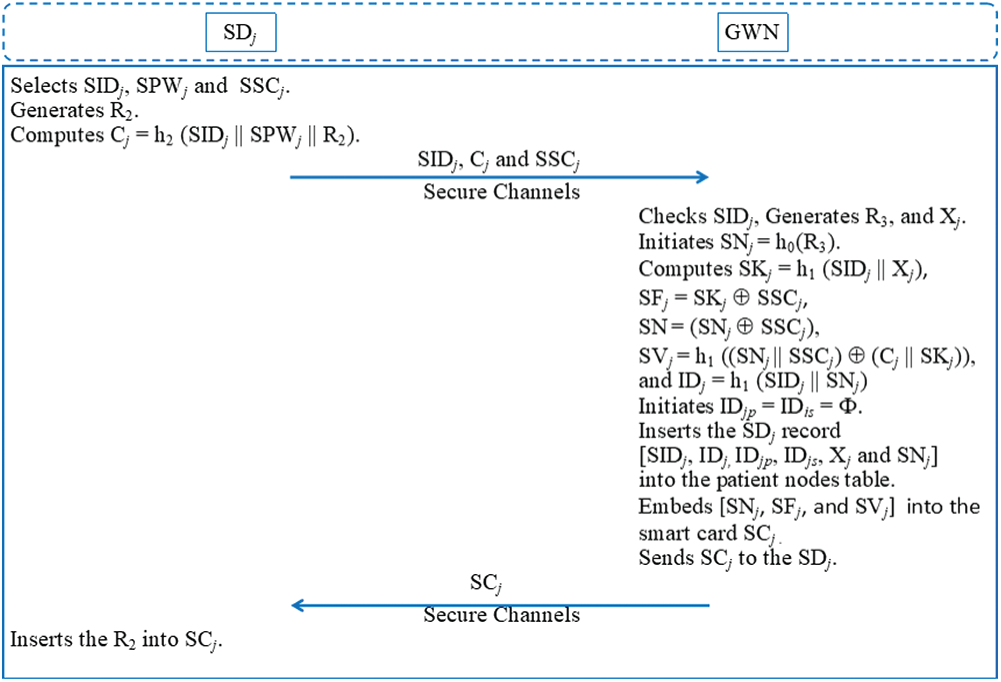
A new patient’s smart device (SDj) receives physiological data from connected WMSN nodes and forwards it to a service provider for periodic monitoring. This device must be registered in the GWN node. Fig. 3 shows the smart device registration phase, whose steps are as follows.

Figure 3: Patient’s smart device registration phase
Step 1: A new smart device (SDj) selects an identity number (SIDj), password (SPWj), and security code (SSCj), whose values are formulated according to the system specifications. SDj generates a random number (R2) and computes Cj=h2(SIDj∥SPWj∥R2). SDj transmits the registration request message {M1: SIDj, Cj, and SSCj} to the GWN node through a secure communication channel.
Step 2: In response to the SDj request, the GWN node verifies the existence of identity SIDj in the table of registered patients. If it exists, the GWN node rejects the request and asks SDj to select another identity. Otherwise, the GWN node generates a random number (R3) and a secret key (Xj), whose value is saved securely. The GWN node initiates SNj=h0(R3), and computes SN=(SSCj⊕ SNj), SKj=h1(SIDj∥Xj), SFj=(SKj⊕ SSCj), and SVj=h1((SNj∥SSCj)⊕ (Cj∥SKj)). The GWN node initiates the pseudonym identity IDj=h1(SIDj∥SNj), and IDjp=IDjs=Φ, assigns a specific Pi to patient SIDj, and securely updates the list of patients for Pi. The GWN node adds the SDj record to the patient node table [SIDj, IDj, IDjp, IDjs, and SNj], and embeds the authentication parameters [SN, SFj, and SVj] in a new smartcard (SCj). The GWN node returns SCj to SDj through a secure communication channel.
Step 3: SDj receives SCj and stores R2 in SCj. SDj initiates and securely stores the session counter (C1j = 0).
2.2.3 WMSN Node Registration Phase
When a new WMSN node (Sk) is created as a sensor node to sense the physiological data of the patient or an actuator node to receive medical instructions from physician node Pi, the WMSN node must be registered in the patient’s smart device SDj. This is a unique characteristic of the proposed authentication scheme. The stage can prevent the use of the sensor node by someone other than the patient. Fig. 4 shows WMSN node registration, which connects Sk and SDj. The steps are as follows.

Figure 4: WMSN node registration phase
Step 1: A new Sk node sends a registration request message M1: SIDk to SDj though a secure communication channel, where the identity value (SIDk) of Sk is initiated when created by the healthcare service provider.
Step 2: In response to the Sk node request message {M1}, SDj randomly generates the session number SNk0=(R4) and initiates sensor sequence numbers SSk0=SSk1=0. SDj adds the Sk node record to the sensor nodes table [SIDk, SSk0, and SNk0]. SDj node securely sends {M2: SSk1, SNk0} to Sk.
Step 3: A new Sk node securely stores [SSk1, SNk0].
2.2.4 Physician Login Authentication Phase
To monitor patients through WMSN services, the physician activates the monitoring device (Pi) by authentication to the smartcard (SCi) obtained from the GWN node during physician node registration. Fig. 5 describes the physician login authentication phase between Pi and SCi. The main steps can be summarized as follows.
Step 1: Pi inserts (PIDi), (PPWi), and (PSCi) as the login authentication request to the SCi.
Step 2: In response to the Pi request, SCi fetches (R0) and computes Ci=h2(PIDi∥PPWi∥R0), PKi=(PFi⊕ PSCi), and XPVi=h1((SNi∥PSCi)⊕ (Ci∥PKi)). SCi verifies whether (XPVi) matches (PVi) as stored in its memory by the GWN node. If not, then SCi rejects the login request and terminates the session. Otherwise, authentication will pass, and Pi is considered a legitimate node and will be used by an authorized physician. SCi initiates the value of IDi=h1(PIDi∥SNi).

Figure 5: Physician login authentication phase
2.2.5 Patient Login Authentication Phase
To use WMSN services, the patient activates his/her smart device (SDj) to authenticate himself/herself to the smartcard (SCj) obtained from the GWN node during smart device registration. Fig. 6 describes the patient login authentication phase between SDj and SCj. The main steps are as follows.
Step 1: SDj inserts (SIDj), (SPWj), and (SSCj) as the login authentication request to SCj.
Step 2: In response to the SDj request, SCj fetches (R2) and computes SNj=(SSCj⊕ SN), Cj=h2(SIDj∥SPWj∥R2), SKj=(SFj⊕ SSCj), and XSVj=h1((SNj∥SSCj)⊕ (Cj∥SKj)). SCj verifies whether (XSVj) matches (SVj) as stored in its memory by the GWN node. If not, then SCj terminates the login request and the session. Otherwise, authentication is passed, SDj is considered a legitimate node, and it will be used by an authorized patient.

Figure 6: Patient login authentication phase
2.2.6 Smart Device Password Change Phase
This is accomplished between SDj and SCj when the patient wants to change a smart device (SDj) password. Fig. 7 shows the smart device password change phase between SDj and SCj without going back to the GWN node. The patient must execute the following steps:
Step 1: The patient inserts (SIDj), (SPWj), (SSCj), and a new password (*SPWj) through SDj as the request to change his/her password.
Step 2: SCj computes Cj=h2(SIDj∥SPWj∥R2), SKj=(SFj⊕ SSCj), and XSVj=h1((SNj∥SSCj)⊕ Cj∥SKj). SCj verifies whether (XSVj) matches (SVj) as stored in its memory by the GWN node. If not, then SCj rejects the request. Otherwise, SCj computes *Cj=h2(SIDj∥*SPWj∥R2) and a new verification code, *SVj=h1((SNj∥SSCj)⊕(*Cj∥SKj)). SCj replaces the new code with the old one (SVj=*SVj).

Figure 7: Smart device password change phase
2.2.7 Physician Password Change Phase
This is accomplished between Pi and SCi when the physician (Pi) wants to change his/her password. Fig. 8 shows the details of the physician password change phase between Pi and SCi without going back to the GWN node. The steps are as follows.
Step 1: The physician inputs (PIDi), (PPWi), (PSCi), and a new password (*PPWi) though Pi to request a password change.
Step 2: SCi computes Ci=h2(PIDi∥PPWi∥R0), PKi=(PFi⊕ PSCi), and XPVi=h1((SNi∥PSCi)⊕ (Ci∥PKi)). SCi verifies whether (XPVi) matches (PVi) as stored in memory by the GWN node. If not, SCi rejects the request. Otherwise, SCj computes *Ci=h2(PIDi∥*PPWi∥R0), and a new verification code *PVi=h1((SNi∥PSCi)⊕ (*Ci∥PKi)), and replaces the verification code with the new one (PVi=*PVi).

Figure 8: Physician password change phase
2.2.8 Long-Term Authentication Phase
A physician can monitor a patient’s medical state by gathering physiological data indirectly from the patient’s smart device through the GWN node. Therefore, the physician, through the monitoring device, must achieve mutual authentication with the GWN node and the patient’s smart device SDj, and to establish the subsequence session key with SDj. Fig. 9 shows the long-term authentication phase between the physician’s monitoring device Pi, the patient’s smart device SDj, and the GWN node as a service provider. The following steps are carried out.
Step 1: Pi initiates the authentication request message through SCi by inserting a patient identity (SIDj). Pi generates a random number (R5) and computes TPKi=(IDi⊕ PKi), where IDi was computed and PKi extracted during physician login authentication. Pi computes CTi0=ETPKi(TP0∥R5∥SIDj) and Vi0=h3(TP0∥TPKi∥SNi∥IDi∥R5), where TP0 is a current timestamp of Pi. Pi sends an authentication request message {M1: IDi, CTi0, and Vi0} to the GWN node through a public communication channel.
Step 2: Upon receiving M1 from Pi, the GWN node searches the table of physician nodes to find (IDip) and (IDis) based on IDi as received from Pi. One of the following cases will occur [18,26]:

Figure 9: Long-term authentication phase
Case 1: (IDi≠IDip) and (IDi≠IDis). The GWN node rejects M1 and terminates the session.
Case 2: (IDi=IDip) and (IDis≠Φ). The GWN node computes new values for SNi=h0(SNi), PKi=h1(PIDi∥Xi), and TPKi=(IDi⊕ PKi). The GWN node computes <TP0∥R5∥SIDj>=DTPKi (CTi0) and checks whether Pi can monitor the medical state of SIDj. If not, then the GWN node rejects M1 and terminates the session. Otherwise, the GWN node verifies the value of (TP0). If it does not hold, then the GWN node rejects M1 and terminates the session. Otherwise, the GWN node computes XVi0=h3(TP0∥TPKi∥SNi∥IDi∥R5) to verify whether (XVi0) matches Vi0. If so, then the GWN node renews IDis=IDip, and IDip=h1(IDi∥R5). Otherwise, the GWN node rejects M1 and terminates the session.
Case 3: (IDi=IDip) and (IDis=Φ). The GWN node computes new values for PKi=h1(PIDi∥Xi) and TPKi=(IDi⊕ PKi), and computes <TP0∥R5∥SIDj>=DTPKi (CTi0). The GWN node checks whether Pi can monitor the medical state of SIDj. If not, then the GWN node rejects M1 and terminates the session. Otherwise, the GWN node verifies the value of (TP0). If it does not hold, then the GWN node rejects M1 and terminates the session. Otherwise, the GWN node computes XVi0=h3(TP0∥TPKi∥SNi∥IDi∥R5) to verify whether XVi0 matches Vi0. If so, then the GWN node renews IDis=IDip and IDip=h1(IDi∥R5). Otherwise, the GWN node rejects M1 and terminates the session.
Case 4: IDi=IDis. The GWN node computes PKi=h1(PIDi∥Xi), TPKi=(IDi⊕ PKi), and <TP0∥R5∥SIDj>=DTPKi (CTi0), and checks whether Pi can monitor the medical status of SIDj. If not, then the GWN node rejects M1 and terminates the session. Otherwise, the GWN node verifies the value of (TP0). If it does not hold, then the GWN node rejects M1 and terminates the session. Otherwise, the GWN node computes XVi0=h3(TP0∥TPKi∥SNi∥IDi∥R5) to verify whether XVi0 matches Vi0. If so, then the GWN node renews IDip=h1(IDi∥R5). Otherwise, the GWN node rejects M1 and terminates the session.
Step 3: According to the values of PIDi and SIDj determined through M1, the GWN node computes the authentication session key PSij=h2((PIDi⊕ Xi)∥(SIDj⊕ Xj)∥SQij), where SQij is a sequence number of the current execution for long-term authentication. The GWN node fetches the SDj node record from the patient table and computes SKj=h1(SIDj∥Xj) and TSKj=(IDj⊕ SKj). The GWN node initiates session counter C0j=(C0j+1) and computes the pseudonym identity IDjp=h1(SIDj∥IDjp), SNj=h0(SNj), and IDj=h1(SIDj∥SNj). The GWN node generates random number R6 and computes CTj0=ETSKj(TGWN0∥R6∥PSij) and Vj0=h3(TGWN0∥PSij∥IDjp∥SIDj∥R6), where TGWN0 is the current timestamp. The GWN node sends an authentication request message {M2: C0j, CTj0, and Vj0} to SDj through an unsecure public communication channel.
Step 4: When M2 is received from the GWN node, the SDj node through the SCj computes ΔCj=(C0j-C1j). SDj checks whether 1≤ΔCj≤μ2, where μ2 is assigned based on system requirements. If not, then SDj rejects M2 and terminates the session. Otherwise, it retrieves SNj=(SSCj⊕ SN), computes SNj=h0(SNj) function for (ΔCj-1) times until (ΔCj-1)=1. SDj updates SN=(SSCj⊕ SNj), and computes IDj=h1(SIDj∥SNj) and TSKj=(IDj⊕ SKj), where SKj was computed during patient login authentication. SDj computes <TGWN0∥R6∥PSij>=DTSKj(CTj0). SDj checks the value of TGWN0. If it does not hold, then SDj rejects M2 and terminates the session. Otherwise, SDj sets IDjs=IDjp and computes IDjs=h1(SIDj∥IDjs) function for (ΔCj-1) times until (ΔCj-1)=1. SDj computes XVj0=h3(TGWN0∥PSij∥IDjs∥SIDj∥C0j) to verify whether XVj0 matches Vj0. If not, then SDj rejects M2 and terminates the session. Otherwise, SDj believes the GWN node is legitimate. SDj generates random number R7, and computes CTj1=ETSKj(TSD∥R7∥C1j) and Vj1=h3(TSD∥TSKj∥PSij∥IDjs∥R7), where TSD is the current timestamp of SDj. Then SDj sets C1ij=C0ij, and sends the response authentication message {M3: IDjs, CTj1, and Vj1} to the GWN node through a public communication channel.
Step 5: Upon receiving M3 from SDj, the GWN node fetches TSKj again to compute <TSD∥R7∥C1j>=DTSKj(CTj1), where the pseudonym identity IDjs=IDjp. The GWN node verifies the value of TSD. If it does not satisfy, the GWN node rejects M3 and terminates the session. Otherwise, the GWN node computes XVj1=h3(TSD∥TSKj∥PSij∥IDjs∥R7) to verify whether XVj1 matches Vj1. If not, then the GWN node rejects M3 and terminates the session. Otherwise, the GWN node believes SDj is legitimate. The GWN node generates random number R8 and computes CTi1=ETPKi(R8∥PSij∥TGWN1), where TGWN1 is the current timestamp. The GWN node computes Vi1=h3(PIDi∥PSij∥R8∥SNi∥TGWN1), and sends the response authentication message {M4: CTi1, and Vi1} to Pi.
Step 6: When M4 is received from the GWN node, Pi computes <R7∥PSij∥TGWN1>=DTPKi(CTi1) and checks the value of TGWN1. If it does not hold, then Pi rejects M4 and terminates the session. Otherwise, Pi computes XVi1=h3(PIDi∥PSij∥R8∥SNi∥TGWN1) to verify whether XVi1 matches Vi1. If not, then Pi rejects M4 and terminates the session. Otherwise, Pi believes the GWN node is legitimate. Pi computes Vi2=h3(PIDi∥PSij∥R8∥SNi∥(TP1-TGWN1)) and Vix=((TP1⊕ TGWN1)∥Vi2), where TP1 is the current timestamp of Pi. Then, Pi updates SNi=h0(SNi) and sets IDi=IDip=h1(IDi∥R5). Pi sends an acknowledgment message {M5: IDi, and Vix} to the GWN node.
Step 7: Upon receiving M5 from Pi, the GWN node computes TP1=((TP1⊕ TGWN1)⊕ TGWN1) and ΔTP=(TP1-TGWN1), and checks whether ΔTP exceeds the threshold μ3, which is assigned based on system requirements. If not, then the GWN node resends M4, with a fresh value of TGWN1, to Pi. Otherwise, the GWN node computes XVi2=h3(IDip∥PSij∥R7∥SNi∥ΔTP) to verify whether XVi2 matches Vi2. If not, then the GWN node rejects M5 and terminates the session. Otherwise, the GWN node believes Pi node is legitimate, and it updates SNi=h0(SNi), IDis=Φ, and SQij=(SQij+1).
2.2.9 Short-Term Authentication Phase
When a physician wants to monitor a patient’s medical status based on real-time data through a direct communication channel, physiological data must be received from the patient’s smart device without returning to the GWN node. In this case, the physician achieves mutual authentication with the patient’s smart device to prevent unauthorized access to the direct unsecured connection.
Fig. 10 shows the short-term authentication phase between the Pi and SDj devices. The following steps are carried out after long-term authentication:
Step 1: Pi initiates an authentication request message through SCi by inserting a patient identity (SIDj). SCi retrieves the authentication session key (PSij) generated during the last long-term authentication phase with SDj through the GWN node. Pi generates random number R9 and initiates a session counter, C0ij=(C0ij+1). Pi computes pseudonym identity ID0ij=h1(SIDj∥ID0ij), PSij=h1(PSij∥ID0ij), CTi2=EPSij(TPi∥R9∥C0ij), and Vi3=h3(TPi∥SIDj∥PSij∥ID0ij∥R9), where TPi is the current timestamp of Pi. Then, Pi sends authentication request message {M1: C0ij, CTi2, Vi3} to SDj.
Step 2: Upon receiving M1, SDj computes ΔCij=(C0ij-C1ij) and checks whether 1≤ΔCij≤μ1, where μ1 is assigned based on system requirements. If not, then SDj rejects M1 and terminates the session. Otherwise, SDj sets ID1ij=ID0ij, computes ID1ij=h1(SIDj∥ID1ij) function for (ΔCij-1) times until ΔCij-1=1. SDj calculates PSij=h1(PSij∥ID0ij) and <TPi∥R9∥C0ij>=DPSij(CTi2). SDj verifies the value of TPi. If it does not satisfy, then SDj rejects M1 and terminates the session. SDj computes XVi3=h3(TPi∥SIDj∥PSij∥ID1ij∥R9) to verify whether XVi3 matches Vi3. If not, then SDj rejects M1 and terminates the session. Otherwise, SDj believes Pi is legitimate. SDj generates random number R10 and computes CTj2=EPSij(TPj∥R10∥C1ij), where TPj is the current timestamp of SDj. SDj computes Vj3=h3(TPj∥SIDj∥PSij∥ID1ij∥R10), sets C1ij = C0ij, and sends the response authentication message M2: ID1ij, CTj2, Vj3 to Pi.
Step 3: Upon receiving M2 from SDj, Pi retrieves PSij, where the pseudonym identity ID1ij = ID0ij. SDj computes < TPj∥R10∥C1ij>=DPSij(CTj2), and Pi verifies TPj. If it does not satisfy, then Pi rejects M2 and terminates the session. Otherwise, Pi computes XVj3=h3(TPj∥SIDj∥PSij∥ID1ij∥R10) to verify whether XVj3 matches Vj3. If not, then Pi rejects M2 and terminates the session. Otherwise, Pi believes SDj is legitimate.

Figure 10: Short-term authentication phase
2.2.10 WMSN Node Authentication Phase
To exchange physiological data and medical instructions between smart device SDj and connected WMSN node Sk, mutual authentication between both is achieved in all authentication sessions. Fig. 11 shows the WMSN node authentication phase between Sk and SDj. The steps are as follows.
Step 1: To achieve mutual authentication with Sk, SDj determines its identity (SIDk) of Sk. SDj randomly generates a secret key (SKk), updates SNk0=h1(SNk0∥SIDk), and computes CTk=((SKk∥ST)⊕ h2(SNk0∥SIDk∥SSk0)), where the value of ST is used to determine whether SDj needs to receive physiological data or forward medical instructions. SDj computes the pseudonym identity IDk=h1(SKk∥SIDk) and Vk0=h3(ST∥SIDk∥SKk∥SNk0∥SSk0), and renews SSk0=SSk0+1. SDj sends an authentication request message {M1: CTk, Vk0, SSk0} to Sk through an unsecure communication channel.
Step 2: Upon receiving M1 from SDj, Sk computes ΔSSk = (SSk0-SSk1) and verifies whether 1≤ΔSSk≤μ0, where μ0 is assigned based on the system requirements. If not, then Sk rejects M1 and terminates the session. Otherwise, Sk sets SNk1=SNk0, computes the SNk1=h1(SNk1∥SIDk) function for ΔSSk times until ΔSSk-1=1.
Sk determines (SKk∥ST)=CTk⊕ h2(SNk0∥SIDk∥SSk0) and computes Vk1=h3(ST∥SIDk∥ SKk∥SNk1∥SSk0-1). Sk verifies whether Vk1 matches Vk0. If not, then Sk rejects M1 and terminates the session. Otherwise, SDj is considered a legitimate smart device for Sk. Then Sk computes SNk0=h1(SNk1∥SIDk), Vk2=h3(ST∥SIDk∥SKk∥SNk0∥SSk0), and IDk=h1(SKk∥SIDk); renews SSk1=SSk0; and computes SNk0=h1 (SNk1∥SIDk). Sk sends response authentication {M2: IDk, and Vk2} to SDj through an unsecure communication channel.
Step 3: When SDj receives M2 from Sk, SDj computes SNk0=h1(SNk0∥SIDk) and Vk3=h3(ST∥SIDk∥SKk∥SNk0∥SSk0), and verifies whether Vk3 matches Vk2. If so, then Sk is considered a legitimate WMSN node for SDj. Otherwise, SDj rejects M2 and terminates the session.

Figure 11: WMSN node authentication phase
3 Security Analysis
We discuss the security of the proposed authentication scheme. First, the BAN logic model is used to illustrate the validity of the mutual authentication service and secure session key [39]. Further analysis demonstrates that the scheme can resist all common attacks.
3.1 Formal Security Validation Using BAN Logic Model
The BAN logic model is used to validate the freshness, trustfulness and originality of the authentication messages exchanged between authentication nodes [41,42,46].
The login authentication and password change phases are not used frequently, and the registration phases are executed through secure communication channels. We concentrate on the soundness of the long-term, short-term, and WMSN node authentication phases. The basic notation and believing rules of the BAN logic model are summarized in Tabs. 2 and 3, respectively.
Table 2: Notation of BAN logic model

Table 3: Rules of BAN logic model

The lists the authentication phase goals, the idealized form of the authentication messages for the long-term, the short-term and WMSN node authentication phases, and the assumptions used in the verification process for the long-term, short-term, and WMSN node authentication phases are illustrated in Tabs. 4–6, respectively.
Table 4: Authentication phase goals

Table 5: Idealized form of authentication phase messages

Table 6: Initial assumptions of authentication phases

The physician node (Pi), GWN node (GWN), patient’s smart device (SDj), and sensor node (Sk) are considered the main involved principles in the security verification of the proposed authentication scheme.
In the long-term authentication phase, TPKi and TSKj are the secret keys used to symmetrically encrypt authentication messages, while sets of unrepeated timestamps (TP0, TP1, TGWN0, TGWN1, and TSD) and random numbers (R5, R6, R7, and R8) are used to guarantee the freshness of an authentication session. In the short-term authentication phase, PSij is a secret key used to symmetrically encrypt the authentication messages, while unrepeated timestamps TPi, and TPj and random numbers R9 and R10 are used to guarantee the freshness of the authentication session. SKk is the secret key used to symmetrically encrypt the authentication messages in the WMSN node authentication phase, while serial numbers SSk0 and SSk1 are used to guarantee the freshness of authentication sessions.
The basic BAN logic rules, idealized form, and assumptions in Tabs. 2, 5, and 6 are used to validate the authentication phases.
3.1.1 Validation of Long-Term Authentication Phase
The validation process of the long-term authentication phase can be summarized as follows.
Using (Mesg1), a1 (GWN◃IDi, CTi0, Vi0: 〈(TP0,R5)〉TPKi) can be seen. From (a1), (Assmp9), the belief rule, and the message meaning rule, a2 (GWN|≡Pi|~〈(TP0,R5)〉TPKi) can be obtained. Using (Assmp3) and the freshness conjuncatenation rule, a3 (GWN|≡#(〈(TP0,R5)〉 TPKi)) can be obtained. Using (a2), (a3), and the nonce verification rule, a4 (GWN|≡Pi|≡ 〈(TP0,R5)〉TPKi) can be obtained. Therefore, from (a3), (a4), and the session key rule, a5 (GWN|≡GWN↔SKPi) can be inferred, which represents (Goal1). Using (Assmp3), (a5), and the nonce verification rule, a6 (GWN|≡Pi|≡GWN↔SKPi) can be inferred, which represents (Goal2) as well.
Similarly, using (Mesg2), b1 (SDj◃C0j,CTj0,Vj0: 〈(TGWN0,R6)〉TSKj) can be seen. Therefore, from (b1), (Assmp11), the belief rule, and the message meaning rule, b2 (SDj|≡GWN|~〈(TGWN0, R6)〉TSKj) can be obtained. Next, using (Assmp6) and the freshness conjuncatenation rule, b3 (SDj|≡#(〈(TGWN0,R6)〉TSKj)) can be obtained. Then, using (b2), (b3), and the nonce verification rule, b4 (SDj|≡GWN|≡〈(TGWN0,R6)〉TSKj) can be obtained. Therefore, from (b3), (b4), and the session key rule, b5 (SDj|≡SDj↔SKGWN) can be inferred, which represents (Goal3). Using (Assmp6), (b5), and the nonce verification rule, b6 (SDj|≡GWN|≡SDj↔SKGWN) can be inferred, which represents (Goal4) as well.
Similarly, using (Mesg3), then c1 (GWN◃IDjs,CTj1,Vj1:〈(TSD,R7)〉TSKj) can be seen. So, from (c1), (Assmp10), the belief rule, and the message meaning rule, c2 (GWN|≡SDj|~ 〈(TSD,R7)〉TSKj) can be obtained. Next, using (Assmp3) and the freshness conjuncatenation rule, c3 (GWN|≡#(〈(TSD,R7)〉TSKj)) can be obtained. Then, using (c2), (c3), and the nonce verification rule, c4 (GWN|≡SDj|≡〈(TSD,R7)〉TSKj) can be obtained. Therefore, from (c3), (c4), and the session key rule, c5 (GWN|≡GWN↔SKSDj) can be inferred, which represents (Goal5). Using (Assmp3), (c5), and the nonce verification rule, c6 (GWN|≡SDj|≡GWN↔SKSDj) can be inferred, which represents (Goal6) as well.
Finally, using (Mesg4), d1 (Pi◃CTi1,Vi1:〈(R8,TGWN1)〉TPKi) can be seen. Thus, from (d1), (Assmp8), the belief rule, and the message meaning rule, d2 (Pi|≡GWN|~〈(R8,TGWN1)〉 TPKi) can be obtained. Next, using (Assmp1) and the freshness conjuncatenation rule, d3 (Pi|≡#(〈(R8,TGWN1)〉TPKi)) can be obtained. Then, using (d2), (d3), and the nonce verification rule, d4 (Pi|≡GWN|≡〈(R8,TGWN1)〉TPKi) can be obtained. Therefore, from (d3), (d4), and the session key rule, d5 (Pi|≡Pi↔SKGWN) can be inferred, which represents (Goal7). Also, using (Assmp1), (d5), and the nonce verification rule, d6 (Pi|≡GWN|≡Pi↔SKGWN) can be inferred, which represents (Goal8).