DOI:10.32604/cmc.2021.015720

| Computers, Materials & Continua DOI:10.32604/cmc.2021.015720 |  |
| Article |
Social Distancing and Isolation Management Using Machine-to-Machine Technologies to Prevent Pandemics
1College of Computing and Information Sciences, PAF KIET, Karachi, Pakistan
2Department of Computer Science, Lahore Garrison University, Lahore, Pakistan
3Department of Computer Science, Umm Al-Qura University, Makkah City, Saudi Arabia
*Corresponding Author: Muhammad Asif. Email: drmuhammadasif@lgu.edu.pk
Received: 01 December 2020; Accepted: 02 January 2021
Abstract: Social distancing and self-isolation management are crucial preventive measures that can save millions of lives during challenging pandemics of diseases such as the Spanish flu, swine flu, and coronavirus disease 2019 (COVID-19). This study describes the comprehensive and effective implementation of the Industrial Internet of Things and machine-to-machine technologies for social distancing and smart self-isolation management. These technologies can help prevent outbreaks of any disease that can disperse widely and develop into a pandemic. Initially, a smart wristband is proposed that incorporates Bluetooth beacon technology to facilitate the tracing and tracking of Bluetooth Low Energy beacon packets for smart contact tracing. Second, the connectivity of the device with Android or iOS applications using long-term evolution technology is realized to achieve mobility. Finally, mathematical formulations are proposed to measure the distance between coordinates in order to detect geo-fencing violations. These formulations are specifically designed for the virtual circular and polygonal boundaries used to restrict suspected or infected persons from trespassing in predetermined areas, e.g., at home, in a hospital, or in an isolation ward. The proposed framework outperforms existing solutions, since it is implemented on a wider scale, provides a range of functionalities, and is cost-effective.
Keywords: Coronavirus disease 2019; pandemic; machine-to-machine; industrial internet of things; social distance; geo-fencing
A pandemic is an outbreak of a disease that rapidly spreads over a wide geographic area, a country, or around the world, and affects a large proportion of the population with a high rate of virulent infections and fatalities. In the 20th century, influenza was declared a global pandemic three times, in 1918, 1957, and 1968. Pandemics have exerted widespread and deadly impacts on Hong Kong, Spain, and Asia [1,2]. In the 21st century, severe acute respiratory syndrome (SARS) emerged, resembling the ongoing coronavirus disease 2019 (COVID-19). SARS is considered the first pandemic of the 21st century and was followed by a second pandemic in 2009, the so-called “swine flu,” which afflicted 11%–21% of the global population. Several other epidemics have occurred in the 21st century, such as the Middle East respiratory syndrome (MERS), Ebola, and the avian flu, among others. While these epidemics were lethal and caused many fatalities, they did not develop into pandemics [3]. In December 2019, however, a precipitous outbreak of an unknown disease originating in Wuhan City, China began to expand rapidly and was given the name CoV-2 or COVID-19 [4]. The outbreak of COVID-19 has to date affected more than 213 countries. Over 12.1 million confirmed cases have been reported, including 550,000 casualties (statistics as of July 9, 2020).
The first known pandemic occurred in 1918. The outbreak of the Spanish flu was one of the deadliest events of that era, resulting in more than 100 million casualties in less than 16 weeks. In addition, two more pandemics occurred in the same era. The Asian and Hong Kong flu outbreaks took place in 1957 and 1968, respectively. In 1957, four million fatalities were reported worldwide due to the proliferation of influenza. Similarly, the H3N2 virus was declared a pandemic in 1968. The H3N2 virus originated in Hong Kong and took more than two million lives around the world. In November 2002, SARS emerged and led to 774 fatalities. It was followed by the swine flu, which was more lethal, claiming approximately 575,000 lives [5].
The outbreak of COVID-19 was declared a pandemic by the World Health Organization (WHO) on March 11, 2020. Since then, hundreds of millions of people have been in a state of lockdown that is affecting local and global economies, and severely hampering their growth prospects. Most countries are striving to keep their economies afloat, and seeking external aid to support their healthcare systems. Mitigation measures for the current pandemic would benefit from the implementation of state-of-the-art technologies, to help improve the global economy. The ultimate objective of this study was to present and provide such solutions. The impact of the shortcomings of many existing technologies to cope with the extent of COVID-19’s effects is being widely felt. Supply chain operations have been severely affected and forced into a partial shutdown, mainly due to the lack of implementation of the necessary technological advancements during this pandemic [6]. The region-wide statistics of COVID-19 cases as of July 9, 2020, as reported by WHO, are presented in Fig. 1.
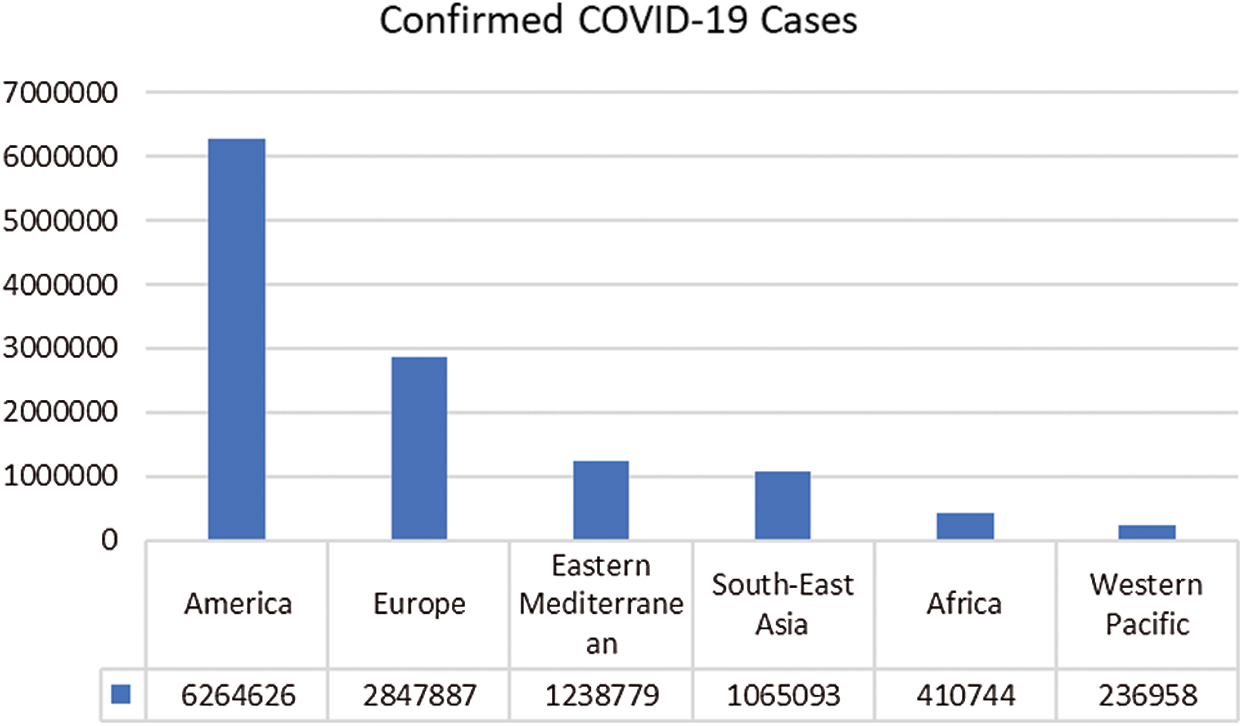
Figure 1: Regional comparison of COVID-19 cases
Moreover, the vulnerabilities of healthcare systems have been exposed due to their lack of preparation for managing such a situation. In the financial arena, the impact of COVID-19 on the stock markets has been ruinous, as highlighted by the charts in Fig. 2. The percent changes of the global market indices (on the y-axis) demonstrate how the stock exchanges of Shanghai, Hang Seng, Nikkei, Dow Jones, and the FTSE 100, respectively of China, Hong Kong, Tokyo, the United States, and London, have all been severely impacted since the declaration of emergency by the WHO. The world economy has been drastically affected in tandem by COVID-19. Meanwhile, the development of a vaccine is still in process and may not be completed soon. In the meantime, the WHO is continually issuing safety recommendations to the general public, including guidelines covering preventive measures in order to inform people of ways to mitigate the spread of the disease. Social distancing, for example, has been one of the strongly recommended preventive measures by the WHO for reducing the spread of COVID-19.
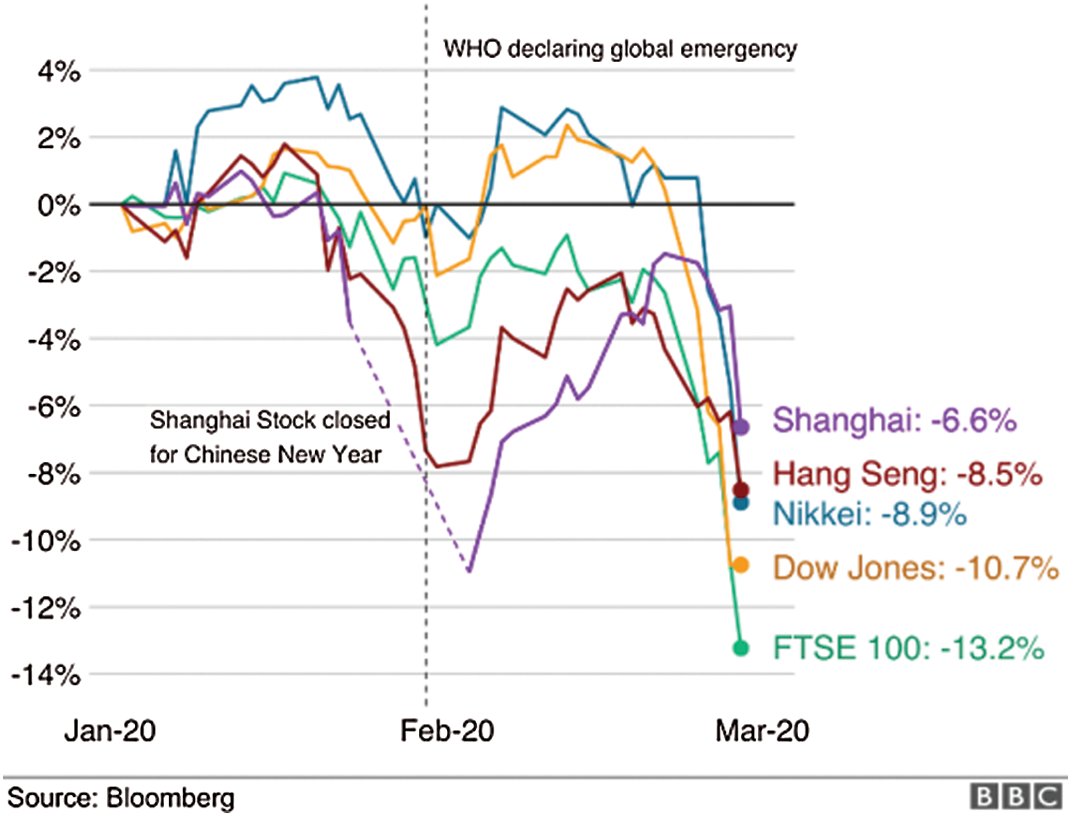
Figure 2: COVID-19 impact on stock markets [7]
Social distancing emphasizes sustaining defined distances between individuals in order to restrict the proliferation of virulent disease and manage pandemics. People are advised to keep at least one meter (about two arm’s lengths) apart and avoid close contact with individuals to adhere to the social distancing standard operating procedures of the WHO. When an infected person coughs, sneezes, or speaks, small liquid droplets containing fragments of a virus are released from the nose or mouth of the infected individual, disperse in the air, and land on the surrounding entities, thus spreading the virus and driving the pandemic. The WHO recommendations are intended to curb such situations.
In the era of influenza, when technology was not as advanced and knowledge was more limited, disease claimed many lives as a result of people not following social distancing. Social distancing was the sole intervention available. It was imposed by traditional lockdown, had a drastic impact on the economy of developing countries, and resulted in worldwide economic crises. The COVID-19 pandemic is occurring in the current era. The solution, an imposed lockdown that drastically impacts economies, is similar despite the advancement of technology.
In this study, several state-of-the-art technologies are described that can be adopted as effective and smart solutions for maintaining social distance. This research provides a comprehensive methodology for achieving smart social distancing and self-isolation management with the help of the Industrial Internet of Things (IIoT) and machine-to-machine (M2M) technologies. A wearable wristband that incorporates Bluetooth beacon technology for smart contact tracing and social distancing is proposed as an IoT device. This provides a smart mechanism for detecting the range and position of workers in offices, factories, and other sectors where employees interact and work together. Wearable device connectivity with the Android/iOS application is maintained in order to achieve mobility using long-term evolution (LTE). Finally, a few mathematical formulations are proposed to determine accurate measurements of the distances between the coordinates that indicate virtual boundaries in the form of circular and polygonal shapes. This helps to restrict suspected or infected people in a specified area, e.g., hospitals, quarantine centers, isolation wards, and other locations. The proposed solution not only reduces the spread of the disease but also acts as a catalyst to improve the economic conditions of any country.
The remaining sections of this manuscript are organized as follows. Section 2 presents a literature review and a brief overview of the technologies that are used to develop an advanced system to achieve social distancing and isolation management techniques. Section 3 describes the proposed system, including the implementation details for preventing the pandemic using advanced technologies. Analysis and discussion are presented in Section 4. Section 5 concludes the article and describes future work.
2 Literature Review and Related Technologies
Recently, various approaches have been taken by the research community to address COVID-19. Several researchers have targeted diagnosis and tracking strategies for the disease [8–12]. Most of the diagnosis-related research has been based on artificial intelligence (AI) techniques that use radiology images for early prediction of the disease. The disease-tracking domain exploits pattern matching and modeling techniques to estimate infected individuals and predict outbreak trajectories. Drug discovery is another prominent area of research for COVID-19. In this area, novel drug compounds are generated with the help of multiple AI techniques [13,14]. Several researchers have highlighted the necessity of awareness and social control by focusing on the detection of the cough types and temperatures of the suspected person through smart devices [15,16]. Social distancing is another critical area that requires attention since there are few published studies on this topic.
The following subsections provide a brief overview of the available technologies that are being used to develop a social distancing and isolation management system.
In early research on social distancing, researchers proposed targeted social distancing to mitigate influenza that emerged as a pandemic in the form of a respiratory disorder. These scientists simulated the spread of influenza within closed social contacts. Subsequently, they recommended the design for social distancing in a conventional community representing a small town in the United States [17].
The procedure for preventing the spread of influenza was to govern the social distancing through the identification of critically ill teenagers, their transmission routes of the virus to the target, and isolation of these individuals for prevention purposes [17]. The number of cases was reduced by safeguarding teenagers at home. The goal was to narrow the social circle by suspending schools, colleges, and universities, which ultimately proved to be a defense against the virulent disease in the absence of a vaccine.
2.2 Industrial Internet of Things
The IIoT refers to industrial devices or sensors that are connected to wireless networks and which gather and share data. The IIoT is significantly utilized in different sectors and industries [18]. IIoT devices can be in the form of actuators, sensors, and electronic chips. Objects gather data from their surroundings, after which they communicate and transmit the data over the Internet for the extraction of meaningful and necessary information [19]. There are hundreds of applications of the Internet of Things (IoT), e.g., home automation, fleet management, fuel telematics, weather broadcasting, and others. [20]. Industrial implementation of the IoT assists the automation and reinforcement of manufacturing, production, and industrial operations [21]. An overview of the applications of the IoT, IIoT, and Industry 4.0 is illustrated in Fig. 3.
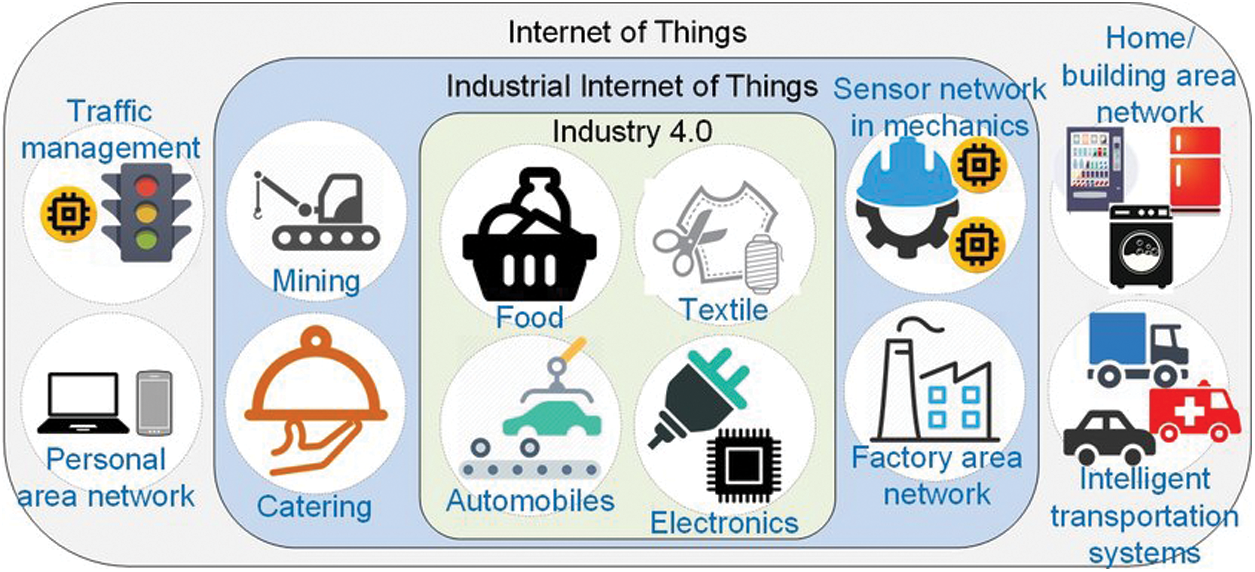
Figure 3: Schematic overview of applications of the IoT, IIoT, and Industry 4.0
M2M is a broad term encompassing any technology that permits devices to interact and share data autonomously. M2M communication is a key sanctioning technology for long-running industrial IoT applications, since no human intervention is required. It plays a vital role in the efficient connectivity and integration of computerized processing machines such as sensors, actuators, controllers, and robots. M2M communication comprises AI and machine learning that facilitates IoT devices to communicate automatically and provides an ultra-modern architecture for the smart communication of IoT devices [22]. The M2M architecture is shown in Fig. 4.
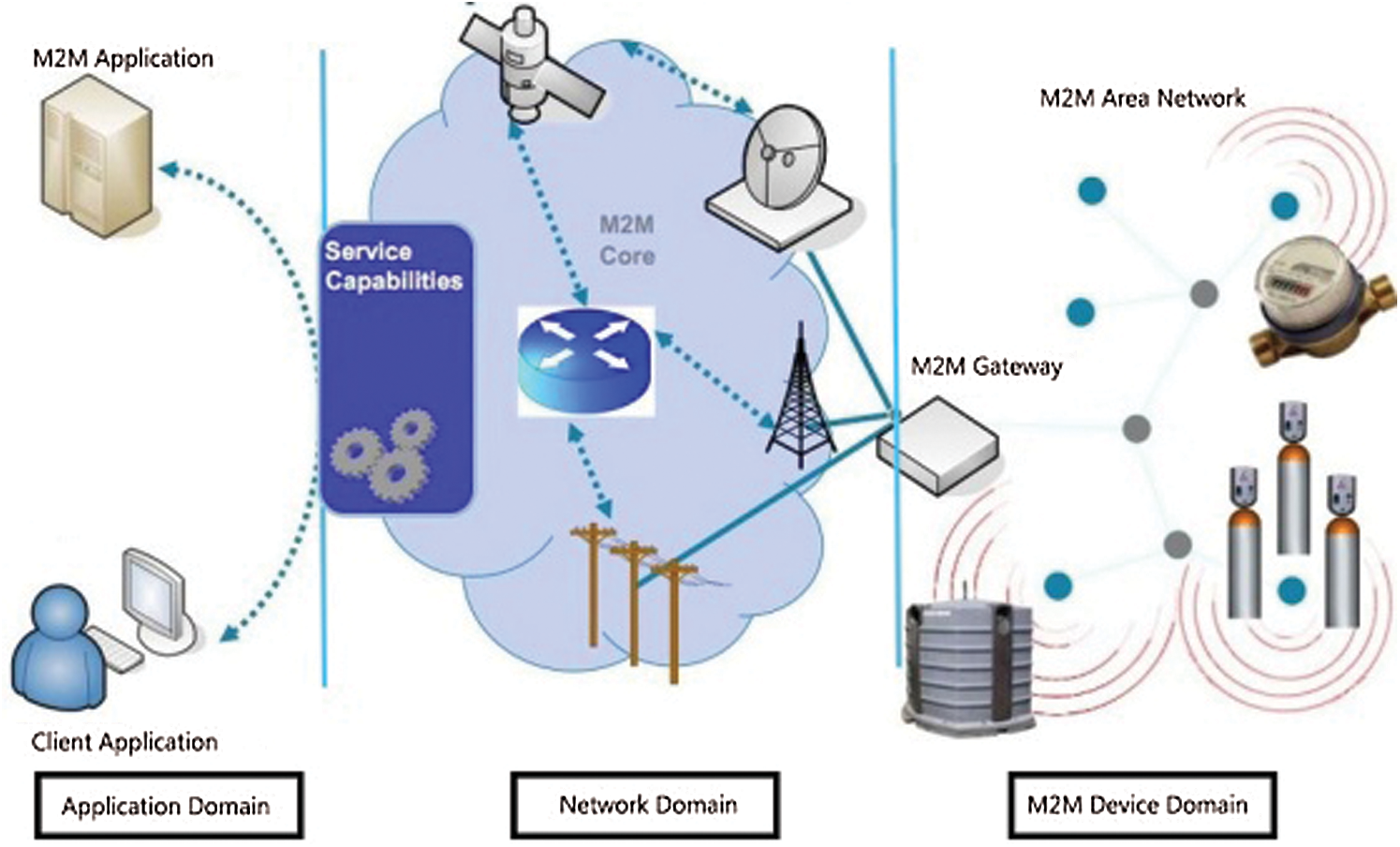
Figure 4: Simple M2M architecture
Geo-fencing can be described as a virtual boundary of coordinates around a desired geographical location. It is used as a service that helps to detect the entry and exit points upon receiving real-time GPS coordinates [23–25]. The different types of geo-fencing are shown in Fig. 5. The movement of subjects is determined for defined global positioning system (GPS) coordinates of specified areas, e.g., hospitals, quarantine centers, isolation areas, and other locations. The usage of geo-fencing is discussed later in the methodology section of this manuscript.
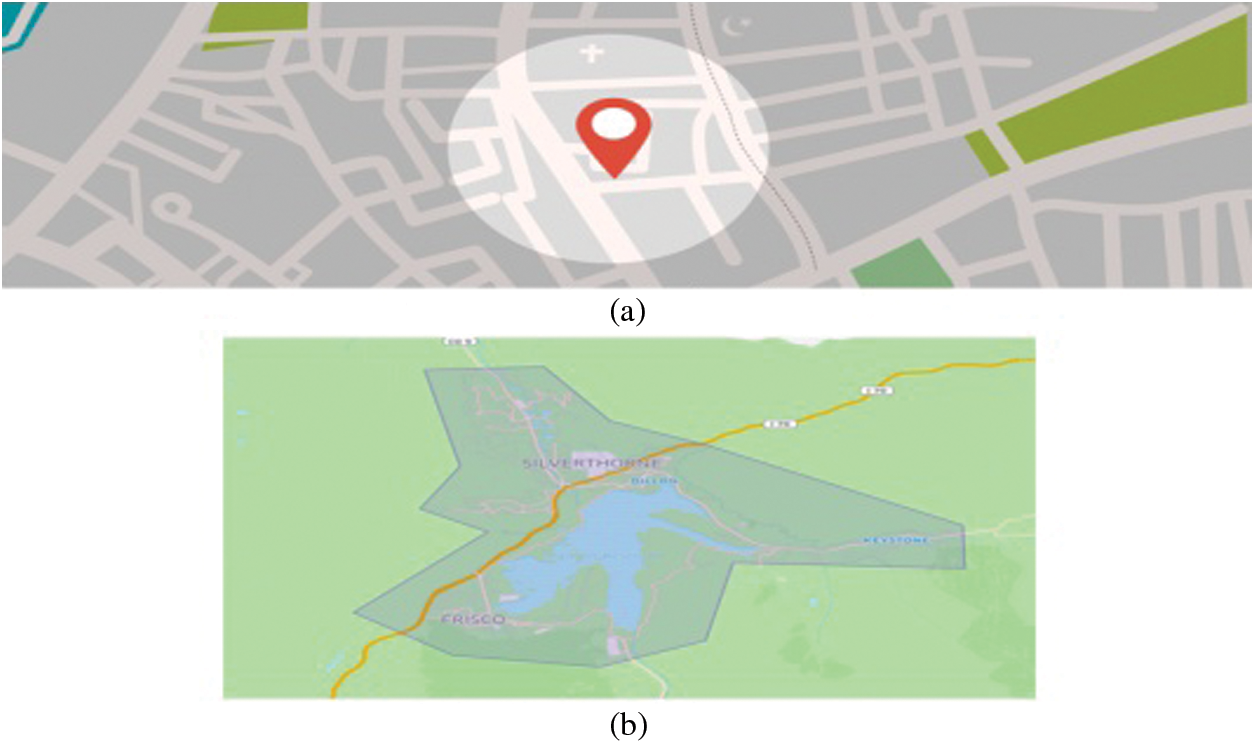
Figure 5: Geo-fencing examples (a) circular (b) polygon
Bluetooth technology was launched in 1999 with the core objective of providing short-range communication for data sharing. It has a short range of up to 100 m. Virtually every smartphone is equipped with this technology for data sharing, although a few disadvantages exist for short-range connections, e.g., a large number of devices are required to deploy coverage of large area networks. The problem that was identified in research on 802.11-based localization is the accuracy of judging the gap from a beacon due to complex signal propagation issues. This problem is mitigated by Bluetooth beacon technology [26].
Unlike other technologies, Bluetooth beacons are very economical and simple to deploy, and are therefore feasible for indoor localization. Solutions based on Bluetooth beacon technology can be implemented for the indoor environment along with the establishment of connectivity to a long-range wide-area network (LoRaWAN) router. This permits smart transmission of beacon packets to servers in order to provide contact tracing. Fig. 6 shows the way a Bluetooth-based mobile or any device transmits data to the server or over the Internet using a Bluetooth-based network. A similar model was adopted in this research, along with the addition of a LoRaWAN router that enables Bluetooth-based networks to route data from local devices to servers for smart utilization at the application layer.
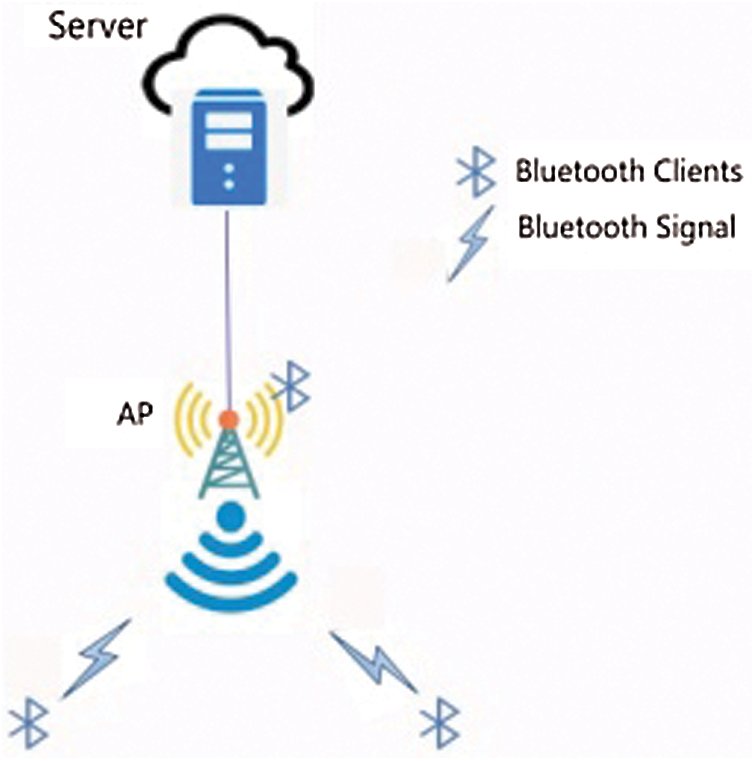
Figure 6: Bluetooth-based transmission of data to the server
Bluetooth beacons can act as an advertiser and continue to transmit signals after a specified interval of approximately 0.1 s. Similarly, at the other end, other devices or access points act as scanners, receive the signal, and perform appropriate actions accordingly.
Various procedures exist to attain localization using Bluetooth beacons, including cell-based methods, triangulation, and trilateration [26]. The triangulation method is inefficient for indoor localization, as it depends upon the line of sight of each beacon. Therefore, the cell-based method is used to determine the region of intersection of visible beacon ranges, since it determines the location of the traveler based on the visibility of beacons. Cell-based methods are not only popular for Bluetooth but also for radiofrequency identification (RFID) and infrared (IR) techniques.
Ultra-wideband (UWB) is one of the advanced wireless technologies, but it is extremely costly due to its high power consumption. UWB can be used to calculate distance in centimeters by measuring the signal time between receiver and transmitter and can be utilized to transmit data over short distances.
3 Proposed System and Implementation
The world is witnessing a crisis due to the persistence of COVID-19, and there is a huge need for social distancing solutions to increase the effectiveness of mitigation measures. Therefore, a wide range of low-energy Bluetooth-based M2M devices have been tested in order to manage the effective implementation of IoT devices that work on a low-power wide-area network and support bi-directional communication. Under these conditions, a single gateway can accommodate up to thousands of devices or nodes.
This section briefly elaborates on techniques and methodologies for the prevention of outbreaks through social distancing using IIoT and M2M technologies followed by smart isolation management based on geo-fencing. This section comprises four subsections. Hardware components to support the proposed technique for social distancing are briefly discussed in Subsection 3.1. Subsection 3.2 emphasizes the establishment of network connectivity between the sensors, router, and server. The step-by-step implementation of the social distancing technique is discussed in Subsection 3.3. The implementation of smart isolation management is demonstrated in Subsection 3.4.
The following components were utilized to develop the social distancing solution:
• M2M device (wearable wristband)
• LoRaWAN router
3.1.1 M2M Device (Wearable Wristband)
The proposed wearable wristband based on Bluetooth Low Energy (BLE) technology (used as an IoT device) is a sophisticated technology that has a low-power-consumption chipset with a rechargeable battery. The specific usage of this device is for contact tracing and personal positioning with continuous transmission capability, although a user application is also available for the configuration of the device, which makes it more convenient for implementation on a very large scale. For example, the user can set the connection type and interval of data transmission for the device. Moreover, it also supports BLE5.0, a three-axis accelerometer, and contains advanced security options such as encryption of credentials and data that are being advertised. The M2M wristband based on BLE beacons is shown in Fig. 7.

Figure 7: M2M wristband based on BLE beacons
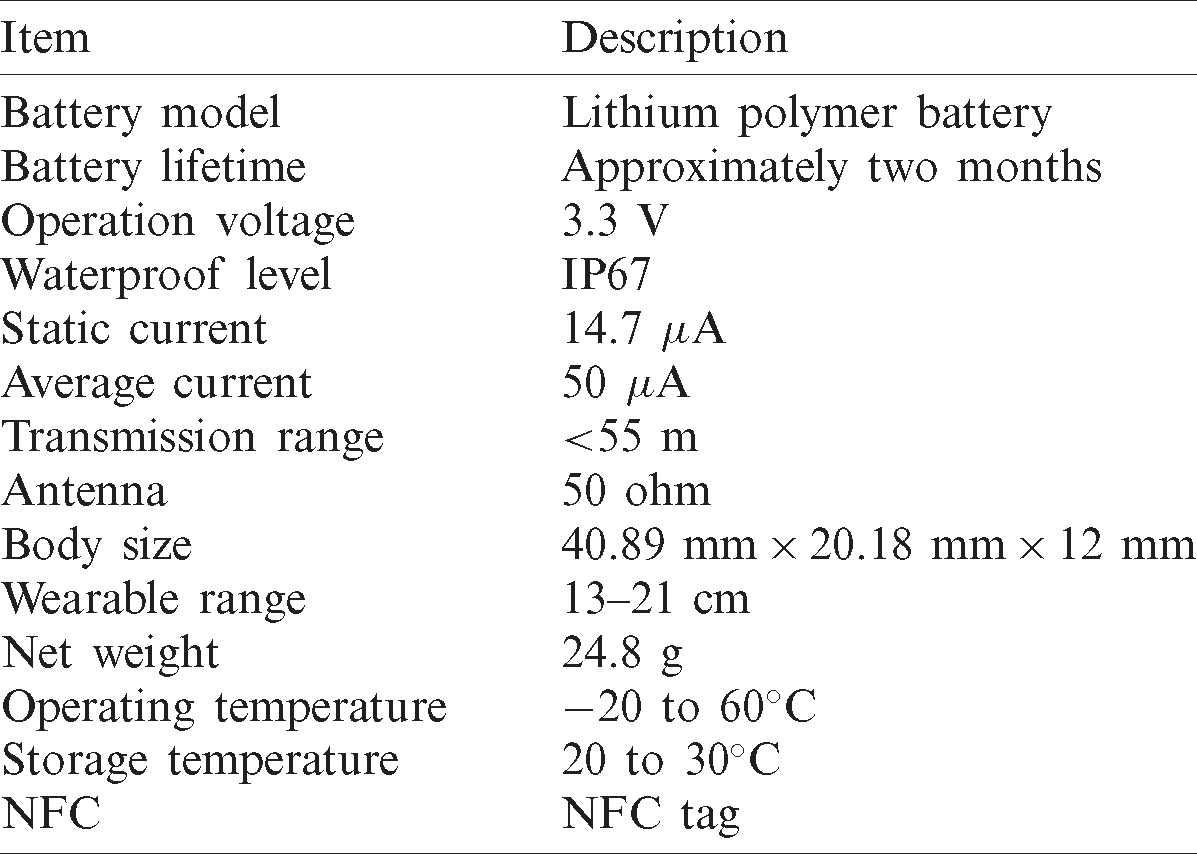
The specifications of the device make it more rigorous for contact tracing, social distancing, and isolation management. The specifications are listed in Tab. 1.
Table 1: Specifications of M2M wristband for social distancing
Contact tracing may be supported by providing wristbands to encourage end users to maintain social distancing. This helps to decrease the impact of the pandemic and to avoid the spread of virulent disease. Localization is managed using a cell-based method that depicts the intersection point based on visible beacon ranges [26]. These methods are prevalent in the implementation of short-range connectivity, e.g., RFID, Bluetooth, and infrared.
A LoRaWAN 8-channel gateway is proposed to operate in indoor locations. The gateway has a compact appearance and is easy to install on a roof, wall, or in an indoor environment [27,28]. A LoRaWAN router can be widely used in smart factories, smart buildings, smart offices, and other IoT systems. A LoRaWAN router is presented in Fig. 8, and its specifications are described in Tab. 2.

Figure 8: LoRaWAN router
Table 2: Specifications of LoRaWAN router

A small network comprised of IoT devices (wristbands), a LoRaWAN router, and a server was established to validate the technique of social distancing and depict the implementation of social distancing through technology (Fig. 9). IoT devices work both as transmitters and receivers. Multiple wristbands equipped with BLE beacons are connected to the LoRaWAN router and are utilized as a connecting medium between the IoT devices and the server. The wristbands support two-way communication and facilitate routing packets (generated by the wristbands) to the server. Subsequently, the data are utilized by the application layer to detect and respond with accurate distance violation alerts.
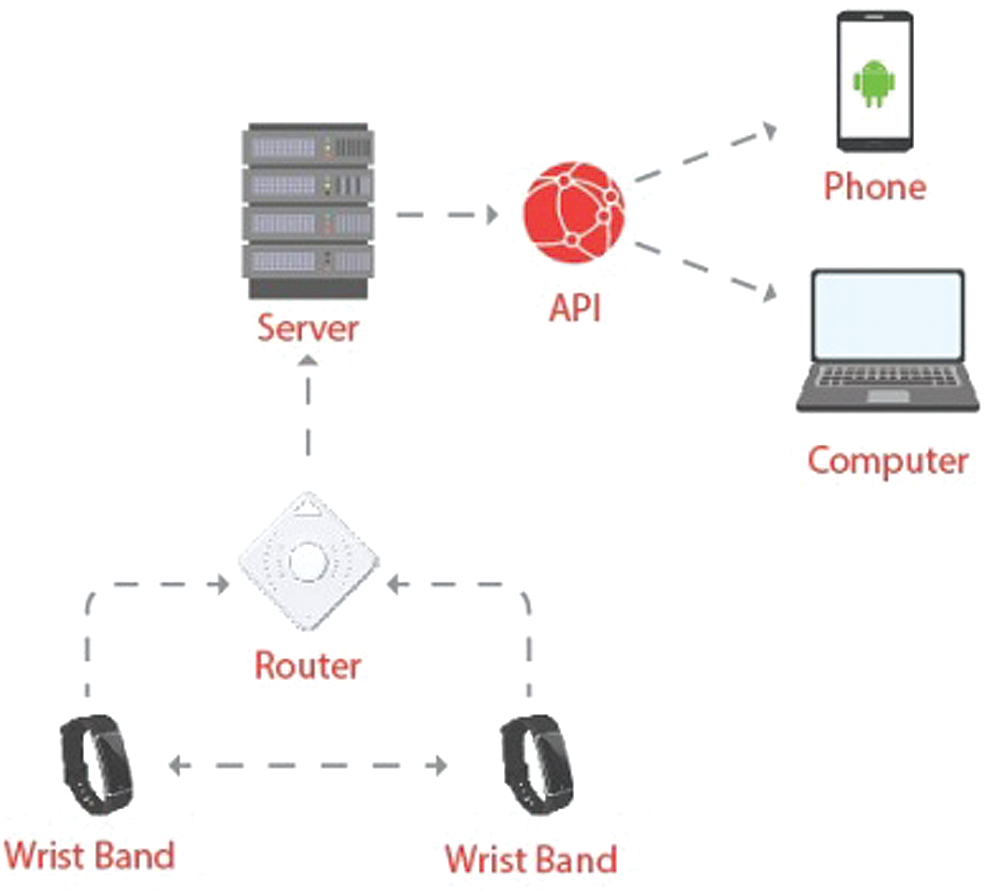
Figure 9: Data flow diagram for contact tracing
3.3 Implementation of Social Distancing Strategy
The implementation of a social distancing solution using M2M technology based on BLE beacons consists of the following steps.
Step 1: The LoRaWAN router is installed on the premises of the implementation area in order to capture signals from beacons and transmit the signals to the server or application layer for the detection of violations.
Step 2: Location is also preserved by restricting connectivity to a specific location for the range of the LoRaWAN router. Subsequently, wearable devices are configured to transmit packets to the servers. The following are the two essential functions that are considered as significant parameters for testing.
• Advertiser: The advertiser configuration settings are essential for setting the transmission interval of beacon packets, which can be configured through a user application. These settings also help to modify data content for the receiving medium. We enabled the broadcast trigger function for testing purposes and set its duration to one second, which served as the interval to obtain packets for the detection of distance violations. The transmission interval of the proposed device can be set from 1 to 65,535 s, as required.
• Scanner: The configuration of the scanner helps to scan and track the other violating device. We enabled this functionality to detect the violations of distancing such that upon violation, packets are transmitted to the server immediately through the network using the LoRaWAN router. The distance between the two bands is configured in meters to obtain instant notifications in the form of vibrations or a beep sound to alert users.
Step 3: After configuration, wristbands are turned in to the end-users for the exercise of social distancing and to keep track of contact tracing violations (Fig. 10).
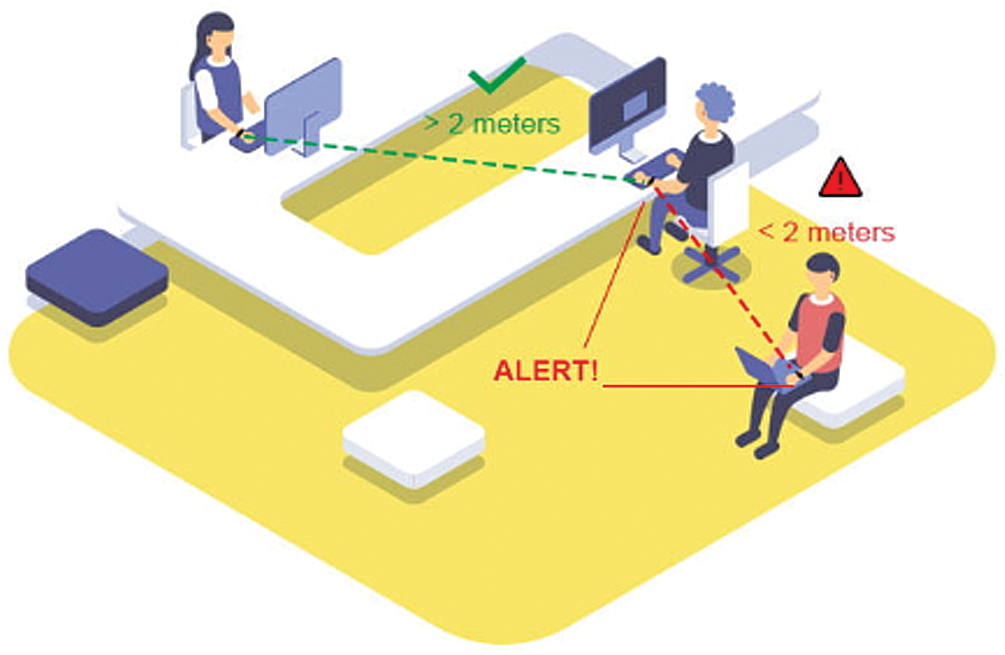
Figure 10: Demonstration of contact tracing
Step 4: Contact tracing logs generated by the IoT devices (wristbands) are helpful in monitoring and controlling the activities of users. The system-generated logs of successful testing are described in Tab. 3 as a proof of concept. The details in Tab. 3 reveal that the intruding incident information comprises the following attributes.
• Date and Time–-Incident timestamp
• Alert Name–-Incident name (i.e., distance violation/fence violation)
• Distance–-Calculated distance between the beacons when a violation occurred
• Employee ID–-Which employee or user wristband generated the violation alert
• Contacting Employee ID–-Which employee or user ID made contact with the wristband of the person who generated the alert.
Table 3: Intruding incident information

3.4 Implementation of Smart Self-Isolation Management
Another effective precautionary measure to overcome the pandemic is self-isolation management. This subsection comprises the extended implementation of a wearable device for isolation management. The proposed device has the proficiency to communicate with Android- and iOS-based applications (Fig. 11). This communication helps to transmit GPS and Beacon data to the server using the Global System for Mobile Communications/General Packet Radio Service (GSM/GPRS) or LTE, regardless of the dependence on any router to achieve mobility. LTE is defined as an Enhanced Data Rates for GSM Evolution (GSM/EDGE) and Universal Mobile Telecommunications Service/High-Speed Packet Access (UMTS/HSPA) technology-based standard for accurate and efficient transformation, which also enhances the speed and capacity of wireless data media. The mobility is achieved regardless of the range restriction of the router at a particular location using wristband and smartphone application connectivity (Fig. 11).
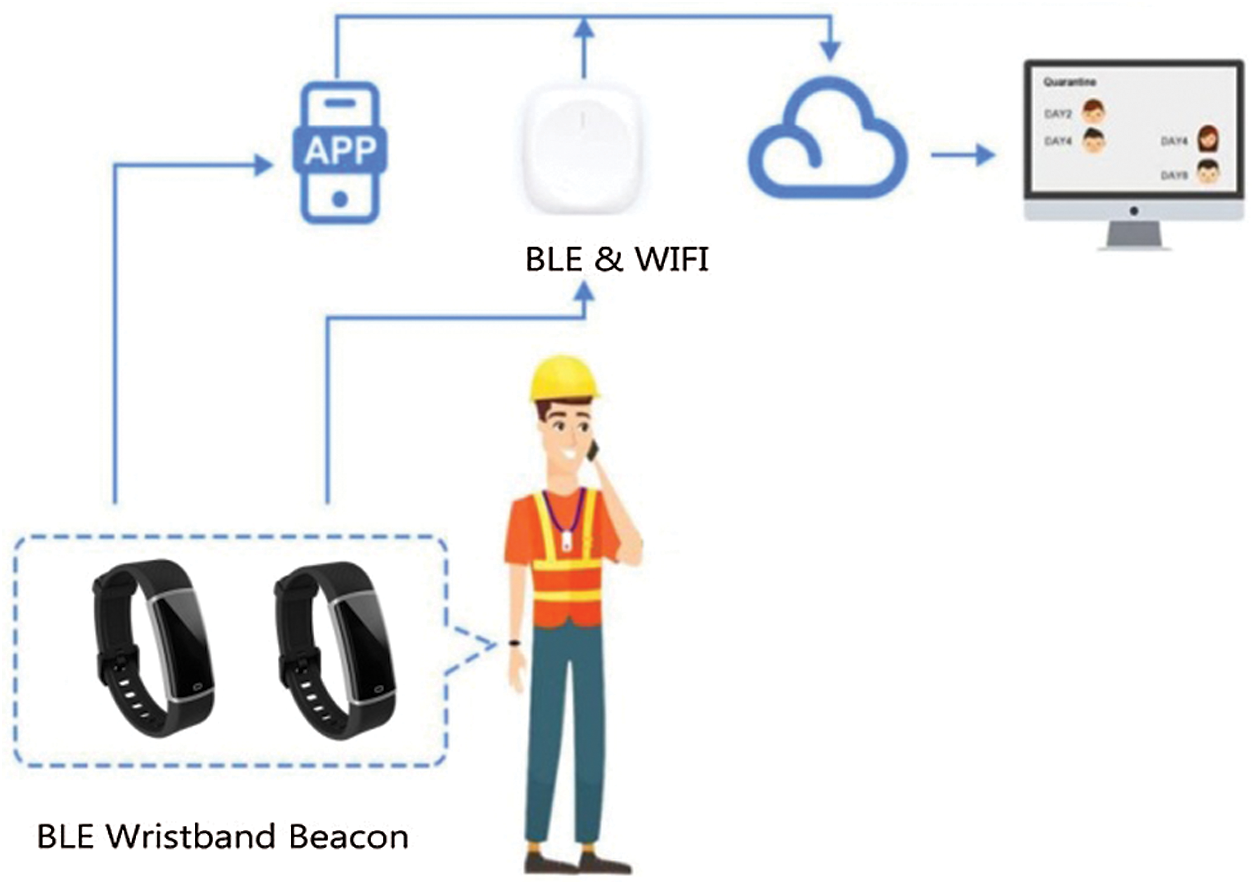
Figure 11: Data transmission
Raw data are transmitted to the phone from the device (Fig. 12); the details are as follows.
• The broadcasted data of the wristband are in standard iBeacon format.
• The response packet contains 0xFF02 non-BLE broadcast-type device service data (including signal strength, Tx power, connection, scan status, battery voltage, media access control, or MAC address) and complete local name (default: Tracker001).
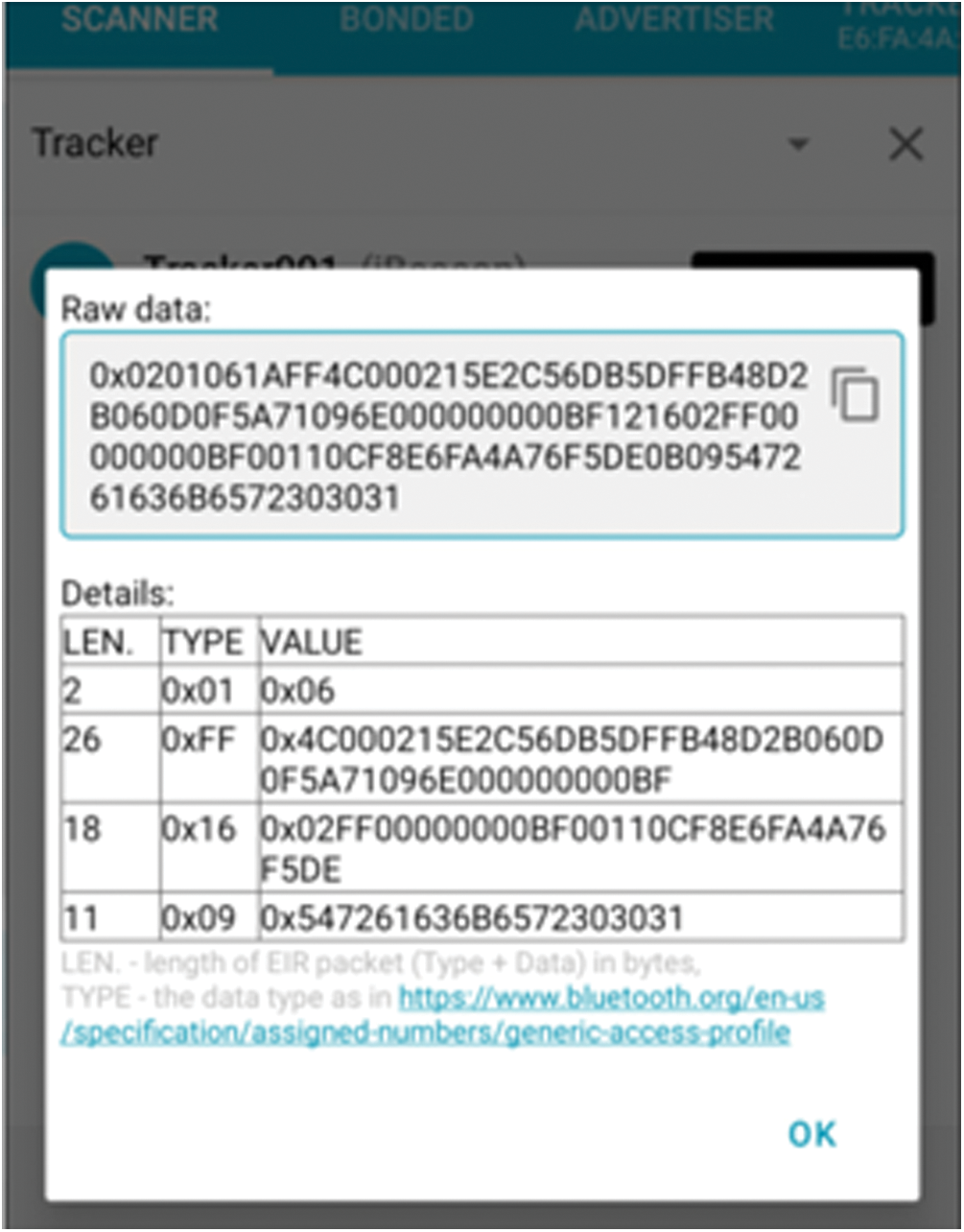
Figure 12: Broadcast data (wristband to a smartphone)
3.4.1 Geo-Fencing Creation for Isolation Management
Geo-fencing helps users to define the virtual boundary or desired fence for patients in hospitals, quarantine centers, and healthcare locations in order to confine them within specified boundaries through the proposed system. Real-time location based on GPS coordinates is obtained through the proposed device to determine the presence of a person inside or outside the fence. In this context, circular and polygonal fences are used to validate the proposed solution. The following steps are applied to achieve the objectives of smart isolation management.
Step 1: Polygonal and circular fences are created over Google Maps for the validation of the proposed techniques. The fences show the location of the quarantine center in order to refrain the mobility of users to a specified area. It was found that proper violation alerts are achieved through the implementation of proposed mathematical equations for distance calculation (discussed in the following section). Similarly, it was discovered that the proposed system can restrict patients to quarantine centers, hospitals, or isolation wards.
Step 2: Once fences are defined, wristbands are provided to users to permit device communication with smart applications. LTE technology is used to transmit coordinates to the server. If a contravention of the policies of the fence occurs, an alert from the smartphone application is sent to the concerned authorities, notifying them of the violation of a certain location and advising them to take necessary actions.
3.4.2 Proposed Mathematical Formulation for Self-Isolation Management
Traditional distance formulae have accuracy issues in detecting fence violations while implementing geo-fencing. Consequently, the following two mathematical equations were analyzed for the detection of distant violations and found to be 100% accurate. Initially, the Pythagorean theorem, as expressed in Eq. (1), is applied for both circular and polygonal fences in order to compute the distance for violation detection:

where (xp, yp) and (xc, yc) indicate patient and quarantine center coordinates, respectively, and D is the distance between the patient and the quarantine center coordinates.
Let R be the radius of the quarantine center. The patient is in the quarantine center if D < R, on its boundary if D = R, and outside the quarantine center if D > R. Implementation of Eq. (1) resulted in less accurate outcomes when assuming polygonal fences, since the radius applies only to circular areas. This deficiency eventually necessitated a smart approach to check polygonal fences. Therefore, to resolve this accuracy issue for polygonal fences, the Haversian formula was utilized and found to be ideal for spherical trigonometry. The Haversian formula is expressed as Eq. (2):
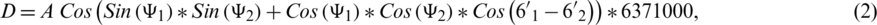
where (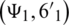 and
and 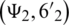 indicate the GPS coordinates of patient and quarantine center, respectively.
indicate the GPS coordinates of patient and quarantine center, respectively.
Eq. (2) achieved satisfactory results for polygonal fences, although it is not recommended for circular fences due to its computational complexity. The distance calculation in Eq. (1) is easy and accurate for circular fences. Hence, it is suggested that in the case of a circular fence Eq. (1) is more appropriate, while Eq. (2) is preferred for polygonal fences.
The following are the working steps.
• The device transmits GPS and iBeacon format data to a smartphone.
• The application in the smartphone receives the data and transmits them to the server.
• The server processes the GPS and iBeacon format data, calculates violations based on the geo-fencing policy, and maintains logs accordingly. Furthermore, the server also keeps track of devices that come into close proximity. The implementation details of geo-fencing are discussed in the following section.
Social distancing is one of the fundamental behaviors to be supervised in circumstances such as the COVID-19 outbreak in order to prevent pandemics. It has been noted that users will practice social distancing in public places to maintain a safe distance with each other using technology, which results in a lower number of positive cases and thus helps control outbreaks of the disease. Hence, technology plays a vital role in helping users maintain social distance, while also providing visibility and transparency for authorities who are attempting to monitor their activities and observe their interactions with one another. For instance, if an employee becomes a victim of a virulent disease, the system will help those concerned to identify his or her contacts using contact tracing logs rather than forcing a complete lockdown of the entire premises, which would ultimately affect production and negatively impact the economy. Therefore, the implementation of technology for contact tracing will not only prevent pandemics but also help to boost the economy even in pandemic-like situations.
Self-isolation management is also described in this study, which can be applied in quarantine centers or hospitals to restrict patients from leaving or violating the fencing policy. More advanced approaches for supervising heterogeneous fences can be considered with the implementation of smart isolation that may apply to diverse sectors. Contact tracing is imperative for practicing social distancing among individuals in order to reduce the impact of COVID-19. The preferred device imparts a contact-tracing mechanism followed by geo-fencing for self-isolation management.
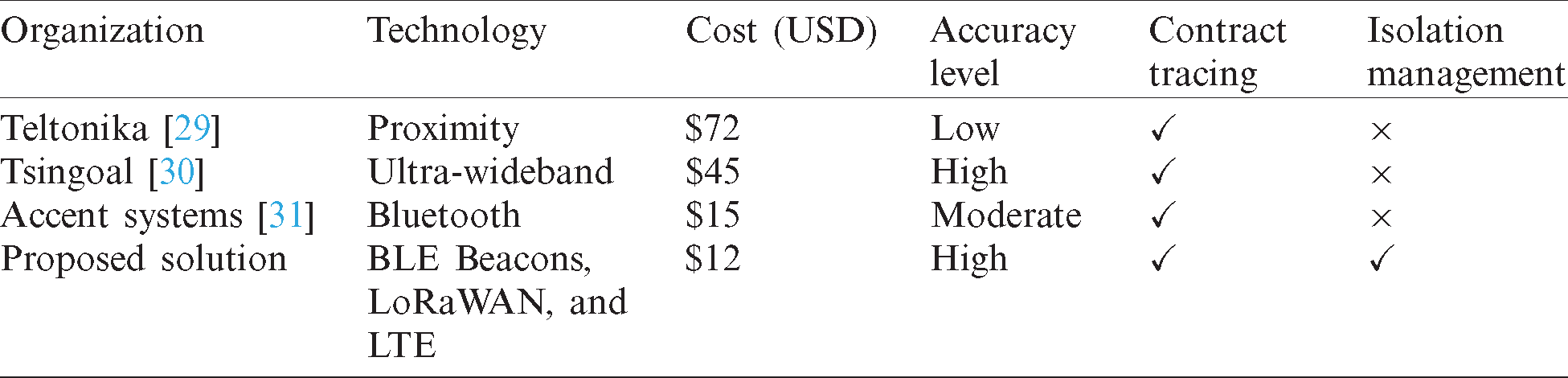
In response to COVID-19, IoT-based organizations are working on different technologies for smart contact tracing. Proximity and UWB technologies are being tested to serve this purpose. Teltonika [29] is one of the organizations that has been providing IoT-based solutions over the past 20 years, and its products and solutions are popular and utilized globally. Recently, Teltonika has launched an autonomous tracking device, which they call “GH5200,” as a proximity solution in response to COVID-19. This device works as an ID card holder and provides instant alerts upon violation of proximity rules for social distancing. It has been reported [30] that this IoT company has deployed over 1200 IoT-based systems worldwide and is also providing contact-tracing solutions based on UWB technology. UWB technology is significantly more expensive than BLE beacons, however. A comparison of the cost of devices using BLE, UWB, and proximity technology is presented in Tab. 4 to validate the possible economical implementation of our proposed solution on a large scale. In addition, Accent Systems is also an IoT-based organization that has launched BLE-based wristbands for contact tracing without a central authority mechanism. In contrast with our solution, their proposed devices store data internally for contacts and do not transmit to servers for centralized monitoring.
Cost is one of the significant factors to be considered when implementing solutions in a pandemic. UWB Tags, which are being proposed by some organizations, have an initial cost of $ 45. This is expensive compared with our proposed solution based on BLE beacons. Each embedded BLE beacon costs around $12, which is 26% less than the UWB tags.
A comparison of contact-tracing solutions from these organizations with our proposed solution is presented in Tab. 4. Proximity-and UWB-based solutions are much more expensive than beacons. In recent years, it has been observed that Bluetooth beacons are preferred for indoor localization services since they are economical and convenient. Similarly, our proposed solution is based exclusively on BLE beacons, which are embedded in wristbands, and available at an affordable price. These devices are portable, have a long battery life, and eliminate the need for an external power source. Moreover, we provide a single-desk operational structure for both contact tracing and geo-fencing functionalities, which differentiates our solution from the existing commercial products. Implementation of the proposed solution is simple and economical for wide ranges compared with other available solutions. Our solution is beneficial for users in public places such as hospitals, isolation units, and facility centers.
Table 4: Technology and cost-wise comparison of available solutions with the proposed solution
5 Conclusions and Future Directions
Research has substantiated that smart social distancing can be achieved using M2M technology based on IIoT devices. Bluetooth beacons play a significant role in contact tracing using two-way communication through the transmitter and receiver. In addition to social distancing, self-isolation management can also be achieved with smart devices using LTE technology. Hence, the effective implementation of M2M technology in wristbands based on BLE beacons is a revolutionary approach for stopping the spread of a disease that may result in a pandemic. Furthermore, industrial implementations of these IoT devices can assist countries in ways that allow businesses to function and simultaneously practice smart preventive measures that eventually stabilize and elevate the economy. Several organizations have financed low-cost devices based on proximity, BLE, and UWB that allow users to comfortably wear the devices and maintain a safe social distance. These technologies may be converted into Narrowband Internet of Things devices after refinements for other computational factors such as processing capability, power consumption, and battery life. In the future, advanced leading-edge technologies such as artificial intelligence, big data, and human-augmented machine learning-based social distancing frameworks may be introduced. Smart cameras may also be employed to monitor personal positioning, which will help to detect violations, corroborate the maintained distance, and fight pandemics. Improvements to the design of the wristband will allow it to have an active connection that will enhance the range of connected devices and help to achieve mobility with embedded GSM/GPRS connectivity.
Acknowledgement: We thank LetPub (www.letpub.com) for its linguistic assistance during the preparation of this manuscript.
Funding Statement: This research work is supported by Data and Artificial Intelligence Scientific Chair at Umm Al-Qura University, Makkah City, Saudi Arabia.
Conflicts of Interest: The authors declare that they have no conflicts of interest regarding the present study.
1. J. K. Taubenberger and D. M. Morens. (2006). “1918 influenza: The mother of all pandemics,” Emerging Infectious Diseases, vol. 12, no. 1, pp. 15–22. [Google Scholar]
2. E. D. Kilbourne. (2006). “Influenza pandemics of the 20th century,” Emerging Infectious Diseases, vol. 12, no. 1, pp. 9–14. [Google Scholar]
3. D. Huremovic. (2019). “Brief history of pandemics,” Nature Public Health Emergency Collection, PMCID: PMC7123574, pp. 7–35. [Google Scholar]
4. T. Singhal. (2020). “A review of coronavirus disease-2019 (COVID-19),” Nature Public Health Emergency Collection, vol. 87, no. 4, pp. 281–286. [Google Scholar]
5. World Health Organization (WHO). (2020). “Severe acute respiratory syndrome (SARS),” . [Online]. Available: https://www.who.int/ith/diseases/sars/en/. [Google Scholar]
6. L. Jones, D. Palumbo and D. Brown. (2020). “Coronavirus: A visual guide to the economic impact,” BBC, . [Online]. Available: https://www.bbc.com/news/business-51706225. [Google Scholar]
7. T. King. (2020). “What to do when the stock market plunges,” Invincible Robots, . [Online]. Available: https://invinciblerobots.com/stock-market-plunges/. [Google Scholar]
8. S. Wang, B. Kang, J. Ma, X. Zeng, M. Xiao et al. (2020). , “A deep learning algorithm using CT images to screen for corona virus disease (COVID-19),” MedRxiv, pp. 1–28, . [Online]. Available: https://www.medrxiv.org/content/10.1101/2020.02.14.20023028v5. [Google Scholar]
9. A. Narin, C. Kaya and Z. Pamuk. (2020). “Automatic detection of coronavirus disease (COVID-19) using X-ray images and deep convolutional neural networks,” ArXiv, pp. 1–17, . [Online]. Available: https://arxiv.org/abs/2003.10849. [Google Scholar]
10. L. Wang and A. Wong. (2020). “COVID-Net: A tailored deep convolutional neural network design for detection of COVID-19 cases from chest X-ray images,” ArXiv, pp. 1–12, . [Online]. Available: https://arxiv.org/abs/2003.09871. [Google Scholar]
11. X. Xu, X. Jiang, C. Ma, P. Du, X. Li et al. (2020). , “Deep learning system to screen coronavirus disease 2019 pneumonia,” ArXiv, pp. 1–29, . [Online]. Available: https://arxiv.org/abs/2002.09334. [Google Scholar]
12. Y. Wang, M. Hu, Q. Li, X. P. Zhang, G. Zhai et al. (2020). , “Abnormal respiratory patterns classifier may contribute to large-scale screening of people infected with COVID-19 in an accurate and unobtrusive manner,” ArXiv, pp. 1–6, . [Online]. Available: https://arxiv.org/abs/2002.05534. [Google Scholar]
13. A. Zhavoronkov, V. Aladinsjiy, A. Zhebrak, B. Zagribelnyy, V. Terentiev et al. (2020). , “Potential COVID-2019 3C-like protease inhibitors designed using generative deep learning approaches,” ChemRxiv, . [Online]. Available: https://doi.org/10.26434. [Google Scholar]
14. A. Makhzani, J. Shlens, N. Jaitly, I. Goodfellow, B. Frey et al. (2015). , “Adversarial autoencoders,” ArXiv, pp. 1–16, . [Online]. Available: https://arxiv.org/abs/1511.05644. [Google Scholar]
15. E. Maddah and B. Beigzadeh. (2020). “Use of a smartphone thermometer to monitor thermal conductivity changes in diabetic foot ulcers: A pilot study,” Journal of Wound Care, vol. 29, no. 1, pp. 61–66. [Google Scholar]
16. E. Nemati, M. M. Rahman, V. Nathan, K. Vatanparvar and J. Kuang. (2019). “A comprehensive approach for cough type detection,” in IEEE/ACM Int. Conf. on Connected Health: Applications, Systems and Engineering Technologies, Washington, D.C., USA. [Google Scholar]
17. R. J. Glass, L. M. Glass, W. E. Beyele and H. J. Min. (2006). “Targeted social distancing design for pandemic influenza,” Emerging Infectious Diseases, vol. 12, no. 11, pp. 1671–1681. [Google Scholar]
18. M. Banerjee, J. Lee and K. K. R. Choo. (2018). “A blockchain future for internet of things security: A position paper,” Digital Communications and Networks, vol. 4, no. 3, pp. 149–160. [Google Scholar]
19. X. Liang, J. Zhao, S. Shetty and D. Li. (2017). “Towards data assurance and resilience in IoT using blockchain,” in IEEE Military Communications Conf., Baltimore, MD, USA, pp. 261–266. [Google Scholar]
20. M. Conoscenti, A. Vetrò and J. C. De Martin. (2016). “Blockchain for the internet of things: A systematic literature review,” in IEEE/ACS 13th Int. Conf. of Computer Systems and Applications, Rome, Italy, pp. 1–6. [Google Scholar]
21. M. A. Khan and K. Salah. (2018). “IoT security: Review, blockchain solutions and open challenges,” Future Generation Computer Systems, vol. 82, no. 15, pp. 395–411. [Google Scholar]
22. Z. Meng, Z. Wu, C. Muvianto and J. Gray. (2017). “A data-oriented M2M messaging mechanism for industrial IoT applications,” IEEE Internet of Things Journal, vol. 4, no. 1, pp. 236–246. [Google Scholar]
23. F. Reclus and K. Drouard. (2009). “Geofencing for fleet & freight management,” in 9th Int. Conf. on Intelligent Transport Systems Telecommunications, Lille, France, pp. 353–356. [Google Scholar]
24. I. M. Almomani, N. Y. Alkhalil, E. M. Ahmad and R. M. Jodeh. (2011). “Ubiquitous GPS vehicle tracking and management system,” in IEEE Conf. on Applied Electrical Engineering and Computing Technologies, Amman, Jordan, pp. 1–6. [Google Scholar]
25. N. Chadil, A. Russameesawang and P. Keeratiwintakorn. (2008). “Real-time tracking management system using GPS, GPRS and Google earth,” in 5th Int. Conf. on Electrical Engineering/Electronics, Computer, Telecommunications and Information Technology, Bankok, Thailand, pp. 393–396. [Google Scholar]
26. S. S. Chawathe. (2008). “Beacon placement for indoor localization using bluetooth,” in 11th Int. IEEE Conf. on Intelligent Transportation Systems, Beijing, China, pp. 980–985. [Google Scholar]
27. F. Adelantado, X. Vilajosana, P. Tuset-Peiro, B. Martinez, J. Melia-Segui et al. (2017). , “Understanding the limits of LoRaWAN,” IEEE Communications Magazine, vol. 55, no. 9, pp. 34–40. [Google Scholar]
28. M. Rizzi, P. Ferrari, A. Flammini and E. Sisinni. (2017). “Evaluation of the IoT LoRaWAN solution for distributed measurement applications,” IEEE Transactions on Instrumentation and Measurement, vol. 66, no. 12, pp. 3340–3349. [Google Scholar]
29. Teltonika | Smart Autonomous Solutions. (2020). “COVID-19 IoT alliance,” Headquarter, Vilius, Lithuania, . [Online]. Available: https://teltonika-sas.com/about-us/covid19-alliance/. [Google Scholar]
30. TSINGAOL | Anti COVID-19. (2020). “Social distancing and impact tracking,” Beijing, China, . [Online]. Available: https://www.uwb-social-distancing.com/. [Google Scholar]
31. Accent Systems. (2020). “Contact tracing for Covid-19,” New York, USA, . [Online]. Available: https://accent-systems.com/. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |