DOI:10.32604/cmc.2021.015533

| Computers, Materials & Continua DOI:10.32604/cmc.2021.015533 |  |
| Article |
Robust Cluster-Based Routing Protocol for IoT-Assisted Smart Devices in WSN
1Department of Computer Science and Software Engineering, International Islamic University Islamabad, Islamabad, Pakistan
2Department of Computer Science, National University of Modern Languages, Islamabad, Pakistan
3Department of Computer Science, College of Computers and Information Technology, Taif University, Taif, 21944, Saudi Arabia
4School of Computer Science and Engineering (SCE), Taylor’s University, Selangor, Malaysia
5Department of Information Systems, College of Computer and Information Science, Jouf University, Al-Jouf, Saudi Arabia
*Corresponding Author: N. Z. Jhanjhi. Email: noorzaman.jhanjhi@taylors.edu.my
Received: 26 November 2020; Accepted: 11 January 2021
Abstract: The Internet of Things (IoT) is gaining attention because of its broad applicability, especially by integrating smart devices for massive communication during sensing tasks. IoT-assisted Wireless Sensor Networks (WSN) are suitable for various applications like industrial monitoring, agriculture, and transportation. In this regard, routing is challenging to find an efficient path using smart devices for transmitting the packets towards big data repositories while ensuring efficient energy utilization. This paper presents the Robust Cluster Based Routing Protocol (RCBRP) to identify the routing paths where less energy is consumed to enhances the network lifespan. The scheme is presented in six phases to explore flow and communication. We propose the two algorithms: i) energy-efficient clustering and routing algorithm and ii) distance and energy consumption calculation algorithm. The scheme consumes less energy and balances the load by clustering the smart devices. Our work is validated through extensive simulation using Matlab. Results elucidate the dominance of the proposed scheme is compared to counterparts in terms of energy consumption, the number of packets received at BS and the number of active and dead nodes. In the future, we shall consider edge computing to analyze the performance of robust clustering.
Keywords: Energy efficiency routing; load balancing; cluster selection
With the rapid growth in the internet of things (IoT) based WSNs, low-cost sensor nodes are manufactured to perform data collection, data transmission, and distant monitoring [1]. The applicability of green sensor nodes provides a broad-scale deployment of WSNs [2]. IoT-enabled smart nodes are resource constraints in terms of energy, computing capabilities, and availability of storage. Therefore, the minimum amount of energy should be consumed for robust routing mechanisms [3]. Efficient energy utilization within a network is a challenging task [4]. Smart sensing devices are utilized in several applications, including battlefield surveillance, structure inspection, target range imaging, and identifying ambient situations like heat, mobility, and noise [5]. The sensor nodes are mostly deployed randomly in hostile environments where the data is collected and shared with the sink node. It arises the need for efficient routing methods along with green computing [6]. The sensor nodes transmit data to the cluster head (CH) that forwards it to the sink or Base Station (BS) for further communication. The aggregated healthcare data is also saved at cloud repositories for further analysis [7]. IoT-enabled smart sensor nodes are suitable for resolving several physical world issues and sensing bottlenecks, where many smart devices exchange information [8]. It is infeasible in hostile environments after deployment to add energy sources in sensor nodes [9]. We consider hierarchical protocols for evaluating energy consumption, network lifetime, and load balancing.
The WSNs have a very limited lifespan owing to the fixed energy capacity of deployed sensor nodes. Consequently, energy-efficient routing is considered a challenging research domain in WSN [10]. Several existing strategies are presented to provide energy-efficient routing in WSNs. However, clustering-based protocols are commonly utilized for routing [11]. In [12], energy is efficiently employed while forwarding data packets towards the BS. Most of the routing based existing research studies have essentially focused on efficient energy consumption [13]. Sensor nodes generate a huge amount of data and transmission of this massive amount of data cause collision. A multi-channel transmission technique is utilized to reduce conflict among sensor nodes [14]. Several conventional routing strategies employed composite event detection to reduce energy consumption. However, centroid based routing enhances the performance of the network by utilizing efficient energy [15]. When communication among sensor nodes and BS is completed, a black hole attack occurs due to the random selection of CH [16].
This paper presents the Robust Custer Based Routing Protocol (RCBRP) that enhances the performance by considering efficient energy consumption. The system model involves sensor nodes, sublayer CH (SCH), CH, and BS. It considers clusters where CH is selected based on the highest weight that depends on maximum energy and shortest distance. The main contributions of this work are as follows;
1. We explored the literature for the routing mechanisms based on clusters of smart devices. Several secure routing strategies are considered.
2. We present the proposed RCBRP approach comprises of six phases like setup phase, initialization, distance calculation, cluster formation, CH selection, rotation, and communication.
3. We proposed the Energy Efficient Clustering and Routing algorithms.
4. We also proposed distance calculation and energy utilization calculation algorithms.
5. Finally, we utilize an efficient energy consumption mechanism to explore the energy utilization between all the nodes. Rotation of CH and SCH is also used for load balancing.
The rest of the paper is arranged as follows: Section 2 explores the literature review for existing routing schemes. Section 3 presents the six phases for the proposed RCBRP approach. Section 4 explores the results and analysis. Finally, Section 5 concludes our work.
In this section, several intelligent routing strategies are discussed. Moreover, IoT enabled WSN are based on intelligent devices that can collect the data from an observed field and communicate with other devices using a wireless link [17]. Data sharing from one node to another seems very easy but efficient transmission of data from sensor nodes to BS is an essential research topic in routing [18]. There do exist multiple algorithms for efficient routing. However, the lifetime of sensor nodes, load balancing [19], the consumption of energy [20], and transmission costs [21] are the main challenging issues in WSN. Several existing studies provide energy-efficient routing algorithms. In this scenario, LEACH [22] presents a clustering algorithm for periodic data collection. It is divided into two phases setup phase and steady phase. The setup phase provides the distribution of CHs, and the steady phase considers the direct transmission of data from CH to the sink node. LEACH-C [23] provides a selection of CH based on the higher residual energy of the nodes. EECS [24] presents an unequal size cluster formation approach while considering the distance from the sink. The existing scheme includes different related routing protocols like TEEN [25], APTEEN [26], LEACH [27,28], SEP [29]. Mostly, routing based schemes are introduced for minimizing energy consumption.
Likewise, TEEN is used to improve the network life [30]. In TEEN, not all packets reached the destination because of the dead nodes. A hybrid routing protocol APTEEN considers the efficient utilization of energy. It supports frequent data sharing in reactive and real networks [31]. PEGASIS forwards the data packets to BS in the ordered form [32]. It did not consider the energy level of CH for selection. It is one of the sequence-based protocols to enhance network life. HEED considers the remaining energy of sensor nodes [33]. Inferior nodes consume more energy as nearer to the BS and manage the additional load. Therefore, multi-hop routing utilizes more energy [34]. The reduction of signals, symmetric links are used but not considered statistical symbols. It transmits the symmetric key over the open network before the actual data packets transmission [35]. LEACH is a time division multiple approach based strategy. It applies to achieve efficient data communication among nodes and the randomly selected CH [36]. EECDRA reduces the route reconstruction cost towards mobile sink node by selecting optimal paths [37]. If the random number is selected between 0 and 1, then it is not be more than threshold as 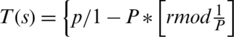 [38]. The energy of normal node is less than advance nodes. The probabilities of advanced node and normal node are
[38]. The energy of normal node is less than advance nodes. The probabilities of advanced node and normal node are 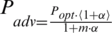 and
and 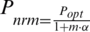 respectively where Popt is the probability of selecting an optimal one from all other nodes to covert as a CH [38]. In improved LEACH protocol, CH expands nodes locality when the distance between nodes is closed and sometimes distant from each other [39]. Several clustering algorithms enhance network lifespan by choosing the nodes with high residual energy [40]. For achieving energy efficiency, the LEACH protocol is utilized to select a specific number of nodes for sending data towards the BS. The decision of nodes is based on random numbers 0 and 1. In the existing round, the nodes become a CH if the total is fewer than the threshold. The percentage of CH is calculated in Eq. (1) [41] at this time
respectively where Popt is the probability of selecting an optimal one from all other nodes to covert as a CH [38]. In improved LEACH protocol, CH expands nodes locality when the distance between nodes is closed and sometimes distant from each other [39]. Several clustering algorithms enhance network lifespan by choosing the nodes with high residual energy [40]. For achieving energy efficiency, the LEACH protocol is utilized to select a specific number of nodes for sending data towards the BS. The decision of nodes is based on random numbers 0 and 1. In the existing round, the nodes become a CH if the total is fewer than the threshold. The percentage of CH is calculated in Eq. (1) [41] at this time 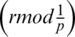 is the appropriate nodes in the round-robin cycle, P is used for the division of CH. In this Context, The Energy-efficient multi-hop LEACH-based clustering protocol elaborates the factors for the selection of the CH in LEACH protocol. EM-LEACH protocol is implemented to enhance the network lifespan and also improve the effectiveness of the energy [42].
is the appropriate nodes in the round-robin cycle, P is used for the division of CH. In this Context, The Energy-efficient multi-hop LEACH-based clustering protocol elaborates the factors for the selection of the CH in LEACH protocol. EM-LEACH protocol is implemented to enhance the network lifespan and also improve the effectiveness of the energy [42].

2.1 Cluster-Based Routing Protocols
In IoT-assisted WSN, many existing protocols are implemented to enhance the network lifetime and energy efficiency. The limited power of a battery is an essential factor in WSNs [43]. Different clustering methods are presented for minimizing energy consumption. In this context, the Leach algorithm decreasing network energy utilization [44]. The introduced algorithm is based on the steady and setup phase for communication and maintenance of clusters [45]. The introduced clustering algorithm reduces energy consumption in the CH selection procedure [46] An enhanced leach algorithm considers the nodes remaining energy, extensive space. It expands the remaining energy range to provide efficient energy consumption and also improve the CH selection criteria [47]. Reference [48] considers the remaining energy of nodes at CH for preserving these nodes’ energy while transmitting data among CH and the BS. Similarly, RPL consumes less energy and increases network lifetime [49]. The improved LEACH algorithm overcomes the defects of the existing leach algorithm while selecting the CH. In this trust aware approach, an energy-efficient heterogeneous method utilizes joint trust to optimally choose a path for communication in the network [50]. The RPL implements a new space path routing protocol of IPv6 to solve the energy problem [51]. Efficient energy consumption is one of the main challenging issues for future research studies in WSN [52]. The progress of IP-based, RPL protocol is an adequate practical standard. The outline of RPL permits to use of altered routing metrics and impartial occupation. For the optimization of the altered item, most of the RPL routing protocols are used. In WSN, sending the packet in the original time is responsible for normal sensor nodes [53]. Multi-hop is the transmission mode of inter-cluster in the arena of the ring. For the arrangement of limitations and metrics, RPL is used to determine the impartial occupation to construct the DoDAG. To established the track near the sink, every node combines with DoDAG [54]. CO-RPL optimizes the real RPL routing protocol for the selection of multiple paths [55]. Constructed centric rings provide equal distribution data for transmission and energy consumption in each ring is identical to cluster-based multi-hop transmissions [56]. In [57] every node checks the escaping time to determine the thresh hold value for clustering formation communication.
The energy-efficient algorithm EECBRA [40] is used for routing data towards the BS. The CH selection is based on maximum remaining energy and the smallest members of the clusters. Before the transmission of packets cost of energy and transmission is preserved. Due to filtering and data aggregation, casual blocking is decreased. The sensor collaborates with a CH for forwarding data towards BS [58]. The K-mean clustering algorithm divides the nodes based on clusters. Then, decide the optimal packet size based on condition channels, the transmitter’s radio parameters, and the receiver [59]. A clustering-based protocol employs a substantial amount of energy in the data communication phase. An uneven cluster formation approach is utilized for energy efficiency and load balancing [60]. The TRAF routing protocol is implemented for the collective networks in the conviction model. It considers security and load balancing. In a practical scenario, this algorithm is inefficient for energy. Therefore, TESRP provides efficient energy consumption. TLAR protocol is utilized for the intention of reliance on straight and secondary values. TESRP and TLAR protocols are not suitable for load balancing [38]. S-SEECH is implemented to evaluate the distance between the CH to the sink node. Many secure routing protocols are introduced due to the cause of attacks that can occur. Keys are utilized for minimizing the consumption of energy and improve performance [61]. The MAC algorithm improves the performance of the system. Hence, a holistic strategy is utilized to enhance system performance. The holistic strategy is the most suitable solution by comparing with single-layer based solutions because the Holistic method considers all network layers. The disadvantage of the holistic approach is that it consumes more time while implementing composite computations [62]. The advanced nodes have extra energy than the common nodes, and some specific kinds of routing protocols present for efficient energy utilization to enhances network life [63]. The nodes around the sink handling heavy traffic loads owing to battery power drop abruptly. The SEP method does not consider the change in energy and dominant nodes die first [64]. The introduced holistic approach makes the routing path energy efficient but this approach takes more time to compute the problematic scheme.
2.2 Energy Efficient Routing Algorithm
The routing protocol provides efficient energy utilization, secure data transmission, and authentication [65]. In [66], it considers the sink node’s distance to the neighbor nodes, energy consumption, and secure routing [67]. LEACH-TM depends on the energy effective routing protocol LEACH and provides trust aware secure routing protocol. An energy-efficient secure routing model is discussed to detect the black hole attack. It also increases network lifespan by decreasing the cost of energy [68]. The development of a secure and energy-efficient routing protocol is a challenging task [69,70]. The efficient protocols are implemented for improving the performance of the system. The opportunistic routing (OR) algorithm helps in the candidate node’s election and provides coordination between the sensor nodes. Moreover, EXOR is a novel approach that capable of performing data routing tasks efficiently [45]. Existing studies prevent different security attacks and also preserve the integrity of sensitive data [71]. In the OR algorithm, the election of candidates from the neighboring table is based on priority. The set selection for transmission is the limitation of this protocol [72]. RAEED-EA formally Analyzed Energy Efficient WSN routing Protocol. It is utilized for secure data routing and security against the DOS attack [73].
3 Proposed Robust Cluster-Based Routing Protocol
This section presents a new Robust Custer Based Routing Protocol (RCBRP) to enhance performance through efficient energy utilisation. The clustering method is utilized for the selection of CH on predefined criteria; each cluster is subdivided into smaller regions. We present six phases including initialization, setup phase, distance calculation, cluster formation, selection of CH, selection of SCH, and energy consumption model. Fig. 1a shows the layers of clusters that include sensor nodes, SCH, CH, and the BS. Firstly, we assume that sensor nodes are equally distributed in the network and send collected data to its perspective SCH. Moreover, SCH sends data towards the main CH. In the first round, when nodes send data to their perspective, CH their energy remains the same after completing the first round. It consumes more energy when the main CH sends data of all the clusters to the BS. This section defines the consumption of energy between all nodes to the BS. The rotation of CH and sublayer CH is used for load balancing. The node whose energy is less than the threshold value is considered a dead node. After completing all rounds, only those nodes take part that is alive. A list of notations is provided in Fig. 1b.
We present an energy-efficient routing protocol where we select CH and SCH based on weight. The weight is determined by considering the remaining energy and distance. Weights are calculated purely based on the minimum distance and maximum remaining energy of each node. The CH and SCH will be those nodes that have greater weight among their respective clusters. For low energy consumption, we introduce two factors. First, we divide the network into the main cluster and sublayer clusters. CH is selected from the main cluster that is closer to the BS whereas the SCH is selected among others. By introducing the concept of sublayer clusters, the distance among the normal nodes to SCH becomes smaller as the size of the sublayer cluster is small as well. Second, we introduce a threshold distance for SCH. When the distance of SCH is greater than the threshold, it will relay its data through other nodes based on their residual energy. Otherwise, it will directly forward the traffic to the CH. The threshold distance is saved energy consumption by maintaining the energy level of the work and preventing the farther nodes from dead early. Finally, we introduce BS at one corner of the network and the nodes at one side of the BS.

Figure 1: Proposed model for RCBRP in (a) and list of notations in (b)
The proposed model took only a single network and this model can help to integrate more networks with the same BS from other sides by introducing directional antennas. The main objective of this work is the selection of the optimal route to prolong the network lifespan. We proposed RCBRP to select the optimal path and maintain the energy load of the whole network. Due to clustering, RCBRP is also balancing the load. In phase-I, we distribute N sensor nodes randomly to set up a network. We assume that BS is placed outside the network, i.e., at one corner of the network. In phase II every sensor node first sends the initialization message or packet to the BS for initialization. In this context, each message contains the following fields, including Message-Id, Max-distance, CH-ID, Average Energy, and Authentication of CH. Sender’s id is utilized to forward the message from the sensor node to the BS. The coordinates of I and j show the location of the node. The sublayer is introduced for the information of CH. Energy levels are used to determine the energy of each node. Message-id is used to inform the receiver about the nature of the message. MAX-distance is considered to determine the distance to each node. The CH-ID is introduced to represent the ID of the CH in the clusters. Authentication ensures route security. The BS calculates the distance among each sensor node defines in the next phase. It sends a broadcast message to each node by using a feedback message comprised of the following fields; Sender’s Id, Coordinates of I, Coordinates of J, Energy Level, Sublayer information, and Authentication of BS. Steps of RCBRA defines in Tab. 1.
Table 1: Clustering and routing Protocol and cluster formation algorithm

During phase-III for distance calculation, nodes send the location information to the BS and the BS forwards feedback messages towards all the nodes to locate the distance of each node with the perspective of BS. The BS also does the clustering in the entire network. Function distance call explores the steps of distance calculation at BS. It calculates the distance from the perspective of the distance formula. In the setup phase, BS computes the distance of each node using its location. Each node exchanges the data packets with BS, and the distance is utilized to evaluate consumed energy as shown in Fig. 2a.

Figure 2: Distances are presented in (a) whereas distance and energy-based algorithm is presented in (b)
The distance formulae  calculate distance where (x2, y2) are the point of ith node’s location and (x1, y1) are the point of BS, respectively. Nodes forward position to the BS that sends a feedback message to all nodes and it consumes extra energy. Initially, the energy of all nodes is equal to 2 J. But for the transmission and reception of data, will consume energy. Function EnergyConsumptionCalc explores the energy consumption model given as
calculate distance where (x2, y2) are the point of ith node’s location and (x1, y1) are the point of BS, respectively. Nodes forward position to the BS that sends a feedback message to all nodes and it consumes extra energy. Initially, the energy of all nodes is equal to 2 J. But for the transmission and reception of data, will consume energy. Function EnergyConsumptionCalc explores the energy consumption model given as  . Fig. 2b illustrates both the functions for distance calculation and energy consumption. In the WSN, we assume to distribute the nodes in the network equally. Sensor nodes forward the position messages to the BS and the BS sends feedback messages to all the nodes and to locate the distance of each node from the BS. The BS performs clustering in the entire network.
. Fig. 2b illustrates both the functions for distance calculation and energy consumption. In the WSN, we assume to distribute the nodes in the network equally. Sensor nodes forward the position messages to the BS and the BS sends feedback messages to all the nodes and to locate the distance of each node from the BS. The BS performs clustering in the entire network.
In Phase-IV, clusters are formed according to the nodes’ location that are closer to form a cluster. We consider a rectangular region and divide our simulation region into 15 clusters where the size of the cluster is random. The CH is selected based on weight. Similarly, SCH selection is also based on weight. For example, the node with a higher weight is considered as the head node. The weight is calculated using distance and higher energy. CH will rotate during the communication but the cluster will not change. Likewise, once the clusters are formed, and the nodes are distributed in their respective clusters, they never change. Function cluster Formation explores the steps for the formation of a cluster.
In Phase-V, we select the CH based on the highest weight in the first layers whereas in the other layers we choose the SCH based on energy. The weight is assigned by using the highest energy and the shortest distance is given as  . A CH from each cluster is selected with a higher weight node and shortest distance as all the nodes’ initial energy level is the same. The function CH_SCH_Selection illustrates the consumed energy is calculated after completing the first round. The transmission of data continues until the threshold value does not reach. The process of rotation for CH and sublayer CH to balance the nodes in the clusters. Similarly, the distances between nodes to SCH, SCH to CH, and CH to BS are calculated. Function distanceCalc_CH_SCH explores the step to calculate the distance at CH by calculating the distance of SCH from all nodes. The threshold distance dth is used to segregate free space
. A CH from each cluster is selected with a higher weight node and shortest distance as all the nodes’ initial energy level is the same. The function CH_SCH_Selection illustrates the consumed energy is calculated after completing the first round. The transmission of data continues until the threshold value does not reach. The process of rotation for CH and sublayer CH to balance the nodes in the clusters. Similarly, the distances between nodes to SCH, SCH to CH, and CH to BS are calculated. Function distanceCalc_CH_SCH explores the step to calculate the distance at CH by calculating the distance of SCH from all nodes. The threshold distance dth is used to segregate free space  and multipath fading environment
and multipath fading environment  (amplification energy). The free space model is considered whenever the distance is inside the range of dth else the multipath model is used. Threshold distance is calculated as
(amplification energy). The free space model is considered whenever the distance is inside the range of dth else the multipath model is used. Threshold distance is calculated as  where d is the distance, Efs is the energy of free space and Eamp is the energy of amplification energy. In Phase-VI, communication takes place among nodes and their respective CH and SCH. Each node senses the data and relays it towards its respective CH. When the distance of threshold is within the range, use the free space model and if the threshold exceeds the multipath fading model. The hierarchy of communication flow is explored as follows; i) nodes transfer data to its head i.e., SCH (Nodes to SCH); ii) SCH collects the information from nodes and relays the traffic to CH; iii) CH collects information from all the SCH and its cluster as well; iv) CH relay the whole traffic of the network to sink node where the information is evaluated for forwarding to the final destination.
where d is the distance, Efs is the energy of free space and Eamp is the energy of amplification energy. In Phase-VI, communication takes place among nodes and their respective CH and SCH. Each node senses the data and relays it towards its respective CH. When the distance of threshold is within the range, use the free space model and if the threshold exceeds the multipath fading model. The hierarchy of communication flow is explored as follows; i) nodes transfer data to its head i.e., SCH (Nodes to SCH); ii) SCH collects the information from nodes and relays the traffic to CH; iii) CH collects information from all the SCH and its cluster as well; iv) CH relay the whole traffic of the network to sink node where the information is evaluated for forwarding to the final destination.
This section explores the results for total energy consumption, number of alive nodes, number of packets received by the BS, and energy utilization on each cluster. We conducted a Matlab simulation to extract results by comparing them with other existing schemes to validate our work. RCBRA completes 14000 rounds on average in its life cycle and its scalability is excellent. In the proposed work multi-hop path is selected by utilizing RCBRA protocol. Moreover, a fixed mobility pattern is adopted for the proposed scheme. A list of simulation parameters is illustrated in Tab. 2.
Table 2: Simulation parameters

A definite amount of energy is needed to forward information, but it is based on the specific levels. Eq. (2) explores the energy consumption during transmission. In the case of reception, energy consumption is calculated as  . In the equation, l is the length of the data packet, d is the distance of a particular node, et is the transmit energy, er is the receiving energy,
. In the equation, l is the length of the data packet, d is the distance of a particular node, et is the transmit energy, er is the receiving energy,  is the free space energy,
is the free space energy,  is the transmit amplifier energy and d
is the transmit amplifier energy and d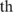 is the threshold distance calculated as
is the threshold distance calculated as  . In the first iteration, each node sends and receives a location message and feedback message. It determines the amount of energy needed for data forwarding and receiving the message. In the communication phase, the utilization of energy is individually determined for each level. While data communication from Nodes to head (RH), sensors take the data and transmit the data to BS by using a particular channel. In this context, the utilization of energy for data forwarding and receiving at the RH is considered as
. In the first iteration, each node sends and receives a location message and feedback message. It determines the amount of energy needed for data forwarding and receiving the message. In the communication phase, the utilization of energy is individually determined for each level. While data communication from Nodes to head (RH), sensors take the data and transmit the data to BS by using a particular channel. In this context, the utilization of energy for data forwarding and receiving at the RH is considered as 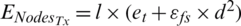 and
and  where n is the number of nodes (except RH) inside an RH.
where n is the number of nodes (except RH) inside an RH.

During data communication from SCH to CH, data forward from nodes to their SCH is obtained by RH. It is collected by SCH and send towards the subsequent level. The amount of energy is used throughout the process is estimated as  and
and  for transmission and reception where
for transmission and reception where 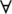 is the sum of nodes in an SCH. CH receives the data packets sent by SCH, aggregates the received traffic, and forwards towards the BS. The energy model evaluates the amount of energy consumed in the procedure which is given as
is the sum of nodes in an SCH. CH receives the data packets sent by SCH, aggregates the received traffic, and forwards towards the BS. The energy model evaluates the amount of energy consumed in the procedure which is given as  where
where 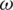 is the sum of SCH in the network. Data packets transmitted from each node are aggregated at CH and forward to the BS. The amount of energy needed to transmit the data towards the BS is calculated as
is the sum of SCH in the network. Data packets transmitted from each node are aggregated at CH and forward to the BS. The amount of energy needed to transmit the data towards the BS is calculated as  where N is the total number of WSs in a network [74].
where N is the total number of WSs in a network [74].
Fig. 3a illustrates the energy consumption comparison for a smaller number of rounds. We determined that LEECH-C spends more energy. The network’s total energy is 200 joules and each protocol consumes its entire energy but the difference is in their lifetime. The difference is due to the poor energy management and the worst energy management is in LEACH-C as it consumes all the energy at approx. 400 rounds. LEACH and EECRP consume energy at different rounds which are approx. 580 and 720 respectively. It can be seen that LEACH-C starts consuming more energy as compared to the other protocols due to which it dies quickly. EECRP is proposed to be better among all of the others, as it consumes the whole energy at 720 rounds. Energy utilization of our RCBRP protocol. The straight-line presents the network’s highest energy and it is analyzed according to the total network energy. We have increased the number of rounds up to 14000 in simulation scenarios to analyze the performance further. The energy consumption has a constant slope from 1000 to 9000 that shows the linear division of the energy in the network. There is no dead node up to 9000 rounds. After 9000, the nodes start dying and the energy consumption becomes nonlinear. The total energy of the network is consumed at 14000 to expire the network. The only reason for the longer network life is efficient load balancing which helps to improve the network lifetime. The maximum packets are delivered are at 11000 rounds and its value is 9.4 * 105. After 11000, packet delivery starts decreasing because dead nodes will increase, which will adversely affect the packet delivery ratio. Due to energy management, results show quite better management in RCBRP as compared to counterparts. Fig. 3b represents the energy consumption where the network’s initial energy is set to 200 J (2 J for each node) with a total of 100 nodes. In this context, we examined that with the increasing number of rounds energy utilization also enhanced. Initially, the energy consumption at 1000 rounds is 20 J, whereas it gradually increases to 200 J at 14000 rounds. The change in slope after 12000 rounds shows that there is less consumption at this point, and it is because the dead nodes start increasing whereas the total consumption decreases as shown in Fig. 3c. The energy consumption of the clusters starts increasing with the number of rounds. Similarly, residual energy starts decreasing. The difference in energy consumption of each cluster is because of the diverse size, different geo-location from BS and main cluster. The cluster which is farther from the main cluster will consume higher energy because its distance is greater than the others. Distance performs an essential role in the utilization of energy and it is the main reason each cluster consumes energy differently. Cluster 1 is the main cluster and it consumes greater energy because it relays the whole network’s data to the sink node. Cluster 4, cluster 6, cluster 2, and cluster 10 are the clusters that are farther from the main cluster and some of them relay the data of the other clusters to CH, though they consume higher energy. The threshold distance determines whether the SCH’s distance is greater than the predefined threshold. Then, the traffic is relayed through other clusters (these clusters will be in between the farther clusters and main cluster) then normal communication will take place.


Figure 3: (a, b) Energy consumption, (c) each cluster’s energy consumption, (d, e) number of alive nodes and (f, g) number of packets received by the BS
4.2 Number of Dead and Alive Nodes
Dead or expired nodes are observed due to extra energy consumption. Energy is consumed when the nodes relay data to the SCH, SCH relays data to CH, and CH to BS. The network keeps working until any of the nodes reaches a certain threshold with reduced energy to declare a dead node. The dead nodes are eliminated from the communication. Results are compared to check the effectiveness of the proposed scheme RCBRP with their counterparts. The most important parameter of the routing protocol is to indicate those sensor nodes that are alive. Fig. 3d illustrates that in the case of LEECH-C the first node dies approximately at 100th rounds and in LEECH, and EECRP the first node dies after at 400th round approximately. By analyzing the life cycle we observed that LEECH-C runs approximately for 420 rounds, LEACH remains alive for roughly 580 rounds. GEEC is quite better than the previous two’s as it runs for 680 the best one which is proposed stays alive for 720 rounds. RCBRP protocol achieves far better results as compared to LEECH, LEECH-C, and EECRP protocols. The first node dies at 80 rounds, 400 rounds, 380 rounds, and 380 rounds in LEECH-C, LEACH, GEEC, and EECRP, respectively. Fig. 3e presents the comparison of active nodes based on the number of rounds. We can say that as the number of rounds are increased the dead nodes also increased. Firstly, at 1000 rounds, all the nodes are active and working effectively. Similarly, the working of the network remains constant until 9000 rounds, after that the network consistency starts breaking. From 10000 to 14000 rounds, the dead nodes start increasing and it affects the active working of the network. At 14000 rounds, there are only 52 nodes alive but the network stops working because the network is no more balanced and it reaches a critical energy level.
4.3 Number of Packets Received by the Base Station
Fig. 3f presented the total received packets at BS. EECRP and LEECH protocol approximately completing 800 rounds to forward data packet towards the BS, LEACH transmits a maximum of 52000 (approx.) packets to BS, LEACH-C transfers approx. 42000 packets, EECRP relays approx. 60000 packets. The changes in the delivered packets considering the rounds are due to the dead nodes. The Sooner the node dies lesser packets will be relayed and the network dies prematurely. Network life is very important and directly related to packet delivery. Greater the network life more packets will be delivered. EECRP delivers more packets than LEEACH and LEEACH-C. The total number of delivered packets are analyzed at each round, therefore, as the rounds increase the packets delivery ratio also increases. Results prove that RCBRP delivered more number of packets as compared to its counterparts. Fig. 3g reflects the delivery of the packets from nodes to the BS. The number of packets increases with the increase of rounds. These are the packets (information) sense by the sensor and relayed to the sink node. A constant slope from 1000 to 9000 shows that each node is alive and delivering information, and a disjoint slope, from 10000 to onward, indicates the dead nodes. At 1000 rounds, the number of delivered packets is  , and there is a constant increase till 9000 rounds which shows that the delivered packets are
, and there is a constant increase till 9000 rounds which shows that the delivered packets are 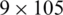 . After 9000 rounds, the dead nodes start increasing, so they don’t transfer any more packets and the curve starts decreeing with the increase in rounds and it becomes around
. After 9000 rounds, the dead nodes start increasing, so they don’t transfer any more packets and the curve starts decreeing with the increase in rounds and it becomes around  packets at 14000 rounds.
packets at 14000 rounds.
IoT-enabled WSN demands a dependable routing solution to share data among smart devices. The low-power sensors carry low computation capabilities, a little amount of battery power, and smaller memory sizes. Although several research mechanisms are designed for energy-efficient routing. However, most of the strategies are not effective enough for IoT-enabled WSN due to the more complexity or simplicity of the discussed strategies. Various strategies present energy-efficient protocols to prolong the network lifespan by balancing the weight between the nodes. In this paper, we propose RCBRP that manages the energy-efficient routing. It reduces the amount of energy consumed for solving the problem of creating clusters. We proposed an optimized protocol based on the number of CH nodes. When the BS is positioned outside the network RCBRP conveys a significant amount of data with less energy consumption. Furthermore, RCBRP achieves longer lifetimes in contrast to existing routing protocols including EECRP, LEECH, LEECH-C, and GEEC. The simulation results prove the supremacy of our proposed scheme is compared to counterparts. In the future, we shall identify the energy consumption at multiple paths from the CH to the BS and evaluate the performance when an energy-efficient path is disconnected.
Funding Statement: Taif University Researchers Supporting Project Number (TURSP-2020/10), Taif University, Taif, Saudi Arabia.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. L. Chan, K. Gomez Chavez, H. Rudolph and A. Hourani. (2020). “Hierarchical routing protocols for wireless sensor network: A compressive survey,” Wireless Networks, vol. 26, no. 5, pp. 3291–3314. [Google Scholar]
2. M. M. Islam, M. M. Hassan, G. W. Lee and E. N. Huh. (2012). “A survey on virtualization of wireless sensor networks,” Sensors, vol. 12, no. 2, pp. 2175–2207. [Google Scholar]
3. B. Jan, H. Farman, H. Javed, B. Montrucchio, M. Khan et al. (2017). , “Energy efficient hierarchical clustering approaches in wireless sensor networks: A survey,” Wireless Communications and Mobile Computing, vol. 2017, pp. 1–14. [Google Scholar]
4. A. Kumar, M. Zhao, K. J. Wong, Y. L. Guan and P. H. J. Chong. (2018). “A comprehensive study of IoT and WSN MAC protocols: Research issues, challenges and opportunities,” IEEE Access, vol. 6, pp. 76228–76262. [Google Scholar]
5. A. Ali, Y. Ming, S. Chakraborty and S. Iram. (2017). “A comprehensive survey on real-time applications of WSN,” Future Internet, vol. 9, no. 4, pp. 1–22. [Google Scholar]
6. A. A. Babayo, M. H. Anisi and I. Ali. (2017). “A review on energy management schemes in energy harvesting wireless sensor networks,” Renewable and Sustainable Energy Reviews, vol. 76, pp. 1176–1184. [Google Scholar]
7. S. A. Dehkordi, K. Farajzadeh, J. Rezazadeh, R. Farahbakhsh, K. Sandrasegaran et al. (2020). , “A survey on data aggregation techniques in IoT sensor networks,” Wireless Networks, vol. 26, no. 2, pp. 1243–1263. [Google Scholar]
8. J. Shen, A. Wang, C. Wang, P. C. K. Hung and C. F. Lai. (2017). “An efficient centroid-based routing protocol for energy management in WSN-assisted IoT,” IEEE Access, vol. 5, pp. 18469–18479. [Google Scholar]
9. T. Kaur and D. Kumar. (2020). “A survey on QoS mechanisms in WSN for computational intelligence based routing protocols,” Wireless Networks, vol. 26, no. 4, pp. 2465–2486. [Google Scholar]
10. M. Shafiq, H. Ashraf, A. Ullah and S. Tahira. (2020). “Systematic literature review on energy efficient routing schemes in WSN—A survey,” Mobile Networks and Applications, vol. 25, no. 3, pp. 882–895. [Google Scholar]
11. N. Moussa, Z. Hamidi-Alaoui and A. El Belrhiti El Alaoui. (2020). “ECRP: An energy-aware cluster-based routing protocol for wireless sensor networks,” Wireless Networks, vol. 26, no. 4, pp. 2915–2928. [Google Scholar]
12. R. E. Mohamed, A. I. Saleh, M. Abdelrazzak and A. S. Samra. (2018). “Survey on wireless sensor network applications and energy efficient routing protocols,” Wireless Personal Communications, vol. 101, no. 2, pp. 1019–1055. [Google Scholar]
13. J. Singh, R. Kaur and D. Singh. (2020). “A survey and taxonomy on energy management schemes in wireless sensor networks,” Journal of Systems Architecture, vol. 111, pp. 1–22. [Google Scholar]
14. J. Shen, A. Wang, C. Wang, Y. Ren and J. Wang. (2015). “Performance comparison of typical and improved LEACH protocols in wireless sensor network,” in Int. Conf. on Computational Intelligence Theory, Systems and Applications, Yilan, pp. 187–192. [Google Scholar]
15. L. N. Devi and A. N. Rao. (2016). “Optimization of energy in wireless sensor networks using clustering techniques,” in Int. Conf. on Communication and Electronics Systems, Coimbatore, pp. 1–4. [Google Scholar]
16. J. Lin, W. Yu, N. Zhang, X. Yang, H. Zhang et al. (2017). , “A survey on internet of things: Architecture, enabling technologies, security and privacy, and applications,” IEEE Internet Things Journal, vol. 4, no. 5, pp. 1125–1142. [Google Scholar]
17. H. Mrabet, S. Belguith, A. Alhomoud and A. Jemai. (2020). “A survey of IoT security based on a layered architecture of sensing and data analysis,” Sensors, vol. 20, no. 13, pp. 1–19. [Google Scholar]
18. Z. A. Aghbari, A. M. Khedr, W. Osamy, I. Arif and D. P. Agrawal. (2020). “Routing in wireless sensor networks using optimization techniques: A survey,” Wireless Personal Communications, vol. 111, no. 4, pp. 2407–2434. [Google Scholar]
19. B. Pourghebleh and V. Hayyolalam. (2020). “A comprehensive and systematic review of the load balancing mechanisms in the internet of things,” Cluster Computing, vol. 23, no. 2, pp. 641–661. [Google Scholar]
20. C. Nakas, D. Kandris and G. Visvardis. (2020). “Energy efficient routing in wireless sensor networks: A comprehensive survey,” Algorithms, vol. 13, no. 3, pp. 1–65. [Google Scholar]
21. M. S. Bensaleh, R. Saida, Y. H. Kacem and M. Abid. (2020). “Review article wireless sensor network design methodologies: A survey,” Journal of Sensors, vol. 2020, pp. 1–13. [Google Scholar]
22. W. R. Heinzelman, A. Chandrakasan and H. Balakrishnan. (2000). “Energy-efficient communication protocol for wireless microsensor networks,” in IEEE Int. Conf. on System Sciences, Maui, Hawaii, pp. 1–10. [Google Scholar]
23. W. B. Heinzelman, A. P. Chandrakasan, S. Member and H. Balakrishnan. (2002). “An application-specific protocol architecture for wireless microsensor networks,” IEEE Transactions on Wireless Communications, vol. 1, no. 4, pp. 660–670. [Google Scholar]
24. M. Ye, C. Li, G. Chen and J. Wu. (2005). “EECS: An energy efficient clustering scheme,” in IEEE Int. Performance, Computing, and Communications Conf., Phoenix, pp. 1–21. [Google Scholar]
25. W. Abushiba, P. Johnson, S. Alharthi and C. Wright. (2017). “An energy efficient and adaptive clustering for wireless sensor network (ch-leach) using leach protocol,” in 13th Int. Computer Engineering Conf., Cairo, pp. 50–54. [Google Scholar]
26. R. Singh and A. K. Verma. (2017). “Energy efficient cross layer based adaptive threshold routing protocol for WSN,” AEUE International Journal of Electronics and Communications, vol. 72, no. 2, pp. 166–173. [Google Scholar]
27. W. Wu, N. Xiong and C. Wu. (2017). “Improved clustering algorithm based on energy consumption in wireless sensor networks,” IET Networks, vol. 6, no. 3, pp. 47–53. [Google Scholar]
28. M. Al-shalabi, M. Anbar, T. C. Wan and A. Khasawneh. (2018). “Variants of the low-energy adaptive clustering hierarchy protocol: Survey, issues and challenges,” Electronics, vol. 7, no. 8, pp. 1–28. [Google Scholar]
29. F. A. Khan, M. Khan, M. Asif, A. Khalid and I. U. Haq. (2019). “Hybrid and multi-hop advanced zonal-stable election protocol for wireless sensor networks,” IEEE Access, vol. 7, pp. 25334–25346. [Google Scholar]
30. Y. Ge, S. Wang and J. Ma. (2018). “Optimization on TEEN routing protocol in cognitive wireless sensor network,” EURASIP Journal on Wireless Communications and Networking, vol. 27, pp. 1–9. [Google Scholar]
31. R. A. Ahmed, Z. A. Ahmed, M. Abd-elnaby, E. S. M. El-rabaie and F. E. A. El-samie. (2019). “Adaptive soft thresholding based energy efficient sensor protocol for wireless sensor networks,” in 36th National Radio Science Conf., Port Said, Egypt, pp. 163–172. [Google Scholar]
32. H. Q. Qadori, Z. A. Zulkarnain, Z. M. Hanapi and S. Subramaniam. (2017). “A spawn mobile agent itinerary planning approach for energy-efficient data gathering in wireless sensor networks,” Sensors, vol. 17, no. 6, pp. 1–16. [Google Scholar]
33. M. Sajwan, D. Gosain and A. K. Sharma. (2018). “Hybrid energy-efficient multi-path routing for wireless sensor networks,” Computers and Electrical Engineering, vol. 67, no. 1, pp. 96–113. [Google Scholar]
34. S. Poudel and S. Moh. (2020). “Energy-efficient and fast MAC protocol in UAV-aided wireless sensor networks for time-critical applications,” Sensors, vol. 20, no. 9, pp. 1–23. [Google Scholar]
35. N. Kumar and Y. Singh. (2016). “An energy efficient and trust management based opportunistic routing metric for wireless sensor networks,” in 4th Int. Conf. on parallel, Distributed and grid Computing, Waknaghat, pp. 5–10. [Google Scholar]
36. V. P. Bawage and D. C. Mehetre. (2016). “Energy efficient secured routing model for wireless sensor networks,” in Int. Conf. on Automatic Control and Dynamic Optimization Techniques, Pune, pp. 865–869. [Google Scholar]
37. J. Wang, J. Cao, S. Ji and J. H. Park. (2017). “Energy-efficient cluster-based dynamic routes adjustment approach for wireless sensor networks with mobile sinks,” Journal of Supercomputing, vol. 73, no. 7, pp. 3277–3290. [Google Scholar]
38. N. Kumar and Y. Singh. (2017). “Trust and packet load balancing based secure opportunistic routing protocol for WSN,” in 4th Int. Conf. on Signal Processing, Computing and Control, Solan, pp. 463–467. [Google Scholar]
39. A. O. A. Salem and N. Shudifat. (2019). “Enhanced LEACH protocol for increasing a lifetime of WSNs,” Personal and Ubiquitous Computing, vol. 23, pp. 901–907. [Google Scholar]
40. H. Yetgin, K. Tsz, K. Cheung, M. El-Hajjar and L. Hanzo. (2017). “A survey of network lifetime maximization techniques in wireless sensor networks,” IEEE Communications Surveys & Tutorials, vol. 19, no. 2, pp. 828–854. [Google Scholar]
41. K. Romer and F. Mattern. (2004). “Event-based systems for detecting real-world states with sensor networks: A critical analysis,” in Int. Conf. on Intelligent Sensors, Sensor Networks and Information Processing, Melbourne, pp. 389–395. [Google Scholar]
42. S. Al-sodairi and R. Ouni. (2018). “Reliable and energy-efficient multi-hop LEACH-based clustering protocol for wireless sensor networks,” Sustainable Computing: Informatics and Systems, vol. 20, pp. 1–13. [Google Scholar]
43. T. M. Behera, S. K. Mohapatra, U. C. Samal, M. S. Khan, M. Daneshmand et al. (2019). , “Residual energy based cluster-head selection in WSNs for IoT application,” IEEE Internet Things Journal, vol. 6, no. 3, pp. 5132–5139. [Google Scholar]
44. Y. Li, C. Ai, S. Member, C. T. Vu and S. Member. (2010). “Delay-bounded and energy-efficient composite event monitoring in heterogeneous wireless sensor networks,” IEEE Transactions on Parallel and Distributed Systems, vol. 21, no. 9, pp. 1373–1385. [Google Scholar]
45. C. A. Suescun and M. Cardei. (2016). “Event-based clustering for composite event detection in wireless sensors networks,” in 35th Int. Performance Computing and Communications Conf., Las Vegas, pp. 1–8. [Google Scholar]
46. C. Hongsong, H. Zhi and F. Zhongchuan. (2015). “Quantitative trustworthy evaluation scheme for trust routing scheme in wireless sensor networks,” in IEEE Int. Conf. Trustcom/BigDataSE/ISPA, Helsinki, pp. 1272–1278. [Google Scholar]
47. M. Zhang, R. Zheng, Q. Wu, W. Wei, X. Bai et al. (2015). , “B-iTRS: A bio-inspired trusted routing scheme for wireless sensor networks,” Journal of Sensors, vol. 2015, pp. 1–8. [Google Scholar]
48. N. Djedjig, D. Tandjaoui, F. Medjek and I. Romdhani. (2020). “Trust-aware and cooperative routing protocol for IoT security,” Journal of Information Security and Applications, vol. 52, no. 7, pp. 1–17. [Google Scholar]
49. D. Airehrour, J. A. Gutierrez and S. K. Ray. (2018). “SecTrust-RPL: A secure trust-aware RPL routing protocol for internet of things,” Future Generation Computer Systems, vol. 93, pp. 860–876. [Google Scholar]
50. P. Rodrigues and J. John. (2020). “Joint trust: An approach for trust-aware routing in WSN,” Wireless Networks, vol. 26, no. 5, pp. 3553–3568. [Google Scholar]
51. P. Sanmartin, A. Rojas, L. Fernandez, K. Avila, D. Jabba et al. (2018). , “Sigma routing metric for RPL protocol,” Sensors, vol. 18, no. 4, pp. 1–18. [Google Scholar]
52. H. Kim, J. Ko, D. E. Culler and J. Paek. (2017). “Challenging the IPv6 routing protocol for low-power and lossy networks (RPLA survey,” IEEE Communications Surveys & Tutorials, vol. 9, no. 4, pp. 2502–2525. [Google Scholar]
53. T. Lalitha and R. Umarani. (2011). “Energy efficient cluster based key management technique for wireless sensor networks,” Oriental Journal of Computer Science and Technology, vol. 4, pp. 293–304. [Google Scholar]
54. O. Younis and S. Fahmy. (2004). “HEED: A hybrid, energy-efficient, distributed clustering approach for ad-hoc sensor networks,” IEEE Transactions on Mobile Computing, vol. 3, no. 4, pp. 1–36. [Google Scholar]
55. Y. Li, L. Guo and S. K. Prasad. (2010). “An energy-efficient distributed algorithm for minimum-latency aggregation scheduling in wireless sensor networks,” in 30th Int. Conf. on Distributed Computing Systems, Genova, pp. 827–836. [Google Scholar]
56. T. T. Huynh and C. S. Hong. (2006). “An energy delay efficient multi-hop routing scheme for wireless sensor networks,” IEICE, vol. 89, no. 5, pp. 1654–1661. [Google Scholar]
57. Shi Bai, W. Zhang, G. Xue, J. Tang and C. Wang. (2012). “DEAR: Delay-bounded energy-constrained adaptive routing in wireless sensor networks,” in IEEE Int. Conf. on Computer and Communications Societies, Orlando, pp. 1593–1601. [Google Scholar]
58. H. M. Ammari. (2013). “On the energy-delay trade-off in geographic forwarding in always-on wireless sensor networks: A multi-objective optimization problem,” Computer Networks, vol. 57, no. 9, pp. 1913–1935. [Google Scholar]
59. G. Dhand and S. S. Tyagi. (2018). “SMEER: Secure multi-tier energy efficient routing protocol for hierarchical wireless sensor networks,” Wireless Personal Communications, vol. 105, pp. 17–35. [Google Scholar]
60. A. Diop, Y. Qi, Q. Wang and S. Hussain. (2013). “An advanced survey on secure energy-efficient hierarchical routing Protocols in wireless sensor networks,” IJCSI, vol. 10, no. 1, pp. 1–11. [Google Scholar]
61. B. Bhushan and G. Sahoo. (2019). “Routing protocols in wireless sensor networks,” in Computational Intelligence in Sensor Networks, Berlin: Springer, pp. 215–248. [Google Scholar]
62. N. Javaid, S. N. Mohammad, K. Latif, U. Qasim, Z. A. Khan et al. (2013). , “HEER: Hybrid energy efficient reactive protocol for wireless sensor networks,” in Int. Conf. on Electronics, Communications and Photonics, Fira, pp. 1–4. [Google Scholar]
63. A. Rajeev and S. C. Sharma. (2018). “Energy optimization of energy aware routing protocol and bandwidth assessment for wireless sensor network,” International Journal of System Assurance Engineering and Management, vol. 9, pp. 612–619. [Google Scholar]
64. Y. Zhu, V. Ramanuja, P. Seung-Jong and S. Raghupathy. (2008). “A scalable correlation aware aggregation strategy for wireless sensor networks,” Information Fusion, vol. 9, no. 3, pp. 354–369. [Google Scholar]
65. K. Haseeb, A. Almogren, N. Islam, I. U. Din and Z. Jan. (2019). “An energy-efficient and secure routing protocol for intrusion avoidance in IoT-based WSN,” Energies, vol. 12, no. 21, pp. 354–369. [Google Scholar]
66. A. Ahmed, K. A. Bakar, M. I. Channa and A. W. Khan. (2016). “A secure routing protocol with trust and energy awareness for wireless sensor network,” Mobile Networks and Applications, vol. 21, pp. 272–285. [Google Scholar]
67. S. M. Muzammal, R. K. Murugesan and N. Z. Jhanjhi. (2020). “A comprehensive review on secure routing in internet of things: Mitigation methods and trust-based approaches,” IEEE Internet Things Journal, pp. 1–25, . https://doi.org/10.1109/JIOT.2020.3031162. [Google Scholar]
68. T. Sharma, B. Kumar and G. S. Tomar. (2012). “Performance comparision of LEACH, SEP and DEEC protocol in wireless sensor network,” in Int. Conf. on Advances in Computer Science and Electronics Engineering, Delhi-NCR, India, pp. 10–15. [Google Scholar]
69. K. Haseeb, N. Islam, A. Almogren and I. U. D. Din. (2019). “Intrusion prevention framework for secure routing in WSN-based mobile internet of things,” IEEE Access, vol. 7, pp. 185496–185505. [Google Scholar]
70. Z. A. Almusaylim, A. Alhumam and N. Z. Jhanjhi. (2020). “Proposing a secure RPL based internet of things routing protocol: A review,” Ad Hoc Networks, vol. 101, no. 6, pp. 102096. [Google Scholar]
71. M. Conti, P. Kaliyar, M. Rabbani and S. Ranise. (2020). “Attestation-enabled secure and scalable routing protocol for IoT networks,” Ad Hoc Networks, vol. 98, no. 3, pp. 102054. [Google Scholar]
72. A. Sari and E. Caglar. (2018). “Load balancing algorithms and protocols to enhance quality of service and performance in data of WSN,” in Security and Resilience in Intelligent Data-Centric Systems and Communication Networks, 1 ed. Italy: Academic Press, pp. 143–178. [Google Scholar]
73. S. U. Maheswari, N. S. Usha, E. A. M. Anita and K. R. Devi. (2016). “A novel robust routing protocol RAEED to avoid dos attacks in WSN,” in Int. Conf. on Information Communication and Embedded Systems, Chennai, pp. 1–5. [Google Scholar]
74. J. Shen, A. Wang, C. Wang, P. C. K. Hung and C. Lai. (2017). “An efficient centroid-based routing protocol for energy management in WSN-assisted IoT,” IEEE Access, vol. 5, pp. 18469–18479. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |