DOI:10.32604/cmc.2021.014007

| Computers, Materials & Continua DOI:10.32604/cmc.2021.014007 |  |
| Article |
Estimating Security Risk of Healthcare Web Applications: A Design Perspective
Department of Computer Engineering, Umm Al-Qura University, Mecca, 24381, Saudi Arabia
*Corresponding Author: Fahad A. Alzahrani. Email: fayzahrani@uqu.edu.sa
Received: 28 August 2020; Accepted: 20 October 2020
Abstract: In the recent years, the booming web-based applications have attracted the hackers’ community. The security risk of the web-based hospital management system (WBHMS) has been increasing rapidly. In the given context, the main goal of all security professionals and website developers is to maintain security divisions and improve on the user’s confidence and satisfaction. At this point, the different WBHMS tackle different types of security risks. In WBHMS, the security of the patients’ medical information is of utmost importance. All in all, there is an inherent security risk of data and assets in the field of the medical industry as a whole. The objective of this study is to estimate the security risk assessment of WBHMS. The risks assessment pertains to securing the integrity of the information in alignment with the Health Insurance Portability and Accountability Act. This includes protecting the relevant financial records, as well as the identification, evaluation, and prevention of a data breach. In the past few years, according to the US-based cyber-security firm Fire-eye, 6.8 million data thefts have been recorded in the healthcare sector in India. The breach barometer report mentions that in the year 2019, the data breaches found were up to 48.6% as compared to the year 2018. Therefore, it is very important to assess the security risk in WBHMS. In this research, we have followed the hybrid technique fuzzy analytic hierarchy process-technique for order of preference by similarity to ideal solution (F-AHPTOPSIS) approach to assess the security risk in WBHMS. The place of this empirical database is at the local hospital of Varanasi, U.P., India. Given the affectability of WBHMS for its board framework, this work has used diverse types of web applications. The outcomes obtained and the procedure used in this assessment would support future researchers and specialists in organizing web applications through advanced support of safety and security.
Keywords: Web based hospital management system; security risk; fuzzy AHP; fuzzy TOPSIS
Several surveys have cited nearly 44% increase in the number of web application users during 2012–2018 [1]. India is reckoned as one amongst the 10 highest spam-sending nations worlwide. The data elaborates that 48% of the ruptures influenced money-related associations. 20 percent of the breaks included medical services associations. 12 percent of them affected the public division elements and 20% intrusions were on the retail and accommodation as shown in Fig. 1. Security risk has become a significant factor in the process of improving programming and the WBHMS with its broad framework plan. Several issues need to be tackled in a WBHMS including the cell phones, ransomware, and malware, among others [2]. The security risk is characterized as the “probability of enduring misfortune that portrays the effect on the venture which could be as low quality of programming arrangement, expanded costs, disappointment, or postponed finish” [3]. Thus, all of these aspects are elemental security concerns. Moreover, every information technology (IT) expert has associated security risks. However, the security risk can be reduced and mitigated through a planned assessment procedure. Furthermore, according to Jasper [4], risk can be broadly divided into two aspects, risk evaluation and risk control.

Figure 1: Pie chart of security risk
The security risk assessment of WBHMS is categorized into three sub-levels risk ID, risk investigation, and risk prioritization. Security risk has to be controlled by the developer by estimating it in two ways, security risk objective and by risk observation. On the other hand, the developers of web-based applications or software has categorized the task of development into a huge, large, and small hospital management application. Their definition depends on the number of lines of code (LOC), the term of the task, and the number of designers associated with the undertaking. According to [4], “WBHMS broadens regularly pass on the equal or more risk as do immense endeavors.” Hence, from the perspective of achieving optimal security in the organizations, this examination proposes a consolidated F-AHPTOPSIS methodology to ascertain the heaviness of each security model and sub-foundation. Secure WBHMS allows patients’ data to be saved as records and enables easy accessibility of data. Moreover, secure WBHMS also highlights the theft and misplacement of data.
Our paper will essentially concentrate on security risk assessment for the hospital management application developer and user framework. Further, the principal objective of this quantitative analysis is to give the developer a thoughtful approach for estimating the present degree of risk evaluation. The paper also gives data about different kinds of risk appraisal models and techniques that are found in the writing depending on the setting of risk evaluation.
The structure of this paper is as follows: Section 2 enumerates the related work done in the context of security risk assessment. Section 3 discusses different security risks based on WBHMS. Section 4 entails the methodology of F-AHPTOPSIS that we adopted for our research work. Section 5 details the calculations done on the empirical data. Section 6 presents a comparative analysis of the results with the classical method, and Section 7 of this study discusses the results. Section 8 concludes the study.
Research initiatives to equate utility and practicality with assurance and security are already underway or have been attempted prievously. Moreover, several studies have been done on the creation, application, and apprising of security efforts [5,6]. Some of the noted investigations in this league are enunciated underneath:
Zech et al. [7] have presented a new approach of vulnerability detection which is useful for our study of security risk analysis of WBHMS. The authors have presented the knowledge-based security approach for vulnerability detection.
Sunitha et al. [8] present a technique for learning-based security testing by rationale programming on Web-based emergency clinic plan frameworks. This system conquers the current common spotlight on utilitarian or non-practical necessities just as the necessary elevated level of security information when performing non-useful security testing. The study shows the technique’s viability in recognizing vulnerabilities in WBHMS, its incentive in making programming framework progressively secure. This component forestalls URL, XSS, and SQL infusion vulnerabilities at the customer side. The approach is useful to understand the security risk in WBHMS.
Schauer et al. [9] proposed a MITIGATE system to dissect the threat of security in the development of a web application network which gives a refreshed risk assessment of digital resources inside every partner and interconnection among those partners. This approach provides a mathematical conclusion and detects the vulnerability of different risks in web-based application security.
Kruse et al. [10] proposed a well-characterized paradigm to gauge the probability and the effect of a protection hazard. The study proposes a Fuzzy multi-criteria basic leadership way to methodically measure the seriousness of protection dangers while demonstrating the imprecision and dubiousness inborn in semantic evaluation. This paper helps us to estimate the risk assessment by the fuzzy multi-criteria decision-making process.
Ionita et al. [11] investigated issues which can be tended to by a structure that uses a hazard evaluation process, the methodology features the significance of every security highlight to item proprietors while guaranteeing that the learning and time required to actualize security necessities are made accessible to the designers.
Radanliev et al. [12] presented a model that has a structured procedure with new hazard evaluation vectors, explicit for IoT digital risk. The study shows the present holes in digital hazard guidelines and strategies and characterizes the structure standards of future digital risk sway appraisal by a model for sway evaluation of IoT digital risk.
Akinrolabu et al. [13] proposed the Cloud Supply Chain Cyber Risk Assessment model, a quantitative hazard evaluation model that is upheld by cloud provider security appraisal and cloud store network mapping. Utilizing this model, the study surveys the danger of a customer relationship management (CRM) application, mapping for recognizing frail connections, and assessing its security dangers.
The ensuing paragraphs cites the research studies that were based on the development of fuzzy AHP and fuzzy TOPSIS. Studies that were integral to our research premise were:
Memari et al. [14] presented a not equivalent F-TOPSIS strategy to choose the privilege practical provider that worries nine criteria and thirty sub-criteria for a car extra parts producer. This methodology gives a reasonable positioning of providers and a solid answer for practical sourcing choices. This paper gave the idea of the F-TOPSIS approach in our study on WBHMS.
Dezert et al. [15] gave the methodology of the multi-criteria basic leadership strategies for positioning solid blend variables and delegate blend structure techniques. The study outlined a structure to recognize basic blend elements found from the solid blend plan strategies for superior solid by utilizing the two-stage AHP and TOPSIS approaches. In multi-criteria decision making, both (F-AHP and F-TOPSIS) are very useful.
Mokhtar et al. [16] proposed a system dependent on the F-AHP and fuzzy method for requesting execution to recognize and rank the dangers of Internet money. This examination characterized risk factors and investigated which components ought to be essentially considered. Given the examination, the study discovered that the monetary hazard is at a significant level.
Zhang et al. [17] built up a fuzzy Delphi-AHP TOPSIS system to recognize obstructions in rising innovation appropriation. This system explores the obstacles for huge information investigation to be received in the sea business.
Dao et al. [18] managed observational research on applying a blend of the F-AHP and the F-TOPSIS to gauge natural clashes developing because of titan mining in Vietnam. The approach joins the F-AHP and the F-TOPSIS to rank ecological clashes.
Solanki et al. [19] proposed a coordinated approach dependent on Strengths, Weaknesses, Opportunities, and Threats (SWOT) examination, AHP, and F-TOPSIS to assess vitality systems for supportable vitality arranging. The SWOT investigation is utilized to decide the elements and sub-factors basic for economic vitality arranging. Accordingly, AHP, a Multi-Criteria Decision Making (MCDM) strategy is utilized to decide loads of each factor and sub-factor.
After a detailed analysis of the above-mentioned studies, we found that these endeavors had worked on relevant approaches required to address the objectives of our research on security risk assessment in WBHMS. As cited in the references, many authors have mentioned different factors that affect the security of the web-based application, and they have also employed the methodology of F-AHP and F-TOPSIS which gives the weight and rank of the factors and its different alternatives. For the assessment of risk, we have used the F-AHP method to obtain the weight of the factors and by F-TOPSIS methodology we have given the different factors the privileged ranking.
3 Security Risk of WBHMS Design
There has been an abrupt and alarming increase the instances of security violence, data breaching, loss of confidentiality and integrity of patients’ data in the recent years. These episodes are like cyber assault on the patients, workers, and workplaces. The digital risk on the crisis facilities has been on the rise in the world and it is not confined to any one country. Computerized violence is boundless and has affected different crisis facilities in both the significant compensation countries like the United States, or in low-focus pay countries like Kenya [20]. A report by the US Department of Justice revealed an appalling fact about Ransomware which is only one sort of malware undermining prosperity workplaces. The report stated that nearly 4000 ransomware ambushes happened each day across different portions in 2018, an increase by 300% since 2017 [3].
The report also discovered the best three sections that were most affected by ransomware. Other than ransomware, there has also been a four-fold increase in the amount of malicious PC programming attacks over the last two years and the prosperity region has ended up being one of the most coordinated zones comprehensively. This is creating stress as centers worldwide are wrapping up their crisis facility information structures for definitive, cash related, and helpful errands along with the usage of related restorative contraptions, circulated capacity organizations, and simultaneously rising framework systems. Further, in a WBHMS design,many security risks have been shown in Fig. 2.

Figure 2: Different factors and alternatives to security risk
Furthermore, Fig. 2 above illustrates the security risks associated with WBHMS. Different security risks are: Risk assessment, authentication, authorization, and access control, session management, data and input validation, cross scripting, error handling, and data breaching. Each of these are connected to every individual attribute from (A1–A10 are security attribute or alternatives). Furthermore, each security risk is connected with every attribute.
Risk Assessment: Is characterized as the blend of future outcomes and related vulnerabilities, it can be viewed as perfect with the triplet meaning of security chance [21].
Authentication: In security frameworks, verification is a particular form of approval. It is a way of giving people access to framework items depending on their personality. Confirmation simply guarantees that the individual in question is indeed who he/she professes to be, yet says nothing regarding the entrance privileges of the person [22].
Authorization and Access Control: Are fundamental and essential structural components of any application’s security. WBHMS framework ought to ensure front-end and back-end information and framework assets by actualizing access control confinements to perform on the information. Access control plan ought to secure against the unapproved survey, adjustment, or duplication of information, get to control components can likewise help limit malware code execution, or unapproved activities through an assailant misusing framework conditions (DNS server, ACE server, and so on). Approval is the demonstration of verifying whether a client has the correct authorization to get to a specific record or play out a specific activity, expecting that client has effectively confirmed himself. It is particularly qualification centered and subordinate around explicit principles and access control records preset by the WBHMS [23].
Session Management: Is an instrument of essential security segment in the expansive scope of the WBHMS course of action frameworks. HTTP is a stateless convention and the session encourages the applications to extraordinarily decide a specific client over a few quantities of discrete demands just as to deal with the information which it collects about the position of the cooperation of the client with the application. It turns into the ideal objective for the security threat against the application. On the other hand, if the hackers can break the session at the board of any application, they can undoubtedly sidestep the entire confirmation controls and cover-up as different clients without having their certifications [24].
Data and Input Validation: Web-based application or software regularly upgrade numerous structures and algorithms for web components that enable the users to login and submit information. The back-end databases will execute this information. Users can, purposefully or inadvertently, enter inappropriate information that, if arrives at those back-end databases, may cause certain genuine harming issues. For appropriate User interface configuration just as for security reasons, it is significant for website specialists to consider input-approval procedures at the User interface level or as right on time as could be expected under the circumstances [25].
Cross-Site Scripting (XSS): Is a kind of infusion security assault in which an assailant infuses information, for example, malware content, into content from generally confided in sites. Cross-webpage scripting assaults happen when an untrusted source is permitted to infuse its code into a Web-based medical clinic plan framework and that pernicious code is incorporated with dynamic substance conveyed to an unfortunate casualty’s program [26].
Error Handling: Inappropriate action on blunders can present a variety of security issues for a web-based application or software. One of the issues raised is that of the nitty-gritty inside error messages, for example, stack overflows, dumps of databases, and blunder codes are shown to the client (programmer). These error messages uncover usage subtleties that should not be uncovered [27].
Data Breaches: An information break is an affirmed episode of information being intruded upon or potentially revealed in an unapproved design. Information ruptures may include Personal Health Information (PHI), Personally Identifiable Information (PII), Exchange privileged insights, or protected innovation. On the off chance that any individual who is not explicitly approved to do so intrudes upon such information, the association accused of securing that data is said to have endured an information break. While programmers and cybercriminals frequently cause information ruptures, there are likewise occurrences where ventures or government offices accidentally uncover touchy or secret information on the web [28].
The different alternatives (A1–A10) are-mediXcel EMR (A1), Trio HIS (A2), Caresoft HIS (A3), GeniPulse (A4), LiveHealth For diagnostic (A5), Visual Hospital Management (A6), eHospital (A7), Medisteer (A8), HospiLogix (A9) and NextGen (A10). These are the various hospital management web-based applications that we have used as the alternatives from the location of the local hospital of Varanasi, India.
The WBHMS design is highly diverse and heterogeneous due to various complex processes. Nowadays health sector is skilled with a great deal of dynamic change like data collection and its security [29–31]. Therefore, the security features in the health sector and WBHMS design have improved the different attributes such as risk assessment, authorization, etc. [32–40]. Keeping in view this background, we proposed the F-AHPTOPSIS approach for the risk assessment in WBHMS. For the proposed study, we have taken eight factors or security risks that are based on WBHMS and different applications which we have mentioned above in Section 3 (A1–A10). Each alternative is connected to each factor. We have to calculate the weights of factors which affect the WBHMS by Fuzzy-AHP [41–45]. After getting the weight, we further evaluated the rank by using Fuzzy-TOPSIS. These procedures have been explicated in Fig. 3.

Figure 3: Flow diagram of fuzzy AHP-TOPSIS
Flow graph of methodology F-AHPTOPSIS is depicted in Fig. 3. There are three major categories: Pre–processing, Fuzzy-AHP, and Fuzzy-TOPSIS. From the analysis of the literature, we listed the different security risks. Then we identified the criteria and determined the risks which further passed through the risk criteria. Fuzzy-AHP was employed to select the multi-criteria decision making between different alternatives [46–50]. The four steps of the procedure included:
First, make a security matrix and compare it pair-wise.
Second, check the further assessment with the condition of the existence of a security attribute after the comparison of condition.
Third, assigning access after the Fuzzy-AHP process.
Fourth, aggregate the rating and calculate the weight of security risk and rank it [51–54].
The different factors (F1–F8) and different attributes/alternatives (A1–A10) are connected which is shown in Fig. 2. Factors are the security risks, and the alternatives are the applications being used in the hospitals of Varanasi, India. We have calculated the weight of the factors with the effect of alternatives and ranked them according to our methodology by using F-AHPTOPSIS. After this, calculated the degree of closeness.
The Usable-security WBHMS plan framework is an accurate mechanism aand also a premise for further research [55–58]. Furthermore, Decision Making issues are consistently experienced for accomplishing the clients’ targets and affectability of the data. Numerous methodologies or estimations exist in the writing that can be applied to clear up such issues. For impost of usable-security, Fuzzy-AHP is a truly appropriate technique instead of the other multi-criteria strategies. However, Fuzzy-AHP can’t resolve the basic lack of clarity and imprecision of a decision inconceivably vague for research. Further, the F-AHP system is essentially founded on the unstable size of decisions. The F-AHP also has a few issues of its own [59–61]. Thus, a consolidated Fuzzy procedure of F-AHPTOPSIS is a special strategy that could help in the productive evaluation of options.
Fuzzy-AHP is the methodology used to cure hard choice issues, Fuzzy-AHP is a prized procedure and every perplexing issue might be inspected by methods for phenomenal arranged scopes of objectives, i.e., chain of command. The issue is isolated directly into a tree shape to clarify it through utilizing Fuzzy-AHP. The connectivity shape has been given in Fig. 2. This connectivity shape is prepared by utilizing experts’ perspectives [62]. The following stage is building the triangular fuzzy number (TFN) from the hierarchal structure. With the help of the effect of one standard on various criteria, span examination of each gathering of ordered objectives becomes an indispensable job.
The accompanying advance is changing over etymological qualities into fresh numbers and TFN. In this investigation, creators utilize the TFN which lies somewhere in the range of 0 and 1 [63]. The reason for such selection of TFN is the computational straightforwardness of TFN enrollment capacities and their capacity to manage Fuzzy information [64,65]. Further, the phonetic qualities have been named as: similarly significant, feebly significant, and so forth, and fresh qualities are classified as 1–9. Besides this, a Fuzzy Number P on Q is called TFN, if its participation capacities are recognized in conditions (1) and (2):


Here l, cf, and mb are given as a lower limit, center farthest point, and maximum breaking point, respectively, in the triangular enrollment work, Fig. 4, Portrays TFN.
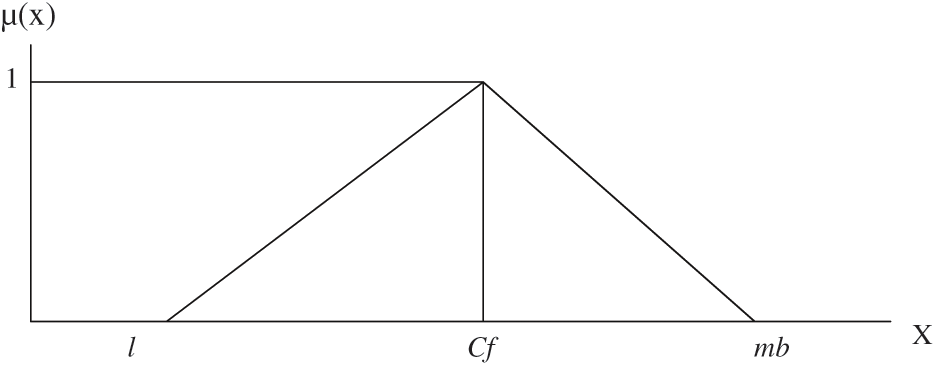
Figure 4: Triangular fuzzy numbers
TFN is denoted as (l, cf, mb). Specialists designated marks to the elements influencing the qualities in a computable manner as indicated by the scale that is exhibited in Tab. 1.

The conditions (3)–(6) were used for changing the numeric qualities into TFN that are assigned as (lij, cfij, 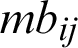 ) where lij is lower esteem,
) where lij is lower esteem, 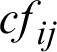 is center worth and
is center worth and 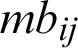 is highest level occasions, the i and j are the row and column of the two-dimensional matrix. Furthermore, TFN [
is highest level occasions, the i and j are the row and column of the two-dimensional matrix. Furthermore, TFN [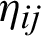 ] is perceived as:
] is perceived as:

where lij≤cfij≤mbij



In the conditions (3)–(6), Jijd demonstrates the near status of the qualities among two variables which is determined by professional d, where i and j imply a couple of elements being chosen by specialists. 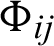 is assessed depending on the geometric mean (GM) of the master’s perspectives for a particular correlation. The GM is capable of accurately joining and connoting the agreement of experts and indicates the most minimal and most elevated scores, compatibly, for the relative centrality between the two elements. Further, conditions (7)–(9) back consolidated TFN values. Consider two TFNs M1 and
is assessed depending on the geometric mean (GM) of the master’s perspectives for a particular correlation. The GM is capable of accurately joining and connoting the agreement of experts and indicates the most minimal and most elevated scores, compatibly, for the relative centrality between the two elements. Further, conditions (7)–(9) back consolidated TFN values. Consider two TFNs M1 and  . The standards of activities are:
. The standards of activities are:



After getting the TFN esteems for each pair of examination, a Fuzzy span correlation framework is developed as  lattice with the assistance of condition (10).
lattice with the assistance of condition (10).

where  represents the dth leaders’ inclination of the ith criteria over the jth criteria. If more than one chief is available, at that point the normal of the inclinations of every leader is obtained with the assistance of condition (11).
represents the dth leaders’ inclination of the ith criteria over the jth criteria. If more than one chief is available, at that point the normal of the inclinations of every leader is obtained with the assistance of condition (11).

Next stage is to refresh the span correlation frameworks for all elements in the chain of importance based on the middle value of inclinations with the assistance of condition (12).

After this, we utilized the GM method as stated in condition (13) to depict the Fuzzy GM and Fuzzy loads of each factor.

The following stage is to finish up the Fuzzy load of the factor with the assistance of the condition (14).

Further, to determine the normal and standardized weight criteria with the assistance of conditions (15) and (16).


Moreover, the center of area (COA) strategy is utilized to compute the best non-fuzzy performance (BNP) estimation of the Fuzzy loads on estimation with the assistance of condition (17).

With P options as a geometrical course of action, m focuses inside the n-dimensional region of the issue; TOPSIS points of view afford a multi gauges choice, thus creating several ambiguities. For TOPSIS, the methodology utilized in this research is fundamentally based on the possibility that a labeled open door has the most limited and is farthest from the positive perfect arrangement and the negative perfect answer for ideal and least perfect arrangements, separately [64]. Experts face problems in distributing a particular exhibition score to an option in the context of criteria [65]. For consistency with this present Fuzzy condition, TOPSIS doles out Fuzzy numbers that align with exact numbers for representing the general centrality of criteria. Also, the F-AHPTOPSIS approach is also the most conversant approach for fixing cooperative choice-making issues underneath Fuzzy situations. F-AHPTOPSIS procedure is enlisted below:
The initial step is to choose loads of the appraisal criteria. This study applies Fuzzy-AHP to finish up Fuzzy decision loads with the assistance of conditions (1)–(16). Further, the analysts make the Fuzzy choice framework and pick the perfect semantic factors as substitutions for the criteria with the help of conditions (18) and Tab. 2.

where, 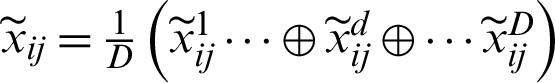 , and
, and 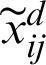 is the performance rating of the alternative Ai concerning factor Cj estimated by the dth practitioner and
is the performance rating of the alternative Ai concerning factor Cj estimated by the dth practitioner and 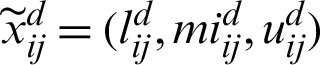 .
.

The following stage is to standardize the Fuzzy choice grid with the help of the condition (19). The standardized Fuzzy choice lattice is denoted by P as follows:

Thereafter, the stabilization procedure can be realized with the help of Eq. (20).

On the other hand, we can set the best-wanted level to be equivalent to 1; generally, the most noticeably awful is 0. The standardized values keep on being TFNs. For TFN, the standardization procedure can be performed comparably. The weighted Fuzzy standardized choice lattice (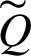 ) is measured with the assistance of the condition (21).
) is measured with the assistance of the condition (21).

where,  and after that, characterize the fuzzy positive-ideal solution (FPIS) and fuzzy negative-ideal solution (FNIS). The weighted standardized Fuzzy choice lattice shows that the components
and after that, characterize the fuzzy positive-ideal solution (FPIS) and fuzzy negative-ideal solution (FNIS). The weighted standardized Fuzzy choice lattice shows that the components 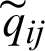 are standardized positive TFN and their extents have a place with the shut interim [0,1]. From there on, we can depict the FPIS T+ (goal levels) and FNIS R− (the most exceedingly awful levels) as appeared in conditions (22) and (23).
are standardized positive TFN and their extents have a place with the shut interim [0,1]. From there on, we can depict the FPIS T+ (goal levels) and FNIS R− (the most exceedingly awful levels) as appeared in conditions (22) and (23).


where,  ,
, 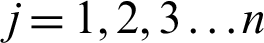 . For ascertaining the separation of every option from FPIS and FNIS, the separations (
. For ascertaining the separation of every option from FPIS and FNIS, the separations ( and
and  ) of every option from A+ and A− can be evaluated by utilizing the territory remuneration procedure as given in the conditions (24) and (25).
) of every option from A+ and A− can be evaluated by utilizing the territory remuneration procedure as given in the conditions (24) and (25).


Closeness coefficients (relative holes’ degree) are determined in the subsequent stage and build up the choices to accomplish the desire levels in each factor. The closeness coefficient is cleared to assess the Fuzzy holes’ degree based on the Fuzzy nearness coefficients to progress the options [36]. When 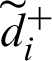 and
and  of every option have been assessed, the likenesses to the perfect arrangement are determined. This progression comprehends the similitude to a perfect arrangement as in condition (26).
of every option have been assessed, the likenesses to the perfect arrangement are determined. This progression comprehends the similitude to a perfect arrangement as in condition (26).

Here,  -defined as fuzzy satisfaction degree in the ith alternative,
-defined as fuzzy satisfaction degree in the ith alternative, 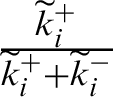 -defined as a fuzzy gap degree in the ith alternative. Based on their positions, the options are achieved. The next procedure is to evaluate the usable-security with the assistance of its contributing characteristics.
-defined as a fuzzy gap degree in the ith alternative. Based on their positions, the options are achieved. The next procedure is to evaluate the usable-security with the assistance of its contributing characteristics.
F-AHPTOPSIS methodology, Fuzzy-AHP process gives the weight of the risk attributes (A1–A10) which we have mentioned in Eqs. (1)–(17) from different risks which are shown in Fig. 2. Fuzzy TOPSIS process gives the ranks of security risks. After getting weights and ranks of the security risks, we determined the degree of closeness and analyzed whether this result should be used in WBHMS software application in the local hospitals of Varanasi. Though, subjective estimation is appropriate for evaluating security chance, it is hard to assess WBHMS quantitatively. In this context, the worldwide aggregate activity has prompted the detailing of hazard appraisal. Recently, the specialists have received hazard evaluation and projects, as it were, Dammak et al. [32] with enormous outcomes. Likewise, associations are attempting to receive high security of web applications. Hence, the security variables’ effect assumes a critical job in the WBHMS advancement process [33]. The ensuing column tabulates a standard procedure for WBHMS structure estimation through F-AHPTOPSIS. We have already deliberated upon the WBHMS in the past segments.
As Fig. 2 shows a trait of the order at one level affects the other properties of a more significant level, yet its effect isn’t the equivalent on them. It might vary. With the end goal of appraisal, we changed over the grouped properties into chains of importance and indicated it in Fig. 2. For the assurance of evaluation, variables of secrecy as for reasonable security at level 2 are denoted as F1, F2,  , F8. Properties of uprightness as for practical security at level 2 are spoken to as A1–A10. As depicted in Fig. 2, with the assistance of these chains of importance, we assessed the safe WBHMS. For gathering the information with the assistance of conditions (1)–(26), secure WBHMS through Fuzzy AHP-TOPSIS has been assessed as:
, F8. Properties of uprightness as for practical security at level 2 are spoken to as A1–A10. As depicted in Fig. 2, with the assistance of these chains of importance, we assessed the safe WBHMS. For gathering the information with the assistance of conditions (1)–(26), secure WBHMS through Fuzzy AHP-TOPSIS has been assessed as:
With the assistance of Tab. 1 and, conditions (1)–(9), creators changed over the etymological qualities into numeric qualities and collected TFNs values. For developing the span examination grid, TFNs qualities have been registered in Tabs. 3–8.
Table 3: Fuzzy AHP aggregated pair-wise matrix


Table 5: Subjective cognition results

Table 6: Normalized fuzzy-decision matrix

Table 7: Weighted normalized fuzzy-decision matrix

Table 8: Closeness coefficients to aspired level among different alternatives

Tab. 3. shows the different security risk be F1–F8 and its TFN its weights and BNP have been shown in Tab. 4.
The fuzzy-AHP process gives the weight of different security risks which we have mentioned in Tab. 4. The following rank of different attributes according to the rank is-authentication (F1), risk assessment (F2), session management (F3), authorization, and access control (F4), error handling (F5), cross-site scripting (F6), data breaches (F7) and data and input validation (F8). These are the weights of different risks through Fuzzy-AHP.
Tabs. 5–7 are the different values of subjective cognition result mentioned in Eq. (20), normalized fuzzy decision matrix in Eq. (18), and weighted normalized decision matrix in Eqs. (24), (25). These values are taken through the Fuzzy-TOPSIS methodology.
Tab. 8. from fuzzy TOPSIS methodology, from Eq. (26), gives the degree of closeness. The degree of closeness of different attributes of security risk in WBHMS is shown in Fig. 2. The result of security risks (F1–F8) and their attributes (A1–A10) in WBHMS is in satisfactory condition due to the data of local hospitals of Varanasi, UP, India. Further, we have mentioned the degree of closeness in a bar chart as shown in Fig. 5.
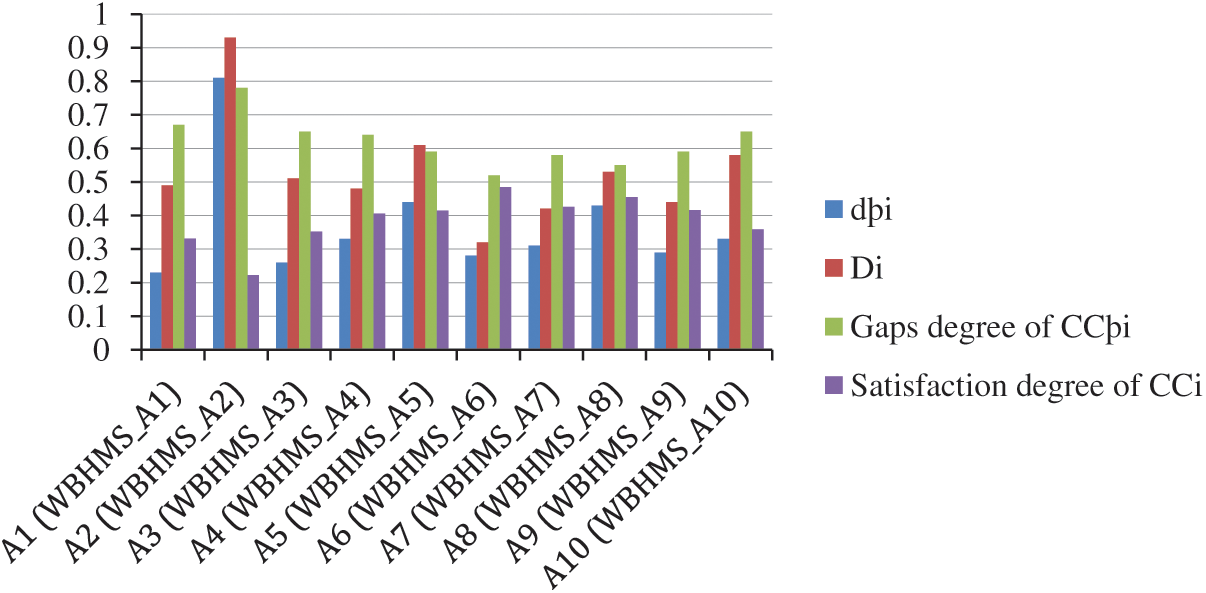
Figure 5: Graph of satisfaction degree
6 Comparison with the Usual AHP TOPSIS Method
The same data results output is different when different methodologies are used [34] and the reliability and efficiency of the technique can only be verified by using different methods [35]. In this paper, we have used the F-AHPTOPSIS methodology to evaluate the efficiency and closeness or accuracy of the result obtained. In AHP-TOPSIS, the method or procedure of data compilation and estimation of that data is the same as in F-AHPTOPSIS but no fuzzification is used. Hence, for usual AHP-TOPSIS, values are taken in their real number form. The difference between the results of fuzzy and usual AHP-TOPSIS is shown in Tab. 9 and Fig. 6. The results elicited through the usual AHP-TOPSIS method are highly interrelated (Pearson correlation coefficient is 0.999176) with the results obtained through the fuzzy AHP-TOPSIS method. The reliability and efficiency of F-AHPTOPSIS is more, and it is a better procedure/method than the usual AHP TOPSIS approach.
Table 9: The result of usual/classical methodand F-AHP and F-TOPSIS method

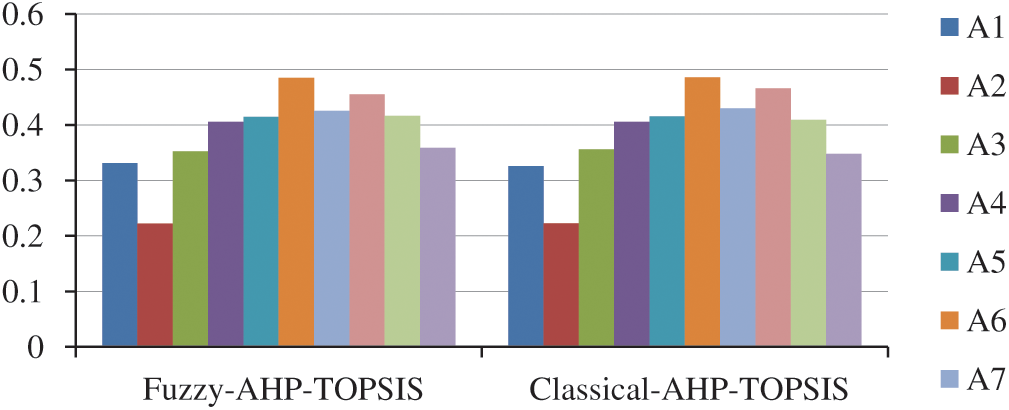
Figure 6: Variances between results
To verify the results with each variable, we have used the sensitivity analysis [36]. This has been depicted below in Tab. 10. The sensitivity analysis is calculated by the weights of variables. In our research on WBHMS, the sensitivity analysis is verified by multiple experiments of each factor with the different experiments that showed different results, as tabulated in Tab. 10. The satisfaction degree (CC−i) is calculated by the weight of each factor (F1–F10 taken as a constant), and by F-AHPTOPSIS methodology, we calculate the (CC−i).
Table 10: Sensitivity analysis

In Tab. 10, the first row shows the original weight; Fig. 7 shows the first bunch of data. According to original weights/results, the alternative-8 (F1–F8) has a high satisfaction degree (CC−i). From A1–A10, ten experiments are completed. Obtained results show that alternative-8 (F1–F8) still has a high satisfaction degree (CC−i) in 10 experiments. Moreover, the alternative with least weight in each experiment is A2. The variations of results with each other show that the ratings of alternatives are sensitive to the weights.
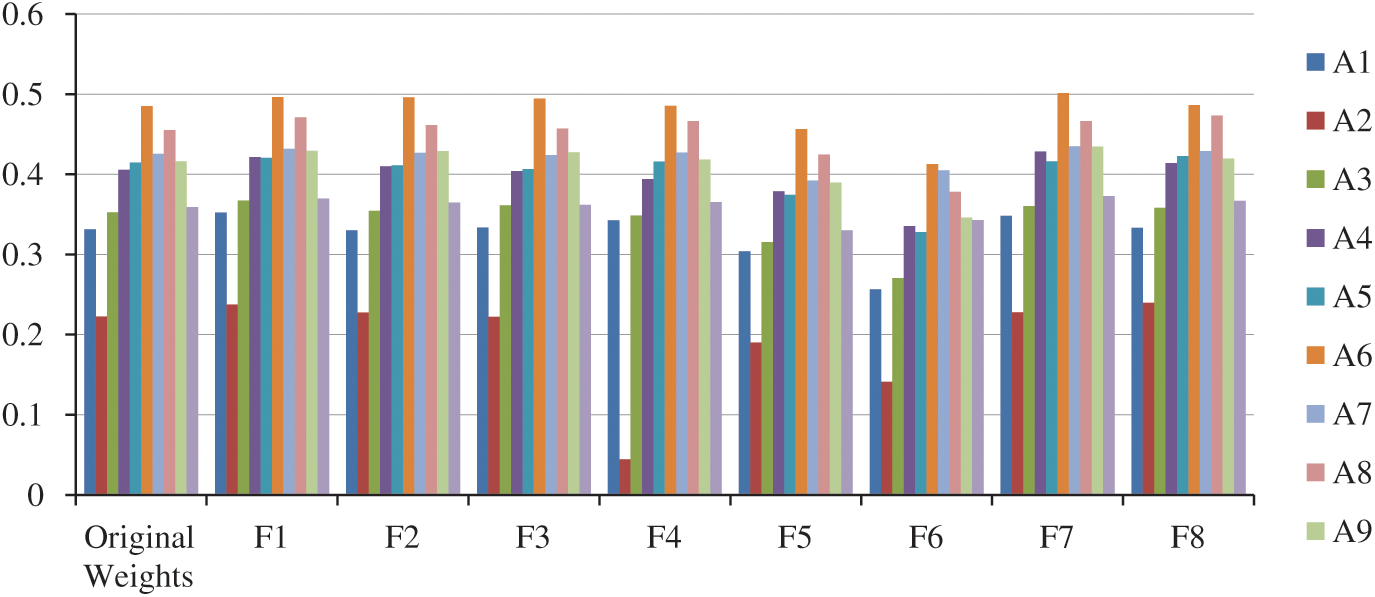
Figure 7: Graphical representation of sensitivity analysis
In the context of security risk assessment, F-AHPTOPSIS technique is considered to be the most significant procedure for verifying web-based healthcare applications. The study undertook an empirical investigation of local hospitals of Varanasi in India to corroborate that the developer’s framework is essential for protecting the WBHMS. The present security concerns have changed to maintainable and secure website composition and medical clinic’s-the developer framework. This examination centers on these two concerns and has made a various leveled structure which at last brings up the significant and contributing variables in the supportable security plan of the medical clinic the developer framework. With the web applications becoming a convincing need, their use and multifaceted nature are developing step by step. Moreover, the exponential development in security assessment forces the need to create a digital medical clinic the developer submits and empower it with high security and effective supportability.
Estimation and evaluation of security risk is the best way to accomplish feasible security. This exploration paper coordinates security just as maintainability factors and assesses reasonable security in a systematic manner. The consequences of the examination will assist the engineers in integrating supportable security with planning web application during its advancement. In this paper, we have taken tasks of the emergency clinic of different WBHMS and made feelings out of experts about the causative supportability, plan, and security variables of the particular WBHMS. Information examined from the experts has been incorporated by using Fuzzy AHP-TOPSIS.
A broad framework of research mentions the development and estimation of secure WBHMS. This paper mentions the security factors and their alternatives according to the case study of the different hospital which uses the different hospital management system application in Varanasi, India. Our research will help the engineers in developing the web application with proper improvement in the development life cycle of WBHMS. There are now numerous estimation models or strategies accessible in the writing for evaluating security independently however the accessibility of models or techniques that coordinate security on the Fuzzy-AHP strategy is altogether less. In this work, we have taken ten alternatives of the security risk of web-based applications. These alternatives were chosen after consulting the experts and collating their opinions about the contributing risk plan, mitigation plan, and security attributes of the particular web-based application.
Discoveries of this work can be enumerated as:
• The quantitative outcomes accomplished by F-AHPTOPSIS will bolster the specialists in classifying higher positioned components of an electronic emergency clinic in the board framework.
• F-AHP method gives the weight of risk attributes; F-TOPSIS gives the rank of the following attributes.
• Comparison of F-AHPTOPSIS with usual AHP TOPSIS gives the betterment of methodologies.
• Sensitivity analysis gives the degree of satisfaction for WBHMS.
• Web-based emergency clinic the board framework must be the foremost priority for both future investigations and present endeavors to optimize the efficacy of WBHMS. This evaluation would assist the engineers in gaining knowledge about the structure of security.
Improvement rules can be delivered over this assessment to help the engineers in refining the structure of security by utilizing high organized aspects in concern. This estimation may have a few delimits which can be defeated later in future studies. Delimits of the results are the following:
• The information gathered for website architecture is noteworthy, however, little. The results may contrast if the information is enormous.
• There may be extra security configuration factors other than those recognized in this work
This paper examined the security dangers that are threatening the web applications, more specifically, WBHMS. The study also analyzed a portion of the security countermeasures for these kinds of dangers. From writing, security dangers are viewed as the most significant countermeasures. As a solution to minimise the possibility of data breaches in WBHMS, this study undertook the estimation of risk assessment and employed the novel methodology of AHP TOPSIS for delivering new technique that suits the specific emergency clinic industry. This system gives distinctive security dangers credits to be decided by the AHP TOPSIS technique. Our research paper also gives the weights and the ranks of security factors. Hence, the validated and highly conclusive results drawn in the study will help the software or web application developers to consider the stated risks while developing the web-based application.
Acknowledgement: The work is funded by Grant No. 12-INF2970-10 from the National Science, Technology and Innovation Plan (MAARIFAH), the King Abdul-Aziz City for Science and Technology (KACST), Saudi Arabia. We thank the Science and Technology Unit at Um Al-Qura University for their continued logistics support.
Funding Statement: King Abdul-Aziz City for Science and Technology (KACST), Saudi Arabia.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. U. J. Butt, M. Abbod, A. Lors, H. Jahankhani, A. Jamalet et al. (2019). , “Ransomware threat and its impact on SCADA,” in IEEE 12th Int. Conf. on Global Security, Safety and Sustainability, London, USA, pp. 205–212.
2. P. Patel, F. G. Fall, R. Sullivan and R. Irwin. (2017). “Documenting attacks on health workers and facilities in armed conflicts,” Bulletin of the World Health Organization, vol. 95, no. 1, pp. 79–81.
3. S. T. Argaw, J. R. T. Pastoriza, D. Lacey, M. V. Florin, F. Calcavacchia et al. (2020). , “Cybersecurity of hospitals: Discussing the challenges and working towards mitigating the risks,” BMC Med Information and Decision Making, vol. 20, no. 2, pp. 146.
4. S. E. Jasper. (2017). “U.S. cyber threat intelligence sharing frameworks,” International Journal of Intelligence and Counter Intelligence, vol. 30, no. 1, pp. 53–65.
5. P. A. Williams and A. J. Woodward. (2015). “Cyber security vulnerabilities in medical devices: A complex environment and multifaceted problem,” Medical Devices (Auckland N.Z.), vol. 8, pp. 305–316.
6. R. Susło, J. Trnka and J. Drobnik. (2017). “Current threats to medical data security in family doctors’ practices,” Family Medicine & Primary Care Review, vol. 3, no. 1, pp. 313–318.
7. P. Zech, M. Felderer and R. Breu. (2012). “Towards risk driven security testing of service centric systems,” in 12th Int. Conf. on Quality Software, Xi’an, China, pp. 140–143.
8. K. V. N. Sunitha and M. Sridevi. (2009). “Automated detection system for SQL injection attack,” International Journal of Computer Science and Security, vol. 4, no. 4, pp. 426.
9. S. Schauer, M. Stamer, C. Bosse, M. Pavlidis, H. Mouratidis et al. (2017). , “An adaptive supply chain cyber risk management methodology,” in Hamburg Int. Conf. of Logistics, Hamburg, Germany, pp. 15–19.
10. C. S. Kruse, B. Frederick, T. Jacobson and D. K. Monticone. (2017). “Cybersecurity in healthcare: A systematic review of modern threats and trends,” Technology and Health Care, vol. 25, no. 1, pp. 1–10. [Google Scholar]
11. D. Ionita, J. Bullee and R. J. Wieringa. (2014). “Argumentation-based security requirements elicitation: The next round,” in IEEE 1st Int. Workshop on Evolving Security and Privacy Requirements Engineering, Karlskrona, pp. 7–12. [Google Scholar]
12. P. Radanliev, D. C. D. Roure, R. Nicolescu, M. Huth, R. M. Montalvo et al. (2018). , “Future developments in cyber risk assessment for the internet of things,” Computers in Industry, vol. 102, no. 1, pp. 14–22. [Google Scholar]
13. O. Akinrolabu, S. New and A. Martin. (2019). “CSCCRA: A novel quantitative risk assessment model for SaaS cloud service providers,” Computers, vol. 8, no. 66, pp. 15–23. [Google Scholar]
14. A. Memari, A. Dargi, M. R. A. Jokar, R. Ahmad, A. Rahman et al. (2019). , “Sustainable supplier selection: A multi-criteria intuitionistic fuzzy TOPSIS method,” Journal of Manufacturing Systems, vol. 50, no. 1, pp. 9–24. [Google Scholar]
15. J. Dezert, D. Han and J. Tacnet. (2017). “Multi-criteria decision making with imprecise scores and BF-TOPSIS,” in 20th Int. Conf. on Information Fusion (FusionXi’an, China, pp. 1–8. [Google Scholar]
16. M. R. Mokhtar, M. P. Abdullah, M. Y. Hassan and F. Hussin. (2015). “Combination of AHP-PROMETHEE and TOPSIS for selecting the best demand side management (DSM) options,” in IEEE Student Conf. on Research and Development, Kuala Lumpur, pp. 367–372. [Google Scholar]
17. Q. Zhang, X. Zhu, Q. Li and X. Han. (2009). “Empirical study on evaluating value creation strategy performance based on GRA and Fuzzy TOPSIS,” in Sixth Int. Conf. on Fuzzy Systems and Knowledge Discovery, Tianjin, China, pp. 79–84. [Google Scholar]
18. M. T. Dao, A. T. Nguyen, T. K. Nguyen, H. T. Pham, D. T. Nguyen et al. (2019). , “A hybrid approach using fuzzy AHP-TOPSIS assessing environmental conflicts in the titan mining industry along central coast Vietnam,” Appllied Sciences, vol. 9, no. 14, pp. 1–24. [Google Scholar]
19. R. Solanki, G. Gulati, A. Tiwari and Q. M. D. Lohani. (2016). “A correlation based Intuitionistic fuzzy TOPSIS method on supplier selection problem, IEEE Int. Conf. on Fuzzy Systems, Vancouver, BC, pp. 2106–2112. [Google Scholar]
20. M. S. Jalali, S. Razak, W. Gordon, E. Perakslis and S. Madnick. (2019). “Health care and cybersecurity: Bibliometric analysis of the literature,” Journal of Medical Internet Research, vol. 21, no. 2, pp. 52–57. [Google Scholar]
21. A. M. Sharif and M. Z. A. Rozan. (2010). “Design and implementation of project time management risk assessment tool for SME projects using oracle application express,” World Academy of Science Engineering, and Technology, vol. 65, no. 54, pp. 1221–1226. [Google Scholar]
22. M. A. Sharif and S. Basri. (2011). “Software Risk Assessment: A review on small and medium software projects, Software Engineering and Computer Systems,” in ICSECS 2011, Communications in Computer and Information Science. vol. 180. Berlin, Heidelberg: Springer, pp. 54–59. [Google Scholar]
23. M. Habiba, M. R. Islam and A. B. M. S. Ali. (2013). “Access control management for Cloud,” in 12th IEEE Int. Conf. on Trust, Security and Privacy in Computing and Communications, Melbourne, VIC, pp. 485–492. [Google Scholar]
24. G. Pujolle, A. Serhrouchni and I. Ayadi. (2009). “Secure session management with cookies,” in 7th Int. Conf. on Information, Communications and Signal Processing (ICICSMacau, pp. 1–6. [Google Scholar]
25. I. Alsmadi and I. Alazzam. (2016). “Websites’ input validation and input misuse based attacks,” in Cybersecurity and Cyberforensics Conf., Amman, pp. 113–116. [Google Scholar]
26. S. K. Mahmoud, M. Alfonse, M. I. Roushdy and A. M. Salem. (2017). “A comparative analysis of cross site scripting (XSS) detecting and defensive techniques,” in 8th Int. Conf. on Intelligent Computing and Information Systems (ICICISCairo, pp. 36–42. [Google Scholar]
27. G. B. de Pádua and W. Shang. (2017). “Revisiting exception handling practices with exception flow analysis,” in IEEE 17th Int. Working Conf. on Source Code Analysis and Manipulation, Shanghai, pp. 11–20. [Google Scholar]
28. R. Barona and E. A. M. Anita. (2017). “A survey on data breach challenges in cloud computing security: Issues and threats,” in Int. Conf. on Circuit, Power and Computing Technologies, Kollam, pp. 1–8. [Google Scholar]
29. A. Keikha and H. M. Nehi. (2015). “A complex method based on TOPSIS and choquet integral to solve multi attribute group decision making problems with interval type-2 fuzzy numbers,” in 4th Iranian Joint Congress on Fuzzy and Intelligent Systems, Zahedan, pp. 1–5. [Google Scholar]
30. S. Chen, S. Cheng and T. Lan. (2016). “A new multicriteria decision making method based on the topsis method and similarity measures between intuitionistic fuzzy sets,” in Int. Conf. on Machine Learning and Cybernetics, Jeju, South Korea, pp. 692–696. [Google Scholar]
31. S. Zhou, W. Chang, S. Zhou and W. Liu. (2014). “The method of risk evaluation for equipment development based on triangular fuzzy number and TOPSIS,” in The 26th Chinese Control and Decision Conf., Changsha, China, pp. 2272–2276. [Google Scholar]
32. F. Dammak, L. Baccour and A. M. Alimi. (2015). “The impact of criterion weights techniques in TOPSIS method of multi-criteria decision making in crisp and intuitionistic fuzzy domains,” in IEEE International Conf. on Fuzzy Systems, Istanbul, pp. 1–8. [Google Scholar]
33. L. W. Lee and S. M. Chen. (2008). “Fuzzy multiple attributes group decision-making based on the extension of TOPSIS method and interval type-2 fuzzy sets,” in Int. Conf. on Machine Learning and Cybernetics, Kunming, 8, pp. 3260–3265. [Google Scholar]
34. W. Hadikurniawati, E. Winarno, D. B. Santoso and Purwatiningtyas. (2019). “A mixed method using AHP-TOPSIS for dryland agriculture crops selection problem,” in 3rd Int. Conf. on Informatics and Computational Sciences, Semarang, Indonesia, pp. 1–5. [Google Scholar]
35. M. Alenezi, M. Nadeem, A. Agrawal, R. Kumar and R. A. Khan. (2020). “Fuzzy multi criteria decision analysis method for assessing security design tactics for web applications,” International Journal of Intelligent Engineering and Systems, vol. 13, no. 5, pp. 181–196. [Google Scholar]
36. M. A. Zytoon. (2020). “A decision support model for prioritization of regulated safety inspections using integrated delphi, AHP and double hierarchical TOPSIS approach,” IEEE Access, vol. 8, pp. 83444– 83464. [Google Scholar]
37. K. Sahu and Rajshree. (2015). “Stability: Abstract roadmap of security,” American International Journal of Research in Science, Engineering & Mathematics, vol. 2, no. 9, pp. 183–186. [Google Scholar]
38. R. Kumar, M. Zaroor, M. Alenezi, A. Agrawal and R. A. Khan. (2019). “Measuring security-durability of software through fuzzy-based decision-making process,” International Journal of Computational Intelligence Systems, vol. 12, no. 2, pp. 627–642. [Google Scholar]
39. A. Agrawal, M. Alenezi, R. Kumar and R. A. Khan. (2019). “Measuring the sustainable-security of web applications through a fuzzy-based integrated approach of AHP and TOPSIS,” IEEE Access, vol. 7, pp. 153936–153951. [Google Scholar]
40. K. Sahu, Rajshree and R. Kumar. (2014). “Risk management perspective in SDLC,” International Journal of Advanced Research in Computer Science and Software Engineering, vol. 4, no. 3, pp. 1247–1251. [Google Scholar]
41. R. Kumar, S. A. Khan and R. A. Khan. (2016). “Analytical network process for software security: A design perspective,” CSI Transactions on ICT, vol. 4, no. 2, pp. 255–258. [Google Scholar]
42. R. Kumar, A. I. Khan, Y. B. Abushark, M. M. Alam, A. Agrawal et al. (2020). , “An integrated approach of fuzzy logic, AHP and TOPSIS for estimating usable-security of web applications,” IEEE Access, vol. 8, pp. 50944–50957. [Google Scholar]
43. K. Sahu and R. K. Srivastava. (2018). “Soft computing approach for prediction of software reliability,” ICIC Express Letters, vol. 12, no. 12, pp. 1213–1222. [Google Scholar]
44. K. Sahu and R. K. Srivastava. (2020). “Needs and importance of reliability prediction: An industrial perspective,” Information Sciences Letters, vol. 9, no. 1, pp. 33–37. [Google Scholar]
45. A. Agrawal, M. Zaroor, M. Alenezi, R. Kumar and R. A. Khan. (2019). “Security durability assessment through fuzzy analytic hierarchy process,” PeerJ Computer Science, vol. 5, no. 5, pp. 1–43. [Google Scholar]
46. K. Sahu and R. K. Srivastava. (2019). “Revisiting software reliability,” in Data Management, Analytics and Innovation (Advances in Intelligent Systems and Computing), vol. 802, pp. 221–235, Springer. [Google Scholar]
47. R. Kumar, S. A. Khan and R. A. Khan. (2015). “Durable security in software development: Needs and importance,” CSI Communication, vol. 39, no. 7, pp. 34–36. [Google Scholar]
48. K. Sahu and Rajshree. (2015). “Software security: A risk taxonomy,” International Journal of Computer Science & Engineering Technology, vol. 7, no. 3, pp. 36–41. [Google Scholar]
49. K. Sahu and Rajshree. (2015). “Helpful and defending actions in software risk management: A security viewpoint,” Integrated Journal of British, vol. 4, pp. 1–7. [Google Scholar]
50. R. Kumar, S. A. Khan and R. A. Khan. (2016). “Durability challenges in software engineering,” Crosstalk, vol. 29, no. 5, pp. 29–31. [Google Scholar]
51. S. A. Khan, M. Alenezi, A. Agrawal, R. Kumar and R. A. Khan. (2020). “Evaluating performance of software durability through an integrated fuzzy-based symmetrical method of ANP and TOPSIS,” Symmetry, vol. 12, no. 4, pp. 1–15. [Google Scholar]
52. A. Agrawal, M. Alenezi, S. A. Khan, R. Kumar and R. A. Khan. (2019). “Multi-level fuzzy system for usable-security assessment,” Journal of King Saud University–-Computer and Information Sciences, pp. 1–9. [Google Scholar]
53. R. Kumar, S. A. Khan, A. Agrawal and R. A. Khan. (2018). “Measuring the security attributes through fuzzy analytic hierarchy process: Durability perspective,” ICIC Express Letters–-An International Journal of Research and Surveys, vol. 12, no. 6, pp. 615–620. [Google Scholar]
54. A. Agrawal, M. Alenezi, D. Pandey, R. Kumar and R. A. Khan. (2019). “Usable-security assessment through a decision making procedure,” ICIC Express Letters–-Part B Applications, vol. 10, no. 8, pp. 665–672. [Google Scholar]
55. M. Alenezi, R. Kumar, A. Agrawal and R. A. Khan. (2019). “Usable-security attribute evaluation using fuzzy analytic hierarchy process,” ICIC Express Letters–-An International Journal of Research and Surveys, vol. 13, no. 6, pp. 453–460. [Google Scholar]
56. R. Kumar, S. A. Khan and R. A. Khan. (2017). “Fuzzy analytic hierarchy process for software durability: Security risks perspective,” Advances in Intelligent Systems and Computing, vol. 508, pp. 469–478. [Google Scholar]
57. A. Agrawal, M. Alenezi, R. Kumar and R. A. Khan. (2020). “A unified fuzzy-based symmetrical multi-criteria decision-making method for evaluating sustainable-security of web applications,” Symmetry, vol. 12, no. 3, pp. 1–23. [Google Scholar]
58. R. Kumar, A. I. Khan, Y. B. Abushark, M. M. Alam, A. Agarwal et al. (2020). , “A knowledge based integrated system of hesitant fuzzy set, AHP and TOPSIS for evaluating security-durability of web applications,” IEEE Access, vol. 8, no. 2, pp. 48870–48885. [Google Scholar]
59. M. Alenezi, A. Agrawal, R. Kumar and R. A. Khan. (2020). “Evaluating performance of web application security through a fuzzy based hybrid multi-criteria decision-making approach: Design tactics perspective,” IEEE Access, vol. 8, no. 1, pp. 25543–25556. [Google Scholar]
60. R. Kumar, S. A. Khan, A. Agrawal and R. A. Khan. (2018). “Security assessment through fuzzy Delphi analytic hierarchy process,” ICIC Express Letters–-An International Journal of Research and Surveys, vol. 12, no. 10, pp. 1053–1060. [Google Scholar]
61. Q. Li. (2010). “An Improved fuzzy AHP approach to evaluating conductor joint alternatives,” in 7th Int. Conf. on Fuzzy Systems and Knowledge Discovery, Yantai, China, pp. 811–814. [Google Scholar]
62. B. Öztaysi, S. Ç. Onar, E. Boltürk and C. Kahraman. (2015). “Hesitant fuzzy analytic hierarchy process,” in IEEE Int. Conf. on Fuzzy Systems (FUZZ-IEEEIstanbul, pp. 1–7. [Google Scholar]
63. A. Agrawal, A. Pandey, A. Baz, H. Alhakami, W. Alhakami et al. (2020). , “Evaluating the security impact of healthcare web applications through fuzzy based hybrid approach of multi criteria decision making analysis,” IEEE Access, vol. 8, pp. 135770–135783. [Google Scholar]
64. R. Kumar, A. I. Khan, Y. B. Abushark, M. M. Alam, A. Agrawal et al. (2020). , “A knowledge based integrated system of hesitant fuzzy set, AHP and TOPSIS for evaluating security durability of web applications,” IEEE Access, vol. 8, pp. 48870–48885. [Google Scholar]
65. A. Agrawal, M. Alenezi, R. Kumar and R. A. Khan. (2019). “Measuring the sustainable security of web applications through a fuzzy based integrated approach of AHP and TOPSIS,” IEEE Access, vol. 7, pp. 153936–153951. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |