DOI:10.32604/cmc.2021.013303

| Computers, Materials & Continua DOI:10.32604/cmc.2021.013303 |  |
| Article |
Intelligent Software-Defined Network for Cognitive Routing Optimization Using Deep Extreme Learning Machine Approach
1Department of Computer Information System, College of Computer Science and Information Technology, Imam Abdulrahman Bin Faisal University, Dammam, 31441, Saudi Arabia
2Department of Computer Science, Umm Al-Qura University, Makkah City, 715, Saudi Arabia
3Department of Computer Science, Lahore Garrison University, Lahore, 54792, Pakistan
4School of Computer Science, NCBA&E, Lahore, 54000, Pakistan
5Department of Computer Science, College of Computer Science and Information Technology, Imam Abdulrahman Bin Faisal University, Dammam, 31441, Saudi Arabia
*Corresponding Author: Muhammad Adnan Khan. Email: madnankhan@lgu.edu.pk
Received: 30 July 2020; Accepted: 04 September 2020
Abstract: In recent years, the infrastructure, instruments, and resources of network systems are becoming more complex and heterogeneous, with the rapid development of current internet and mobile communication technologies. In order to efficaciously prepare, control, hold and optimize networking systems, greater intelligence needs to be deployed. However, due to the inherently dispensed characteristic of conventional networks, Machine Learning (ML) techniques are hard to implement and deployed to govern and operate networks. Software-Defined Networking (SDN) brings us new possibilities to offer intelligence in the networks. SDN’s characteristics (e.g., logically centralized control, global network view, software-based site visitor analysis, and dynamic updating of forwarding rules) make it simpler to apply machine learning strategies. Various perspectives of fiber-optic communications including fiber nonlinearity coverage, optical performance checking, cognitive shortcoming detection/anticipation, and arranging and improvement of software-defined networks are examined in Machine Learning (ML) applications. This research paper has presented an imaginative framework concept called Intelligent Software Defined Network (ISDN) for Cognitive Routing Optimization (CRO) using Deep Extreme Learning Machine (DELM) approach (ISDN-CRO-DELM) in light of the new challenges in the development and operation of communication systems, and capturing motivation from how living creatures deal with difficulty and usability. The proposed methodology develops around the planned applications of progressive DELM methods and, specifically, probabilistic generative models for framework wide learning, demonstrating, improvement, and information description. Furthermore, ISDN-CRO-DELM, suggest to integrate this learning framework with the ISDN for CRO and reconfiguration approaches at the system level. MATLAB 2019a is used for DELM simulation and superior results show the effectiveness of the proposed framework.
Keywords: SDN; DELM; machine learning; cognition
In recent times, data processing is growing exponentially in the world, with the accelerated growth of mobile devices (e.g., cell phones, mobile vehicles and smart home appliances) as well as network technology (e.g., cloud storage and edge computing) [1]. Networks are becoming heterogeneous and it is a challenge to automate the flow of traffic and control a large number of devices [2]. In general, the production network uses many devices, operates a number of procedures and supports a number of applications [3,4]. As an example, different types of modules have been used in wireless networks, such as ZigBee, WiMAX, IEEE 802.11 ac/ad, Bluetooth, and Long-Term Evolution (LTE), with specific communication range, strength, and operating mechanisms and numerous communication technologies. Further, transparency in networks is one way to solve these problems. A few years ago, the Knowledge Plan (KP) proposed an approach to develop automation, advice and wisdom on the Internet through the use of ML and cognitive technologies [5]. However, the KP is still not prototyped or implemented at the time of this writing. The main reason is that conventional networks are fundamentally distributed, where each node, such as a router or switch, can only access and operate on a small network ratio. It’s really hard to learn from the networks that they have only a partial knowledge of the entire network to manage the entire domain [6]. Luckily, recent developments in the Software Defined Network (SDN) domain will enable learning more complex.
In the other direction, this will enable us to develop massive information and communication technologies (ICTs) [7]. Even today, no one can imagine our life without the Internet [8]. It is even hard to consider that the increasing accessibility of connected products means that today the Internet has not gained its importance by enabling people to discover data and providing us with innovative facilities in our daily lives [9]. According to the Internet of Things (IoT) European Research Cluster, IoT is a vibrant, global network infrastructure that automatically configures and communicates physical and virtual objects through standard and interoperable procedures. IoT would have been the best hope for a viable city [10]. In order to make IoT smart, a number of computational technologies use IoT. Considering a wide range of IoT applications, data mining, artificial intelligence, cloud computing and neural networks are among the most important technologies [11].
Cognitive networks focus on the “cognitive loop” as shown in Fig. 1. The Sense, Plan, Decision, Act, follow a full cognitive protocol with learning and environmental input. The state of sense gathers, tracks, and pre–processes information. The plan state then interprets the collected data in the framework and uses the findings for scheduling purposes. The state of Decision sets out the measures and analyzes information for possible options. Eventually, the active state imposes the actual operation of the network. Environmental data is used to restart the loop and in the final control, alarms and alerts can also be sent. All previous states provide feedback that improves the efficiency and response of the learning algorithm under the specified policies.
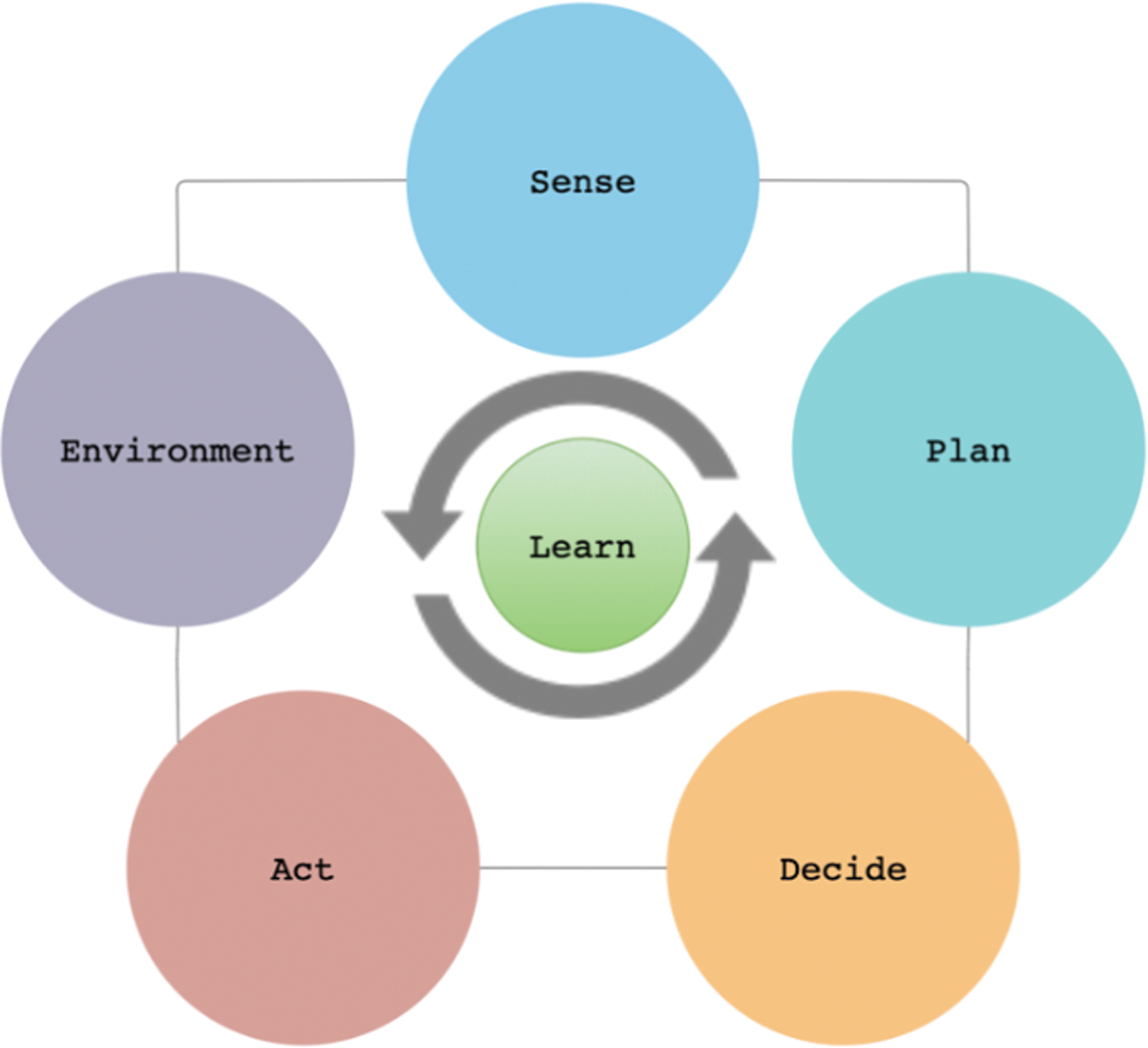
Figure 1: The cognition loops
Some of the work on cognitive networks suggested that cognitive entities may use the best tools to perform optimization tasks [12,13], while others have used special reasoning techniques: they have also not explained clearly why these techniques should be chosen [14]. Over the last decade, numerous published papers have explored the implementation of various ML algorithms with a view to improving the limited management capabilities of legacy SDNs.
The Internet of Things (IoT) transforms communities around the world into “smart cities” by creating a new way of living in urban areas [15]. Main advantages include improved safety, health, improved environment for education and housing, energy consumption, better climate and ecosystem efficiency, green economy and better employment [3]. Although the central knowledge of smart cities has been around for more than a decade, the definition has improved a lot since its initial release, it is now expected to fundamentally change city life as a number of important facilitators. Hall et al. [16] claimed that the vision of smart cities for all systems, such as electricity, water and logistics, is a clean, stable, green and efficient future metropolitan center. Bakıcı et al. [17] indicated that smart city is an innovation-intensive and better city that combines people, information and urban features with innovative technology to create a healthy and safe city with competitiveness and innovative commerce to improve quality of life. Giffinger et al. [18] argued that the smart city is an ingenious community in which a number of components, such as individuals, ecosystems, flexibility, democracy and the economy, are integrated into a smart system.
In our research, SDN routing optimization is the primary concept for the implementation of complicated network tracking systems or malicious behavior or policy infringement systems. This work summarizes the problems of SDN routing and smart networking, and then defines a coherent framework for optimizing the software-defined network. The DELM method will be used to make software-defined networks more secure with improved performance. Safe and efficient networks bring together potential smart cities with advanced systems and policies to adapt to demands [19].
The control plane and the data plane shall be separated by the SDN. The network resources in SDN are managed by the networking operating system, which serves as a logically centralized controller. The network must be dynamically managed by the SDN controller. In addition, the centralized controller has a global perspective on the system by monitoring and assembling the status and arrangement of the system information as well as packet and stream sized data.
The implementation of SDN ML methods is acceptable and effective for the following reasons. First, the recent development of computer technology such as the Graphical Processing Unit (GPU) and the Tensor Processing Unit (TPU) provides a decent opportunity to use the exciting ML networking area (e.g., deep neural networks) [20,21]. Second, data is essential for data-driven machine learning algorithms. The concentrated SDN controller has a global network opinion and is able to gather numerous network information that makes the implementations of ML algorithms easier. Third, ML methods can transport SDN controller intelligence based on data assessment, network optimization in addition to the automated delivery of network facilities based on the historical network, and real-time information. Finally, SDN technology allows optimized network solutions (e.g., configuration and resource allocation) to be used in real-time on the network using machine-learning algorithms [22].
Present cognitive science theory has presented various approaches that conflict with the way they tackle the relationship between sensory-motor and cognitive processes. This research adds to the dialog by claiming that the investigation is appropriately expressed as a developmental investigation and that, eventually, in order to perceive the properties of human cognition, the researcher asked how human cognition had these properties. The researcher assumes that, since advancement creates brains, bodies, and conditions for cognition, it is inflexibly linked to procedures for detecting and acting invisible to them.
This article examines the state-of-the-art ML strategies that can be developed and implemented in SDN. The review will focus on the use of ML methods to enhance the efficiency, intelligence, effectiveness and safety of SDN, followed by a concise diagram of things to inquire about presented solutions in related regions. The proposed model is included in the methodology as shown in Fig. 2. This paper examines the DELM for optimization of the software-defined network in order to achieve optimum accuracy. A data set, NSL-KDD, with 47840 data samples is used in the training and testing of SDN optimization with DELM, so that each sample has specific and diverse features. The analysis and comparison shall be carried out using state-of-the-art approaches of machine learning.
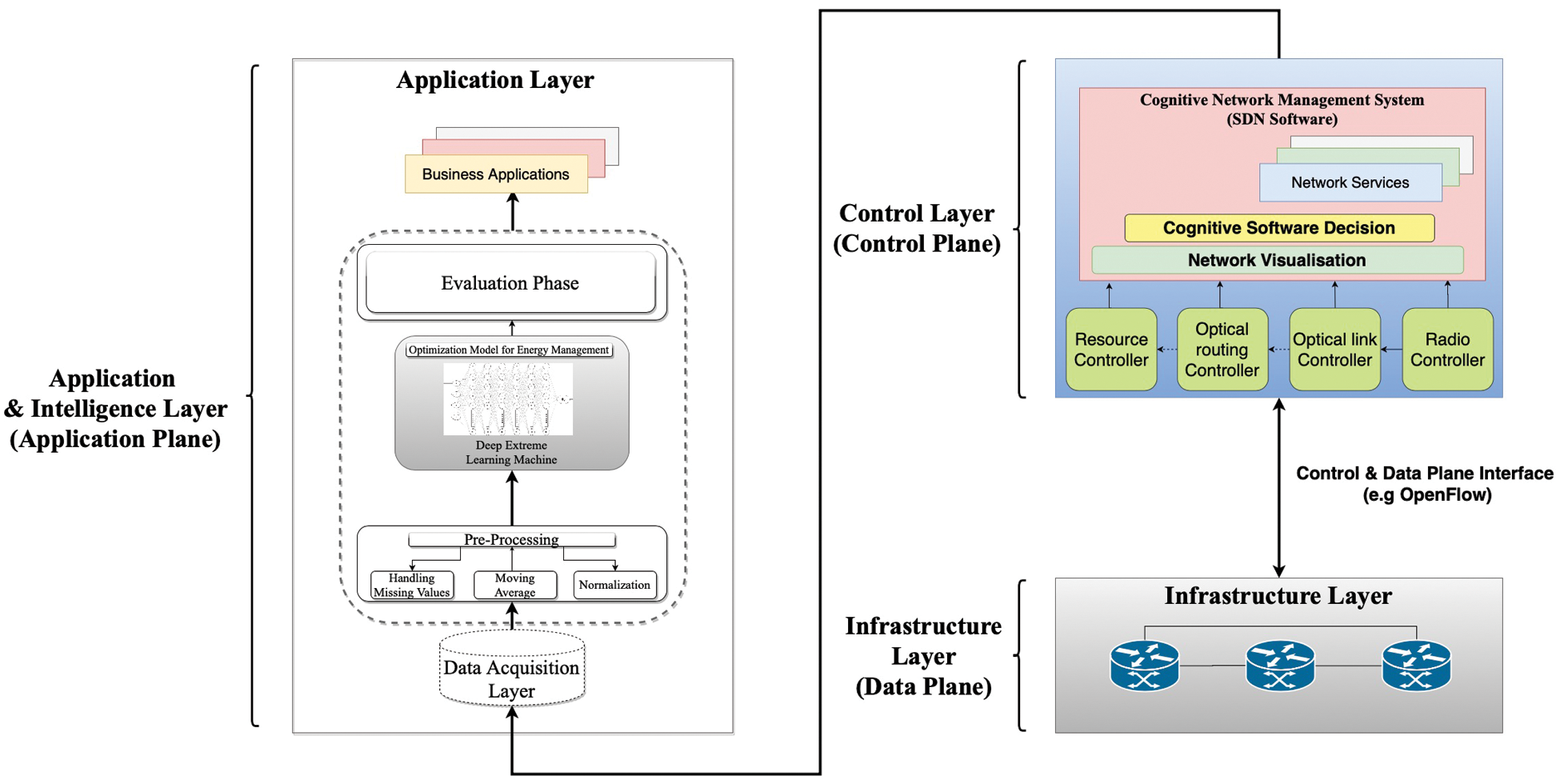
Figure 2: Proposed model for software defined network routing optimization
ML applications have attracted a lot of attention. Patcha et al. [23] have provided a thorough report of the applications for intrusion detection ML methods. Nguyen et al. [24] have reported a detailed description on the classification of IP traffic using ML. Bkassiny et al. [25] have researched many complex learning difficulties in Cognitive Radio Networks (CRNs) and analyzed current ML-based solutions. How ML approaches can be utilized to solve common problems in the network of wireless sensors has been investigated in [26]. Wang et al. [27] presented state-of-the-art techniques to develop heterogeneous networks in Artificial Intelligence (AI) and discussed future research problems. Buczak et al. [28] investigated cybersecurity intrusion detection methods for ML and Data Mining (DM). Klaine et al. [29] have investigated classification & comparison of machine-learning systems and their results in cellular networks. Fadlullah et al. [30] have explored how ML methods can be used to enhance network traffic organizations. Similar to [23], Hodo et al. [31] have focused on the ML-based Intrusion Detection System (IDS). Zhou et al. [32] have investigated on the utilization of ML and cognitive radiation innovation to develop the wireless 2 network spectrum and enhanced its energy efficiency. Chen et al. [33] have researched solutions based on neural networks to address wireless network problems such as connectivity, virtual reality and edge caching.
Tang et al. [34] have managed to incorporate artificial intelligence in fog computing to facilitate intelligent large-scale data discovery. Feng et al. [35] have presented a theoretical paradigm for smart households utilizing theoretical analytics, IoT frameworks, Bayesian Inference and Reinforcement Learning (RL) models in their cognitive memory. Cognitive IoT (CIoT) is another work initiative designed to build a cognitive framework for IoT applications [36]. Vlacheas et al. [37] have proposed a cognitive management system that would enable intelligent objects to interact and benefit end-users.
Moore et al. [38] have predicted that by 2050, 70% of the world would reside in cities. The smart concept is used to build comfort in your life. Smart City is an initiative that uses new technologies to enhance the efficiency of public life. Smart cities also enhance environmental efficiency and provide residents with optimum amenities [39]. Transmission and computer technology are essential for the promotion and transformation of urban areas into smart cities [40]. The Internet of Things (IoT) integrates a wide range of physical objects, vehicles, smartphones and devices that can communicate and share data with equipment, apps, controllers, sensors and the network. Data mining approaches and machine learning algorithms should be equipped to collect details and expertise on the development of data waste [41].
SDN has received widespread attention in recent years. The Open Networking Foundation is a non-profit consortium that aims to develop standardize SDNs. The Open Networking Foundation (ONF) describes the SDN as follows, “The control plane, data plane and network intelligence are logically decoupled, network intelligence and the underlying network architecture is logically centralized and excluded from applications” [42].
With regard to routing optimization, Francois et al. [43] have designed Random Neural Networks with Reinforcement Learning (RL) based centralized Cognitive Routing Engine (CRE) that recognizes the optimized network paths. Raimundo-Neto et al. [44] have proposed a wireless network with a cognitive optical wireless system of 2.4 and 5 GHz. Shan et al. [45] have suggested a centralized wireless cognitive compression sensing algorithm. Li et al. [46] have proposed an enhanced learning approach that is implemented in cognitive wireless through fiber to introduce dynamic channel selection. All processing capabilities are based on Cognitive Access Point (CAP), which gathers snapshots of different Routing Area Update (RAU).
Recent research [47,48] on the importance of cognitive use in femtocells (small cells) research shows that Quality of Service (QoS) is compromised with potential interferences. It also stresses opportunistic cellular network cooperation. Therefore, an effective network management system is required for cognitive deployment. SDN is an active area of research that can support a high efficiency and provide intelligent control of the network.
Although the performance of the SDN in various organizations has been encouraging, the separation of the control plane from the data plane increases the likelihood that the SDN application would be exposed to multiple challenges and risks [49]. As a result, SDNs are susceptible to a number of network infringements, including volumetric threats. These attacks will bring security concerns to the three layers of SDN. There are several security mechanisms to detect and mitigate Denial of Service (DoS) attacks on the SDN network as presented in [50]. Such strategies are constructed by collecting the flow characteristics of the packets received, such as the average number of packets, the Internet Protocol (IP) address size, the average number of bytes, etc.
In case of the malicious traffic, the monitoring packages are larger in size than the threshold or borderline of the decision as described above [51]. Although current techniques do not require a high level of data flow management and monitoring tools, they cannot protect the network for a long time. The main drawbacks of the current situation are the rapid increase in the information and the large data packets to be managed in real time. Due to a similarity between good traffic and malicious packets, it is difficult to detect malicious traffic. The intruder will easily adjust the packet header to mimic the usual traffic and mislead the protection systems. As anomalies are constantly evolving, the attacker can make simple changes that will make it possible to use this technique with new attacks. A lot of research has been performed in a number of areas, but only a few have used SDN [52].
The concept describes a high-level SDN architecture consisting of three primary planes, the information plane, control plane, and application plane. The structural modules and connections of each plane have been presented in Fig. 2.
The data plane is the lowest layer in the SDN framework and is also referred to as the infrastructure plane. This plane consists of transmission gadgets consisting of physical switches and virtual switches. Virtual switches are built-in programming tools that can run within normal operating frameworks. These switches are responsible for delivering, dropping, and modifying packets based on the Control Plane (CP) policy. The control plane is connected to the Southbound Interfaces (SBIs) by means of which the control unit can control the processing and transmission capabilities of the data plane.
The control plane is the intelligence of SDN schemes that can program network resources, dynamically change security regulations and make network management scalable and agile. The central module of the control unit is a reasonably central control plane that manages communication between transmission units and applications. Next, the controller uncovered and outlined information from the data plane to the application plane. On the other hand, the controller is modifying the request into custom strategies and disseminating it to sending units. The controller also offers vital features, along with shortest route routing, network topology stockpiling, gadget design, and national data warnings, that a considerable number of system applications require. Fig. 3 shows the Cognitive Software Decision (CSD) is comprised of four layers named sensing control layer, data semantic layer, decision making layer, and service evaluation layer.
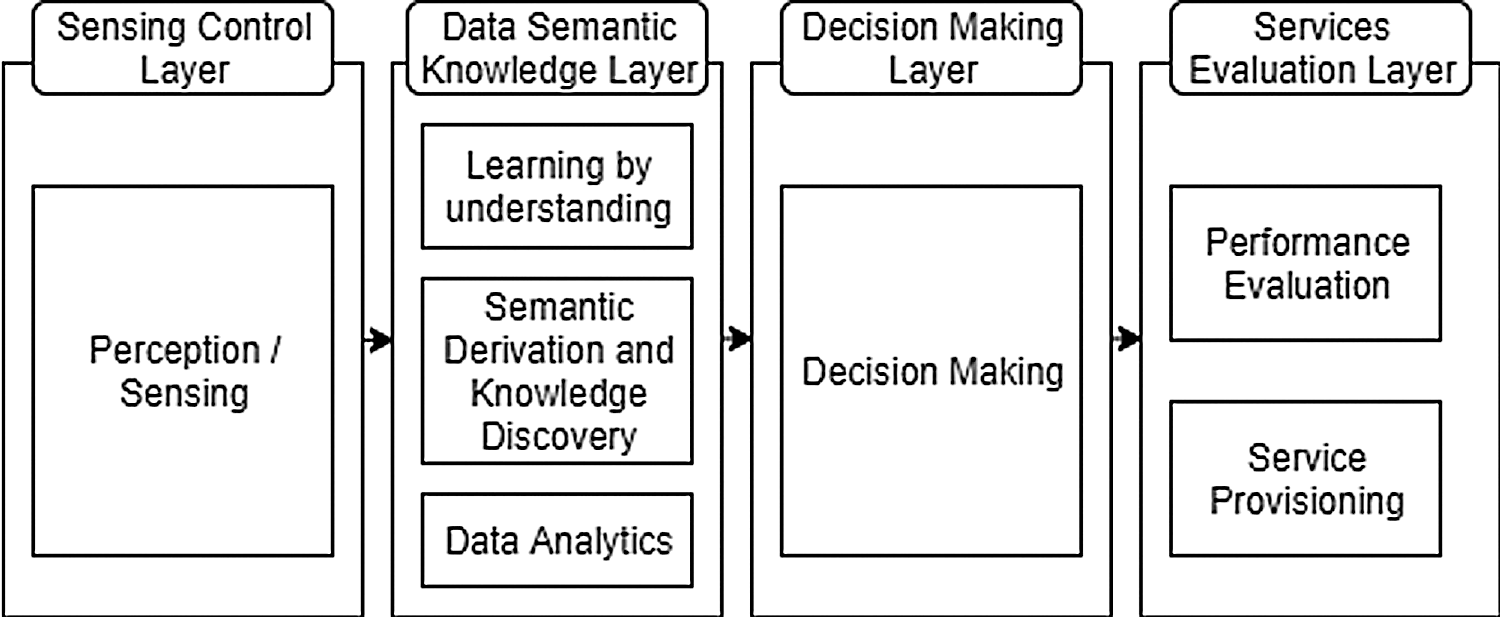
Figure 3: Proposed model for cognitive software decision
This is the fundamental layer that contains the significant participation of this research. This layer is a cognitive software designed inspired layer that has the ability to detect the ground similar to a human’s performance. The entire CSD is comprised of the sensing process.
3.1.2 Data Semantic Knowledge Layer
In view of the information that has been sent from the sensing control layer, this layer changes the information into knowledge utilizing semantic reasoning and knowledge learning. The data is sent to the decision-making layer.
This layer is accountable for making the decision based on the gathered data from the data semantic layer. This layer can establish itself in which movement is dependent on the present state.
3.1.4 Service Evaluation Layer
This layer is inclined to negotiating the service of the sensors and furthermore liable for assessing its display based on the service provider.
The application plane consisting of business applications is the top layer within the SDN framework. These applications can provide new facilities and optimize business processes. In general, the NBIs of the controllers allow applications to obtain the necessary network information. Applications may implement the control logic to modify the actions of the network, based on the data received and the business needs.
Fig. 4 illustrates the number of hidden layers, hidden neurons, and different forms of activation functions that have been employed in the Deep Extreme Learning Machine (DELM) to obtain the optimal architecture for enhancing the software-defined network. The suggested methodology consists of three separate layers, specifically the data collection, pre-processing, and the application layer. The application layer consists of two sub-layers in which one layer is for prediction and the other layer is for evaluation. Real data was obtained from sensors for experimental research. After the collection of data from the sensor, the data is delivered as feedback to the data collection level. In the pre-processing layer, numerous information cleaning and analysis processes were applied to eliminate irregularities in the data. In the application layer, DELM has been utilized for software-defined network optimization.
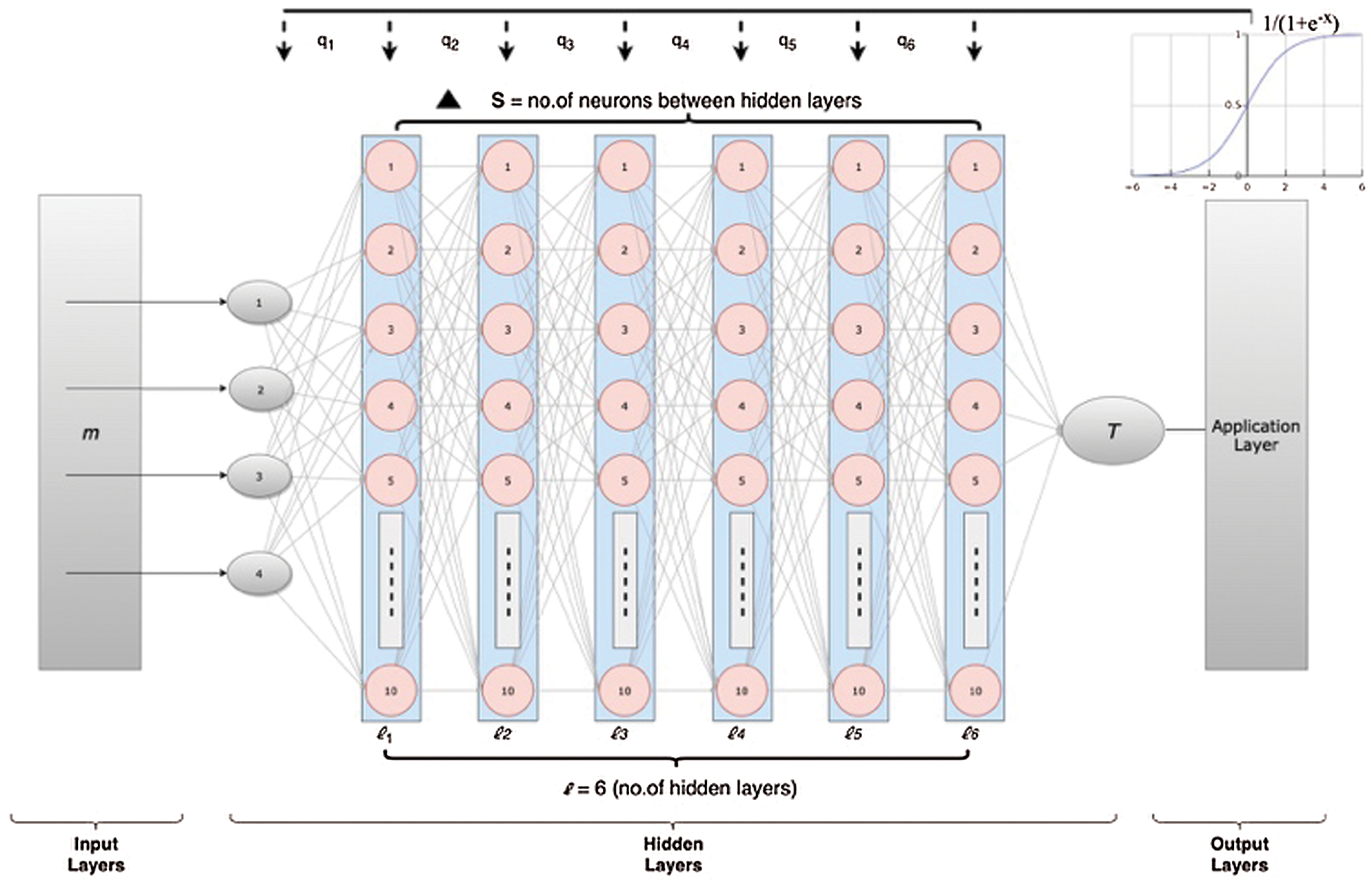
Figure 4: Systemic illustration of a deep extreme learning machine
3.2 Deep Extreme Learning Machine
The Deep Extreme Learning Machine (DELM) can be used in various fields to predict health problems, energy consumption forecasts, transport and traffic management, etc. [53–55]. DELM can be widely used for identification and regressive objectives in various ways, as it learns quickly and improves the level of framework complexity.
Extreme Learning Machine (ELM) is a feed-forward neural network, which means that input only travels one direction across a set of layers, but we have also used the back-propagation approach in this predictive framework through the training process, where data streams back across the network and back-propagation, the neural network adjusts weights to achieve high accuracy at minimal error. Weights are constant during the validation phase of the network in which the qualified model is imported and actual data is predicted. Information layer, numerous hidden, with one output layer in the DELM model. Fig. 4 shows the fundamental model of a DELM in which m is described as input, 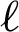 describes hidden, and op denotes output layer nodes.
describes hidden, and op denotes output layer nodes.
Mean Square Error (MSE) measurement to optimize software-defined network illustrated during the evaluation phase. In the deep extreme learning machine method, the input, hidden, and output node are notated as an, pi, and gm, correspondingly, while all the N input nodes, l hidden nodes, and M output nodes can be illustrated as  ,
, 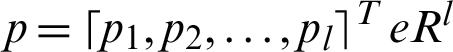 ,
,  , correspondingly. The DELM framework will therefore be efficiently portrayed as:
, correspondingly. The DELM framework will therefore be efficiently portrayed as:

And

where 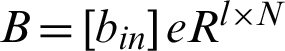 ,
, 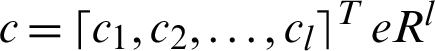 ,
, 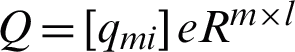 , and the activation function f( ) could be employed as sigmoid, linear Gaussian prototypes, etc.
, and the activation function f( ) could be employed as sigmoid, linear Gaussian prototypes, etc.
Assume here are V different training data, and allow 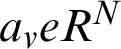 and
and 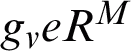 and denote the vth training and the resulting vth training outcome, correspondingly, where
and denote the vth training and the resulting vth training outcome, correspondingly, where 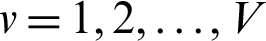 . In the training set the input structure and outcome structure presented as:
. In the training set the input structure and outcome structure presented as:

And

Correspondingly. We are able to replace Eq. (3) into Eq. (1) to acquire

where 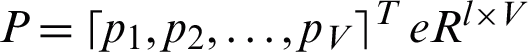 is the assessment categorization of all l hidden nodes, and
is the assessment categorization of all l hidden nodes, and  Kronecker product Rewrite Eqs. (4) and (5) in Eq. (2) to attain the real training sequence.
Kronecker product Rewrite Eqs. (4) and (5) in Eq. (2) to attain the real training sequence.

In DELM, only output weight Q is adaptable, though B (for example the input weights) and c (for example the prejudices of the hidden nodes) are randomly focused. Label the projected outcome as Y. Afterward DELM purely reduces the evaluation error.

By considering a minimum combination of squares Q for the situation

where 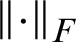 indicates the Frobenius norm. For the problematic Eq. (8), an outstanding least-square minimum standard solution is:
indicates the Frobenius norm. For the problematic Eq. (8), an outstanding least-square minimum standard solution is:

To prevent overfitting, it is possible to use the common Tikhonov regularization to adjust Eq. (9) into

where 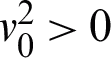 indicate the regularization phrase. The backpropagation method involves the configuration of weight, forward propagation, backward propagation of error, and the updating of distinguishability. An activation function like
indicate the regularization phrase. The backpropagation method involves the configuration of weight, forward propagation, backward propagation of error, and the updating of distinguishability. An activation function like 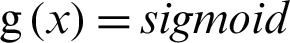 is present in the hidden layer on each neuron. This helps to design the sigmoid input function and the DELM hidden layer.
is present in the hidden layer on each neuron. This helps to design the sigmoid input function and the DELM hidden layer.

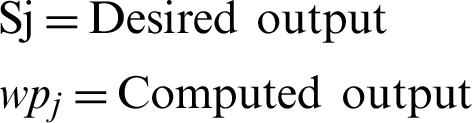
Eq. (11) specifies a backpropagation error, which can be measured by splitting the square summation from the required outcome by 2. The adjustment in weight is needed to mitigate the common error. The weight shift rates are shown for the output layer in Eq. (12).

where 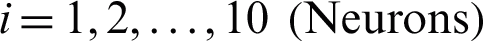 and
and 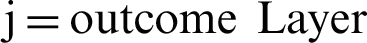

Write Eq. (13) through the chain rule technique:

The change weight value can be obtained by replacing the values in Eq. (13) as indicated in Eq. (14).
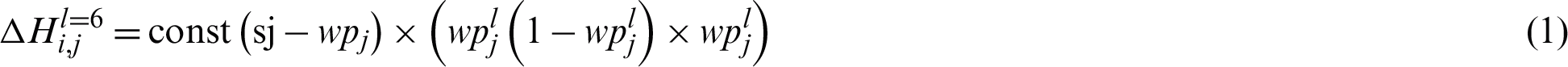
From wp to H6

The calculation for the related weight shift to the hidden weight is shown in the following segment. It is quite complicated, because it may contribute to errors per weighted association on the growing node.
From H6 to H1 or Hn
where n = 5, 4, 3, 2, 1
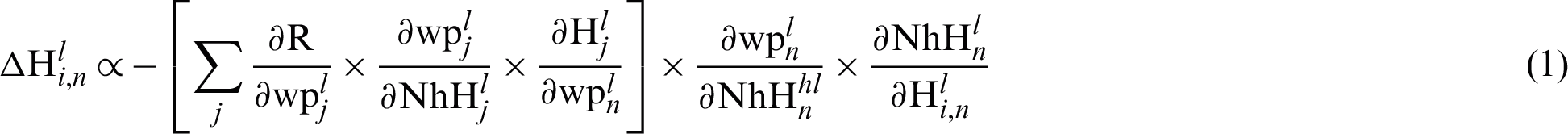
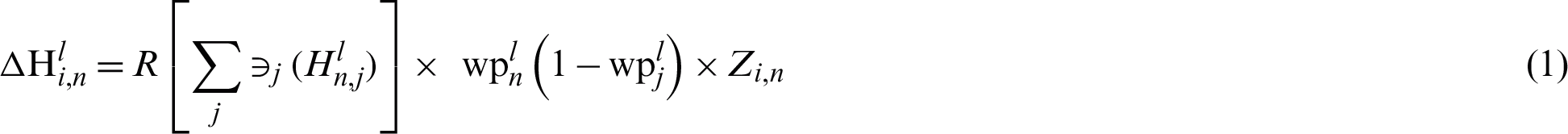

where

The method for increasing the weight and the bias among the performance and the hidden layer is illustrated in Eq. (16e).

Eq. (17) Demonstrates how weight and difference amongst input and hidden layer can be changed.

The DELM method was employed in the suggested article [56] using MATLAB 2019. The proposed solution based on DELM was used to train and fit the 148516 information instances. This information is distributed randomly to 85% of the training (125973 records), and 15% of the records are used for validation (22543 records). The data is pre-processed in order to remove anomalies and error values. Along these lines, the proposed system has used a large number of neurons and a variety of dynamic capacities are used in hidden layers. The proposed DELM is implemented in order to investigate the viability of the proposed framework. In order to evaluate the DELM approach, we have used the accuracy and misrate of the factual estimates as described in the following equations (Eqs. (18), (19)).


In Eqs. (18) and (19), O signifies the projecting outcome of SDN and T denotes the real outcome. O0 and T0 show that the situation is normal and no attack is found in the predictive output and actual output respectively. O1 and T1 represents the attack is found in the predictive and actual outputs respectively. 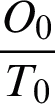 and
and 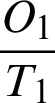 signifies that predictive and real output are same. Similarly,
signifies that predictive and real output are same. Similarly, 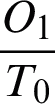 and
and 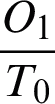 signifies the difference between the predictive and real outputs.
signifies the difference between the predictive and real outputs.
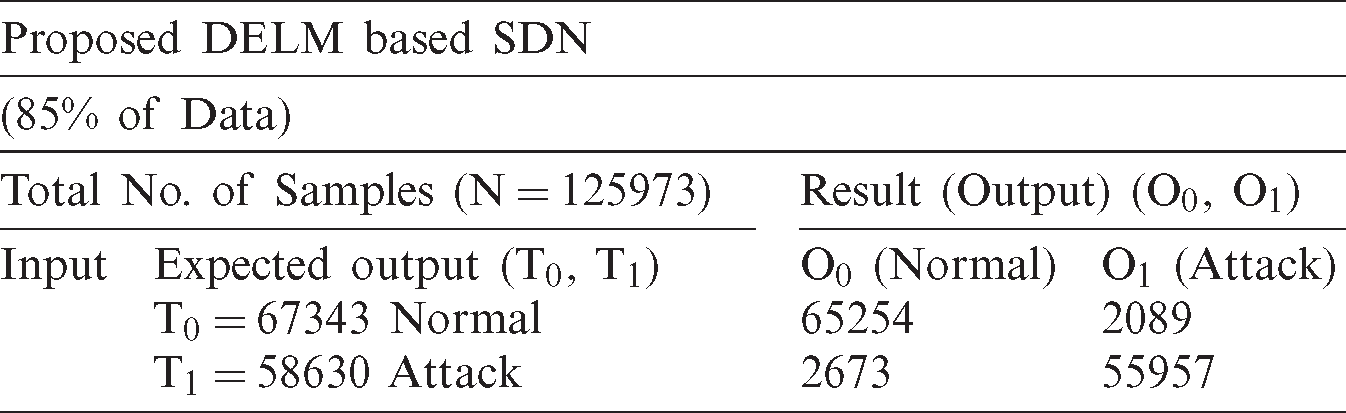
Tab. 1 shows the proposed DELM based software-defined network model that predicts intrusion detection during the training phase. In training, a total of 125973 samples are included, which are then divided into 67343 and 58630 for normal and attack conditions. It is observed that 65254 normal-class samples without any attack are correctly predicted and 2089 records are misclassified. Likewise, a total number of 58630 samples are obtained in the event of an attack, in which 55957 samples are correctly predicted and 2673 records are found to be incorrect.
Table 1: Training of the suggested DELM based software defined network framework during the prediction of intrusion
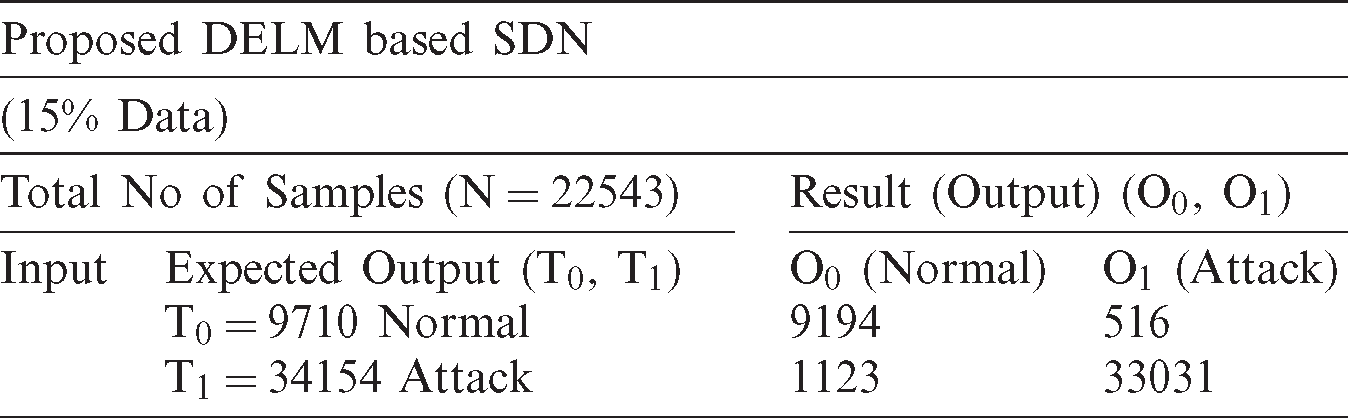
Tab. 2 shows the proposed DELM based software-defined network model that predicts intrusion detection during the validation stage. In validation, a total of 22543 samples are included that are split into 9710 and 34154 for normal and attack conditions. It is observed that 9194 samples of the normal class are correctly predicted and 516 records are misclassified. Similarly, out of total 34154 samples, 33031 samples are correctly predicted and 1123 records are found to be incorrect.
Table 2: Validation of the suggested DELM based software defined network framework during the prediction of SDN attack
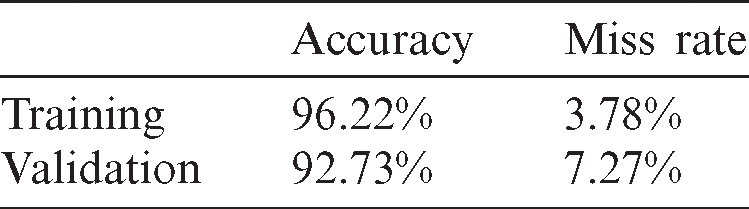
Tab. 3 demonstrates the proposed DELM-based software-defined network architecture output in terms of accuracy and error rate across the training and validation process. It is shown that the projected DELM based software-defined network system in training achieves 96.22% and 3.78% accuracy and miss rate correspondingly. In across validation, the proposed DELM based software-defined network system attains 92.73% and 7.27% accuracy and miss rate, respectively.
Tab. 4 shows the performance of the proposed DELM based software defined network model using DELM in comparison to previous approaches in the literature [57,58].
Table 3: Performance assessment of proposed deep extreme learning machine-based software defined network system model in validation & training
Tab. 4 shows the comparison of attacks in SDN for the proposed DELM model with previous methods as proposed by Li et al. [57] and Cui et al. [58]. Accuracy and Miss Rate metrics are used to measure the evaluation of the proposed DELM based software-defined network system model with l [57,58].
Table 4: Comparison results of the DELM based software defined network framework with literature
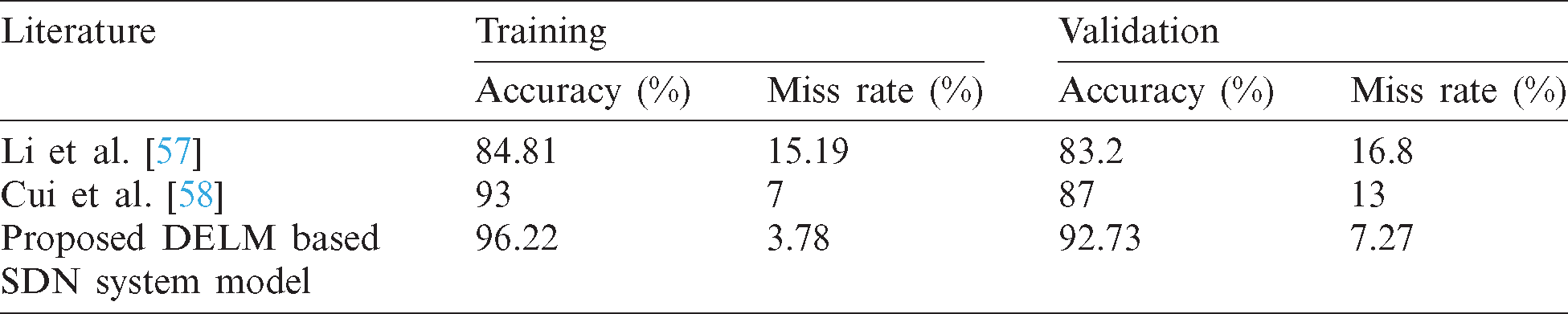
The proposed DELM based Software Defined Network model achieves the best classification results of 96.22% and 92.73% for accuracy whereas 3.78% and 7.27% miss rate are computed in training and validation phases respectively.
In this research, the proposed methodology has introduced an innovative concept called Intelligent Software Defined Networking (ISDN) for Cognitive Routing Optimization (CRO) using Deep Extreme Learning Machine (DELM) approach (ISDN-CRO-DELM). The proposed research has employed DELM technique for simulation and attained better results in comparison to the previous techniques. Considering past approaches, the proposed DELM technique outperforms them and achieves superior performance. The proposed technique exhibits 96.22% accuracy that is far better than the existing techniques. In future, our proposed technique will be expanded by including more datasets and new machine learning techniques, structures, and algorithms will be employed.
Acknowledgement: Thanks to our families & colleagues who supported us morally.
Funding Statement: This Work is supported by Data and Artificial Intelligence Scientific Chair at Umm AlQura University.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. A. Atta, S. Abbas, M. A. Khan, G. Ahmed and U. Farooq. (2020). “An adaptive approach: Smart traffic congestion control system,” Journal of King Saud University-Computer & Information Sciences, vol. 32, no. 9, pp. 1012–1019.
2. H. Chourabi, T. Nam, S. Walker, J. R. Gil-Garcia, S. Mellouli et al. (2012). , “Understanding smart cities: An integrative framework,” in Proc. of 45th Hawaii Int. Conf. on System Science, Maui, HI, pp. 2289–2297.
3. A. Fatima, M. A. Khan, S. Abbas, M. Waqas, L. Anum et al. (2019). , “Evaluation of planet factors of smart city through multi-layer fuzzy logic (MFL),” ISC International Journal of Information Security, vol. 11, no. 3, pp. 51–58.
4. M. Naphade, G. Banavar, C. Harrison, J. Paraszczak and R. Morris. (2011). “Smarter cities and their innovation challenges,” Computer, vol. 44, no. 6, pp. 32–39.
5. D. D. Clark, C. Partridge, J. C. Ramming and J. T. Wroclawski. (2003). “A knowledge plane for the internet,” in Proc. of the 2003 Conf. on Applications, Technologies, Architectures, & Protocols for Computer Communications, Germany, pp. 3–10.
6. A. Mestres, A. Rodriguez-Natal, J. Carner, P. Barlet-Ros, E. Alarcon et al. (2017). , “Knowledge-defined networking,” ACM SIGCOMM Computer Communication Review, vol. 47, no. 33, pp. 2–10.
7. M. A. Khan, M. Umair and M. A. S. Choudhry. (2015). “GA based adaptive receiver for MC-CDMA system,” Turkish Journal of Electrical Engineering & Computer Sciences, vol. 23, no. 1, pp. 2267–2277.
8. S. Abbas, M. S. Khan, K. Ahmed, M. Abdullah and U. Farooq. (2011). “Bio-inspired neuro-fuzzy based dynamic route selection to avoid traffic congestion,” International Journal of Scientific & Engineering Research, vol. 2, no. 6, pp. 284–289.
9. N. Naz, S. Abbas, M. A. Adnan, B. Abid, N. Tariq et al. (2019). , “Efficient load balancing in cloud computing using multi-layered mamdani fuzzy inference expert system,” International Journal of Advanced Computer Science & Applications, vol. 10, no. 3, pp. 569–577.
10. M. Dohler, I. Vilajosana, X. Vilajosana and J. Llosa. (2011). “Smart cities: An action plan,” in Proc. of Barcelona Smart Cities Congress, Barcelona, Spain, pp. 1–6. [Google Scholar]
11. R. Khare and P. Shrivasta. (2018). “Data mining for the Internet of Things,” in Exploring the Convergence of Big Data & the Internet of Things, Chicago: IGI Global, pp. 181–191. [Google Scholar]
12. R. Thomas, D. Friend, L. Dasilva and A. Mackenzie. (2006). “Cognitive networks: Adaptation and learning to achieve end-to-end performance objectives,” IEEE Communications Magazine, vol. 44, no. 12, pp. 51–57. [Google Scholar]
13. J. R. P. Mähönen, M. Petrova and M. Wellens. (2006). “Cognitive wireless networks: Your network just became a teenager,” in Proc. of the INFOCOM, San Francisco, CA, pp. 23–29. [Google Scholar]
14. C. Fortuna and M. Mohorcic. (2009). “Trends in the development of communication networks: Cognitive networks,” Computer Networks, vol. 53, no. 9, pp. 1354–1376. [Google Scholar]
15. A. Zanella, N. Bui, A. P. Castellani, L. Vangelista and M. Zorzi. (2014). “Internet of Things for smart cities,” IEEE Internet of Things Journal, vol. 1, no. 1, pp. 22–32. [Google Scholar]
16. R. E. Hall, B. Bowerman, J. Braverman, J. Taylor, H. Todosow et al. (2000). , “The vision of a smart city; Brookhaven national lab,” in 2nd International Life Extension Technology Workshop, Paris, France, pp. 1–6. [Google Scholar]
17. T. Bakıcı, E. Almirall and J. Wareham. (2013). “A smart city initiative: The case of barcelona,” Journal of the Knowledge Economy, vol. 4, no. 2, pp. 135–148. [Google Scholar]
18. R. Giffinger and H. Gudrun. (2010). “Smart cities ranking: An effective instrument for the positioning of the cities,” ACE: Architecture, City and Environment, vol. 4, no. 12, pp. 7–26. [Google Scholar]
19. M. Batty, K. W. Axhausen, F. Giannotti, A. Pozdnoukhov, A. Bazzani et al. (2012). , “Smart cities of the future,” European Physical Journal Special Topics, vol. 214, no. 1, pp. 481–518. [Google Scholar]
20. M. Wang, Y. Cui, X. Wang, S. Xiao and J. Jiang. (2018). “Machine learning for networking: Workflow, advances and opportunities,” IEEE Network, vol. 32, no. 2, pp. 92–99. [Google Scholar]
21. M. Usama, J. Qadir, A. Raza, H. Arif, K. L. A. Yau et al. (2019). , “Unsupervised machine learning for networking: Techniques, applications and research challenges,” IEEE Access, vol. 7, pp. 65579–65615. [Google Scholar]
22. G. Xu, Y. Mu and J. Liu. (2017). “Inclusion of artificial intelligence in communication networks and services,” ITU Journal: ICT Discoveries, vol. Special, no. 1, pp. 1–6. [Google Scholar]
23. A. Patcha and J. M. Park. (2007). “An overview of anomaly detection techniques: Existing solutions and latest technological trends,” Computer Networks, vol. 51, no. 12, pp. 3448–3470. [Google Scholar]
24. T. T. T. Nguyen and G. Armitage. (2008). “A survey of techniques for internet traffic classification using machine learning,” IEEE Communicatons Surveys & Tutorials, vol. 10, no. 4, pp. 56–76. [Google Scholar]
25. M. Bkassiny, Y. Li and S. K. Jayaweera. (2013). “A survey on machine- learning techniques in cognitive radios,” IEEE Communications Surveys & Tutorials, vol. 15, no. 3, pp. 1136–1159. [Google Scholar]
26. M. A. Alsheikh, S. Lin, D. Niyato and H. P. Tan. (2014). “Machine learning in wireless sensor networks: Algorithms, strategies, and applications,” IEEE Communications Surveys & Tutorials, vol. 16, no. 4, pp. 1996–2018. [Google Scholar]
27. X. Wang, X. Li and V. C. M. Leung. (2015). “Artificial intelligence-based techniques for emerging heterogeneous network: State of the arts, opportunities, and challenges,” IEEE Access, vol. 3, no. 3, pp. 1379–1391. [Google Scholar]
28. A. L. Buczak and E. Guven. (2016). “A survey of data mining and machine learning methods for cyber security intrusion detection,” IEEE Communications Surveys & Tutorials, vol. 18, no. 2, pp. 1153–1176. [Google Scholar]
29. P. V. Klaine, M. A. Imran, O. Onireti and R. D. Souza. (2017). “A survey of machine learning techniques applied to self organizing cellular networks,” IEEE Communications Surveys & Tutorials, vol. 19, no. 4, pp. 2392–2431. [Google Scholar]
30. Z. M. Fadlullah, F. Tang, B. Mao, N. Kato, O. Akashi et al. (2017). , “State-of-the-art deep learning: Evolving machine intelligence toward tomorrow’s intelligent network traffic control systems,” IEEE Communications Surveys & Tutorials, vol. 19, no. 4, pp. 2432–2455. [Google Scholar]
31. E. Hodo, X. Bellekens, A. Hamilton, C. Tachtatzis and R. Atkinson. (2017). “Shallow and deep networks intrusion detection system: A taxonomy and survey,” arXiv preprint arXiv, vol. 2017, pp. 1–15. [Google Scholar]
32. X. Zhou, M. Sun, G. Y. Li and B. H. Juang. (2017). “Machine learning and cognitive technology for intelligent wireless networks,” Information Theory, vol. 2107, pp. 1–53. [Google Scholar]
33. M. Chen, U. Challita, W. Saad, C. Yin and M. Debbah. (2017). “Machine learning for wireless networks with artificial intelligence: A tutorial on neural networks,” arXiv preprint arXiv, vol. 2017, pp. 1–8. [Google Scholar]
34. B. Tang, Z. Chen, G. Hefferman, S. Pei, T. Wei et al. (2017). , “Incorporating intelligence in fog computing for big data analysis in smart cities,” IEEE Transactions on Industrial Informatics, vol. 13, no. 5, pp. 2140–2150. [Google Scholar]
35. S. Feng, P. Setoodeh and S. Haykin. (2017). “Smart home: Cognitive interactive people-centric Internet of Things,” IEEE Communication Magzine, vol. 55, no. 2, pp. 34–39. [Google Scholar]
36. Q. Wu, G. Ding, Y. Xu, S. Feng, Z. Du et al. (2014). , “Cognitive Internet of Things: A new paradigm beyond connection,” IEEE Internet of Things, vol. 1, no. 2, pp. 129–143. [Google Scholar]
37. P. Vlacheas, R. Giaffreda, V. Stavroulaki, D. Kelaidonis, V. Foteinos et al. (2013). , “Enabling smart cities through a cognitive management framework for the Internet of Things,” IEEE Communications Magazine, vol. 51, no. 6, pp. 102–111. [Google Scholar]
38. M. Moore, P. Gould and B. S. Keary. (2003). “Global urbanization and impact on health,” International Journal of Hygiene & Environmental Health, vol. 206, no. 3, pp. 269–278. [Google Scholar]
39. P. Hall. (2000). “Creative cities and economic development,” Urban Studies, vol. 37, no. 4, pp. 639–649. [Google Scholar]
40. R. P. Dameri. (2012). “Defining an evaluation framework for digital cities implementation,” in Int. Conf. on Information Society (i-Society 2012London, pp. 466–470. [Google Scholar]
41. R. Kitchin. (2014). “The real-time city? Big data and smart urbanism,” GeoJournal, vol. 79, no. 1, pp. 1–14. [Google Scholar]
42. S. Scott-Hayward, P. K. Chouhan, B. Fraser, D. Lake, S. Sezer et al. (2013). , “Are we ready for SDN? Implementation challenges for software-defined networks,” IEEE Communincation Magazine, vol. 51, no. 7, pp. 36–43. [Google Scholar]
43. F. Francois and E. Gelenbe. (2016). “Optimizing secure SDN-enabled inter- data centre overlay networks through cognitive routing,” in IEEE 24th Int. Symp. on Modeling, Analysis & Simulation of Computer & Telecommunication Systems, London, pp. 283–288. [Google Scholar]
44. E. Raimundo-Neto, J. R. G. da Rosa, M. A. F. Casaroli, I. Feliciano da Costa, A. M. Alberti et al. (2014). , “Implementation of an optical-wireless network with spectrum sensing and dynamic resource allocation using optically controlled reconfigurable antennasg optically controlled reconfigurable antennas,” International Journal of Antennas & Propagation, vol. 2014, pp. 1–14. [Google Scholar]
45. B. Shan, H. Ji and Y. Li. (2013). “Centralized compressed sensing with structurally random matrix in cognitive WLAN over fiber,” in Wireless Communications & Networking Conference, 2013 IEEE, Shanghai, China, pp. 106–111. [Google Scholar]
46. Y. Li, H. Ji, X. Li and V. Leung. (2012). “Dynamic channel selection with reinforcement learning for cognitive WLAN over fiber,” International Journal of Communication Systems, vol. 25, no. 8, pp. 1077–1090. [Google Scholar]
47. R. Urgaonkar and M. J. Neely. (2012). “Opportunistic cooperation in cognitive femtocell networks,” IEEE Journal on Selected Areas in Communications, vol. 30, no. 3, pp. 607–616. [Google Scholar]
48. S. Al-Rubaye, A. Al-Dulaimi and J. Cosmas. (2011). “Cognitive femtocell,” IEEE Vehicular Technology Magazine, vol. 6, no. 1, pp. 44–51. [Google Scholar]
49. Q. Yan, F. R. Yu, Q. Gong and J. Li. (2015). “Software-defined networking and distributed denial of service (DDoS) attacks in cloud com- puting environments: A survey, some research issues, and challenges,” IEEE Communications Surveys & Tutorials, vol. 18, no. 1, pp. 602–622. [Google Scholar]
50. B. Yuan, D. Zou, S. Yu, H. Jin, W. Qiang et al. (2016). , “Defending against flow table overloading attack in software-defined networks,” IEEE Transactions on Services Computing, vol. 12, no. 2, pp. 231–246. [Google Scholar]
51. S. Dev, B. Wen, Y. H. Lee and S. Winkler. (2016). “Ground-based image analysis: A tutorial on machine-learning techniques and applications,” IEEE Geoscience & Remote Sensing Magazine, vol. 4, no. 2, pp. 79–93. [Google Scholar]
52. C. S. Nwosu, S. Dev, P. Bhardwaj, B. Veeravalli and D. John. (2019). “Predicting stroke from electronic health records,” in Proc. 41st Annual Int. Conf. of the IEEE Engineering in Medicine and Biology Society, Berlin, Germany, pp. 5704–5707. [Google Scholar]
53. S. Abbas, M. A. Khan, L. E. Falcon-Morales, A. Rehman, Y. Saeed et al. (2020). , “Modeling, simulation and optimization of power plant energy sustainability for IoT enabled smart cities empowered with deep extreme learning machine,” IEEE Access, vol. 8, no. 1, pp. 39982–39997. [Google Scholar]
54. A. Rehman, A. Athar, M. A. Khan, S. Abbas, A. Fatima et al. (2020). , “Modelling, simulation, and optimization of diabetes type II prediction using deep extreme learning machine,” Journal of Ambient Intelligence and Smart Environments, vol. 12, no. 2, pp. 125–138. [Google Scholar]
55. M. A. Khan, S. Abbas, K. M. Khan, M. A. Ghamdi, A. Rehman et al. (2020). , “Intelligent forecasting model of COVID-19 novel coronavirus outbreak empowered with deep extreme learning machine,” Computers, Materials & Continua, vol. 64, no. 3, pp. 1329–1342. [Google Scholar]
56. Kaggle. (2020). [Online]. Available: https://www.kaggle.com/hassan06/nslkdd. [Google Scholar]
57. Y. J. Li, X. B. Li and O. Yoshie. (2014). “Traffic engineering framework with machine learning based meta-layer in software-defined networks,” in Proc. IEEE ICNIDC’14, Beijing, China, pp. 121–125. [Google Scholar]
58. C. X. Cui and Y. B. Xu. (2016). “Research on load balance method in sdn,” International Journal of Grid & Distributed Computing, vol. 9, no. 1, pp. 25–36. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |