DOI:10.32604/cmc.2021.013124

| Computers, Materials & Continua DOI:10.32604/cmc.2021.013124 |  |
| Article |
Fuzzy Based Decision-Making Approach for Estimating Usable-Security of Healthcare Web Applications
Computer Engineering Department, Umm Al-Qura University, Mecca, 24381, Saudi Arabia
*Corresponding Author: Fahad A. Alzahrani. Email: fayzahrani@uqu.edu.sa
Received: 27 July 2020; Accepted: 27 August 2020
Abstract: Usability and security are often considered contradictory in nature. One has a negative impact on the other. In order to satisfy the needs of users with the security perspective, the relationship and trade-offs among security and usability must be distinguished. Security practitioners are working on developing new approaches that would help to secure healthcare web applications as well increase usability of the web applications. In the same league, the present research endeavour is premised on the usable-security of healthcare web applications. For a compatible blend of usability and security that would fulfill the users’ requirments, this research proposes an integration of the Fuzzy AHP-TOPSIS method for assessing usable-security of healthcare web applications. Since the estimation of security-usability accrately is also a decision making problem, the study employs Multiple Criteria Decision Analysis (MCDA) for selecting the most decisive attributes of usability as well as security. Furthermore, this study also pinpoints the highest priority attributes that can strengthen the usable-security of the healthcare web applications. The effectiveness of the suggested method has been tested on the healthcare web applications of local hospitals in Mecca, Saudi Arabia. The results corroborate that Fuzzy AHP-TOPSIS is indeed a reliable technique that will help the developers to design a healthcare web applications that delivers optimum usable-security.
Keywords: Decision making; healthcare web application; usable-security; fuzzy ahp; fuzzy topsis
Usability and security have become two significant priorities in the present scenario for developing web applications for healthcare sector because the end users want to invest their resources only in those healthcare web applications that afford them utmost security while retaining the ease of use [1]. However, the integration of usability and security has various contradictory factors [2]. Security is inconvenient and this inconvenience has a negative impact on the usability of the healthcare web applications [2]. Researchers have been concerned over the past five years about usable-security of healthcare web applications [1–6]. In addition, some experts in technological research and development claim that human-factor in not a reliable aspect while securing the healthcare web applications in the design phase. In 2011, Carrión et al. noted that 80–90% of security related issues are caused by vulnerabilities related to human factors [4]. Since its foundation, healthcare web applications and end-user’s data integrity have been at high risk. Therefore, users with different points of view are considered for both usability and security. It is the user who verifies the usability in perspective of usability of healthcare web applications. However, at times, the customers themselves are the causes for the vulnerabilities in security perspective of healthcare web applications.
Growing use of healthcare web applications in the present day lifestyles has forced individuals to be online and save their medical information on it. Passwords, authentication and data integrity are the focal points for usable-security of healthcare web applications [5,6]. The architecture also affects the capability of users to safely execute their responsibilities. For instance, a difficult CAPTCHA can affect usability, but it authenticates the consumer for security purposes [7,8]. Researchers have worked on its various characteristics for ensuring security of healthcare web applications with longer usability. Similar efforts to improve usability are also underway. But insufficient mathematical or empirical efforts have been made to confirm the usable-security of healthcare web applications [4–6]. Though, the usability and security characteristics are contradictory, the security and usability characteristics selected in this work will have only a positive effect on the overall usable-security of healthcare web applications [9,10].
Multiple Criteria Decision Analysis (MCDA) area offers multiple procedures, approaches and tools to resolve the conflict between altered characteristics of an issue in question [11]. As per the results of the evaluation procedure, the decision-makers can make appropriate decisions. In order to make the most responsive choice, the decision-makers should not only know the characteristics which contribute to usable-security of healthcare web applications, but should also be able to point the highest useful characteristic. Given this backdrop, usable-security assessment framework is proposed in this work. To ensure the feasibility of this approach, the research team has evaluated the suggested technique on local hospitals of Mecca, Saudi Arabia.
The estimation of usable-security characteristics of healthcare web applications with an appropriate methodology plays a noteworthy role in enhancing the quality of the services. Furthermore, the selection and evaluation of usable-security of healthcare web applications is a decision-making problem [11,12]. In this contribution, the authors have opted for the fuzzy-based integrated approach of the Analytic Hierarchy Process (AHP) and Technique for Preference Order by Similarity to Ideal Solution (TOPSIS) procedures [12]. This integrated approach provides optimum results and would be highly accurate for evaluating the impact of usable-security characteristics.
Many practitioners have been successful in assessing the constant outcomes by using the Fuzzy-TOPSIS method [13,14]. Unfortunately, specific guidelines have not yet been given for assigning quantitative from qualitative weights of characteristics. Fuzzy-AHP method supports the practitioners’ attempts by analytically weighting the characteristics, thereby removing any ambiguity and vagueness in decision. Furthermore by using the pair-wise comparisons and fuzzy numbers, the consistent characteristic weights can be obtained. But the Fuzzy-AHP method is inefficient due to the repetitive calculations and a vast number of pair-wise comparisons for a maximum number of alternatives. Hence, the authors suggest that this integrated approach should be used without complicated calculations to determine the effect of alternatives in a fair amount of time and that too with slight effort.
This empirical contribution is divided into five segments: Remaining first part is devoted to the research work performed so far in the field of usable-security of healthcare web applications. The second section concerns usable-security and the associated characteristics and methodology. Its execution has been defined in Section 3. Section 4 includes a summary of the findings. Conclusion has been covered in Section 5.
Various studies have already been done on the usable-security assessment by using different approaches and techniques. Alongside fuzzy AHP, TOPSIS and fuzzy AHP with TOPSIS techniques have also been used in various research areas to solve the Multi Criteria Decision Making (MCDM) problems. Following are some of the latest and pertinent studies:
Rajeev Kumar et al. [11]—This research study evaluated the usable-security using multi-level fuzzy AHP technique. In this study, the authors have integrated five security criteria and four usability criteria and have applied fuzzy AHP hybrid technique to evaluate usable security. The utmost significant element found between the nine usable-security elements is the user-error protection. The study concludes that the fuzzy AHP provides more efficient results than AHP. A. Mardani et al. [12]—This study applied hybrid approach of Delphi-AHP and fuzzy TOPSIS for the selection of renewable-energy resources. Four main factors with 20 sub-factors have been considered to estimate five renewable-energy resources for electricity generation. Authors applied Delphi method to determine and choose the best relevant factors to select renewable energy resources. Thereafter, AHP is applied to get the weights of factors and the sub-factors of the decision-model. For final assessment, the fuzzy TOPSIS technique is applied to find the optimal renewable energy resource from the given five renewable energy alternatives.
Ismailova [13]—This study uses fuzzy ANP and TOPSIS procedures for the most appropriate software selection. With four alternatives Soft1, Soft2, Soft3 and Soft4, Security, reliability, user friendly, and maintenance are taken as identified criteria for software selection assessment. Fuzzy-ANP is used to evaluate characteristic weights and also to assess the quality of interdependence among them. After that, the weights of characteristics are provided as inputs to the TOPSIS model to determine the final alternative ranking. Toll et al. [14]—This research study identified the most suitable technique of authentication for smart phone banking service by using ANP procedure. Authors of this paper considered three criteria (security, convenience and cost) with eleven sub-elements, three sub-networks and four alternatives to create the whole network. The outcome of the research indicated that biometric is the most suitable in the security dimension, OTP is the most suitable in the convenience aspect, and public key certificate is most appropriate in the coastal aspect. OTP has been discovered to be the optimal authentication technique in overall performance in safety, convenience and cost.
Lyon et al. [15] devised a model to estimate usable-security by using F-AHP to overcome the gap between software security and software usability. Three attributes of security (confidentiality, integrity and availability) and three attributes of usability (effectiveness, efficiency and satisfaction) are collectively considered for usable security evaluation. After deriving weights and priority by using fuzzy-AHP technique, Satisfaction of the user gets the highest priority among all these attributes. To validate the accuracy of results, AHP method is used as a comparative technique with fuzzy-AHP. W. Bai et al. [16]—In this research study, the authors use neutrosophic aggregation operator to sum up all the opinions of experts and Euclidean-distance has been applied to calculate the distances of every alternative from positive-ideal solution and from negative-ideal solution. Four alternatives and six criteria are taken in this study for evaluation. Finally authors of this study find that for multi attribute decision making problems, TOPSIS method with neutrosophic set information has very high chances of success.
Dutta et al. [17] proposed a hybrid model for estimating carbon performance of suppliers by integrating F-ANP and F-TOPSIS methods for carbon-management of a green-supplier selection system. Thirteen criteria are identified for evaluating the carbon-performance of suppliers. Among these 13 criteria, carbon-governance, carbon-policy and carbon-reduction targets are considered most important criteria. The study also found that the devised hybrid model helped in determining the best supplier in carbon management. Gordieiev et al. [18]—This study is on APIs usability for ensuring security of software. Authors of this work identified 11 definite usability factors to examine the APIs security and proposed an extensive model to address the current space of API usability. Besides, for future applications, the authors proposed the mechanism to design APIs security to ensure more usable-security.
Thigpen [19], by using fuzzy ANP method, calculated the weights and interdependence of eight important criteria to evaluate specific web sites of E-commerce. Authors of this study found that satisfaction (weight = 0.238) and security (weight = 0.228) criteria are important factors for E-commerce evaluation. Al-Zubaidie et al. [20]—In this study, AHP is applied to assess the web sites of Indian E-commerce. Later fuzzy-TOPSIS is applied for alternative ranking. This study’s results found that Amazon has got the highest rank followed by Flipkart and Ebay. Ronquillo et al. [21] devised a model by using Analytic Hierarchy Process and fuzzy-TOPSIS methods for cloud-service selection. Four cost criteria and six benefit criteria are considered for the selection of cloud service with six alternatives. From the final results, it was found that Softlayer is the most feasible cloud service provider followed by Amazon web services and Digital Ocean.
After reviewing these related works, the contributors established that interactions between usability and security and their characteristics are integral and yet there isn’t a standardized procedure to produce a secure and usable healthcare web applications. Maintaining usability and security is also a challenge in decision-making problem for the user’s sake and medical data responsiveness. Hence, the present study attempts at filling this gap in the analysis. This study suggests using Fuzzy based AHP-TOPSIS integrated method to solve all the problems of decision-making in order to achieve optimum outcomes. Estimated findings from this approach will be useful for security experts who can enlist the usable-security recommendations during development process.
3 Usable-Security of Healthcare Web Applications
Most of the healthcare web applications have frequently failed because of the lack of the end user’s responsiveness and their limited knowledge. A National Research Council Committee on Maintaining Privacy and Security in Health Care Applications of the National Information Infrastructure cites that about 60% of small corporations were heedless of the malicious attacks and generally overlooked the small attacks that are often the originators of larger and serious attacks [22]. That’s why the customers in this chain are considered to be the fragile link. Healthcare web application usable-security is a crucial component for the overall system security, but is still overlooked during development.
Zaidan et al. noted that usability and security are opposite to one another [23]. While the security of healthcare web applications is intended to make uninvited actions, the purpose of usability of healthcare web applications is to make it easier for the user to do the necessary actions. It is unfortunate that security and usability are observed as each other’s opponents. Thus, completing both at the same time in any stage of healthcare web applications development poses a challenge. Security as well as usability has different characteristics that in some cases influence each other. Therefore, in the case study for healthcare web applications, contributors of this research work have measured the vital characteristics of security and usability in a single structure to test the usable-security. In this row, in their recently published work [1], the contributors proposed a hierarchy of usable-security characteristics which is shown in Fig. 1.
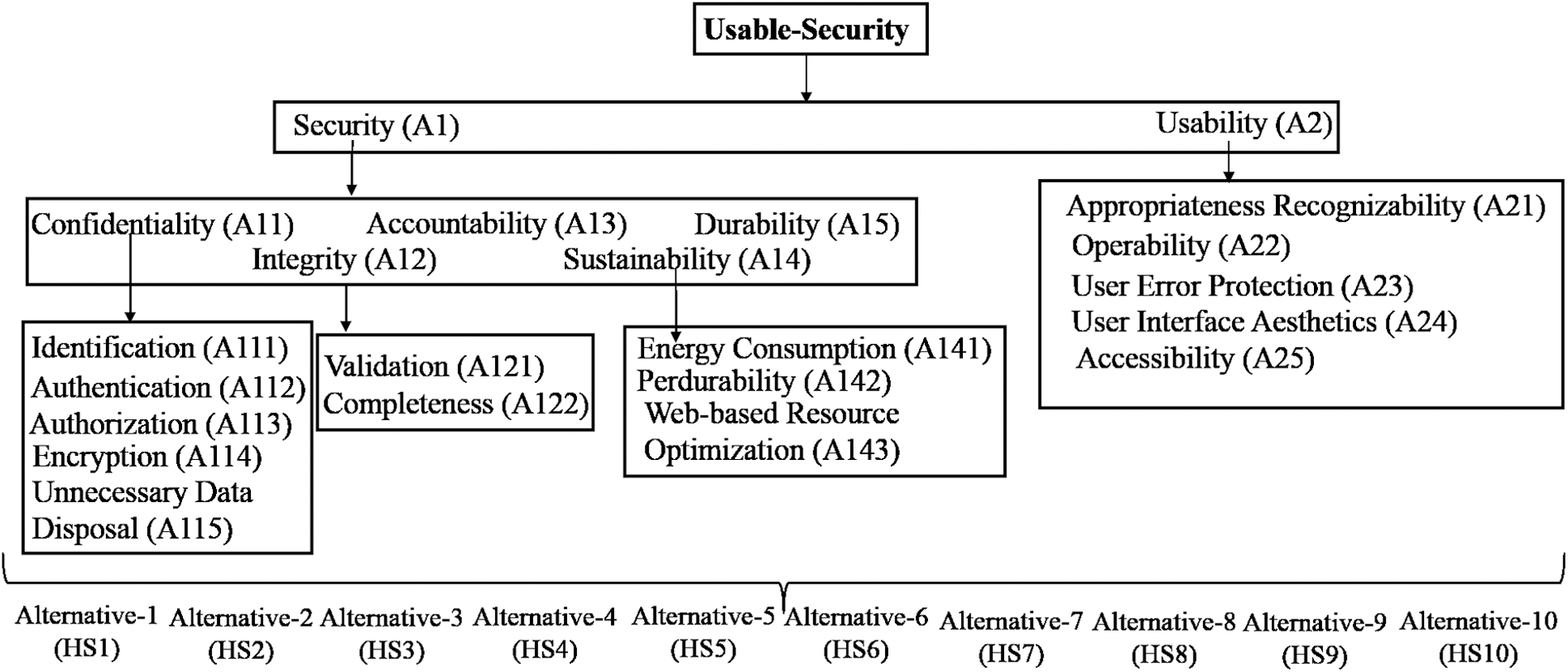
Figure 1: Hierarchy of usable-security characteristics
The characteristics that feature in Fig. 1 are significant for improving usable-security of healthcare web applications. The explanation given for each characteristic is as follows:
• Usable-Security: As stated above, users of healthcare web applications are seen as the fragile connection. Presently, security controls fixed in the device use the customer’s incapacity to comprehend the security as a shattered wall [24,25]. Therefore, planning usable-security is an imperative aspect of developing secure healthcare web applications. Usable-security designs a secure healthcare web application, thus making it easy for the end user to access it.
• Security (A1): Security of healthcare web applications is the awareness to build web applications in such a way that it protects itself from the malicious attacks [26,27]. Designing security of healthcare web applications is a complex procedure at early stage of development. Malicious intruders can hack systems through defects of website, therefore the detection and repair of these defects of website can only warranty highest security. Various methodologies, mechanisms, metrics, etc., have been proposed and implemented to prevent malicious attacks. Omer Tripp et al. estimated the security through automated tools in their study, and concluded that they decreased usability of healthcare web applications [27]. In 2019, Ouissem Ben Fredj announced the SPHERES: The system security for a single web server for hospital management system which is essential and crucial [28]. There are several benefits to it over other systems. Though such structures and practices secure the healthcare web applications, they decrease usability. Therefore, confirming usability with growing security of healthcare web applications is at the core of examination because the end user is the individual for whom the services need to be user centric.
• Usability (A2): Usability of healthcare web applications is the ease of use and understanding. In one of her studies, a usability specialist, A. Agrawal states that, “Security topographies that have human interaction in their use should be informal to use to improve usability topographies” [29]. Because of the increased complexity of the security architecture, usability decreases. Thus, the developers must prioritize both security and usability.
• Confidentiality (A11): Confidentiality of healthcare web applications is haphazardly similar to medical data privacy. It is a difficult procedure to avoid uninvited individuals from breaching the confidentiality [30]. Numerous stages and methods have been undertaken previously to enhance security, while making the features more applicable for the users. But sometimes security of medical data can harm usability of healthcare web applications or it can even increase usability. Therefore this characteristic is measured significantly for usability as well as security. Education for confidentiality in research is to enhance security while retaining optimum device usability.
• Integrity (A12): Maintaining integrity and security includes ensuring the regularity and functionality of the healthcare web applications throughout their entire life. Sensitive medical data should not be modified, and care must be taken to ensure that the medical data enters the recipient as it was when it was sent [31]. In addition, the stages taken to guarantee usability are increasing the sophistication of end user’s healthcare web applications [11]. Therefore, to ensure the usable-security of healthcare web applications, integrity must be taken into account in this regard.
• Accountability (A13): Accountability is a vital aspect of a security design of healthcare web applications during the development process [32,33]. The accountability means that each individual who works with the hospital data should have clear accountabilities for ensuring the security of the hospital data; the individual should also be accountable for the information created or distributed.
• Sustainability (A14): Sustainability is described as a quantity of how constant a design is to secure a web application to recommended accountabilities [34]. In addition, web application sustainability can be distinct as the capability of constructing a web application in a sustainable way [35]. Additionally, sustainability displays a vital character for high security design.
• Durability (A15): Durability of secure healthcare web applications is comparatively a novel theory which has only gained prominence during the 21st century [36,37]. Security-durability can be described as the life-span of healthcare web applications for a particular life-span. Security-durability is influenced by usable-security, as the safety time limit has a huge consequence on the overall usable-security of healthcare web applications.
• Appropriateness Recognizability (A21): Recognizability of appropriateness is the characteristic by which customers can determine whether or not the security offered fits their needs [38,39]. It is the end user who decides if security of healthcare web applications is acceptable. This also affects security although it is a mere principle of usability.
• Operability (A22): Operability is a characteristic which determines the ease of healthcare web applications operations. Security methodologies and mechanisms on healthcare web applications pose challenges in system operability [40,41]. Thus, it is essential to consider operability as an important characteristic of usable-security when evaluating security and usability of healthcare web applications together.
• User Error Protection (A23): Protection or the prevention of user errors is the characteristic that guarantees that the healthcare web application itself secures the program from the errors [42]. Preventing the user from creating mistakes additionally enhances the security of the healthcare web applications. This circumstance highlights the necessity to recognize user error protection as a characteristic in usable-security estimation.
• User Interface Aesthetics (A24): User Interface Aesthetics (UIA) is the characteristic that confirms user interface and allows the user interaction to be pleasing and satisfying [43]. Increasing the security with sophistication can have a serious effect on UIA. This is the reason why the authors have selected the UIA is in the characteristics hierarchy of usable-security characteristics for calculating healthcare web application usable-security.
• Accessibility (A25): Accessibility is the characteristic that enlists that customers with the broadest range of topographies can use the healthcare web applications [44]. The security and their sophistication affect usability. Usable-security evaluation cannot be done without the significant contribution of usability of healthcare web applications.
• Identification (A111): Identification occurs when a user name is asserted by an individual, program or method [45]. In all the other words, it is a representation of one’s individuality where the user or any other person is unaware of it.
• Authentication (A112): It is called the method of identifying a customer whose individuality is based on the password and name as an authentication [46]. Authentication agrees whether the individual is honest and is indeed the person he/she claims to be. It is a mere security principle, but usability of the framework depends on the use of the password as well as identity. This could affect the complete healthcare web application usable-security; this is why it should be taken into account when determining the usable-security.
• Authorization (A113): Authorization is the procedure through which privileges are granted for accessing the resources of the device. It determines the resource control domain of a user, based on their authentication [47].
• Encryption (A114): Encryption is a process of converting plaintext into ciphertext to ensure that the digital data is secured and confidential [48].
• Data Disposal (A115): Unnecessary Data Disposal means that if the data is no longer used, it must be destroyed or deleted properly so that the data removed cannot be recovered and misappropriated [48].
• Validation (A121): Data validation or confirmation ensures that the data is transmitted to relevant applications, programs or services in a clear, accurate and consistent manner [47]. It can be measured as a proportion of valid data within the range of the available data.
• Completeness (A122): The completeness of the information is a measure of the thoroughness of the accessible data [41] and ensures that there is really no lack of any important or necessary data item related to the full description of the state of the action or individual under consideration [42].
• Energy Consumption (A141): Sustainable-security energy consumption is the amount of power used by a web application when conducting its security functions fulfills the security needs [43].
• Perdurability (A142): Perdurability is the concept of generating long-lasting, adaptable and recyclable, sustainable application security, i.e., going to increase those factors which make the web application last long, with the ability to adapt to change without losing its quality-related functionality [44].
• Web-based resource Optimization (A143): Web-based resource management is the collection of theories and practices used to align the available resources, such as human resources, equipment, and finance, with the organization’s security criteria to achieve the well-known sustainability and safety goals. Optimizing resources is achieving the required outcomes within the specified time and budget with minimum resource usage [45].
The authors have named hierarchy characteristics and sub-characteristics as A1 and A2 for security and usability, respectively. In addition, A11, A12, A13, A14 and A15 are used as second level characteristics in security perspective. A21, A22, A23, A24, and A25 are used as second level characteristics in usability perspective. Further, A111, A112, A113, A114, A115, A121, A122, A141, A142, and A143 are used as third level characteristics in confidentiality, integrity and sustainability perspective, respectively.
In addition, its characteristics should be defined and set up in a classified way to solve it by using the MCDA approach to address the issue of usable-security assessment [1,11]. In this contribution, the Fuzzy AHP-TOPSIS methodology is adopted for usable-security estimation of healthcare web applications. The next segment outlines the approach to follow.
Most of the practitioners have tried to tackle the gap between usability and security with its estimation. Among these efforts, usability, security and integration of both for healthcare web applications is the locus for present and future research investigations in healthcare perspective [11]. Furthermore, multiple criteria decision-making topics repeatedly occur in real time scenarios of security and usability [11,13]. From the point of literature review, it is clear that there are multiple methods available to tackle such situations in real life [16,19]. But because of its hierarchical nature of dependencies of attributes, for usable-security estimation, AHP seems to be a very appropriate technique than the other MCDM approaches [21,22]. To reduce the ambiguity and imprecision among the decisions, the authors analyzed that AHP alone is not efficient and that AHP should be combined with some other method to improve its efficiency [11]. Moreover, AHP contains an ambivalent decision scale which lessens its efficiency and Fuzzy logic has its own disadvantages [16]. Combining both the methods gives precise results but in big size of data situations this Fuzzy-AHP method is insufficient. Hence, a unified AHP, TOPSIS and Fuzzy technique is an extraordinary procedure that might aid in proficient alternative consideration. Methodology of Fuzzy AHP integrated with TOPSIS procedure is shown in following section:
Fuzzy AHP: Fuzzy AHP methodology is used to choose the best option in selection problems where the decision is hard to formulate. Fuzzy logic with AHP is a valued procedure and in this method every characteristic can be observed by using hierarchy. Methodology of Fuzzy-AHP transforms the goals into a tree shape. Fig. 1 provides the tree shape. This hierarchy structure is diagramed by specialists’ observations [16]. After the creation of hierarchy of characteristics, the next segment of this study defines the membership function such as Triangular Fuzzy Number (TFN). Through the help of the individual characteristic’s influence on diverse characteristic, the pair-wise comparison of each set of categorized aspiration acts as a vital agent in evaluation. The opinions retrieved from practitioners were in linguistic format. Hence, the next phase involved transforming these language based values into corresponding numeric information and membership function. There are numerous kinds of membership functions which include Generalized Bell, Gaussian, triangular, Trapezoidal fuzzy numbers, and many more. For this work, the authors chose to opt for triangular membership functions (Range: 0 to 1) [19,23–25]. This paper uses TFNs because of its simplicity to handle data uncertainty [26–28]. In addition, the subjective scores are classified as Similarly important, uncertainly important, intensely important, etc., and their corresponding numerical values are classified as 1, 2, ……….. 9, correspondingly. Eqs. (1) and (2) show a fuzzy number called T on Fz which is Triangular Fuzzy Number:

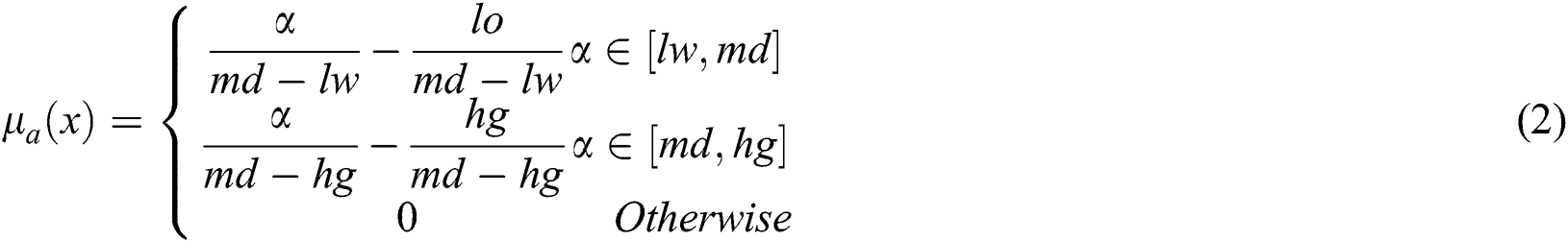
Limits of Lower, middle, and higher are defined as lw, md, and hg. Fig. 2 also applies to triangular membership features.
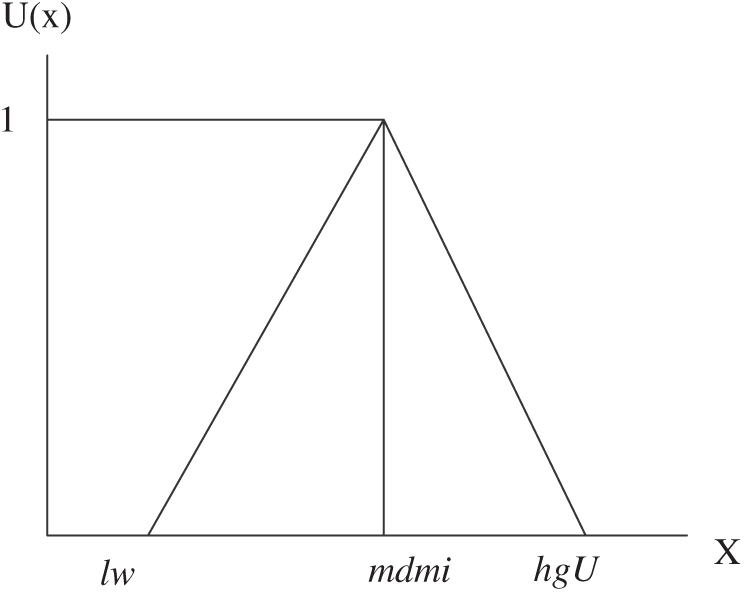
Figure 2: Triangular fuzzy numbers
Triangular Fuzzy Numbers, i.e., TFN (lw, md, hg). Practitioners and experts’ decisions linguistically are done by the scale provided in Tab. 1 [29,30].

The Eqs. (3)–(6) are used to change the linguistic values from numeric values to corresponding TFN [31–34] which are further identified as (lwij, mdij, hgij) where, lwij is lower, mdij is middle, and hgij is higher.

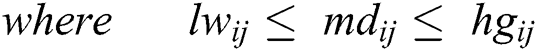



Jijk in the above Eqs. (3)–(6), demonstrates the proportional meaning of two characteristics for each other (i and j shows specialist or decision maker Ex). Geometric Mean (GM) is used to calculate mean of the specialist’s decision for a particular conclusion. From the above calculation, the TFN standards are obtained and matrix comparison for a fuzzy pair-wise is now accumulated using Eq. (7) in the n×n matrix method.

where (kij^k) represents the primary choice of the ith characteristic by the decisions expert over the jth attribute. In case of more than one expert, Eq. (8) is used to calculate the result.

Comparison matrixes for overall characteristics are evaluated from Eq. (9).

To calculate each characteristic’s fuzzy GM (Geometric Mean) and fuzzy weights, Eq. (10) is used by the contributors as given follows:

Use Eq. (11) to calculate the fuzzy weight of the characteristic.

Eqs. (12) and (13) are used to calculate the average and uniform weight requirements.


In addition, the Center of Area (COA) method is used with Eq. (14) to estimate the BNP value of each characteristic’s fuzzy weights.
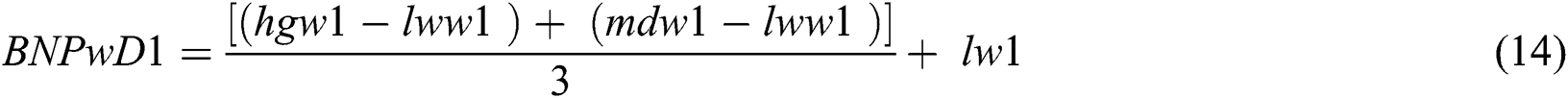
Fuzzy TOPSIS: TOPSIS is a multi-standard collection problem-making with P alternatives as a geometric structure of P points within the n-dimensional target area. The approach used in this research work is based on the idea that a substitution alternative has the shortest and longest distance to the Positive-Ideal Solution (PIS) and the Negative-Ideal Solution (NIS), respectively, for optimal and less ideal solutions [22,23,35–38]. Specialists typically experience problems while associating a specific rank with a given characteristic [24]. TOPSIS assigns precedence for the relative strengths of the trait to accurate numbers for consistency with significant-world fuzzy environment. Furthermore, a fuzzy-based approach to AHP-TOPSIS is especially suited for real issue-solving group decision-making in flowing environments. The very main stage is to determine weights for performance indicators. Using Eqs. (1)–(12), this work uses Fuzzy AHP to achieve weights. Subsequent step is to produce the fuzzy decision matrix and select the ideal linguistic variables as characteristic from Eq. (15) and Tab. 2.



where, 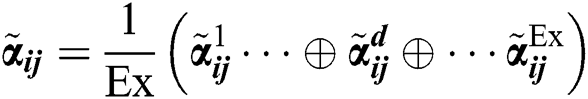 , and
, and 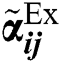 is the rating for the performance of the substitute Ai with respect to the
is the rating for the performance of the substitute Ai with respect to the 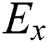 th expert’s Crj characteristic and
th expert’s Crj characteristic and 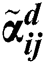 = (
= (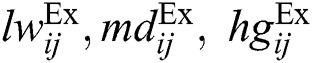 ). U’s standardized matrix of fuzzy decision is portrayed as shown below:
). U’s standardized matrix of fuzzy decision is portrayed as shown below:

Using the Eq. (17) can then achieve the normal form.
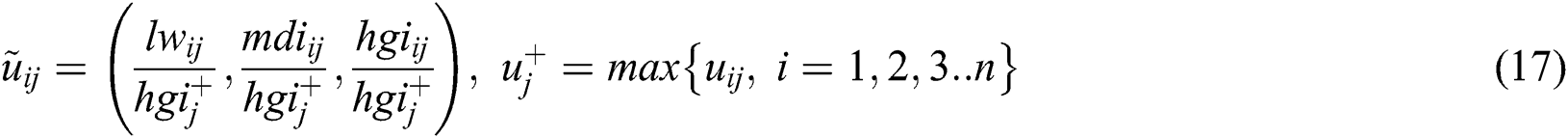
Alternatively, we should set the finest anticipated level= 1, 2,. N is 1; else the poorest is 0. The normalized 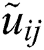 remains TFNs. TFN-like normalization technique can be done. The weighted standardized decision matrix (Q) is enumerated using Eq. (18).
remains TFNs. TFN-like normalization technique can be done. The weighted standardized decision matrix (Q) is enumerated using Eq. (18).

In the above equations, 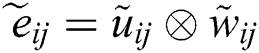 and the FPIS and FNIS is described in the next step, respectively, which are fuzzy positive ideal solutions and negative ones. The matrix for the weighted normalized fuzzy decisions specifies that the characteristics
and the FPIS and FNIS is described in the next step, respectively, which are fuzzy positive ideal solutions and negative ones. The matrix for the weighted normalized fuzzy decisions specifies that the characteristics 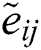 are positively normalized. TFN and its’ ranges are contained in the closed interval [0,1]. Subsequently using the equations as shown in Eqs. (19) and (20), contributors evaluated the FPIS A+ (aspiration levels) and FNIS A− (the worst levels)
are positively normalized. TFN and its’ ranges are contained in the closed interval [0,1]. Subsequently using the equations as shown in Eqs. (19) and (20), contributors evaluated the FPIS A+ (aspiration levels) and FNIS A− (the worst levels)


where,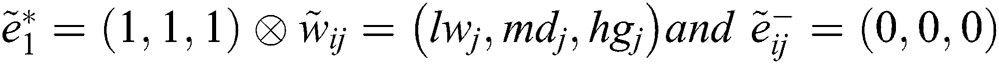 ,
, 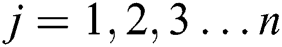 .
.
Distance of every individual alternative is calculated from FPIS and FNIS, using the area compensation technique given in Eqs. (21) and (22).
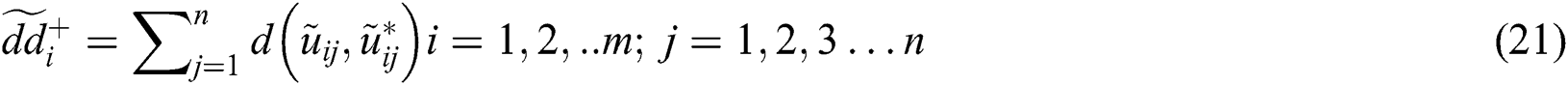
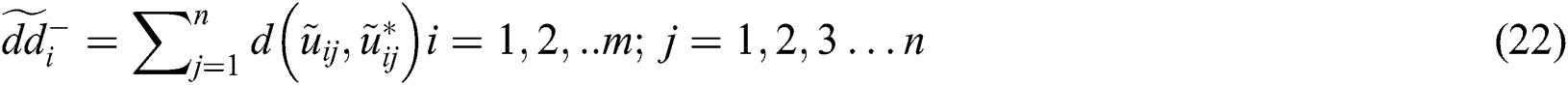
Further, the subsequent step is to calculate the closeness coefficients (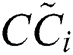 ) and advance the alternatives to meet each characteristic’s objective amounts. Distance to the optimal solution was calculated after measuring
) and advance the alternatives to meet each characteristic’s objective amounts. Distance to the optimal solution was calculated after measuring 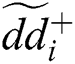 and
and 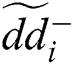 of each alternative. Eq. (23) is used in this phase to solve distances to an ideal solution.
of each alternative. Eq. (23) is used in this phase to solve distances to an ideal solution.
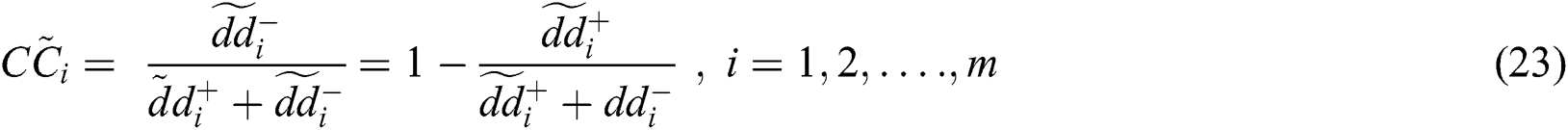
where (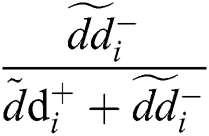 ) depicted in the alternative as fuzzy contentment degree and (
) depicted in the alternative as fuzzy contentment degree and (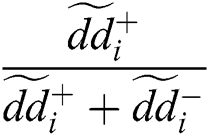 ) depicted as degree of fuzzy gap in the ith alternative.
) depicted as degree of fuzzy gap in the ith alternative.
Subjective assessment is usually sufficient to determine the usable-security of healthcare web applications. Numerically, it is complicated to perform usable-security estimation of healthcare web applications. In the proposed study, the contradictory facets of security and usability are pooled together to determine the overall usable-security of healthcare web applications. Lately, with great effort and success, developers and researchers have adopted the security and usability strategies [25,26,39–41]. Organizations are also looking for high accessibility of healthcare web applications with preventable security. In fact, the regulation of usable-security requirements performs a considerable portion of usable-security [27,28,42–45]. This research work therefore offers usable-security assessment by using a fuzzy based decision making AHP-TOPSIS methodology.
From their previous work mentioned in Section 3 of the paper, contributors have followed the usable-security classified characteristics. A close grouping structure of usable-security characteristics is shown in Fig. 1, from the discussion in previous sections. For the purpose of gathering the data, this article has taken opinions from seventy specialists via questionnaires (including questions related to various usable-security characteristics) from academia, hospitals and various companies [46–49]. The results are obtained by using the Eqs. (1)–(23) and Tabs. 1 and 2. Usable-security estimation was calculated as follows:
From Eqs. (1)–(9) and Tab. 1, contributors translated the language based scores into corresponding numerical scores and aggregated TFNs. TFNs scores are determined as:
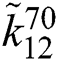 = (1, 1, 1)1/70⊗ (1/4, 1/3, 1/2)1/70⊗ ··· ⊗ (7, 8, 9)1/70 = ((1 × 1/4 × ··· × 7)1/70, (1 × 1/3 × ··· × 8)1/70, (1 × 1/2 ··· × 9)1/70) = (0.305000, 0.389000, 0.561000)
= (1, 1, 1)1/70⊗ (1/4, 1/3, 1/2)1/70⊗ ··· ⊗ (7, 8, 9)1/70 = ((1 × 1/4 × ··· × 7)1/70, (1 × 1/3 × ··· × 8)1/70, (1 × 1/2 ··· × 9)1/70) = (0.305000, 0.389000, 0.561000)
The matrix for pair-wise comparison of the characteristics of level 1 is determined by using Eq. (10) and Tabs. 3–8 show the same process.
Table 3: Fuzzy based combined matrix for pair-wise comparison at level 1 for usable-security

Table 4: Fuzzy based combined matrix for pair-wise comparison at level 2 for security

Table 5: Fuzzy based combined matrix for pair-wise comparison at level 2 for usability

Table 6: Fuzzy based combined matrix for pair-wise comparison at level 3 for confidentiality

Table 7: Fuzzy based combined matrix for pair-wise comparison at level 2 for integrity

Table 8: Fuzzy based combined matrix for pair-wise comparison at level 2 for sustainability

Eqs. (11)–(13) are used to estimate the weights in fuzzified form of characteristics; the assessment of the weight technique is shown as follows:
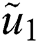 = [(1.000000, 1.000000, 1.000000) ⊗ (0.305000, 0.389000, 0.561000)]1/2
= [(1.000000, 1.000000, 1.000000) ⊗ (0.305000, 0.389000, 0.561000)]1/2
= [(1.000000 × 0.305000)1/2, (1.000000 × 0.389000)1/2, (1.000000 × 0.561000)1/2]
= (0.305000)1/2, (0.389000)1/2, (0.561000)1/2 = (0.552270, 0.623700, 0.749000)
Likewise, we can get the other: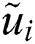 as:
as: 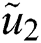 = (0.891250, 1.285000, 1.639000)
= (0.891250, 1.285000, 1.639000)
One can consider the weight of each characteristic using the Eqs. (14)–(16):
 = (0.3136513990, 0.3267664320, 0.382584790)
= (0.3136513990, 0.3267664320, 0.382584790)
Equally, we obtained the remaining: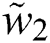 = (0.617415210, 0.673233570, 0.686348600).
= (0.617415210, 0.673233570, 0.686348600).
In addition, the Best Non-Fuzzy Performance Value (BNP) of each characteristic is determined with the aid of Eq. (14), as follows:
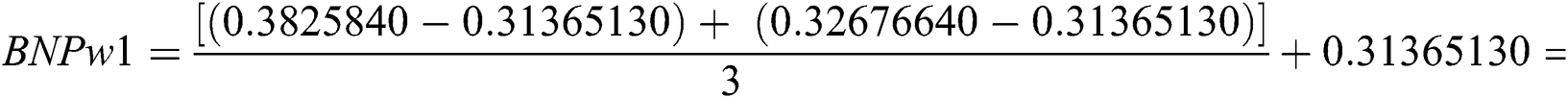
Tab. 9 shows the other characteristics weights which are calculated and which show the independent and dependent weight of characteristics throughout the hierarchy. Tab. 9 presents the dependent weights of each characteristic of usable-security in relation to healthcare web applications.
Table 9: Overall weights through the hierarchy

The findings from the result review Tab. 9 indicate that A121, the Validation, is the top priority. The second feature of the precedent is Encryption of healthcare web applications and so on. Thereafter, we determined the characteristic-related impacts of usable-security in alternative. Ten successive projects of healthcare web applications developed for local hospitals of Mecca, Saudi Arabia, were used to test the usable-security. HS 1, HS 2, HS 3, HS 4, HS 5, HS 6, HS 7, HS 8, HS 9 and HS 10 denote the ten healthcare web applications of different projects. All projects require exceptional usable-security of healthcare web applications due to very sensitive hospital information [50–53]. Tab. 2 was used by specialists to take the linguistic data of the ten alternatives. Authors aggregated opinions in TFN with the aid of Eqs. (1)–(6), as given in Tab. 10 and assessed regularized matrix for fuzzy decision with the help of Eqs. (18)–(20) as delivered in Tab. 11. Authors evaluated the weighted decision matrix for normalized fuzzy with the help of Eq. (21) as given in Tab. 12. Additionally, authors estimated the fuzzy satisfaction degree and fuzzy gap degree with the help of Eqs. (22) and (23) as given in Tab. 13 and Fig. 3.
Table 10: Subjective comprehension tests of linguistic evaluators


Table 11: Normalized fuzzy-decision matrix

Table 12: Weighted normalized fuzzy-decision matrix

Table 13: Closeness coefficients to the desired level between alternatives

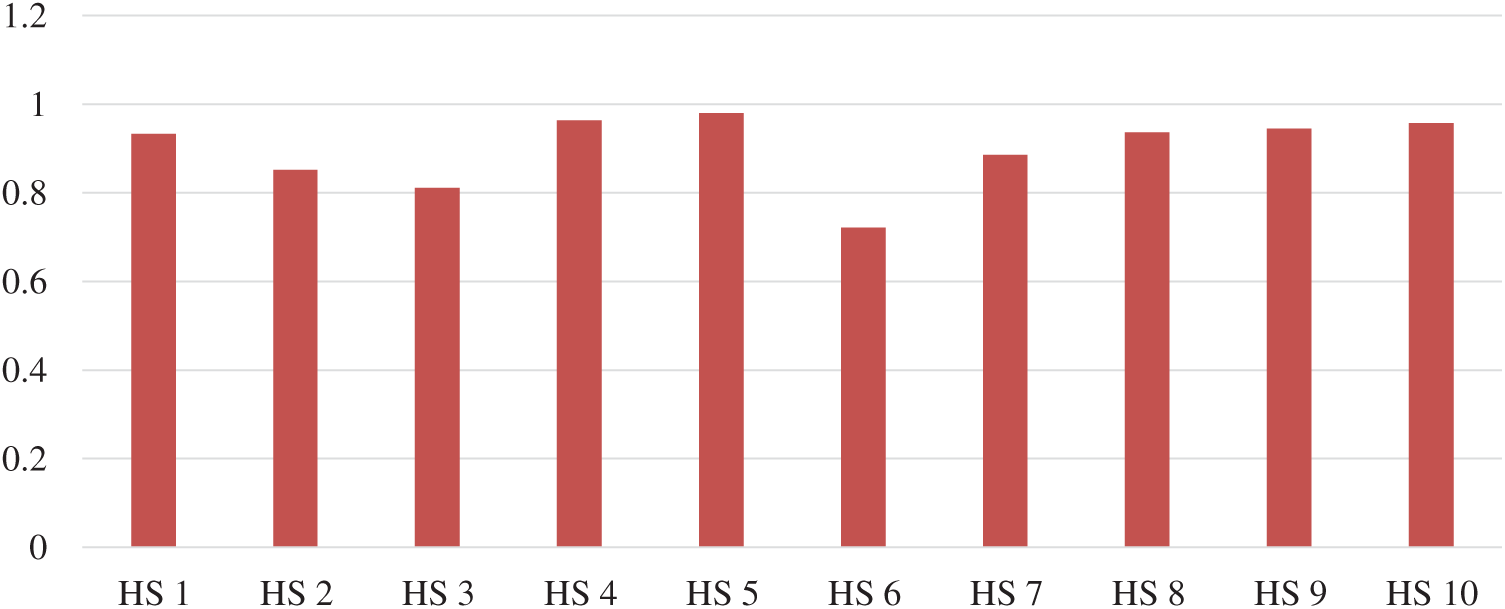
Figure 3: Graphical chart of satisfaction degree of the alternatives
The sensitivity research is conducted to verify the authenticity of the results when changes are made to the variables [29,54–56]. Since the measurements in this work are dependent, the sensitivity analysis is performed on the weights. In this analysis, there are seventeen characteristics in the last level throughout the hierarchy, and sensitivities are then tested through seventeen observations. The weights of all the characteristics vary, whereas the weights of other characteristics have been constant [57–59]. The degree of satisfaction is calculated by using Fuzzy AHP-TOPSIS. Tab. 14 and Fig. 4 show the outcomes of the sensitivity analysis.
Table 14: Sensitivity analysis

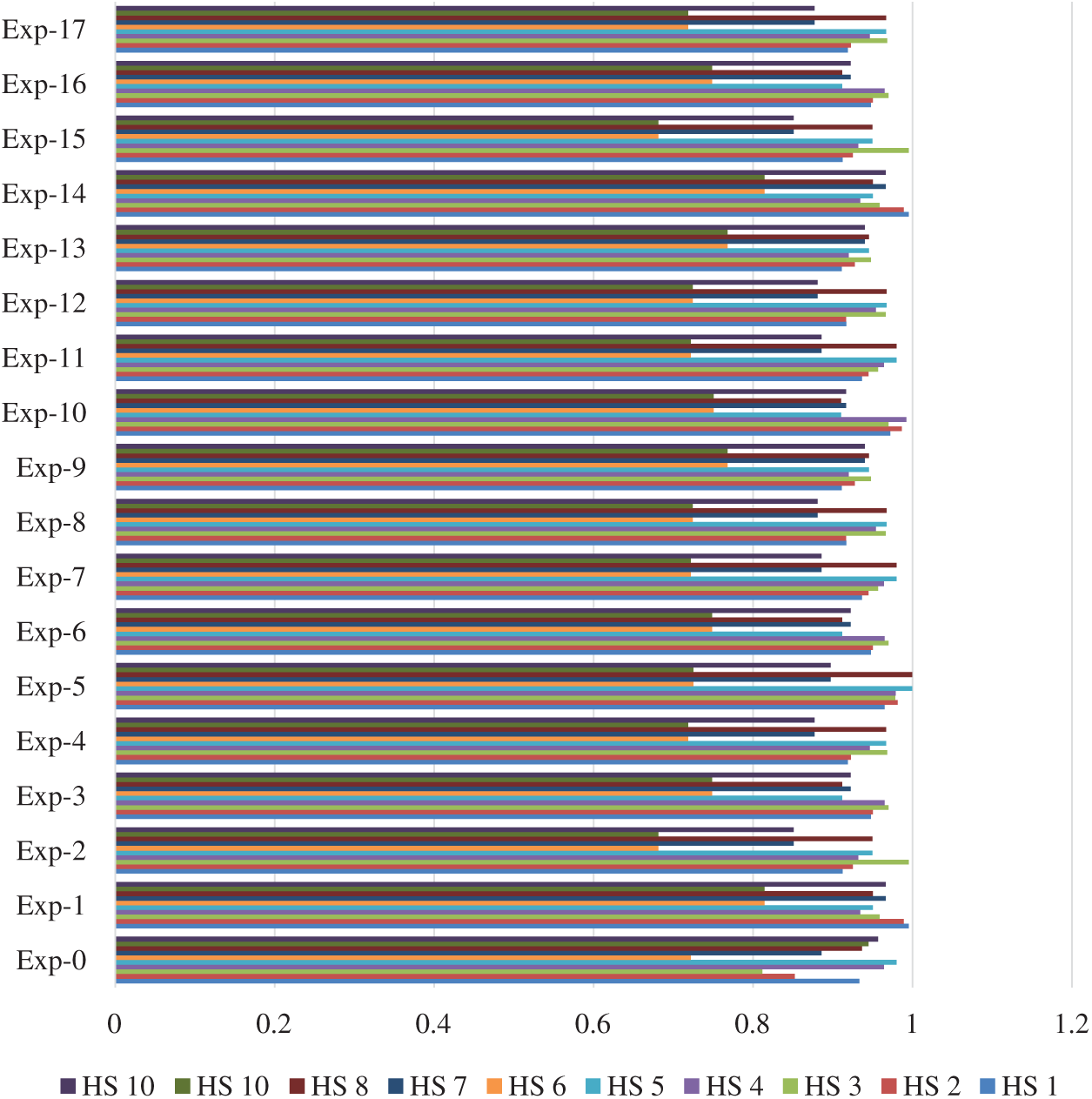
Figure 4: Graphical chart of sensitivity analysis
The original weights of this work are shown in the first row in Tab. 14. HS-8 has elevated satisfaction degree according to the original results. Seventeen experiments are performed, from A111 to A25. Results obtained show that, in seventeen studies, HS-8 still has an elevated degree of satisfaction. The least amount of alternative weight in each study is also A21. Differing results suggest that the alternatives ratings are weight prone.
7 Comparison through Various AHP-TOPSIS Approaches
Analogous data gives conflicting outcomes when used with altered approaches [12,13]. Researchers have used one or more approaches to verify that the outcomes obtained through the proposed approach are accurate [14]. This study uses Simple and Classical AHP-TOPSIS [15], Fuzzy-AHP-SAM (Analytic Hierarchy Process-Simple Aggregation Method) [15], Delphi-AHP with integration to TOPSIS and Fuzzy-Delphi-AHP with integration to TOPSIS methods [16,17] to approximate the results using a different approach and to test the accuracy of the results. Fuzzy sets, in a short time, have attracted the attention of several researchers since ambiguous situations are very common in widely different world issues and this new strategy encourages the handling of unwillingness-caused uncertainty. A fuzzy set is known as a function that returns for each characteristic within the set of membership values. In fuzzy set, the degree of membership at any point has one possible value in [0,1]. In addition, the data collection and estimation processes in classical AHP-TOPSIS and Delphi-AHP-TOPSIS are the same without fluctuation as in Fuzzy based AHP-TOPSIS processing. Thus, data in its original numerical form is used to determine usable-security of healthcare web applications. Tab. 15 and Fig. 5 show the comparison of the tests.
Table 15: Results from different AHP based methods

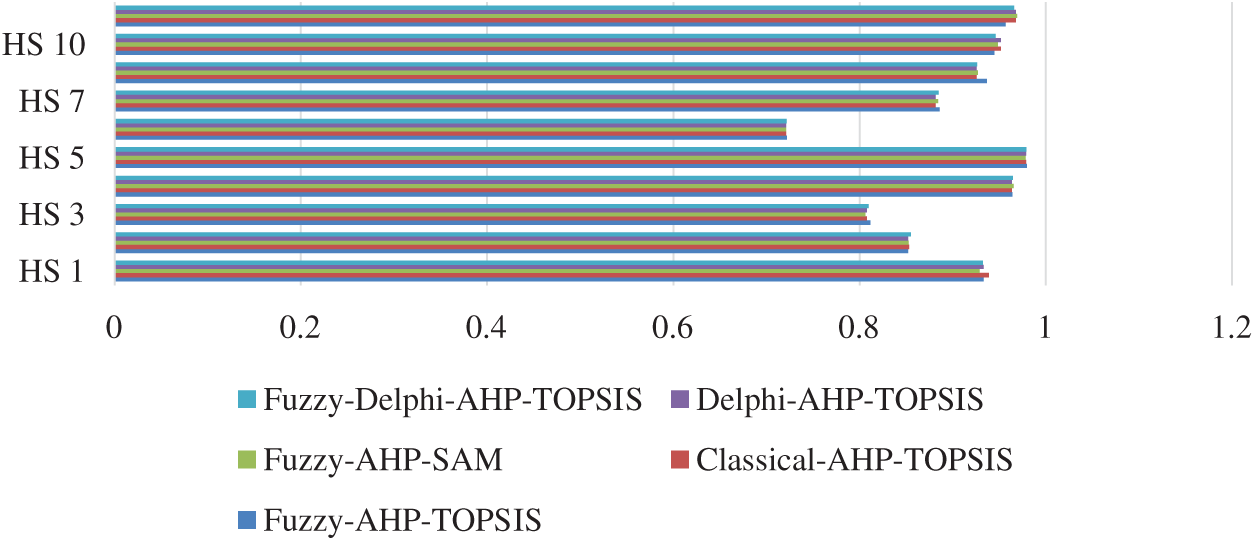
Figure 5: Graphical chart of comparative results
The alternatives are graded by using five hybrid methods based on AHP, according to Tab. 15. The results produced by the methods are highly correlated with the methodology’s results. The Pearson correlation coefficient values between Fuzzy-AHP-TOPSIS and Classical-AHP-TOPSIS, Fuzzy-AHP-SAM, Delphi-AHP-TOPSIS, Fuzzy-Delphi-AHP-TOPSIS are 0.99737, 0.986636, 0.985877 and 0.985877, respectively, using statistical evaluation. The results indicated that other approaches used are highly correlated with the adopted methodology. Furthermore, the grouping of Fuzzy-AHP and Fuzzy-TOPSIS reflects its benefits in linking experts amid priorities which are contrary to consensus. Systematic approach is beneficial as it helps to solve multifaceted, multi-person, and multi-criteria decision-making problems by analyzing ecological issues and connecting them with the corresponding alternative of the healthcare web applications.
Each and every physical system is associated with the internet because of the growth of IoT. This has contributed to the perpetuation of numerous vulnerabilities in security of healthcare web applications. Khan et al. [48] point out that “Security developers began to talk about reuse of credentials by requiring that credentials be updated regularly so that if a password were stolen by any hacker it would only be accessible for a short period”. While this was good for security, it was not very functional for the end user. Usable-security assertion thus emerges as a solution to simultaneously make healthcare web applications secure and usable. In 2013, PhD thesis submitted published by Tripp, M., gave four recommendations to ensure usable-security as much as possible. One of the recommendations was to include the users in the early development phases to ensure usable-security [47]. The author also criticized the fact that new methods are not presented to developers for better implementation. The article’s contributor deliberated on the difficulties developer faces while ensuring usable-security of healthcare web applications.
This research investigation has provided a comprehensive overview that point out the significant and high prioritized usable-security characteristics of healthcare web applications. Additionally, high security is required to defend against the malicious attacks. The main outcomes of this analysis include:
• Usability-security is indeed a persistent issue of this period and requires effective remedial interventions. This evaluation cum priority setting will help the developers to understand usable-security design.
• As evaluation is the primary method of achieving usable-security, the article’s contribution combines both usability and security considerations and assesses the usable-security of healthcare web applications.
• Validation is the most important characteristic according to the outcomes achieved. This confirmation will further help to focus on the characteristics prioritized to achieve high usable-security of healthcare web applications.
• The findings of this research contribution will assist the practitioners in determining the useful and significant characteristics among the number of usable-security characteristics of healthcare web applications.
• Seventeen usable-security characteristics were assessed at the final level by the contributors in this research work. Usable-security considerations can be put into focus with the aid of the tests, thus integrating usable-security into the healthcare web applications.
This paper selected ten alternatives of healthcare web applications and gathered the opinions of the experts on the degree and measure of significance of each alternative that contributed to security and usability characteristics. Records were obtained from the views of the experts with the aid of the Fuzzy AHP-TOPSIS process. The possible delimits in the entire investigation can be summated as:
• The data gathered during this analysis may be inadequate because of the available resources. This dataset may be extended.
• Other usable-security characteristics which could also affect usable-security profoundly might have not been opted for in this work.
Security-usability and the amalgamation of both during the development of healthcare web applications need clarification of current expectations of usability and interpretation of a current framework for evaluation of security. This article used fuzzy-based AHP integrated with TOPSIS framework for usability and security estimation as a milestone. The most prioritized characteristic discovered through the assessment was Validation. The second high-priority characteristic was Encryption. The results thus corroborate that practitioners ought to concentrate on Validation (high prioritized characteristic) and Encryption for achievement of the usable as well as secure healthcare web applications. The present state of usability and security is not yet at the standard it needs to be. Therefore, new experiments need to be recognized by the developers and researchers in order to achieve maximum security. In addition, the business still relies on few obsolete security principles that make the code more complicated and therefore less usable. Advance security strategies of healthcare web applications that also emphasize usability are the requirement of this era. In this analysis, the measurement of usable-security would help the developers to insource strategies for making healthcare web applications more secure and usable.
Acknowledgement: The work is funded by grant number 12-INF2970-10 from the National Science, Technology and Innovation Plan (MAARIFAH), the King Abdul-Aziz City for Science and Technology (KACST), Kingdom of Saudi Arabia. We thank the Science and Technology Unit at Umm Al-Qura University for their continued logistics support.
Funding Statement: King Abdul-Aziz City for Science and Technology (KACST), Saudi Arabia.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. F. A. Al-Zahrani. (2020). “Evaluating the usable-security of healthcare software through unified technique of fuzzy logic, ANP and TOPSIS,” IEEE Access, vol. 8, pp. 109905–109916. [Google Scholar]
2. J. F. Chen, H. N. Hsieh and Q. H. Do. (2015). “Evaluating teaching performance based on fuzzy AHP and comprehensive evaluation approach,” Applied Soft Computing, vol. 28, pp. 100–108. [Google Scholar]
3. O. Sohaib, M. Naderpour, W. Hussain and L. Martínez-López. (2019). “Cloud computing model selection for e-commerce enterprises using a new 2-tuple fuzzy linguistic decision-making method,” Computers & Industrial Engineering, vol. 132, pp. 47–58.
4. K. Sahu and Rajshree. (2015). “Stability: Abstract roadmap of security,” American International Journal of Research in Science, Engineering & Mathematics, vol. 2, no. 9, pp. 183–186. [Google Scholar]
5. J. Davis, “The 10 biggest healthcare data breaches of 2019, so far,” Health IT Security, 2019. [Online]. Available: https://healthitsecurity.com/news/the-10-biggest-healthcare-data-breaches-of-2019-so-far. [Google Scholar]
6. R. Kumar, M. Zaroor, M. Alenezi, A. Agrawal and R. A. Khan. (2019). “Measuring security-durability of software through fuzzy-based decision-making process,” International Journal of Computational Intelligence Systems, vol. 12, no. 2, pp. 627–642. [Google Scholar]
7. A. Agrawal, M. Alenezi, R. Kumar and R. A. Khan. (2019). “Measuring the sustainable-security of web applications through a fuzzy-based integrated approach of AHP and TOPSIS,” IEEE Access, vol. 7, pp. 153936–153951. [Google Scholar]
8. A. Ullah, H. Xiao and T. Barker. (2019). “A study into the usability and security implications of text and image based challenge questions in the context of online examination,” Education and Information Technologies, vol. 24, no. 1, pp. 13–39. [Google Scholar]
9. K. Sahu, Rajshree and R. Kumar. (2014). “Risk management perspective in SDLC,” International Journal of Advanced Research in Computer Science and Software Engineering, vol. 4, no. 3, pp. 1247–1251. [Google Scholar]
10. R. Kumar, S. A. Khan and R. A. Khan. (2016). “Analytical network process for software security: A design perspective,” CSI Transactions on ICT, vol. 4, no. 2, pp. 255–258. [Google Scholar]
11. R. Kumar, A. Irshad Khan, Y. B. Abushark, M. M. Alam, A. Agrawal et al. (2020). , “An integrated approach of fuzzy logic, AHP and TOPSIS for estimating usable-security of web applications,” IEEE Access, vol. 8, pp. 50944–50957. [Google Scholar]
12. M. Mardani, A. Jusoh, K. Nor, Z. Khalifah, N. Zakwan et al. (2015). , “Multiple criteria decision-making techniques and their applications-a review of the literature from 2000 to 2014,” Economic Research-EkonomskaIstraživanja, vol. 28, no. 1, pp. 516–571. [Google Scholar]
13. R. Ismailova. (2017). “Web site accessibility, usability and security: A survey of government web sites in Kyrgyz Republic,” Universal Access in the Information Society, vol. 16, no. 1, pp. 257–264. [Google Scholar]
14. E. T. Toll, M. A. Alkureishi, W. W. Lee, S. F. Babbott, P. A. Bain et al. (2019). , “Protecting healing relationships in the age of electronic health records: Report from an international conference,” JAMIA Open, vol. 2, no. 3, pp. 282–290. [Google Scholar]
15. A. R. Lyon, C. C. Lewis, A. Melvin, M. Boyd, S. Nicodimos et al. (2016). , “Health information technologies-academic and commercial evaluation (hit-ace) methodology: Description and application to clinical feedback systems,” Implementation Sciences, vol. 11, no. 1, pp. 128. [Google Scholar]
16. W. Bai, M. Namara, Y. Qian, P. G. Kelley, M. L. Mazurek et al. (2016). , “An inconvenient trust: User attitudes toward security and usability tradeoffs for key-directory encryption systems,” in Twelfth Sym. on Usable Privacy and Security, pp. 113–130, . [Online]. Available: https://www.usenix.org/system/files/conference/soups2016/soups2016-paper-bai.pdf. [Google Scholar]
17. S. Dutta, S. Madnick and G. Joyce. (2015). “SecureUse: Balancing security and usability within system design,” in Int. Conf. on Human-Computer Interaction, Springer, pp. 471–475. [Google Scholar]
18. O. Gordieiev, V. S. Kharchenko and K. Vereshchak. (2017). “Usable-security versus secure usability: An assessment of attributes interaction,” in ICTERI, pp. 727–740, . [Online]. Available: http://ceur-ws.org/Vol-1844/10000727.pdf. [Google Scholar]
19. B. L. Thigpen. (2020). “Strategies to lower security risks involving medical devices in patient care, . [Online]. Available: https://scholarworks.waldenu.edu/cgi/viewcontent.cgi?article=9698&context=dissertations. [Google Scholar]
20. M. Al-Zubaidie, Z. Zhang and J. Zhang,. (2019). “PAX: Using pseudonymization and anonymization to protect patients’ identities and data in the healthcare system,” International Journal of Environmental Research and Public Health, vol. 16, no. 9, 1490. [Google Scholar]
21. J. G. Ronquillo, J. W. Erik, K. Cwikla, R. Szymanski and C. Levy. (2018). “Health IT, hacking, and cybersecurity: National trends in data breaches of protected health information,” JAMIA Open, vol. 1, no. 1, pp. 15–19. [Google Scholar]
22. K. Sahu and R. K. Srivastava. (2018). “Soft computing approach for prediction of software reliability,” ICIC Express Letters, vol. 12, no. 12, pp. 1213–1222. [Google Scholar]
23. T. Koulopoulos, 60 Percent of Companies fail in 6 Months because of this (It’s Not What you Think). Inc., 2017. [Online]. Available: https://www.inc.com/thomas-koulopoulos/the-biggest-risk-to-your-business-cant-be-eliminated-heres-how-youcan-survive-i.html. [Google Scholar]
24. K. Sahu and R. K. Srivastava. (2020). “Needs and importance of reliability prediction: An industrial perspective,” Information Sciences Letters, vol. 9, no. 1, pp. 33–37. [Google Scholar]
25. H. R. Peikari, M. H. Shah and M. C. Lo. (2018). “Patients’ perception of the information security management in health centers: The role of organizational and human factors,” BMC Medical Informatics and Decision Making, vol. 18, no. 1, pp. 102. [Google Scholar]
26. N. K. Hai, S. Lawpoolsri, P. Jittamala, P. T. T. Huong and J. Kaewkungwal. (2017). “Practices in security and confidentiality of HIV/AIDS patients’ information: A national survey among staff at HIV outpatient clinics in Vietnam,” PLoS One, vol. 12, no. 11, e0188160. [Google Scholar]
27. I. Carrión, J. L. Fernández-Alemán and A. Toval. (2011). “Usable privacy and security in personal health records,” Lecture Notes in Computer Science, vol. 6949, no. 5, pp. 54–87. [Google Scholar]
28. O. B. Fredj. (2019). “SPHERES: An efficient server-side web application protection system,” International Journal of Information and Computer Security, vol. 11, no. 1, pp. 33–60. [Google Scholar]
29. A. Agrawal, M. Zaroor, M. Alenezi, R. Kumar and R. A. Khan. (2019). “Security durability assessment through fuzzy analytic hierarchy process,” PeerJ Computer Science, vol. 5, no. 5, pp. 1–43. [Google Scholar]
30. K. Sahu and R. K. Srivastava. (2019). “Revisiting software reliability,” in Data Management, Analytics and Innovation (Advances in Intelligent Systems and ComputingSpringer, pp. 221–235. [Google Scholar]
31. S. K. Beach. (2014). “Usable cybersecurity: Human factors in cybersecurity education curricula,” National Cybersecurity Institute Journal, vol. 5, pp. 5–15. [Google Scholar]
32. U. Lechner. (2019). “Future Security: Processes or properties?—Research directions in cybersecurity,” in Models, Mindsets, Meta: The What, the How, and the Why Not?, Cham: Springer, vol. 11200. [Google Scholar]
33. C. Sun. (2010). “A performance evaluation model by integrating fuzzy AHP and fuzzy TOPSIS methods,” Expert Systems with Applications, vol. 37, no. 2, pp. 7745–7754. [Google Scholar]
34. A. Samvedi, V. Jain and F. T. Chan. (2013). “Quantifying risks in a supply chain through integration of fuzzy AHP and fuzzy TOPSIS,” International Journal of Production Research, vol. 51, no. 8, pp. 2433–2442. [Google Scholar]
35. R. Kumar, S. A. Khan and R. A. Khan. (2015). “Durable security in software development: Needs and importance,” CSI Communication, vol. 39, no. 7, pp. 34–36. [Google Scholar]
36. K. Sahu and Rajshree. (2015). “Software security: A risk taxonomy,” International Journal of Computer Science & Engineering Technology, vol. 7, no. 3, pp. 36–41. [Google Scholar]
37. J. J. Gonzalez and A. Sawicka. (2003). “A framework for human factors in information security,” . [Online]. Available: http://www.computerhope.com/jargon/p/privacy.htm. [Google Scholar]
38. N. Wang, C. Y. Yang and H. C. Cheng. (2019). “A fuzzy multicriteria decision-making (MCDM) model for sustainable supplier evaluation and selection based on triple bottom line approaches in the garment industry,” Processes, vol. 7, no. 7, pp. 400–415. [Google Scholar]
39. C. Calabrese, R. Costa, N. Levialdi and T. Menichini. (2019). “Integrating sustainability into strategic decision-making: A fuzzy AHP method for the selection of relevant sustainability issues,” Technological Forecasting and Social Change, vol. 139, pp. 155–168. [Google Scholar]
40. K. Sahu, F. A. Alzahrani, R. K. Srivastava and R. Kumar, “Hesitant fuzzy sets based symmetrical model of decision-making for estimating the durability of web application,” Symmetry, vol. 12, no. 11, pp. 1770–1782, 2020. [Google Scholar]
41. K. Sahu and Rajshree. (2015). “Helpful and defending actions in software risk management: A security viewpoint,” Integrated Journal of British, vol. 4, pp. 1–7. [Google Scholar]
42. R. Kumar, S. A. Khan and R. A. Khan. (2016). “Durability challenges in software engineering,” Crosstalk, vol. 29, no. 5, pp. 29–31. [Google Scholar]
43. N. S. Good and A. Krekelberg. (2013). “Usability and privacy: A study of Kazaa P2P file-sharing,” in Proc. of the SIGCHI Conf. on Human Factors in Computing Systems, ACM, pp. 137–144, . Available: https://img2.helpnetsecurity.com/dl/articles/KazaaUsability.pdf. [Google Scholar]
44. P. Napoli. (2018). “Developing accessible and usable-security (ACCUS),” in Extended Abstracts of the 2018 CHI Conf. on Human Factors in Computing Systems, ACM, pp. SRC16, . [Online]. Available: https://doi.org/10.1145/3170427.3180292. [Google Scholar]
45. C. Braz, A. Seffah and D. M’Raihi. (2007). “Designing a trade-off between usability and security: A metrics based-model,” In: Baranauskas, C., Abascal, J., Barbosa, S.D.J. (eds.INTERACT 2007, vol. 4663. Heidelberg: LNCS, Springer, pp. 114–126. [Google Scholar]
46. 2019 healthcare data breach report. HIPAA Journal, 2019. [Online]. Available: https://www.hipaajournal.com/2019-healthcare-databreach-report/. [Google Scholar]
47. A. Tripp, M. Pistoia, P. Cousot, R. Cousot and S. Guarnieri. (2013). “Andromeda: Accurate and scalable security analysis of web applications,” in Int. Conf. on Fundamental Approaches to Software Engineering, Berlin, Heidelberg: Springer, pp. 210–225. [Google Scholar]
48. S. A. Khan, M. Alenezi, A. Agrawal, R. Kumar and R. A. Khan. (2020). “Evaluating performance of software durability through an integrated fuzzy-based symmetrical method of ANP and TOPSIS,” Symmetry, vol. 12, no. 4, pp. 1–15. [Google Scholar]
49. A. Agrawal, M. Alenezi, S. A. Khan, R. Kumar and R. A. Khan. (2019). “Multi-level fuzzy system for usable-security assessment,” Journal of King Saud University-Computer and Information Sciences, pp. 1–9. [Google Scholar]
50. R. Kumar, S. A. Khan, A. Agrawal and R. A. Khan. (2018). “Measuring the security attributes through fuzzy analytic hierarchy process: Durability perspective,” ICIC Express Letters—An International Journal of Research and Surveys, vol. 12, no. 6, pp. 615–620. [Google Scholar]
51. A. Agrawal, M. Alenezi, D. Pandey, R. Kumar and R. A. Khan. (2019). “Usable-security assessment through a decision making procedure, ICIC Express Letters-Part B,” Applications, vol. 10, no. 8, pp. 665–672.
52. M. Alenezi, R. Kumar, A. Agrawal and R. A. Khan. (2019). “Usable-security attribute evaluation using fuzzy analytic hierarchy process,” ICIC Express Letters—An International Journal of Research and Surveys, vol. 13, no. 6, pp. 453–460.
53. R. Kumar, S. A. Khan and R. A. Khan. (2017). “Fuzzy analytic hierarchy process for software durability: Security risks perspective,” Advances in Intelligent Systems and Computing, vol. 508, pp. 469–478. [Google Scholar]
54. A. H. Seh, M. Zarour, M. Alenezi, A. K. Sarkar, A. Agrawal et al. (2020). , “Healthcare data breaches: Insights and implications,” Healthcare, vol. 8, no. 133, pp. 1–18. [Google Scholar]
55. A. Agrawal, M. Alenezi, R. Kumar and R. A. Khan. (2020). “A unified fuzzy-based symmetrical multi-criteria decision-making method for evaluating sustainable-security of web applications,” Symmetry, vol. 12, no. 3, pp. 1–23.
56. R. Kumar, A. I. Khan, Y. B. Abushark, M. M. Alam, A. Agrawal et al. (2020). , “A knowledge based integrated system of hesitant fuzzy set, AHP and TOPSIS for evaluating security-durability of web applications,” IEEE Access, vol. 8, no. 2, pp. 48870–48885. [Google Scholar]
57. M. Alenezi, A. Agrawal, R. Kumar and R. A. Khan. (2020). “Evaluating performance of web application security through a fuzzy based hybrid multi-criteria decision-making approach: Design tactics perspective,” IEEE Access, vol. 8, no. 1, pp. 25543–25556. [Google Scholar]
58. R. Kumar, S. A. Khan, A. Agrawal and R. A. Khan. (2018). “Security assessment through fuzzy Delphi analytic hierarchy process,” ICIC Express Letters—An International Journal of Research and Surveys, vol. 12, no. 10, pp. 1053–1060.
59. A. Algarni, M. Ahmad, A. Attaallah, A. Agrawal, R. Kumar et al. (2020). , “A fuzzy multi-objective covering-based security quantification model for mitigating risk of web based medical image processing system,” International Journal of Advanced Computer Science and Applications, vol. 11, no. 1, pp. 481–489. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |