DOI:10.32604/cmc.2020.013743

| Computers, Materials & Continua DOI:10.32604/cmc.2020.013743 |  |
| Article |
A Comprehensive Utility Function for Resource Allocation in Mobile Edge Computing
1Telecommunications and Networking (TeleCoN) Research Laboratory, GIK Institute of Engineering Sciences and Technology, Topi, 23640, Pakistan
2Faculty of Electrical Engineering, GIK Institute of Engineering Sciences and Technology, Topi, 23640, Pakistan
3Faculty of Computer Sciences and Engineering, GIK Institute of Engineering Sciences and Technology, Topi, 23640, Pakistan
4Department of Information and Communication Technology, University of Agder (UiA), Grimstad, 4898, Norway
5Department of Information and Communication Engineering, Inha University, Incheon, 22212, Korea
6Department of Computer and Electronics Systems Engineering, Hankuk University of Foreign Studies, Gyeonggi-do, 17035, Korea
*Corresponding Author: Muhammad Bilal. Email: m.bilal@ieee.org
Received: 19 August 2020; Accepted: 14 September 2020
Abstract: In mobile edge computing (MEC), one of the important challenges is how much resources of which mobile edge server (MES) should be allocated to which user equipment (UE). The existing resource allocation schemes only consider CPU as the requested resource and assume utility for MESs as either a random variable or dependent on the requested CPU only. This paper presents a novel comprehensive utility function for resource allocation in MEC. The utility function considers the heterogeneous nature of applications that a UE offloads to MES. The proposed utility function considers all important parameters, including CPU, RAM, hard disk space, required time, and distance, to calculate a more realistic utility value for MESs. Moreover, we improve upon some general algorithms, used for resource allocation in MEC and cloud computing, by considering our proposed utility function. We name the improved versions of these resource allocation schemes as comprehensive resource allocation schemes. The UE requests are modeled to represent the amount of resources requested by the UE as well as the time for which the UE has requested these resources. The utility function depends upon the UE requests and the distance between UEs and MES, and serves as a realistic means of comparison between different types of UE requests. Choosing (or selecting) an optimal MES with the optimal amount of resources to be allocated to each UE request is a challenging task. We show that MES resource allocation is sub-optimal if CPU is the only resource considered. By taking into account the other resources, i.e., RAM, disk space, request time, and distance in the utility function, we demonstrate improvement in the resource allocation algorithms in terms of service rate, utility, and MES energy consumption.
Keywords: Cloud computing; energy efficient resource allocation; mobile edge computing; service rate; user equipment; utility function
With the exponential growth of the Internet of Things (IoT) and 5G technologies, highly advanced mobile applications, such as online games, face and speech recognition etc., are rapidly emerging [1]. Because of the computationally and communicationally expensive applications, the computation capability and battery life of a user equipment (UE) are normally insufficient [2]. Cloud computing can, to a certain extent, enhance the computing capacity of UEs, however, long distances between cloud and UEs lead to high latency and energy consumption [3,4]. Moreover, the demand for high definition and low latency mobile applications is increasing day by day. This tendency poses significant challenges to the existing mobile networks especially during the high traffic hours [5]. To address these problems, a new computing paradigm has emerged, known as mobile edge computing (MEC) [1,2]. MEC enables the cloud computing capabilities and storage services at the edge of a network, which enables UEs to execute their tasks more efficiently [3].
In MEC, two problems are of great importance, namely, task offloading and resource allocation [6]. This paper concerns the latter, which refers to the ability of a central control unit to assign UEs to mobile edge servers (MESs) and to allocate specific amount of resources to UE requests. Thus, the UEs execute their applications remotely in a more efficient way by using powerful MESs. The MESs, in return for allowing their resources to be used, obtain a reward in terms of a unit-less quantity, named as utility [7].
According to Wu et al. [7], different individuals have different utility functions due to distinct needs towards a specific service. However, there are some general requirements in resource allocation problems in MEC, which must be considered in utility functions. Central processing unit (CPU), random access memory (RAM), hard disk, and the time for which these resources will be used are important parameters to be considered in a utility function. The authors in Fernandes et al. [8] consider CPU, RAM, and other hardware components to design a virtual machine (VM) scheduler, which schedules VMs in such a way to minimize the energy consumption of data centers. However, this approach is not a utility based approach and can be used only for cloud computing. The authors in [9,10] investigate the resource allocation problem and propose a deep learning approach to minimize the service time and efficiently allocate resources to UEs. However, the energy consumption and the utility function for MESs are not considered. The authors in Dlamini et al. [11] propose a computing-plus-communication energy model for resource allocation in MEC, where they use a hybrid-powered MES and switching techniques of transmission drivers to minimize MESs’ energy consumption.
The authors in Li et al. [12] present a stochastic approach, using Lyapunov optimization technique, for wireless-powered MEC to minimize the energy consumption by optimizing the transmission power of MESs. The authors in Liu et al. [13] use the effect of dynamic energy variation to propose a dynamic game-based approach for resource allocation in wireless powered MEC. In their approach, the resources are optimally allocated by computing optimal transmission power and optimal task offloading. The authors in Kan et al. [14] consider the task offloading and resource allocation problems in MEC. The resource allocation problem is solved as a cost minimization problem. However, the work mainly focuses on task offloading, and for resource allocation the utility for MESs is ignored. Futhermore, the authors in [15,16] propose a VM placement algorithm for cloud computing. The main objective of their work is to minimize the energy consumption by minimizing the number of active servers. However, in a utility function realistic needs of UEs can be introduced to generalize the technique for MEC.
Most of the literature on resource allocation [17–20] in MEC and cloud computing considers only the CPU as resource requested by the UEs. However, hard disk space, RAM, and the time that an MES allocates to UEs for using resources are also important parameters but are ignored in dealing with UE requests. Moreover, most of the related work considers the utility function as a uniform random variable [7] or only considers the requested CPU in utility function [21,22]. However, the utility function for MES must be proportional to the amount of all resources used by UEs.
In the literature, there are certain algorithms that employ the concept of utility function for resource allocation problem in MEC and cloud computing [1,22]. In this paper, by utilizing our comprehensive mathematical model for utility function and UE requests, we modify these algorithms and make them more comprehensive for MEC. To make the mathematical model more realistic and comprehensive, we consider CPU, RAM, disk space, required time, and the distance between MES and UE in the mathematical model for UE request and utility function. To the best of our knowledge, no such comprehensive mathematical model exists for UE request and utility function in MEC resource allocation. The novelty and contributions of our work are summarized as follows:
• We consider CPU, RAM, hard disk, and requested time that will be used by UEs, as a UE request in resource allocation problem in MEC. The existing schemes consider only CPU as UE request.
• A novel comprehensive utility function for MESs is developed which depends on all the above mentioned resources. It also depends on the distance between UE and MES, which ensures the dependency of utility on quality-of-service (QoS).
• By using our proposed mathematical model, we improve four well-known MES resource allocation algorithms, namely, Basic Over-provisioning (BO), Greedy Max (GM), Minimum Expand (MinExpand), and Power Minimum Expand (PowExpand).
• Our corresponding comprehensive algorithms, namely, Comprehensive Basic Overprovisioning (CBO), Comprehensive Greedy Max (CGM), Comprehensive Minimum Expand (CMinExpand), and Comprehensive Power Minimum Expand (CPowExpand), improve the utility for MESs and the service rate, and minimize the energy consumption of MESs.
The rest of the paper is structured as follow. Section II describes the mathematical model for the UE request and utility function. Section III presents the proposed comprehensive resource allocation schemes. Section IV presents simulation results and Section V concludes the paper.
When a UE offloads its task for execution to the central control unit of MEC, it is important to allocate resources of different MESs upon incoming UE’s requests. In our system model, there are multiple MESs with different amounts of available resources, as shown in Fig. 1. It is a challenging task to select an MES and allocate its resource to incoming UE’s requests to improve service rate, power efficiency, and utility simultaneously. In this paper, we propose utility based comprehensive algorithms for resources allocation. We consider the same multi-user multi-server scenario as used by Cardosa et al. [22]. The number of incoming requests is modeled according to the Poisson distribution. It is assumed that the system consists of a central control unit that detects the incoming UE requests, selects the optimal MES for each request, and allocates MES resources to these requests.
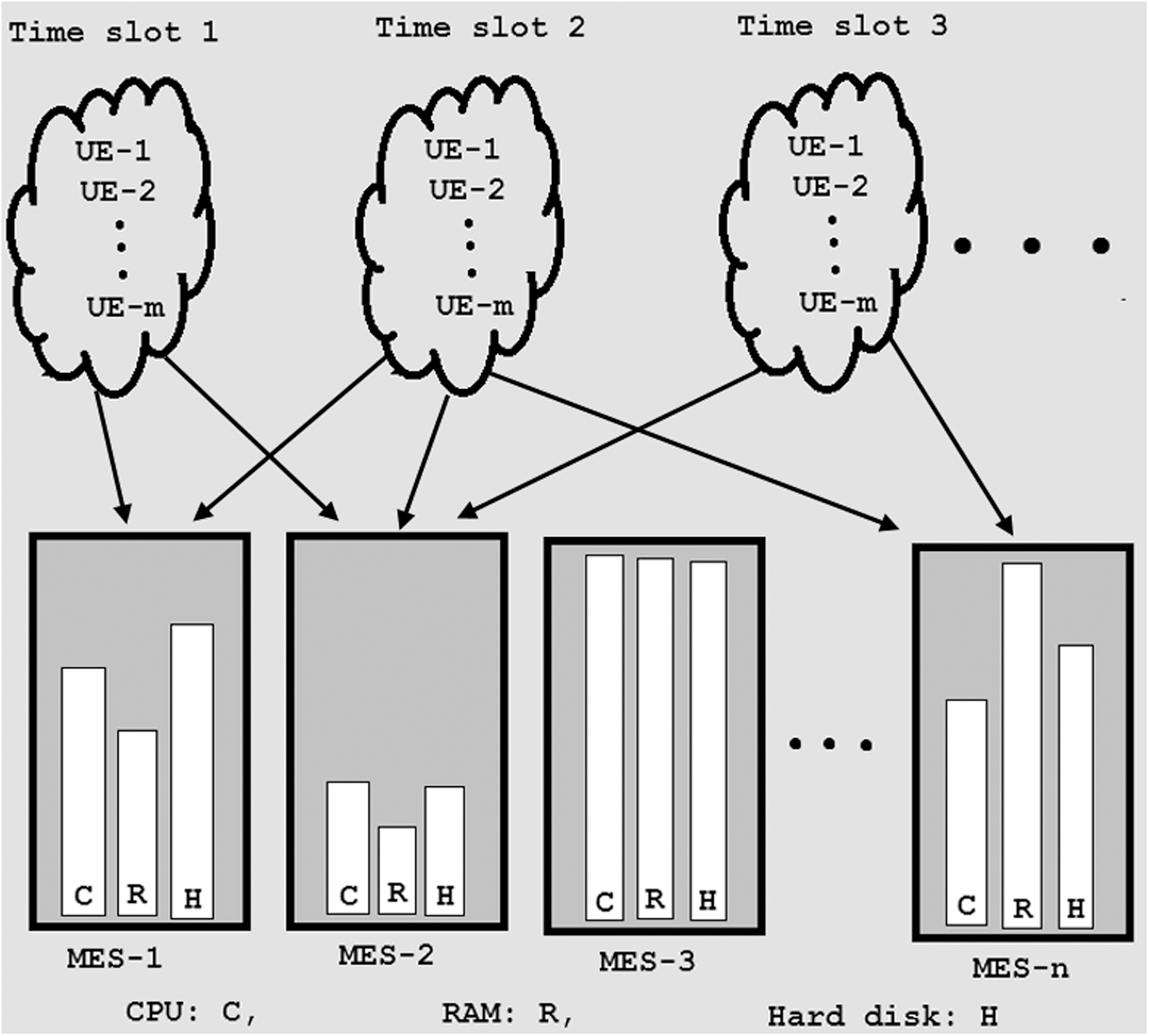
Figure 1: MESs with different amounts of available resources
We consider n servers and m UE requests. The request matrix is modelled in two parts: (i) The requested resources matrix Q, and (ii) The distance matrix D. The resource matrix Q is given by:
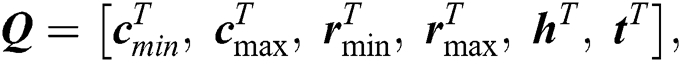
where 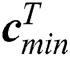 and
and 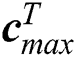 , respectively, represent the vectors of the minimum and the maximum amount of CPU in m UE requests.
, respectively, represent the vectors of the minimum and the maximum amount of CPU in m UE requests. 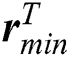 and
and 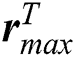 , respectively, represent the vectors of the minimum and the maximum amount of RAM in UE requests.
, respectively, represent the vectors of the minimum and the maximum amount of RAM in UE requests. 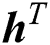 is the vector of the amount of disk space in UE requests, and
is the vector of the amount of disk space in UE requests, and 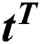 is the vector of the number of time slots specified in the UE requests for which these resources are needed. We assume that this required time for using the resources of an MES is enough for execution of UE’s task. Alternatively, the required time can be exceeded in the next UE request. For example, if the requested time is not enough for the execution of the given task then UE sends another request for the remaining task. The disk space is not modeled as a variable resource because, in most real-word scenarios, an application needs a fixed amount of disk space for its operation. Thus, there are six important parameters that a UE sends to the central control unit as its request. Therefore, the order of the matrix Q is m × 6, where m is the total number of incoming UE requests. The vectors in Q can be written as:
is the vector of the number of time slots specified in the UE requests for which these resources are needed. We assume that this required time for using the resources of an MES is enough for execution of UE’s task. Alternatively, the required time can be exceeded in the next UE request. For example, if the requested time is not enough for the execution of the given task then UE sends another request for the remaining task. The disk space is not modeled as a variable resource because, in most real-word scenarios, an application needs a fixed amount of disk space for its operation. Thus, there are six important parameters that a UE sends to the central control unit as its request. Therefore, the order of the matrix Q is m × 6, where m is the total number of incoming UE requests. The vectors in Q can be written as:
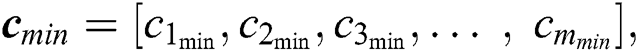
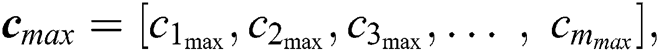
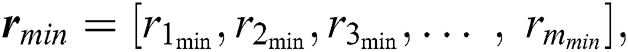
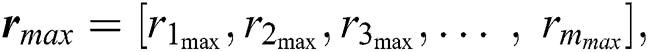
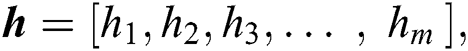
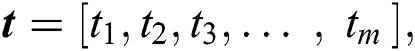
where 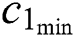 ,
, 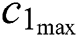 ,
, 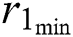 ,
, 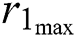 ,
, 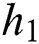 , and
, and 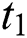 represent the minimum CPU, the maximum CPU, the minimum RAM, the maximum RAM, the disk space, and the time requested by UE 1, respectively. In general for UE j, we can denote these requested resources as
represent the minimum CPU, the maximum CPU, the minimum RAM, the maximum RAM, the disk space, and the time requested by UE 1, respectively. In general for UE j, we can denote these requested resources as 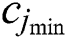 ,
, 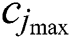 ,
, 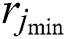 ,
, 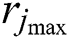 ,
, 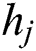 , and
, and 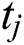 . The dimensions of vectors
. The dimensions of vectors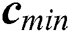 ,
, 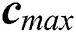 ,
, 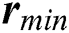 ,
, 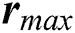 ,
, 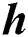 , and
, and 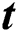 are 1 × m.
are 1 × m.
The distance matrix D, containing the distances of m users from n MESs, is given by:
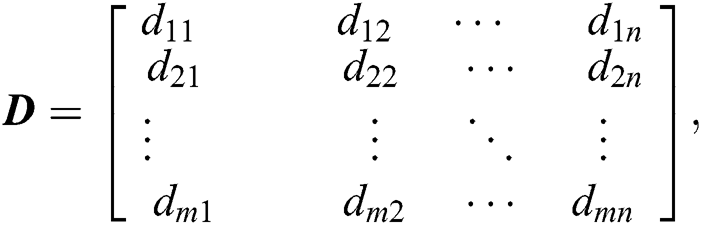
where 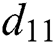 is the distance between UE 1 and MES 1. Similarly,
is the distance between UE 1 and MES 1. Similarly, 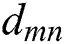 is the distance between UE m and MES n. In general,
is the distance between UE m and MES n. In general, 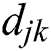 represents the distance of UE j from MES k.
represents the distance of UE j from MES k.
2.2 The Proposed Comprehensive Utility Function
Utility is the reward that an MES receives for allowing its resources to be used by UEs. Since MESs provide their CPU, RAM, and hard disk for a specific period of time to UEs, the utility in this paper depends on the amount of CPU, RAM, and disk space requested by the UE, the time for which a UE has requested these resources, and the distance between the UE and the MES. Therefore, the utility function is directly proportional to the requested resources and time. The QoS that the UE receives is inversely proportional to the distance between the UE and the MES because of the network conditions, the transmission range of the UE and the MES, the frequent disconnections, and the latency in communication. The utility is, therefore, given as:
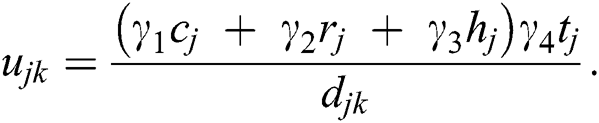
Here, 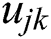 is the utility for MES k for serving UE j.
is the utility for MES k for serving UE j. 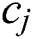 ,
, 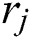 , and
, and 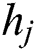 , respectively, denote the amount of CPU, RAM and hard disk space allocated to UE j by MES k,
, respectively, denote the amount of CPU, RAM and hard disk space allocated to UE j by MES k, 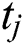 is the time for which these resources are allocated, and
is the time for which these resources are allocated, and 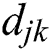 is the distance between UE j and MES k. The requested resources are weighted and normalized by the unit balancing and weighting coefficients (
is the distance between UE j and MES k. The requested resources are weighted and normalized by the unit balancing and weighting coefficients (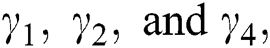 respectively) as:
respectively) as:
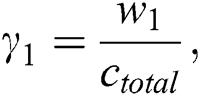
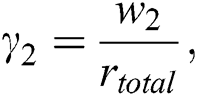
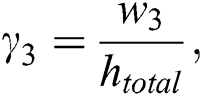
where 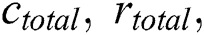 and
and 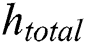 are the combined total CPU, RAM, and hard disk space of all the servers, respectively, and
are the combined total CPU, RAM, and hard disk space of all the servers, respectively, and 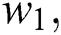
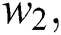 and
and 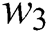 are the weighting coefficients. For example, the value of
are the weighting coefficients. For example, the value of 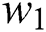 shows the relative contribution of CPU to the utility function. These coefficients can be adjusted to represent the expensiveness of different resources. Similarly, to keep the utility function unitless,
shows the relative contribution of CPU to the utility function. These coefficients can be adjusted to represent the expensiveness of different resources. Similarly, to keep the utility function unitless, 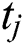 and
and 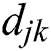 are normalized with respect to the unit balancing and weighting coefficient
are normalized with respect to the unit balancing and weighting coefficient 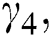 i.e.,
i.e.,
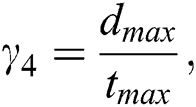
where 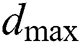 is the maximum distance within which all MESs and UEs can operate, and
is the maximum distance within which all MESs and UEs can operate, and 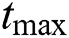 is the maximum time that a UE is allowed to request. The upper threshold on time is configured such that a UE cannot occupy all the resources and prevent other UEs from obtaining the service.
is the maximum time that a UE is allowed to request. The upper threshold on time is configured such that a UE cannot occupy all the resources and prevent other UEs from obtaining the service.
The utility for each MES is different from other MESs for serving the UE requests because of the UE’s location. An MES receives higher utility by serving the nearby UE than by serving a far UE because a user closer to the MES has better QoS and pays a higher premium for it. The utility of n MESs for entertaining the same UE j can, thus, be represented by a vector u as:
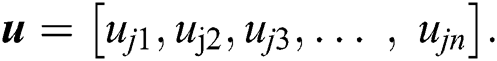
Similarly, the utility matrix U for m UEs and n MESs can be written as:
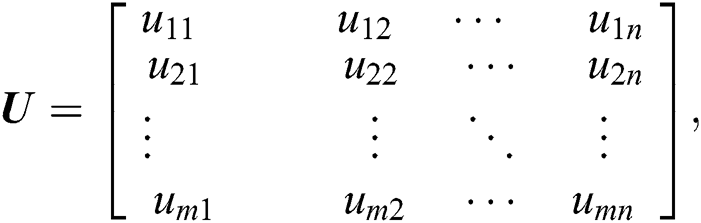
where 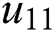 is the utility of UE 1 at MES 1,
is the utility of UE 1 at MES 1, 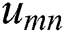 is the utility of UE m at MES n.
is the utility of UE m at MES n.
According to a UE request, the minimum and the maximum utilities that an MES can achieve by serving the request are represented as:
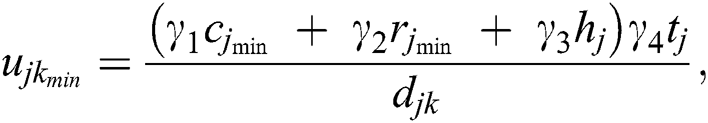
and
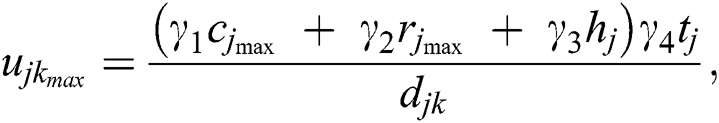
where 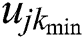 and
and 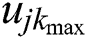 , respectively, represent the minimum and maximum utilities for MES k from UE j.
, respectively, represent the minimum and maximum utilities for MES k from UE j. 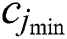 and
and 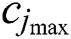 , respectively, represent the minimum and maximum of the CPU resources requested by UE j. Moreover,
, respectively, represent the minimum and maximum of the CPU resources requested by UE j. Moreover, 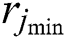 and
and 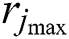 , respectively, represent the minimum and maximum amounts of RAM requested by UE j.
, respectively, represent the minimum and maximum amounts of RAM requested by UE j.
From a set of n available MESs, we find an MES k, such that 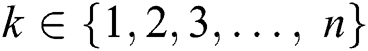 , for which the utility of a UE j is maximum. This MES k is called the optimal MES,
, for which the utility of a UE j is maximum. This MES k is called the optimal MES, 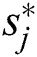 , for UE j, and is represented as:
, for UE j, and is represented as:

An MES k is feasible for UE j if the currently available resources of MES k exceed the resources requested by UE j. A feasibility vector 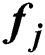 for UE j is given by:
for UE j is given by:
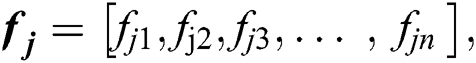
where 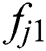 is the feasibility status of MES 1 for UE j, and so on. Formally,
is the feasibility status of MES 1 for UE j, and so on. Formally, 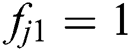 means that MES 1 is feasible for UE j and
means that MES 1 is feasible for UE j and 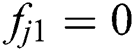 means that MES 1 is not feasible for UE j. The dimension of the feasibility vector
means that MES 1 is not feasible for UE j. The dimension of the feasibility vector 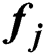 is 1 × n. The feasibility
is 1 × n. The feasibility 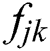 is calculated as:
is calculated as:
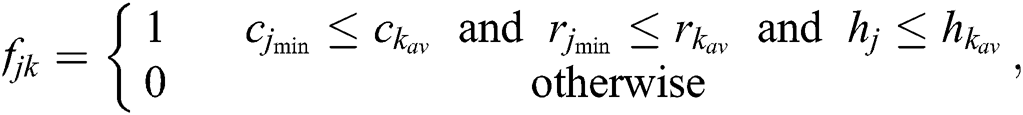
where 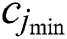 ,
, 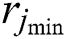 , and
, and 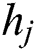 are the minimum resources requested by UE j.
are the minimum resources requested by UE j. 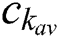 ,
, 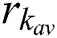 , and
, and 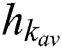 are the resources currently available at MES k. This feasibility vector represents the feasibility of servers for each UE. For example,
are the resources currently available at MES k. This feasibility vector represents the feasibility of servers for each UE. For example, 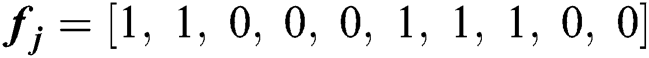 means that MES 1, 2, 6, 7, and 8 are feasible for UE j. We can only serve UE j at one of the feasible servers.
means that MES 1, 2, 6, 7, and 8 are feasible for UE j. We can only serve UE j at one of the feasible servers.
The energy consumed by each MES for keeping itself ON (active) is different from other MESs because of its capacity and type of hardware used. The energy consumed per unit time in keeping the MES k ON is represented by 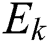 . The total resources of MES k define its capacity
. The total resources of MES k define its capacity 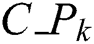 as:
as:
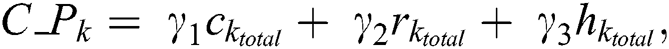
where 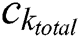 ,
, 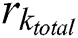 , and
, and 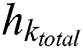 represent the total CPU resources, RAM, and hard disk space of MES k, respectively. The energy consumption per unit capacity,
represent the total CPU resources, RAM, and hard disk space of MES k, respectively. The energy consumption per unit capacity, 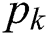 , of MES k can be written as:
, of MES k can be written as:
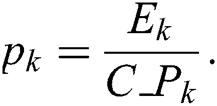
The MESs are sorted in increasing order of 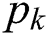 . An MES with lower value of
. An MES with lower value of 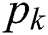 shows that it has a higher capacity for serving larger UE requests while its energy consumption for keeping it ON is low. Hence, it should be employed more often than other MESs with higher value of
shows that it has a higher capacity for serving larger UE requests while its energy consumption for keeping it ON is low. Hence, it should be employed more often than other MESs with higher value of 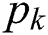 .
.
An MES that is already in the ON state should be prioritized for entertaining new UE requests, whereas the MESs that are in the idle state should be avoided to activate as long as possible to conserve energy. Our proposed algorithms use the more profitable and already active servers first, and only activate the less profitable servers if the currently active servers are not enough to handle the incoming traffic. Therefore, we introduce the penalty in the utility function as:
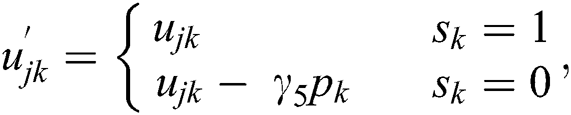
where 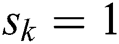 indicates that MES k is ON, and
indicates that MES k is ON, and 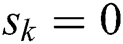 implies that MES k is idle. The unit balancing coefficient
implies that MES k is idle. The unit balancing coefficient 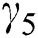 is given as:
is given as:
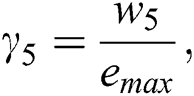
where 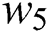 is the weighting coefficient and its value can be adjusted to make the threshold for activating an idle server higher or lower, and
is the weighting coefficient and its value can be adjusted to make the threshold for activating an idle server higher or lower, and 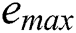 is the sum of the
is the sum of the 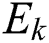 for all servers.
for all servers.
The energy consumption due to the usage of CPU, RAM, and disk space depends on the instruction type and architecture of the system used in an MES. We assume linear relation between the energy consumption and usage of CPU, RAM, and disk space [23]. The energy consumption due to CPU usage, RAM usage, and disk space usage of MES k, i.e., 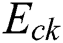 ,
, 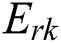 , and
, and 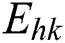 , respectively, can be given as:
, respectively, can be given as:
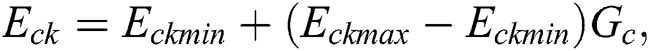

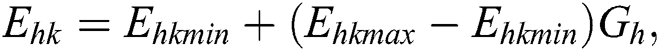
where 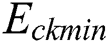 ,
, 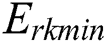 , and
, and 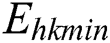 , respectively, represent the energy consumption when the CPU, RAM, and disk space are not in use. Similarly,
, respectively, represent the energy consumption when the CPU, RAM, and disk space are not in use. Similarly, 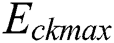 ,
, 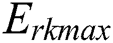 , and
, and 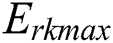 represent the energy consumption when the CPU, RAM, and disk space, respectively, are fully utilized.
represent the energy consumption when the CPU, RAM, and disk space, respectively, are fully utilized. 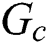 ,
, 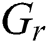 , and
, and 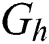 are the utilization of CPU, RAM, and disk space, respectively. The total energy consumption of MES k,
are the utilization of CPU, RAM, and disk space, respectively. The total energy consumption of MES k, 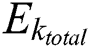 , is therefore calculated as:
, is therefore calculated as:
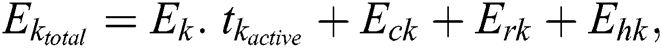
where 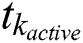 is the total time for which the MES k was active. The total energy consumption of all the MESs,
is the total time for which the MES k was active. The total energy consumption of all the MESs, 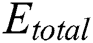 , can be written as:
, can be written as:
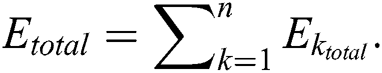
In MEC, the central control unit assigns MESs and the resources of MESs to different UE’s requests. To select the best MES for a specific UE and to allocate the resources according to the request of UE are challenging. In the literature, there are certain general algorithms used for resource allocation in cloud computing and MEC which only consider the CPU as UE requests or a random utility function independent of UE requests. We improve the well-known MES resource allocation algorithms [22] by considering our comprehensive mathematical formulation for UE request and utility function of MES. In this section, we explain our proposed comprehensive algorithms.
3.1 Comprehensive Basic Over-Provisioning
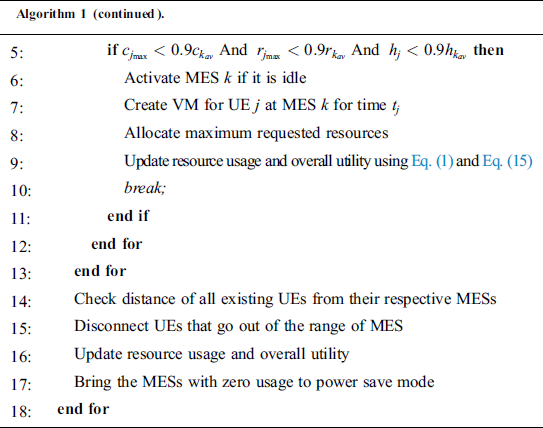
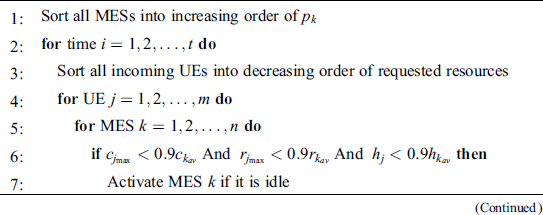
The idea behind basic over-provisioning scheme (BO) used in Cardosa et al. [22] is about serving the UEs on a first-come first-served basis by allocating the maximum requested CPU to them. The BO scheme keeps fitting VMs into the first available MES until the server is left with 10% of its maximum CPU. Following the same approach, our proposed comprehensive BO (CBO) scheme determines the available capacity at the servers one by one in the decreasing order of their profitability and creates the VM of the incoming UE requests at the first available MES.
Algorithm 1 explains CBO, which is different from BO in the sense that it also considers RAM and disk space instead of considering CPU only. In addition, it also considers the time for which a UE has requested these resources and creates the VM for that particular time. When the time that the UE requested has elapsed, the VM is deleted automatically and the resource usage of the MES is adjusted accordingly. CBO is similar to BO in the sense that it does not differentiate between UE requests in terms of their utilities.
Algorithm 1: Comprehensive Basic Over-provisioning

Serving the UE requests regardless of the utility that they offer is disadvantageous for MESs. The Greedy Max (GM) algorithm [22] tackles this problem. However, GM considers only CPU as UE request and, therefore, the utility function only depends on the requested CPU. We propose a Comprehensive Greedy Max (CGM) algorithm in which we consider CPU, RAM, hard disk, required time, and distance as UE request. Therefore, we model our comprehensive utility function depending on these realistic values in a UE request. Contrary to CBO, CGM first sorts the incoming UE requests in the decreasing order of their utility. For instance, if there are three UE requests in the first time slot, CBO scheme allocates the maximum requested resources to each of them regardless of any priority, whereas CGM sorts them into the decreasing order of their maximum requested resources (maximum utility), and then allocates the maximum requested resources to them. CGM is presented in Algorithm 2.
Algorithm 2: Comprehensive Greedy Max
In the case of high traffic, the difference between the performance of CBO and CGM is clear when the MESs start filling up and some of the UEs are denied services. The UEs that are denied services, in case of CGM scheme, will always be the ones that offered the lowest utility.
3.3 Comprehensive Minimum Expand
The problem with CBO and CGM schemes is that in peak hours, they keep allocating the maximum requested resources to certain UEs and keep denying service to all others. Comprehensive Minimum Expand (CMinExpand) solves this problem by allocating the minimum requested CPU, RAM, and hard disk space to UEs for the complete time that they requested the resources for. Later, the scheme allocates them more resources only if there is still room available at the MES after giving the minimum resources to all incoming UE requests. Thus, the scheme allocates minimum resources to all the UEs and then expands to maximum requested resources. Therefore, this scheme is called CMinExpand. In this way, CMinExpand gives service to a lot more UEs in peak hours than CBO and CGM. CMinExpand is the extended version of MinExpand algorithm [22], which considers only CPU as UE request.
CMinExpand is also greedy in nature because it follows the same principal as the CGM scheme for sorting when it is expanding the existing VMs. It allocates the minimum resources to all UEs, but then expands them due to their decreasing utility. In this manner, the more profitable VMs get expanded first. The expansion takes place until there is room on the MES. Thus, if some of the VMs do not get expanded because of the server running out of resources to allocate, they will always be the least profitable VMs. The expansion takes place until the UEs’ requested maximum resources have reached or the server runs out of resources, whichever happens first. CMinExpand is presented in Algorithm 3.
Algorithm 3: Comprehensive Minimum Expand

3.4 Comprehensive Power Minimum Expand
The disadvantage of all the above described allocation schemes is that they prioritize service provisioning to UEs regardless of any energy consumption constraints on the MES side. If the most profitable server becomes full, they turn the next server ON without setting any utility threshold for it. Comprehensive Power Minimum Expand (CPowExpand) attempts to find a balance between providing service to UEs and the energy consumption of the MES. CPowExpand is the improved version of PowExpand algorithm [22].
CPowExpand sets a certain threshold for bringing a server to ON state from idle state and employs the penalized utility function given by Eq. (23). If a server is already in the ON state, the utility is the same as before. However, if a server is in the idle state for energy saving, it subtracts a penalty term from the utility function so that the servers that are already in the ON state are prioritized over the idle server as long as there is resource available on them. As before, the difference between the PowExpand and our proposed CPowExpand is that the latter considers RAM, disk space, time, distance from the MES as part of the UE request, and the utility function for MES. CPowExpand is presented in Algorithm 4.
Algorithm 4: Comprehensive Power Minimum Expand

The disadvantage of CPowExpand is that some UEs may be denied services if the utility they offer is too small as compared to the threshold of activating an MES for them. The parameter 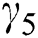 can be adjusted for a stricter or lighter emphasis on threshold.
can be adjusted for a stricter or lighter emphasis on threshold.
The implementation complexity of our improved schemes is the same as for their corresponding existing schemes because every scheme has to find the best allocation option for m UEs with n available MESs. There are nm total possible options from which an allocation scheme selects the best option in terms of energy consumption, service rate, and utility for MES. From simulation results, we can observe that our schemes select the best allocation option by consuming low energy and getting high service rate and utility.
We use MATLAB (R2019a) to evaluate the performance of the proposed comprehensive algorithms in comparison with the benchmark algorithms [22], namely, BO, GM, MinExpand, and PowExpand. The request arrival is modeled as a Poison process with mean 5. The results of the resource allocation schemes are recorded for 1000 time slots. The amount of CPU, RAM, and disk space at MES are taken as Normal distribution with mean and variance 15 and 5; 10 and 2; and 25 and 5, respectively. The energy consumption per unit time to keep an MES ON is taken proportional to the amount of resources of an MES. The coverage range of an MES is assumed to be up to 800 m. The distance between users and MES is taken as a uniform random variable with 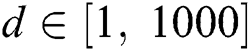 . The unit balancing coefficients
. The unit balancing coefficients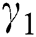 ,
, 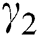 ,
, 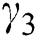 , and
, and 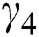 are considered as 0.4, 0.25, 0.25, and 0.1, respectively, since we assume that the expensiveness of CPU is greater than those of RAM and disk space. We also assume that the maximum distance between UE and MES is 1 km and the maximum time slots a UE can request is 10 units. The utility, service rate, and energy consumption of MESs are chosen as performance metrics. The effects of varying the UE requests, and the total number of MESs are observed.
are considered as 0.4, 0.25, 0.25, and 0.1, respectively, since we assume that the expensiveness of CPU is greater than those of RAM and disk space. We also assume that the maximum distance between UE and MES is 1 km and the maximum time slots a UE can request is 10 units. The utility, service rate, and energy consumption of MESs are chosen as performance metrics. The effects of varying the UE requests, and the total number of MESs are observed.
Fig. 2a presents a comparison of the utility for all the algorithms. The solid lines show the utility of the proposed comprehensive algorithms, whereas the dashed lines show the utility of the algorithms that only consider CPU. It is clear that the utility of the comprehensive algorithms is always higher than the benchmark algorithms because the benchmark algorithms allocate resources proportional to CPU only and face disconnections when the MES does not have enough other resources to serve the UE’s request. The comprehensive algorithms use the utility function to evaluate incoming UE’s requests and prioritize the more profitable ones, hence, generating a higher utility.
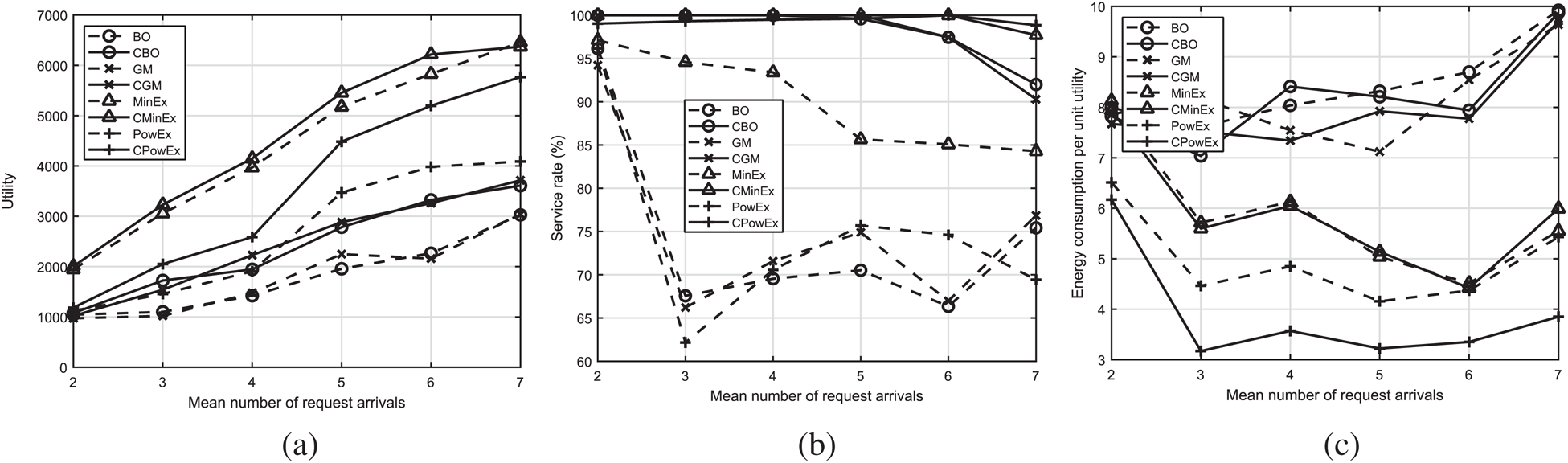
Figure 2: a) Utility under varying traffic scenarios, b) Service rate under varying traffic scenarios, c) Energy consumption per unit utility under varying traffic scenarios
Fig. 2b shows the comparison of the service rate for all the algorithms in low and high traffic. The solid lines represent the service rate of the comprehensive algorithms whereas the dashed lines show the service rate of the benchmark algorithms that only consider CPU. When very low traffic is injected, the service rates of all algorithms range from 90% to 99% because the available resources are enough to provide services to the incoming UEs. The service rates of all algorithms start decreasing when the traffic density starts increasing because the available resources are insufficient. Under very high traffic conditions, the service rate of the proposed comprehensive algorithms still remains above 90%. The benchmark algorithms face significant degradation in service rate even under medium traffic. This shows the importance of considering the heterogeneous nature of applications and the requested resources at deeper level.
Fig. 2c shows the energy consumption per unit utility for all the algorithms against different levels of incoming traffic. All the algorithms perform reasonably in low traffic conditions and their energy consumption per unit utility is quite low. However, under high traffic conditions, the algorithms that allocate the maximum requested resources to the users have a very high energy consumption per unit utility ratio. This represents that the energy consumption of non-comprehensive algorithms is very high for a relatively low level of utility, which means that for the same utility, our comprehensive algorithms will consume less energy.
4.2 Effect of Varying Total Number of Servers
In the previous subsection, we evaluated the impact of varying traffic on utility, service rate, and energy consumption of MES. In this subsection, we discuss the impact of varying the total number of servers available for the UE requests. Figs. 3a and 3b show the utility and service rate, respectively, of all the algorithms under varying number of total MESs available. When the number of servers is insufficient to serve all requests, both utility and service rate of all the algorithms is comparable. The difference in performance becomes apparent once there are enough MESs for all UE requests. For 10 MESs, we get high service rate with high utility under traffic with mean = 5 for all the algorithms. However, for more than 10 MESs, the comprehensive algorithms yield 100% service rate and high utility, whereas BO, GM, MinExpand, and PowExpand work at sub-optimal levels and achieve 60% to 90% service rate at best.
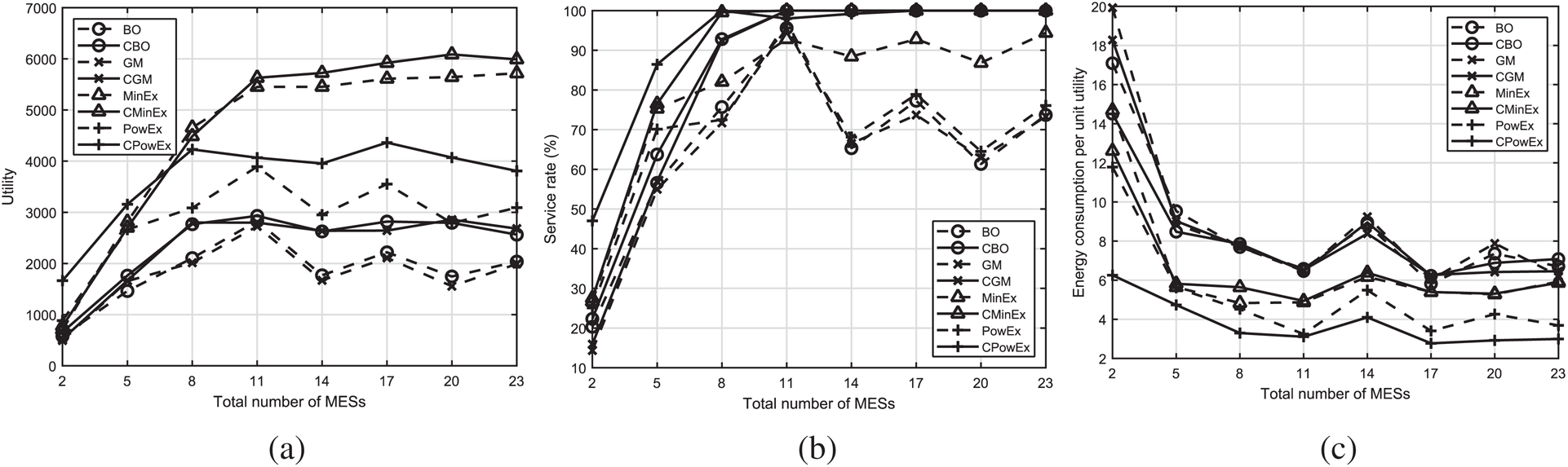
Figure 3: a) Utility under varying number of MESs, b) Service rate under varying number of MESs, c) Energy consumption per unit utility for different number of MESs
Fig. 3c shows the energy consumption per unit utility as a function of the number of servers. When the number of servers increases, the utility as well as the energy consumption of all the algorithms increases. Energy consumption per unit utility provides a meaningful measure of performance to compare different algorithms. It is clear that our comprehensive algorithms outperform the benchmark algorithms because of the higher utility of comprehensive algorithms for the same amount of energy consumption.
The simulation results show reasonable performance improvement of all the proposed comprehensive algorithms under varying traffic scenarios and varying number of MESs. The results highlight the importance of comprehensive utility function, especially when there are enough servers or low traffic, and all UE requests can be serviced. The proposed comprehensive algorithms are, in general, enough to be applied in most scenarios and the weights assigned to different resources can be adjusted according to the utility plan and applications. The performance improvements are achieved because the requested resources are considered at deeper level in our comprehensive approach. However, at present, we have not considered UE mobility and handover of UE requests from one MES to another. Therefore, as a future work, we will consider the VM migration for the mobile UEs.
For resource allocation in MEC, most literature considers CPU as the only resource that UEs can request. However, UEs can be denied services if servers run out of RAM or disk space while still having sufficient CPU resources to serve the UE’s requests. In this paper, we have presented a comprehensive utility function that considers all realistic resources needed by UEs, including CPU, RAM, storage, required time, and the distance between MES and UE. We have improved the service rate and utility of several existing MES resource allocation schemes by incorporating our comprehensive utility function. We have also minimized the energy consumption of MESs, proposed a UE request structure and modeled the utility function on the information provided by UEs. The proposed utility function is used mainly for two purposes, i.e., choosing the optimal MES, and assigning different priorities to UE requests. We achieve significant improvement in service rate and utility while maintaining a low energy consumption for MESs. The results suggest that considering the heterogeneous nature of applications and the resources at deeper level can lead to high utility and service rate for resource allocation in MEC. As a future work, we aim to consider UE mobility to further optimize resource allocation in MEC.x
Funding Statement: This work was supported by National Research Foundation of Korea-Grant funded by the Korean Government (Ministry of Science and ICT) -NRF-2020R1AB5B02002478.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. N. Abbas, Y. Zhang, A. Taherkordi and T. Skeie. (2018). “Mobile edge computing: A survey,” IEEE Internet of Things Journal, vol. 5, no. 1, pp. 450–465. [Google Scholar]
2. Y. Mao, C. You, J. Zhang, K. Huang and K. B. Letaief. (2017). “A survey on mobile edge computing: The communication perspective,” IEEE Communications Surveys & Tutorials, vol. 19, no. 4, pp. 2322–2358. [Google Scholar]
3. Y. Wei, Z. Wang, D. Guo and F. R. Yu. (2019). “Deep Q-Learning based computation offloading strategy for mobile edge computing,” Computers, Materials & Continua, vol. 59, no. 1, pp. 89–104. [Google Scholar]
4. A. Naseri and N. J. Navimipour. (2019). “A new agent-based method for QoS-aware cloud service composition using particle swarm optimization algorithm,” Journal of Ambient Intelligence and Humanized Computing, vol. 10, no. 5, pp. 1851–1864. [Google Scholar]
5. Q. Tang, R. Xie, T. Huang and Y. Liu. (2019). “Jointly caching and computation resource allocation for mobile edge networks,” IET Networks, vol. 8, no. 5, pp. 329–338. [Google Scholar]
6. Z. Ali, L. Jiao, T. Baker, G. Abbas, Z. H. Abbas et al. (2019). , “A deep learning approach for energy efficient computational offloading in mobile edge computing,” IEEE Access, vol. 7, pp. 149623–149633. [Google Scholar]
7. C. Wu, R. Buyya and K. Ramamohanarao. (2019). “Modeling cloud business customers’ utility functions,” Future Generation Computer Systems, vol. 105, pp. 737–753. [Google Scholar]
8. F. Fernandes, D. Beserra, E. D. Moreno, B. Schulze and R. C. G. Pinto. (2016). “A virtual machine scheduler based on CPU and I/O-bound features for energy aware in high performance computing clouds,” Computers & Electrical Engineering, vol. 56, pp. 854–870. [Google Scholar]
9. J. Wang, L. Zhao, J. Liu and N. Kato. (2019). “Smart resource allocation for mobile edge computing: A deep reinforcement learning approach,” IEEE Transactions on Emerging Topics in Computing, Early Access. [Google Scholar]
10. S. Vimal, M. Khari, N. Dey, R. G. Crespo and Y. H. Robinson. (2020). “Enhanced resource allocation in mobile edge computing using reinforcement learning based MOACO algorithm for IIOT,” Computer Communications, vol. 151, pp. 355–364. [Google Scholar]
11. T. Dlamini and A. F. Gambin. (2019). “Adaptive resource management for a virtualized computing platform within edge computing,” in Proc. 16th Annual IEEE Int. Conf. on Sensing, Communication, and Networking, IEEE, Boston, MA, USA, pp. 1–9. [Google Scholar]
12. C. Li, W. Chen, H. Tang, Y. Xin and Y. Luo. (2019). “Stochastic computation resource allocation for mobile edge computing powered by wireless energy transfer,” Ad Hoc Networks, vol. 93, pp. 101897. [Google Scholar]
13. B. Liu, H. Xu and X. Zhou. (2019). “Resource allocation in wireless-powered mobile edge computing systems for internet of things applications,” Electronics, vol. 8, no. 2, pp. 206. [Google Scholar]
14. T. Y. Kan, Y. Chiang and H. Y. Wei. (2018). “Task offloading and resource allocation in mobile-edge computing system,” in Proc. 27th Wireless and Optical Communication Conf., IEEE, Hualien, Taiwan, pp. 1–4. [Google Scholar]
15. M. K. Gupta and T. Amgoth. (2018). “Resource-aware virtual machine placement algorithm for IaaS cloud,” Journal of Supercomputing, vol. 74, no. 1, pp. 122–140. [Google Scholar]
16. R. Shaw, E. Howley and E. Barrett. (2019). “An energy efficient anti-correlated virtual machine placement algorithm using resource usage predictions,” Simulation Modelling Practice and Theory, vol. 93, pp. 322–342. [Google Scholar]
17. J. Plachy, Z. Becvar and E. C. Strinati. (2016). “Dynamic resource allocation exploiting mobility prediction in mobile edge computing,” in Proc. 27th Annual Int. Sym. on Personal, Indoor, and Mobile Radio Communications, IEEE, Valencia, Spain, pp. 1–6. [Google Scholar]
18. C. F. Liu, M. Bennis and H. V. Poor. (2017). “Latency and reliability-aware task offloading and resource allocation for mobile edge computing,” in Proc. IEEE GLOBECOM Workshops, IEEE, Singapore, pp. 1–7. [Google Scholar]
19. A. Al-Shuwaili and O. Simeone. (2017). “Energy-efficient resource allocation for mobile edge computing-based augmented reality applications,” IEEE Wireless Communications Letters, vol. 6, no. 3, pp. 398–401. [Google Scholar]
20. R. Wang, J. Yan, D. Wu, H. Wang and Q. Yang. (2018). “Knowledge-centric edge computing based on virtualized D2D communication systems,” IEEE Communications Magazine, vol. 56, no. 5, pp. 32–38. [Google Scholar]
21. D. Minarolli and B. Freisleben. (2011). “Utility-based resource allocation for virtual machines in cloud computing,” in Proc. IEEE sym. on Computers and Communications, IEEE, Kerkyra, Greece, pp. 410–417. [Google Scholar]
22. M. Cardosa, M. R. Korupolu and A. Singh. (2009). “Shares and utilities based power consolidation in virtualized server environments,” in Proc. IFIP/IEEE Int. Sym. on Integrated Network Management, IEEE, Long Island, NY, USA, pp. 327–334. [Google Scholar]
23. X. Zhang, J. Lu and X. Qin. (2013). “BFEPM: Best fit energy prediction modeling based on CPU utilization,” in Proc. IEEE Eighth Int. Conf. on Networking, Architecture and Storage, IEEE, Xi'an, China, pp. 41–49. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |