DOI:10.32604/cmc.2020.012379

| Computers, Materials & Continua DOI:10.32604/cmc.2020.012379 |  |
| Article |
Memetic Optimization with Cryptographic Encryption for Secure Medical Data Transmission in IoT-Based Distributed Systems
1Faculty of Computing, Botho University, Gaborone, Botswana
2Department of Computer Science, Gaborone University College of Law and Professional Studies, Gaborone, Botswana
3Vels Institute of Science, Technology & Advanced Studies, Chennai, 600117, India
4Global Institute of Management and Technology, West Bengal, 741102, India
5Faculty of Computer Science and Multimedia, Lincoln University College, Kelantan, 15050, Malaysia
6Center for Visualization & Simulation, Duy Tan University, Da Nang, 550000, Vietnam
7Faculty of Information Technology, Haiphong University, Haiphong, 180000, Vietnam
*Corresponding Author: Chung Le Van. Email: levanchung@duytan.edu.vn
Received: 23 June 2020; Accepted: 04 September 2020
Abstract: In the healthcare system, the Internet of Things (IoT) based distributed systems play a vital role in transferring the medical-related documents and information among the organizations to reduce the replication in medical tests. This datum is sensitive, and hence security is a must in transforming the sensational contents. In this paper, an Evolutionary Algorithm, namely the Memetic Algorithm is used for encrypting the text messages. The encrypted information is then inserted into the medical images using Discrete Wavelet Transform 1 level and 2 levels. The reverse method of the Memetic Algorithm is implemented when extracting a hidden message from the encoded letter. To show its precision, equivalent to five RGB images and five Grayscale images are used to test the proposed algorithm. The results of the proposed algorithm were analyzed using statistical methods, and the proposed algorithm showed the importance of data transfer in healthcare systems in a stable environment. In the future, to embed the privacy-preserving of medical data, it can be extended with blockchain technology.
Keywords: Internet of Things; medical images; cryptography; memetic algorithm; steganography
In the recent decade, IoT acts as a backbone for the completely connected sensor devices for achieving integrated communication environments and their respective platforms both in terms of virtual as well as in real-world altogether [1] in terms of distributed systems. Recently, an organization called Health Information Exchange (HIE) Has implemented medical data transfer to speed up care of patients. The medical data has now become a regular event of everyday life across all hospitals. When it comes to the word internet, then the next word comes in the mind of people is security. Security is one of the major concerns when the internet comes into the picture. Though HTTPs is there in the scenarios for security still it is in an open debate. Therefore, it is essential to build a secure method to transmit medical data in the IoT environment [2–5]. Addressing this is possible with the integration of steganographic techniques as well as the encryption and decryption algorithms [6–13].
Another cryptographic word is Data Encryption [14]. Encryption in cryptography is the technique where the data is converted into the unreadable message so that the intruders access it. In contrast, the authorized persons with proper keys can be able to make it. Identifying the key for such a process is an NP-hard problem since the combination of numbers goes exponentially as the length of the key increases linearly. For addressing NP-Hard problems, bio-inspired algorithms play a vital role in recent times [15–17]. Memetic Algorithm is one such bio-inspired algorithm improved from the Genetic Algorithm, which is inspired by the reproductive system of living beings. The Memetic Algorithm is used for this research work to provide an effective method for the encryption of medical images to provide a useful model for the transmission of text messages. The memetic algorithm is an improved variant of the former Genetic algorithm introduced with the evolution of the human method of reproduction. The model encompasses the crossover models and mutation models for the better evolution of upcoming generations. The memetic algorithm improvises every gene of a chromosome (solutions/individuals) for its betterment of success rate towards the optimal solution. The applications of bio-inspired optimization models can be found in [18–35].
The idea of steganography is to hide the data and securely transfer the information by hiding the information within the image to avoid the intruder interception. The Discrete Wavelet Transform is the key point with phenomenal spatial localization, with multi-resolution characteristics and frequently spread. DWT is the one that almost matches the forms of the visual system of humans [36–40]. The importance of steganography is to prevent and remove suspicious hidden information by the intruder. The text messages are sensitive issues which should convey in a way that is difficult to detect. Steganography applies to two things, namely steganography capability and imperceptibility. Balancing these two terms in steganography is hard as increasing the capacity while maintaining imperceptibility.
This research aims to enhance the security model for the transmission of medical data using the Memetic Algorithm. The major contributions of this work are as follows:
1. We developed an adaptive bio-inspired model for Encryption on medical data for secure transmission in IoT.
2. A DWT based Steganographic procedure has imposed to improve the mode of security.
3. An intuitive bio-inspired model developed to decrypt the encrypted data using the memetic algorithm.
4. An extensive implicated towards experimentation procedure to prove the significance of the proposed model using recent datasets (Example, DME Eyes Dataset and DICOM dataset).
The further sections of the paper organized into various sections. The literature review on securing the model for the transmission of medical data discussed in Section 2. Section 3 explains the Memetic Algorithm; the proposed model for encryption of sensitive information explained in Section 4. Section 5 deals with the experimental evaluation that includes the setup of simulations, experimental results and analysis, and the final section concludes the paper and suggests further research work.
In 2018, Razzaq et al. [2] composed a detailed survey on the security issues concern in IoT. Security controls on different issues such as authentication, confidentiality, are discussed in detail. In 2016, Bairagi et al. [3] presented a model namely 3 coloured image steganography techniques to provide security for efficient data transmission in IoT networks. Among the three techniques, the first and third technique makes use of red, blue and green channels to offer heightened security while the second technique takes green and blue. In 2015, Anwer et al. [4] proposed a technique and tested the model with a medical image data set to secure the images from the intruder. AES encryption algorithm was used in the generic technique to encrypt the medical images. However, the proposed model helped to achieve security in terms of integrity, authorization, and availability. In the year 2018, a detailed mobile app vulnerable on medical stream has been published, which detailed the various vulnerabilities and risk factors in the stream [5].
Razzaq et al. [6] proposed a fusion for achieving security using encryption, steganography, and watermarking methods. The proposed methodology consists of XOR operator for cover image encryption, Least Significant Bits for embedding encrypted data into the cover image, and watermarking using spatial and frequency domains. In the year 2016, Choudary et al. [8] used a decision tree model for encryption of text data of a patient inside the medical image of the respective patient. They used the steganographic technique to achieve data hiding. BFS and RSA algorithms are used for embedding the text inside the image. Zaw et al. [10] proposed a methodology for efficient transfer of medical data after being encrypted using the proposed algorithm. According to the proposed method, the given image can be divided into the standard number of blocks each about the same size. The blocks arranged for proceeding with a transformation algorithm. After the transformation process, each block encrypted using Blowfish Algorithm. Form the result analysis, and it is evident that that proposed algorithm reduces the correlation when the entropy increases. Sreekutty et al. [19] improved the security in medical image transformation using medical integrity verification system. The system consists of two-stage processes to protect and verify secret messages to achieve confidentiality and Integrity. Bashir et al. [27] proposed a new concept for encrypting medical images using AES and the shift image block integration.
In this method, the shifting algorithm used to divide the image into the number of blocks. Shifting technique is used to shuffle image rows and columns, so that shifted content defers from the original content. Muhammed et al. [28] proposed a secure method to address the RGB images via Gray Level Modification (GLM) and Multi-Level Encryption (MLE). In recent years bio-inspired methods are also used for image encryption and cryptography theory which can be found in [30,31]. Some of the other recent algorithms in bio-inspired computing applied in [18–20]. Prabu et al. worked on multi-discipline in the image processing stream, which includes cryptography technique and watermarking techniques [32–34]. Pal et al. [35] have discussed resource allocation algorithms in cloud-based distributed systems and also VM utilization, which will help the researchers to comprehend the procedure of implementing the cryptographic algorithm in IoT based distributed systems.
From the literature, it is evident that there is a need to enhance the security model for transmission of medical data and hence Memetic Algorithm can be used for effective encryption mechanisms of medical images for efficient data transmission model of text messages.
A Memetic Algorithm is a population-based metaheuristic algorithm that includes the standard evolutionary model as well as the local heuristic method for optimal convergence towards the optimal solution. Memetic Algorithm addresses an optimization problem with a specific procedure which is described in the following session iteratively. It aims to find the optimal solution for a problem that forms a pool of solutions called population. There are four summative methods which are defined as follows:
1. Parent Selection: The parents selected in each iteration which intends to participate in further iterations for generation quality offspring. The parents selected for the reproduction process, which generates new offspring with high quality of solutions. The high quality is indicated by the fitness of the solution. Fitness of a solution is considered as the objective function of the problem which has two modes: maximization and minimization.
2. Combination of Parents: combining two different parents to generate new offspring will lead to the generation of new solutions with better quality. Better solutions get emerged by the fusion of two quality parents.
3. Offspring Improvement Procedure: Offspring improvement deals with the heuristic procedure, which improves the quality of the offspring to the maximum extent it can be. The choice of heuristic function is highly dependent on the problem.
4. Population Update: At this point, a decision promoted on whether to engage or substitute the solution in the next generation. The decision process builts on the quality of the solution and diversity. There are two basic update rules in MA. The quality-based rule replaces the worst solution, and the diversity-based rule replaces the solution, which is like each other.
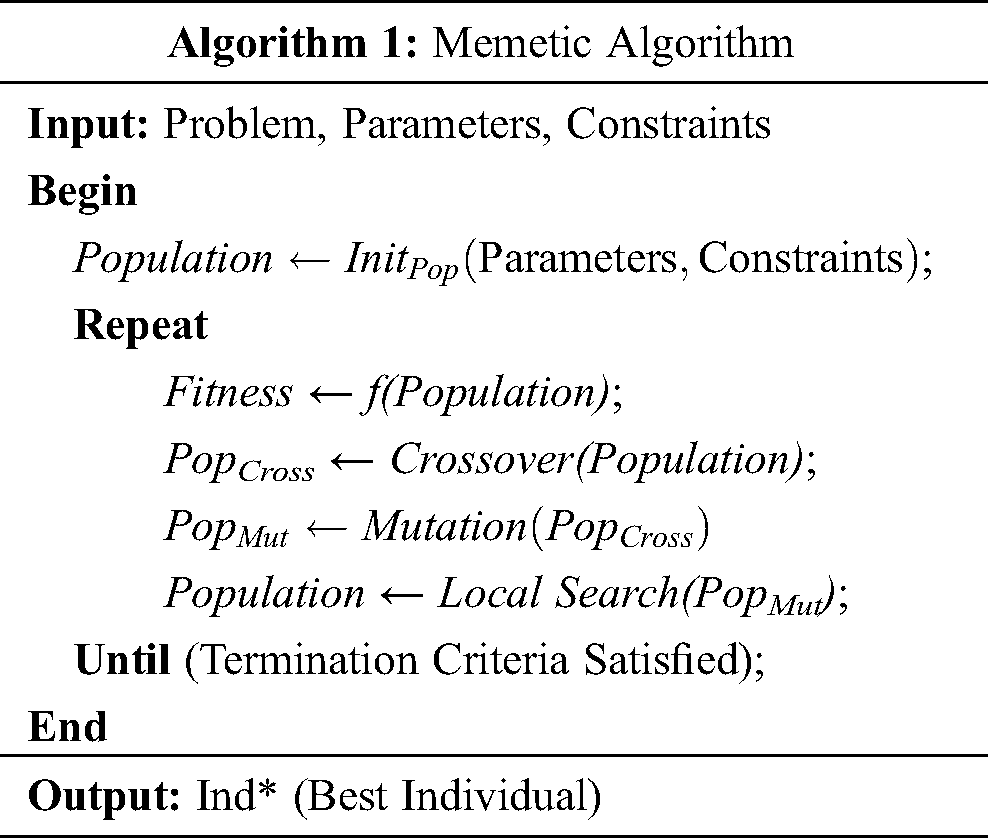
4 Memetic Algorithm on Secure Medical Data Transmission
In this section, a detailed model of a secure data transmission model for communicating medical images along with hidden text messages using the Memetic Algorithm. The proposed scheme consists of four subsections for effective, secure data transmission:
(1) Sensitive information is encrypted using Memetic Algorithm.
(2) The encrypted information is embedded or hidden in the patient’s medical image using DWT and generated a steganographic image.
(3) the information extracted from the hidden image and
(4) The extracted data decrypted to get the original information. A detailed explanation of each phase given below.
4.1 Information Encryption Using Memetic Algorithm
The memetic algorithm used to address problems with NP-Hard, where the search space is unbounded and has several constraints. For this data encryption, the information encrypted to indicate this is due to intruders or hackers. AES and RSA algorithms used to encrypt the data. However, when the brute force attack applied to it, it can be easily decrypted. Hence the choice of the Memetic Algorithm through its combination with the generation of Pseudorandom numbers can be a better choice. Hence the choice of Pseudorandom number generation is applied as a local search in the memetic algorithm. In this section, the generation of the pseudorandom numbers and the image encryption method explained in detail.
4.2 Pseudorandom Number Generation
Pseudorandom numbers used to generate a random number technically. This method makes multiplicative congruential generator also called a power residue generator. The generation of the pseudorandom number is as follows:
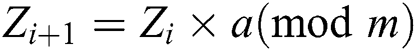
where m is a positive integer and a is a constant; Z represents the pseudorandom number. The equation means that the value of the pseudorandom number in the last iteration i will have a constant multiplication factor with a and the result divided by m. Choosing m and a have a set of rules which are defined as follows:
1. The random number generated should be less than, or equal to, m. Hence, random number collection does not exceed 2147383648. M should be picked wide enough.
2. Choosing 'a' is a prime number to m. Thus, choosing 'a' may be an odd number with a 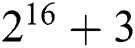 limit.
limit.
4.3 Memetic Algorithm On Data Encryption
The encryption schema depicts in the form of Algorithm 6.
4.4 Steganography Procedure Using DWT
Discrete Wavelet forms used to sample the signals discretely. For an input represented by a list of 2n numbers, the Haar wavelet transforms considered to pair up input values, storing the difference, and passing the sum. This process repeated recursively, pairing up the sums to prove the next scale, which leads to 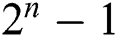 difference and a final sum. Haar-DWT imposed for embedding the encrypted text into the medical image. Both Haar-DWT and 2D-DWT-2L uses a constructive transformation. Constructive transformation uses high and low pass filters.
difference and a final sum. Haar-DWT imposed for embedding the encrypted text into the medical image. Both Haar-DWT and 2D-DWT-2L uses a constructive transformation. Constructive transformation uses high and low pass filters.
Fig. 1 shows the process of Steganography of the image where it shows the process of decomposition of image C with dimensions  . They subdivided into four sub compounds, namely HH, HL, LH, and LL frequency bands.
. They subdivided into four sub compounds, namely HH, HL, LH, and LL frequency bands.
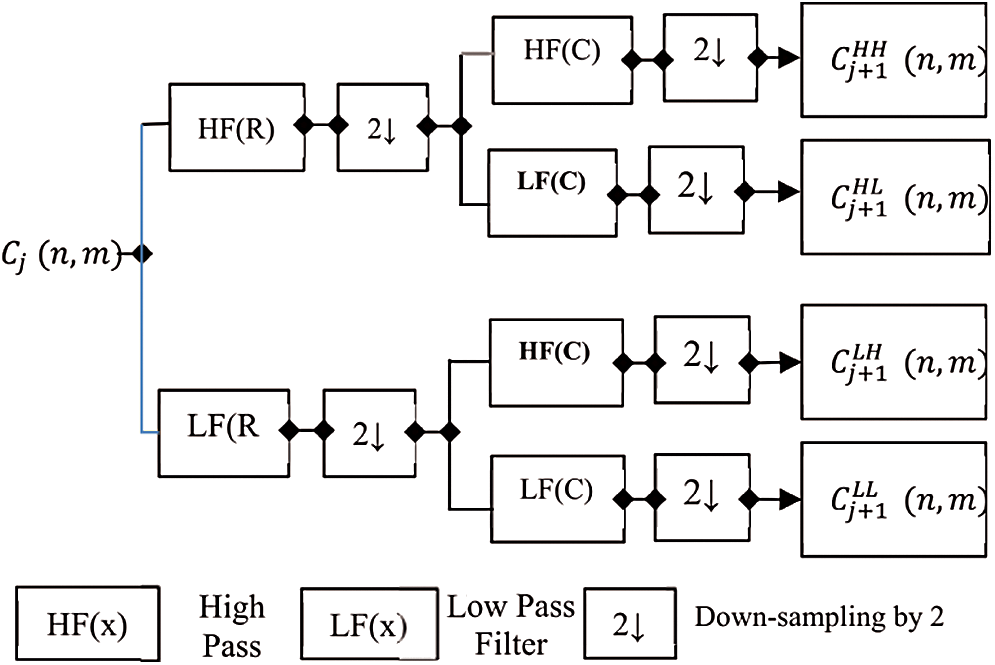
Figure 1: Decomposition process of DWT-2L
After the successful embedding process of encrypted text to the image, the image transmits through any wired or wireless channel to the destined user. Extraction of encrypted text from the image has to be taken care of in the receiver hand. For that purpose, 2D-DWT-2L will be used to extract the encrypted information from the image file. When out of the picture, the encrypted text removed then, the cover image reconstructed using IDWT2 for both the second and first stages. Fig. 2 provides a detailed explanation of the operation.
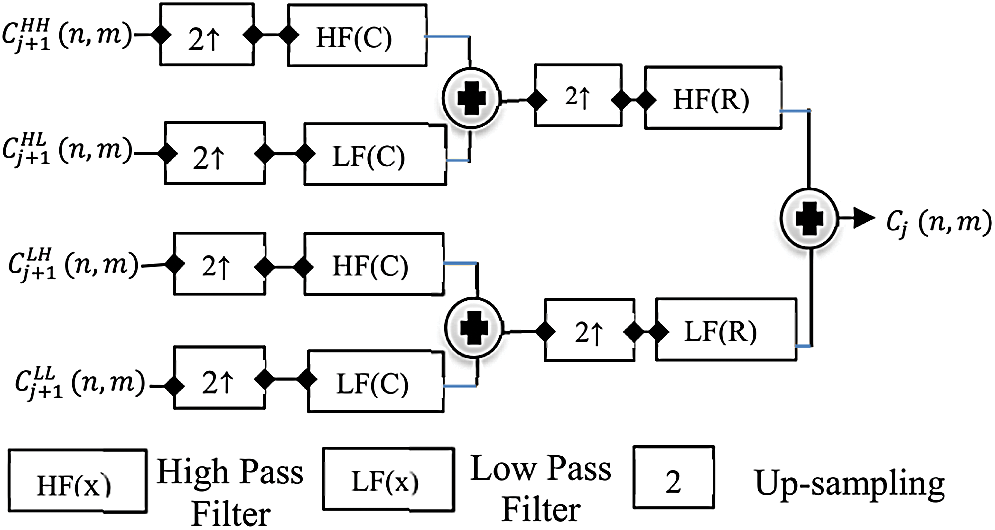
Figure 2: Synthesis process of DWT-2L
4.5 The Decryption of Confidential Information
This process refers to converting an encrypted message to its original form of text. The reverse technique applied to the encryption method. The key the sender uses to decrypt the encrypted message must be used by the recipient.
5 Experimental Evaluation and Results Analysis
In MATLAB version 9.1, the proposed algorithm implemented with the machine equipped with the Intel Core i7 CPU, 8 GB RAM, and 2 TB HDD, Windows 10 OS. We used sufficient statistical tests to illustrate the importance of the proposed algorithm: Peak Signal to Noise Ratio (PSNR), Correlation, Structural Content (SC), Structural Similarity (SSIM), and Mean Square Error (MSE).
Peak Signal to Noise Ratio (PSNR): It computes the imperceptibility of the steganographic image [19]. When the PSNR is high, then it states that the steganographic image has a higher quality. PSNR calculated as
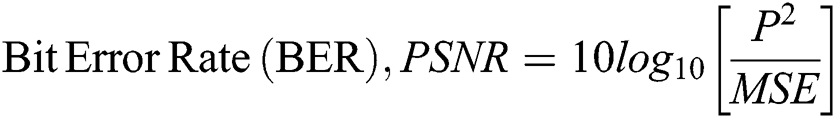
where P denotes the maximum pixel value in an image.
Mean Square Error (MSE): This measures the error value in terms of an average magnitude error between the original and steganographic images [20]. Mathematically represented as
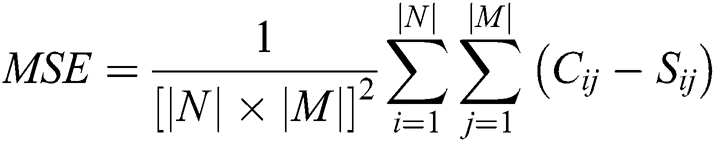
where 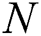 and
and 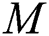 represent the rows and columns of the image and
represent the rows and columns of the image and 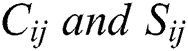 represents the strength respectively of each pixel of the cover and the steganographic image.
represents the strength respectively of each pixel of the cover and the steganographic image.
Bit Error Rate (BER): It calculates the deviation of the bits that transformed due to the attenuation noise or any other noise [21]. It calculated as
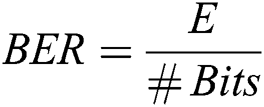
where  denotes the errors.
denotes the errors.
Structural Similarity (SSIM): It measures the similarity in terms of their structure between the cover and steganographic image [22]. It can be calculated as
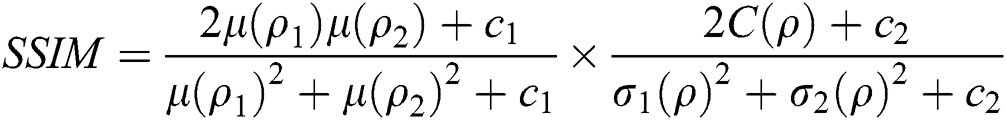
where 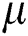 represents the mean and
represents the mean and  represent the standard deviation.
represent the standard deviation.
Structural Content (SC): It measures the similarity between the cover and the steganographic image [23]. Further calculated as
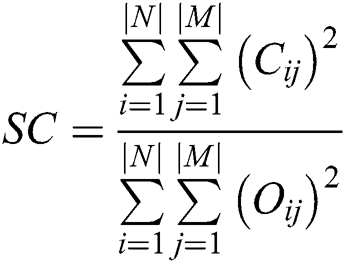
where 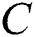 represents the cover image, and
represents the cover image, and  represents the original image.
represents the original image.
Correlation: This determines the similarity and disparity between the magnitude and the data step [24]. Further calculated as
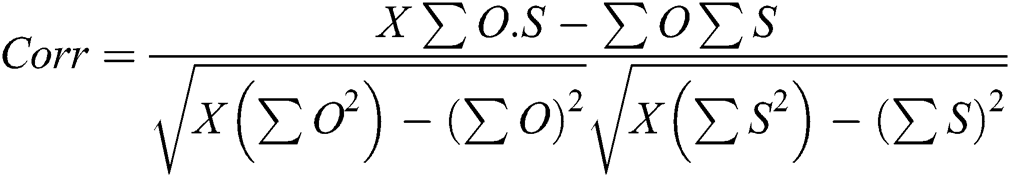
where 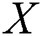 denotes the pairs in the information,
denotes the pairs in the information,  is the original image, and
is the original image, and 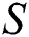 is the steganographic image. In Fig. 3. different color and grey images used for evaluation purpose.
is the steganographic image. In Fig. 3. different color and grey images used for evaluation purpose.
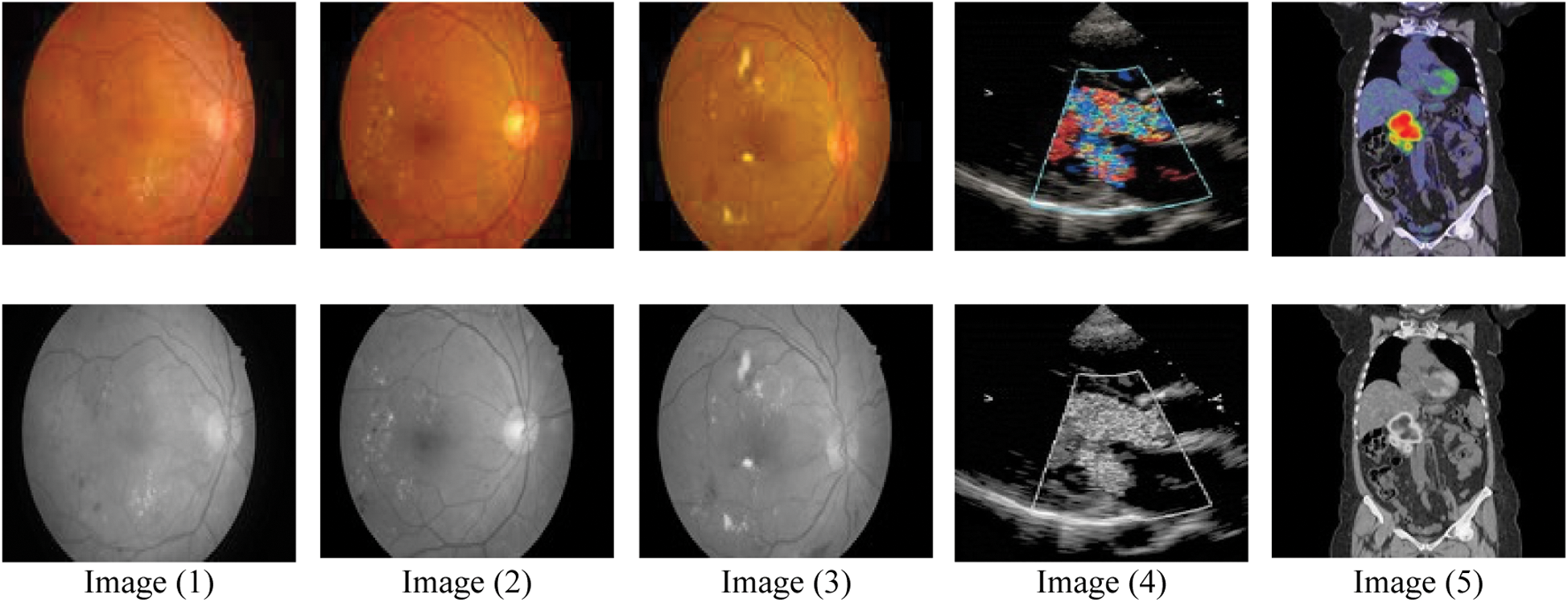
Figure 3: Color and gray images used for evaluation
The study of the steganographic image performs over the original image. The proposed Memetic Algorithm tested with various text sizes, and the hidden images are all images of color and white. The text messages analyzed before and during the encryption and decryption process. This study will prove that a lesser number of distortions occur before and after embedding the hidden message in the picture. The output of the proposed algorithm evaluated through two separate datasets. DME Eyes Dataset [25] and DICOM dataset [26].
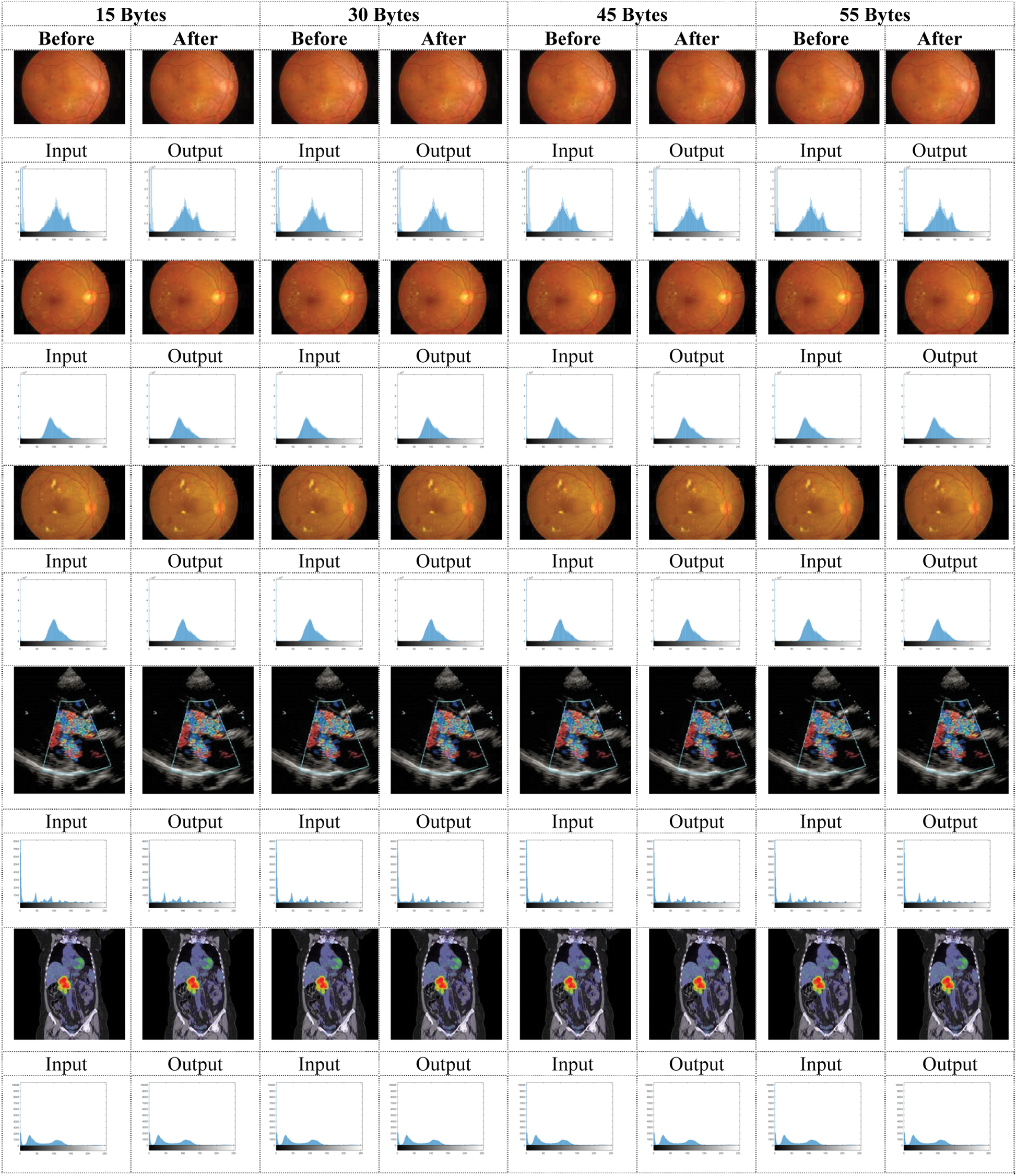
Figure 4: Histogram of the color images before and after applying memetic algorithm with text sizes (15, 30, 45, 55 Bytes)
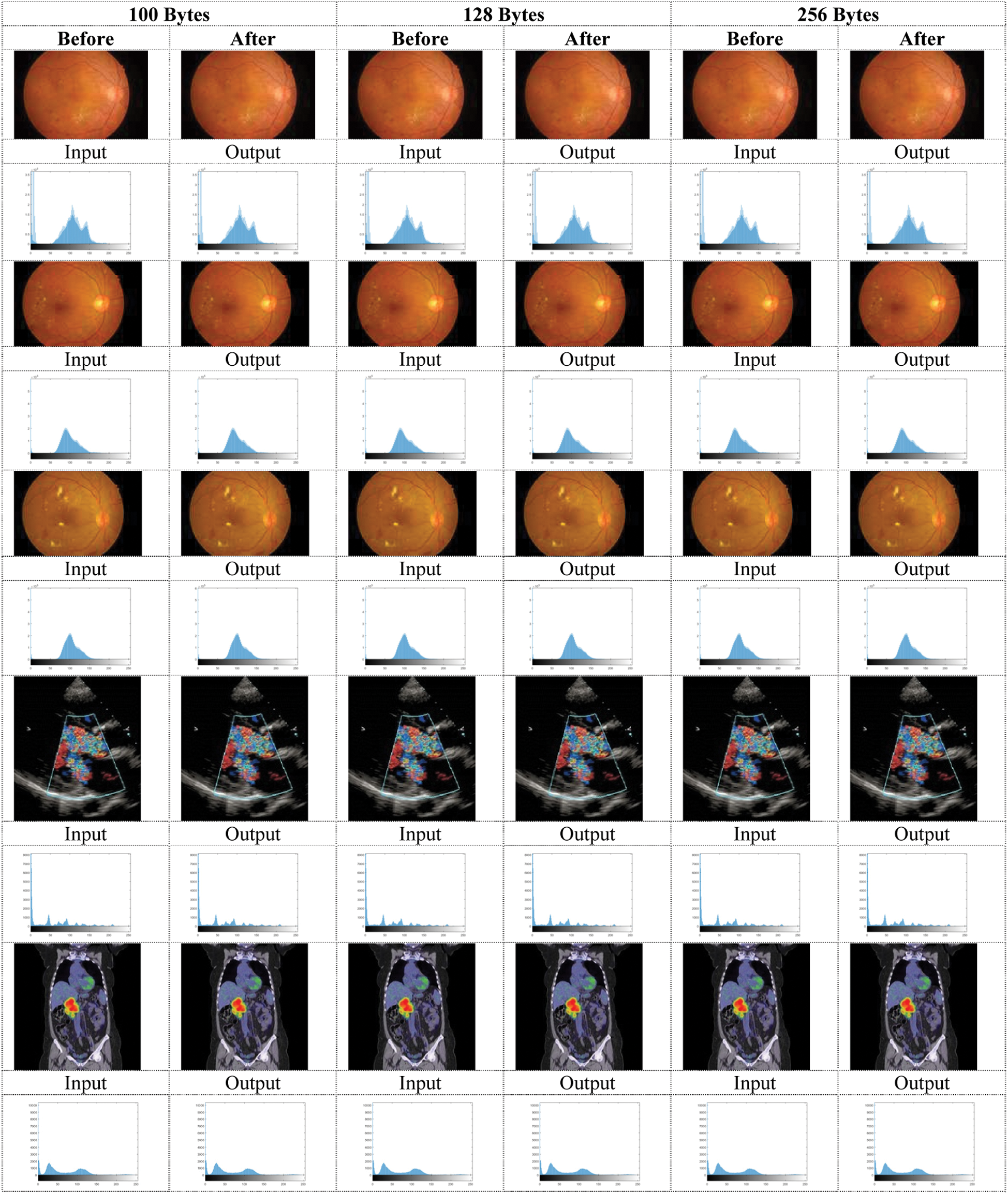
Figure 5: Histogram of the color images before and after applying a memetic algorithm with text sizes (100, 128, 256 Bytes)
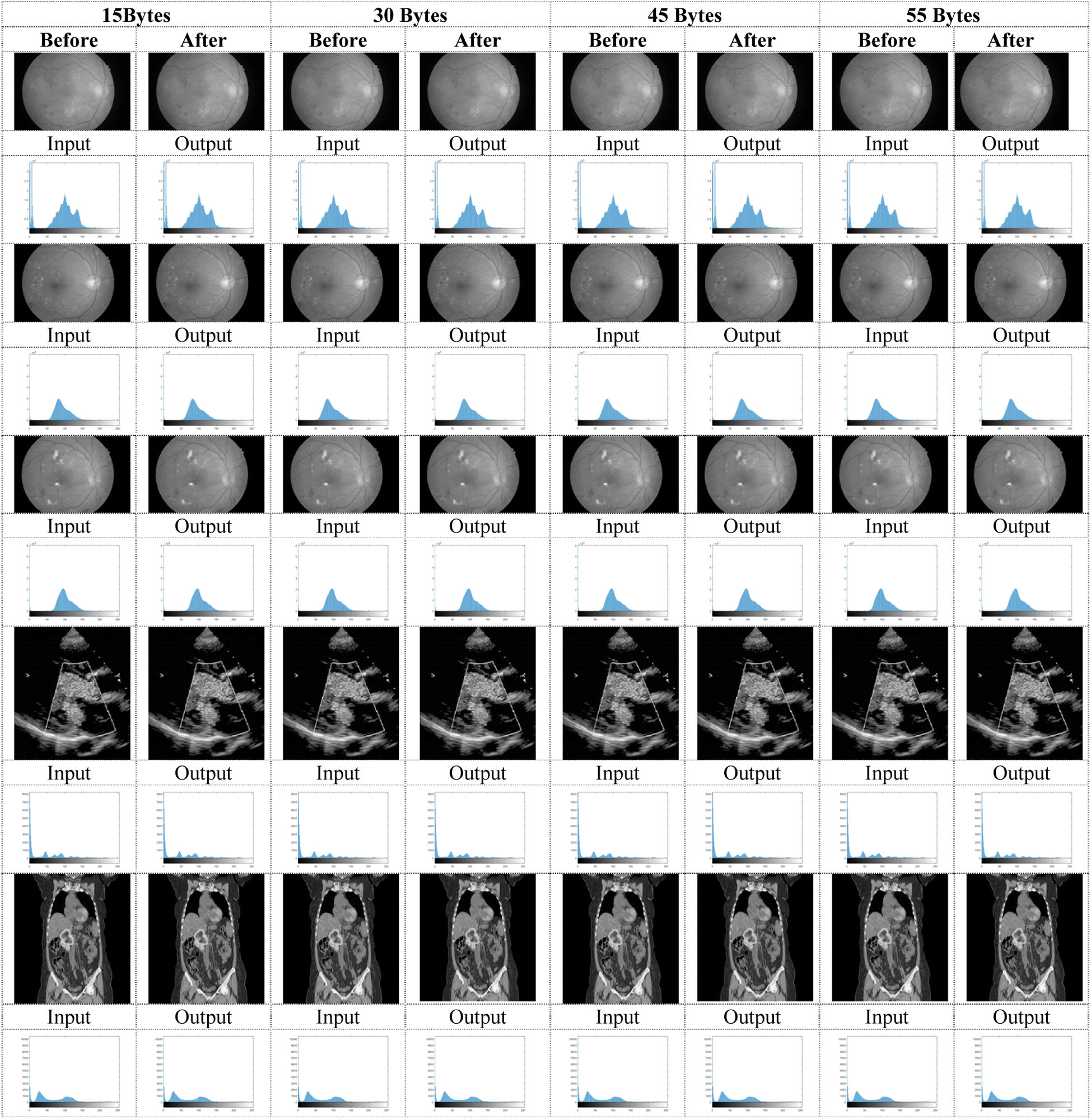
Figure 6: Histogram of the gray images before and after applying a memetic algorithm with text sizes (15, 30, 45, 55 Bytes)
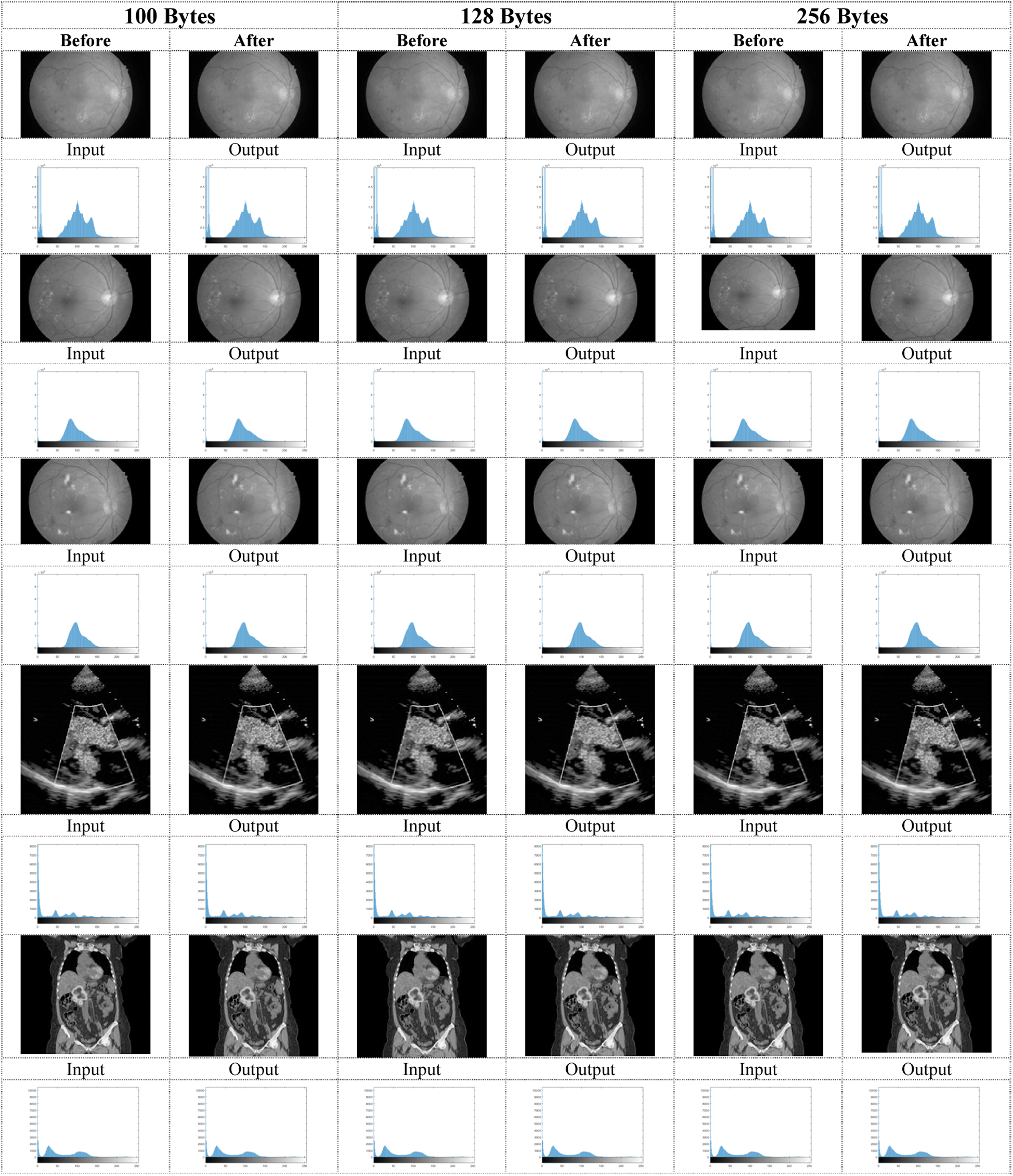
Figure 7: Histogram of the gray images before and after applying a memetic algorithm with text sizes (100, 128, 256 Bytes)
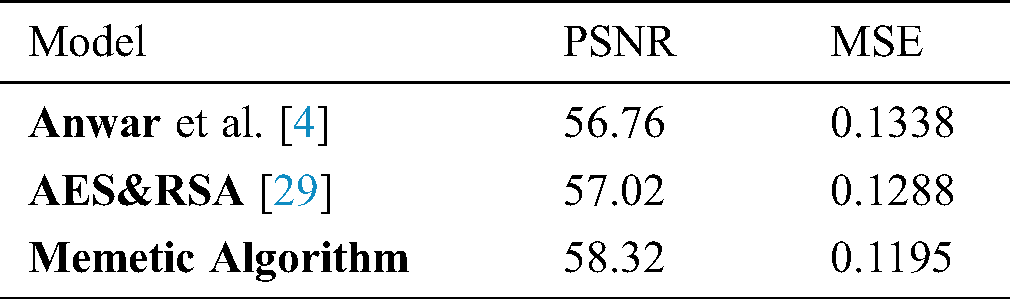
For Colored images comparing the experimental results from Tab. 1. infers that as the packet size increases, the PSNR value decreases in DWT 2L and DWT 1L. On comparing the results between high packet and small packet sizes on Image 1, DWT 2L shows the improvement of 9.51% and DWT 1L with 22.75%. For Gray images on comparing the experimental results from Tab. 2. it can be inferred that as the packet size increases, the PSNR value decreases in DWT 2L and DWT 1L. On comparing the results between high packet and small packet sizes on Image 1, DWT 2L shows the improvement of 8.41% and DWT 1L with 21.70%. From Tabs. 3 and 4. it is evident that the proposed method achieves better PSNR value with less MSE when compared with the other algorithms in the existing approaches.
Table 1: Peak signal to noise ratio and mean square error for colored images
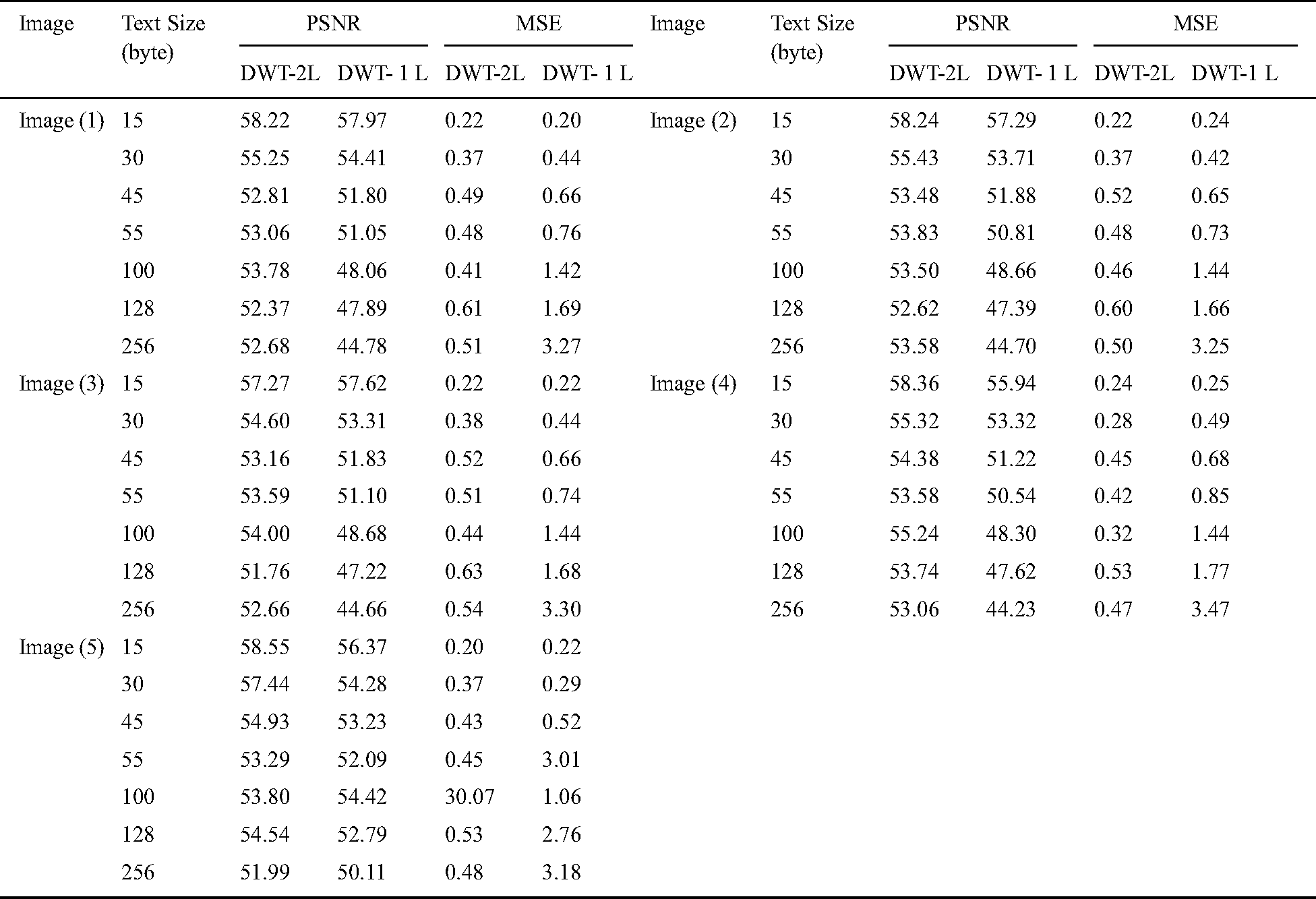
Table 2: Peak signal to noise ratio and mean square error for gray scale images
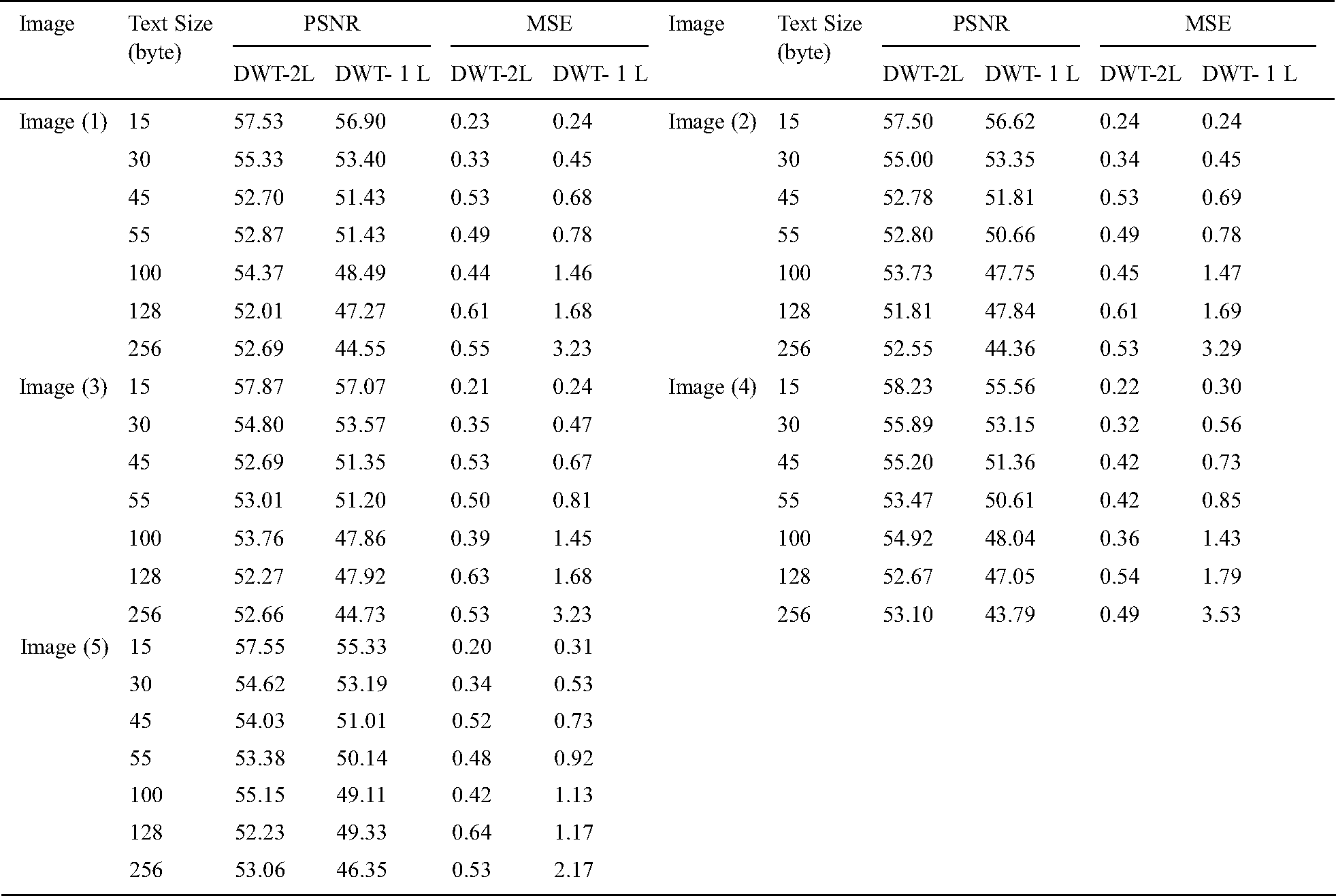
Table 3: Bit error rate, structure similarity, structural content, and correlation of color images
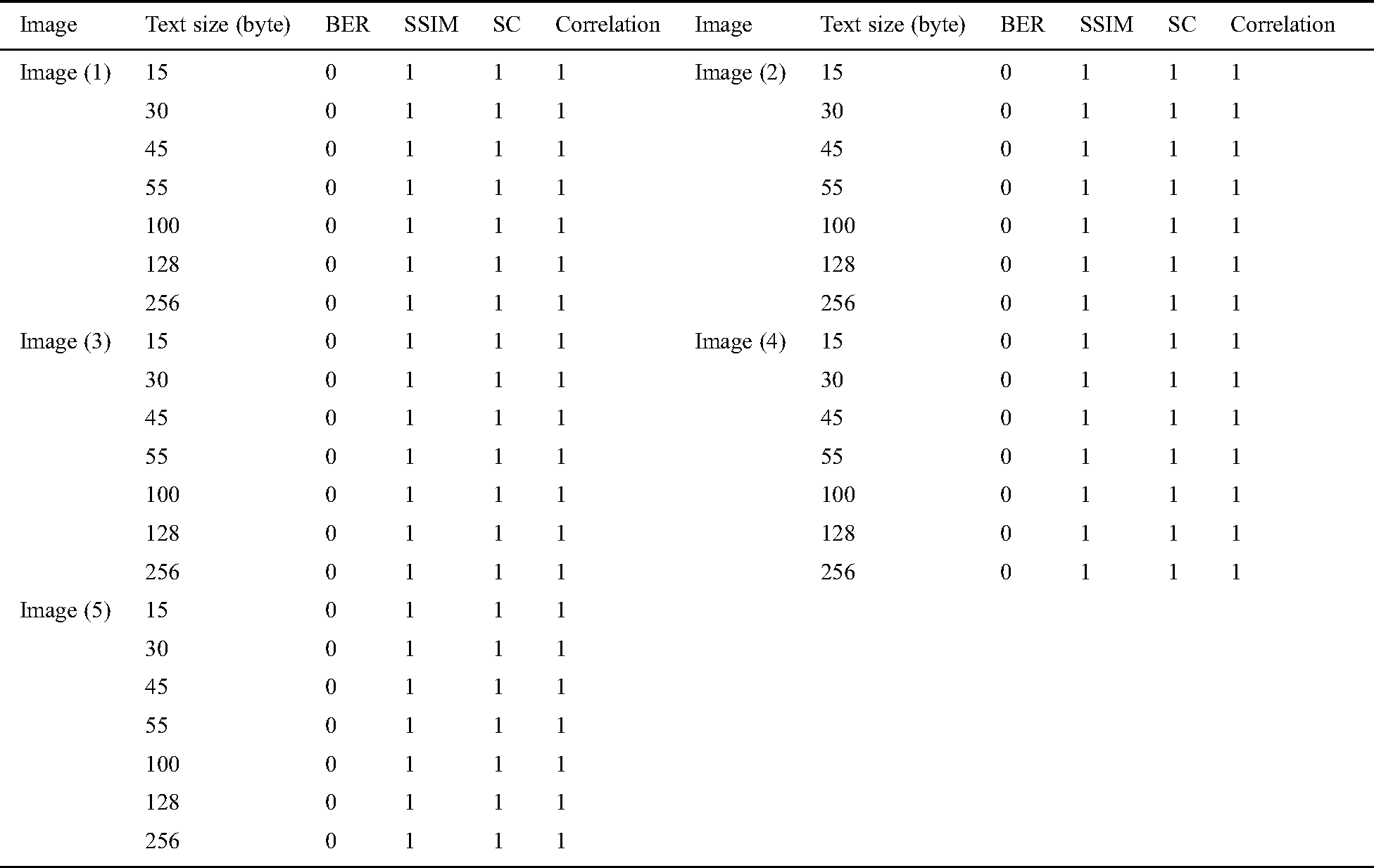
Table 4: Comparison table of PSNR and MSE values between Memetic and existing approaches
In this paper, the Evolutionary algorithm, namely the Memetic Algorithm, is used for the secure transmission of medical images using encryption and Steganography. The results of the proposed algorithm evaluated using the performance metrics such as PSNR, MSE, SSIM, Correlation, SC, and BER. The results show the significance of the proposed algorithm over the existing methodologies. On comparing the histogram of the covered and original messages both in color and grayscale images, there is not much deviation in PSNR values which states that the proposed algorithm performs better in encryption and decryption procedure. Thus, the security concerns in healthcare systems via IoT are highly secure and confidential. The future work of this proposed method is to reduce the computational time of the encryption process.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. A. Darwish, A. E. Hassanien, M. Elhoseny, A. K. Sangaiah and K. Muhammad. (2019). “The impact of the hybrid platform of internet of things and cloud computing on healthcare systems: Opportunities, challenges, and open problems,” Journal of Ambient Intelligence and Humanized Computing, vol. 10, no. 10, pp. 4151–4166. [Google Scholar]
2. A. Shehab, M. Elhoseny, K. Muhammad, A. K. Sangaiah, P. Yang et al. (2018). , “Secure and robust fragile watermarking scheme for medical images,” IEEE Access, vol. 6, pp. 10269–10278. [Google Scholar]
3. A. K. Bairagi, R. Khondoker and R. Islam. (2016). “An efficient steganographic approach for protecting communication in the Internet of Things (IoT) critical infrastructures,” Information Security Journal: A Global Perspective, vol. 25, no. 4, pp. 197–212. [Google Scholar]
4. A. S. Anwar, K. K. A. Ghany and H. E. Mahdy. (2015). “Improving the security of images transmission,” International Journal of Bio-Medical Informatics and e-Health, vol. 3, no. 4, pp. 7–13. [Google Scholar]
5. A. Abdelaziz, M. Elhoseny, A. S. Salama and A. M. Riad. (2018). “A machine learning model for improving healthcare services on cloud computing environment,” Measurement, vol. 119, pp. 117–128. [Google Scholar]
6. M. A. Razzaq, R. A. Sheikh, A. Baig and A. Ahmad. (2017). “Digital image security: fusion of encryption, steganography and watermarking,” International Journal of Advanced Computer Science and Applications, vol. 8, no. 5, pp. 224–228. [Google Scholar]
7. N. Dey and V. Santhi. (2017). “Intelligent techniques in signal processing for multimedia security,” Studies in Computational Intelligence, vol. 660, Springer. [Google Scholar]
8. M. Jain, R. C. Choudhary and A. Kumar. (2016). “Secure medical image steganography with RSA cryptography using decision tree, ” in Contemporary Computing and Informatics (IC3I), pp. 291–295. [Google Scholar]
9. L. Yehia, A. Khedr and A. Darwish. (2015). “Hybrid security techniques for internet of things healthcare applications,” Advances in Internet of Things, vol. 5, no. 3, pp. 21–25. [Google Scholar]
10. Z. M. Zaw and S. W. Phyo. (2015). “Security enhancement system based on the integration of cryptography and steganography,” International Journal of Computer, vol. 19, no. 1, pp. 26–39. [Google Scholar]
11. R. K. Gupta and P. Singh. (2013). “A new way to design and implementation of hybrid crypto system for security of the information in public network,” International Journal of Emerging Technology and Advanced Engineering, vol. 3, no. 8, pp. 108–115. [Google Scholar]
12. S. A. Laskar and K. Hemachandran. (2012). “High capacity data hiding using LSB steganography and encryption,” International Journal of Database Management Systems, vol. 4, no. 6, pp. pp.–57. [Google Scholar]
13. L. Yu, Z. Wang and W. Wang. (2012). “The application of hybrid encryption algorithm in software security,” in IEEE Int. Conf. on Computational Intelligence and Communication Networks, Phuket, Thailand, pp. 762–765. [Google Scholar]
14. S. F. Mare, M. Vladutiu and L. Prodan. (2011). “Secret data communication system using steganography, AES and RSA,” in IEEE 17th Int. Sym. for Design and Technology in Electronic Packaging, Timisoara, Romania, pp. 339–344. [Google Scholar]
15. K. Thirugnanasambandam, S. Prakash, V. Subramanian, S. Pothula and V. Thirumal. (2019). “Reinforced cuckoo search algorithm-based multimodal optimization,” Applied Intelligence, vol. 1, no. 25, pp. 2059–2083. [Google Scholar]
16. K. Thirugnanasambandam, J. Amudhavel and S. Pothula. (2017). “Oppositional cuckoo search for solving economic power dispatch,” Inst of Integrative Omies and Applied Biotechnology Journal, vol. 8, no. 2, pp. 199–207. [Google Scholar]
17. T. Kalaipriyan, J. Amudhavel and S. Pothula. (2018). “Solving virtual machine placement in cloud data centre based on novel firefly algorithm,” Bioscience Biotechnology Research Communication, vol. 11, no. 1, pp. 48–53. [Google Scholar]
18. A. Alharbi and M. T. Kechadi. (2017). “A steganography technique for images based on wavelet transform,” in Int. Conf. on Future Data and Security Engineering, Ho Chi Minh, Vietnam, pp. 273–281. [Google Scholar]
19. M. S. Sreekutty and P. S. Baiju. (2017). “Security enhancement in image steganography for medical integrity verification system,” in Int. Conf. on Circuit, Power and Computing Technologies, Kollam, India, pp. 1–5. [Google Scholar]
20. F. A. Jassim. (2013). “A novel steganography algorithm for hiding text in image using five modulus method.” arXiv preprint. [Google Scholar]
21. C. J. Willmott and K. Matsuura, “Advantages of the mean absolute error (MAE) over the root mean square error (RMSE) in assessing average model performance.“ Climate research, vol. 30, no. 1, pp. 79-82, 2005. [Google Scholar]
22. Z. Wang, A. C. Bovik, H. R. Sheikh and E. P. Simoncelli. (2004). “Image quality assessment: from error visibility to structural similarity,” IEEE Transactions on Image Processing, vol. 13, no. 4, pp. 600–612. [Google Scholar]
23. C. Sasi Varnan, A. Jagan, J. Kaur, D. Jyoti and D. S. Rao. (2011). “Image quality assessment techniques in spatial domain,” International Journal of Computer Science and Technology, vol. 2, no. 3, pp. 177. [Google Scholar]
24. E. A. Silva, K. Panetta and S. S. Agaian. (2007). “Quantifying image similarity using a measure of enhancement by entropy,” Mobile Multimedia/Image Processing for Military and Security Applications, vol. 6579, pp. 65790U. [Google Scholar]
25. H. Rabbani, M. J. Allingham, P. S. Mettu, S. W. Cousins and S. Farsiu. (2015). “Fully automatic segmentation of fluorescein leakage in subjects with diabetic macular edema automatic leakage segmentation in DME,” Investigative Ophthalmology and Visual Science, vol. 56, no. 3, pp. 1482–1492. [Google Scholar]
26. F. J. McEvoy and E. Svalastoga. (2009). “Security of patient and study data associated with DICOM images when transferred using compact disc media,” Journal of Digital Imaging, vol. 22, no. 1, pp. 65–70. [Google Scholar]
27. A. Bashir, A. S. Hasan and H. Almangush. (2012). “A new image encryption approach using the integration of a shifting technique and the AES algorithm,” International Journal of Computers and Applications, vol. 42, no. 9, pp. 36–45. [Google Scholar]
28. K. Muhammad, J. Ahmad, H. Farman, Z. Jan, M. Sajjad et al. (2015). , “A secure method for color image steganography using gray-level modification and multi-level encryption,” KSII Transactions on Internet and Information Systems, vol. 9, no. 5, pp. 1938–1962. [Google Scholar]
29. M. Elhoseny, G. Ramírez-González, O. M. Abu-Elnasr, S. A. Shawkat, N. Arunkumar et al. (2018). , “Secure medical data transmission model for IoT-based healthcare systems,” IEEE Access, vol. 6, pp. 20596–20608. [Google Scholar]
30. J. Blackledge, S. Bezobrazov, P. Tobin and F. Zamora. (2013). “Cryptography using evolutionary computing,” in 24th IET Irish Signals and Systems Conference, Letterkenny, Ireland, pp. 12–21. [Google Scholar]
31. S. Mishra and S. Bali. (2013). “Public key cryptography using genetic algorithm,” International Journal of Recent Technology and Engineering, vol. 2, no. 2, pp. 150–154. [Google Scholar]
32. J. Irene, U. Prabu, V. Gomathi, M. K. Tejaswini, M. Kavipriya et al. (2015). , “Random grid and deterministic visual cryptography with enhanced color patterns,” in Int. Conf. on Advanced Research in Computer Science Engineering & Technology, Unnao, India, pp. 1–5. [Google Scholar]
33. U. Prabu, G. Priyadharshini, M. Saranya and N. R. Praveen. (2015). “Efficient personal identification using multimodal biometrics,” in IEEE Int. Conf. on Circuit, Power and Computing Technologies, Nagercoil, India, pp. 46–54. [Google Scholar]
34. N. Thilagavathi, D. Saravanan, S. Kumarakrishnan, S. Punniakodi, J. Amudhavel et al. (2015). , “A survey of reversible watermarking techniques, application and attacks,” in 2015 Int. Conf. on Advanced Research in Computer Science Engineering & Technology, pp. 1–7. [Google Scholar]
35. S. Pal, R. Kumar and L. H. Son. (2019). “Novel probabilistic resource migration algorithm for cross-cloud live migration of virtual machines in public cloud,” Journal of Supercomputers, vol. 75, no. 9, pp. 5848–5865. [Google Scholar]
36. K. Thirugnanasambandam, S. Prakash and V. Subramanian. (2019). “Reinforced cuckoo search algorithm-based multimodal optimization,” Applied Intellgience, vol. 49, no. 6, pp. 2059–2083. [Google Scholar]
37. D. N. Le, B. Seth and S. Dalal. (2018). “A hybrid approach of secret sharing with fragmentation and encryption in cloud environment for securing outsourced medical database: a revolutionary approach,” Journal of Cyber Security and Mobility, vol. 7, no. 4, pp. 379–408. [Google Scholar]
38. B. Seth, S. Dalal, V. Jaglan, D. N. Le, S. Mohan and et al. (2020). , “Integrating encryption techniques for secure data storage in the cloud,” Transactions on Emerging Telecommunications Technologies, vol. e4108. [Google Scholar]
39. T. N. Bao, Q. T. Huynh, X. T. Nguyen, G. N. Nguyen and D. N. Le, “A Novel Particle Swarm Optimization Approach to Support Decision-Making in the Multi-Round of an Auction by Game Theory,” International Journal of Computational Intelligence Systems, vol. 13, no. 1, pp. 1447–1463, 2020. [Google Scholar]
40. L. N. Bao, D. N. Le, G. N. Nguyen, V. Bhateja and S. C. Satapathy, “Optimizing feature selection in video-based recognition using Max–Min Ant System for the online video contextual advertisement user-oriented system,” Journal of Computational Science, vol. 21, pp. 361–370, 2017. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |