DOI:10.32604/cmc.2020.012146

| Computers, Materials & Continua DOI:10.32604/cmc.2020.012146 |  |
| Article |
Blockchain Data Privacy Access Control Based on Searchable Attribute Encryption
1Lanzhou University of Technology, Lanzhou, 730050, China
2College of Computer Science and Technology, Guizhou University, Guizhou, China
3School of Computer, Xiandian University, Xi’an, China
*Corresponding Author: Tao Feng. Email: fengt@lut.cn
Received: 16 June 2020; Accepted: 28 August 2020
Abstract: Data privacy is important to the security of our society, and enabling authorized users to query this data efficiently is facing more challenge. Recently, blockchain has gained extensive attention with its prominent characteristics as public, distributed, decentration and chronological characteristics. However, the transaction information on the blockchain is open to all nodes, the transaction information update operation is even more transparent. And the leakage of transaction information will cause huge losses to the transaction party. In response to these problems, this paper combines hierarchical attribute encryption with linear secret sharing, and proposes a blockchain data privacy protection control scheme based on searchable attribute encryption, which solves the privacy exposure problem in traditional blockchain transactions. The user’s access control is implemented by the verification nodes, which avoids the security risks of submitting private keys and access structures to the blockchain network. Associating the private key component with the random identity of the user node in the blockchain can solve the collusion problem. In addition, authorized users can quickly search and supervise transaction information through searchable encryption. The improved algorithm ensures the security of keywords. Finally, based on the DBDH hypothesis, the security of the scheme is proved in the random prediction model.
Keywords: Blockchain; privacy protection; attribute encryption; access control; searchable-encryption
Blockchain technology, as an undisturbed, chronologically verifiable chain-like storage architecture, provides a new method for data security and privacy protection, and its application in power balance trading platforms has also received extensive attention. For example, Xia et al. [1] analyzed the trading mechanism of the electricity surplus market. In order to make information symmetrical and fair, they designed smart contracts for multi-party bidding of power resources based on blockchain technology, and realized decentralized transaction decisions. Literature [2] summarizes the related applications and research of existing blockchain technology, and focuses on the application of blockchain traceability technology in various fields. According to the above research and investigation, blockchain will help improve solutions in multiple areas such as the Internet of Things, smart cities and supply chains. However, the ledger that records and stores transaction information in blockchain technology is open to any node that joins the blockchain network. Through mathematical analysis of transaction records in the global ledger, attackers may pose a threat to users’ transaction privacy and identity privacy [3]. Transaction privacy threats refer to certain threats that contain detailed information about transactions. For example, an attacker can obtain some valuable information through in-depth analysis of a series of transactions of a specific account, transaction details, related accounts, and capital flows. Identity privacy threat mainly refers to the potential threat of the identity of the trader. In addition, on the basis of analyzing the transaction data, the attacker can obtain the identity information of the trader by combining some background knowledge. Jordan [4] uses cluster analysis to analyze transaction data in the blockchain and determine different addresses belonging to the same user. This is a good example of the use of analyzing transaction data to obtain the identity of a trader. In addition, since all transactions performed by users are permanently recorded in the blockchain, once the transaction is implemented, all relevant transaction information will be leaked. In addition, as the blockchain is increasingly used in daily payments, attackers can use off-chain information [5] to infer the identity of the account in the blockchain.
In the traditional blockchain, the user’s account transaction information is directly stored in the block without using encryption technology, so the user’s account is completely open to all nodes. At the same time, when a user initiates a transaction, the transaction amount in the transaction information is completely disclosed. The verification node on the blockchain performs mathematical analysis on the user’s transaction amount and account balance to verify whether the transaction is legal. Although this method realizes the decentralization of the blockchain and cannot be tampered with, the user’s account privacy [6] will be completely exposed. In response to these problems, there are some blockchain privacy protection mechanisms. Therefore, Shen Tu et al. [7] proposed a more effective blind signature hybrid scheme based on elliptic curve encryption algorithm m in reference. This scheme is simple and easy to operate, and is usually suitable for various digital currencies, but it is a centralized currency scheme. After that, in the hybrid scheme, Gao et al. [8] uses cryptographic techniques such as blind signatures to protect privacy issues, but this scheme increases computational costs, and the implementation of token processing by a third party inevitably increases additional service overhead. Some scholars also use ring signatures to protect the privacy of the blockchain. For example, Noether et al. [9] proposed an improved ring-based secret transaction scheme, which can hide the amount in reference. In this scheme, a large number of ring signatures are placed in multiple layers of linkable spontaneous anonymous group signatures [10], and its solution can protect identity privacy and transaction privacy. Although ring signature provides strong anonymity, it has three limitations:
1.Its transaction event volume is huge, each transaction event is nearly several kilobytes, which increases the storage space of the entire blockchain record.
2.The inherent disadvantage of ring signatures is that the size of the signature is proportional to the number of participants. Therefore, in reality, each transaction has only a limited number of outputs (for example, by default, each transaction has 4 outputs).
3.The hidden amount increases the difficulty of review, that is, it not only verifies whether a secret cryptocurrency is generated during the transaction, but also determines the additional amount at a specific moment.
Chen et al. [11] proposed an anti-quantum proxy blind signature scheme based on lattice cryptography, which provides user anonymity and non-traceability for distributed applications of BIoT. The proposed proxy blind signature scheme can completely solve the unforgeable problem without authorization to protect user privacy. Chiesa et al. [12] proposed the Zerocash scheme, which introduced zk-SNARK [13], a non-interactive zero-knowledge proof technology in cryptography that converts into digital currency, which can ensure the unlinkability of transactions And confidentiality, while it supports any amount of money. However, the disadvantage of this scheme is that if an attacker obtains the secret data introduced at the beginning, the token may be forged. Subsequently, in order to solve the privacy problem in the public chain off-chain payment protocol, many studies have constructed offline payment protocols, such as two-way micro-payment channels [14] Lightning Network and Spirtes [15]. However, in these schemes, both parties in the transaction must use the relay node to complete the transaction, and the transaction information is public to the relay node, so the privacy of both parties in the transaction will be exposed to the relay node. For offline payment privacy issues, there are some studies, such as the Tumble Bit solution proposed by Alshenibr et al. [16]. This solution can hide payment channel information from relay nodes. In addition, Tumble Bit solutions are generally suitable for compatible Bitcoin systems. But the time and efficiency costs are relatively high. Green et al. [17] proposed the Bolt scheme, which ensures that payments under the same channel are independent of each other, and the payment time does not require block confirmation to reach the second level. If someone pays through the payment channel provided by the payee, the payee will receive a notification. There are still many problems to be solved in the security of payment protocols.
A privacy protection mechanism for blockchain retrieval based on searchable keywords is proposed [18], which realizes the private search of authorized keywords without changing the retrieval order. But the keywords in this scheme are relatively short, they cannot resist collusion, and can communicate privately between nodes. Aiming at data sharing privacy, Do et al. [19] proposed a distributed data storage system using blockchain technology and a private keyword search scheme, which provides authorization for data owners and supports dedicated keyword search for encrypted data sets. However, this program has not yet implemented document revocation and Boolean search. The data storage incentive mechanism of wireless sensor network (WSN) [20], which uses double chains, one chain is used to store the data of each node, and the other chain is used to control data access. In addition, the reserved hash function is used to compare the stored data with the new data block. New data can be stored in the node closest to the existing data, and only different sub-blocks can be stored, which can greatly save the storage space of network nodes. However, the confidentiality of the data was not discussed. Using the DCOMB method, literature [21] proposed a blockchain-based IoT data query model. This model combines the IoT data stream with the timestamp of the blockchain to improve the interoperability of data and the versatility of the IoT database system. The data query model in this solution can quickly query the public key corresponding to the data stream. The query is in a fully encrypted environment, which can ensure the privacy and security of IoT data. However, the data pre-reading process will take extra time, and MySQL query performance will cost more.
In the above scheme, the data privacy problem has not been completely resolved. Therefore, it is urgent to solve its privacy problem. The contribution of this paper is as follows:
1.In this paper, the public key searchable encryption method is used to encrypt the transaction privacy data in the blockchain, which solves the privacy leakage problem caused by the disclosure of all data in the traditional public blockchain, meanwhile, realizes the privacy of protecting the sensitive information of the blockchain transaction.
2.The use of attribute encryption technology combined with secret sharing enables fine grained access control of transaction ciphertext in the blockchain.
3.In addition, the users who have access to transaction can quickly search ciphertext, which realizes the supervision of transaction information.
The Organization of the paper is structured as follows: In Section 1, we introduce the research on the privacy of blockchain; We introduce the basic cryptographic primitives in Section 2; In Section 3, the system model in general and the security model of security requirements are proposed; In Section 4, the specific construction of the scheme is described; In Section 5, we analyze the security of the scheme in detail; We compare the related work in Section 6; In Section 7, we summarize our scheme.
Definition 1: Let 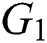 and
and 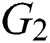 are multiplicative cyclic groups whose order q is prime. For a random generator p of a group, there exists a bilinear pair mapping that satisfies the following properties:
are multiplicative cyclic groups whose order q is prime. For a random generator p of a group, there exists a bilinear pair mapping that satisfies the following properties:
(1) Bilinear: for 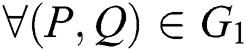 and
and 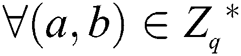 are true.
are true.
(2) Non-degenerate: 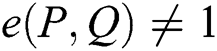 .
.
(3) Computability: For 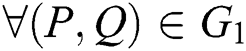 , there is a polynomial time algorithm for calculation
, there is a polynomial time algorithm for calculation 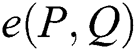 .
.
2.2 Determining the Bilinear Diffie–Hellman Assumption (DBDH)
Select a generator 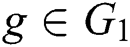 and choose
and choose 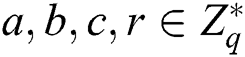 , for
, for 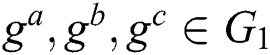 ,
, 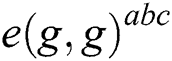 and
and 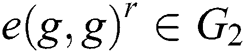 , determine if the relationship between
, determine if the relationship between 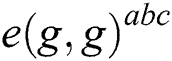 and
and 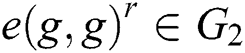 is equal.
is equal.
Definition 2: For the arbitrary polynomial probability time algorithm adversary A, the advantage of solving the decision bilinear Diffie–Hellman (DBDH) hypothesis [i] is defined as:
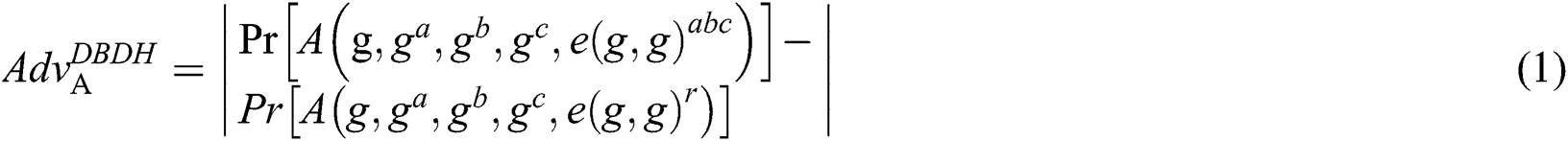
If the determined value 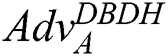 is negligible, then the decision bilinear Diffie–Hellman hypothesis will be established.
is negligible, then the decision bilinear Diffie–Hellman hypothesis will be established.
2.3 Lsss Linear Secret Sharing Scheme
A linear secret sharing scheme [22] will be called linear on a group of participants P if the following conditions are satisfied:
(1) The share of the participants for each party comes from a matrix 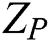 above.
above.
There is a matrix M with c rows and d columns called the shared generation matrix Π. For all 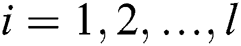 , the function
, the function  defines the participant marking of the i-th row of M as
defines the participant marking of the i-th row of M as  . When we consider the row vector
. When we consider the row vector 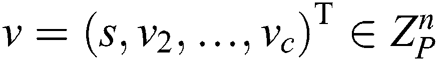 , which
, which 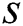 is the secret that is shared, and
is the secret that is shared, and 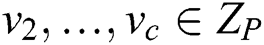 is randomly chosen.
is randomly chosen. 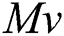 is the secret share according to the vector
is the secret share according to the vector 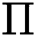 . The share
. The share 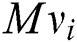 belongs to
belongs to 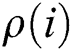 .
.
(2) Assume that Π is an LSSS for the access structure. Let 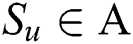 be an arbitrary subset of authorizations, and
be an arbitrary subset of authorizations, and 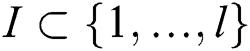 . If
. If 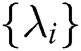 is the valid share of any secret S according to Π, there will be a constant
is the valid share of any secret S according to Π, there will be a constant 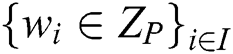 that makes
that makes 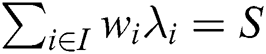 at this time. Furthermore, these constants
at this time. Furthermore, these constants 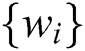 can be found in the time polynomial of the shared generator matrix M.
can be found in the time polynomial of the shared generator matrix M.
The block chain data privacy access control system model based on searchable attribute encryption is shown in Fig. 1, which includes four types of participating entities: Data owner, verification nodes, user and miner node, Trading generates is shown in Fig. 2.
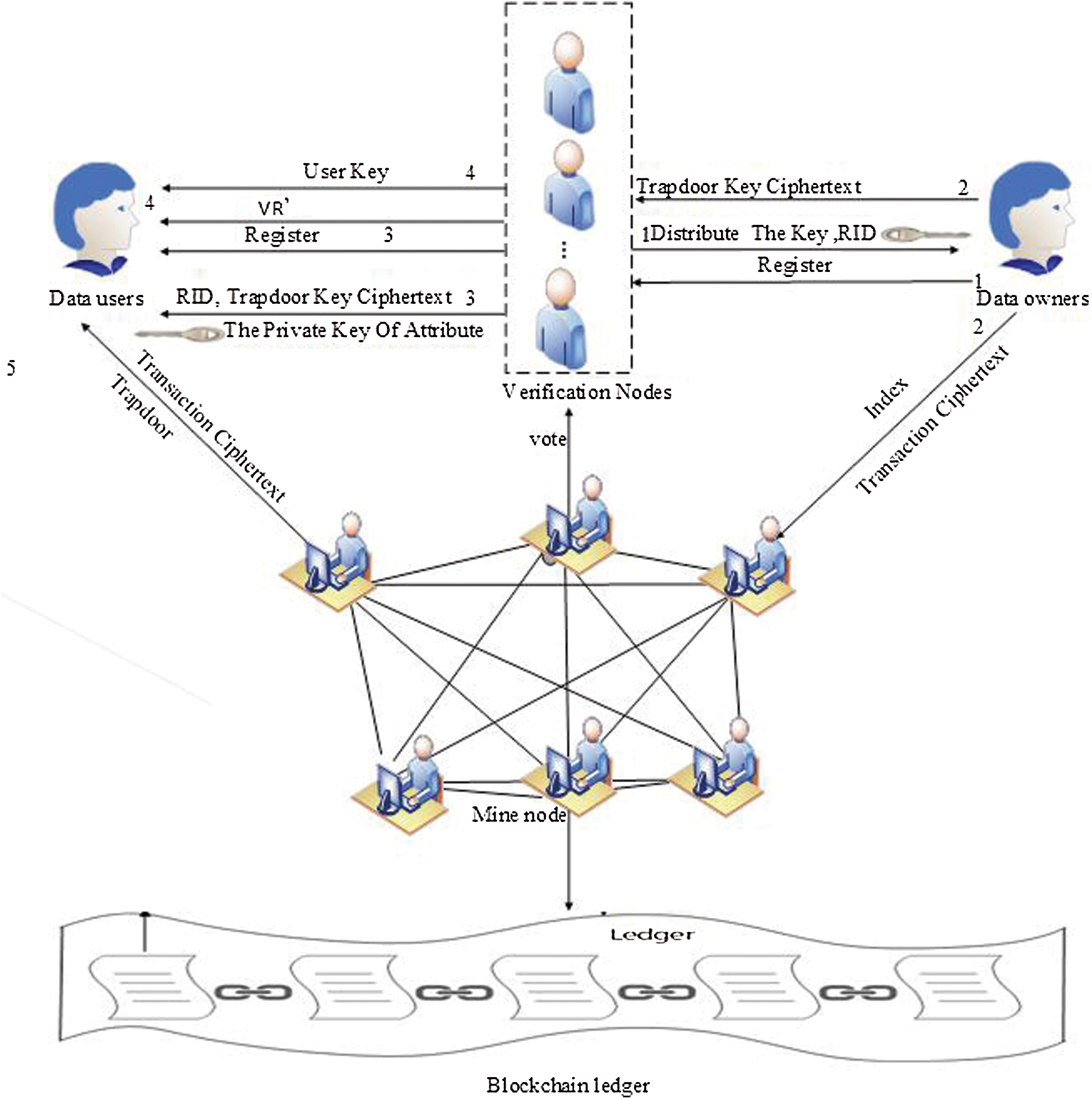
Figure 1: System model
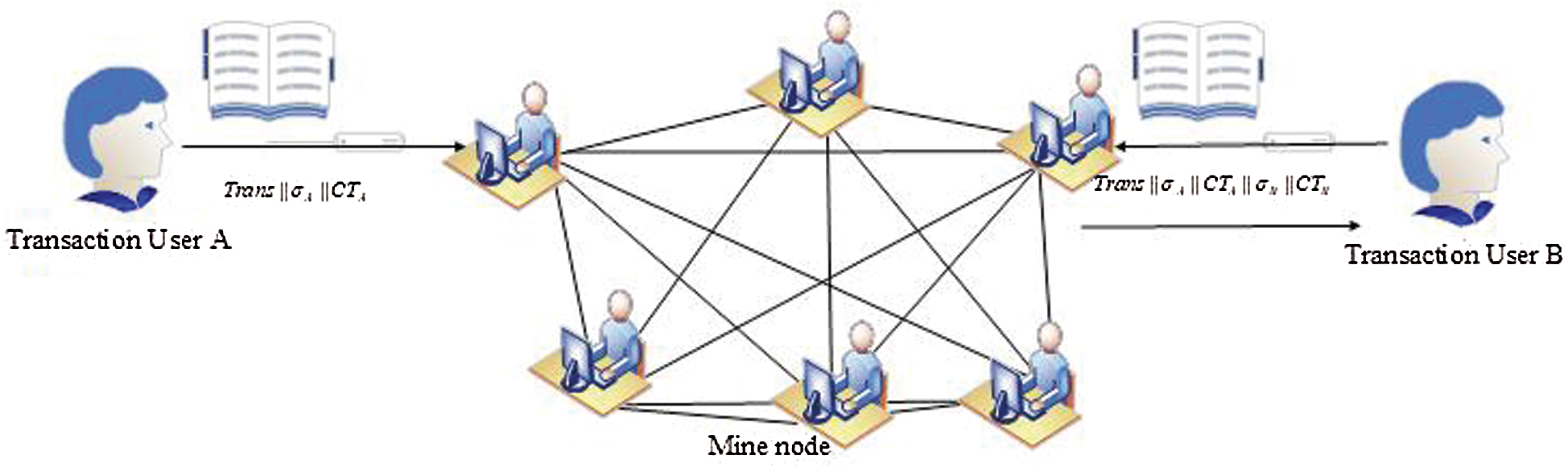
Figure 2: Trading generates
Data Owner: Firstly, initializing generates the index key and the trapdoor key, extracts the keywords of the transaction, then uses the index key to encrypt the index and form the index ciphertext; Secondly, encrypt the trapdoor key to form the trapdoor key ciphertext and share the data. Finally, using the secure signature algorithm signs the transaction and encrypts, meanwhile, data owners appends the indexes keyword to the ciphertext file of the transaction ciphertext. Above all the data owner can be a user on the blockchain for Bitcoin transactions or a miner.
User: The registration system generates an identity identifier RID corresponding to the real identity and a private key corresponding to the user attribute. In addition, user decrypts the trapdoor key ciphertext and gains the user key to generate a trapdoor, and sends the blockchain to request the transaction ciphertext.
Verification Nodes: Verify the correctness of the user’s identity and permissions, and calculate the user’s attribute and private key parameters and permission parameters in the attribute collection to distribute the trapdoor key ciphertext, and distribute the user key UK to the legitimate user.
Miner Node: The miner node broadcasts all the transaction information during this period, and each node performs verification and joins the blockchain after verification. The trapdoor and the index sent by the data owner are calculated and matched, then the transaction ciphertext will be sent to the data consumer after the matching is successful.
The solution proposed in this paper only the Verification Node is completely credible, the private key can be generated and distributed honestly for the user. Most miner nodes are honest but curious. In addition, users may collude to decrypt data that they do not have access to.
The security model refers to the game between the opponent and the challenger. The game is described as follows:
IND-CPA security model
Initialization: Challenger A runs the initialization algorithm to generate the public parameters and master key, and sends the public parameters to the adversary.
Phase 1: The adversary C continually repeats the corresponding set of attributes  , where none of the attributes satisfy the access structure.
, where none of the attributes satisfy the access structure.
Challenge: The enemy C picks two messages 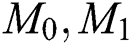 and sends them to the challenger A. The challenger A randomly picks a byte
and sends them to the challenger A. The challenger A randomly picks a byte  and encrypts the message M of the access structure, then the challenger A sends the ciphertext to the rival C.
and encrypts the message M of the access structure, then the challenger A sends the ciphertext to the rival C.
Phase 2: Phase 1 is repeated guess: The guess of the enemy C input 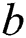 , if the opponent guesses
, if the opponent guesses 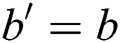 , the enemy C will win the game. The advantage of rival C in this game is defined as
, the enemy C will win the game. The advantage of rival C in this game is defined as 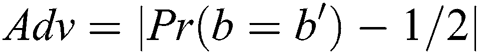 .
.
Definition 1: If the advantage 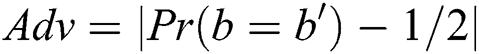 of the above game is negligible in the time of all polynomials, the proposed solution can be IND-CPA security.
of the above game is negligible in the time of all polynomials, the proposed solution can be IND-CPA security.
IND-CKA security model
Initialization: Repeat the initialization of the above security model.
Phase 1: The adversary adaptively proposes the following polynomial query.
Hash Ask: The adversary can ask the random oracle 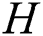 .
.
Trapdoor request: The adversary can request any keyword trapping.
Challenge: The adversary submits two keywords and gives the challenger C, the limit is that the enemy can’t ask for the keyword.
Phase 2: Phase 1 is repeated.
Guess: The opponent A outputs the guess 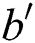 of
of 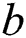 , if the opponent guesses
, if the opponent guesses 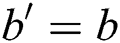 , the enemy C will win the Game. The advantage of rival C in this game is defined as
, the enemy C will win the Game. The advantage of rival C in this game is defined as 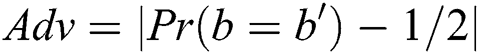 .
.
Definition 2: If the advantage of the above game is negligible at the time of the polynomial, the proposed scheme can be IND-CKA security.
In this part, we present the specific implementation process of the blockchain data privacy protection access control method algorithm based on searchable attribute encryption.
a) Registration
The user submits a registration application to the system, obtains the identity RID and the user attribute set corresponding to the real identity information, and the data owners (transaction users) register to obtain the key and the identity identifier.
b) Initialization
Data owner initialization: Select a group 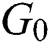 with the prime number
with the prime number 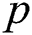 as the order, generate the group with the element
as the order, generate the group with the element 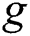 , select N elements in the limit field, and use the system attribute to form the system attribute set S, and the attributes in S according to the correlation between the attributes. S is divided into
, select N elements in the limit field, and use the system attribute to form the system attribute set S, and the attributes in S according to the correlation between the attributes. S is divided into 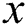 trees,
trees, 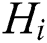 set to the depth of the i-th tree,
set to the depth of the i-th tree, 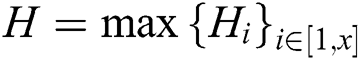 defined as the maximum depth in the tree; randomly select vector
defined as the maximum depth in the tree; randomly select vector 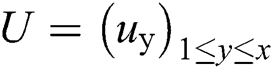 and
and 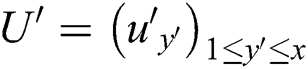 ,
, 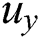 represents the public parameter corresponding to the
represents the public parameter corresponding to the 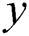 attribute tree, data owner selects a sequence of prime
attribute tree, data owner selects a sequence of prime  , and generates a group of
, and generates a group of 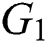 ,
, 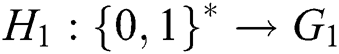 is a hash function. Data owner chooses two random numbers
is a hash function. Data owner chooses two random numbers  ,
,  , calculates the public key
, calculates the public key 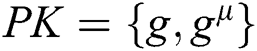 ,and the private key
,and the private key 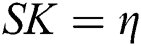 represents the trapdoor key.
represents the trapdoor key.
The verification node initialization: 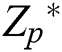 expresses a set of elements in the finite field with p-primitives, from which two random numbers
expresses a set of elements in the finite field with p-primitives, from which two random numbers  ,
, 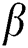 of different sizes are selected, the verification node calculates
of different sizes are selected, the verification node calculates  and
and 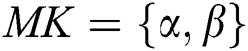 to define a bilinear map
to define a bilinear map  .
.
c) Transaction generation and signature
Transaction user A generates transaction information, encrypts its own identity, runs the wallet signature algorithm and signs it with the private key corresponding to the wallet address, then sends it to transaction user B. The user signature is calculated as follows:

d) Index generation
The trader extracts the keyword from the transaction plaintext information, and encrypts the keyword with the index key 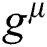 and the random number
and the random number  ,
, 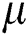 . The keywords of the transaction information are calculated as follows:
. The keywords of the transaction information are calculated as follows:

e) Encrypt The
The 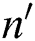 user attribute
user attribute 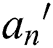 in the ciphertext policy attribute set H is located in the
in the ciphertext policy attribute set H is located in the 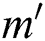 attribute tree, and its depth
attribute tree, and its depth  , its path is
, its path is  , where
, where 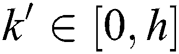 ,
, 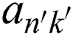 is the corresponding attribute of the user attribute
is the corresponding attribute of the user attribute 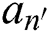 in the path
in the path 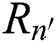 the layer
the layer 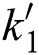 , and for the policy attribute
, and for the policy attribute  , according to the mapping p selects its corresponding secret share
, according to the mapping p selects its corresponding secret share 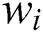 . The calculation of attribute ciphertext
. The calculation of attribute ciphertext  and policy parameters
and policy parameters 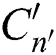 are as follows:
are as follows: 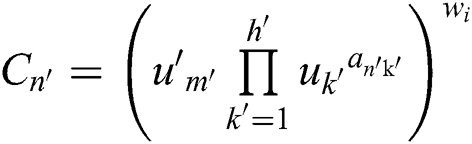 ,
, 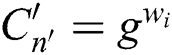 . The public parameter
. The public parameter 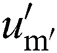 corresponding to the
corresponding to the  attribute tree,
attribute tree, 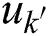 indicates the public parameter of the
indicates the public parameter of the 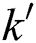 layer, the ciphertexts are as follows:
layer, the ciphertexts are as follows:
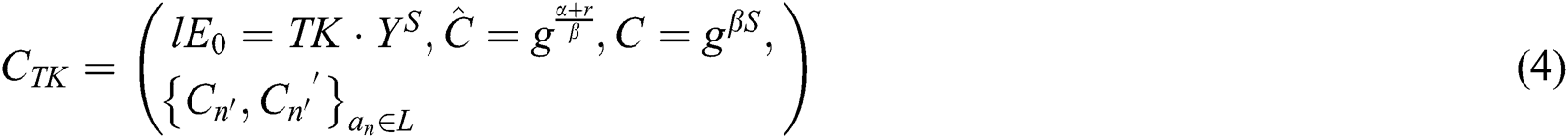

M is the transaction plaintext information, 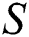 is a secret value, and
is a secret value, and 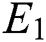 is a partial ciphertext containing the transaction plaintext information M.
is a partial ciphertext containing the transaction plaintext information M.
f) Trapdoor generation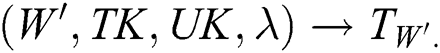 In this algorithm, select a random number and calculate the trapdoor:
In this algorithm, select a random number and calculate the trapdoor:

g) Test  According to the UK execution calculation, the match
According to the UK execution calculation, the match 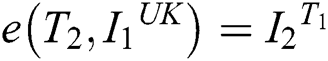 submitted by the user and corresponding to this algorithm is as follows:
submitted by the user and corresponding to this algorithm is as follows:
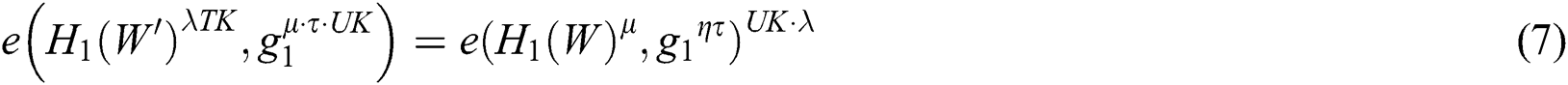
If the user’s search keyword is the same as the search keyword contained in the index, the equation will establish. The blockchain returns the result to the user, otherwise it returns an empty set to the user.
h) Key generation
For the user’s attribute set 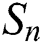 , the n-th user attribute
, the n-th user attribute 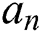 is located in the i-th attribute tree, and its depth is
is located in the i-th attribute tree, and its depth is 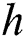 , its path
, its path  , where
, where 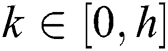 is the corresponding attribute of the k-th layer in the user attribute
is the corresponding attribute of the k-th layer in the user attribute 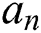 path
path 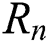 , and the verification node selects the random number
, and the verification node selects the random number 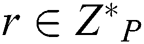 used to resist the collusion attack. For the attribute
used to resist the collusion attack. For the attribute 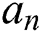 of the user, select the random number
of the user, select the random number 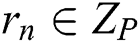 , calculate the attribute private key
, calculate the attribute private key 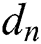 , the private key parameter
, the private key parameter 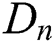 and the permission parameter set
and the permission parameter set 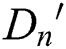 , these calculations are as follows:
, these calculations are as follows:
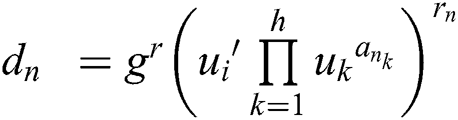 ,
, 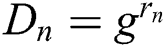 ,
, 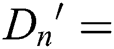
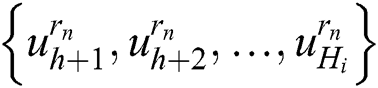 . Combining the private key component, the user can get the private key as:
. Combining the private key component, the user can get the private key as:

i) Decryption
In the attribute authorization set 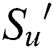 , the user attribute
, the user attribute 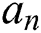 is in the m-th attribute tree, the policy attribute
is in the m-th attribute tree, the policy attribute 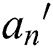 is in the
is in the 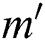 attribute tree, and
attribute tree, and 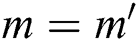 is satisfied; the depth h of the user attribute
is satisfied; the depth h of the user attribute  is satisfied with the depth
is satisfied with the depth  of the policy attribute
of the policy attribute 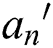 , The relationship between the path of the attribute is
, The relationship between the path of the attribute is 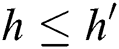 ; The path
; The path 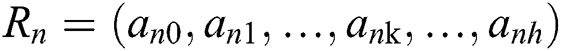 of the user’s attribute and attribute path
of the user’s attribute and attribute path 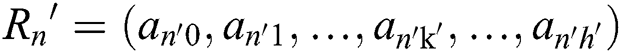 are satisfied:
are satisfied: 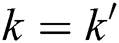 ,
,  ,
, 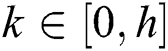 ,
, 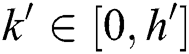 ; For the consumer attribute
; For the consumer attribute 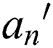 of the override policy attribute, the decryption permission value
of the override policy attribute, the decryption permission value 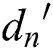 is calculated as follows:
is calculated as follows:
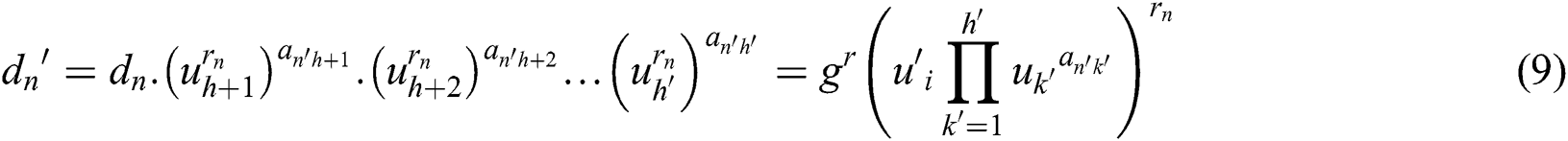
Decrypt the bilinear map 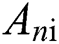 and calculate the user’s permissions
and calculate the user’s permissions 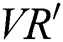 as follows:
as follows:
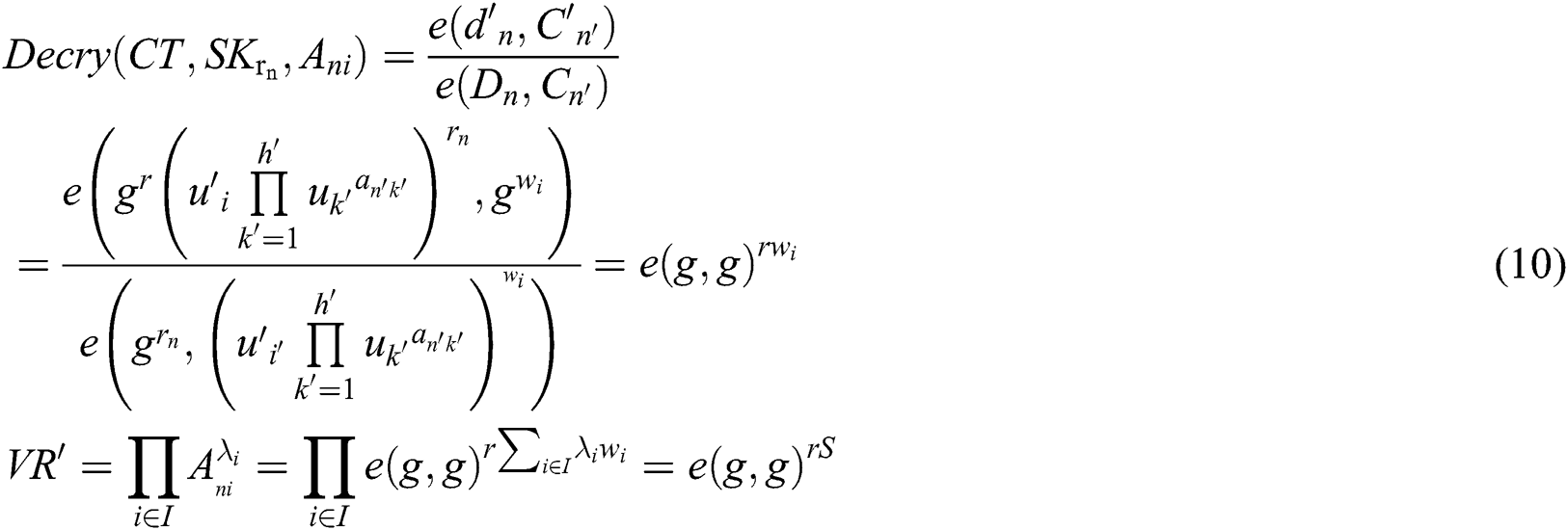
If the user’s permissions satisfy the structure, they can decrypt the trapdoor key as:
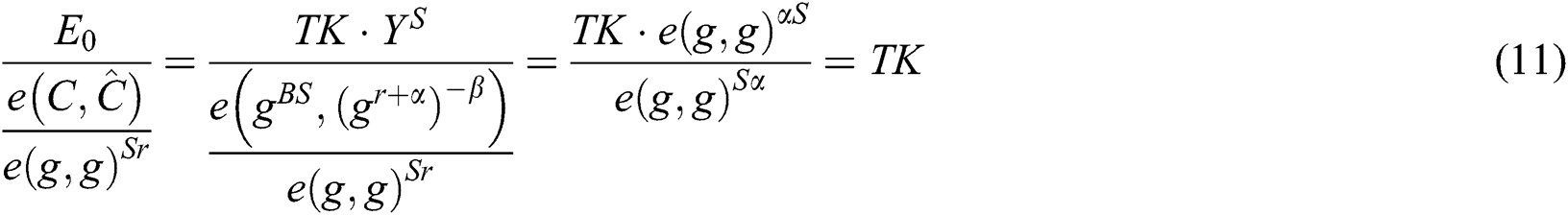
The transaction message can be restored to:

In this part, the proposed scheme is proved to be security under the random oracle model.
Lemma 5.1 Based on the DBDH hypothesis, our solution can resist selected plaintext attacks in the random Oracle model, then our solution is CPA-security.
Proof: Assuming a probabilistic polynomial time, an adversary can exploit advantage 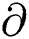 to attack our solution. We prove that the following DBDH games can be attacked by a advantage
to attack our solution. We prove that the following DBDH games can be attacked by a advantage  of enemy C.
of enemy C. 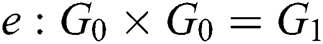 is a bilinear map, where G is a cyclic group with a generator element
is a bilinear map, where G is a cyclic group with a generator element 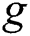 order of
order of 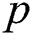 . The challenger is randomly selected
. The challenger is randomly selected 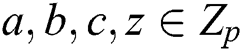 ,
, 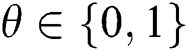 and if
and if 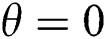 , set
, set 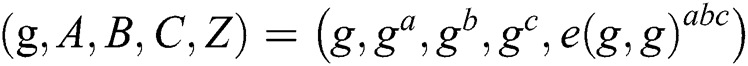 , if
, if 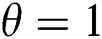 , set
, set 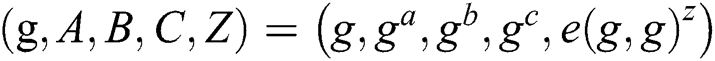 .
.
Initialization: The adversary controls a set of authorized permissions, at least two of which are controlled by the adversary, and the remaining permissions are controlled by the challenger. The adversary affirmed the challenge of the LSSS access structure.
The challenger randomly selected  , and
, and 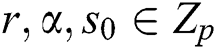 were all randomly selected. Set and send
were all randomly selected. Set and send 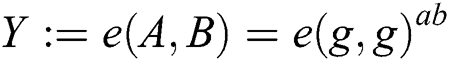 public parameters to the adversary.
public parameters to the adversary.
Stage 1: The adversary asks for many of the private keys he wants according to the attribute set, but these private keys do not satisfy the access structure. Upon receiving the private key request of A with the identity RID, the challenger randomly selects 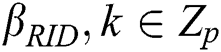 and calculates the private key component for each attribute
and calculates the private key component for each attribute 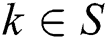 as follows:
as follows: 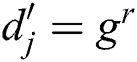
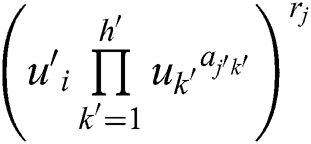 ,
, 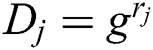 ,
, 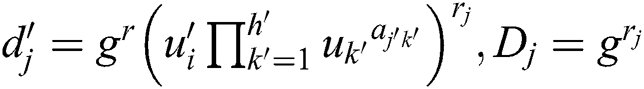
Phase 2: Repeat phase 1.
Guess: The adversary submitted a  guess of
guess of  , when
, when 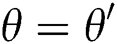 , if
, if  , the simulator representing the challenger will output
, the simulator representing the challenger will output  , otherwise output a DBDH array
, otherwise output a DBDH array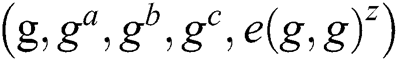 . If
. If 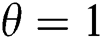 , the adversary will not get useful information, and its advantage is
, the adversary will not get useful information, and its advantage is  .When
.When 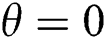 , its advantage is
, its advantage is  . Therefore, the probability polynomial time of the opponent in the DBDH game is
. Therefore, the probability polynomial time of the opponent in the DBDH game is 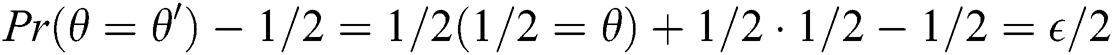 . In short, if the polynomial time in our game is
. In short, if the polynomial time in our game is 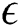 , the adversary has a non-negligible advantage
, the adversary has a non-negligible advantage 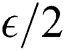 . Therefore, based on the DBDH assumption, the adversary has no advantage in our security game, so our solution is safe.
. Therefore, based on the DBDH assumption, the adversary has no advantage in our security game, so our solution is safe.
Lemma 5.2 If we assume DBDH is established, our scheme can resist selected keyword attacks in the random Oracle model, then our scheme is semantically CKA-security.
Initialization: The simulator received a DBDH challenge, selecting two multiplicative loop groups of order 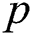 , the generator
, the generator 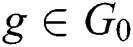 , and a bilinear map
, and a bilinear map 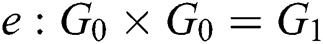 . Secondly, the simulator
. Secondly, the simulator 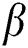 randomly select
randomly select  , select
, select 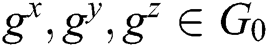 ,
, 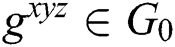 . The simulator randomly selects
. The simulator randomly selects 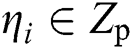 so that the enemy’s public key
so that the enemy’s public key  and private key are
and private key are 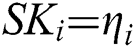 . The SK is set to represent the trapdoor key as
. The SK is set to represent the trapdoor key as 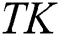 , and the PK is the index key IK.
, and the PK is the index key IK.
Stage 1: The adversary adaptively asks the following query:
Hash-ask: The adversary can ask the random oracle 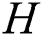 at any time. In order to answer the inquiry, the simulator maintains the list
at any time. In order to answer the inquiry, the simulator maintains the list  . At first this list is empty. When the adversary asks for any keyword
. At first this list is empty. When the adversary asks for any keyword 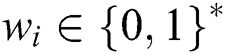 on the random oracle, the simulator’s answer is as follows:
on the random oracle, the simulator’s answer is as follows:
1. If the query keyword 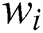 exists in the list
exists in the list 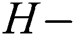 , the corresponding response of the simulator can be
, the corresponding response of the simulator can be 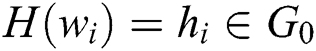 .
.
2. Otherwise, the simulator generates a random coin  so that
so that  .
.
If  , the simulator can calculate
, the simulator can calculate 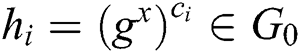 .
.
If 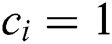 , the simulator can calculate
, the simulator can calculate 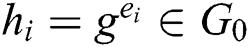 , which
, which 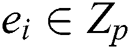 is randomly selected. The array
is randomly selected. The array 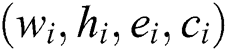 is then added to the
is then added to the  list and
list and 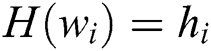 will be returned to the adversary.
will be returned to the adversary.
Trapdoor inquiry: When the adversary asks for any keyword 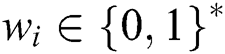 in the trapdoor, the simulator first performs an inquiry to obtain the sum corresponding to the list. The simulator answers as follows:
in the trapdoor, the simulator first performs an inquiry to obtain the sum corresponding to the list. The simulator answers as follows:
1. If 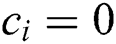 , the simulator will announce the failure and termination and output the guess
, the simulator will announce the failure and termination and output the guess 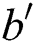 value of
value of 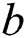 .
.
2. If 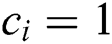 ,
,  , the simulator will select the random value
, the simulator will select the random value 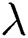 ,
, 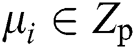 , and calculates the trapdoor, and the simulator sends the trapdoor
, and calculates the trapdoor, and the simulator sends the trapdoor 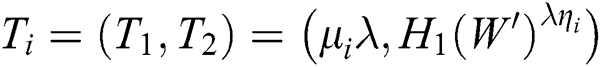 to the adversary.
to the adversary.
Challenge: The adversary submitted a pair of keywords 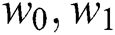 , which
, which 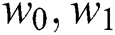 are keywords that the enemy did not ask before. The keyword index generated by the adversary is as follows:
are keywords that the enemy did not ask before. The keyword index generated by the adversary is as follows:
1. Firstly, simulator perform two 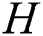 queries to get
queries to get 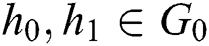 so that
so that 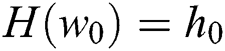 ,
, 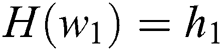 . For
. For 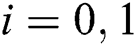 , we set the array
, we set the array 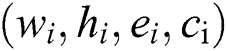 corresponding to the list
corresponding to the list  . If
. If 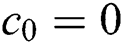 and
and 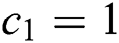 , the simulator announces the failure and termination. We know that at least
, the simulator announces the failure and termination. We know that at least  and
and 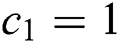 one is equal to zero. The simulator selects one byte
one is equal to zero. The simulator selects one byte 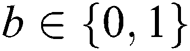 for
for 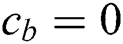 .
.
2. Simulator answers the keyword index  . The simulator then randomly selects the parameters
. The simulator then randomly selects the parameters 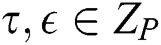 , and the keyword index is calculated as follows:
, and the keyword index is calculated as follows: 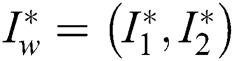
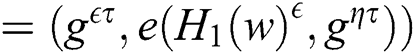 , and the trapdoor and keyword index are sent to the adversary.
, and the trapdoor and keyword index are sent to the adversary.
Phase 2: Phase1 is repeated.
The opponent outputs the guess 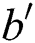 value of the keyword
value of the keyword 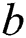 . If the adversary wins in the game, the simulator will output
. If the adversary wins in the game, the simulator will output 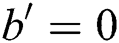 . If
. If  , output
, output 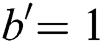 .
.
Possibility Analysis: The adversary A performs the most trapping 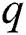 and indexing queries. The probability
and indexing queries. The probability 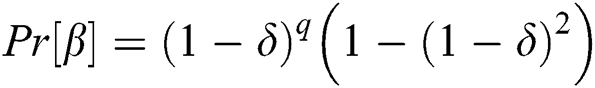 that the simulator is not aborted in the game, the probability
that the simulator is not aborted in the game, the probability 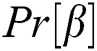 is not negligible. Under the premise that the simulator does not suspend the game, if A successfully guesses the keyword, then the value
is not negligible. Under the premise that the simulator does not suspend the game, if A successfully guesses the keyword, then the value  can be known. The probability that an enemy wins the game is
can be known. The probability that an enemy wins the game is 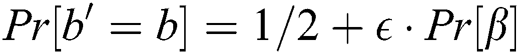 , which
, which 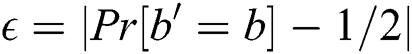 is the advantage of winning the adversary. Based on the DBDH assumption, no adversary can break our algorithm, and our solution is security.
is the advantage of winning the adversary. Based on the DBDH assumption, no adversary can break our algorithm, and our solution is security.
Lemma 5.3 If the DBDH assumption is true, our scheme will be security under the random oracle model.
Proof directly from Lemma 5.1 and Lemma 5.2.
6.1 Privacy Protection Analysis
Content privacy: This paper uses the ciphertext policy-based attribute encryption mechanism algorithm to encrypt trapdoor key information, which is more secure than symmetric encryption algorithms. By encrypting trapdoor key information with the LSSS linear secret sharing structure and encrypting transaction information with searchable encryption, we can ensure the privacy of both parties’ content. In the process of generating the private key, the random number and the identifier RID of the user interaction are introduced. Even if different users collude with each other, they cannot obtain the private key without permission. Therefore, even if there is collusion, illegal users cannot obtain the transaction information and the secret of sharing.
Identity privacy: Use the verification node in the blockchain data privacy protection access control method based on searchable attribute encryption. The verification node stores the trapdoor key ciphertext. The transaction user A does not need to be online at any time, and randomly generates key UK and identity RID for each user. In the process of interaction, the RID sequence represents the identity of the user, which protects the identity privacy of the user.
Searching privacy: Our scheme’s search mechanism is against multiple attacks. In the process of index generation, the transaction party A uses the random number 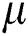 to encrypt the indexed keyword, and the node on the blockchain cannot perform the internal keyword guessing attack by matching the candidate keyword with the trapdoor. In the trapdoor generation phase, we use random numbers to hide the search keywords, which prevents malicious nodes from performing keyword replay attacks after trapdoor cracking. Therefore, blockchain network nodes and attackers cannot obtain useful information about keywords. Therefore, our solution guarantees the privacy of the keyword without reducing the security of the previous algorithm.
to encrypt the indexed keyword, and the node on the blockchain cannot perform the internal keyword guessing attack by matching the candidate keyword with the trapdoor. In the trapdoor generation phase, we use random numbers to hide the search keywords, which prevents malicious nodes from performing keyword replay attacks after trapdoor cracking. Therefore, blockchain network nodes and attackers cannot obtain useful information about keywords. Therefore, our solution guarantees the privacy of the keyword without reducing the security of the previous algorithm.
Attribute privacy: The verification node implements fine-grained access control, and the verification node authorizes the user of the blockchain by verifying the 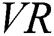 , which avoids the risk of submitting the access structure to the blockchain network. This mechanism protects the attributes of the linear access structure developed by the counterparty.
, which avoids the risk of submitting the access structure to the blockchain network. This mechanism protects the attributes of the linear access structure developed by the counterparty.
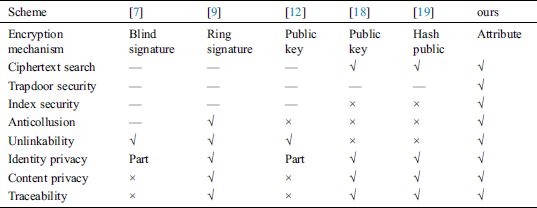
The literature [7] applied the elliptic curve encryption algorithm to propose a more efficient blind signature hybrid scheme, which protects the privacy of transaction information. In literature [9], the transaction amount is hidden by the ring signature, and a secret transaction scheme based on ring signature is proposed, thus protecting transaction privacy and identity privacy. Literature [12] presented a zero cash scheme using public key encryption to protect transaction privacy. In Literature [18], public key cryptography is used to propose a blockchain retrieval privacy protection mechanism based on searchable keywords. Literature [19] proposed a distributed data storage system using blockchain technology and a privacy keyword search scheme. It can be seen from Tab. 1 that this paper adopts the access control method of searchable hierarchical attribute encryption, which not only hides the transaction amount for the nodes without access rights on the blockchain, but also the permission of the blockchain user node can quickly and efficiently query valid information of the transactions through trapdoor keywords.
Table 1: Comparison of this article and existing privacy protection schemes
In this section, we analyze the performance of the solution. We use E for exponential operation and P for linear operation. H represents a hash operation, and m represents the number of users. In Tab. 2, we present the performance calculations for our scheme and Reference [18–19].
Table 2: Performance calculation comparison
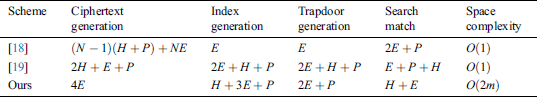
Since the global ledger that uses blockchain technology to store transaction information is open to any node joining the blockchain network, it is necessary to further strengthen and improve the data privacy of the blockchain. A blockchain data privacy protection access control scheme based on searchable attribute encryption is proposed. This scheme uses attribute encryption based on ciphertext strategy to encrypt trapdoor keys, and then uses searchable encryption to encrypt transactions on the blockchain. User authorization allows authorized users to access transaction information. It not only realizes the privacy protection of transaction information on the blockchain, but also enables authorized users to efficiently access transaction information. Under the random oracle model, the safety and effectiveness of the scheme are proved.
Acknowledgement: Thanks to teacher Feng for his guidance on the scheme of my paper, thanks to teacher Youliang Tian for his proposal on the modification of my paper, and finally thanks to Xiaoqin Feng and Rong Ma for the revision of the overall grammar of my paper.
Funding Statement: This research was supported by The National Natural Science Foundation of China (No. 61462060, No. 61762060) and The Network and Information Security Innovation Team of Gansu Provincial Department of Education Lanzhou University of Technology (No. 2017C-05). Tao Feng is the corresponding author.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1Z. Q. Xia, J. J. Tan, J. Wang, R. L. Zhu and H. G. Xiao. (2019), “Research on fair trading mechanism of surplus power based on blockchain. ,” Journal of Universal Computer Science, vol. 25, no. (10), pp, 1240–1260, .
2J. Y. Zhang, S. Q. Zhong, T. Wang, H. C. Chao and J. Wang. (2020), “Blockchain-based systems and applications: A survey. ,” Journal of Internet Technology, vol. 21, no. (1), pp, 1–14, . [Google Scholar]
3H. Y. Duan, Z. Z. Li and S. P. Qu. (2018), “Blockchain technology: Application and problems. ,” Journal of Xi’an University of Posts and Telecommunications, vol. 23, no. (1), pp, 1–13, . [Google Scholar]
4G. Jordan, K. Levchenko, D. McCoy, S. Meiklejohn, M. Pomarole. (2013). et al., “A fistful of bitcoins: Characterizing payments among men with no names. ,” in Proc. of on Int. Measurement Conf., ACM, pp, 127–140, . [Google Scholar]
5M. Conti, E. Sandeep Kumar, C. Lal and S. Ruj. (2018), “A survey on security and privacy issues of bitcoin. ,” IEEE Communications Surveys & Tutorials, vol. 20, no. (4), pp, 3416–3452, . [Google Scholar]
6Q. Feng, D. He, M. K. Khan, N. Kumar and S. Zeadally. (2018), “A survey on privacy protection in blockchain system. ,” Journal of Network and Computer Applications, vol. 126, no. (10), pp, 45–58, . [Google Scholar]
7Q. C. Shen Tu and J. P. Yu. (2015), “A blind-mixing scheme for bitcoin based on an elliptic curve cryptography blind digital signature algorithm. ,” Computer Science, vol. 1510, no. (05833), pp, 1–17, arXiv preprint arXiv. [Google Scholar]
8F. Gao, M. Shen and L. Zhu. (2017), “Research review on blockchain privacy protection. ,” Computer Research and Development, vol. 54, no. (10), pp, 2170–2186, . [Google Scholar]
9S. Noether, A. Mackenzie and Research Lab T. M.. (2016), “Ring confidential transactions. ,” Ledger, vol. 1, pp, 1–18, . [Google Scholar]
10J. K. Liu, V. K. Wei and D. S. Wong. (2016), “Linkable spontaneous anonymous group signature for ad hoc groups. ,” in Australasian Conf. on Information Security and Privacy, Berlin, Heidelberg: Springer, vol. 3108, pp, 325–335, . [Google Scholar]
11Y. Chen, A. Haseeb, C. Li, J. Li and G. Xu. (2019), “A new anti-quantum proxy blind signature for blockchain-enabled internet of things. ,” Computers, Materials & Continua, vol. 61, no. (2), pp, 711–726, . [Google Scholar]
12A. Chiesa, C. Garman and E. B. Sasson, “Zerocash: Decentralized anonymous payments from bitcoin. ,” in IEEE Symp. on Security and Privacy, 2014. [Google Scholar]
13A. Chiesa, D. Genkin and E. B. Sasson. (2013), “Snarks for c: Verifying program executions succinctly and in zero knowledge. ,” in Annual Cryptology Conf., Berlin, Heidelberg: Springer, pp, 90–108, . [Google Scholar]
14C. Decker and R. Wattenhofer. (2015), A fast and scalable payment network with bitcoin duplex micropayment channels. In: A. Stabilization, Safety, and Security of Distributed Systems, vol. 9212. New York: Springer Verlag, 3–18, . [Google Scholar]
15I. Bentov, R. Kumaresa and A. Miller, “Sprites: Payment channels that go faster than lightning. ,” Available https://arxiv.org/abs/1702.05812. [Google Scholar]
16L. Alshenibr, F. Baldimtsi and E. Heilman. (2017), “TumbleBit: An untrusted bitcoin-compatible anonymous payment hub. ,” Network & Distributed System Security Symposium, [Google Scholar]
17M. Green and I. Miers. (2017), “Bolt: Anonymous payment channels for decentralized currencies. ,” in Proc. of the 2017 ACM SIGSAC Conf. on Computer and Communications Security, ACM, pp, 473–489, . [Google Scholar]
18F. Guo, P. Jiang and K. Liang. (2020), “Searchain: Blockchain-based private keyword search in decentralized storage. ,” Future Generation Computer Systems, vol. 107, no. (2), pp, 781–792, . [Google Scholar]
19H. G. Do and W. K. Ng. (2017), “Blockchain-based system for secure data storage with private keyword search. ,” 2017 IEEE World Congress on Services, vol. 23, pp, 90–93, . [Google Scholar]
20S. Ji, Y. Liu and Y. Ren. (2018), “Incentive mechanism of data storage based on blockchain for wireless sensor networks. ,” Mobile Information Systems, vol. 2018, pp, 6874158, . [Google Scholar]
21Y. Ren, P. K. Sharma and F. Zhu. (2020), “Data query mechanism based on hash computing power of blockchain in internet of things. ,” Sensors, vol. 20, no. (1), pp, 207, . [Google Scholar]
22J. Li, Z. Liu and L. Zu. (2014), “New ciphertext-policy attribute-based encryption with efficient revocation, 2014. ,” in IEEE Int. Conf. on Computer and Information Technology, Xi’an, pp, 281–287, . [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |