DOI:10.32604/cmc.2020.012205

| Computers, Materials & Continua DOI:10.32604/cmc.2020.012205 |  |
| Article |
Secure and Efficient Data Storage and Sharing Scheme Based on Double Blockchain
1College of Information Engineering, Yangzhou University, Yangzhou, 225127, China
2School Math & Computer Science, Quanzhou Normal University, Quanzhou, 362000, China
3Division of Computer Science, University of Aizu, Aizu–Wakamatsu, 9658580, Japan
4Key Laboratory of Intelligent Computing and Signal Processing of Ministry of Education, School of Computer Science and Technology, Anhui University, Hefei, 230601, China
5Medical College of Yangzhou University, Yangzhou, 225001, China
6Department of Gynecology and Obstetrics, Affiliated Hospital of Yangzhou University, Yangzhou, China
7Department of Computer Software Engineering, Soonchunhyang University, Asan, Korea
*Corresponding Author: Lejun Zhang. Email: zhanglejun@yzu.edu.cn
Received: 19 June 2020; Accepted: 19 July 2020
Abstract: In the digital era, electronic medical record (EMR) has been a major way for hospitals to store patients’ medical data. The traditional centralized medical system and semi-trusted cloud storage are difficult to achieve dynamic balance between privacy protection and data sharing. The storage capacity of blockchain is limited and single blockchain schemes have poor scalability and low throughput. To address these issues, we propose a secure and efficient medical data storage and sharing scheme based on double blockchain. In our scheme, we encrypt the original EMR and store it in the cloud. The storage blockchain stores the index of the complete EMR, and the shared blockchain stores the index of the shared part of the EMR. Users with different attributes can make requests to different blockchains to share different parts according to their own permissions. Through experiments, it was found that cloud storage combined with blockchain not only solved the problem of limited storage capacity of blockchain, but also greatly reduced the risk of leakage of the original EMR. Content Extraction Signature (CES) combined with the double blockchain technology realized the separation of the privacy part and the shared part of the original EMR. The symmetric encryption technology combined with Ciphertext-Policy Attribute-Based Encryption (CP–ABE) not only ensures the safe storage of data in the cloud, but also achieves the consistency and convenience of data update, avoiding redundant backup of data. Safety analysis and performance analysis verified the feasibility and effectiveness of our scheme.
Keywords: Cloud storage; blockchain; electronic medical records; access control; data sharing; privacy
With the rapid development of information technology, medical data has become the key to discovering and treating diseases [1]. More and more data is transferred from paper to electronic equipment because of the digitization of electronic storage [2,3]. EMR has been a major way for hospitals to store patients’ medical data. The emergence of EMR has brought great opportunities to the development of wise medical practice [4]. Because the value inherent in EMR has given birth to business entities [5,6], EMR sharing is considered to be a promising approach [7,8]. However, there are few critical problems in this environment. 1) It is difficult for patients to obtain the data stored in the hospital [9]. 2) The conventional solutions are still vulnerable to information loss [10]. 3) Different medical institutions are loath to share their data [11]. To address these issues and meet the high demands on data sharing [12], some researchers proposed to use a third–party cloud instead of a private database for data sharing [13,14], and some cryptographic schemes have been proposed to solve these issues, though the disadvantages still exist [15,16]. For the storage and sharing of EMR, there are still some challenges, such as interoperability [17], data security, and privacy [18,19]. For the hospital, the sheer volume of data stored with third parties is not reassuring [20]. The consistency and interoperability of the different types of data from different medical institutions are big problems for data sharing [21]. The emergence of blockchain ensure security and transparency [22]. In recent years, the distributed healthcare blockchain system [23] has emerged [24,25].
Although the emergence of blockchain provides the possibility to solve these issues, the storage capacity of blockchain is limited and single blockchain schemes have poor scalability and low throughput. To address these issues, we propose an EMR storage and sharing scheme based on double blockchain. The main contributions of this paper are summarized as follows:
1.CES combined with the double blockchain technology realizes the separation of the privacy part and the shared part of the original EMR.
2.Cloud storage combined with the double blockchain technology not only solves the problem of the limited storage capacity of the blockchain and reduces the risk of medical data leakage, but also improves throughput and enhances scalability.
3.The symmetric encryption technology combined with the CP–ABE technology not only ensures the storage security of data in the cloud, but also achieves the consistency and convenience of data update.
The rest of the article is organized as follows: in Section 2, we review the related work about the storage and sharing of EMR, and then discuss their limitations. The related technologies of this paper will be described in Section 3. Next in Section 4, the system model of this paper will be described. In Section 5, the process of EMR storage, sharing and management in this scheme will be described in detail. In Section 6, we will conduct security analysis and performance analysis on our scheme. Finally, Section 7 concludes the paper and illustrates future expansion.
In this section, we outline the research status of cloud services and blockchain technology to achieve secure storage and efficient sharing of EMR.
Zhang et al. [26] propose a secure medical record storage and sharing scheme based on double blockchain. In this article, patients encrypt their EMR with private keys and store them in a third-party cloud server. In fact, there is no reliable third party in the real world. The system designed by Xi et al. [27] is based on a permissioned blockchain which allows access to invited users and verified users. The strict access control reduces the efficiency of EMR sharing. The above two schemes both have the same problem in the sharing process of EMR. When a third party needs to view part of the EMR, the compete EMR must be transmitted. It is easy to leak the privacy of the patient and cause waste of resources. To solve this problem and improve efficiency, scientific researchers have proposed CES. Liu et al. proposed a blockchain—based privacy—preserving data sharing scheme [28]. This scheme uses CES to achieve the separation of the private part and shared part of EMR. After patients remove the private part of the EMR, each shared part is encrypted and uploaded to the cloud, and the indexes are stored in the blockchain. Because the cloud only stores the shared part, the patient cannot retrieve the complete EMR.
The traditional centralized medical system and semi-trusted cloud storage are difficult to achieve a dynamic balance between privacy protection and data sharing. The storage capacity of blockchain is limited and single blockchain schemes have poor scalability and low throughput. To address these issues, we propose a secure and efficient medical data storage and sharing scheme based on double blockchain. In our scheme, we encrypt the original EMR and store it in the cloud. The storage blockchain stores the index of the complete EMR, and the shared blockchain stores the index of the shared part of the EMR. Users with different attributes can make requests to different blockchains to share different parts of the EMR according to their own permissions.
Blockchain technology is the basic technology of Bitcoin [29] invented by the mysterious Satoshi Nakamoto in 2008. The block header contains information such as version number, previous block hash, nonce, Merkle root, timestamp and target difficulty. The blockchain operates in a peer-to-peer manner. After all transactions are broadcast in the blockchain network, all transactions will be allocated to each network maintenance node in the blockchain for verification. Only when 51% of the participating nodes in the blockchain network reach a consensus can the block be validated and added to the blockchain. All legal transactions are stored in data blocks. The basic structure of the blockchain is shown in Fig. 1.
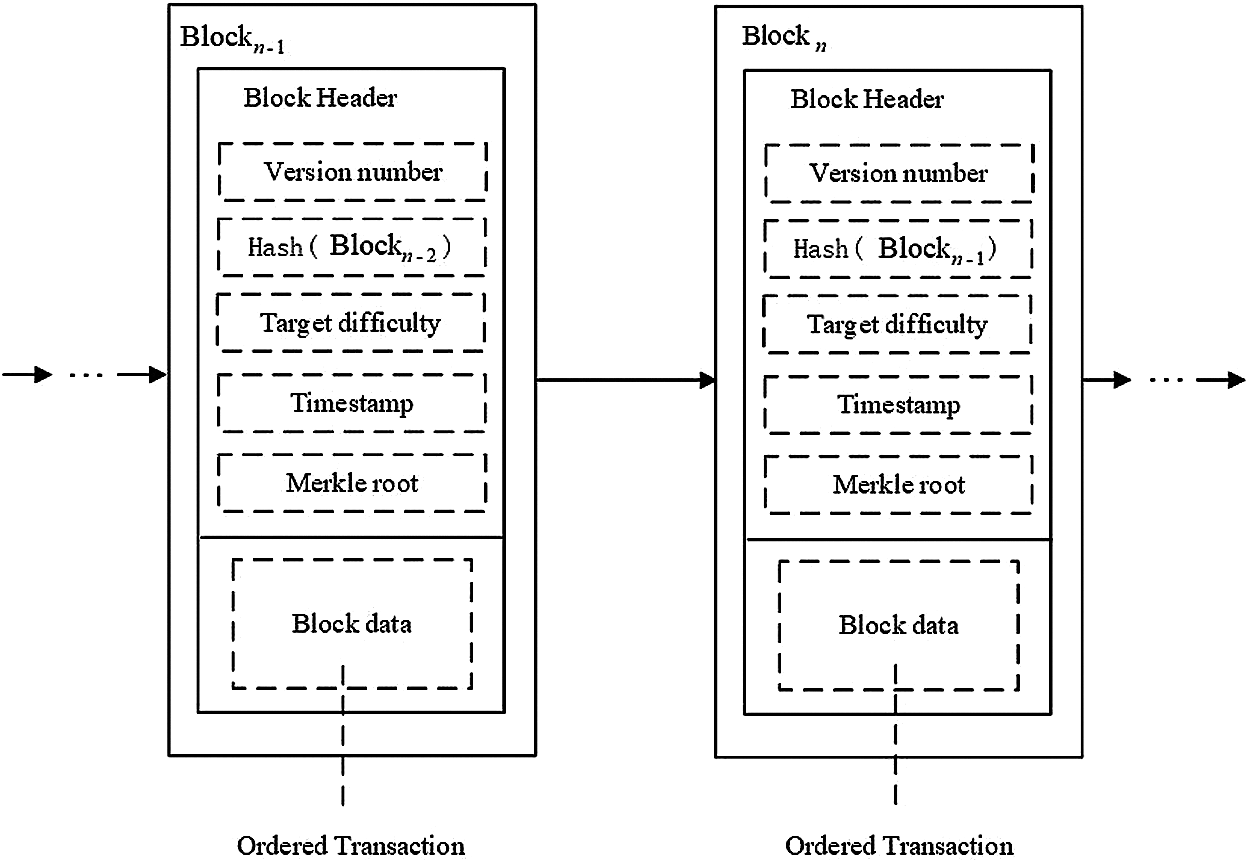
Figure 1: Blockchain basic structure
The concept of smart contract was first proposed in 2014. Although the idea of smart contracts was proposed long ago, it has never been able to be implemented. It was not until the emergence of blockchain technology that it provided a supportable platform for smart contracts. Smart contracts are modular, reusable, and automatically executed scripts that run on the blockchain. Once the preset conditions are met, the smart contract can be performed automatically without a third party, and the results are written into the blockchain. Through using smart contracts, we can achieve trusted transactions, and these transactions are traceable and irreversible. For users who violate smart contracts, the smart contract setter has the right to revoke the user’s authority.
3.3 Content Extraction Signature
When a third party needs to view part of the EMR, the compete EMR must be transmitted. But it is easy to leak patients’ privacy and cause waste of resources. Therefore, there is a need for a digital signature scheme based on fine-grained level which must ensure that users can sign at any granular level and the signer can control the extraction method of the signed content. CES can meet the above requirements, and this method is more efficient in terms of computation and communication. CES allows users to remove private data according to their wishes and extract the shared data [30]. It has been widely used in many fields.
3.4 Ciphertext Policy Attribute Based Encryption
The concept of attribute-based encryption not only realizes one-to-many communication means, but also enhances the information confidentiality. The attribute encryption mechanism is divided into Key Policy Attribute Based Encryption (KP–ABE) and CP–ABE. The specific process is described as follows: Firstly, the authority sets public parameters and master key. Secondly, the data owner can define his own access control policy. The ciphertext adopts a tree structure to describe the access policy. Thirdly, the data owner encrypts the message to form a ciphertext. Fourthly, after users submit their attributes to the certification authority, they will obtain their own public key and private key. Finally, only when their attributes satisfied the access policy, the user can decrypt the ciphertext.
4 EMR Storage and Sharing Model Based on Double Blockchain
Notations and corresponding descriptions are given in Tab. 1.
As shown in Fig. 2, our model is divided into three layers. The role of these three layers is introduced as follows.
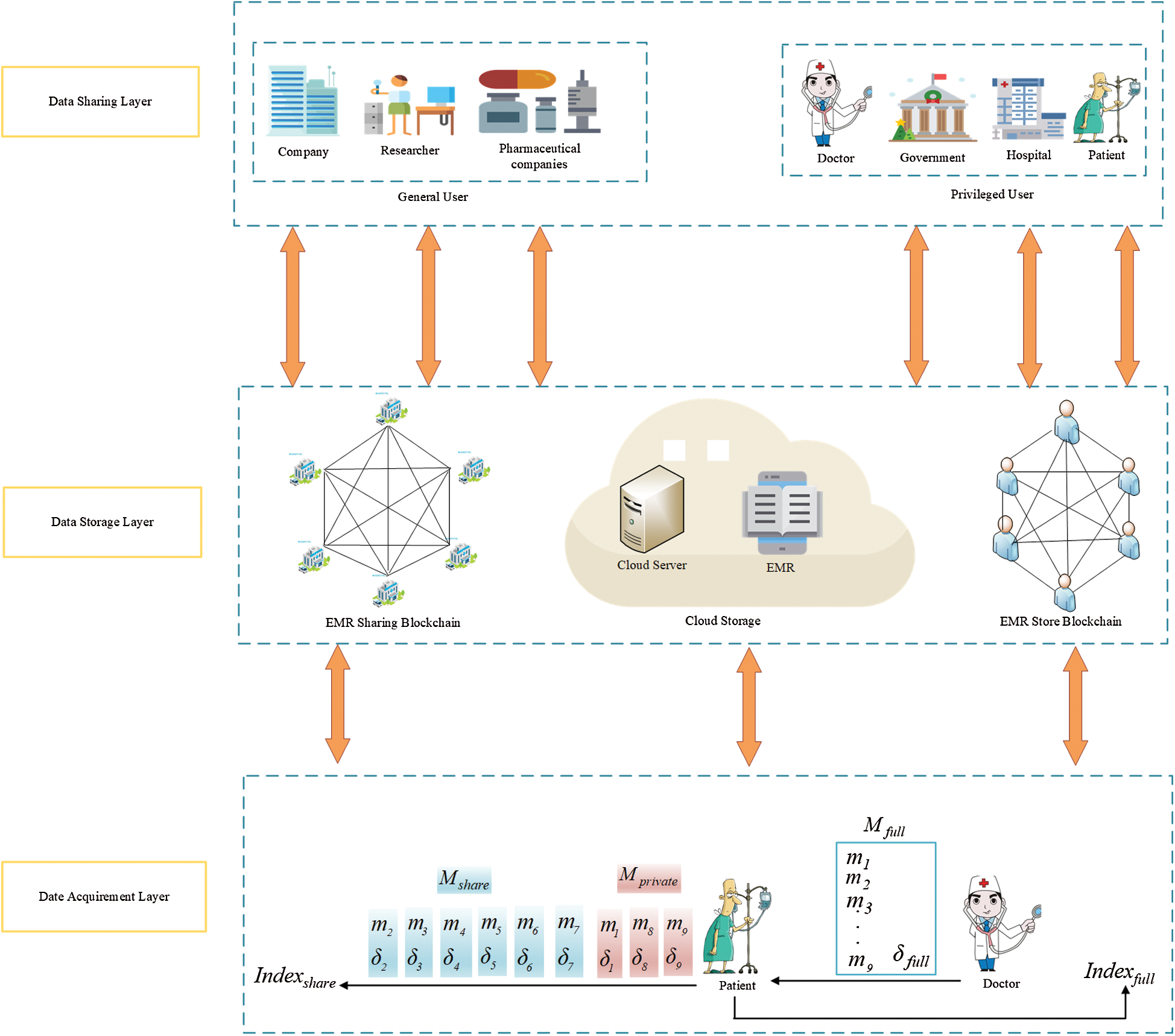
Figure 2: System overall framework
Data Acquirement Layer. In the data acquirement layer,  generates
generates 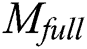 and
and 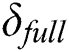 .
. 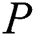 can extract the sub-messages from
can extract the sub-messages from 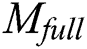 . After
. After  uploads corresponding information to the cloud, the cloud will return
uploads corresponding information to the cloud, the cloud will return 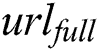 .
. 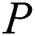 can generate
can generate 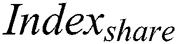 and
and 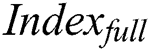 according to
according to 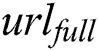 .
.
Data Storage Layer. The main function of this layer is to store  ,
, 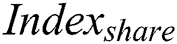 and
and 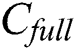 . We use the storage blockchain to store
. We use the storage blockchain to store  and use the shared blockchain to store
and use the shared blockchain to store 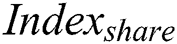 . The cloud stores the ciphertext of sub-message, the corresponding symmetric key ciphertext, and the signature of the sub-message.
. The cloud stores the ciphertext of sub-message, the corresponding symmetric key ciphertext, and the signature of the sub-message.
Data Sharing Layer. We achieve the data sharing of 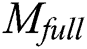 and
and 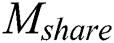 .
. 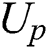 can obtain
can obtain 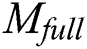 after making a request to the storage blockchain.
after making a request to the storage blockchain. 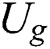 can send requests to the sharing blockchain to achieve sharing
can send requests to the sharing blockchain to achieve sharing 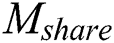 .
.
5 EMR Storage and Sharing Scheme Based on Double Blockchain
5.1 EMR Storage Based on Double Blockchain
5.1.1 EMR Storage Based on Double Blockchain
It is assumed that EMR contains 9 parts: Name, gender, date of birth, 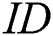 number, symptoms, diagnosis result, prescription, medical examination report and medical history,
number, symptoms, diagnosis result, prescription, medical examination report and medical history, 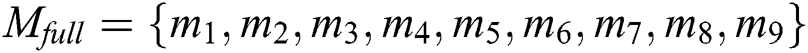 ,
, 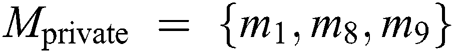 ,
, 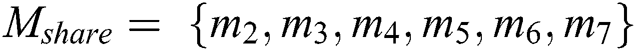 . Because the complete signature generation requires key pair, we first introduce key pair generation method.
. Because the complete signature generation requires key pair, we first introduce key pair generation method.
Key generation: Firstly, the certification authority randomly selects two unequal prime numbers: 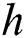 and
and 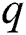 . Secondly, the certification authority calculates
. Secondly, the certification authority calculates 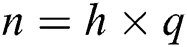 and sets Euler function:
and sets Euler function: 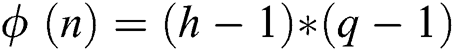 . Thirdly,
. Thirdly,  randomly selects an integer
randomly selects an integer  that is prime with
that is prime with 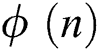 in the interval
in the interval 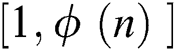 , and find an integer
, and find an integer 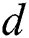 to satisfy
to satisfy 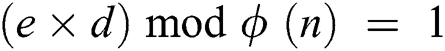 . Finally, according to the above calculation,
. Finally, according to the above calculation, 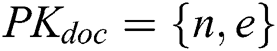 .
. 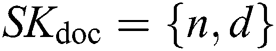 .
.
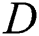 will use the generated key pair to generate
will use the generated key pair to generate 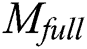 ’s
’s 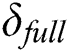 based on the complete signature generation algorithm.
based on the complete signature generation algorithm.
Algorithm name: The complete signature generation algorithm
Input: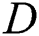 ’s private key,
’s private key, 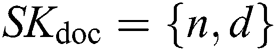 ;
; 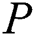 ’s EMR,
’s EMR, 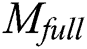
Output: The full signature, 
1) int 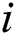 = 1; //Parameter for cyclic control
= 1; //Parameter for cyclic control
2) for (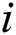 = 1;
= 1;  <= 9;
<= 9; 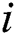 ++) {
++) {
3) Select a CES–Tag randomly with a fixed length, defined as 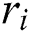 ;}
;}
4) for (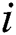 = 1;
= 1; 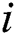 <= 9;
<= 9; 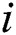 ++) {
++) {
5) 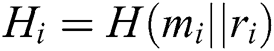 ;} //The symbol || stands for connection, calculate the hash value of the sub-message connected with random number
;} //The symbol || stands for connection, calculate the hash value of the sub-message connected with random number
6) 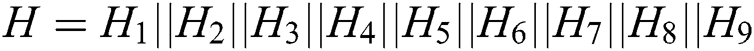 ; // Connect the values of
; // Connect the values of 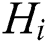 together
together
7) 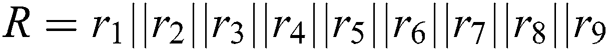 ; //Connect the values of
; //Connect the values of 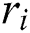 together
together
8) 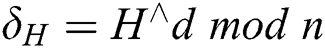 ; //Sign a with
; //Sign a with 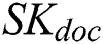
9) 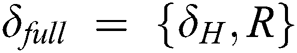 ;
;
10) return 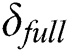 ;
;
In order to ensure the transmission security of data, 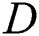 will use his symmetric encryption key
will use his symmetric encryption key 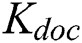 to encrypt
to encrypt 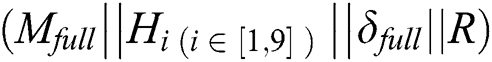 , and use
, and use 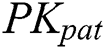 to encrypt
to encrypt 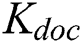 . Then
. Then 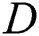 sends the set of two encrypted information
sends the set of two encrypted information 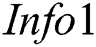 to
to 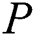 , the set formula is shown in Eq. (1).
, the set formula is shown in Eq. (1).
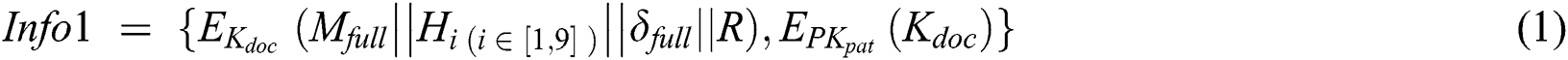
5.1.2 Extraction of Sub-Messages
In this section, CES realizes the separation of the privacy part and the shared part. After  receive the set of two encrypted information
receive the set of two encrypted information 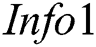 ,
, 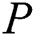 first decrypt ciphertext of
first decrypt ciphertext of 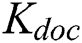 with
with 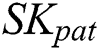 and obtains
and obtains 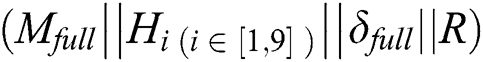 further. In order to ensure the integrity and authenticity of the data,
further. In order to ensure the integrity and authenticity of the data, 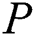 will verify the correctness of
will verify the correctness of 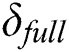 . 1) For each sub-message
. 1) For each sub-message 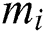 ,
, 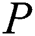 calculate the hash value
calculate the hash value 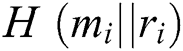 , where
, where 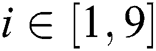 .
. 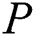 determine whether the calculated hash value is equal to the hash value obtained in the decrypted message. If they are equal, go to step two. 2)
determine whether the calculated hash value is equal to the hash value obtained in the decrypted message. If they are equal, go to step two. 2) 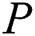 verify the correctness of
verify the correctness of 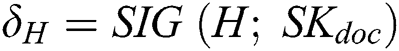 using
using  and calculate
and calculate 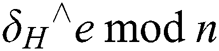 , If the calculation result is equal to
, If the calculation result is equal to 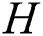 ,
, 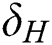 is a valid signature.
is a valid signature.
After 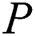 ensure that EMR and
ensure that EMR and 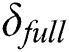 is accurate,
is accurate, 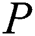 can extract each sub-message from EMR. We assume that the subset to be extracted is defined as
can extract each sub-message from EMR. We assume that the subset to be extracted is defined as 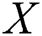 . The extraction signature generation algorithm is as follows.
. The extraction signature generation algorithm is as follows. 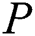 can generate a signature corresponding to the sub-message according to the extraction signature generation algorithm. Therefore, the corresponding signature of the privacy part is
can generate a signature corresponding to the sub-message according to the extraction signature generation algorithm. Therefore, the corresponding signature of the privacy part is 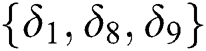 , and the corresponding signature of the shared part data is
, and the corresponding signature of the shared part data is 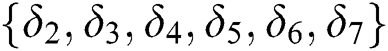 .
.
Algorithm name: The extraction signature generation algorithm
Input: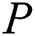 ’s EMR,
’s EMR, 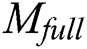 ; EMR’s full signature,
; EMR’s full signature, 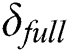 ; The subset to be extracted,
; The subset to be extracted, 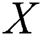
Output: Extract signature of subset to be extracted, 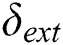
1) int 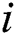 = 1; //Parameter for cyclic control
= 1; //Parameter for cyclic control
2) 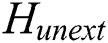 = null; //
= null; //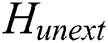 represents the hash value of the unextracted message, the initial value is null.
represents the hash value of the unextracted message, the initial value is null.
3) 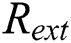 = null; //
= null; //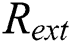 represents the random number of the extracted message, the initial value is null.
represents the random number of the extracted message, the initial value is null.
4) for (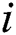 = 1;
= 1; 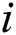 <= 9;
<= 9; 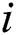 ++) {
++) {
5) Extract 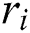 from
from  ;}
;}
6) for (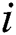 = 1;
= 1; 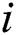 <= 9;
<= 9; 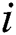 ++) {
++) {
7) if (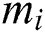 ∉
∉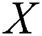 ) {
) {
8) 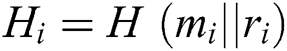 ;
;
9) 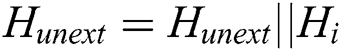 ; }
; }
10) else {
11) 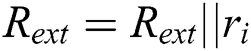 ;}}
;}}
12) 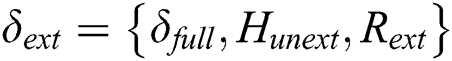 ;
;
13) return 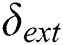
5.1.3 Encryption of Sub-Messages
In this section, the symmetric encryption technology combined with CP–ABE not only ensures the safe storage of data in the cloud, but also achieves the consistency and convenience of data update, avoiding redundant backup of data. After 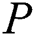 extract each sub-message from EMR and generate an extraction signature corresponding to the sub-message, two different encryption methods need to be performed in sequence.
extract each sub-message from EMR and generate an extraction signature corresponding to the sub-message, two different encryption methods need to be performed in sequence.
Firstly, 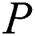 will use different symmetric encryption keys to encrypt each sub-message. The encryption method is shown in Eq. (2).
will use different symmetric encryption keys to encrypt each sub-message. The encryption method is shown in Eq. (2).

Secondly, 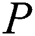 set different access control policies for different symmetric encryption keys
set different access control policies for different symmetric encryption keys 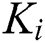 , where
, where 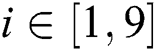 ,
, 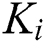 ’s
’s 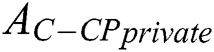 is shown in Fig. 3, where
is shown in Fig. 3, where 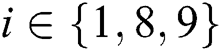 .
. 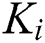 ’s
’s 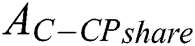 is shown in Fig. 4, where
is shown in Fig. 4, where 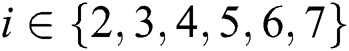 . The ciphertext
. The ciphertext 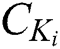 is generated as shown in Eq. (3), where
is generated as shown in Eq. (3), where 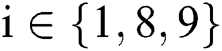 . The ciphertext
. The ciphertext 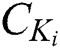 is generated as shown in Eq. (4), where
is generated as shown in Eq. (4), where 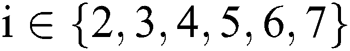 .
.
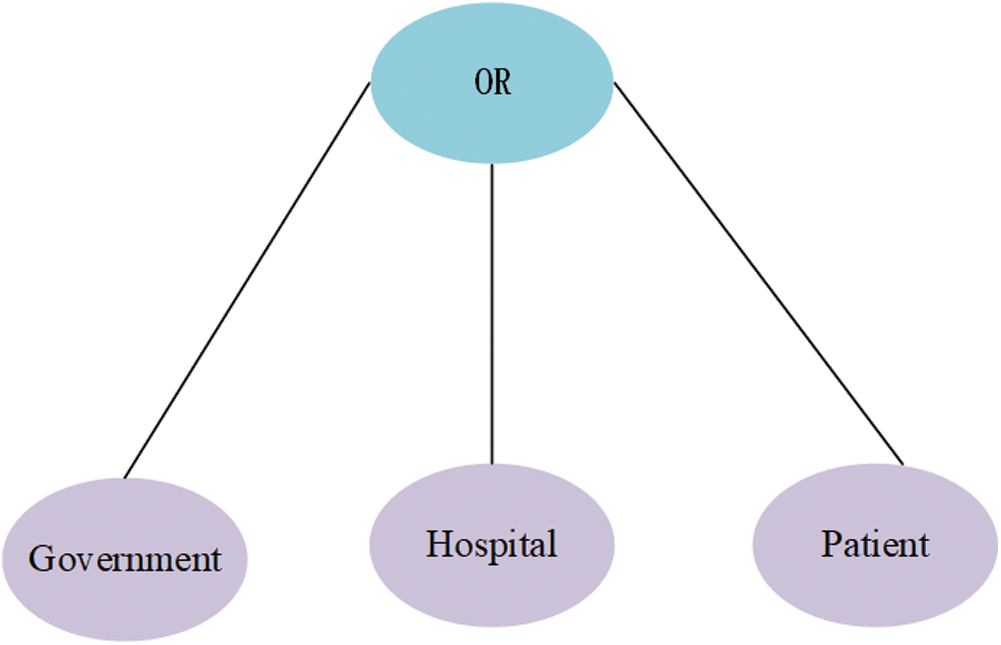
Figure 3: 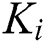 ’s tree structure access control policy,
’s tree structure access control policy, 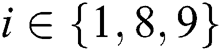
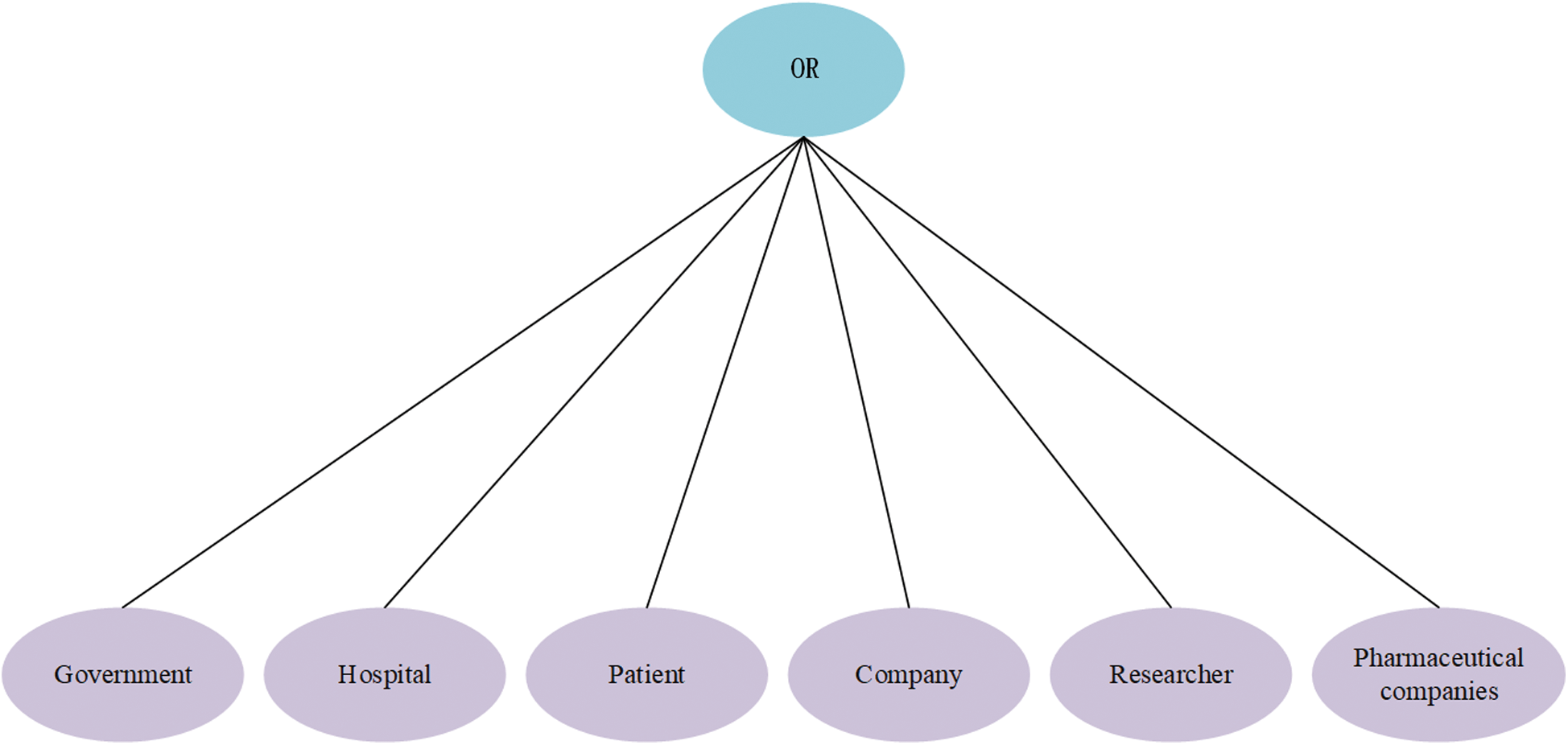
Figure 4: Ki’s tree structure access control policy, i ∈ {2,3,4,5,6,7}
After  uploads the ciphertext to the cloud,
uploads the ciphertext to the cloud,  will receive the storage address
will receive the storage address 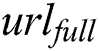 . The ciphertext stored in the cloud is shown in Eq. (5).
. The ciphertext stored in the cloud is shown in Eq. (5).
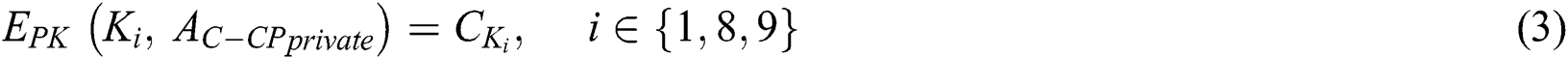
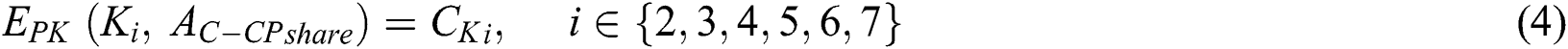

In this section,  generates indexes of
generates indexes of 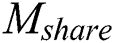 and
and 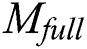 respectively according to
respectively according to 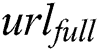 . The two index generation methods are introduced as follows.
. The two index generation methods are introduced as follows.
 Indexshare generation: After
Indexshare generation: After 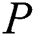 receive
receive 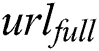 ,
, 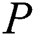 first use
first use 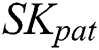 to sign the two parts of
to sign the two parts of 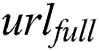 and
and 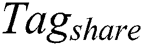 , the generated signature is defined as
, the generated signature is defined as 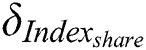 , then
, then 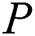 use
use 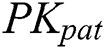 to encrypt
to encrypt 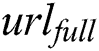 ,
, 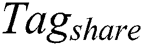 and
and  . The encryption result combined with
. The encryption result combined with  generates
generates 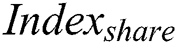 . Finally,
. Finally, 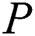 store
store 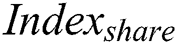 to shared blockchain.
to shared blockchain. 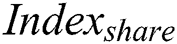 generation process is shown in Eq. (6).
generation process is shown in Eq. (6).
 Indexfull generation: The process of
Indexfull generation: The process of 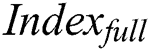 generation is similar to the process of
generation is similar to the process of 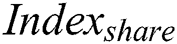 generation.
generation. 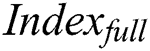 generation process is shown in Eq. (7).
generation process is shown in Eq. (7).

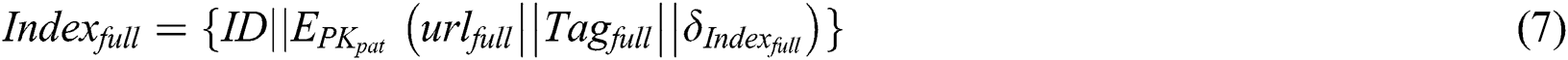
In this section, unlike traditional index release, A double blockchain structure is used to achieve index release. The storage blockchain stores the index of the complete EMR, and the shared blockchain stores the index of the shared part. The detailed process is described as follows. 1)  use
use  to sign
to sign 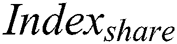 and
and 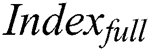 respectively and get the signatures
respectively and get the signatures 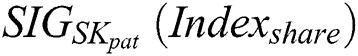 and
and 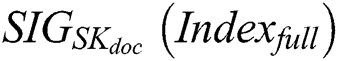 . 2) After
. 2) After 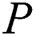 generate the signature and calculating the index hash,
generate the signature and calculating the index hash, 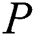 will send a request
will send a request 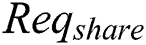 to the shared blockchain to request storage
to the shared blockchain to request storage 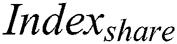 , the request generation process is shown in Eq. (8).
, the request generation process is shown in Eq. (8). 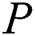 will also send a request
will also send a request 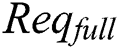 to the storage blockchain to request storage
to the storage blockchain to request storage 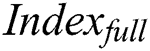 , the request generation process is shown in Eq. (9).
, the request generation process is shown in Eq. (9).
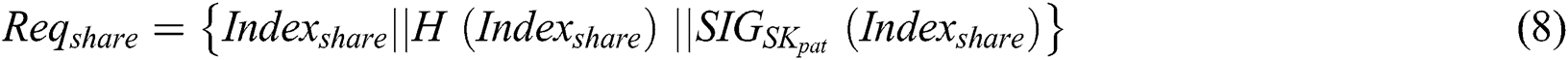
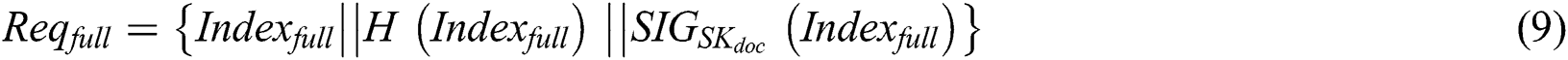
In the next section, 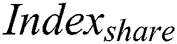 and
and 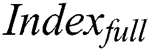 are collectively referred to as
are collectively referred to as 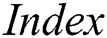 .
. 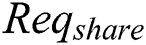 and
and 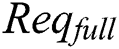 are collectively referred to as
are collectively referred to as 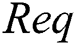 . Consensus process is described as follows.
. Consensus process is described as follows.
(1) The master node will verify and collect legal transactions in a data set 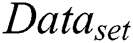 , the generation method of the data set is shown in Eq. (10). The master node will broadcast
, the generation method of the data set is shown in Eq. (10). The master node will broadcast 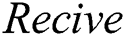 to all consensus nodes for verification. The hash value of the data set is shown in Eq. (11), and the set
to all consensus nodes for verification. The hash value of the data set is shown in Eq. (11), and the set 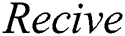 is shown in Eq. (12).
is shown in Eq. (12).


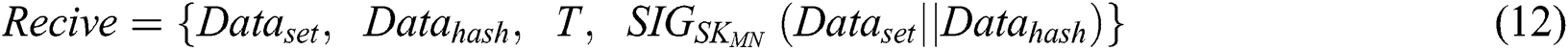
(2) If more than 50% of the consensus nodes agree, this means that new blocks are successfully created, the data will be uploaded to the blockchain. 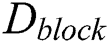 is shown in Eq. (13). The public key of the consensus node is defined as
is shown in Eq. (13). The public key of the consensus node is defined as 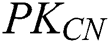 .
.
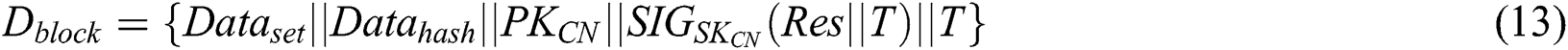
5.2 EMR Sharing Based on Double Blockchain
5.2.1 Double Blockchain Access Authentication
In order to achieve the sharing of EMR, first of all, patients first need to make a request to the blockchain to obtain the cloud data storage address. The steps to obtain the cloud data storage address are the same for both sharing 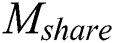 and sharing
and sharing 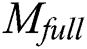 .
. 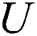 initiates an EMR request transaction
initiates an EMR request transaction 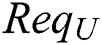 to the blockchain network. The request
to the blockchain network. The request 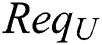 is shown in Eq. (14). Once the preset conditions are met, the smart contract can be performed automatically without a third party, and the results are written into the blockchain. Through using smart contracts, we can achieve trusted transactions, and these transactions are traceable and irreversible. For users who violate smart contracts, the smart contract setter has the right to revoke the user’s authority.
is shown in Eq. (14). Once the preset conditions are met, the smart contract can be performed automatically without a third party, and the results are written into the blockchain. Through using smart contracts, we can achieve trusted transactions, and these transactions are traceable and irreversible. For users who violate smart contracts, the smart contract setter has the right to revoke the user’s authority.

In this section, 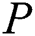 will obtain the ciphertext stored in the cloud according to the obtained index. The detailed process is described as follows.
will obtain the ciphertext stored in the cloud according to the obtained index. The detailed process is described as follows.
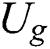 first send a request to the sharing blockchain. If the request meets the access control preset by the smart contract, the smart contract will be automatically induced to use
first send a request to the sharing blockchain. If the request meets the access control preset by the smart contract, the smart contract will be automatically induced to use 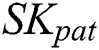 to decrypt
to decrypt 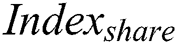 , then
, then 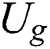 can obtain
can obtain 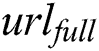 ,
, 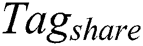 and
and 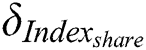 . After
. After 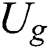 submits these data to the cloud server, the cloud server will verify the correctness of the signature, if the signature is correct, the cloud server will send the ciphertext
submits these data to the cloud server, the cloud server will verify the correctness of the signature, if the signature is correct, the cloud server will send the ciphertext 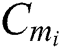 , the corresponding symmetric encryption key ciphertext
, the corresponding symmetric encryption key ciphertext 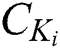 and the corresponding signature
and the corresponding signature 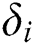 to
to 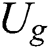 , where
, where 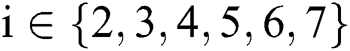 .
.
The process of  requesting to share
requesting to share 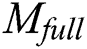 is similar to
is similar to 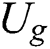 requesting to share
requesting to share 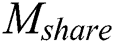 .
.
5.2.3 Ciphertext Decryption and Verification
In order to decrypt and verify the obtained ciphertext, 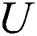 first submit
first submit  to the authorized institution. After the authorized institution verifies the accuracy of the attribute of
to the authorized institution. After the authorized institution verifies the accuracy of the attribute of 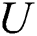 , the authorized institution will generate
, the authorized institution will generate 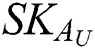 , then the authorized institution sends
, then the authorized institution sends 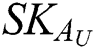 and
and 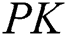 to
to 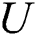 . Therefore, the public key of
. Therefore, the public key of 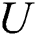 is
is 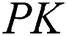 and the private key is
and the private key is 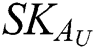 . Because different data users have different permissions, the decryption of ciphertext is divided into two parts:
. Because different data users have different permissions, the decryption of ciphertext is divided into two parts: 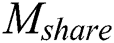 ciphertext decryption and
ciphertext decryption and 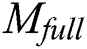 ciphertext decryption. The following two detailed decryption processes are introduced as follows.
ciphertext decryption. The following two detailed decryption processes are introduced as follows.
(1) 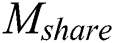 ciphertext decryption
ciphertext decryption
After 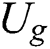 obtain the shared part ciphertext
obtain the shared part ciphertext 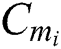 , the corresponding symmetric encryption key ciphertext
, the corresponding symmetric encryption key ciphertext 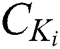 and the corresponding signature
and the corresponding signature 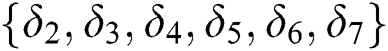 , where
, where 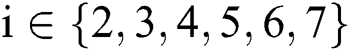 .
. 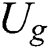 will first decrypt the symmetric encryption key ciphertext, decryption process is shown in Eq. (15). Then
will first decrypt the symmetric encryption key ciphertext, decryption process is shown in Eq. (15). Then 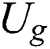 use the obtained symmetric encryption key to decrypt
use the obtained symmetric encryption key to decrypt 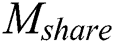 ciphertext, decryption process is shown in Eq. (16). Therefore,
ciphertext, decryption process is shown in Eq. (16). Therefore, 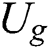 have realized the sharing of
have realized the sharing of 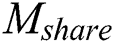 .
.
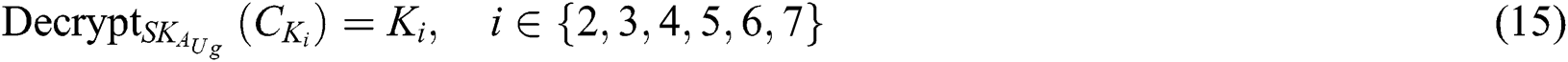
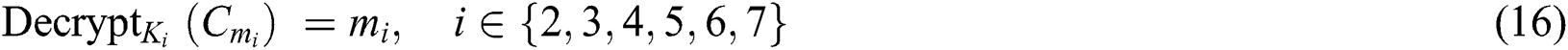
(2) 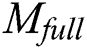 ciphertext decryption.
ciphertext decryption.
After 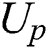 obtain the shared part ciphertext
obtain the shared part ciphertext 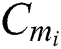 , the corresponding symmetric encryption key ciphertext
, the corresponding symmetric encryption key ciphertext 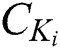 and the corresponding signature
and the corresponding signature 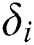 , where
, where 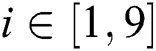 .
. 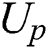 will first decrypt the symmetric encryption key ciphertext, decryption process is shown in Eq. (17), then
will first decrypt the symmetric encryption key ciphertext, decryption process is shown in Eq. (17), then 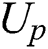 use the obtained symmetric encryption key to decrypt
use the obtained symmetric encryption key to decrypt 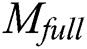 ciphertext, decryption process is shown in Eq. (18). Therefore,
ciphertext, decryption process is shown in Eq. (18). Therefore, 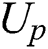 have realized the sharing of
have realized the sharing of 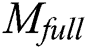 .
.


5.3 EMR Management Based on Double Blockchain
5.3.1 Definition of Sub-Message
In our scheme, 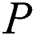 have the absolute right to use and control EMR. and patients should be able to redefine the privacy and shared parts according to their wishes.
have the absolute right to use and control EMR. and patients should be able to redefine the privacy and shared parts according to their wishes.
Next a real scene will be described, assume that 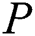 need to define the medical examination report
need to define the medical examination report 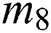 that was originally private data as shared data. In our scheme,
that was originally private data as shared data. In our scheme, 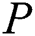 only need to change the original access policy from
only need to change the original access policy from 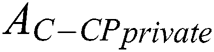 to
to 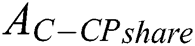 , and then re-encrypt
, and then re-encrypt 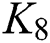 to obtain a new ciphertext
to obtain a new ciphertext 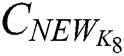 , encryption process is shown in Eq. (19). After obtaining the new ciphertext
, encryption process is shown in Eq. (19). After obtaining the new ciphertext 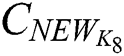 ,
,  only need to replace the original ciphertext
only need to replace the original ciphertext 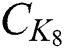 with the new one
with the new one 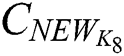 . Through the above simple process,
. Through the above simple process, 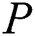 can redefine the privacy and shared parts.
can redefine the privacy and shared parts.

5.3.2 Definition of User Rights
For 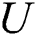 who violate the treaty,
who violate the treaty, 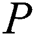 should have the right to revoke
should have the right to revoke 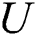 ’s authority. Therefore, the redefinition of user rights is very significant for
’s authority. Therefore, the redefinition of user rights is very significant for 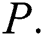
Next a real scene will be described, suppose 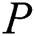 define the government that was originally
define the government that was originally 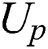 as
as 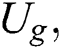 and
and 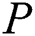 define the researchers who were originally as
define the researchers who were originally as 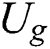 as
as 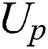 . In our scheme,
. In our scheme, 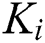 ’s access control policy need to change from
’s access control policy need to change from 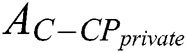 to
to 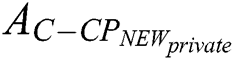 , where
, where 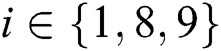 .
. 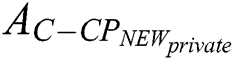 is shown in Fig. 5.
is shown in Fig. 5. 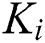 ’s access control policy need to change from
’s access control policy need to change from 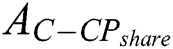 to
to 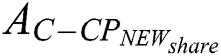 , where
, where 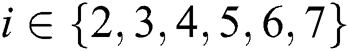 .
. 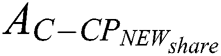 is shown in Fig. 6.
is shown in Fig. 6. 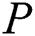 need to encrypt
need to encrypt 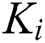 to obtain a new ciphertext
to obtain a new ciphertext 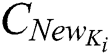 using a new access strategy
using a new access strategy 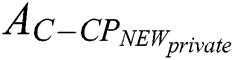 , where
, where 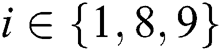 . The encryption process is shown in Eq. (20), then
. The encryption process is shown in Eq. (20), then  need to encrypt
need to encrypt  to obtain a new ciphertext
to obtain a new ciphertext 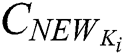 using a new access strategy
using a new access strategy 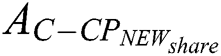 , where
, where 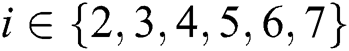 . The encryption process is shown in Eq. (21). Through the above simple process,
. The encryption process is shown in Eq. (21). Through the above simple process,  can redefine user rights.
can redefine user rights.
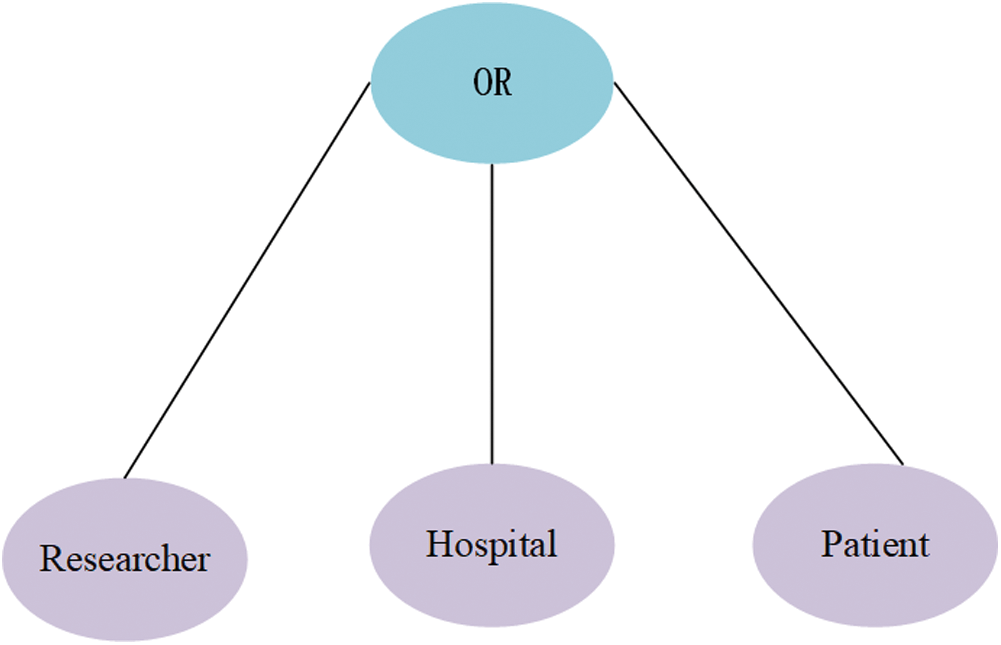
Figure 5: 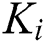 ’s tree structure access control policy
’s tree structure access control policy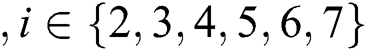
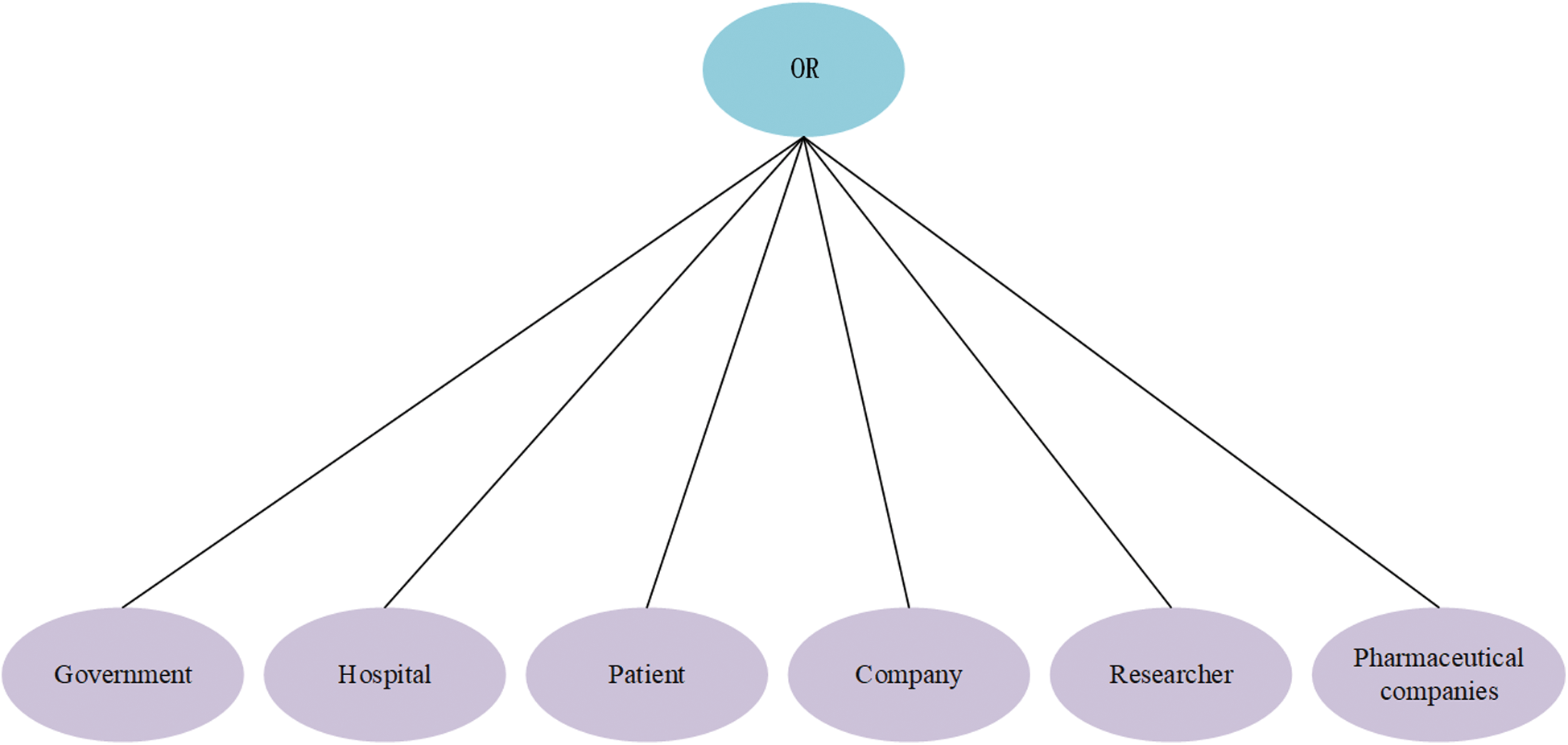
Figure 6: 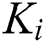 ’s tree structure access control policy
’s tree structure access control policy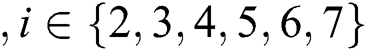
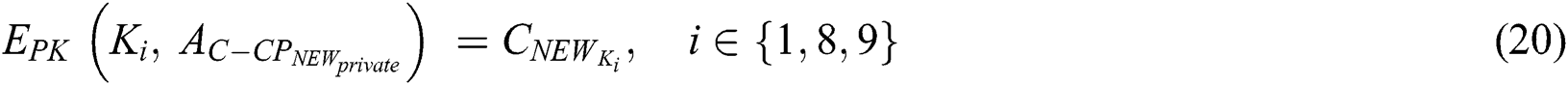
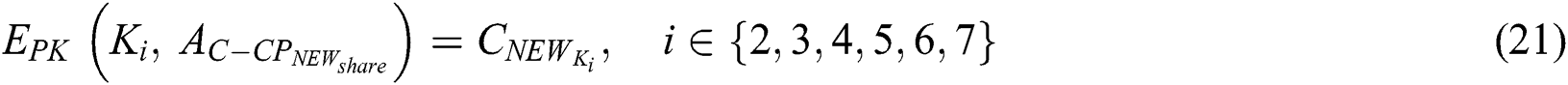
Security is a key issue in EMR sharing. Here, we analyze the security of our scheme from the following four aspects.
1.Anti-tampering: Our scheme encrypts the original EMR and stores it in the cloud,  Indexfull is stored in the storage blockchain. Indexshare is stored in the shared blockchain. Therefore, the tamper-proof feature of the blockchain ensures that the original EMR stored in our cloud are immutable and cannot be modified arbitrarily.
Indexfull is stored in the storage blockchain. Indexshare is stored in the shared blockchain. Therefore, the tamper-proof feature of the blockchain ensures that the original EMR stored in our cloud are immutable and cannot be modified arbitrarily.
2.Privacy protection: In our scheme, the semi-trusted cloud cannot obtain the plaintext of EMR. Compared with setting strict access control, P can separate the private part and shared part of the EMR according to their own wishes in our scheme, the double blockchain technology also realizes the separation of the private data and shared data. Our scheme achieves true privacy protection.
3.Data consistency: In order to realize that users with different attributes can access different parts, the cloud needs to store a complete EMR and a shared part in traditional schemes. While in our scheme, we use CP–ABE technology to encrypt Mshare and Mprivate separately so that the cloud only needs to store an original EMR, ensuring the consistency of data update and avoiding redundant backup of data.
4.Data integrity: From the generation of the complete EMR, to the extraction of the privacy and shared parts, and then to storage and sharing. Throughout these processes, our scheme ensures the integrity and accuracy of EMR.
6.2.1 Cloud Storage Efficiency Analysis
We compare the amount of data that the three schemes of traditional scheme, BPDS and our scheme need to store in the cloud, as shown in Tab. 2.
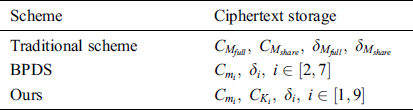
From Tab. 2 we can see the comparison of the amount of data that the traditional scheme and our scheme. The cloud needs to store 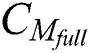 ,
, 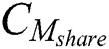 ,
, 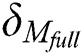 and
and 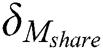 in the traditional scheme. Our scheme only needs to store
in the traditional scheme. Our scheme only needs to store 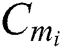 ,
, 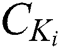 and
and 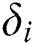 , where
, where 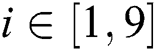 , there is no need to back up
, there is no need to back up 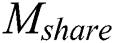 . Although our scheme stores symmetric encryption ciphertext and signature of the key, the amount of these data is very small compared to
. Although our scheme stores symmetric encryption ciphertext and signature of the key, the amount of these data is very small compared to 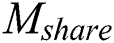 . Our scheme not only ensures the safe storage of data in the cloud, but also achieves the consistency and convenience of data update, avoiding redundant backup of data.
. Our scheme not only ensures the safe storage of data in the cloud, but also achieves the consistency and convenience of data update, avoiding redundant backup of data.
From Tab. 2 we can see the comparison of the amount of data between 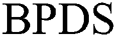 scheme and our scheme.
scheme and our scheme. 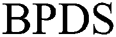 scheme only needs to store
scheme only needs to store 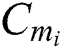 ,
,  in the cloud, where
in the cloud, where 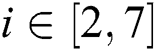 , while our scheme needs to stored
, while our scheme needs to stored 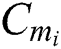 ,
, 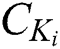 ,
, 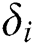 in the cloud, where
in the cloud, where  . Although our scheme stores more data, our scheme does not cause redundant backup of data. Compared with
. Although our scheme stores more data, our scheme does not cause redundant backup of data. Compared with 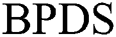 scheme, our scheme can realize that
scheme, our scheme can realize that 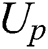 can access
can access 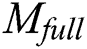 and
and 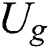 can access
can access 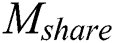 .
.
It is assumed that the number of sub-messages in each complete EMR is 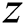 , the number of sub-messages in the shared part is
, the number of sub-messages in the shared part is 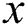 and the number of sub-messages in the privacy part is
and the number of sub-messages in the privacy part is 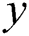 .
. 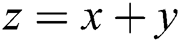 . In the BPDS scheme, when
. In the BPDS scheme, when 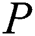 upload an EMR to the cloud, they need to upload the sub-messages of the shared part separately. But in our scheme,
upload an EMR to the cloud, they need to upload the sub-messages of the shared part separately. But in our scheme, 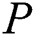 only need to upload the EMR once.
only need to upload the EMR once.
The above results show that the amount of data that our scheme needs to store in the cloud is between the traditional scheme and  scheme. Compared with the traditional scheme, our scheme saves storage space in cloud storage. Compared with
scheme. Compared with the traditional scheme, our scheme saves storage space in cloud storage. Compared with  scheme, our scheme saves the time of uploading EMR and the time of index generation, our scheme also provides better server quality.
scheme, our scheme saves the time of uploading EMR and the time of index generation, our scheme also provides better server quality.
6.2.2 Blockchain Storage Efficiency Analysis
When 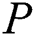 need to store and share his own EMR,
need to store and share his own EMR,  need to store these
need to store these 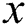 indexes into the blockchain in
indexes into the blockchain in  scheme. But in our scheme,
scheme. But in our scheme, 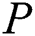 only need to store the index of the complete EMR in the storage blockchain, and store the index of the shared part in the shared blockchain. The storage capacity of the blockchain is limited, our scheme better realizes the storage of the indexes and reduces the burden of blockchain storage.
only need to store the index of the complete EMR in the storage blockchain, and store the index of the shared part in the shared blockchain. The storage capacity of the blockchain is limited, our scheme better realizes the storage of the indexes and reduces the burden of blockchain storage.
6.2.3 Blockchain Sharing Efficiency Analysis
In 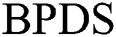 scheme, all users request to share the shared part of the EMR on a blockchain. Because each sub-message of the shared part is separate,
scheme, all users request to share the shared part of the EMR on a blockchain. Because each sub-message of the shared part is separate, 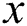 request needs to be issued for the sharing of an EMR. But in our scheme, we adopt a tamper-proof double blockchain structure to distinguish users, at the same time, users only need to issue one request on a blockchain. Compared with
request needs to be issued for the sharing of an EMR. But in our scheme, we adopt a tamper-proof double blockchain structure to distinguish users, at the same time, users only need to issue one request on a blockchain. Compared with 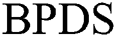 scheme, our efficiency has improved a lot. The experimental results are shown in Figs. 7 and 8.
scheme, our efficiency has improved a lot. The experimental results are shown in Figs. 7 and 8.
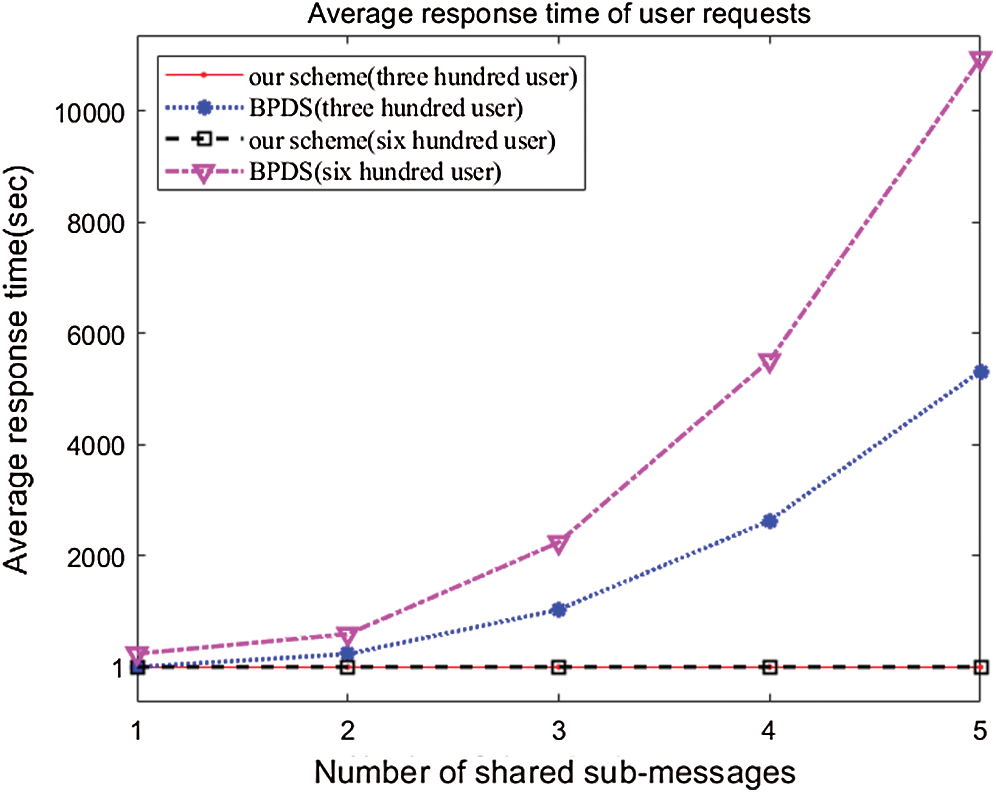
Figure 7: Response time of user requests when number of users and shared sub-messages is different
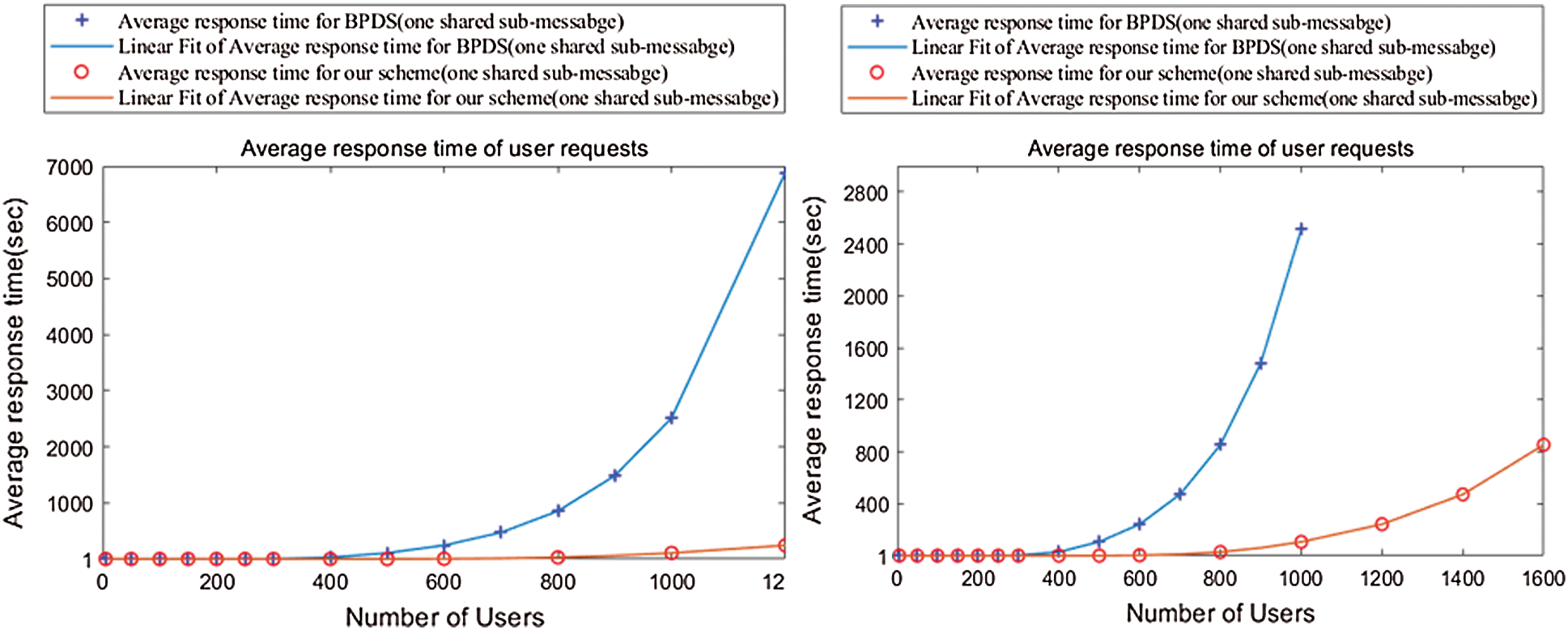
Figure 8: Average response time of user requests when number of users is different
As can be seen from Fig. 7, when the number of users in the system is fixed, as the number of sub-messages increases, the response time for processing user requests continues to increase in  scheme. The reason is that each sub-message in
scheme. The reason is that each sub-message in  scheme is separated. However, in our scheme, our cloud stores a complete EMR, so the response time for processing user requests is not affected by the number of sharing sub-messages.
scheme is separated. However, in our scheme, our cloud stores a complete EMR, so the response time for processing user requests is not affected by the number of sharing sub-messages.
As can be seen from Fig. 8, when the number of users does not exceed the carrying capacity of the system, our scheme and BPDS scheme can still quickly process user requests, but as the number of users increases, the double blockchain structure has more and more obvious advantages compared with the traditional single blockchain, in the meanwhile, the double blockchain structure allows users with different attributes to request sharing on different blockchains.
6.2.4 Analysis of EMR Update Efficiency
(1) Definition of sub-message: When 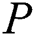 need to redefine whether the sub-message of the EMR belongs to private data or shared data in
need to redefine whether the sub-message of the EMR belongs to private data or shared data in 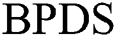 scheme,
scheme, 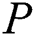 cannot reset the privacy and shared parts of EMR. But in our scheme, after extracting all the sub-messages of the EMR,
cannot reset the privacy and shared parts of EMR. But in our scheme, after extracting all the sub-messages of the EMR, 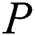 only need to re-encrypt the symmetric encryption key corresponding to the sub-message, and replace the original symmetric encryption key ciphertext.
only need to re-encrypt the symmetric encryption key corresponding to the sub-message, and replace the original symmetric encryption key ciphertext.
(2) Definition of user rights: EMR that has been uploaded to the cloud should exist as a kind of historical data. When 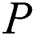 need to redefine user rights,
need to redefine user rights, 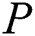 need to re-encrypt the EMR and upload them to the cloud in
need to re-encrypt the EMR and upload them to the cloud in 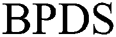 scheme. The replacement of the original EMR will often lead to inconsistencies in the data. But in our scheme, re-encrypting symmetric encryption keys can realize the redefinition of user rights without changing and replacing the original EMR, our scheme ensures data update consistency and convenience.
scheme. The replacement of the original EMR will often lead to inconsistencies in the data. But in our scheme, re-encrypting symmetric encryption keys can realize the redefinition of user rights without changing and replacing the original EMR, our scheme ensures data update consistency and convenience.
The traditional centralized medical system and semi-trusted cloud storage are difficult to achieve a dynamic balance between privacy protection and data sharing. The traditional EMR storage and sharing scheme based on a single blockchain has poor scalability and low throughput. Our paper proposes an EMR storage and sharing scheme based on double blockchain. The original EMR is encrypted and stored in a semi-trusted cloud. We use a tamper-proof double blockchain structure to store the index of the complete EMR and the index of the shared part. Double blockchain structure allows users with different attributes to request sharing on different blockchains. CES combined with CP–ABE allows 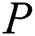 to share EMR according to their wishes. Through experimental analysis, compared with the traditional scheme and
to share EMR according to their wishes. Through experimental analysis, compared with the traditional scheme and  scheme. our scheme not only saves the cloud storage space, but also ensures the consistency of storage. In our scheme,
scheme. our scheme not only saves the cloud storage space, but also ensures the consistency of storage. In our scheme, 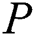 can achieve complete privacy protection when sharing data.
can achieve complete privacy protection when sharing data.
Acknowledgement: The authors would like to thank the reviewers for their detailed reviews and constructive comments, which have helped improve the quality of this paper.
Funding Statement: This work is sponsored by the Natural Science Foundation of Heilongjiang Province of China under Grant No. LC2016024. Natural Science Foundation of the Jiangsu Higher Education Institutions Grant No. 17KJB520044 and Six Talent Peaks Project in Jiangsu Province No. XYDXX–108.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1K. O. Asamoah, E. B. Sifah, A. Smahi, Q. Xia, H. Xia. (2018). et al., “GridMonitoring: Secured sovereign blockchain based monitoring on smart grid. ,” Access IEEE, vol. 6, pp, 9917–9925, .
2G. Perera, A. Holbroo and L. Thdbane. (2011), “Views on health information sharing and privacy from primary care practices using electronic medical records. ,” International Journal of Medical Informatics, vol. 80, no. (2), pp, 94–101, . [Google Scholar]
3M. Turkanović, M. Hölbl, K. Košič, M. Heričko and A. Kamišalić. (2018), “EduCTX: A blockchain-based higher education credit platform. ,” Access IEEE, vol. 6, pp, 5112–5127, . [Google Scholar]
4J. Gu, B. Sun, X. Du, J. Wang, Y. Zhuang. (2018). et al., “Consortium blockchain-based malware detection in mobile devices. ,” Access IEEE, vol. 6, pp, 12118–12128, . [Google Scholar]
5M. A. Uddin, A. Stranieri, I. Gondal and V. Balasubramanian. (2018), “Continuous patient monitoring with a patient centric agent: A block architecture. ,” Access IEEE, vol. 6, pp, 32700–32726, . [Google Scholar]
6N. Tapas, G. Merlino and F. Longo. (2018), “Blockchain-based IoT-cloud authorization and delegation” in SMARTCOMP, pp, 411–416, . [Google Scholar]
7C. Li, Y. Cao, Z. Hu and M. Yoshikawa. (2019), “ Blockchain-based bidirectional updates on fine-grained medical data,” in 2019 IEEE 35th Int. Conf. on Data Engineering Workshops, Macao, IEEE, pp. 22–27, . [Google Scholar]
8R. Guo, H. Shi, D. Zheng, C. Jing, C. Zhuang. (2019). et al., “Flexible and efficient blockchain-based ABE scheme with multi-authority for medical on demand in telemedicine system. ,” Access IEEE, pp, 1, . [Google Scholar]
9K. Fan, S. Wang, Y. Ren, H. Li and Y. Yang. (2018), “MedBlock: Efficient and secure medical data sharing via blockchain. ,” Journal of Medical Systems, vol. 42, no. (8), pp, 136, . [Google Scholar]
10J. Y. Zhang, S. Q. Zhong, T. Wang, H. C. Chao and J. Wang. (2020), “Blockchain-based systems and applications: A survey. ,” Journal of Internet Technology, vol. 21, no. (1), pp, 1–14, . [Google Scholar]
11Y. R. Ge, D. K. Ahn, B. Unde, H. D. Gage and J. J. Carr. (2013), “Patient-controlled sharing of medical imaging data across unaffliated healthcare organizations. ,” Journal of the American Medical Informatics Association, vol. 20, no. (1), pp, 157–163, . [Google Scholar]
12S. J. Lee, E. B. Larson, S. Dublin, R. L. Walker, Z. Marcum. (2017). et al., “Electronic medical record (EMR) predictors of undiagnosed dementia. ,” Alzheimers & Dementia, vol. 13, no. (7), pp, 1040–1041, . [Google Scholar]
13S. Jiang, J. Cao, H. Wu, Y. Yang, M. Ma. (2018). et al., “BlocHIE: A blockchain-based platform for healthcare information exchange,” in SMARTCOMP, pp, 49–56, . [Google Scholar]
14J. Huang. (2015), “A new economic model in cloud computing: Cloud service provider vs. network service provider,” in GLOBECOM, pp, 1–6, . [Google Scholar]
15R. Calvo, D. Thilakanathan and S. Chen. (2014), “Secure multiparty data sharing in the cloud using hardware-based TPM devices. ,” in 2014 IEEE 7th Int. Conf. on Cloud Computing, Anchorage, AK, IEEE, pp. 224–231, . [Google Scholar]
16A. N. Khan, M. L. M. Kiah, M. Ali, S. A. Madani and A. U. R. Khan. (2014), “BSS: Block-based sharing scheme for secure data storage services in mobile cloud environment. ,” Journal of Supercomputing, vol. 70, no. (2), pp, 946–976, . [Google Scholar]
17N. Zeinali, A. Asosheh and S. Setareh. (2016), “The conceptual model to solve the problem of interoperability in health information systems. ,” in 2016 8th Int. Sym. on Telecommunications, Tehran, IEEE, pp. 684–689, . [Google Scholar]
18A. Sajid and H. Abbas. (2016), “Data privacy in cloud-assisted healthcare systems: State of the art and future challenges. ,” Journal of Medical Systems, vol. 40, no. (6), pp, 151, . [Google Scholar]
19A. J. Burke. (2015), “Health information exchange (HIE) technology infrastructure for privacy assurance trustmark (PAT) test and development,” in Southeastcon, [Google Scholar]
20B. Mishra and D. Jena. (2016), “Securing files in the cloud. ,” in 2016 IEEE Int. Conf. on Cloud Computing in Emerging Markets, Bangalore, IEEE, pp. 40–45, . [Google Scholar]
21Z. Q. Xia, J. J. Tan, J. Wang, R. L. Zhu, H. G. Xiao. (2019). et al., “Research on fair trading mechanism of surplus power based on blockchain. ,” Journal of Universal Computer Science, vol. 25, no. (10), pp, 1240–1260, . [Google Scholar]
22W. J. Gordon and C. Catalini. (2018), “Blockchain technology for healthcare: Facilitating the transition to patient-driven interoperability. ,” Computational & Structural Biotechnology Journal, vol. 16, pp, 224–230, . [Google Scholar]
23A. Gervais, G. O. Karame, K. Wust, V. Glykantzis, H. Ritzdorf. (2016). et al., “On the security and performance of proof of work blockchains. ,” in Proc. of the ACM SIGSAC Conf. on Computer and Communications Security, Vienna, Austria: , pp, 3–16, . [Google Scholar]
24A. Dubovitskaya, Z. G. Xu, S. Ryu, M. Schumacher and F. S. Wang. (2017), “Secure and trustable electronic medical records sharing using blockchain. ,” in Amia Annual Sym. proceedings, Washington, D.C., IEEE, pp, 650–659, . [Google Scholar]
25K. Peterson, R. Deeduvanu, P. Kanjamala and K. Boles. (2016), “A blockchain-based approach to health information exchange networks. ,” in Proc. of NIST Workshop Blockchain Healthcare, Gaithersburg, MD, USA: , pp, 1–10, . [Google Scholar]
26N. Zeinali, A. Asosheh and S. Setareh. (2016), “The conceptual model to solve the problem of interoperability in health information systems. ,” in 2016 8th Int. Sym. on Telecommunications, Tehran, IEEE, pp. 684–689, . [Google Scholar]
27X. Qi, S. Emmanuel and S. Abla. (2017), “BBDS: Blockchain-based data sharing for electronic medical records in cloud environments. ,” Information—An International Interdisciplinary Journal, vol. 8, no. (2), pp, 44, . [Google Scholar]
28J. Liu, X. Li, L. Ye, H. Zhang, X. Du. (2018). et al., “BPDS: A blockchain based privacy-preserving data sharing for electronic medical records,” in GLOBECOM, Abu Dhabi: , . [Google Scholar]
29Y. Wang, A. Zhang, P. Zhang and H. Wang. (2019), “Cloud-assisted EHR sharing with security and privacy preservation via consortium blockchain. ,” Access IEEE, vol. 7, pp, 136704–136719, . [Google Scholar]
30S. J. Lee, E. B. Larson and S. Dublin. (2017), “Electronic medical record (EMR) predictors of undiagnosed dementia. ,” Alzheimers & Dementia, vol. 13, no. (7), pp, 1040–1041, . [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |