 Open Access
Open Access
ARTICLE
MV-Honeypot: Security Threat Analysis by Deploying Avatar as a Honeypot in COTS Metaverse Platforms
1 SysCore Lab. (Convergence Engineering for Intelligent Drone), Sejong University, Seoul, 05006, Republic of Korea
2 Division of Computer Engineering, Hankuk University of Foreign Studies, Yongin-si, 17035, Republic of Korea
3 Department of Information Security, Sejong University, Seoul, 05006, Republic of Korea
* Corresponding Author: Ki-Woong Park. Email:
(This article belongs to the Special Issue: Advanced Security for Future Mobile Internet: A Key Challenge for the Digital Transformation)
Computer Modeling in Engineering & Sciences 2024, 141(1), 655-669. https://doi.org/10.32604/cmes.2024.053434
Received 30 April 2024; Accepted 01 July 2024; Issue published 20 August 2024
Abstract
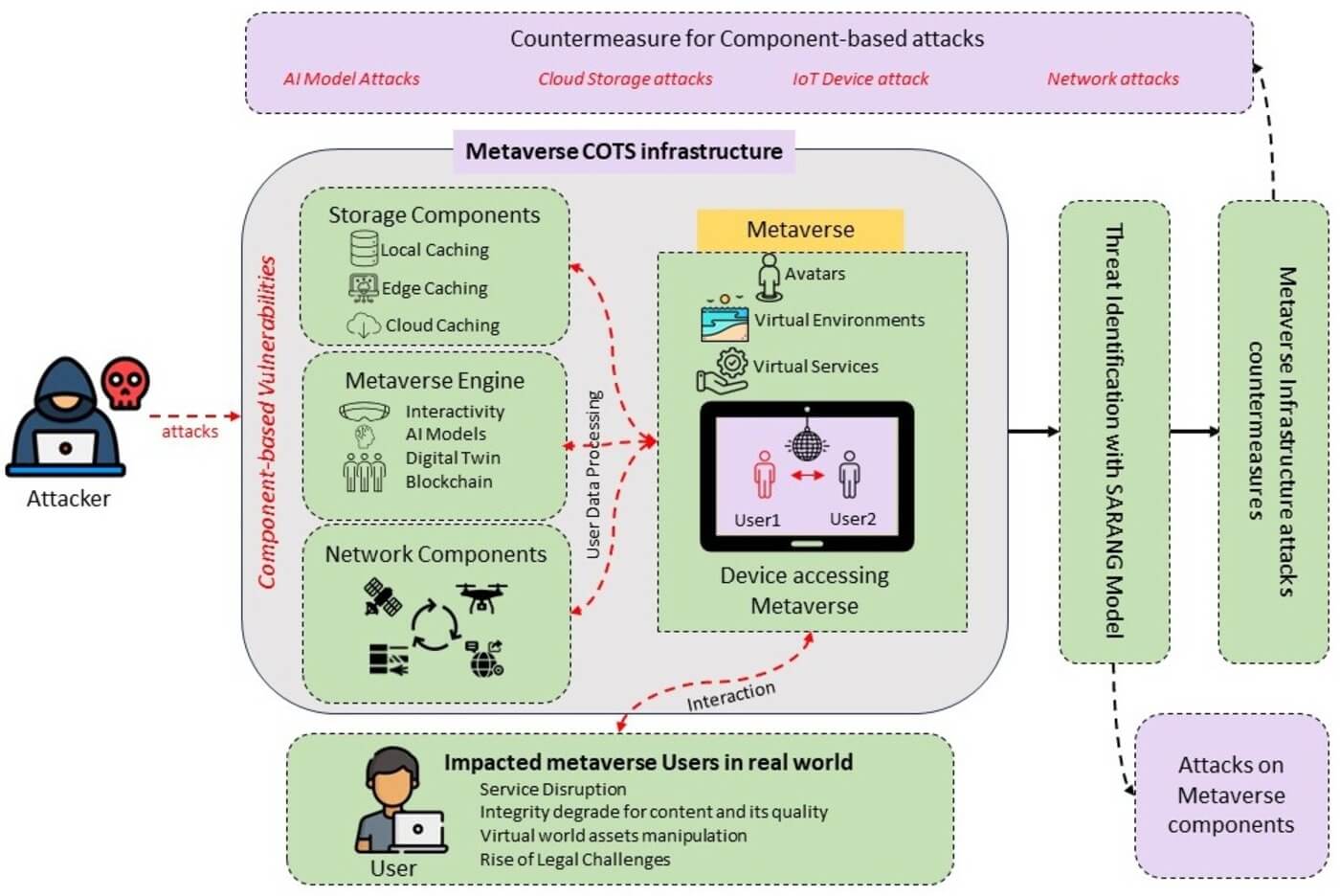
Nowadays, the use of Avatars that are unique digital depictions has increased by users to access Metaverse—a virtual reality environment—through multiple devices and for various purposes. Therefore, the Avatar and Metaverse are being developed with a new theory, application, and design, necessitating the association of more personal data and devices of targeted users every day. This Avatar and Metaverse technology explosion raises privacy and security concerns, leading to cyber attacks. MV-Honeypot, or Metaverse-Honeypot, as a commercial off-the-shelf solution that can counter these cyber attack-causing vulnerabilities, should be developed. To fill this gap, we study user’s engagements with Avatars in Metaverse, analyze possible security vulnerabilities, and create a model named Simplified Avatar Relationship Association with Non-linear Gradient (SARANG) that draws the full diagram of infrastructure components and data flow through accessing Metaverse in this paper. We also determine the most significant threat for each component’s cyberattacks that will affect user data and Avatars. As a result, the commercial off-the-shelf (COTS) of the MV-Honeypot must be established.Graphic Abstract
Keywords
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools