 Open Access
Open Access
ARTICLE
Cross-Domain Bilateral Access Control on Blockchain-Cloud Based Data Trading System
1 Electronics and Information Communications Research Center, Pukyong National University, Busan, 48513, Republic of Korea
2 Department of Information Security, Graduate School, Pukyong National University, Busan, 48513, Republic of Korea
3 Division of Computer Engineering, Pukyong National University, Busan, 48513, Republic of Korea
* Corresponding Author: Sang Uk Shin. Email:
(This article belongs to the Special Issue: Advanced Security for Future Mobile Internet: A Key Challenge for the Digital Transformation)
Computer Modeling in Engineering & Sciences 2024, 141(1), 671-688. https://doi.org/10.32604/cmes.2024.052378
Received 31 March 2024; Accepted 16 July 2024; Issue published 20 August 2024
Abstract
Data trading enables data owners and data requesters to sell and purchase data. With the emergence of blockchain technology, research on blockchain-based data trading systems is receiving a lot of attention. Particularly, to reduce the on-chain storage cost, a novel paradigm of blockchain and cloud fusion has been widely considered as a promising data trading platform. Moreover, the fact that data can be used for commercial purposes will encourage users and organizations from various fields to participate in the data marketplace. In the data marketplace, it is a challenge how to trade the data securely outsourced to the external cloud in a way that restricts access to the data only to authorized users across multiple domains. In this paper, we propose a cross-domain bilateral access control protocol for blockchain-cloud based data trading systems. We consider a system model that consists of domain authorities, data senders, data receivers, a blockchain layer, and a cloud provider. The proposed protocol enables access control and source identification of the outsourced data by leveraging identity-based cryptographic techniques. In the proposed protocol, the outsourced data of the sender is encrypted under the target receiver’s identity, and the cloud provider performs policy-match verification on the authorization tags of the sender and receiver generated by the identity-based signature scheme. Therefore, data trading can be achieved only if the identities of the data sender and receiver simultaneously meet the policies specified by each other. To demonstrate efficiency, we evaluate the performance of the proposed protocol and compare it with existing studies.Keywords
The development of the Internet-of-Things (IoT) infrastructure and devices has led to the generation and collection of IoT data at an explosive rate. These data have become valuable assets in the era of the data economy. Data trading enables data owners and data requesters to sell and buy data. Data generated by IoT technologies has significant value for data owners seeking economic benefits and data requesters developing data-intensive applications. This trend necessitates a data marketplace that enables data trading between the data owner (sender) and the requester (receiver) in a reliable and efficient manner.
Blockchain is a distributed tamper-resistant ledger with verifiable state updates [1,2] that can serve as a transparent and reliable data trading controller. It is believed that blockchain has the advantage of achieving reliable data trading without relying on a trusted third party. In blockchain-cloud based data trading systems, the blockchain can be used to track the actions performed by senders and receivers, and the cloud can provide a way to store and access vast amounts of data. In addition, smart contracts on blockchain can facilitate automatic payments in digital currency when predefined conditions are satisfied. The mediation of smart contracts enables the enforcement of consent-based access control over data and records data trading instances as provenance evidence.
IoT is made up of technologies in various domains and application areas. Organizations or developers of these domains may wish to participate in the IoT data marketplace. For example, as shown in Fig. 1, cloud providers, technology companies, research institutes, and application developers can form a consortium to manage a blockchain-based data trading platform [3]. Then, members of these organizations can share and trade their data on the platform. In this system model, it is essential to achieve access control and source identification for the data managed by the external cloud. While the data sender aims to specify policies on who can access the data entrusted to the external cloud, the data receiver aims to specify attributes for the specific data senders from whom the receiver wants to purchase data. This can be achieved by bilateral access control, where both the sender and receiver must meet each other’s policies. In addition, it is necessary to ensure accountability by providing a transparent process for transactions to prevent misbehavior.

Figure 1: Concept of blockchain-cloud fusion IoT data marketplace
Recently, matchmaking encryption (ME) has been studied [4]. ME is a novel type of encryption that enables the sender to specify a receiver who can decrypt the message and the receiver to verify if the received message is from the intended sender [5]. Due to the functionality of ME, some recent studies have proposed bilateral access control schemes based on ME for secure data trading [6–8]. The authors of [8] proposed a secure data trading system with bilateral authorization using the identity-based ME (IBME) scheme [4]. They consider that the sender and receiver are under the authorization of the same domain authority responsible for the key generation center (KGC). Therefore, their IBME-based system is not suitable for a multiple domain environment because it requires another globally trusted KGC to issue identity-based keys to the sender and the receiver who belong to different organizations. As an alternative to this problem, a cross-domain IBME (cd-IBME) [9] may be employed in the data trading system. The authors of [7] proposed a secure data trading framework based on the cd-IBME. There is no doubt that IBME is useful for secure communication because no information is revealed unless the target identities (i.e., access policies) specified by the sender and receiver match the respective counterparts. However, the policy-match is verified by the receiver after the final IBME decryption, which puts a heavy computational burden on the receiver. In [8], the authors proposed a data-sharing scheme for cloud services based on IBME (named IBME-DS) which delegates the policy-matching process to the cloud. However, their scheme works in a single-domain environment and still puts lots of computations on the receiver.
Based on the above considerations, we propose a cross-domain bilateral access control protocol for a blockchain-cloud based data trading system. Table 1 summarizes the features of the proposed protocol compared to some related work. In this paper, bilateral access control is to verify if the target identities specified by the sender and receiver satisfy the access policy of the other party. It ensures that only the designated receiver can decrypt the sender’s encrypted data. The proposed protocol leverages identity-based encryption (IBE) [10] and the identity-based signature (IBS) [11] instead of using the IBME to design a more efficient protocol. The proposed policy-match procedure is based on the idea that the sender and receiver generate their authorization tags using the IBS and the cloud provider verifies whether the tags are simultaneously valid under the target identities of the sender and receiver when the receiver requests the sender’s data stored in the cloud. In addition, to restrict access to the sender’s data to the designated receiver, the sender’s outsourced data is encrypted under the target receiver’s identity by using the IBE. The IBE of [10] is practical in a multiple-domain environment because each domain can set up its own domain KGC which generates identity-based keys only for the users within the domain. The IBS of [11] enables batch verification that verifies multiple signatures efficiently at once. Hence, two authorization tags from the sender and receiver can be simultaneously verified by the cloud provider in an efficient manner. The contributions of this paper are summarized as follows:
• For cross-domain bilateral access control in a blockchain-cloud based data trading system, we present a system architecture that consists of domain authorities, data senders, data receivers, a blockchain layer, and a cloud provider.
• By using IBE and IBS, we propose a bilateral access control protocol that restricts data sharing and trading to only the sender and receiver who satisfy each other’s policy in the system.
• We devise a policy-match procedure with IBS-based authorization tags of the sender and receiver. To reduce the computational overhead on the receiver, the cloud provider performs policy-match verification on the authorization tags to provide only the matched data to the receiver.
• To demonstrate the efficiency of the system, we evaluate the performance of the proposed protocol and compare it with existing IBME-based studies.

The rest of this paper is organized as follows: Section 2 briefly introduces related work on blockchain-cloud based data trading system models. Section 3 outlines the IBE and the IBS which serve as cryptographic building blocks of the proposed protocol. The system architecture is presented in Section 4, and the bilateral access control protocol in this system architecture is proposed in Section 5. Security and performance of the proposed protocol are evaluated in Section 6. Finally, Section 7 concludes this paper.
Blockchain is a decentralized immutable ledger technology where the records on the blockchain are kept by a reliable and transparent way through a consensus mechanism. The types of blockchain can be broadly categorized into permissionless blockchain and permissioned blockchain [12]. Permissionless blockchain is a public and decentralized blockchain where any peer can participate in the consensus process. So, transactions transferred to the blockchain network can be read by all peers. Bitcoin [13] and Ethereum [14] are typical instances. However, due to privacy concerns, it is not advisable to implement data business solutions on a public blockchain. On the other hand, in a permissioned blockchain, only a limited set of authorized peers can join the blockchain network. The widely known instances of permissioned blockchain are Hyperledger Fabric [15] and Corda [16]. A consortium blockchain is a kind of permissioned blockchain collaboratively managed by multiple organizations. A consortium blockchain provides a method to secure the interactions among organizations that have a common goal.
Due to the immutability and auditability of the blockchain, accompanied by smart contracts, the blockchain is evolving into a platform to develop a decentralized applications in various fields. It is regarded that secure and reliable data trading can be achieved on the blockchain. Recently, research on blockchain-based data trading models has received a great deal of attention, and several system models have been introduced. The existing data trading system models can be roughly classified into on-chain models and on/off-chain models. The data is directly shared or traded via blockchain in the on-chain models [17–19]. Such on-chain models can find practical applications when the data volume is small. However, managing data in on-chain data trading models becomes ineffective due to the continuously growing data volume in IoT environments.
To reduce the on-chain storage cost, a hybrid model of on-chain and off-chain is considered. In this model, an off-chain storage service such as the cloud is employed to host a huge volume of data in the on/off-chain model [3,6,20,21]. Therefore, a novel paradigm of blockchain and cloud fusion has been widely considered as a promising data trading platform. Moreover, the data is usually encrypted before being outsourced to the blockchain or cloud storage. For secure sharing and trading of data, the data owner can specify access policies and manage decryption rights to the data. In addition to the on-chain and off-chain models, Wang et al. introduced the concept of an off-state system model for big data sharing [22]. They discussed some issues in off-chain based schemes built on a public blockchain and designed an off-state data-sharing protocol based on a permissioned blockchain which addresses the security and autonomy issues in off-chain data sharing schemes.
With regard to fair data trading, Li et al. proposed a decentralized data trading system using blockchain to guarantee fair data transactions with authentication [23]. For a digital data marketplace based on the blockchain, Dixit et al. proposed a decentralized platform that hosts data in a reliable and fault-tolerant manner [24]. Chen et al. proposed a blockchain-based non-repudiable IoT data trading system [25], in which the blockchain records data trading behaviors of data sellers and buyers to facilitate on-chain and off-chain arbitration. However, their system does not consider secure data trading with access control for data confidentiality.
For secure data trading, Alsharif et al. proposed a medical data marketplace based on the blockchain [26]. They applied the ciphertext-policy ABE scheme [27] in order for the seller to enforce access control policies on the encrypted records. In [28], Li et al. proposed a secure blockchain platform for fair data trading by using the plaintext checkable encryption scheme [29]. However, Alsharif et al.’s and Li et al.’s systems only focused on the access control by the seller for data confidentiality and burdened the on-chain procedures with complex cryptographic computations.
There are some studies on cross-domain secure data sharing for industrial IoT [30–32]. Sing et al. proposed a centralized cloud-based cross-domain data-sharing platform using multiple security gateways that use the blockchain to store the information in the cloud [30]. Yu et al. proposed a consortium blockchain-based cross-domain industrial IoT data-sharing mechanism [31]. The authors introduced a consortium blockchain to construct trust among different domains, and proxy re-encryption and group signature schemes for secure cross-domain data sharing and privacy-preservation of end devices. In [32], Zheng et al. also proposed cross-domain data sharing by deploying permissioned blockchain. The authors developed a key agreement protocol and zero-knowledge proof to verify data ownership under the criterion of confidence and anonymity.
3 Cryptographic Building Blocks
We briefly outline the IBE in multiple KGC environment of Wang et al. [10] and the IBS of Cha et al. [11] based on bilinear map.
Let
• Bilinearity:
• Non-degenerate:
• Computable: It is efficient to compute
3.2 Wang-Cao Identity-Based Encryption
Wang and Cao’s IBE is constructed as follows:
1. G-Setup: It sets the global public parameter
2. Setup: It chooses a random
3. KeyGen: Given an identity
Encrypt: To encrypt a message
Decrypt: On input a ciphertext
3.3 Cha-Cheon Identity-Based Signature
Cha and Cheon’s IBS consists of the following algorithms:
1. Setup: Given the system parameter
2. KeyGen: Given an identity
Sign: To sign a message
Verify: To verify a signature
If it holds, the signature
We consider the data trading architecture as shown in Fig. 2 which consists of supervising authority, data sender (owner), data receiver (requester), blockchain layer, and cloud provider.
• Supervisors consist of a set of domain authorities (DA) which cooperate to manage the data marketplace. For instance, a group of organizations that want to participate in the data marketplace may form a consortium and collaborate in managing the data trading platform based on the blockchain. DA is responsible for setting up the public system parameters for bilateral access control. Each domain authority acts as a KGC that issues identity-based private keys to senders and receivers belonging to it. In addition, if a dispute occurs, DA forms a committee to identify the dishonest party by examining the evidence recorded on the blockchain.
• Data sender (S) offers its own data through the system. To ensure that only an authorized receiver can access the data, S sets the receiver policy which specifies the allowed identity of the receiver, and encrypts the data under the target receiver identity. S obtains its identity-based private key from the domain authority to which S belongs. When S outsources the data to the cloud, S attaches its authorization tag generated by the private key and the target receiver’s identity.
• Data receiver (R) requests the data when R finds interesting data provided by the desirable sender S satisfying the sender policy. R obtains its identity-based private keys from the domain authority to which R belongs. When requesting the data, R presents its authorization tag generated by the private key and the target sender’s identity to the cloud. R can obtain the data if and only if the encrypted data is associated with its identity which corresponds to the receiver policy of S.
• Blockchain layer serves as a decentralized and trusted platform that enforces data trading rules, verifiably updates data trading state, and facilitates payments using digital currency. Blockchain is a ledger that records the state of data trading between the sender and the receiver. Smart contracts on the blockchain execute the business logic of data trading and define the terms and actions necessary for the involved parties to carry out specific aspects of data trading transactions.
• The cloud provider (CP) serves storage to host a huge volume of data shared by the customers. For bilateral access control, CP runs the policy-match verification procedure for the authorization tags presented by the sender and the receiver. When successful match occurs, CP allows the receiver to access the sender’s data.

Figure 2: Overview of the system architecture for the proposed protocol
DAs establish a trust relationship among themselves as consortium members, while the sender and receiver only trust their respective affiliated authorities. Each DA advocates for the rights and interests of internal users, so DA will not collude with any external user. CP is semi-trusted entity that carries out the protocol honestly but may be curious about the data contents, which makes users anxious about data confidentiality of their data on the cloud. When a sender outsources its data to cloud storage, data confidentiality requires that CP do not learn any information about the data, while receivers designated by the sender can access the data. A malicious entity may impersonate the receiver or the sender to gain illegal access to data or mislead the receiver. Under the threat model, we consider the following security goals.
• Policy-match: For bilateral access control, the sender and receiver can specify their own access policies that the other party must satisfy. The data trading is achieved only if their identities simultaneously meet the policies specified by the respective counterparts.
• Privacy: The outsourced data must be protected from being revealed to the cloud provider. In addition, the identities of the sender and receiver must be hidden from the cloud provider even in the policy-match verification.
• Accountability: The system can supervise and keep track of transactions processed by the sender and receiver to prevent misconduct.
The proposed protocol aims to ensure the above security goals on the data trading system so that the receiver specified by the sender obtains the correct data from the sender specified by the receiver. Here, the correct data means the same encrypted data as the sender commits to the blockchain. However, this paper does not consider cheating by a dishonest party attempting to gain unfair financial profits. Such a problem can be addressed by fair exchange protocols with incentive and penalty techniques [33–35], and arbitration protocols can be introduced to resolve disputes [36].
The proposed cross-domain bilateral access control protocol for the data trading system is presented in this section. Table 2 describes the notations used in the protocol.
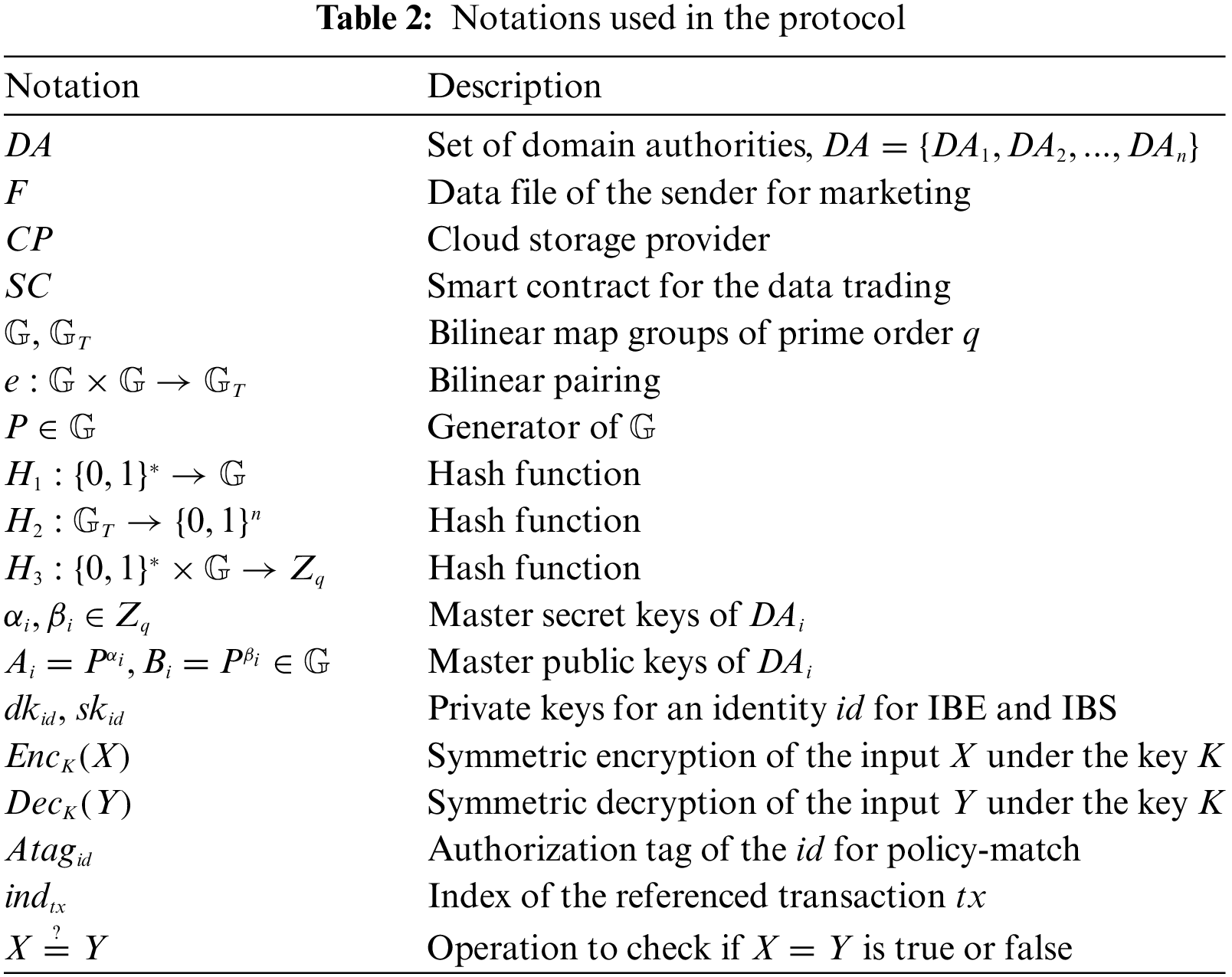
The basic idea of the proposed bilateral access control protocol is twofold. One is that the sender’s data entrusted to the cloud is encrypted under the target receiver’s identity by using the IBE to allow only the designated receiver to decrypt the data. The other is that the cloud provider checks if the authorization tags based on the IBS of the sender and receiver are valid under the target identities specified by the other party at the same time.
In the proposed system, data senders and receivers who want to participate in the data trading system should obtain their identity-based private keys by their domain authorities, respectively. The sender encrypts its data under the target receiver’s identity, and generates its IBS-based authorization tag to prove that the sender is an authorized entity of the specified identity. Then, the sender registers the encrypted data along with the authorization tag to the cloud. The receiver also generates its authorization tag, and presents the tag to the cloud provider when requesting the sender’s data. The cloud provider performs policy-match verification on the authorization tags of the sender and receiver. If the tags are valid under the specified sender’s and receiver’s identities at the same time, the cloud provider allows the receiver to access the sender’s encrypted data. Therefore, the receiver can decrypt the actual data if the receiver is the authorized holder of the target identity specified by the sender.
The consortium of domain authorities DA establishes an efficient blockchain as a transparent and reliable controller for data trading, and agrees on the global public system parameters
5.3 Data Trading with Bilateral Access Control
Suppose that a sender S provides a data F and a requester R purchases the data through the data trading system. S and R perform the data trading protocol with the mediation of the smart contract (SC) on the blockchain. For simplicity, we assume that S and R are under the authorization of
To participate in the data trading, S must obtain its identity-based key issued by
1. choose a random secret key K and encrypt the file F as
2. compute
3. choose a random
Note that
In addition to the encryption of data, S generates its authorization tag
1. pick a random
2. output
S forms the encrypted file package as
5.3.2 Data Request and Policy-Match Verification
When R is interested in the data registered by
1. compute
2. pick a random
3. output
R presents
1. parse the tags as
2. compute
3. check
If S and R satisfy the policies, that is,
5.3.3 Order and Offer Decryption Key
When
Upon receiving the order from R, S takes
5.3.4 Decryption and Confirmation
Once
After decrypting the file, R verifies the authenticity of F by checking
Bilateral access control is that the identities of the sender and receiver must satisfy the policies specified by the other party simultaneously to accomplish data trading between them. In the proposed protocol, the sender S and receiver R are required to presents their authorization tags
Moreover, these tags are based on Cha-Cheon’s IBS scheme secure against existential forgery on a chosen message and identity attack according to the hardness of the computational Diffie-Hellman problem [11]. Only S and R, who obtained their identity-based private keys
Except the sender and receiver specified by the other party, no one can know the data contents and the identity information about the sender and receiver in the proposed protocol. For access control and data confidentiality, the data file F is encrypted by using a symmetric key encryption as
According to the security of Wang-Cao’s IBE, only the authorized receiver R that possesses the identity-based private key
Furthermore, CP may also need to know the identities of the target sender and receiver for policy-match verification. However, the identity information of S and R given to CP are hidden in
Data trading is performed by means of smart contracts which define the valid state of data trading progress and transaction logic. All transactions processed by the smart contract at each phase are recorded on the tamper-resistant ledger on the blockchain. These records can be regarded as evidence of the behaviors performed by the sender and receiver throughout the data trading protocol.
The recorded transactions at each phase can be regarded as evidence of the behaviors taken by the participants during the data trading protocol. One goal of the proposed system is to ensure that the receiver obtains the correct data as same as the sender commits to the blockchain. S must submit
In this section, we evaluate the performance of the proposed protocol in terms of the computational overhead of the sender, receiver, cloud provider, and key generation center. Table 3 shows the analysis of computational overhead and comparison with the existing approaches of IBME-based [6], cd-IBME-based [8], and IBME-DS [7] systems. In Table 3,

In addition, we estimated the processing time by using the benchmark results of Java Pairing-Based Cryptography (JPBC) library [38] tested on Intel(R) Core(TM) Quad CPU Q6600 @ 2.4 GHz for the group

Figure 3: Processing time required by each entity
To demonstrate the efficiency on the receiver’s side, we also estimated the processing time expected for the receiver and cloud provider when the receiver finds and decrypts policy-matched data among multiple data packages on the cloud. Let
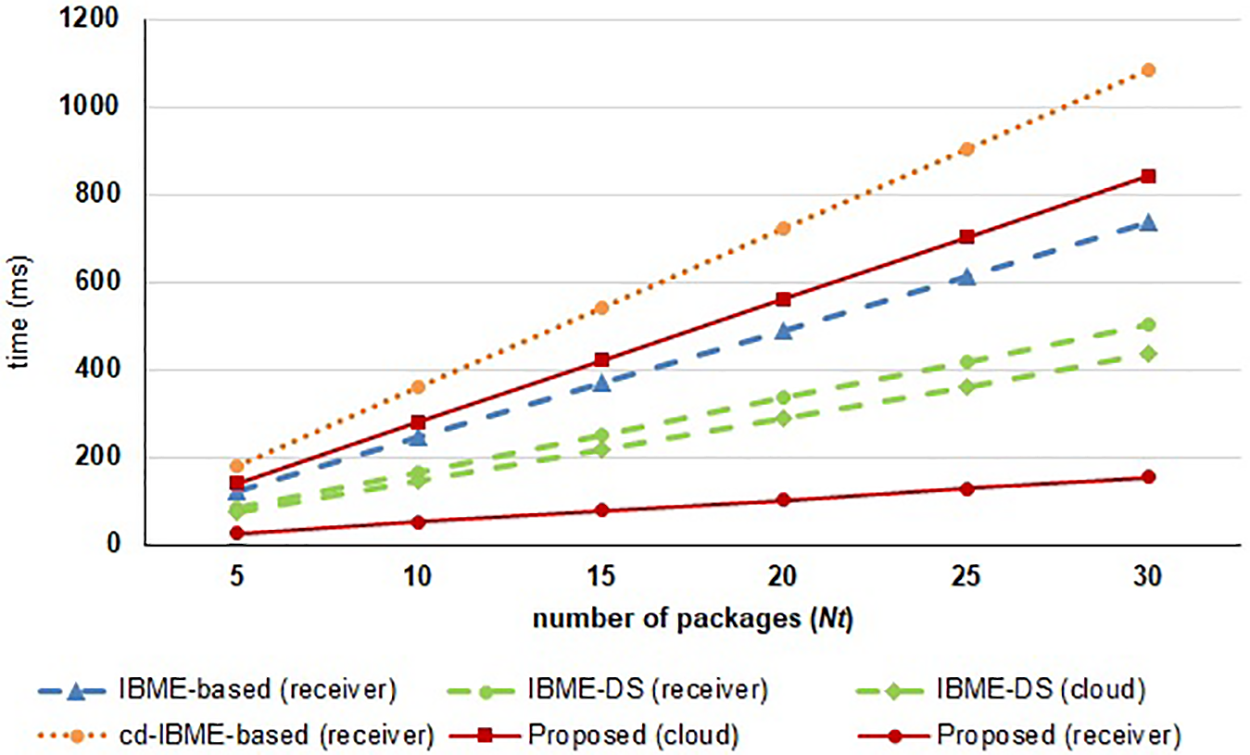
Figure 4: Processing time of the receiver and cloud provider to find and decrypt matched data
Another advantageous aspect of the proposed system is the efficiency on the sender’s side in multi-receiver scenarios. Intuitively, to generate separately encrypted data for N receivers, the sender needs to perform N data encryptions. However, in the proposed protocol, the sender can generate N encrypted data in less time than N encryptions. We consider two scenarios to demonstrate the sender’s efficiency in a multi-receiver environment. One scenario is for the receivers with different identities in a single domain (scen1) and the other is for the receivers with the same identity across multiple domains (scen2). In the proposed protocol, when the sender generates an encrypted data package, the partial ciphertext
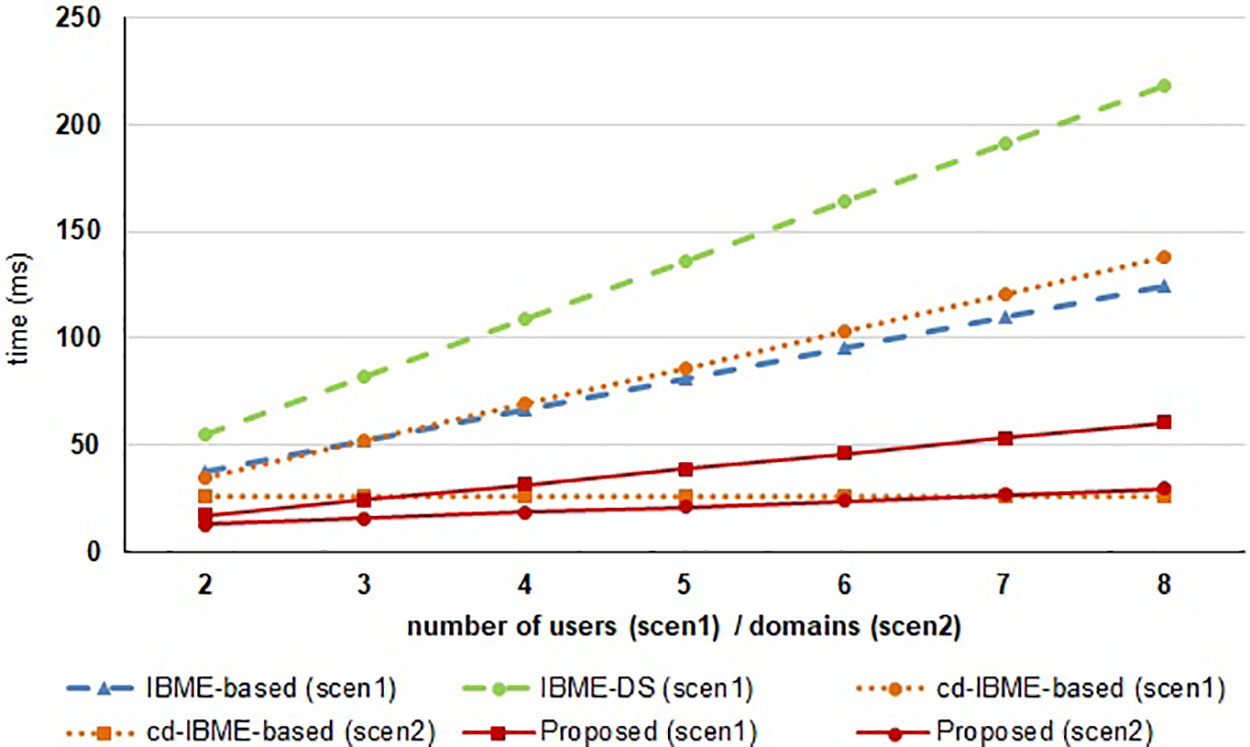
Figure 5: Processing time of the sender in multi-receiver scenarios
In a blockchain-cloud based data trading system, the blockchain can be used to keep track of behaviors performed by both the sender and receiver, while the cloud can provide a way to store and access a vast amount of data. However, it remains a challenge to securely trade the data outsourced to the external cloud in a way that restricts access to the data only to authorized users across multiple domains. Therefore, in this paper, we proposed a bilateral access control protocol by leveraging identity-based encryption and signature schemes. In the proposed protocol, the outsourced data of the sender is encrypted under the target receiver’s identity, and the cloud provider runs policy-match verification on the authorization tags of the sender and receiver generated by an identity-based signature scheme. Therefore, the proposed protocol enables data trading is achieved only if the identities of the data sender and receiver simultaneously meet the policies specified by each other. In addition, we evaluated the performance of the proposed protocol and compared it with the existing IBME-based systems to demonstrate improved efficiency. In a multi-receiver environment, the performance of the proposed protocol is more affected by the number of identities rather than the number of domains. It remains future work to explore a bilateral access control protocol for multiple receivers with different identities.
Acknowledgement: The authors wish to express their appreciation to the reviewers for their helpful suggestions which greatly improved the presentation of this paper.
Funding Statement: This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (No. 2022R1I1A3063257), and supported by the MSIT (Ministry of Science and ICT), Korea, under the Special R&D Zone Development Project (R&D)—Development of R&D Innovation Valley Support Program (2023-DD-RD-0152) supervised by the Innovation Foundation.
Author Contributions: The authors confirm contribution to the paper as follows: study conception and design: Youngho Park, Sang Uk Shin; data collection: Su Jin Shin; analysis and interpretation of results: Youngho Park, Sang Uk Shin; draft manuscript preparation: Youngho Park. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Data sharing not applicable to this article as no datasets were generated or analyzed during the current study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. Underwood S. Blockchain beyond bitcoin. Commun ACM. 2016;59(11):15–7. doi:10.1145/2994581. [Google Scholar] [CrossRef]
2. Ruoti S, Kaiser B, Yerukhimovich A, Clark J, Cunningham R. Blockchain technology: what is it good for? Commun ACM. 2020;63(1):46–53. doi:10.1145/3369752. [Google Scholar] [CrossRef]
3. Liu D, Huang C, Ni J, Lin X, Shen XS. Blockchain-cloud transparent data marketing: consortium management and fairness. IEEE Trans Comput. 2022;71(12):3322–35. doi:10.1109/TC.2022.3150724. [Google Scholar] [CrossRef]
4. Ateniese G, Francati D, Nunez D, Venturi D. Match me if you can: Matchmaking encryption and its applications. In: Advances in cryptology—CRYPTO 2019; 2019. vol. 11693, p. 701–31. doi:10.1007/978-3-030-26951-7_24. [Google Scholar] [CrossRef]
5. Xu S, Ning J, Li Y, Zhang Y, Xu G, Huang X, et al. Match in my way: fine-grained bilateral access control for secure cloud-fog computing. IEEE Trans Dependable Secure Comput. 2022;19(2):1064–77. doi:10.1109/TDSC.2020.3001557. [Google Scholar] [CrossRef]
6. Park Y, Jeon MH, Shin SU. Blockchain-based secure and fair IoT data trading system with bilateral authorization. Comput Mater Contin. 2023;79(2):1871–90. doi:10.32604/cmc.2023.039462. [Google Scholar] [CrossRef]
7. Park Y, Shin SJ, Park YH, Shin SU. A cross-domain secure data trading framework based on blockchain-cloud fusion. In: Proceedings of the 7th International Conference on Mobile Internet Security, 2023; Okinawa, Japan; p. 70. [Google Scholar]
8. Wu T, Ma X, Yan H. Enabling privacy-preserving data sharing with bilateral access control for cloud. Electronics. 2023;12(23):4798. doi:10.3390/electronics12234798. [Google Scholar] [CrossRef]
9. Wu A, Weng J, Luo W, Yang A, Liu J-N, Jiang Z. Cross-domain identity-based matchmaking encryption. Cryptol ePrint Arch. 2022. Available from: https://eprint.iacr.org/2022/085. [Accessed 2024]. [Google Scholar]
10. Wang S, Cao Z. Practical identity-based encryption (IBE) in multiple PKG environments and its applications. Cryptol ePrint Arch. 2007. Available from: https://eprint.iacr.org/2007/100. [Accessed 2024]. [Google Scholar]
11. Cha JC, Cheon JH. An identity-based signature from gap diffie-hellman groups. In: Public key cryptography—PKC 2003; 2003. vol. 2567, p. 18–30. [Google Scholar]
12. Wüst K, Gervais A. Do you need a blockchain? In: Proceedings of the 2018 Crypto Valley Conference on Blockchain Technology (CVCBT), 2008; Zug, Switzerland; p. 45–54. [Google Scholar]
13. Nakamoto S. Bitcoin: a peer-to-peer electronic cash system. 2008. Available from: https://bitcoin.org/bitcoin.pdf. [Accessed 2024]. [Google Scholar]
14. Wood G. Ethereum: a secure decentralized generalized transaction ledger. 2024. Available from: https://ethereum.github.io/yellowpaper/paper.pdf. [Accessed 2024]. [Google Scholar]
15. Androulaki E, Barger A, Bortnikov V, Cachin C, Christidis K, De Caro A, et al. Hyperledger fabric: a distributed operating system for permissioned blockchains. In: Proceedings of the 13th EuroSys Conference (EuroSys’18), 2018; New York, NY, USA; p. 1–15. [Google Scholar]
16. Brown RG. The corda platform: an introduction. 2018. Available from: https://www.corda.net/content/corda–platform–whitepaper.pdf. [Accessed 2024]. [Google Scholar]
17. Bhaskaran K, Ilfrich P, Liffman D, Vecchiola C, Jayachandran P, Kumar A, et al. Double-blind consent-driven data sharing on blockchain. In: Proceedings of the 2018 IEEE International Conference on Cloud Engineering (IC2E), 2018; Orlando, USA; p. 385–91. [Google Scholar]
18. Gunasinghe H, Kundu A, Bertino E, Krawczyk H, Chari S, Singh K, et al. Prividex: privacy preserving and secure exchange of digital identity assets. In: Proceedings of the World Wide Web Conference, 2019; New York, NY, USA; p. 594–604. [Google Scholar]
19. Kokoris-Kogias E, Alp EC, Gasser L, Jovanovic P, Syta E, Ford BA. CALYPSO: private data management for decentralized ledgers. Proc VLDB Endow. 2020;14(4):586–99. [Google Scholar]
20. Zhu L, Wu Y, Gai K, Choo K-KR. Controllable and trustworthy blockchain-based cloud data management. Future Gener Comput Syst. 2019;91:527–35. doi:10.1016/j.future.2018.09.019. [Google Scholar] [CrossRef]
21. Francati D, Ateniese G, Faye A, Milazzo AM, Perillo AM, Schiatti L, et al. Audita: a blockchain-based auditing framework for off-chain storage. In: Proceedings of the Ninth International Workshop on Security in Blockchain and Cloud Computing (SBC’21), 2021; New York, USA; p. 5–10. [Google Scholar]
22. Wang S, Yang M, Jiang S, Chen F, Zhang Y, Fu X. BBS: a secure and autonomous blockchain-based big-data sharing system. J Syst Architect. 2024;150:103133. doi:10.1016/j.sysarc.2024.103133. [Google Scholar] [CrossRef]
23. Li Y, Li L, Zhao Y, Guizani N, Yu Y, Du X. Toward decentralized fair data trading based on blockchain. IEEE Netw. 2020;35(1):304–10. doi:10.1109/MNET.011.2000349. [Google Scholar] [CrossRef]
24. Dixit A, Singh A, Rahulamathavan Y, Rajarajan M. Fast data: a fair, secure and trusted decentralized iiot data marketplace enabled by blockchain. IEEE Internet Things J. 2023;10(4):2934–44. doi:10.1109/JIOT.2021.3120640. [Google Scholar] [CrossRef]
25. Chen F, Wang J, Jiang C, Xiang T, Yang Y. Blockchain based non-repudiable IoT data trading: simpler, faster, and cheaper. London, UK; 2022. p. 1958–67. [Google Scholar]
26. Alsharif A, Nabil M. A blockchain-based medical data marketplace with trustless fair exchange and access control. In: Proceedings of the GLOBECOM 2020—2020 IEEE Global Communications Conference, 2020; Taipei, Taiwan; p. 1–6. [Google Scholar]
27. Bethencourt J, Sahai A, Waters B. Ciphertext-policy attribute-based encryption. In: Proceedings of the 2007 IEEE Symposium on Security and Privacy—SP 2007, 2007; Berkeley, USA; p. 321–34. [Google Scholar]
28. Li Y-N, Feng X, Xie J, Feng H, Guan Z, Wu Q. A decentralized and secure blockchain platform for open fair data trading. Concurr Comput. 2019;32(7):e55785. doi:10.1002/cpe.5578. [Google Scholar] [CrossRef]
29. Ma S, Mu Y, Susilo W. A generic scheme of plaintext-checkable database encryption. Inf Sci. 2018;429:88–101. doi:10.1016/j.ins.2017.11.010. [Google Scholar] [CrossRef]
30. Sing P, Masud M, Hossain MS, Kaur A. Cross-doamin secure data sharing using blockchain for industrial iot. J Parallel Distr Comput. 2021;156(7):176–84. doi:10.1016/j.jpdc.2021.05.007. [Google Scholar] [CrossRef]
31. Yu X, Xie Y, Xu Q, Xu Z, Xiong R. Secure data sharing for cross-domain industrial iot based on consortium blockchain. In: Proceeding of the 26th International Conference on Computer Supported Cooperative Work in Design (CSCWD), 2023; Brazil: Rio de Janeiro; p. 1508–13. [Google Scholar]
32. Zeng S, Cao B, Sun Y, Sun C, Wan Z, Peng M. Blockchain-assisted cross-domain data sharing in industrial IoT. IEEE Internet Things J, 2023. doi:10.1109/JIOT.2023.3329577. [Google Scholar] [CrossRef]
33. Dziembowski S, Eckey L, Faust S. FairSwap: how to fairly exchange digital goods. In: Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security—CCS 2018, 2018; Toronto, Canada; p. 967–84. [Google Scholar]
34. Eckey L, Faust S, Schlosser B. OptiSwap: Fast optimistic fair exchange. In: Proceedings of the 15th ACM Asia Conference on Computer and Communications Security—ASIA CCS 2020, 2020; Taipei, Taiwan; p. 543–57. [Google Scholar]
35. Qin B, Wang Q, Wu Q, Li S, Shi W, Bi Y, et al. BDTS: Blockchain-based data trading system. In: Information and communications security; 2023. vol. 14252, p. 645–64. doi:10.1007/978-981-99-7356-9_38. [Google Scholar] [CrossRef]
36. Lesaege C, Ast F, George W. Kleros—long paper v2.0.2. 2021. Available from: https://kleros.io. [Accessed 2024]. [Google Scholar]
37. Cha JC, Cheon JH, Kim Y. Batch verifications with id-based signatures. In: Information security and cryptology—ICISC 2004; 2005. vol. 3506, p. 233–48. [Google Scholar]
38. De Caro A, Iovino V. jPBC: java pairing based cryptography. In: Proceedings of the 16th IEEE Symposium on Computers and Communications (ISCC), 2011; Kerkyra (CorfuGreece; p. 850–5. [Google Scholar]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools