 Open Access
Open Access
ARTICLE
An Efficient and Provably Secure SM2 Key-Insulated Signature Scheme for Industrial Internet of Things
1 School of Mechanical Engineering, Northwestern Polytechnical University, Xi’an, China
2 Department of Process and Information Technology, Chengdu Aircraft Industrial (Group) Co., Ltd., Chengdu, China
3 School of Information and Software Engineering, The Network and Data Security Key Laboratory of Sichuan Province, University of Electronic Science and Technology of China, Chengdu, China
* Corresponding Author: Yang Zhao. Email:
(This article belongs to the Special Issue: Information Security Practice and Experience: Advances and Challenges)
Computer Modeling in Engineering & Sciences 2024, 138(1), 903-915. https://doi.org/10.32604/cmes.2023.028895
Received 14 January 2023; Accepted 31 March 2023; Issue published 22 September 2023
Abstract
With the continuous expansion of the Industrial Internet of Things (IIoT), more and more organisations are placing large amounts of data in the cloud to reduce overheads. However, the channel between cloud servers and smart equipment is not trustworthy, so the issue of data authenticity needs to be addressed. The SM2 digital signature algorithm can provide an authentication mechanism for data to solve such problems. Unfortunately, it still suffers from the problem of key exposure. In order to address this concern, this study first introduces a key-insulated scheme, SM2-KI-SIGN, based on the SM2 algorithm. This scheme boasts strong key insulation and secure key-updates. Our scheme uses the elliptic curve algorithm, which is not only more efficient but also more suitable for IIoT-cloud environments. Finally, the security proof of SM2-KI-SIGN is given under the Elliptic Curve Discrete Logarithm (ECDL) assumption in the random oracle.Keywords
In recent years, the Industrial Internet of Things (IIoT), a core subset of the Internet of Things (IoT) [1,2], has seen rapid development and has brought substantial and sustainable advancement to industries [3]. The IIoT is a technology that connects sensors, smart devices and actuators to the existing “Internet” through Wireless Sensor Networks (WSNs) [4]. In IIoT environment, all smart devices can monitor, transmit, collect, and analyze information automatically. Apparently, compared to traditional industries, IIoT achieves more efficient and sustainable production, significantly reducing operating costs and resource consumption [5]. Consequently, the implementation of IIoT-centered smart industry plays a significant role in promoting the development of traditional manufacturing industry to smart manufacturing industry [6]. However, despite IIoT brings plenty of benefits, it also faces thorny data processing issues. Of particular concern is the huge amount of data that is monitored and collected by IIoT smart devices. How to store and process the big data raise serious challenges [7]. Fortunately, cloud computing can provide us with a solution to appropriately deal with the aforementioned problems [8]. Cloud computing has broad network access and resource pooling, as well as formidable processing power and low cost advantages [9]. In IIoT-cloud computing environment, the challenges of big data collection, storage and processing can be properly solved [10].
Although the IIoT-cloud computing environment brings new ideas to solve the aforementioned problems, the authenticity and integrity of the data still need to be addressed urgently [5]. Generally, the channel between the cloud server and the smart device is considered undependable [11]. Therefore, ensuring that the authenticity of data is not maliciously intercepted and modified during transmission is a very difficult challenge. The digital signatures are a promising cryptographic primitive to address these challenges [12] (We give an example of a digital signature in Fig. 1). The data can be signed by the signer’s private key before it is sent from the smart devices to the cloud server. The recipient, in turn, can verify the integrity of the message by verifying the signature [4]. Consequently, a series of public key infrastructure (PKI) signature protocols were progressively presented [13].

Figure 1: Digital signature
In a PKI-based digital signature system, a trusted certification authority (CA) binds a user's identity to a corresponding public key using an issued certificate. In 1976, the first digital signature scheme was proposed by Diffie et al. [14]. It is through the paper [14] that the foundation of Public Key Cryptography (PKC) has been established for the first time. In the next decades, Public Key Infrastructure (PKI) is a popularly applied authentication architecture in traditional PKC-based schemes. Based on the aforementioned knowledge, the U.S. government has released a federal information processing standard: Digital Signature Standard (DSS). And the Chinese government adopts RSA digital signature scheme.
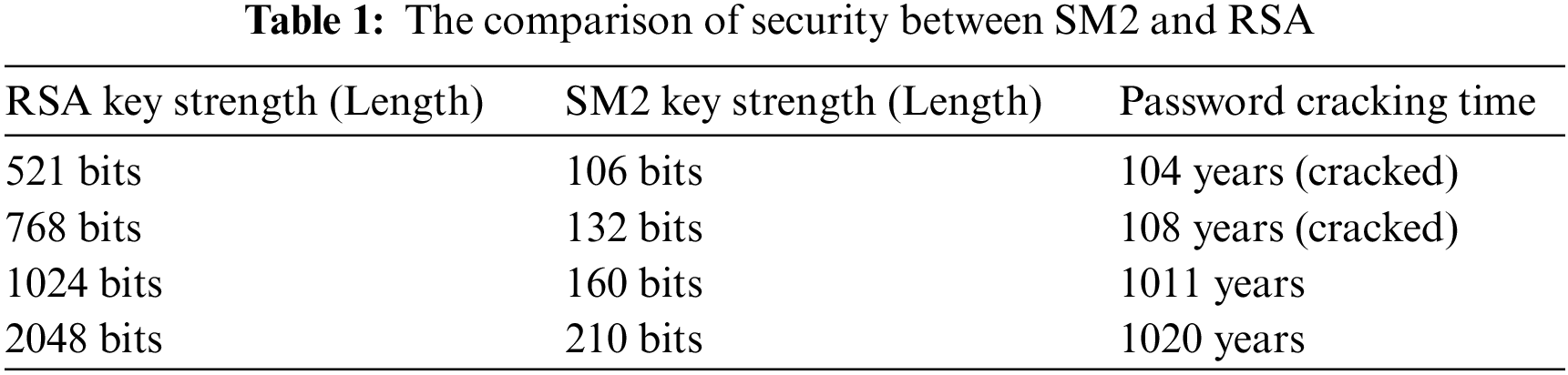
With the development of cryptography and computer technology, the commonly used 1024-bit RSA algorithms are facing serious security threats. In 1987, the Elliptic Curve Cryptography (ECC), which performs better than traditional cryptosystem (such as RSA and DSA) in security and efficiency, was proposed for the first time [15]. On December 17 2010, the public key cryptographic algorithm SM2, published by the Chinese State Cryptography Administration Office in 2010 [16], is also an ECC. Noticeable, it has been standardized by ISO/IEC in ISO/IEC 14888-3:2016/DAMD 1 [17]. Since the algorithm is based on ECC, its signature speed and secret key generation speed are faster than RSA. Compared with RSA algorithm, 256-bit SM2 password strength is already higher than 2048-bit RSA password strength. In order to demonstrate the advantages of SM2 over RSA more intuitively, we have made a comparison between the two dimensions of security and speed. The comparison results are listed in Tables 1 and 2. Thus, SM2 has better performance and security: high password complexity, fast processing speed, and less machine performance consumption. Now, SM2 algorithm is already widely executed in lots of fields, such as electronic authentication systems, E-Commerce systems and E-Government systems.

Another inevitable thorny problem is the key exposure problem since the signature operations are often executed frequently on insecure smart devices. It is obvious that key exposure will lead to disastrous consequences. The primitive of key-insulated was given by Dodis et al. in 2002 [18] for the first time. This cryptographic primitive effectively deals with the problem of catastrophic key exposure. The signer’s temporary signing key completes the key evolution with the assistance of the helper. Without the helper providing an update message, the signer’s key cannot be updated from the last time period to the current time period. With the helper’s key secure, an adversary can only forge the signature scheme for the current time period rather than the next one. After that, A strong key-insulated signature scheme was proposed by Dodis et al. [19]. Then, a number of well-designed key-insulated schemes were gradually constructed based on the work of Hanaoka et al. [20–22]. It is worth noting that the scheme proposed by Zhou et al. [22] does not have the nature of strong key-insulated. This means that an adversary can forge a signature as a legitimate user if the helper’s key is cracked. Therefore, Weng et al. [23] proposed a promising idea, namely secure key-updates. At present, this idea has been widely applied.
Given the above analysis, it faces the key exposure issue when the SM2 digital signature algorithm is integrated into the IIoT-cloud computing environment. This problem has attracted widespread attention from domestic and international authors [24,25]. In order to address the thorny issue of key exposure mentioned above, an efficient and provable secure key-insulated signature scheme based on SM2 (SM2-KI-SIGN) is proposed by us in the IIoT-cloud environment now. Our scheme is inspired by the idea of secure key-updates [23]. Our scheme also has the properties of strong key-insulated and secure key-updates. However, it is more efficient than the Weng et al. [23] due to the use of Elliptic Curve Cryptography (ECC).
Our core contributions in this paper are as follows:
1) Introduction of an efficient and secure key-insulated signature scheme based on the SM2 cryptosystem, termed SM2-KI-SIGN;
2) Demonstration that SM2-KI-SIGN achieves EUF-CMA (existential unforgeability under chosen message attacks) and has the key-insulated property, thereby efficiently mitigating the key exposure issue;
3) Empirical validation of the efficiency and applicability of SM2-KI-SIGN through specific experimental simulations and performance assessments.
The organization is illustrated in this paragraph. In Section 2, we demonstrate some corresponding preliminaries such as elliptic curve, security assumption, and system framework. In Section 3, the concrete construction of SM2-KI-SIGN is provided. In Section 4, the associated security proof, the theoretical as well as experiment evaluation is demonstrated. Finally, Section 5 gives a summary of this paper.
2.1 Elliptic Curve Discrete Logarithm (ECDL) Problem
Set E (
There is a
Let
1) Bilinearity:
2) Non-degeneracy:
3) Computability: There exists an algorithm to calculate bilinear map
2.4 Elliptic Curve Cryptography
In recent decades, Elliptic Curve Cryptography (ECC) has been widely studied and applied. In 1985, a mathematician named Victor Miller studied elliptic curves in cryptography and hypothesised that it was highly unlikely that exponential calculus methods would work for elliptic curves. ECC is a public key cryptography method based on the algebraic structure of elliptic curves over a finite field, allowing the use of smaller keys to provide equivalent security. Elliptic curves have now been applied to tasks such as key negotiation, digital signatures, pseudo-random generators. ECC utilises smaller keys, which reduces storage and transmission consumption. Thus, ECC can be better adapted to the IIoT-cloud environment.
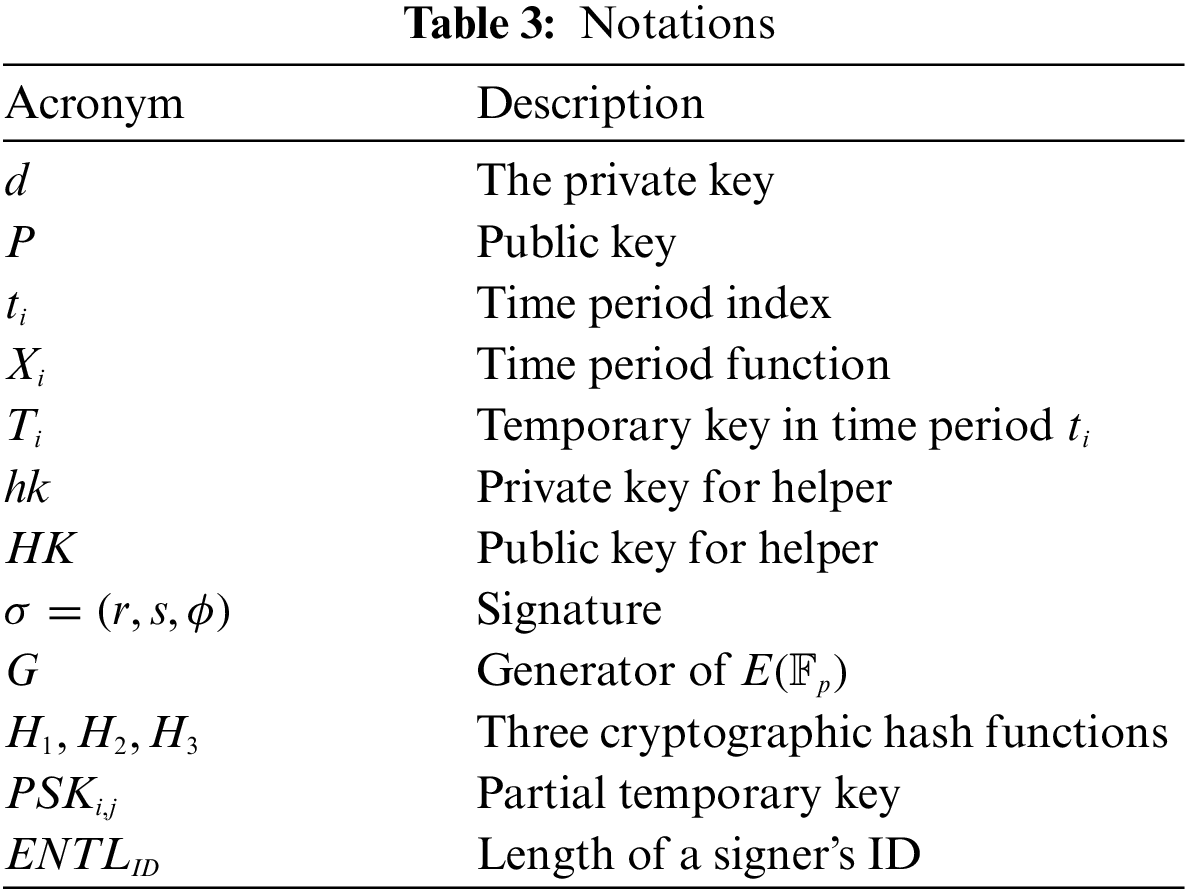
The notations presented in the SM2-KI-SIGN scheme are defined in Table 3.
The SM2-KI-SIGN scheme consists of six different algorithms described below:
1)
2)
3)
4)
5)
6)
3 Our Proposed SM2-KI-SIGN Scheme
In this section, we further elaborate the detailed construction of SM2-KI-SIGN digital signature scheme we proposed. This scheme consists of six different algorithms as listed below. In these algorithms,

Figure 2: Process of SM2-KI-SIGN scheme
1.
• Generate an elliptic curve
• Select
• Set the public parameters
• Select three cryptographic hash functions
2.
• Select
• Calculate
• Output the pair of the private and public key
• Given the time period
• Select
• Calculate the public key for the helper
• Output
• Calculate initial time period key
3.
• Calculate
• Calculate the partial temporary key
• Return
4.
• Set
• Return the temporary key
5.
• Calculate
• Calculate
• Select
• Calculate
• Calculate
• Calculate
• Output the signature
6. Verify: Input params, the public key
• Calculate
• If
• If
• Set
• Calculate
• Calculate
• Calculate
• Calculate
7.
1)
1)
2)
3)
4) Extract-Private-Key:
5) Extract-Public-Key:
6) Public-Key-Replace: After
7) Signature query: After
Forgery: After polynomially bounded queries,
Set
There are three unknown numbers
1).
2).
3).
Thus,
2)
The proof is same as those of
3)
4)
To certify the efficiency and feasibility of the proposed SM2-KI-SIGN scheme, we compare it with the existing works in this subsection. The comparison results are demonstrated in figures and tables.
In Table 4, we summarise and compare the properties between SM2-KI-SIGN scheme and other relevant schemes. We compare the existing schemes from three dimensions: strong key-insulated, secure key-updates and security assumption in Table 4. Here, it should be noted that the symbol “
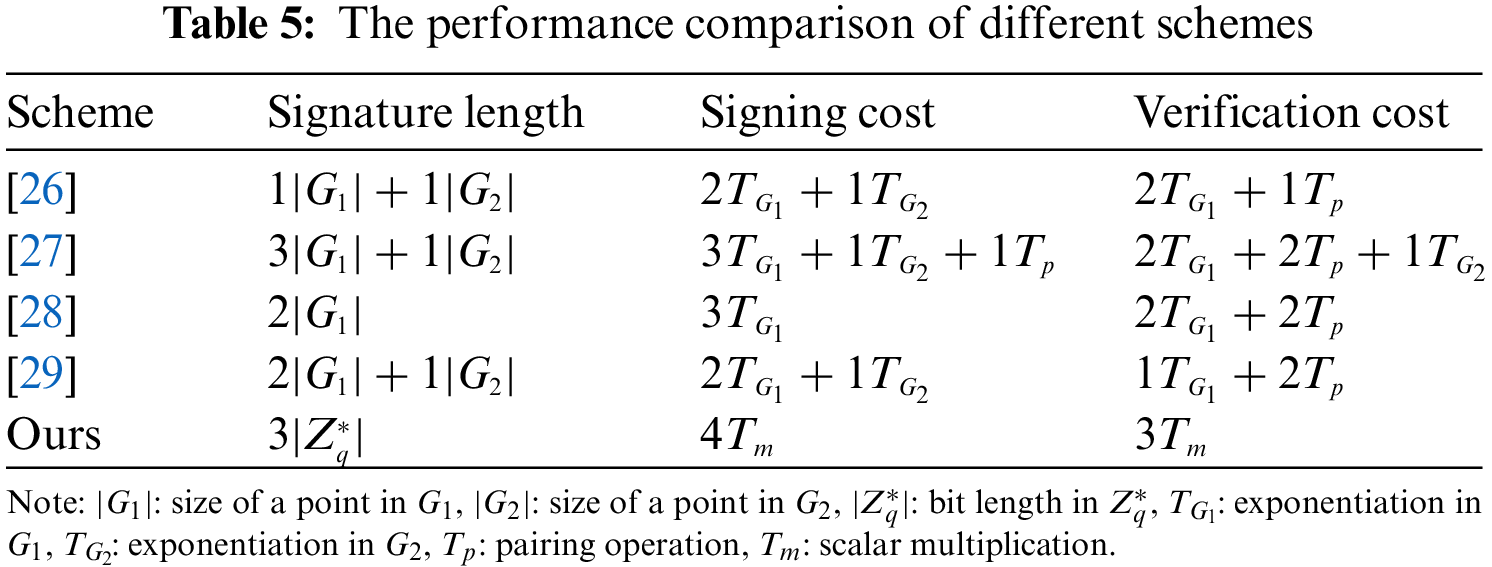
Then, a simulation experiment that runs on a Windows 10 computer equipped with an Intel Core i7-6700@2.60-GHz processor, as well as 8 GB, is given in this section. Then, it is implemented in IDEA with Java pairing-based cryptography (JPBC) library. To achieve the same security level as 1024-bit RSA, the super-singular curve
Compared with the existing schemes especially the schemes listed here, our scheme has more advantages in cost. This advantage makes SM2-KI-SIGN scheme more suitable for untrusted channels in IIoT-cloud computing environment. At the same time, we show a cost comparison of SM2-KI-SIGN with other schemes [26–29] in Fig. 3.

Figure 3: Comparison of cost
This paper presented the first key-insulated digital signature scheme SM2-KI-SIGN based on the SM2 algorithm. The proposed SM2-KI-SIGN scheme can effectively reduce the risk of key exposure due to untrusted channels in IIoT-cloud computing environment. We first gave a formal outline of the scheme. Following this, a concrete scheme and the formal security proof under the ECDLP assumption in the random oracle model were given. Finally, according to the theoretical analysis and simulation experiments, the SM2-KI-SIGN scheme is more efficient and practical than other related key-insulated works. In the current research field, SM2-KI-SIGN introduces a method to make up for the key exposure defects of existing SM2 signature algorithms. On the other hand, our work can provide a new idea for future commercial digital signature schemes.
Acknowledgement: We have already revised the Acknowledgement section in the manuscript.
Funding Statement: This work was supported in part by the National Natural Science Foundation of China (Nos. 62072074, 62076054, 62027827, 62002047), the Sichuan Science and Technology Innovation Platform and Talent Plan (Nos. 2020JDJQ0020, 2022JDJQ0039), the Sichuan Science and Technology Support Plan (Nos. 2020YFSY0010, 2022YFQ0045, 2022YFS0220, 2023YFG0148, 2021YFG0131), the YIBIN Science and Technology Support Plan (No. 2021CG003), the Medico-Engineering Cooperation Funds from University of Electronic Science and Technology of China (Nos. ZYGX2021YGLH212, ZYGX2022YGRH012).
Author Contributions: study conception and design: Senshan Ouyang, Baichuan Shao and Yang Zhao; analysis and interpretation of results: Xiang Liu, Lei Liu, Shangchao Wang; draft manuscript preparation: Senshan Ouyang and Baichuan Shao; figures and tables production: Baichuan Shao.
Availability of Data and Materials: Our current research is limited to algorithm design and analysis, and has not yet applied it to practical scenarios, so we have not yet addressed the source and use of data and materials.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. Chen, J., Liu, G., Liu, Y. (2020). Lightweight privacy-preserving raw data publishing scheme. IEEE Transactions on Emerging Topics in Computing, 9(4), 2170–2174. [Google Scholar]
2. Chen, J., Liu, Y., Xiang, Y., Sood, K. (2021). RPPTD: Robust privacy-preserving truth discovery scheme. IEEE Systems Journal, 16(3), 4525–4531. [Google Scholar]
3. Boyes, H., Hallaq, B., Cunningham, J., Watson, T. (2018). The Industrial Internet of Things (IIoTAn Analysis Framework. Computers in Industry, 101(8), 1–12. [Google Scholar]
4. Xiong, H., Mei, Q., Zhao, Y. (2019). Efficient and provably secure certificateless parallel key-insulated signature without pairing for IIoT environments. IEEE Systems Journal, 14(1), 310–320. [Google Scholar]
5. Sisinni, E., Saifullah, A., Han, S., Jennehag, U., Gidlund, M. (2018). Industrial Internet of Things: Challenges, opportunities, and directions. IEEE Transactions on Industrial Informatics, 14(11), 4724–4734. [Google Scholar]
6. Yu, K., Tan, L., Aloqaily, M., Yang, H., Jararweh, Y. (2021). Blockchain-enhanced data sharing with traceable and direct revocation in IIoT. IEEE Transactions on Industrial Informatics, 17(11), 7669–7678. [Google Scholar]
7. Sadeghi, A. R., Wachsmann, C., Waidner, M. (2015). Security and privacy challenges in industrial Internet of Things. 2015 52nd ACM/EDAC/IEEE Design Automation Conference (DAC), IEEE. [Google Scholar]
8. Xiong, H., Zhao, Y., Hou, Y., Huang, X., Jin, C. et al. (2020). Heterogeneous signcryption with equality test for IIoT environment. IEEE Internet of Things Journal, 8(21), 16142–16152. [Google Scholar]
9. Kumar, M., Sharma, S. C., Goel, A., Singh, S. P. (2019). A comprehensive survey for scheduling techniques in cloud computing. Journal of Network and Computer Applications, 143(2), 1–33. [Google Scholar]
10. Li, Q., Yue, Y., Wang, Z. (2020). Deep robust cramer shoup delay optimized fully homomorphic for IIoT secured transmission in cloud computing. Computer Communications, 161(10), 10–18. [Google Scholar]
11. Hou, Y., Xiong, H., Huang, X., Kumari, S. (2021). Certificate-based parallel key-insulated aggregate signature against fully chosen key attacks for Industrial Internet of Things. IEEE Internet of Things Journal, 8(11), 8935–8948. [Google Scholar]
12. Wang, W., Xu, H., Alazab, M., Gadekallu, T. R., Han, Z. et al. (2021). Blockchain-based reliable and efficient certificateless signature for IIoT devices. IEEE Transactions on Industrial Informatics, 18(10), 7059–7067. [Google Scholar]
13. ElGamal, T. (1985). A public key cryptosystem and a signature scheme based on discrete logarithms. IEEE Transactions on Information Theory, 31(4), 469–472. [Google Scholar]
14. Diffie, W., Hellman, M. E. (2022). New directions in cryptography. In: Democratizing cryptography: The work of whitfield diffie and martin hellman, pp. 365–390. [Google Scholar]
15. Koblitz, N. (1987). Elliptic curve cryptosystems. Mathematics of Computation, 48(177), 203–209. [Google Scholar]
16. Administration, S. C. (2010). Public key cryptographic algorithm SM2 based on elliptic curves-Part 2: Digital signature algorithm. http://www.sca.gov.cn/sca/xwdt/2010-12/17/1002386/files/b791a9f908bb4803875ab6aeeb7b4e03.pdf [Google Scholar]
17. Administration, S. C. (2016). Our SM2 and SM9 digital signature algorithms officially become ISO/IEC international standard. http://www.sca.gov.cn/sca/qjd/2017-11/17/content_1019960.shtml [Google Scholar]
18. Dodis, Y., Katz, J., Xu, S., Yung, M. (2002). Key-insulated public key cryptosystems. In: International Conference on the Theory and Applications of Cryptographic Techniques, pp. 65–82. Springer. [Google Scholar]
19. Dodis, Y., Katz, J., Xu, S., Yung, M. (2003). Strong key-insulated signature schemes. International Workshop on Public Key Cryptography, Springer. [Google Scholar]
20. Hanaoka, G., Hanaoka, Y., Imai, H. (2006). Parallel key-insulated public key encryption. International workshop on public key cryptography, pp. 105–122. Springer. [Google Scholar]
21. Hanaoka, Y., Hanaoka, G., Shikata, J., Imai, H. (2005). Identity-based hierarchical strongly key-insulated encryption and its application. International Conference on the Theory and Application of Cryptology and Information Security, pp. 495–514. Springer. [Google Scholar]
22. Zhou, Y., Cao, Z., Chai, Z. (2006). Identity based key insulated signature. International Conference on Information Security Practice and Experience, pp. 226–234. Springer. [Google Scholar]
23. Weng, J., Liu, S., Chen, K., Li, X. (2006). Identity-based key-insulated signature with secure key-updates. International Conference on Information Security and Cryptology, pp. 13–26. Springer. [Google Scholar]
24. Hou, H. X., Yang, B., Zhang, L. N., Zhang, M. R. (2020). Secure two-party SM2 signature algorithm. Acta Electonica Sinica, 48(1), 1–8. [Google Scholar]
25. Zhang, Y., He, D., Zhang, F., Huang, X., Li, D. (2020). An efficient blind signature scheme based on SM2 signature algorithm. International Conference on Information Security and Cryptology, pp. 368–384. Springer. [Google Scholar]
26. Karati, A., Islam, S. H., Karuppiah, M. (2018). Provably secure and lightweight certificateless signature scheme for IIoT environments. IEEE Transactions on Industrial Informatics, 14(8), 3701–3711. [Google Scholar]
27. Chen, J., Wang, L., Wen, M., Zhang, K., Chen, K. (2021). Efficient certificateless online/offline signcryption scheme for edge IoT devices. IEEE Internet of Things Journal, 9(11), 8967–8979. [Google Scholar]
28. Cha, S. C., Chen, J. F., Su, C., Yeh, K. H. (2018). A blockchain connected gateway for BLE-based devices in the internet of things. IEEE Access, 6, 24639–24649. [Google Scholar]
29. Reddy, P. V., Gopal, P. (2017). Identity-based key-insulated aggregate signature scheme. Journal of King Saud University-Computer and Information Sciences, 29(3), 303–310. [Google Scholar]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF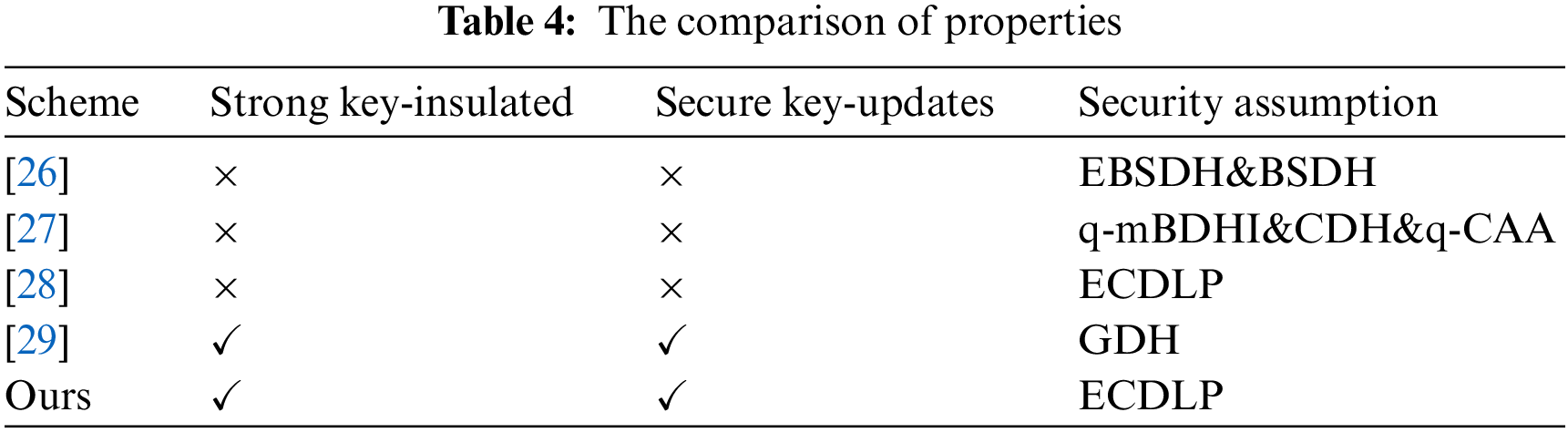
 Downloads
Downloads
 Citation Tools
Citation Tools