 Open Access
Open Access
ARTICLE
A Secure Device Management Scheme with Audio-Based Location Distinction in IoT
1 College of Economics and Management, Nanjing University of Aeronautics and Astronautics, Nanjing, 211106, China
2 Chengdu Aircraft Industrial (Group) Co., Ltd., Chengdu, 610073, China
3 Academy of Military Sciences of PLA, Beijing, 100091, China
4 School of Information and Software Engineering, University of Electronic Science and Technology of China, Chengdu, 610054, China
5 Ningbo WebKing Technology Joint Stock Co., Ltd., Ningbo, 315000, China
6 The Network and Data Security Key Laboratory of Sichuan Province, University of Electronic Science and Technology of China, Chengdu, 610054, China
* Corresponding Author: Mingsheng Cao. Email:
(This article belongs to the Special Issue: Information Security Practice and Experience: Advances and Challenges)
Computer Modeling in Engineering & Sciences 2024, 138(1), 939-956. https://doi.org/10.32604/cmes.2023.028656
Received 30 December 2022; Accepted 05 May 2023; Issue published 22 September 2023
Abstract
Identifying a device and detecting a change in its position is critical for secure devices management in the Internet of Things (IoT). In this paper, a device management system is proposed to track the devices by using audio-based location distinction techniques. In the proposed scheme, traditional cryptographic techniques, such as symmetric encryption algorithm, RSA-based signcryption scheme, and audio-based secure transmission, are utilized to provide authentication, non-repudiation, and confidentiality in the information interaction of the management system. Moreover, an audio-based location distinction method is designed to detect the position change of the devices. Specifically, the audio frequency response (AFR) of several frequency points is utilized as a device signature. The device signature has the features as follows. (1) Hardware Signature: different pairs of speaker and microphone have different signatures; (2) Distance Signature: in the same direction, the signatures are different at different distances; and (3) Direction Signature: at the same distance, the signatures are different in different directions. Based on the features above, a movement detection algorithm for device identification and location distinction is designed. Moreover, a secure communication protocol is also proposed by using traditional cryptographic techniques to provide integrity, authentication, and non-repudiation in the process of information interaction between devices, Access Points (APs), and Severs. Extensive experiments are conducted to evaluate the performance of the proposed method. The experimental results show that the proposed method has a good performance in accuracy and energy consumption.Keywords
With the rapid development of emerging technologies (e.g., 5G Communications and beyond [1–3], Artificial Intelligence [4–6], and Information Security [7–9]), the Internet of Things (IoT) have become an important part of people’s life and work which provide people with intelligent, secure and privacy-protected services, such as smart medical care [10,11], smart city [12], and intelligent manufacturing [13,14]. As we all know, massive smart devices are extremely important in the IoT, as they undertake a variety of high-precision and difficult tasks [15–17]. It is noted that a lot of smart devices in IoT are extremely expensive. To reduce the acquisition cost of smart devices and improve their utilization of them, a large number of smart devices have been realized as mobile and portable [18–21]. It is necessary to manage smart devices, such that they can be accurately located when we need them [22–24]. Moreover, as the number of IoT nodes continue to increase, the risks associated with malicious attacks on the IoT also continue to rise [25,26]. When an IoT device is compromised, it is critical to locate the device among the vast number of IoT devices. However, the mobility and portability of devices have brought great challenges to secure device management [27–29]. In the midst of existing challenges, identifying an IoT device and detecting a change in its position are critical challenges in many IoT applications (e.g., intelligent logistics, intelligent transportation, and intelligent manufacturing [30,31]).
There are several existing methods to realize the identification and movement detection of devices. In [32], the radio frequency identification devices (RFID) based device tracking method was proposed, in which, RFID tags can be used to identify and track devices. In this method, the devices are attached with an RFID tag, which can be identified by an RFID reader. However, using the RFID-based method requires a large number of readers. This will come at a high cost, as the RFID reader is expensive. In [33], an IoT device management system was designed by using cloud computing to realize the dynamic task scheduling of devices. In [34], a single pixel tracking system is proposed for the microfluidic device monitoring without image processing. Other related works also include [35–37], which considers the secure management of smart devices. However, both of them focus on the security in smart device management and lack device tracking.
In this paper, a device management scheme is proposed, which includes device identification and movement detection by using audio-based location distinction techniques. In our system, a set of devices
The proposed scheme includes three main stages: Device Registration, Position Report, and Location Distinction. We utilize traditional cryptographic techniques to realize the integrity, authentication, and non-repudiation of information transmitted between devices, APs, and Severs. Moreover, the audio-based location distinction method is designed to identify the devices and detect the position change of them. The audio frequency response (AFR) at several frequency points are utilized as the signature of a device [39,40] to identify the devices and detect the movements because of the following features. (1) Hardware Signature: the obtained signatures of different loudspeaker and microphone pairs are difference [41]; and (2) Location Signature: the obtained signatures are completely different for different distances in the same direction and the obtained signatures are different for different directions in the same distances. To evaluate the performance of the proposed scheme, extensive experiments are conducted. In our experiments, several mobile phones (i.e., HUAWEI Mate 40, HUAWEI nova 9pro, and HUAWEI nova 9SE) are used as devices and APs. We selected 31 frequency points ranging from 10 to 16 KHz with steps length of 0.2 KHz in our experiments. Extensive experiments show that the audio-based location distinction method has a good performance in security, accuracy and energy consumption.
The main contributions of this paper are shown as follows:
• We propose a secure IoT device management scheme with audio-based location distinction and traditional cryptographic techniques.
• We design an audio-based location distinction method to identify the IoT devices and detect the position change of them.
• We conduct extensive experiments to evaluate the performance of the proposed scheme. The results show that our scheme has a good performance in security, accuracy and energy consumption.
The structure of the paper is as follows. The system model is introduced in Section 2. Section 3 describes the proposed the details of IoT device management scheme. Audio-based location distinction method is discussed in Section 4. The experimental results are pretended in Section 5. Finally, Section 6 concludes this paper.
There are three entities involved in our system, as shown in Fig. 1, e.g., IoT device, Access Point, and Sever. Specifically, in the proposed system, there is a set of devices

Figure 1: The system model
The audio frequency response (AFR) at several frequency points is used as the location signature of a device for movement detection. It is necessary to introduce the acoustic propagation model. As sound wave is a kind of energy, its energy will gradually decline with the increase of the transmission distance owing to the diffusion, absorption and scattering, when it propagates in certain medium. Actually, the received energy is related to the propagation distance, the gain of the built-in loudspeaker at sender and the built-in microphone at receiver, and the frequency of the sound wave. The acoustic attenuation model is shown as follows:
where
The audio frequency response (AFR) at frequency point
It is clear that the frequency response at
can be used as the hybrid signature.
In our system, it is assumed that there is an adversary who is equipped with loudspeaker and microphone. The adversary can obtain all the parameters of the proposed system, know the position of a target IoT device, and access to such devices. The adversary can record the sound of the target IoT device with its loudspeaker, and launch replay attacks with its microphone through adaptive selection of the appropriate positions to trick the AP into recognizing it as the target IoT device.
Assumed that there is a device manager who has a handhold smart terminal device (e.g., a mobile phone) and is in charge of assisting device registration during the registration phase and inputting basic information of the devices into the server database. The manager and server have a pair of public/private key
In order to register a new device
Step 1. The manager first transmits the identification number
• Defining
to the sever, where
Step 2. After receiving registration information
• The sever checks the validity of
• If so, the sever can obtain the key
• Then, the sever decrypts M from
• If so, the sever chooses an initial section key
Step 3. The device manager decrypts
If a device
Step 1.
where
Step 2. After obtaining
where
Step 3. When the sever received
• First of all, it verifies the validity of the signature
• Then, it obtains
• Finally, it verifies the consistency between
Step 4. After receiving
to sever through
Step 5. The sever decrypts
If the device
• Audio Signal Generation. After finishing the position report,
• Hybrid Signature Extraction. When
• Movement Detection.
For the details of the audio-based location distinction method, please refer to the next section.
4 Audio-Based Location Distinction Method
4.1 Location and Audio-Hardware Fingerprints
From the discussion above, the vector
Hardware Signature. In the first experiment, three different smart phones are used to investigate the hardware differences, in which the phone

Figure 2: Hardware signature
Location Signature. In the second experiment, two smart phones (i.e., Phone 1 and Phone 2) are used to study the location differences. Fig. 3 plots the vectors

Figure 3: Distance signature
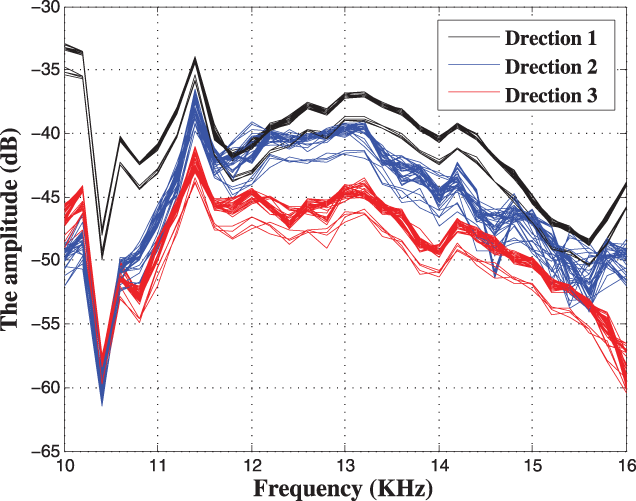
Figure 4: Direction signature
4.2 Audio-Based Location Distinction Scheme
Based on the discussion above, a novel location distinction scheme are proposed by using the AFR. Besides being able to determine whether a node is moving with location signature, the proposed scheme can also resist node impersonation attacks with the audio hardware signature. The details of the proposed scheme is shown as follows:
Audio Signal Generation. When
for
Hybrid Signature Extraction. After completing the location report phase,
with its loudspeaker to
with the microphone,
for
Movement Detection. When
where
If
Hypothesis testing is used to decide two hypotheses
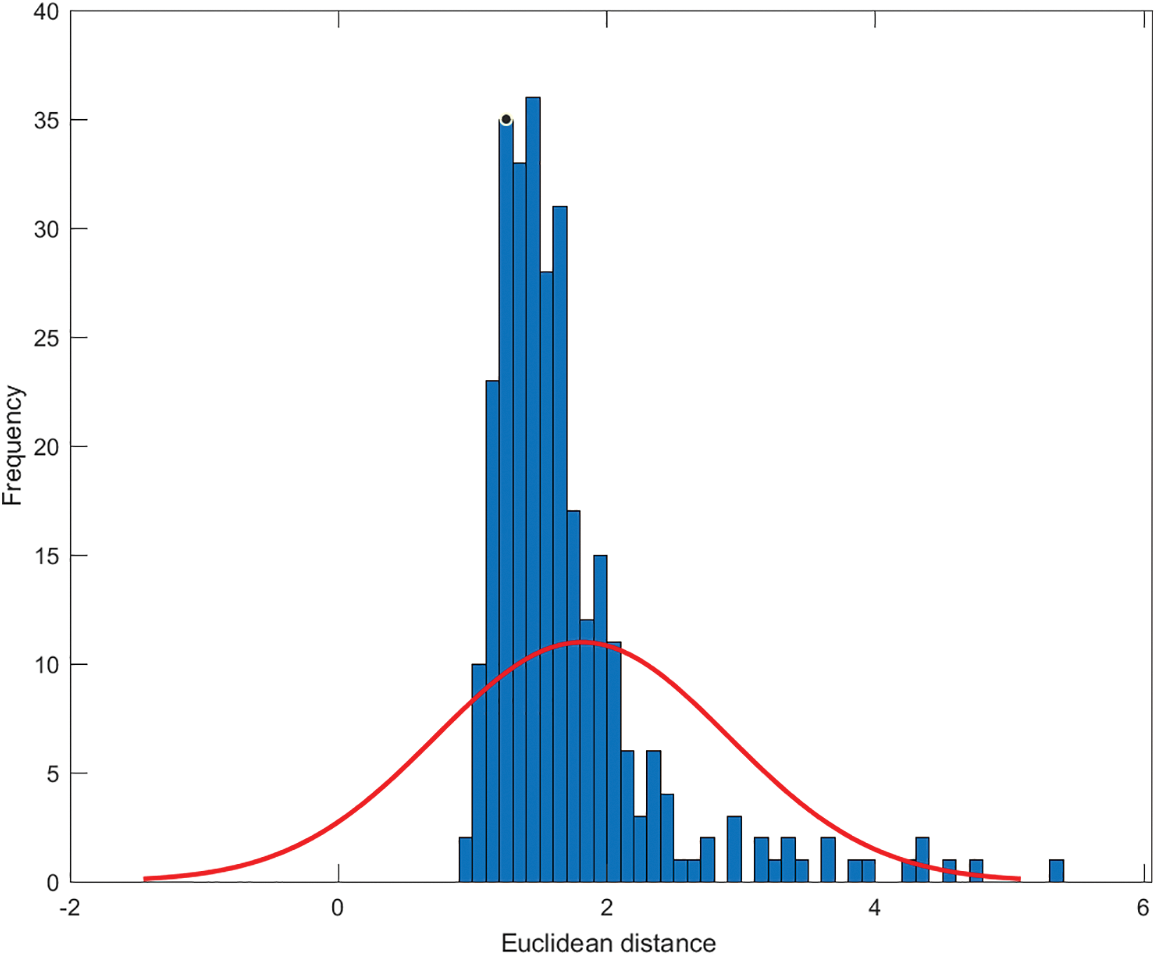
Figure 5: The distribution of statistics of the Euclidean distance between two signatures at the same position
Supposed that
Then, the false negative probability
In order to evaluate the performance of the proposed scheme, we design an evaluation methodology as follows:
where
In this section, extensive experiments are conducted to verify the performance of the proposed scheme.
In our experiments, several mobile phones (i.e., HUAWEI Mate 40, HUAWEI nova 9pro, and HUAWEI nova 9SE) are used as devices and APs. Note that, due to the limitation of hardware, the maximum frequency of sound produced by a mobile phone is about 16 KHz. Therefore, it selected 31 frequency points ranging from 10 to 16 KHz with steps length of 0.2 KHz in our experiments.
The position change diagram of the device in the experiments is shown in the Fig. 6. We consider the changing of starting position of the device from the 20 to 100 cm with step-length 20 cm in four different directions, where the AP is on the central position. In other words, there are five points for each direction, and each point is 20, 40, 60, 80, and 100 cm away from the central position. The AP records the sound signal from the device to get the 31 results after FFT transformation for each period of time, and then, calculates the Euclidean distance of link signature according to the obtained value. Moreover, we found that the fading of high frequency band is too fast. In order to average the granularity of each frequency, we refer to the experimental test and influence factors of acoustic attenuation model, and change the frequency weight to exponential growth from low frequency to high frequency.

Figure 6: The position change diagram of the device in the experiments
First of all, we discuss how to determine the threshold of the proposed location distinction method. From Figs. 2–4, we have the conclusion that the location signatures have two properties: the aggregation with time difference and the separation with space difference. The conclusion shows that finding a threshold of movement detection is possible.
An experiment is conducted to obtain the Euclidean distance of two signatures under different distance change between device and AP with 20 cm as the step length in each direction. As shown in Fig. 7, the solid black dot means the Euclidean distance of two signatures of the starting position; the red square means the Euclidean distance of two signatures in the starting position and the position at 20 cm, respectively; the red star means the Euclidean distance of two signatures in the starting position and the position at 40 cm, respectively; the blue triangle means the Euclidean distance of two signatures in the starting position and the position at 60 cm, respectively; the green diamond means the Euclidean distance of two signatures in the starting position and the position at 80 cm, respectively; the black circle means the Euclidean distance of two signatures in the starting position and the position at 100 cm, respectively. From this figure, we can find that the Euclidean distance of two signatures increases as the distance between measured positions increases.
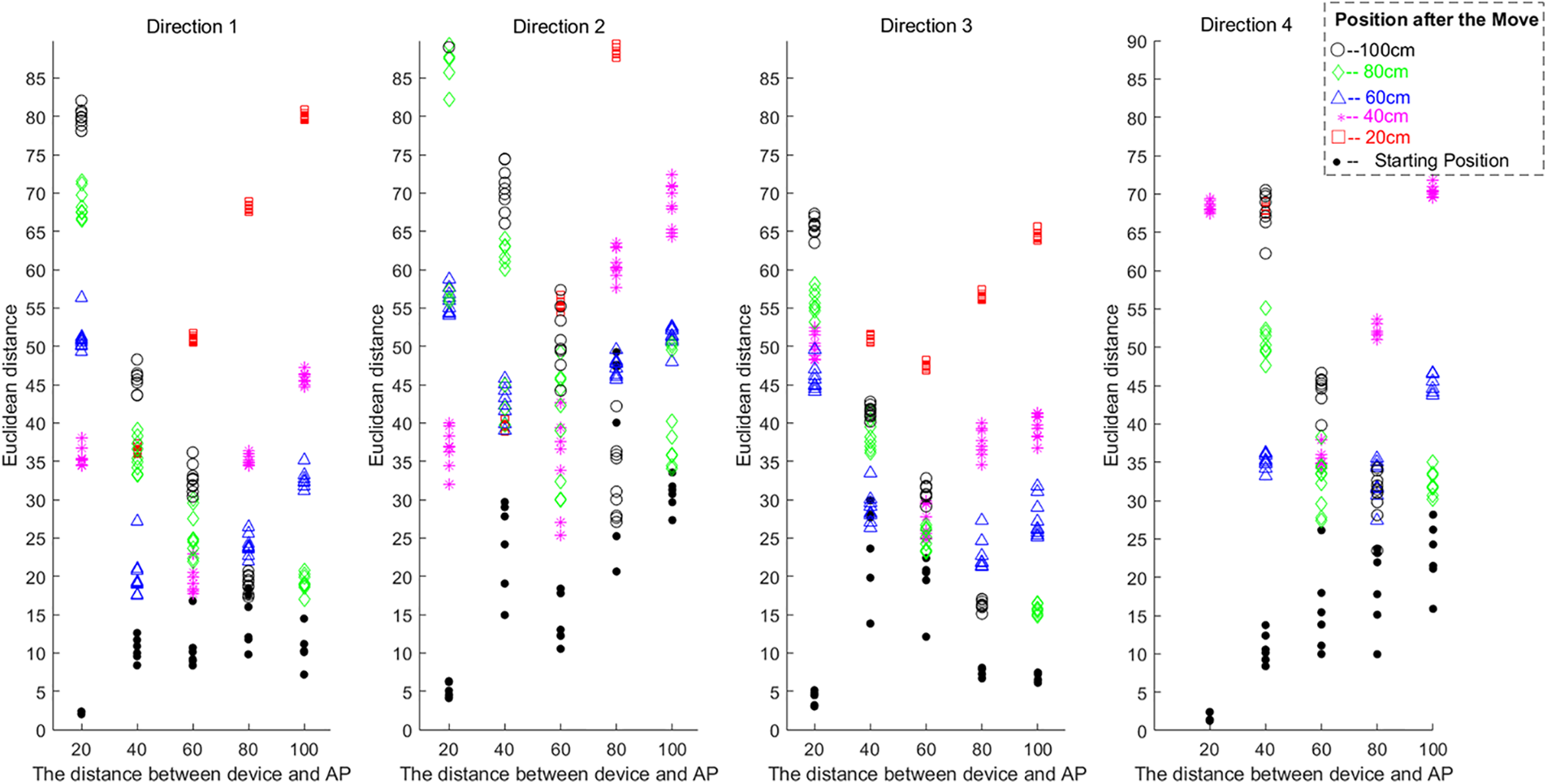
Figure 7: Threshold discussion
In order to obtain a fixed threshold suitable for all distances, the

Figure 8: The impact of the value of the threshold on the detection performance
Now we discuss the adversary’s replay attacks with an experiment. Assumed that a legitimate device is located 20, 40, and 60 cm in direction 1, and an adversary is located at 5 cm before and after these three points. In this experiment, the adversary records and replays the sound of the legitimate device. The experimental result is shown in Fig. 9, in which the threshold is set to 15. The blue line combination is the sum of the signature of the legitimate device. We can see in the figure that its separation from the purple and black lines from the recording playback of the adversary. By comparing the threshold with the Euclidean distance between signatures from the legitimate device and adversary, it is found that the attack inefficiency is 100%. This test verifies the proposed scheme can against recording replay attacks.

Figure 9: Adversary’s replay attacks
Assumed that the adversary can obtain the original position and the original audio from the legitimate device, an experiment is conduct as follows. A mobile phone is used as the legitimate device at the position 20 cm in direction 1, and another mobile phone is used as the adversary at the position 20 and 2 cm before and after, and 2 cm around. Fig. 10 plots the Euclidean distance of the signature of legitimate device and the signature of adversary at different positions in different time slots. In this figure, the middle red line is the threshold. The experimental results show that all attacks failed, although the Euclidean distance between the signature of legitimate device and the signature of adversary at the original position is the closest one to the threshold.
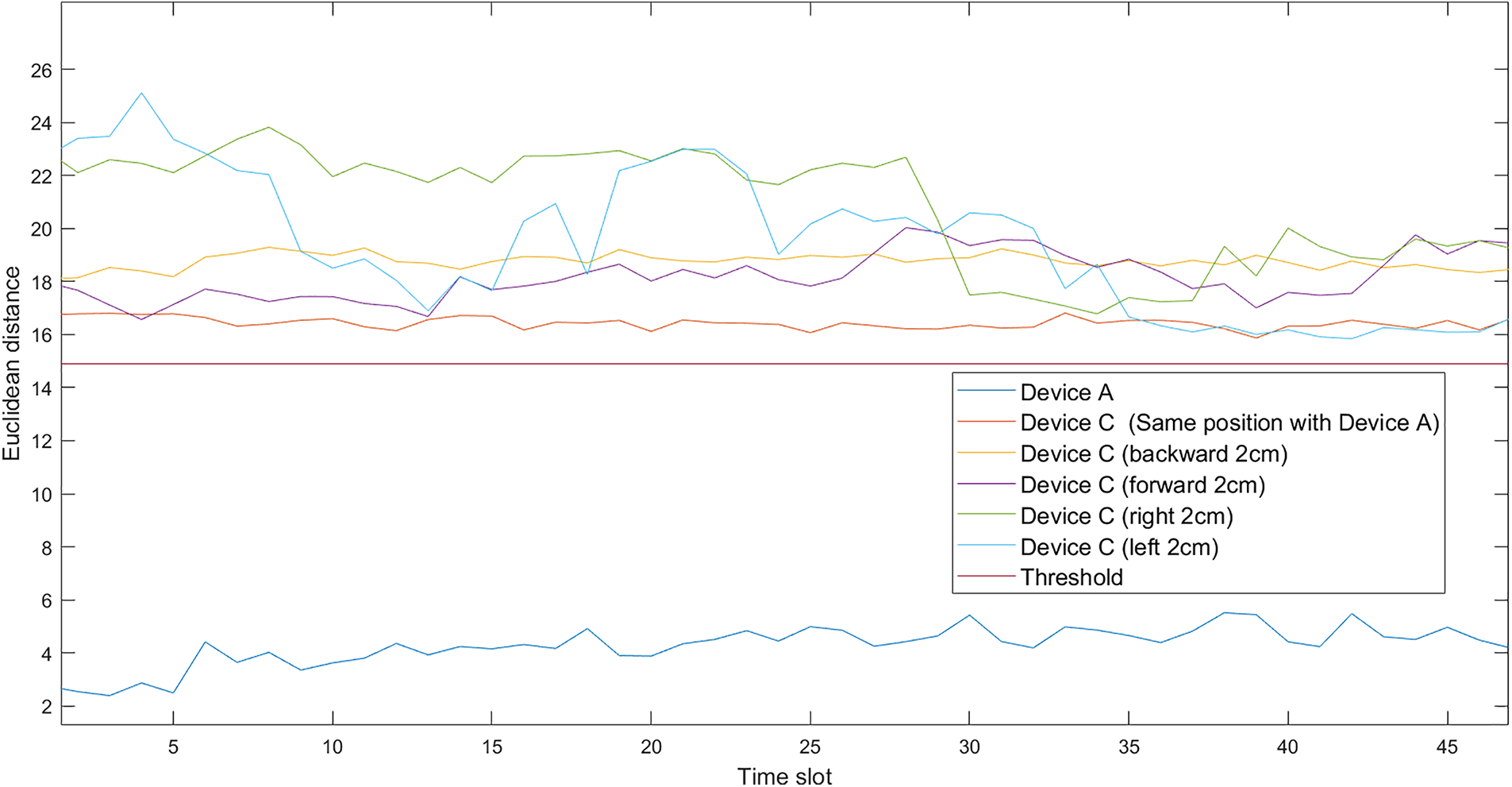
Figure 10: Attacks analysis when the adversary can obtain the original position and the original audio from the legitimate device
In order to study the performance of the proposed scheme, an experiment is conducted, in which, the distance between the device and the AP is
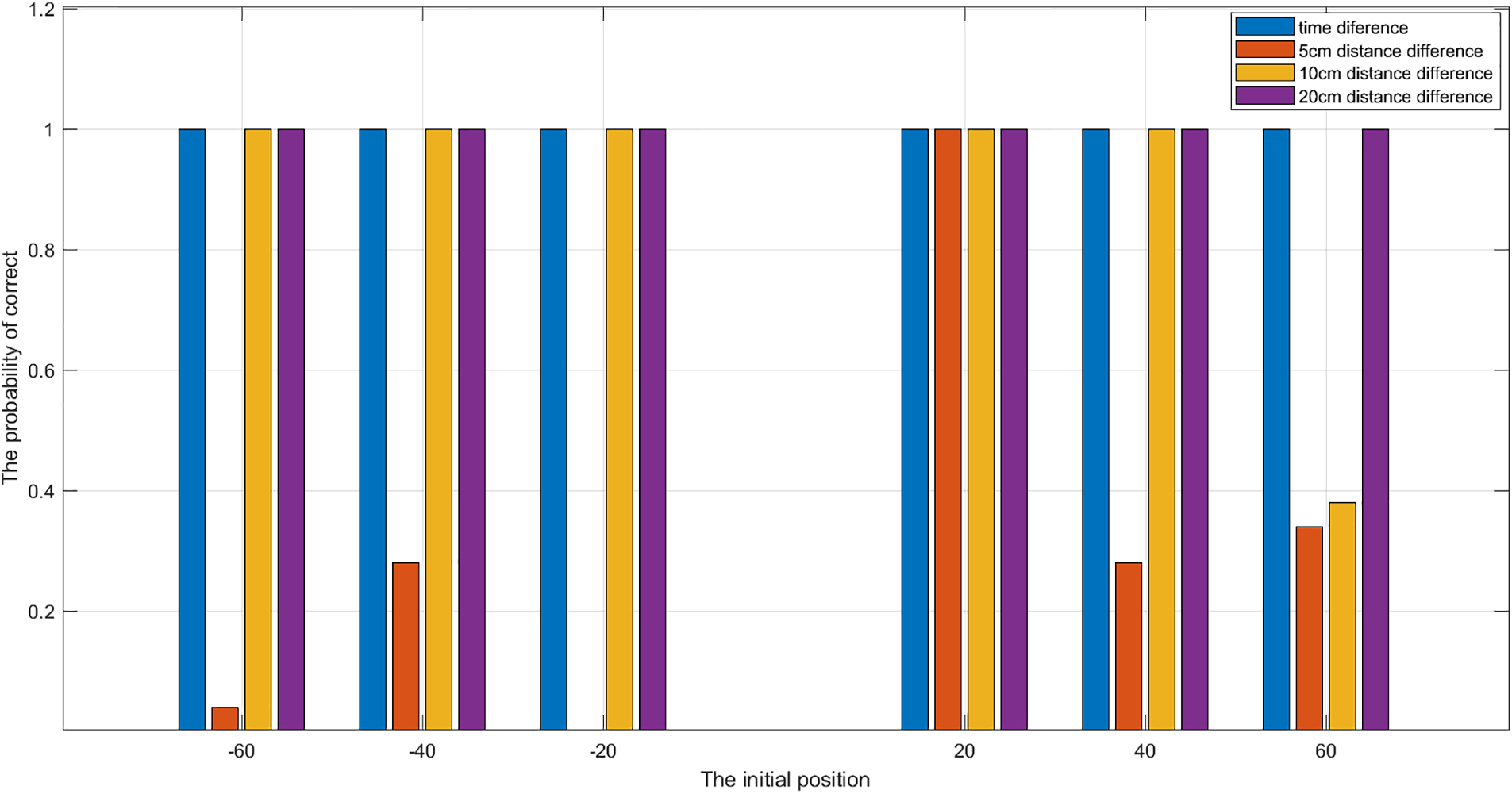
Figure 11: The performance of the proposed scheme
To further discuss the performance, we test the proposed scheme by selecting three places that are very common in daily life, and the noise level ranged from high to low: restaurants, supermarkets and classrooms. In this experiment, the AP is 100 cm away from the device in the direction 1, and 1000 groups of tests are performed for each place, in which the first 500 groups of talking phones do not move and the last 500 groups of talking phones move 30 cm away. The test results are shown in the Fig. 12. It can be seen that, whether in a noisy restaurant or a quiet classroom, the proposed scheme can identify whether a device to move with a 100% probability, which is perfectly in line with the expectation.
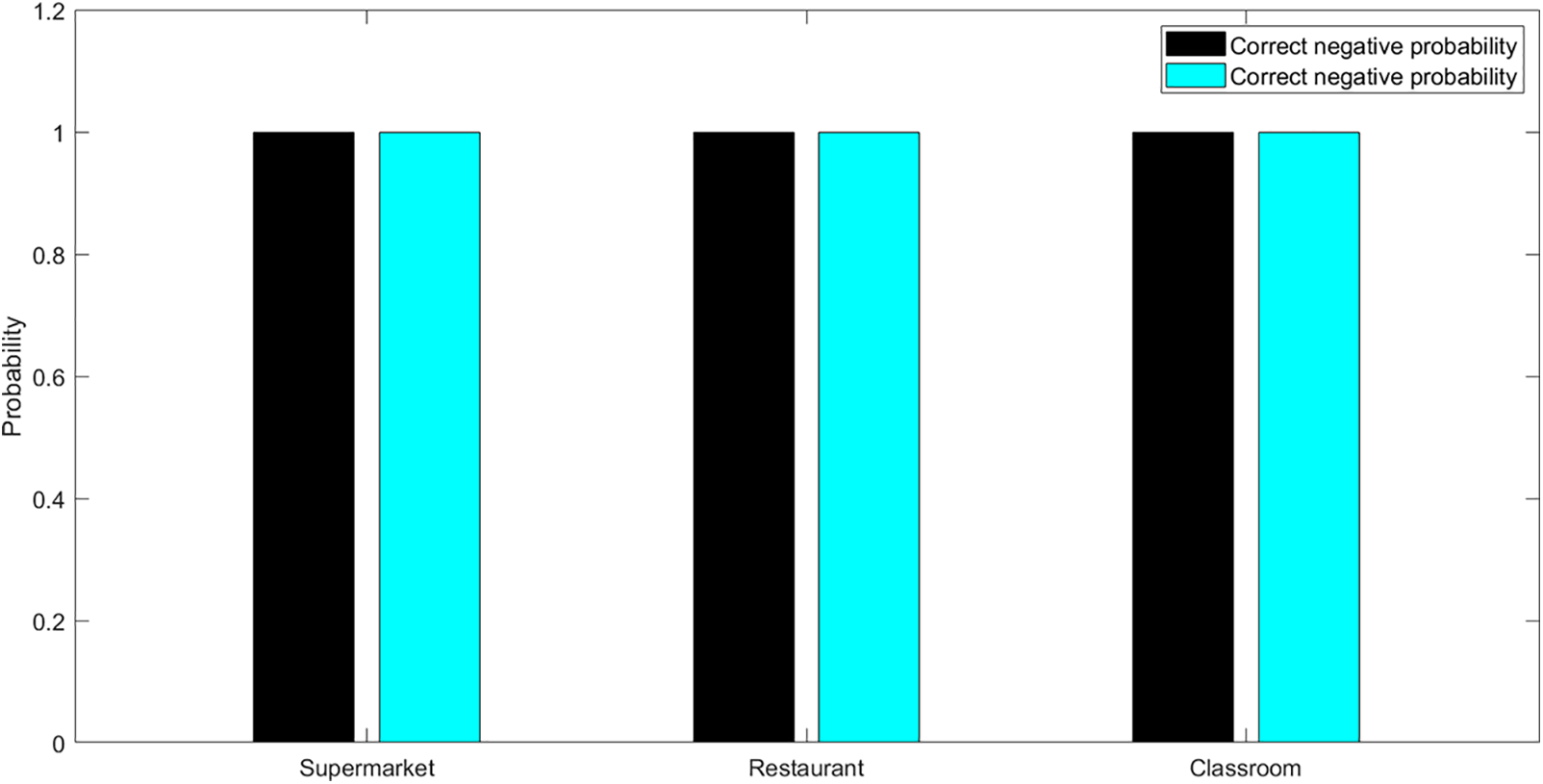
Figure 12: The test of the proposed scheme over restaurants, supermarkets and classrooms
Finally, we conduct an experiment to evaluate the energy consumption compared with several common APPs on mobile phones in the Fig. 13. In this experiment, all applications are turned off except the test software. We measure the power consumption of the proposed scheme and other applications (i.e., NetEases could music, QQ music, QQ, and Microblog) within one hour to verify the efficiency of the software. We can see that the power consumption of the proposed scheme is more than 30 times lower than that of similar music playing software, 18 times lower than that of chat tool software, and 40 times lower than that of video and picture browsing software.

Figure 13: The energy consumption of the proposed scheme compared with several common APPs
Discussion. The disadvantage of the proposed scheme is that the transmission of high-frequency sound waves may disturb nearby people. Possible solutions include replacing mixed sine-wave signals with melodious mid-to-high frequency music or using ultrasonic frequencies to send and receive acoustic signals.
In this paper, a secure device management scheme with audio-based location distinction in IoT has been proposed by utilizing traditional cryptographic techniques. In our scheme, the traditional cryptographic techniques are utilized to realize the integrity, authentication, and non-repudiation of information transmitted between devices, APs, and Severs; and the audio-based location distinction method is designed for identifying the devices, as well as detecting the position change of them. The audio frequency response (AFR) at several frequency points is utilized as the signature of a device to identify the devices and detect the movements. To evaluate the performance of the proposed scheme, extensive experiments are conducted. The experimental results show that the proposed scheme has a good performance in security, accuracy and energy consumption. Future research directions include implementing the designed method using ultrasound and verifying the validity of the method in a real IoT scenario, such as the Internet of Medicine (IoM).
Acknowledgement: Authors thank editors and reviewers for helping the enrichment of this article.
Funding Statement: This work is supported by Demonstration of Scientific and Technology Achievements Transform in Sichuan Province under Grant 2022ZHCG0036, National Natural Science Foundation of China (62002047).
Author Contributions: Study conception and design: Haifeng Lin, Mingsheng Cao; data collection: Xiangfeng Liu, Chen Chen; analysis and interpretation of results: Zhibo Liu, Dexin Zhao; draft manuscript preparation: Yiwen Zhang, Weizhuang Li. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Not available.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. Shen, X., Gao, J., Wu, W., Li, M., Zhou, C. et al. (2022). Holistic network virtualization and pervasive network intelligence for 6G. IEEE Communications Surveys & Tutorials, 24(1), 1–30. [Google Scholar]
2. Wu, W., Zhou, C., Li, M., Wu, H., Zhou, H. et al. (2022). AI-native network slicing for 6G networks. IEEE Wireless Communications, 29(1), 96–103. [Google Scholar]
3. Zhang, N., Yang, P., Ren, J., Chen, D., Yu, L. et al. (2018). Synergy of big data and 5G wireless networks: Opportunities, approaches, and challenges. IEEE Wireless Communications, 25(1), 12–18. [Google Scholar]
4. James Jose, C., Rajasree, M. (2023). Implicit continuous user authentication for mobile devices based on deep reinforcement learning. Computer Systems Science and Engineering, 44(2), 1357–1372. [Google Scholar]
5. Chen, D., Zhao, Z., Qin, X., Luo, Y., Cao, M. et al. (2022). MAGLeak: A learning-based side-channel attack for password recognition with multiple sensors in IIoT environment. IEEE Transactions on Industrial Informatics, 18(1), 467–476. [Google Scholar]
6. Ale, L., Zhang, N., Wu, H., Chen, D., Han, T. et al. (2019). Online proactive caching in mobile edge computing using bidirectional deep recurrent neural network. IEEE Internet of Things Journal, 6(3), 5520–5530. [Google Scholar]
7. Chen, D., Jiang, S., Zhang, N., Liu, L., Choo, K. K. R. (2022). On message authentication channel capacity over a wiretap channel. IEEE Transactions on Information Forensics and Security, 17, 3107–3122. [Google Scholar]
8. Mei, Q., Xiong, H., Chen, Y., Chen, C. (2022). Blockchain-enabled privacy-preserving authentication mechanism for transportation CPS with cloud-edge computing. IEEE Transactions on Engineering Management. https://doi.org/10.1109/TEM.2022.3159311 [Google Scholar] [CrossRef]
9. Xiong, H., Zhou, Z., Wang, L., Zhao, Z., Huang, X. et al. (2022). An anonymous authentication protocol with delegation and revocation for content delivery networks. IEEE Systems Journal, 16(3), 4118–4129. [Google Scholar]
10. Ghubaish, A., Salman, T., Zolanvari, M., Unal, D., Al-ALi, A. et al. (2020). Recent advances in the internet-of-medical-things (IoMT) systems security. IEEE Internet of Things Journal, 8(11), 8707–8718. [Google Scholar]
11. Bohr, A., Memarzadeh, K. (2020). The rise of artificial intelligence in healthcare applications. In: Artificial intelligence in healthcare, pp. 25–60. Cambridge: Academic Press. [Google Scholar]
12. Gheisari, M., Najafabadi, H., Alzubi, J., Gao, J., Wang, G. et al. (2021). OBPP: An ontology-based framework for privacy-preserving in IoT-based smart city. Future Generation Computer Systems, 123, 1–13. [Google Scholar]
13. Wang, J., Xu, C., Zhang, J., Zhou, R. (2022). Big data analytics for intelligent manufacturing systems: A review. Journal of Manufacturing Systems, 62, 738–752. [Google Scholar]
14. Chen, D., Wang, H., Zhang, N., Nie, X., Dai, H. et al. (2022). Privacy-preserving encrypted traffic inspection with symmetric cryptographic techniques in IoT. IEEE Internet of Things Journal, 9(18), 17265–17279. [Google Scholar]
15. Iadanza, E., Gonnelli, V., Satta, F., Gherardelli, M. (2019). Evidence-based medical equipment management: A convenient implementation. Medical Biological Engineering & Computing, 57(10), 2215–2230. [Google Scholar]
16. Hernández-Lŏpez, L., Pimentel-Aguilar, A., Ortiz-Posadas, M. (2020). An index to prioritize the preventive maintenance of medical equipment. Health and Technology, 10(2), 399–403. [Google Scholar] [PubMed]
17. Lu, L., Pan, J. (2021). Does hospital competition lead to medical equipment expansion? Evidence on the medical arms race. Health Care Management Science, 24(3), 582–596. [Google Scholar] [PubMed]
18. Park, J., Yim, K. (2021). Technical survey on the real time eye-tracking pointing device as a smart medical equipment. Smart Media Journal, 10(1), 9–15. [Google Scholar]
19. Yao, W., Wu, M., Wang, J. (2018). Internet of Things in centralized management of medical equipment. 2018 11th International Congress on Image and Signal Processing, BioMedical Engineering and Informatics (CISP-BMEI), pp. 1–5. Piscataway, IEEE. [Google Scholar]
20. Kai, Y. (2020). Research on intelligent interactive system of medical equipment and sickbed. 2020 IEEE 2nd Eurasia Conference on Biomedical Engineering, Healthcare and Sustainability (ECBIOS), pp. 89–91. Piscataway, IEEE. [Google Scholar]
21. Verma, R., Kumari, A., Anand, A. (2022). Revisiting shift cipher technique for amplified data security. Journal of Computational and Cognitive Engineering. https://doi.org/10.47852/bonviewJCCE2202261 [Google Scholar] [CrossRef]
22. Jang, B., Kim, H. (2018). Indoor positioning technologies without offline fingerprinting map: A survey. IEEE Communications Surveys & Tutorials, 21(1), 508–525. [Google Scholar]
23. Zuo, Z., Liu, L., Zhang, L. (2018). Indoor positioning based on Bluetooth low-energy beacons adopting graph optimization. Sensors, 18(11), 3736. [Google Scholar] [PubMed]
24. Bahreini, R., Doshmangir, L., Imani, A. (2018). Affecting medical equipment maintenance management: A systematic review. Journal of Clinical & Diagnostic Research, 12(4), IC01–IC07. [Google Scholar]
25. Wani, A., Khaliq, R. (2018). SDN-based intrusion detection system for IoT using deep learning classifier (IDSIoT-SDL). CAAI Transactions on Intelligence Technology, 6(3), 281–290. [Google Scholar]
26. Wang, Y., Wang, Q., Chen, X., Chen, D., Fang, X. et al. (2020). Containerguard: A real-time attack detection system in container-based big data platform. IEEE Transactions on Industrial Informatics, 18(5), 3327–3336. [Google Scholar]
27. Xiong, H., Hou, Y., Huang, X., Chen, C. (2022). Heterogeneous signcryption scheme from IBC to PKI with equality test for WBANs. IEEE Systems Journal, 16(2), 2391–2400. [Google Scholar]
28. Qin, Z., Sun, J., Chen, D., Xiong, H. (2017). Flexible and lightweight access control for online healthcare social networks in the context of the Internet of Things. Mobile Information Systems, 2017, 1–15. [Google Scholar]
29. Xiong, H., Yang, M., Yao, T., Chen, J., Kumari, S. (2022). Efficient unbounded fully attribute hiding inner product encryption in cloud-aided WBANs. IEEE Systems Journal, 16(4), 5424–5432. [Google Scholar]
30. Ahmed, S., Alhumam, A. (2021). Unified computational modelling for healthcare device security assessment. Computer Systems Science and Engineering, 37(1), 1–18. https://doi.org/10.32604/csse.2021.015775 [Google Scholar] [CrossRef]
31. Turab, N., Abu Owida, H., Al-Nabulsi, J., Abu-Alhaija, M. (2022). Recent techniques for harvesting energy from the human body. Computer Systems Science and Engineering, 40(1), 167–177. https://doi.org/10.32604/csse.2022.017973 [Google Scholar] [CrossRef]
32. Tsai, M. H., Pan, C. S., Wang, C. W., Chen, J. M., Kuo, C. B. et al. (2019). RFID medical equipment tracking system based on a location-based service technique. Journal of Medical and Biological Engineering, 39(1), 163–169. [Google Scholar]
33. Yao, L., Shang, D., Zhao, H., Hu, S. (2021). Medical equipment comprehensive management system based on cloud computing and Internet of Things. Journal of Healthcare Engineering, 2021(4), 1–12. [Google Scholar]
34. Ni, M., Deng, H., He, X., Gong, X. (2021). A single pixel tracking system for microfluidic device monitoring without image processing. Optics and Lasers in Engineering, 151, 106875. [Google Scholar]
35. Gladson, S., Purusothaman, T. (2022). Lightweight and secure mutual authentication scheme for iot devices using coap protocol. Computer Systems Science and Engineering, 41(2), 767–780. https://doi.org/10.32604/csse.2022.020888 [Google Scholar] [CrossRef]
36. Ahmad, M., Al-Amri, J., Subahi, A., Khatri, S., Hussain, A. et al. (2022). Healthcare device security assessment through computational methodology. Computer Systems Science and Engineering, 41(2), 811–828. https://doi.org/10.32604/csse.2022.020097 [Google Scholar] [CrossRef]
37. Cao, S., Zhang, G., Liu, P., Zhang, X., Ne, F. (2019). Cloud-assisted secure eHealth systems for tamper-proofing EHR via blockchain. Information Sciences, 485, 427–440. [Google Scholar]
38. Zou, J., Ling, F., Shi, X., Xu, K., Wu, H. et al. (2021). An electromagnetic fiber acoustic transducer with dual modes of loudspeaker and microphone. Small, 17(45), 2102052. [Google Scholar]
39. Chen, D., Zhang, N., Qin, Z., Mao, X., Qin, Z. (2017). S2M: A lightweight acoustic fingerprints based wireless device authentication protocol. IEEE Internet of Things Journal, 4(1), 88–100. [Google Scholar]
40. Qin, Z., Zhao, P., Zhuang, T., Deng, F., Ding, Y. et al. (2023). A survey of identity recognition via data fusion and feature learning. Information Fusion, 91, 694–712. [Google Scholar]
41. Chen, D., Mao, X., Qin, Z., Wang, W., Li, X. et al. (2015). Wireless device authentication using acoustic hardware fingerprints. Proceedings of Bigcom 2015, pp. 193–204. Hangzhou, China. [Google Scholar]
42. Akkar, M., Giraud, C. (2001). An implementation of DES and AES, secure against some attacks. Proceedings of International Workshop on Cryptographic Hardware and Embedded Systems, pp. 309–318. Berlin, Heidelberg, Springer. [Google Scholar]
43. Malone-Lee, J., Mao, W. (2003). Two birds one stone: Signcryption using RSA. In: Topics in cryptology-CT-RSA 2003, vol. 2612, pp. 211–225. San Francisco, CA, USA, Berlin, Heidelberg: Springer. [Google Scholar]
44. Chen, D., Zhang, N., Wu, H., Zhang, K., Lu, R. et al. (2022). Security techniques for secure device-to-device (D2D) communications. IEEE Network, 36(6), 54–59. [Google Scholar]
45. Faragallah, O., Farouk, M., El-Sayed, H., El-Bendary, A. M. (2022). Secure audio transmission over wireless uncorrelated rayleigh fading channel. Computers, Materials & Continua, 70(1), 1603–1615. https://doi.org/10.32604/cmc.2022.019710 [Google Scholar] [CrossRef]
46. Si, H., Cai, Y., Cheng, Z. (2010). An improved RSA signature algorithm based on complex numeric operation function. IEEE International Conference on Challenges in Environmental Science and Computer Engineering, pp. 397–400. Wuhan, China. [Google Scholar]
47. Christ, M., Braun, N., Neuffer, J., Kempa-Liehr, A. W. (2018). Time series feature extraction on basis of scalable hypothesis tests (tsfresh–A python package). Neurocomputing, 307, 72–77. [Google Scholar]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools