 Open Access
Open Access
ARTICLE
Quantum-Resistant Multi-Feature Attribute-Based Proxy Re-Encryption Scheme for Cloud Services
1 State Key Laboratory of Public Big Data, College of Computer Science and Technology, Guizhou University, Guiyang, 550025, China
2 Key Laboratory of Advanced Manufacturing Technology, Ministry of Education, Guizhou University, Guiyang, 550025, China
3 College of Information, Guizhou University of Finance and Economics, Guiyang, 550025, China
* Corresponding Author: Changgen Peng. Email:
(This article belongs to the Special Issue: Information Security Practice and Experience: Advances and Challenges)
Computer Modeling in Engineering & Sciences 2024, 138(1), 917-938. https://doi.org/10.32604/cmes.2023.027276
Received 22 October 2022; Accepted 28 April 2023; Issue published 22 September 2023
Abstract
Cloud-based services have powerful storage functions and can provide accurate computation. However, the question of how to guarantee cloud-based services access control and achieve data sharing security has always been a research highlight. Although the attribute-based proxy re-encryption (ABPRE) schemes based on number theory can solve this problem, it is still difficult to resist quantum attacks and have limited expression capabilities. To address these issues, we present a novel linear secret sharing schemes (LSSS) matrix-based ABPRE scheme with the fine-grained policy on the lattice in the research. Additionally, to detect the activities of illegal proxies, homomorphic signature (HS) technology is introduced to realize the verifiability of re-encryption. Moreover, the non-interactivity, unidirectionality, proxy transparency, multi-use, and anti-quantum attack characteristics of our system are all advantageous. Besides, it can efficiently prevent the loss of processing power brought on by repetitive authorisation and can enable precise and safe data sharing in the cloud. Furthermore, under the standard model, the proposed learning with errors (LWE)-based scheme was proven to be IND-sCPA secure.Keywords
It is worth noting that sensitive data is being shared and held increasingly in the third party, such as AWS, AliCloud, iCloud, etc. In the current era of cloud computing and data protection, fine-grained access management of encrypted data is a crucial requirement. While sharing data in an open, complicated network environment, there is a chance that personal information will be compromised. For example, in telemedicine system, patients have to store the medical data to the cloud server of the hospital, so that medical service personnel can better analyze the health status of patients after downloading from the cloud. While sharing medical data brings about much convenience to patients and medical service personnel in the system, it also causes new privacy and security issues. Medical data usually contains patients’ sensitive information, thus, it is extremely important for patients. In addition, patients would only like the medical data to be obtained by authorized medical service personnel. In an ideal situation, people hope to encrypt data to a semi-trusted cloud service provider for privacy protection purposes. At the same time, the encrypted data can realize data access control and ciphertext selection calculation as well. In other words, a cryptographic mechanism is needed to make sure “who” can access the encrypted data, and that they can get “what” from the encrypted data.
Proxy re-encryption (PRE) [1] is regarded as a particular primitive in public key cryptography that can give flexible data access authorization for encrypted data in accordance with user needs. Additionally, due to the capability of PRE to securely convert ciphertext, this technology has undergone extensive research and has proven to be quite useful in the cloud context. Currently, PRE is widely employed in many areas of the cloud computing environment, including access control, distributed file systems, encrypted mail forwarding systems, spam filtering systems, etc. ABPRE provides a good solution for the above scenarios. A semi-trusted proxy in an ABPRE system having access to a re-encryption key (created by a delegator) can convert ciphertext that satisfies an access policy into another ciphertext for a delegatee that complies with a new access policy. This greatly reduces the overhead of the data encryption process, enhances non-interactive fine-grained access control, and significantly improves efficiency. Users can share or access data securely, and reliably through a semi-trusted cloud computing service provider. It should be noted that in this process, the proxy is unable to obtain anything about the plaintext. Users achieve the goal of sharing data file safely and efficiently in this way. Due to its characteristics, ABPRE is very suitable for cloud storage environment.
In 2011, Boneh et al. [2] put forth the idea of functional encryption (FE), which broke the deadlock of the original “all or nothing” access mode. FE can not only accomplish the objective of fine-grained access control (only users who meet certain policies can decrypt), but also can select ciphertext. Compared with traditional public-key cryptography (PKC), FE has stronger expression ability. Later, the fuzzy identity-based encryption was constructed by Sahai et al. [3], which was also regarded as the original form of attribute-based encryption (ABE). Especially, ABE is a special FE. In an ABE system, the ciphertext and the secrect key correspond to the attribute set and access policy respectively. The user can decode and access the ciphertext via the secret key after the attribute set of the ciphertext fulfills the access policy.
Lattice cryptography is a kind of PKC, which is widely considered to not be threatened by quantum computing. What’s more, the security of lattice cryptography is based on the difficulty of solving lattice problems in the average case. Based on this superior feature, scholars began to focus on the design of the FE schemes on lattice. Boyen [4] realized FE for access structures based on the LWE hardness assumptions in 2013. More specifically, the key-policy attribute-based encryption (KP-ABE) scheme with monotonic access structure was the first ABE scheme on lattice that supported general Boolean expressions. In 2018, Dai et al. [5] first reported their implementation of a lattice-based KP-ABE scheme, which used short secret keys. What’s more, the homomorphism of the public key and the ciphertext was considered in their proposed scheme as well. In 2019, Tsabary [6] constructed a fully secure ciphertext-policy attribute-based encryption (CP-ABE) for t-CNF from LWE. Varri et al. [7] presented a CP-ABE scheme from the lattice. It is noteworthy that their scheme only allowed valid users of the access policy to conduct keyword searches on the encrypted index, but users who were not in the access policy could not obtain documents in the ciphertext. Recently, to realize attribute revocation, Zhao et al. [8] presented a revocable ABE scheme, which can expediently renew users’ attributes to revoke or grant their access rights. Besides, Fu et al. [9] put forward an offline/online CP-ABE, which had better computational performance for mobile device scenario. In the same year, Fu et al. [10] comprehensively summarized various kinds of ABE schemes from the lattice in terms of complexity assumptions, expressiveness, security, efficiency. In addition, they discussed ABE schemes on lattices which were deserving further research.
With the rapid development of cloud storage technology, the problems of data security and sharing have received extensive attention from industry and academia. PRE is an encryption method that can safely convert ciphertext. It allows that a non-completely trusted third party can directly convert the user Alice’s ciphertext into other users’ ciphertext without decryption, which guarantees the privacy and security of the data left with the third party.
The following desired characteristics should be met by a pretty PRE scheme:
• Proxy transparency: In the transparent PRE scheme, neither the delegator nor the delegatee knows the existence of the proxy, meanings that the ciphertext sent to the delegatee after re-encryption is indistinguishable from the ciphertext originally sent to the delegatee;
• Non-interactivity: The delegator does not require the assistance of the delegatee or any other third party for the generation of the proxy re-encryption key;
• Unidirectionality: The non-reliable proxy can only change the ciphertext of the delegator into the ciphertext of the delegatee; Conversely, it cannot change the delegatee’s ciphertext;
• Multi-use: The non-reliable proxy can also repeatedly re-encrypt the ciphertext that has already been re-encrypted in the unidirectional PRE, as shown in Fig. 1.

Figure 1: Schematic of multi-use PRE
The initial proposal for a lattice-based multi-bit encryption, unidirectional, and multi-use PRE scheme was made by Jiang et al. [11]. They improved the encryption efficiency. Besides, they proved that in the standard model under LWE, the scheme achieved CPA security. In 2016, PRE with multiple properties was put forward by Kim et al. [12]. What’s more, the scheme was key optimality, non-interactivity, unidirectional, invisibility, collusion-resistant and non-transferability. But unfortunately, only in the random oracle model was it demonstrated to be secure. In 2021, Dutta et al. [13] presented the concrete constructions identity-based PRE, which proved both selective and adaptive security. Furthermore, the scheme they came up with satisfied the nature of unidirectionality and anti-collusion. However, fine-grained access control was not supported by the proposed scheme. Therefore, the subsequent research work was aimed at designing a new cryptographic primitive combining ABE and PRE [14,15] in order to meet the requirements.
The ABPRE scheme combines ABE with PRE. This not only ensures that the new encryption scheme has the special conversion property of PRE, but also enables accessing the encrypted data of users who satisfy the access structure. This is achieved by setting up a corresponding access structure. The owner of the data has total authority over the data, while ensuring data confidentiality. Nowadays, ABPRE is widely used in distributed file systems, electronic medical systems, cloud storage services and other scenarios. Li et al. [16] constructed a key-policy attribute-based proxy re-encryption (KP-ABPRE) scheme based on the matrix access structure, but it was difficult to resist quantum attacks. Although lattice-based ABE and PRE schemes have been realized with the continuous development of lattice theory, the ABPRE schemes against quantum attacks have been realized only in the last few years. Therefore, there is less relevant literature about lattice-based ABPRE. Li et al. [17] designed the first ciphertext-policy ABPRE under the LWE assumption. Their scheme only supported the access structure of the AND gate, and the access policy’s expressiveness was relatively weak. To be able to control the proxy’s ability to re-encrypt the original ciphertext, Liang et al. [18] constructed the conditional ABPRE from lattice firstly, which met the requirements of more fine-grained data sharing. However, the schemes of [17] and [18] only satisfied the nature of single-use. This limited the practicality of the scheme. In addition, Susilo et al. [19] constructed an ABPRE that is honest and secure against re-encryption attacks, improving the security of ABPRE. To illustrate the potential of our research, we compare the existing (attribute-based) PRE schemes with our put forward scheme in Table 1.
From the Table 1, we can see that the existing PRE schemes generally have the following obvious problems:
• The majority of the assumptions underlying current ABPRE scheme research come from traditional number theory. However, these traditional encryption schemes can not resist quantum attacks;
• The feasibility of the existing PRE schemes is somewhat hampered by the fact that they only meet two or three characteristics. Besides, the proxy is regarded as a semi-trusted party, but there are few restrictive measures to check the legitimacy on the malicious proxy’s activities;
• At present, most ABPRE schemes expression strategies are limited, which seriously hinders the feasibility of the ABPRE schemes in practical applications.
In summary, it is crucial to create a powerful ABPRE scheme to withstand quantum attacks in cryptography. Fortunately, the lattice-based cryptosystems can effectively resist quantum attacks. Consequently, constructing lattice-based ABPRE schemes with multiple properties has important theoretical significance and broad application prospects.
Designing a post-quantum secure ABPRE scheme with a variety of properties under the standard model is a very meaningful research project. Therefore, we constructed an ABPRE scheme based on key-policy with re-encryption verifiability in the research (named KPAB-VPRE):
• LSSS matrix is adopted to obtain a KP-ABPRE scheme that supports any monotonic policies. The delegator can formulate the corresponding attribute sets and encrypt the message on these attribute sets. Only when the attribute sets on the ciphertext meet the delegatee’s access policy can the ciphertext be decrypted. Our KP-ABPRE scheme uses the access structure constructed by the attribute sets to control the delegatee that can realize the flexible PRE. The delegatee can be one person, one organization or multiple organizations;
• Taking the activities of corrupt proxy into consideration, the scheme is combined with homomorphic signature technology to realize the verifiability of re-encryption. In other words, during the re-encryption process, our KP-ABPRE with re-encryption verifiability (KPAB-VPRE) scheme can be verified whether the proxy performed an honest re-encryption operation. This property greatly enhances the security of the PRE;
• In general, few ABPRE schemes can satisfy three or more properties. While, we design a multi-feature KPAB-VPRE scheme with proxy transparency, non-interactivity, unidirectionality multi-use and anti-quantum attack, which can greatly enhance the practicability of the program. What’s more, under the standard model, our KPAB-VPRE scheme is proven to be selectively IND-CPA secure.
In order to better obtain an understanding of this article, we introduce the relevant notations in the next Section 2, and briefly discuss some basic knowledge that we use. The definition and security model of the KPAB-VPRE scheme are described in the part of Section 3. Then, we construct a KPAB-VPRE scheme with various properties based on LWE. Besides, the security and properties of KPAB-VPRE are analyzed in Section 4. Furthermore, we also assess the effectiveness of the KPAB-VPRE in comparison to relevant literature in Subsection 4.5. Finally, Section 5 presents the conclusions.
In this paper, we apply some initial symbols, as shown in the Table 2.

We give the following useful definitions and lemmas according to literature [4,24–27], consisting of lattice, some algorithms, decision LWE, LSSS and HS.
Definition 2.1. Given a
Lemma 2.1. Set the following parameters,
Here
Lemma 2.2. We assume that given a prime number
•
• There exists a PPT algorithm SamplePre
• There is a PPT algorithm SampleBasisLeft
• Given three matrices
Lemma 2.3. Given a positive integer
The above lemmas are used in the security proof of our scheme to show that the simulated system is indistinguishable from the real system.
Definition 2.2. We assume that the positive integers
•
•
The attacker
Definition 2.3. If the following requirements are met by a secret sharing system
• Each participant’s shares compose a vector over
• The share generating matrix
In addition, a LSSS has linear reconstruction’s characteristics.
2.2.4 Homomorphic Signature-HS
Lemma 2.4. The HS scheme typically makes up the following four algorithms:
• HS.KeyGen
• HS.Sign
• HS.SignEval
• HS.Verify
Correctness: The HS scheme is correct if the following equation holds for any
3 Defnition and the Security Model of KPAB-VPRE
Fig. 2 is an illustration of KPAB-VPRE. And in this encryption system, if user 1 and user 2 want to share encrypted data files, they need to execute the following series of algorithms (Setup, KeyGen, Encrypt, ReKeyGen, ReEncrypt, ReEncVer, Decrypt). Especially, an additional verification algorithm ReEncVer, executed by the verification server, is used to determine whether the ciphertext is an honest transformation. First, User 2 sends a sharing request to User 1, and uploads the access policy to the key generation center. Next, the key generation center issues public and private keys to User 1 and User 2, respectively. After receiving the request, user 1 encrypts the data to be shared with its own private key and calculates the re-encryption key. Then sends the original ciphertext and re-encrypted key to the proxy. The proxy re-encrypts the ciphertext with the re-encryption key and sends the re-encryption ciphertext to the verification server. The verification server sends the re-encrypted ciphertext to User 2 after judgment. Finally, User 2 decrypts the shared data of User 1 by its private key.

Figure 2: The system model of our proposed KPAB-VPRE
Definition 3.1. The following seven algorithms make up a KPAB-VPRE scheme:
• Setup
• KeyGen
• Encrypt
• ReKeyGen
• ReEncrypt
• ReEncVer
• Decrypt
(i) For the original ciphertext
(ii) For the converted ciphertext
Correctness: For parameters
In the part, we mainly describe the security model of KPAB-VPRE, which is based on the indistinguishability under chosen-plaintext attack in the selective security model (IND-sCPA). And we illustrate the model through the interactive games between the adversary
• Target. The adversary
• Instance. The adversary
• Phase 1. The adversary
(i) Secret Key Query
(ii) Re-Encryption Key Query
(iii) Re-Encryption Verification Query
• Challenge. First,
• Phase 2:
• Guess.
For any PPT
• Setup
(i) For each attribute
(ii) Chooses a uniform random variable
(iii) Finally, returns the public parameters
• KeyGen
(i) Converts the user’s access policy P into a shared access policy
(ii) Lets
(iii) Finally, outputs
• Encrypt
(i) Chooses uniformly at random a matrix
(ii) Sets
(iii) Computes
(iv) Outputs the ciphertext
• ReKeyGen
(i) For each attribute
(ii) Creates a low-norm matrix
Therefore, we set
(iii) Runs the algorithm HS.KeyGen
(iv) Finally, delivers
• ReEncrypt
(i) Finds the vector
(ii) Sets two vectors
(iii) Computes a signature
(iv) Finally, outputs the re-encryption ciphertext
• ReEncVer
• Decrypt
(i) Construct two new vectors
where
where
(ii) Lets
(iii) Given a Gaussian parameter
(iv) Calculates
(v) Outputs the result:
(i) The accuracy of unconverted ciphertext decoding. When
(ii) Decryption correctness of converted ciphertext. When
(iii) Correctness of re-encryption ciphertext verification. The effectiveness of the re-encryption ciphertext verification depends on the output of the verification algorithm HS.Verify. Besides, in the ReEncrypt
Remark 4.1. If the parameter setting is reasonable and the noise item in Eqs. (23) and (24) is small enough, the plaintext message can be recovered correctly after decryption.
(i) According to the assumption of the LWE problem, for the Gaussian noise distribution
(ii) According to the algorithm TrapGen
(iii) According to the algorithm SamplePre
(iv) In order to make the error term
Since
Thus, we decided on the following scheme parameters:
where
Theorem 4.1. Assume that
Proof. We utilize the assumption that there is a PPT adversary
Game sequence:
• Game0:
• Game1: This game changes the generation of
(i) TrapGen
(ii) The challenger
(iii) Finally, the attacker
• Game2: The production of the challenge ciphertext
If Game1 is indistinguishable from Game0, and Game2 is indistinguishable from Game1, our KPAB-VPRE scheme is IND-sCPA secure in the standard model.
Game transfer:
• Game0 to Game1: We now prove that Game0 and Game1 are indistinguishable through the Lemma 4.1.
• Lemma 4.1. If
Proof.
(i) The matrix
(ii) For the private key,
From the Lemma 4.1, we can see that the
• Game1 to Game2: Assuming that in the selective security model, an attacker
–Target. The challenger
• –Instance. The challenger
–Setup. The challenger
(i) The central authority selects the appropriate system parameters
(ii) If the attribute
(iii) The remaining parameters are the same as Game1 settings.
Remark 4.2. The above settings have the correct distribution.
–Phase 1. The attacker
Secret Key Query
(i) The attacker
(ii) According to the parameters in Game1, the challenger
Re-Encryption Key Query
(i) The challenger
(ii)
Re-Encryption Verification Query
(i) After
(ii) Finally,
Remark 4.3. Because of the unforgeability of HS, the algorithm ReEncVer cannot provide any additional capabilities for
–Challenge. In order to indicate that it is open to a challenge,
(i) Constructing ciphertext
where
(ii) The challenger
Remark 4.4. The above challenge ciphertext
∗ If
Due to the setting of public parameters, the ciphertext obtained is
where
where
The above
∗
–Phase 2. The simulator
–Guess. After enough questioning, the attacker outputs his guess of
In the attacker
(i) In a pseudo-random sampler, an attacker
(ii) In a true random predictor, an attacker
Therefore, assuming that an attacker
to solve the decision
As a result, Game2 and Game1 cannot be distinguished under the assumption of the decision
In conclusion, the security of our designed KPAB-VPRE scheme is compactly reduced to the decision
• Non-interactivity. Our scheme is non-interactive, because the re-encryption key
• Proxy transparency. Our scheme satisfies this property, because the size of the re-encrypted ciphertext
• Unidirectionality. This property requires that the ciphertext direction can only be converted from Alice to Bob, not in reverse. This is true, because the proxy can get the re-encryption key
• Multi-use. We suppose that
Set
In this part, we compare our KPAB-VPRE with other relevant schemes [13,17,28–30] in terms of the size of the ciphertext, access policy, multi-use, security model, and re-encryption verifiability. And Table 3 displays the comparison’s findings.
As can be seen from Table 3, in the same type of schemes, the literature [13,28–30] did not support the expression of access policy, while the literature [17] only supports “AND” expression. While, our scheme adopts the LSSS matrix to express the access policy and supports the operations of “AND, OR, THRESHOLD”. What’s more, matrix operation is used to realize encryption and decryption algorithm, which has higher efficiency. In terms of the re-encryption verification, only Wu et al. [30] supported this property, but this scheme cannot support arbitrary access policies. Therefore, the proposed scheme realizes fine-grained access and sharing of encrypted data, as well as meets the multi-use and re-encryption verification, which makes the scheme more practical. Especially, our KPAB-VPRE achieves IND-sCPA security under the standard model.
We present a multi-functional LSSS matrix-based KPAB-VPRE scheme from lattice that is proven to be IND-sCPA secure under the standard model. The scheme based on the lattice is implemented by matrix operation, which can facilitate parallel algorithm design and has superior efficiency, as opposed to the classic ABPRE schemes based on bilinear mapping. This scheme is based on the construction of LWE difficult problems from lattice. From the complexity of lattice difficult problems in the worst case, we can see that under the appropriate parameter selection, there is no effective algorithm to solve these difficult problems in polynomial time, even if it is a quantum computer. Therefore, this scheme can resist quantum attacks. In addition, the data owner can encrypt messages on any attribute sets. The ciphertext cannot be actively decoded until the attribute put on it complies with the user’s access policy. Furthermore, the verification of re-encryption is realized by introducing homomorphic signature technology, thereby detecting the activities of corrupt proxies, which has higher security and enforceability in practical scenarios. However, in our KPAB-VPRE scheme, the size of the ciphertext is not fixed, and it grows linearly as the number of attributes increases. Therefore, the next study will focus on creating a multi-functional ABPRE system with fixed ciphertext length in the future.
Acknowledgement: The authors are willing to express our appreciation to the reviewers for their constructive comments which significantly enhanced the presentation of the study.
Funding Statement: The project is provided funding by the Natural Science Foundation of China (Nos. 62272124, 2022YFB2701400), the Science and Technology Program of Guizhou Province (No. [2020]5017), the Research Project of Guizhou University for Talent Introduction (No. [2020]61), the Cultivation Project of Guizhou University (No. [2019]56), the Open Fund of Key Laboratory of Advanced Manufacturing Technology, Ministry of Education, GZUAMT2021KF[01] and the Postgraduate Innovation Program in Guizhou Province (No. YJSKYJJ[2021]028).
Author Contributions: The authors confirm contribution to the paper as follows: study conception and design: Jinqiu Hou; data collection: Weijie Tan; analysis and interpretation of results: Changgen Peng. Hongfa Ding; draft manuscript preparation: Jinqiu Hou. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: All data generated or analysed during this study are included in this published article.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. Blaze, M., Bleumer, G., Strauss, M. (1998). Divertible protocols and atomic proxy cryptography. In: Nyberg, K. (Ed.Advances in cryptology-EUROCRYPT’98, pp. 127–144. Germany: Springer. https://doi.org/10.1007/BFb0054122 [Google Scholar] [CrossRef]
2. Boneh, D., Sahai, A., Waters, B. (2011). Functional encryption: Definitions and challenges. In: Ishai, Y. (Ed.Theory of cryptography, pp. 253–273. Germany: Springer. https://doi.org/10.1007/978-3-642-19571-6_16 [Google Scholar] [CrossRef]
3. Sahai, A., Waters, B. (2005). Fuzzy identity-based encryption. In: Cramer, R. (Ed.Advances in cryptology-EUROCRYPT 2005, pp. 457–473. Germany: Springer. https://doi.org/10.1007/11426639_27 [Google Scholar] [CrossRef]
4. Boyen, X. (2013). Attribute-based functional encryption on lattices. In: Sahai, A. (Ed.Theory of cryptography, pp. 122–142. Germany: Springer. https://doi.org/10.1007/978-3-642-36594-2_8 [Google Scholar] [CrossRef]
5. Dai, W., Doröz, Y., Polyakov, Y., Rohloff, K., Sajjadpour, H. et al. (2018). Implementation and evaluation of a lattice-based key-policy ABE scheme. IEEE Transactions on Information Forensics and Security, 13(5), 1169–1184. https://doi.org/10.1109/TIFS.2017.2779427 [Google Scholar] [CrossRef]
6. Tsabary, R. (2019). Fully secure attribute-based encryption for T-CNF from LWE. In: Boldyreva, A., Micciancio, D. (Eds.Advances in cryptology-CRYPTO 2019, pp. 62–85. Germany: Springer. https://doi.org/10.1007/978-3-030-26948-7_3 [Google Scholar] [CrossRef]
7. Varri, U., Pasupuleti, S. K., Kadambari, K. V. (2021). CP-ABSEL: Ciphertext-policy attribute-based searchable encryption from lattice in cloud storage. Peer-to-Peer Networking and Applications, 14(3), 1290–1302. https://doi.org/10.1007/s12083-020-01057-3 [Google Scholar] [CrossRef]
8. Zhao, S., Jiang, R., Bhargava, B. K. (2022). RL-ABE: A revocable lattice attribute based encryption scheme based on R-LWE problem in cloud storage. IEEE Transactions on Services Computing, 15(2), 1026–1035. https://doi.org/10.1109/TSC.2020.2973256 [Google Scholar] [CrossRef]
9. Fu, X., Wang, Y., You, L., Ning, J., Hu, Z. et al. (2022). Offline/Online lattice-based ciphertext policy attribute-based encryption. Journal of Systems Architecture, 130(6), 102684. https://doi.org/10.1016/j.sysarc.2022.102684 [Google Scholar] [CrossRef]
10. Fu, X., Ding, Y., Li, H., Ning, J., Wu, T. et al. (2022). A survey of lattice based expressive attribute based encryption. Computer Science Review, 43(5), 100438. https://doi.org/10.1016/j.cosrev.2021.100438 [Google Scholar] [CrossRef]
11. Jiang, M., Hu, Y., Wang, B., Wang, F. H., Lai, Q. (2015). Lattice-based multi-use unidirectional proxy re-encryption. Security and Communication Networks, 8(18), 3796–3803. https://doi.org/10.1002/sec.1300 [Google Scholar] [CrossRef]
12. Kim, K. S., Jeong, I. R. (2016). Collusion-resistant unidirectional proxy re-encryption scheme from lattices. Journal of Communications and Networks, 18(1), 1–7. https://doi.org/10.1109/JCN.2016.000003 [Google Scholar] [CrossRef]
13. Dutta, P., Susilo, W., Duong, D. H., Roy, P. S. (2021). Collusion-resistant identity-based proxy re-encryption: Lattice-based constructions in standard model. Theoretical Computer Science, 871(1), 16–29. https://doi.org/10.1016/j.tcs.2021.04.008 [Google Scholar] [CrossRef]
14. Zhang, Y., Deng, R. H., Xu, S., Sun, J., Li, Q. et al. (2020). Attribute-based encryption for cloud computing access control: A survey. ACM Computing Surveys, 53(4), 83:1–83:41. https://doi.org/10.1145/3398036 [Google Scholar] [CrossRef]
15. Wang, X., Hu, A., Fang, H. (2020). Improved collusion-resistant unidirectional proxy re-encryption scheme from lattice. IET Information Security, 14(3), 342–351. https://doi.org/10.1049/iet-ifs.2018.5246 [Google Scholar] [CrossRef]
16. Li, K., Zhang, Y., Ma, H. (2013). Key policy attribute-based proxy re-encryption with matrix access structure. 2013 5th International Conference on Intelligent Networking and Collaborative Systems, Xi’an, China, IEEE. https://doi.org/10.1109/INCoS.2013.17 [Google Scholar] [CrossRef]
17. Li, J., Ma, C., Zhang, K. (2019). A novel lattice-based ciphertext-policy attribute-based proxy re-encryption for cloud sharing. In: Meng, W., Furnell, S. (Eds.Security and privacy in social networks and big data, pp. 32–46. Germany: Springer. https://doi.org/10.1007/978-981-15-0758-8_3 [Google Scholar] [CrossRef]
18. Liang, X., Weng, J., Yang, A., Yao, L., Jiang, Z. et al. (2021). Attribute-based conditional proxy re-encryption in the standard model under LWE. In: Bertino, E., Shulman, H., Waidner, M. (Eds.Computer security-ESORICS 2021, pp. 147–168. Germany: Springer. https://doi.org/10.1007/978-3-030-88428-4_8 [Google Scholar] [CrossRef]
19. Susilo, W., Dutta, P., Duong, D. H., Roy, P. S. (2021). Lattice-based HRA-secure attribute-based proxy re-encryption in standard model. In: Bertino, E., Shulman, H., Waidner, M. (Eds.Computer security-ESORICS 2021, pp. 169–191. Germany: Springer. https://doi.org/10.1007/978-3-030-88428-4_9 [Google Scholar] [CrossRef]
20. Deng, H., Qin, Z., Wu, Q., Guan, Z., Zhou, Y. (2020). Flexible attribute-based proxy re-encryption for efficient data sharing. Information Sciences, 511(1), 94–113. https://doi.org/10.1016/j.ins.2019.09.052 [Google Scholar] [CrossRef]
21. Ge, C., Susilo, W., Baek, J., Liu, Z., Xia, J. et al. (2022). A verifiable and fair attribute-based proxy re-encryption scheme for data sharing in clouds. IEEE Transactions on Dependable and Secure Computing, 19(5), 2907–2919. https://doi.org/10.1109/TDSC.2021.3076580 [Google Scholar] [CrossRef]
22. Xiong, H., Wang, L., Zhou, Z., Zhao, Z., Huang, X. et al. (2022). Burn after reading: Adaptively secure puncturable identity-based proxy re-encryption scheme for securing group message. IEEE Internet of Things Journal, 9(13), 11248–11260. https://doi.org/10.1109/JIOT.2021.3126230 [Google Scholar] [CrossRef]
23. Hou, J., Jiang, M., Guo, Y., Song, W. (2019). Efficient identity-based multi-bit proxy re-encryption over lattice in the standard model. Journal of Information Security and Applications, 47, 329–334. https://doi.org/10.1016/j.jisa.2019.05.015 [Google Scholar] [CrossRef]
24. Agrawal, S., Boneh, D., Boyen, X. (2010). Efficient lattice (H) IBE in the standard model. Annual International Conference on the Theory and Applications of Cryptographic Techniques, Germany, Springer. https://doi.org/10.1007/978-3-642-13190-5_28 [Google Scholar] [CrossRef]
25. Howe, J., Khalid, A., Rafferty, C., Regazzoni, F., O’Neill, M. (2018). On practical discrete gaussian samplers for lattice-based cryptography. IEEE Transactions on Computers, 67(3), 322–334. https://doi.org/10.1109/TC.2016.2642962 [Google Scholar] [CrossRef]
26. Regev, O. (2009). On lattices, learning with errors, random linear codes, and cryptography. Journal of the ACM, 56(6), 34:1–34:40. https://doi.org/10.1145/1568318.1568324 [Google Scholar] [CrossRef]
27. Zhao, J., Gao, H. (2017). LSSS matrix-based attribute-based encryption on lattices. 13th International Conference on Computational Intelligence and Security, Hong Kong, China, IEEE. https://doi.org/10.1109/CIS.2017.00062 [Google Scholar] [CrossRef]
28. Li, J., Qiao, Z., Zhang, K., Cui, C. (2021). A lattice-based homomorphic proxy re-encryption scheme with strong anti-collusion for cloud computing. Sensors, 21(1), 288. https://doi.org/10.3390/s21010288 [Google Scholar] [PubMed] [CrossRef]
29. Singh, K., Rangan, C. P., Agrawal, R., Sheshank, S. (2020). Provably secure lattice based identity based unidirectional PRE and PRE+ schemes. Journal of Information Security and Applications, 54, 102569. https://doi.org/10.1016/j.jisa.2020.102569 [Google Scholar] [CrossRef]
30. Wu, L., Yang, X., Zhang, M., Wang, X. A. (2022). IB-VPRE: Adaptively secure identity-based proxy re-encryption scheme from LWE with re-encryption verifiability. Journal of Ambient Intelligence and Humanized Computing, 13(1), 469–482. https://doi.org/10.1007/s12652-021-02911-9 [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF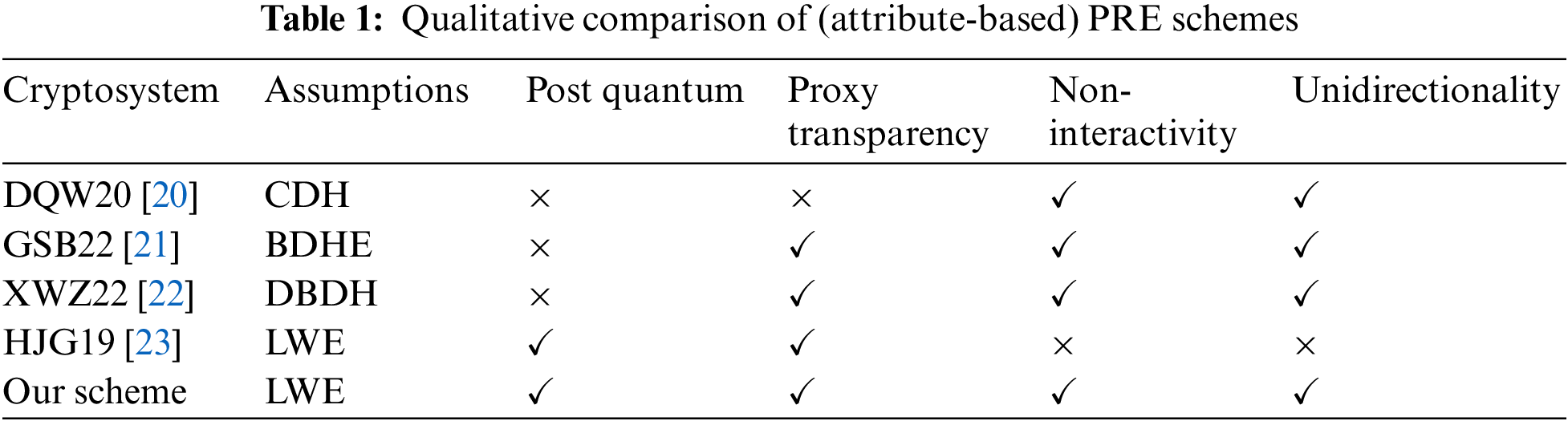

 Downloads
Downloads
 Citation Tools
Citation Tools