 Open Access
Open Access
ARTICLE
Heterogeneous Fault-Tolerant Aggregate Signcryption with Equality Test for Vehicular Sensor Networks
1 Network and Data Security Key Laboratory of Sichuan Province, University of Electronic Science and Technology of China, Chengdu, 610054, China
2 Department of Mathematics, Chaudhary Charan Singh University, Meerut, 250004, India
* Corresponding Author: Saru Kumari. Email:
(This article belongs to the Special Issue: Information Security Practice and Experience: Advances and Challenges)
Computer Modeling in Engineering & Sciences 2023, 137(1), 555-575. https://doi.org/10.32604/cmes.2023.026808
Received 26 September 2022; Accepted 15 December 2022; Issue published 23 April 2023
Abstract
The vehicular sensor network (VSN) is an important part of intelligent transportation, which is used for real-time detection and operation control of vehicles and real-time transmission of data and information. In the environment of VSN, massive private data generated by vehicles are transmitted in open channels and used by other vehicle users, so it is crucial to maintain high transmission efficiency and high confidentiality of data. To deal with this problem, in this paper, we propose a heterogeneous fault-tolerant aggregate signcryption scheme with an equality test (HFTAS-ET). The scheme combines fault-tolerant and aggregate signcryption, which not only makes up for the deficiency of low security of aggregate signature, but also makes up for the deficiency that aggregate signcryption cannot tolerate invalid signature. The scheme supports one verification pass when all signcryptions are valid, and it supports unbounded aggregation when the total number of signcryptions grows dynamically. In addition, this scheme supports heterogeneous equality test, and realizes the access control of private data in different cryptographic environments, so as to achieve flexibility in the application of our scheme and realize the function of quick search of plaintext or ciphertext. Then, the security of HFTAS-ET is demonstrated by strict theoretical analysis. Finally, we conduct strict and standardized experimental operation and performance evaluation, which shows that the scheme has better performance.Graphic Abstract
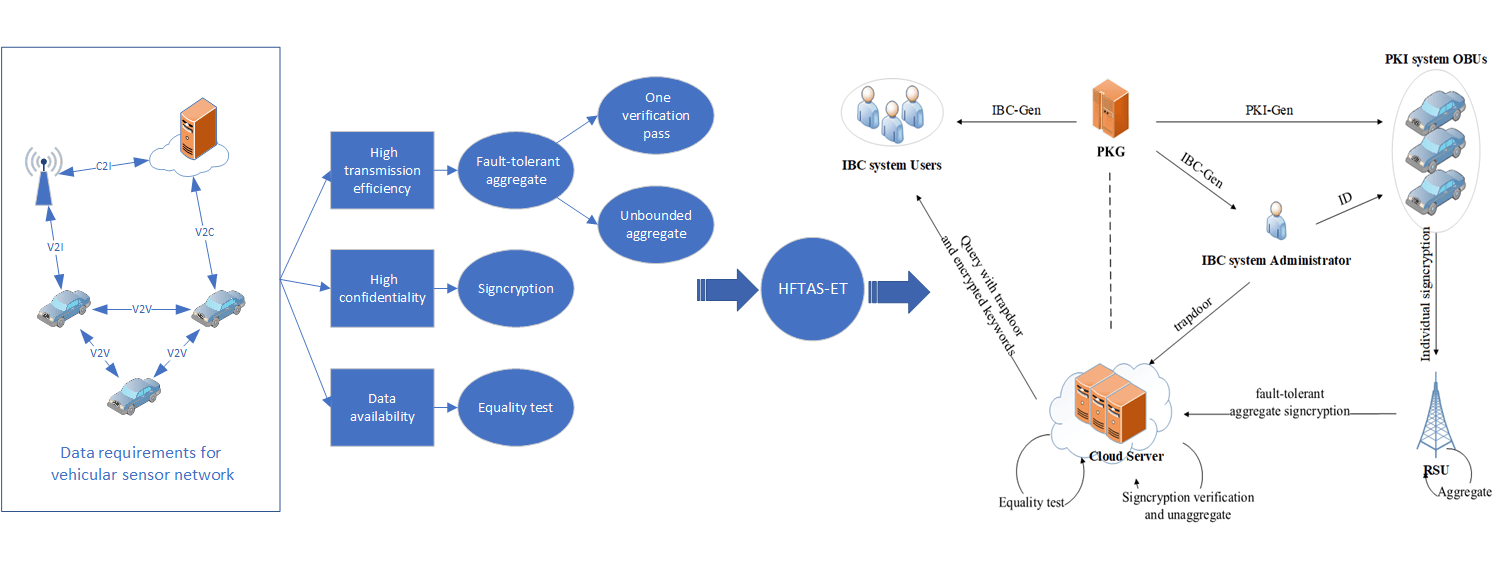
Keywords
In the past few years, the application of Internet of Things (IoT) devices has grown at a great lick, including Industrial Internet of Things (IIoT), intelligent supply chain, electronic medical, smart home and other aspects [1]. Among them, internet of vehicles is one of the most important applications, and the VSN is also one of the key research directions in the academic world. Through wireless communication technology, vehicle equipments effectively use all the dynamic data and information of vehicles in the information network platform. And diverse functional services will be provided by vehicle equipments in the operation control of vehicles.
In the environment of the VSN, massive private data generated by vehicles are transmitted in open channels, such as driving operations inside vehicles, information transmission between vehicles and between vehicles and the Internet. In this case, data confidentiality and transmission efficiency are crucial. At the same time, most IoT rely on cloud computing [2] for massive data processing and services, and strict authentication is required for data use. In this case, data confidentiality and user access are necessary. Therefore, maintaining high transmission efficiency and confidentiality of data is a very important challenge.
In 1976, Diffie [3] researched public key cryptography, and then proposed the concept of digital signature. Digital signature technology combines the identity information of the signer with the signed message, indicating that the signer has signed the message. The verifier can verify that the information is really signed by the signer. Moreover, forging a signature by imitating the signer is difficult. Later, certificate-based signature [4], identity-based signature [5–7] and certificateless signature (CLS) schemes [8–10] emerged successively. However, traditional digital signature has higher computational overhead and lower efficient, so it is not suitable for massive data.
Boneh et al. [11] conducted several research studies to raise verification efficiency and reduce storage capacity. Finally, an aggregate signature scheme was proposed in 2003. This scheme uses the properties of bilinear pairs to generate a short signature, which is more flexible, but it requires different messages to be signed and different participants, which has too many restrictions, higher resource cost and lower availability. Cheon et al. [12] proposed an aggregate signature based identity (IBAS) in 2004. Two certificateless aggregate signature schemes (CLAS) were proposed by Gong et al. [13]. After that, schemes for improvement were put forward in abundance. For example, PFCBAS and CL-DVAAS were proposed respectively by Verma et al. [14] and Deng et al. [15]. These two schemes do not need pair operation, which further improves the verification efficiency. In 2021, Han et al. [16] further improved the existing scheme and proposed an efficient pairing-free CLAS (eCLAS), which reduced the length of signature and the computation cost of verification process. Aggregate signature algorithm is convenient, and it greatly improves the efficiency of verification and effectively reduce the storage capacity. However, aggregate signatures still have two problems: first, the confidentiality of aggregate signatures is low; second, the invalidity of aggregate signatures will lead to the negation of all signatures.
To address the first problem of aggregate signature, Selvi et al. [17] first gave an aggregate signcryption scheme in 2009. Aggregate signcryption aggregates multiple signcrypted ciphertext into a single aggregate signcryption, and the recipient only needs to verify the aggregate signcryption. This means increases the confidentiality of aggregate signature and effectively controls the computation and communication costs [18–21]. In 2011, Lu et al. [22] presented certificateless aggregate signcryption (CLAS), which is based on bilinear mapping and verifiably meets confidentiality and unforgeability. Later, Ren et al. [23] gave a provably secure aggregate signcryption scheme based on identity, which greatly reduced communication overhead, but did not achieve complete aggregation. In 2020, Kim et al. [24] presented a certificateless aggregate signcryption. According to the security requirements and computer resource constraints of IoT, this scheme reduces the computation overhead, communication overhead and storage space, and solves the key aging problem. However, the majority of the existing aggregate signcryption schemes do not support fault tolerance function, and invalid signature will cause that all the aggregated signcrypted ciphertext fail to pass verification.
To address the second issue of aggregate signature, Hartung et al. [25] first presented the concept of fault-tolerant aggregate signatures in 2016, emphasizing fault-tolerant and not mentioning aggregate signature too much, but the scheme was not flexible enough to be applied in practice. In 2019, Wang et al. [26] proposed an improved fault-tolerant aggregate signature scheme with improved flexibility, but there are still defects, that is, all signatures may still be negated due to a certain or very few invalid signatures. Xiong et al. [27] proposed SECLS, a secure certificateless signature scheme. The scheme supports invalid signature recognition and batch verification. Zhao et al. [28] gave CLFTAS, certificateless fault-tolerant aggregate signature. These two schemes further made up for the defects of fault-tolerant aggregate signature, but when all signatures are valid, the two schemes have higher computation overhead and lower verification efficiency. Xiong et al. [29] proposed an efficient batch verification scheme, while focusing on invalid signature identification. In addition, most aggregate signature schemes do not consider unbounded scheme and do not support the case that the dynamic growth of the total number of signatures.
To ensure the availability of data and searchability, Boneh et al. [30] combined the function of a keyword search with public key encryption, and then presented PKE-KS. This scheme not only ensures data confidentiality, but also ensures data searchability. However, there is a problem: data can be searched if the keyword and data are encrypted using the same public key. Xiong et al. [31], Huang et al. [32] and Chen et al. [33] respectively gave solutions can solve the privacy problems caused by cloud servers (CSs), to achieve access control. Xiong et al. [34] and Mei et al. [35] respectively proposed solutions to the privacy problems of Internet of vehicles and blockchain. In 2010, Yang et al. [36] combined the function of equality test with public key encryption, and then presented PKE-ET. This scheme is not affected by the public key in the encryption process and can carry out equality test discretionarily between ciphertexts. Since then, many scholars have conducted in-depth studies in this field [37–39]. In 2020, Xiong et al. [40] improved this method and applied it to the IIoT environment, which realized data access control in a heterogeneous environment and further improved data security and confidentiality. After that, Xiong et al. [41] ameliorated the scheme further. Xiong et al. [42] revocable scheme and Wu et al. [43] key agreement scheme focus on key security.
For the sake of resolving the above problems, and considering heterogeneity in actual IoT environment, different entities may have different cryptographic environments, so it is necessary to design a fault-tolerant aggregate signcryption scheme that supports a heterogeneous environment.
As shown in Fig. 1, a vehicle in the PKI system (because the vehicle interior is the on-board unit with computing power and communication ability, so the vehicle can be called on-board unit (OBU)) signcrypts message by using the administrator’s ID and its own private key to form an individual signcryption, then sends it to the roadside unit (RSU). RSU implements fault-tolerant aggregate of multiple signcryptions and sends aggregate signcryption to CS. At the same time, CS receives trapdoor generated by the administrator in the IBC system. When a user wants to use some data in the IBC system, he encrypts the keywords with his own ID and the corresponding trapdoor, and then sends the encrypted messages to CS. CS determines user’s access rights by executing an equality test on the encrypted messages. If the user has right to access these data, CS will return the corresponding data to him.
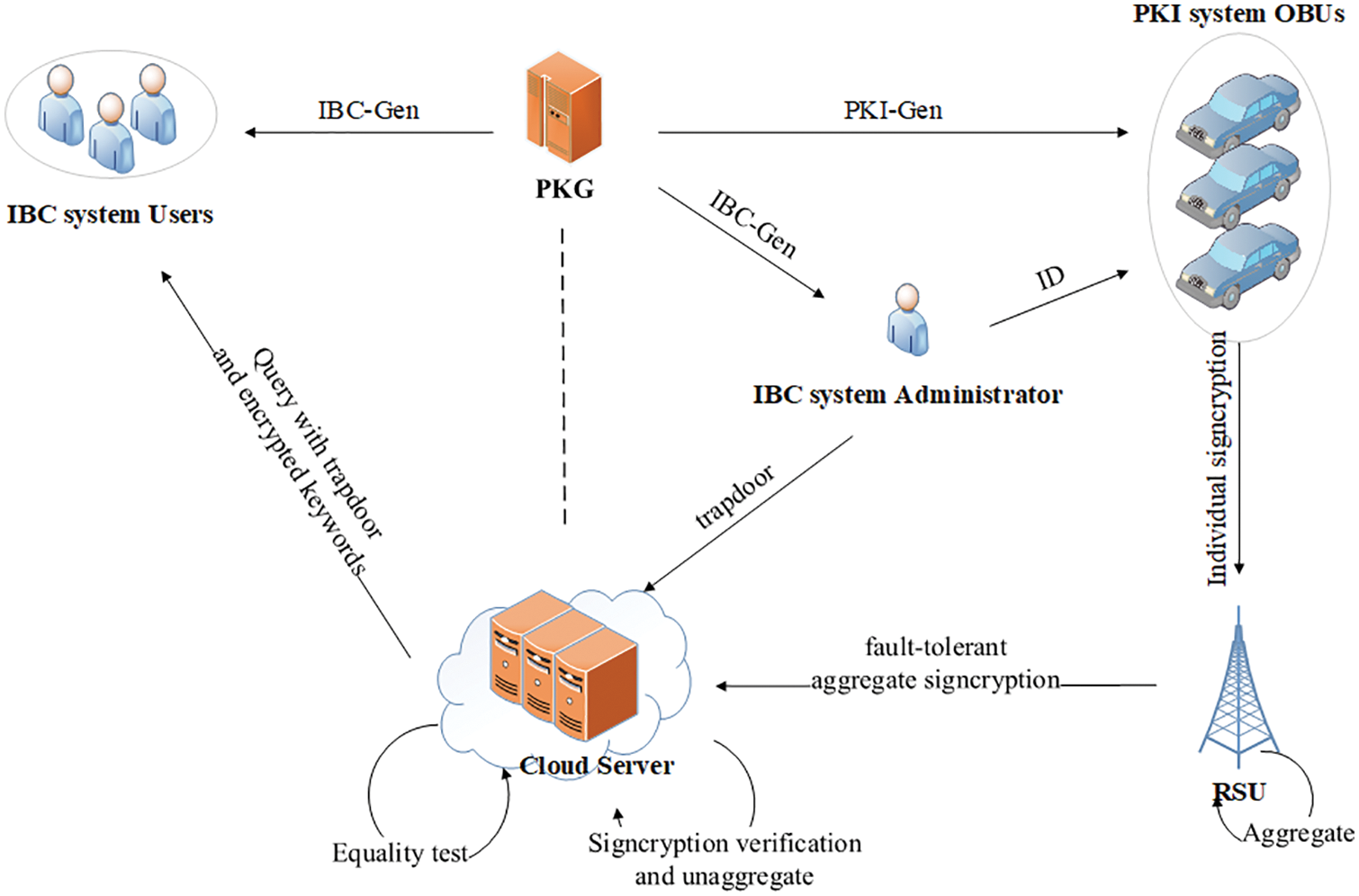
Figure 1: System model
The detailed contributions of our paper are given below:
(1) The paper constructs a heterogeneous fault-tolerant aggregate signcryption scheme with an equality test (HFTAS-ET). Aggregate signcryption function improves communication data confidentiality and reduces communication overhead. Fault-tolerant function not only tolerates invalid signatures and reduces the verification cost, but also realizes one verification pass when all signcryptions are valid. At the same time, it realizes an unbounded scheme when the number of signcryptions increases dynamically. The scheme supports heterogeneous environment to ensure its flexibility of the scheme, and provides the function of an equality test to control access rights of data in a heterogeneous environment ensuring the confidentiality and availability of data.
(2) The security of the scheme is verified by strict theoretical analysis. Through detailed functional and performance comparisons, we have concluded that our scheme has better performance and higher efficiency than existing schemes.
(3) This scheme is applicable to the VSN.
Suppose G and
(1) Bilinearity:
(2) Nondegeneracy:
(3) Computability:
G and
BDHIA holds if there do not exist probabilistic polynomial-time adversary
G is a cyclic group and its prime orders is p. P is a generator of G. For a random number
CDHIP holds if there do not exist probabilistic polynomial-time adversary
In our scheme, d-cover-free families (d-CFFs) is the basis of fault tolerance.
D-cover-Free Family: There exists two sets, one is
If the characteristic vectors of subsets in
Nested Family:
If
Our scheme contains eight algorithms:
(1) Setup: It is executed by the private key generator (PKG) according to a number k called security parameter, which generates a collection of system public parameters and master secret key MSK.
(2) PKI-Gen: It is executed by PKG according to input a randomly number chosen by a sender
(3) IBC-Gen: It is executed by PKG according to input the ID of a receiver in IBC system and further produces the corresponding secret key
(4) Trapdoor: Given secret key
(5) Signcrypt: It is excuted by OBUs. The sender generates a signcryption
(6) Aggregate: After receiving n senders, n corresponding signcryptions
(7) Unaggregate: Given the fault-tolerant aggregate signcryption
(8) Test: After receiving signcryption
In this scheme, the identity of the administrator is exclusively denoted by
Setup: After obtaining a security parameter k, challenger
Phase
(1) Key Generation Queries: After receiving the ID of the required query from
(2) Aggregate Queries: After receiving the
(3) Unaggregate Queries: After receiving the signcryption
Challenge:
Phase II:
Guess:
Definition 1: If all IND-CCA2 adversaries
Setup: After obtaining a security parameter k, challenger
Phase I:
(1) Key Generation Queries: After receiving the ID of the required query from
(2) Trapdoor Queries: After receiving the required query from
(3) Aggregate Queries: After receiving the
(4) Unaggregate Queries: After receiving the signcryption
Challenge:
Phase II:
Guess:
Definition 2: If all OW-CCA2 adversaries
Setup: After obtaining a security parameter k, challenger
Queries:
(1) Key Generation Queries: After receiving the ID of the required query from
(2) Signcryption Queries: After receiving a plaintext M and a receiver’s ID of the required query from
Forgery:
Definition 3: If all EUF-CMA adversaries
(1) Setup: Given a random number k as security parameter, PKG produces cyclic groups G and
(2) PKI-Gen: PKG input a number
(3) IBC-Gen: PKG input ID of a receiver in IBC system and produces the corresponding secret key
(4) Trapdoor: Input the secret key
(5) Signcrypt: Given the
(a) Randomly pick
(b) Set
(c) Calculate
Output the ciphertext
(6) Aggregate: When receiving n signcryptions
(a) The
(b) In the matrix
(c) Create a new position
(d) The core of aggregate signcryption
The fault-tolerant aggregate signcryption:
Unbounded-fault-tolerant aggregate
Let
Let
If one or both of the two sets
Aggregate the corresponding positions of
(i) for
(ii) for
(iii) for
Aggregate with
Output
(7) Unaggregate: After receiving the fault-tolerant aggregate signcryption
for
(a)
(b)
(c)
(i) When
(ii) When
(8) Sign: After receiving a sender’s signcryption
(a)
(b) Randomly pick
(c) Set
(d) Calculate
(e) Generate
(9) Test: After receiving a sender’s ciphertext
(a) Verify if
(b)
(c)
(d) Check
4.2 The Identification of Invalid Signcryptions
Given the fault-tolerant aggregate signcryption
(1) Verify if
(2) Let
(3) Let
(4) For each
(5) If not hold, this signcryption are not valid. Meanwhile, create a new sete called “The Invalid Set” and add the invalid signcryption to it. Then output
Theorem 1: Suppose that BDHIA holds. Our scheme HFTAS-ET is secure against IND-CCA2.
Proof. Suppose there is a challenger
Setup:
Phase I:
(1)
(2)
(3)
(4)
(5) Key Generation Queries: After receiving a query with
(6) Aggregate Queries: After receiving a query with
(7) Unaggregate Queries: When receiving the query with
where
Then,
If it holds, return
And return the valid set to
Challenge: After receiving the receiver’s
(1) If
(2) Otherwise,
Phase II:
Guess:
Theorem 2: Suppose that BDHIA holds. Our scheme HFTAS-ET is secure against OW-CCA2.
Proof. Suppose there is a challenger
Setup:
Phase I:
(1)
Meanwhile,
(2)
-Queries: After receiving a query with
(3)
(4)
(5) Key Generation Queries: After receiving a query with
(6) Trapdoor Queries: After receiving this query, judge whether
(7) Aggregate Queries: After receiving a query with
(8) Unaggregate Queries: When receiving the query with
where
If it holds, return
And return the valid set to
Challenge: After receiving a receiver’s
(1) If
(2) Otherwise,
Phase II:
Guess:
Theorem 3: Suppose that CDHIA holds. Our scheme HFTAS-ET is secure against EUF-CMA.
Proof. Suppose there is a challenger
Setup:
Queries:
(1)
(2)
(3)
(4)
(5) Key Generation Queries: After receiving a query with
(6) Signcryption Queries: After receiving a query with the
(a) Randomly pick
(b) Calculate
(c) Patch the hash value
(d) Calculate
Forgery: According to forking lemma,
In this section, we make a comparison of our scheme and several existing schemes with respect to function comparison, communication and computation overhead.
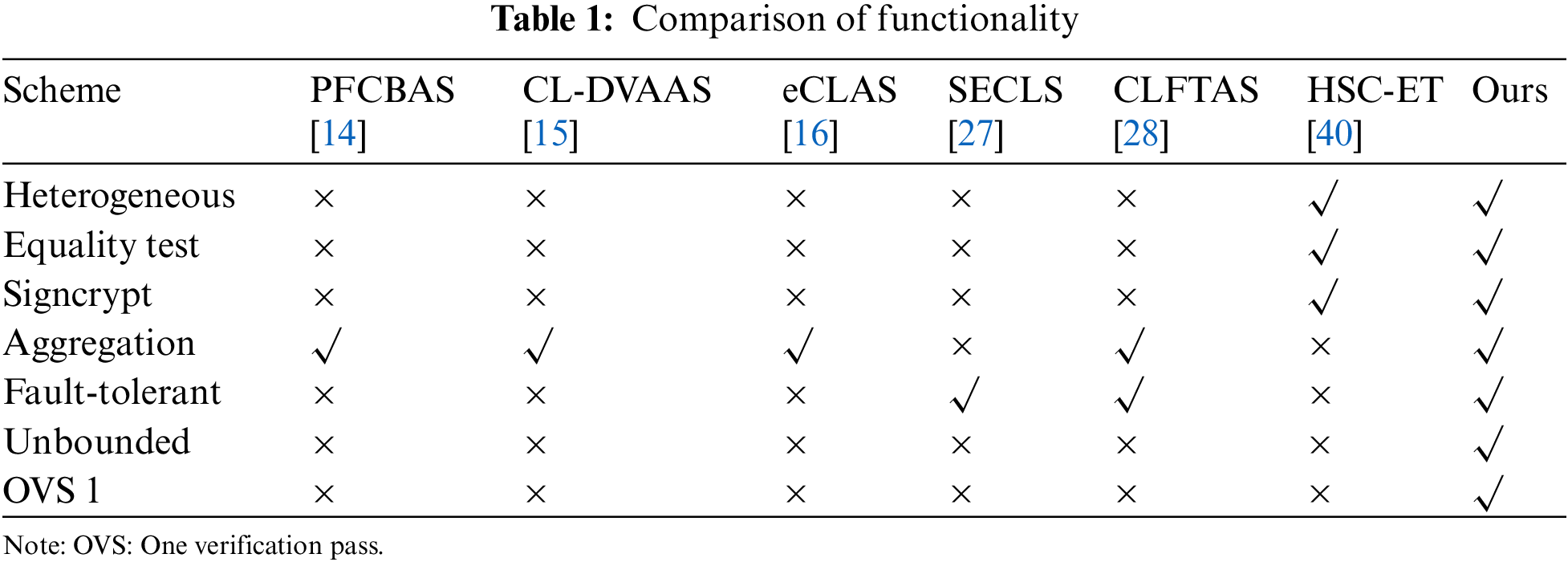
In Table 1, we list the functionalities of our scheme compared with the previous similar schemes. From this table, it illustrates that only scheme [40] and our scheme can support heterogeneous signcryption network and have a function of equality test. Among the schemes [14–16,28] that support aggregate signature, only our scheme can support both fault-tolerant aggregation and aggregate signcryption. Compared with the scheme [28] that supports fault-tolerant aggregate signature, our scheme is an unbounded fault-tolerant aggregate signcryption scheme, which improves efficiency. In addition, our scheme supports one verification pass when all signcryptions are valid, which further improves efficiency.
6.2 Communication Overhead and Computation Cost
To easily evaluate and analyze the efficiency of our scheme and existing schemes, we use JPBC library to run the experiment on a machine with Windows 10 operating system and Intel Core i7-11700 CPU at 2.50 GHz.
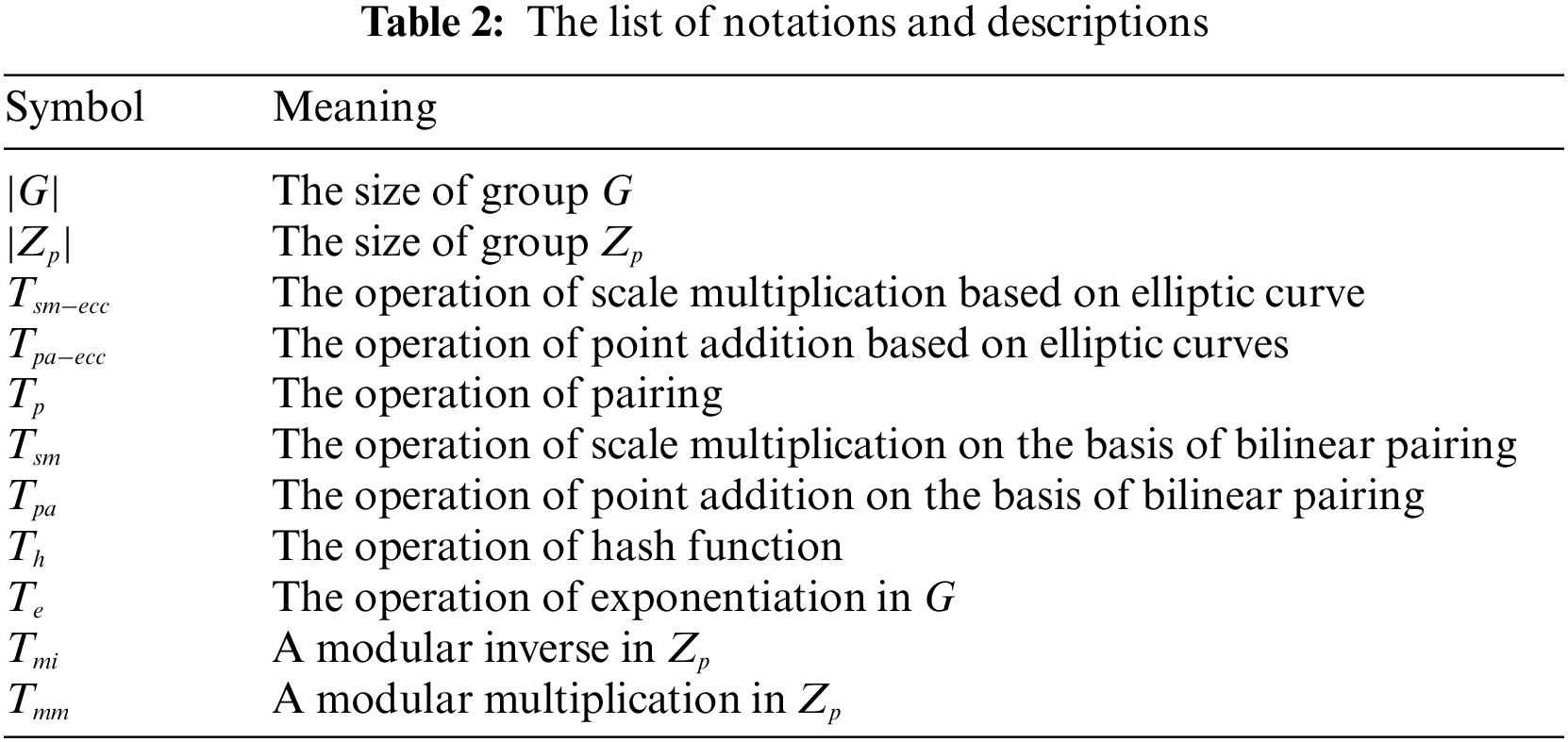
The experimental scheme consists of pairing-based schemes and ECC-based schemes, therefore it is necessary to ensure the same security level. Therefore, two groups are selected, respectively. One is a bilinear pairing
Relevant symbols in this paper are implied in Table 2.
We contrast our scheme and the previous similar schemes in terms of communication overhead. As shown in Table 3, there is not much difference among these schemes. However, the size of aggregate signcryption of our scheme is significantly less than those of schemes [14–16], while almost the same to scheme [28]. And since our scheme is unbounded aggregation of signcryptions, the small gap is tolerable. Overall, our scheme performs better in terms of communication overhead.
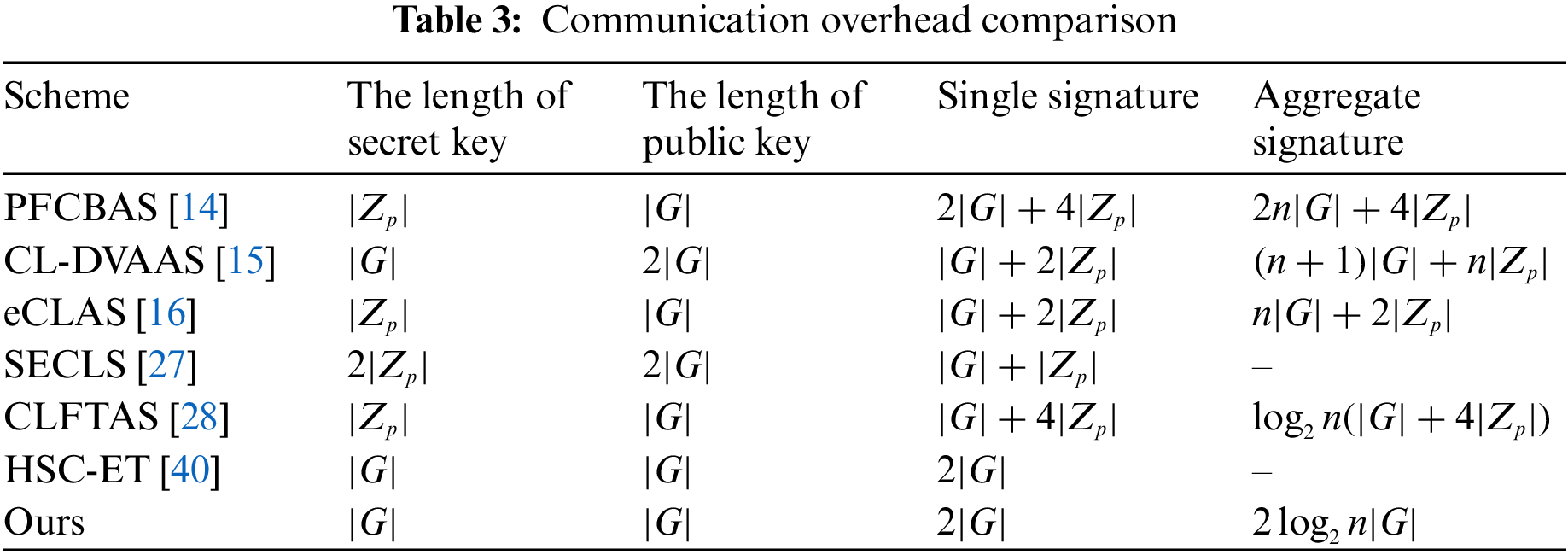
Table 4 displays a detailed comparison of computation overhead for each phase. Moreover, we perform a detailed comparison experiment as detailed below.
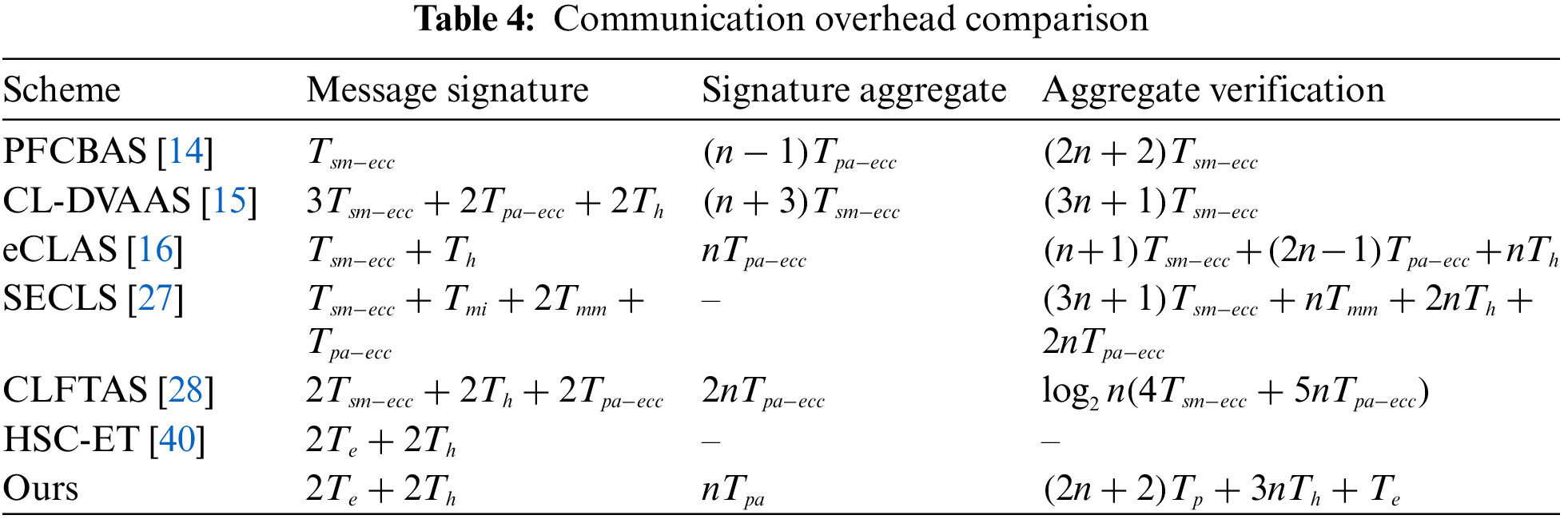
Fig. 2 shows that time consumption of encryption/signcryption of existing schemes [14–16,27,28,40] and our scheme. Our scheme’s signcryption time consumption is slightly higher than that of scheme [14,16], but obviously much lower than that of [15,27,28]. And scheme [14,16] does not need to consider the impact of signcryption stage on fault-tolerant performance in the signature stage, so our scheme has a better signcryption efficiency.
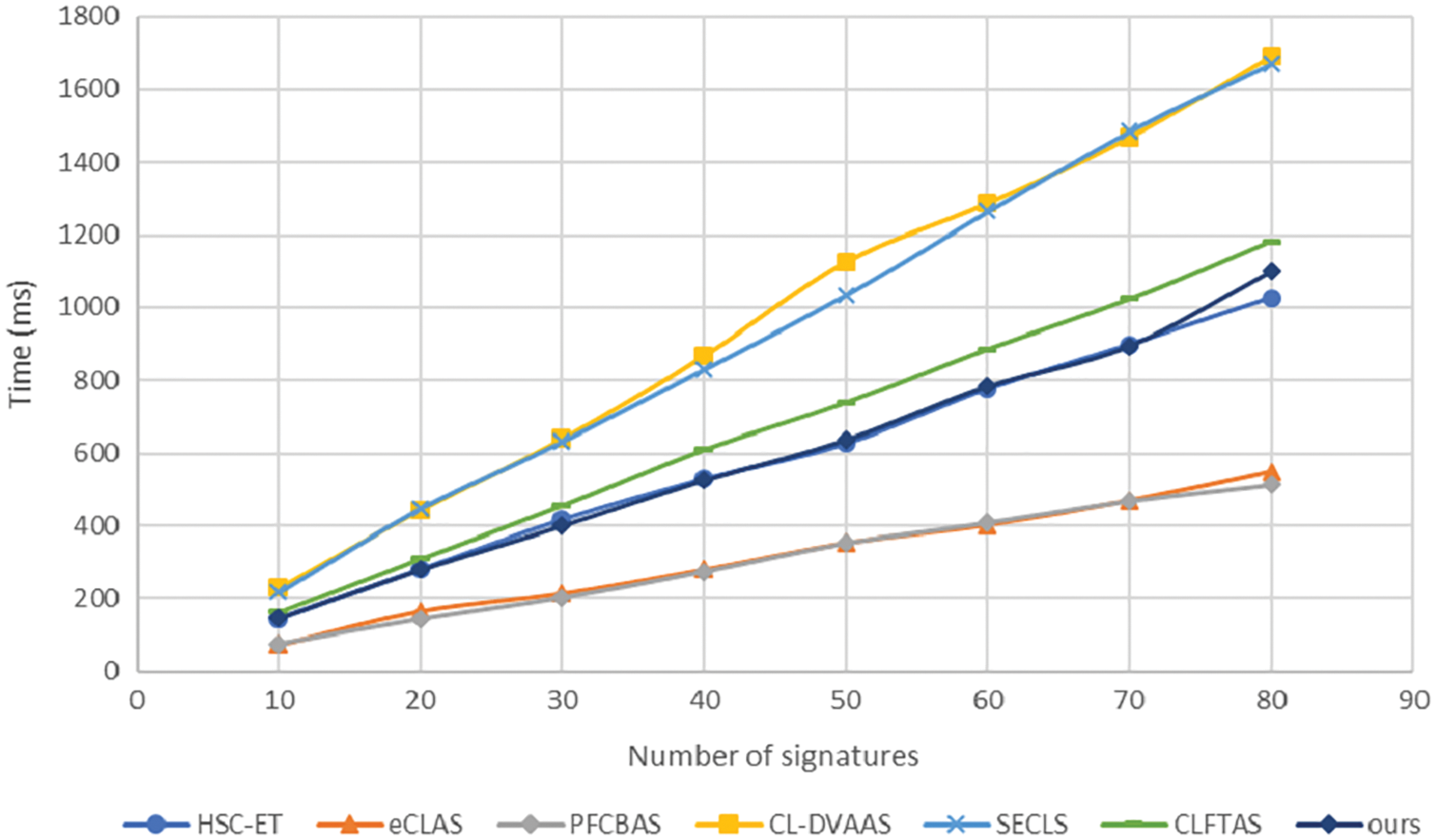
Figure 2: Comparison of encryption (signcryption) cost
Fig. 3 below shows that time consumption of signatures/signcryptions aggregation in existing schemes [14–16,28] and our scheme. At this stage, our scheme’s time consumption is similar to that of [14–16]. In addition, only the scheme [28] and our scheme are fault-tolerant aggregate signature schemes, while the aggregation time of our scheme is far less than the scheme [28].
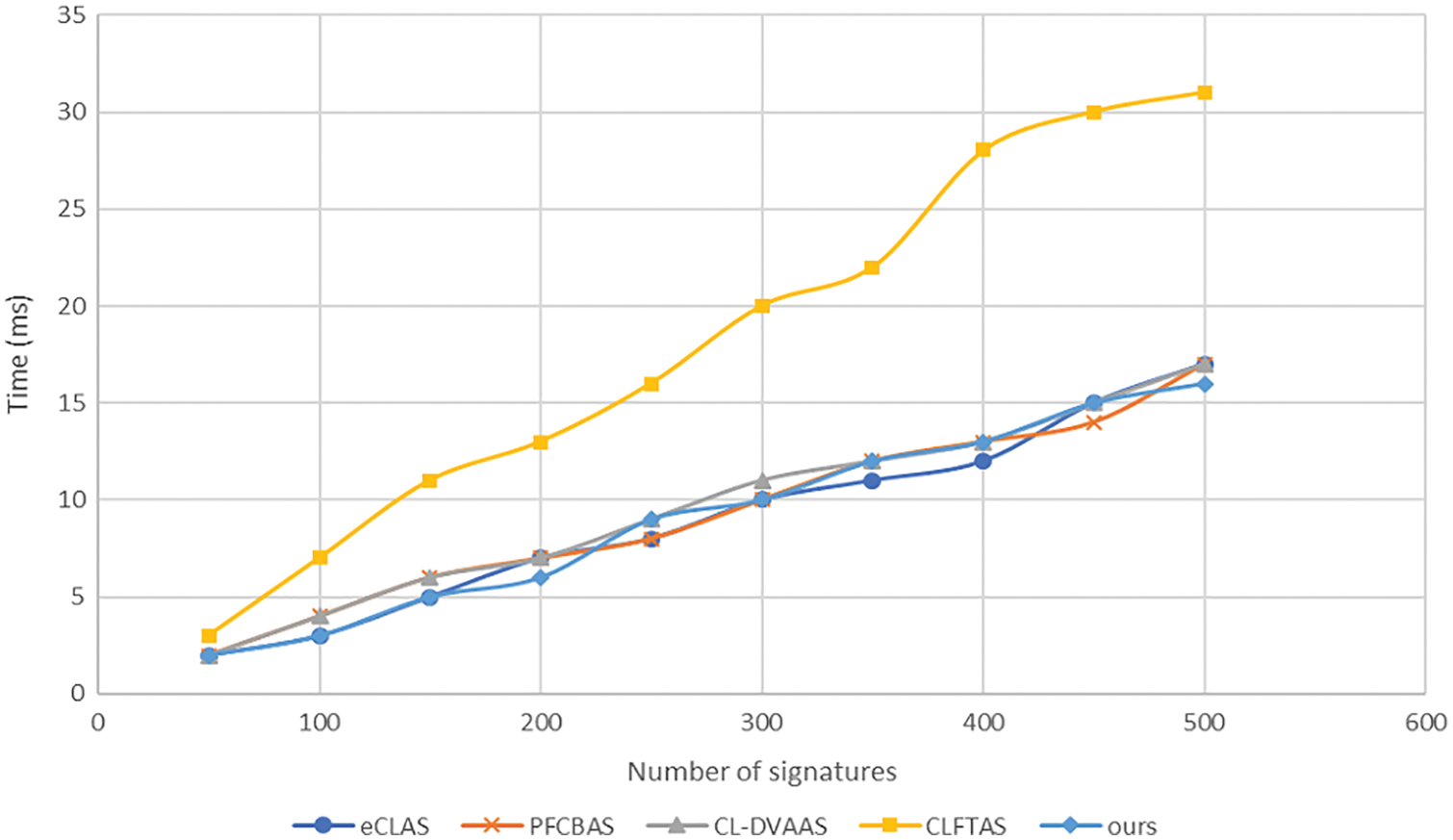
Figure 3: Comparison of signatures (signcryptions) aggregation cost
Fig. 4 below shows that the average time consumption of aggregate signature/signcryption verification in the existing scheme [14–16,28] and our scheme. Our scheme maintains
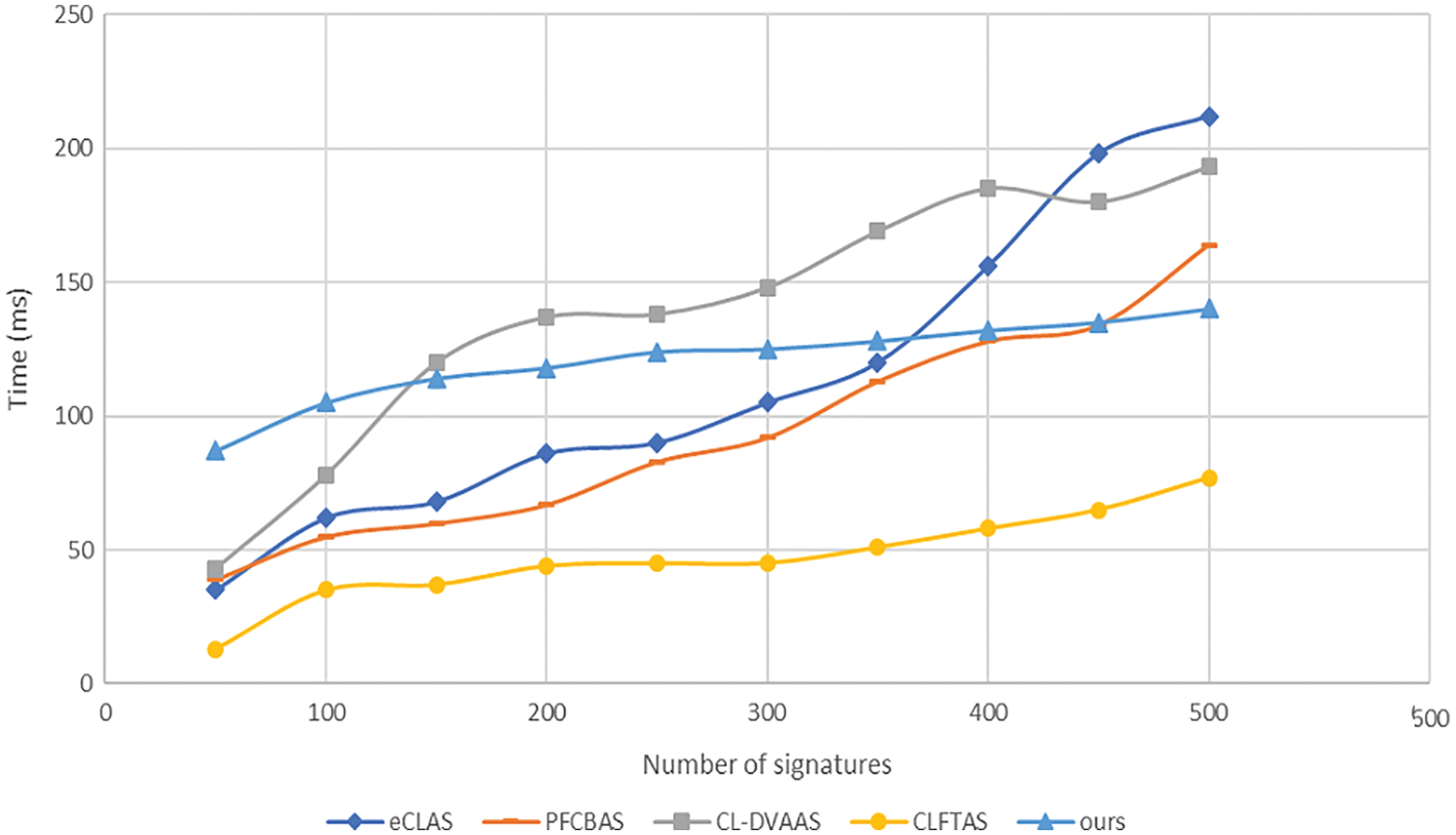
Figure 4: Comparison of aggregate signature (signcryption) verification cost
Finally, we experiment on identifying invalid signatures/signcryptions, as shown in Fig. 5. We assume that signatures/signcryptions n = 100 has an invalid signature/signcryption. In addition, we use binary search method to identify invalid signatures for the scheme [16]. Our scheme supports the identifying of invalid signcryptions information and fault-tolerance, while the scheme [16] only verify the existence of invalid signatures, but cannot tolerate invalid signatures. Therefore, our scheme sacrifices a little verification efficiency, the time consumption of the scheme [16] is less than ours in the best case. But in the worst case, our scheme has less time consumption than the scheme [16].
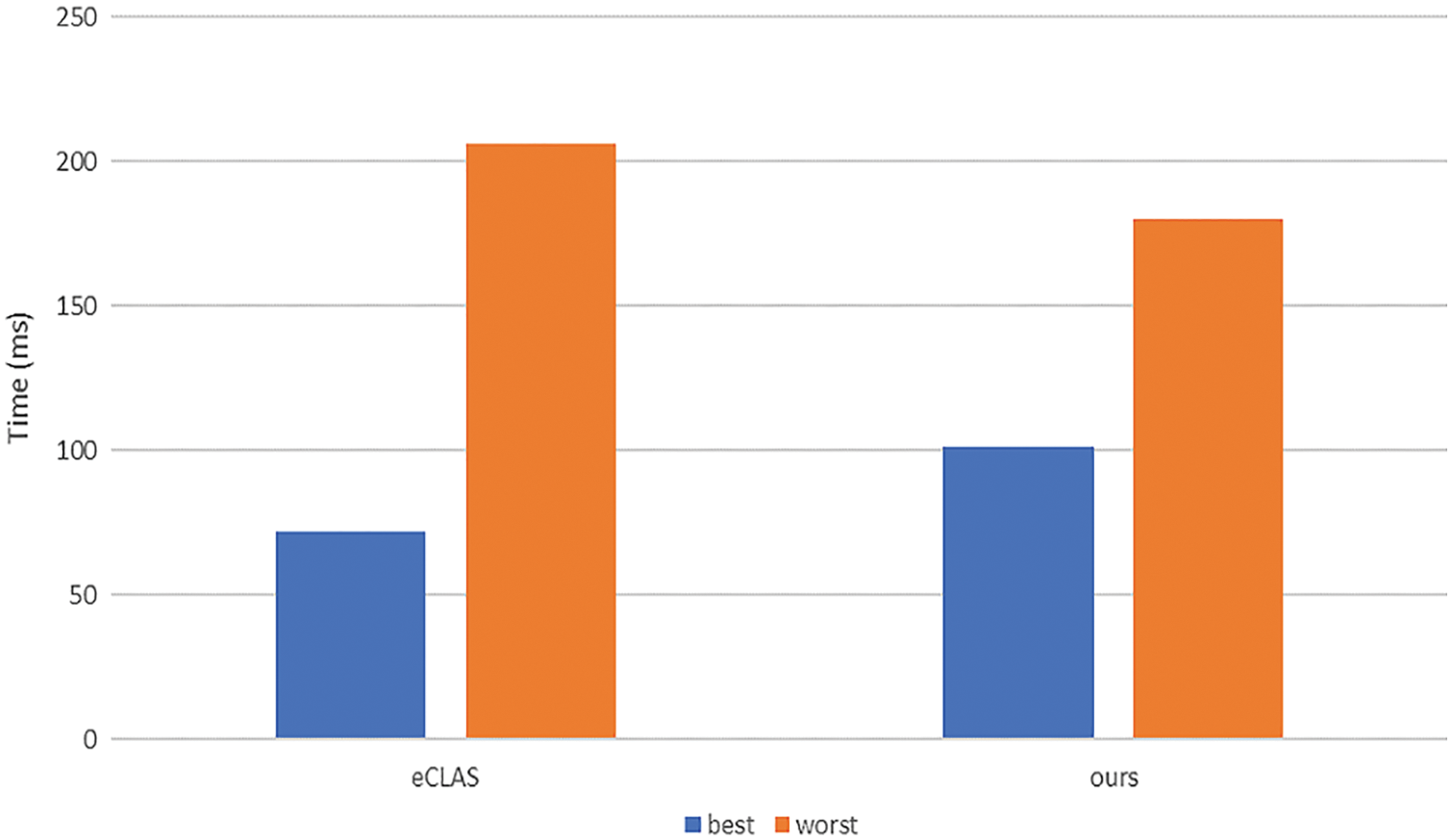
Figure 5: Comparison of identifying invalid signatures (signcryptions)
According to the analysis above, it is clear that our scheme has good performance in message signature/signcryption, aggregate signature/signcryption, aggregate signature/signcryption verification and invalid signature/signcryption identification.
In this paper, we give a heterogeneous fault-tolerant aggregate signcryption scheme with equality test, and apply it to the VSN. The scheme adds an unbounded-fault-tolerant function on the basis of aggregate signcryption, which not only strengthens the data confidentiality, but also improves the signcryption verification efficiency. At the same time, the equality test can control data access and ensure the confidentiality of data. In addition, we give a security model of the scheme and prove its security. Finally, experimental operation and performance evaluation show that the scheme has better performance.
Funding Statement: This work was supported in part by the Open Fund of Advanced Cryptography and System Security Key Laboratory of Sichuan Province under Grant SKLACSS-202102, in part by the Intelligent Terminal Key Laboratory of Sichuan Province under Grant SCITLAB-1019.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. Asghari, P., Rahmani, A. M., Javadi, H. H. S. (2019). Internet of Things applications: A systematic review. Computer Networks, 148, 241–261. https://doi.org/10.1016/j.comnet.2018.12.008 [Google Scholar] [CrossRef]
2. Esposito, C., Castiglione, A., Martini, B., Choo, K. K. R. (2016). Cloud manufacturing: Security, privacy, and forensic concerns. IEEE Cloud Computing, 3(4), 16–22. https://doi.org/10.1109/MCC.2016.79 [Google Scholar] [CrossRef]
3. Diffie, W. (1976). New direction in cryptography. IEEE Transactions on Information Theory, 22, 472–492. [Google Scholar]
4. Thompson, M. R., Essiari, A., Mudumbai, S. (2003). Certificate-based authorization policy in a PKI environment. ACM Transactions on Information and System Security (TISSEC), 6(4), 566–588. https://doi.org/10.1145/950191.950196 [Google Scholar] [CrossRef]
5. Shamir, A. (1984). Identity-based cryptosystems and signature schemes. Workshop on the Theory and Application of Cryptographic Techniques, pp. 47–53. Springer, Berlin, Heidelberg. [Google Scholar]
6. Hess, F. (2002). Efficient identity based signature schemes based on pairings. International Workshop on Selected Areas in Cryptography, pp. 310–324. ST Johns, Canada. [Google Scholar]
7. Paterson, K. G., Schuldt, J. C. N., Paterson, K. G., Schuldt, J. C. N., Batten, L. M. et al. (2006). Efficient identity-based signatures secure in the standard model. 11th Australasian Conference on Information Security and Privacy, vol. 4058, pp. 207–222. Melbourne, Australia. [Google Scholar]
8. Al-Riyami, S. S., Paterson, K. G. (2003). Certificateless public key cryptography. International Conference on the Theory and Application of Cryptology and Information Security, pp. 452–473. Taipei, Taiwan. [Google Scholar]
9. Huang, X., Susilo, W., Mu, Y., Zhang, F. (2005). On the security of certificateless signature schemes from Asiacrypt 2003. International Conference on Cryptology and Network Security, pp. 13–25. Berlin, Germany. [Google Scholar]
10. Harn, L., Ren, J., Lin, C. (2009). Design of DL-based certificateless digital signatures. Journal of Systems and Software, 82(5), 789–793. https://doi.org/10.1016/j.jss.2008.11.844 [Google Scholar] [CrossRef]
11. Boneh, D., Gentry, C., Lynn, B., Shacham, H. (2003). Aggregate and verifiably encrypted signatures from bilinear maps. International Conference on the Theory and Applications of Cryptographic Techniques, pp. 416–432. Warsaw, Poland. [Google Scholar]
12. Cheon, J. H., Kim, Y., Yoon, H. J. (2004). A new ID-based signature with batch verification. Cryptology ePrint Archive. [Google Scholar]
13. Gong, Z., Long, Y., Hong, X., Chen, K. (2007). Two certificateless aggregate signatures from bilinear maps. Eighth ACIS International Conference on Software Engineering, Artificial Intelligence, Networking, and Parallel/Distributed Computing (SNPD 2007), vol. 3, pp. 188–193. Qungdao, China. [Google Scholar]
14. Verma, G. K., Singh, B., Kumar, N., Kaiwartya, O., Obaidat, M. S. (2019). Pfcbas: Pairing free and provable certificate-based aggregate signature scheme for the e-healthcare monitoring system. IEEE Systems Journal, 14(2), 1704–1715. https://doi.org/10.1109/JSYST.4267003 [Google Scholar] [CrossRef]
15. Deng, L., Yang, Y., Gao, R. (2021). Certificateless designated verifier anonymous aggregate signature scheme for healthcare wireless sensor networks. IEEE Internet of Things Journal, 8(11), 8897–8909. https://doi.org/10.1109/JIOT.2021.3056097 [Google Scholar] [CrossRef]
16. Han, Y., Song, W., Zhou, Z., Wang, H., Yuan, B. (2022). eCLAS: An efficient pairing-free certificateless aggregate signature for secure VANET communication. IEEE Systems Journal, 16(1), 1637–1648. https://doi.org/10.1109/JSYST.2021.3116029 [Google Scholar] [CrossRef]
17. Selvi, S., Vivek, S. S., Shriram, J., Kalaivani, S., Rangan, C. P. (2009). Identity based aggregate signcryption schemes. International Conference on Cryptology in India, pp. 378–397. New Delhi, India. [Google Scholar]
18. Wang, H., Liu, Z., Liu, Z., Wong, D. S. (2016). Identity-based aggregate signcryption in the standard model from multilinear maps. Frontiers of Computer Science, 10(4), 741–754. https://doi.org/10.1007/s11704-015-5138-2 [Google Scholar] [CrossRef]
19. Yiliang, H., Fei, C. (2015). The multilinear maps based certificateless aggregate signcryption scheme. 2015 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery, pp. 92–99. Shanghai, China. [Google Scholar]
20. Eslami, Z., Pakniat, N. (2014). Certificateless aggregate signcryption: Security model and a concrete construction secure in the random oracle model. Journal of King Saud University-Computer and Information Sciences, 26(3), 276–286. https://doi.org/10.1016/j.jksuci.2014.03.006 [Google Scholar] [CrossRef]
21. Chen, J., Ren, X. (2016). A privacy protection scheme based on certificateless aggregate signcryption and masking random number in smart grid. International Conference on Mechanical Materials and Manufacturing Engineering, pp. 10–13. Wuhan, China. [Google Scholar]
22. Lu, H., Xie, Q. (2011). An efficient certificateless aggregate signcryption scheme from pairings. 2011 International Conference on Electronics, Communications and Control (ICECC), pp. 132–135. Ningbo, China. [Google Scholar]
23. Ren, X. Y., Qi, Z. H., Geng, Y. (2012). Provably secure aggregate signcryption scheme. ETRI Journal, 34(3), 421–428. https://doi.org/10.4218/etrij.12.0111.0215 [Google Scholar] [CrossRef]
24. Kim, T. H., Kumar, G., Saha, R., Alazab, M., Buchanan, W. J. et al. (2020). CASCF: Certificateless aggregated signcryption framework for internet-of-things infrastructure. IEEE Access, 8, 94748–94756. https://doi.org/10.1109/Access.6287639 [Google Scholar] [CrossRef]
25. Hartung, G., Kaidel, B., Koch, A., Koch, J., Rupp, A. et al. (2016). Fault-tolerant aggregate signatures. 19th IACR International Conference on the Theory and Practice of Public-Key Cryptography (PKC), vol. 9614, pp. 331–356. Taipei, Taiwan. https://doi.org/10.1007/978-3-662-49384-7_13 [Google Scholar] [CrossRef]
26. Wang, G., Cao, Z., Dong, X., Liu, J. (2019). Improved fault-tolerant aggregate signatures. The Computer Journal, 62(4), 481–489. https://doi.org/10.1093/comjnl/bxy108 [Google Scholar] [CrossRef]
27. Xiong, H., Wu, Y., Su, C., Yeh, K. -H. (2020). A secure and efficient certificateless batch verification scheme with invalid signature identification for the internet of things. Journal of Information Security and Applications, 53, 102507. https://doi.org/10.1016/j.jisa.2020.102507 [Google Scholar] [CrossRef]
28. Zhao, Y., Dan, G., Ruan, A., Huang, J., Xiong, H. (2021). A certificateless and privacy-preserving authentication with fault-tolerance for vehicular sensor networks. 2021 IEEE Conference on Dependable and Secure Computing (DSC), pp. 1–7. Aizuwakamatsu, Japan. [Google Scholar]
29. Xiong, H., Jin, C., Alazab, M., Yeh, K. H., Wang, H. et al. (2022). On the design of blockchain-based ecdsa with fault-tolerant batch verification protocol for blockchain-enabled iomt. IEEE Journal of Biomedical and Health Informatics, 26(5), 1977–1986. https://doi.org/10.1109/JBHI.2021.3112693 [Google Scholar] [PubMed] [CrossRef]
30. Boneh, D., Crescenzo, G. D., Ostrovsky, R., Persiano, G. (2004). Public key encryption with keyword search. International Conference on the Theory and Applications of Cryptographic Techniques, pp. 506–522. Interlaken, Switzerland. [Google Scholar]
31. Xiong, H., Yang, M., Yao, T., Chen, J., Kumari, S. (2021). Efficient unbounded fully attribute hiding inner product encryption in cloud-aided wbans. IEEE Systems Journal, 16(4), 5424–5432. https://doi.org/10.1109/JSYST.2021.3125455 [Google Scholar] [CrossRef]
32. Huang, X., Xiong, H., Chen, J., Yang, M. (2021). Efficient revocable storage attribute-based encryption with arithmetic span programs in cloud-assisted Internet of Things. IEEE Transactions on Cloud Computing, 1. https://doi.org/10.1109/TCC.2021.3131686 [Google Scholar] [CrossRef]
33. Chen, C. M., Tie, Z., Wang, E. K., Khan, M. K., Kumar, S. et al. (2021). Verifiable dynamic ranked search with forward privacy over encrypted cloud data. Peer-to-Peer Networking and Applications, 14(5), 2977–2991. https://doi.org/10.1007/s12083-021-01132-3 [Google Scholar] [CrossRef]
34. Xiong, H., Chen, J., Mei, Q., Zhao, Y. (2022). Conditional privacy-preserving authentication protocol with dynamic membership updating for vanets. IEEE Transactions on Dependable and Secure Computing, 19(3), 2089–2104. https://doi.org/10.1109/TDSC.2020.3047872 [Google Scholar] [CrossRef]
35. Mei, Q., Xiong, H., Chen, Y. C., Chen, C. M. (2022). Blockchain-enabled privacy-preserving authentication mechanism for transportation cps with cloud-edge computing. IEEE Transactions on Engineering Management, 1–12. https://doi.org/10.1109/TEM.2022.3159311 [Google Scholar] [CrossRef]
36. Yang, G., Tan, C. H., Huang, Q., Wong, D. S. (2010). Probabilistic public key encryption with equality test. Cryptographers’ Track at the RSA Conference, pp. 119–131. San Francisco, CA. [Google Scholar]
37. Lee, H. T., Ling, S., Seo, J. H., Wang, H. (2016). Semi-generic construction of public key encryption and identity-based encryption with equality test. Information Sciences, 373, 419–440. https://doi.org/10.1016/j.ins.2016.09.013 [Google Scholar] [CrossRef]
38. Wu, T., Ma, S., Mu, Y., Zeng, S. (2017). Id-based encryption with equality test against insider attack. Australasian Conference on Information Security and Privacy, pp. 168–183. Auckland, New zealand. [Google Scholar]
39. Qu, H., Yan, Z., Lin, X. J., Zhang, Q., Sun, L. (2018). Certificateless public key encryption with equality test. Information Sciences, 462, 76–92. https://doi.org/10.1016/j.ins.2018.06.025 [Google Scholar] [CrossRef]
40. Xiong, H., Zhao, Y., Hou, Y., Huang, X., Jin, C. et al. (2020). Heterogeneous signcryption with equality test for IIoT environment. IEEE Internet of Things Journal, 8(21), 16142–16152. https://doi.org/10.1109/JIOT.2020.3008955 [Google Scholar] [CrossRef]
41. Xiong, H., Hou, Y., Huang, X., Zhao, Y., Chen, C. M. (2022). Heterogeneous signcryption scheme from IBC to PKI with equality test for wbans. IEEE Systems Journal, 16(2), 2391–2400. https://doi.org/10.1109/JSYST.2020.3048972 [Google Scholar] [CrossRef]
42. Xiong, H., Zhou, Z. D., Wang, L. L., Zhao, Z. T., Huang, X. et al. (2022). An anonymous authentication protocol with delegation and revocation for content delivery networks. IEEE Systems Journal, 16(3), 4118–4129. https://doi.org/10.1109/JSYST.2021.3113728 [Google Scholar] [CrossRef]
43. Wu, T. Y., Wang, T., Lee, Y. Q., Zheng, W., Kumari, S. et al. (2021). Improved authenticated key agreement scheme for fog-driven iot healthcare system. Security and Communication Networks, 2021. https://doi.org/10.1155/2021/6658041 [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools