 Open Access
Open Access
ARTICLE
Secure Downlink Transmission Strategies against Active Eavesdropping in NOMA Systems: A Zero-Sum Game Approach
School of Electronics and Information Engineering, Nanjing University of Information Science and Technology, Nanjing, 210044, China
* Corresponding Author: Xiaopeng Ji. Email:
(This article belongs to the Special Issue: Cyberspace Intelligent Mapping and Situational Awareness)
Computer Modeling in Engineering & Sciences 2023, 136(1), 531-553. https://doi.org/10.32604/cmes.2023.024531
Received 01 June 2022; Accepted 15 September 2022; Issue published 05 January 2023
Abstract
Non-orthogonal multiple access technology (NOMA), as a potentially promising technology in the 5G/B5G era, suffers from ubiquitous security threats due to the broadcast nature of the wireless medium. In this paper, we focus on artificial-signal-assisted and relay-assisted secure downlink transmission schemes against external eavesdropping in the context of physical layer security, respectively. To characterize the non-cooperative confrontation around the secrecy rate between the legitimate communication party and the eavesdropper, their interactions are modeled as a two-person zero-sum game. The existence of the Nash equilibrium of the proposed game models is proved, and the pure strategy Nash equilibrium and mixed-strategy Nash equilibrium profiles in the two schemes are solved and analyzed, respectively. The numerical simulations are conducted to validate the analytical results, and show that the two schemes improve the secrecy rate and further enhance the physical layer security performance of NOMA systems.Keywords
Non-orthogonal multiple access (NOMA) has been envisioned as a potentially promising technology for fifth generation (5G) and beyond 5G (B5G) wireless communication networks for its superior performance over the conventional orthogonal multiple access (OMA) in terms of spectral efficiency, connection density, as well as user fairness [1–4]. However, due to the broadcast nature of wireless communication, the NOMA system is vulnerable to eavesdropping. To secure information transmission against malicious eavesdropping, many countermeasures, such as encryption-based approaches implemented at the higher layers [5] and physical layer security (PLS) [6,7], have been put forward in recent years. PLS, as a promising solution to safeguard confidential transmission from the wireless information-theoretic perspective, exploits the intrinsic randomness of the wireless medium to enhance security, and can provide a secure transmission without keys or sophisticated encryption/decryption algorithms. In addition, the physical layer security techniques can be easily implemented and have the capability to quickly adapt to different wireless scenarios [8].
Recently, the concept of PLS has been applied to NOMA systems for secure transmission, and has attracted significant attention and increasing interest in both academia and industry [9,10]. The existing work generally falls into two categories: the security-oriented system design, and X-assisted security scheme. Specifically, the security-oriented system design approaches enhance security by optimizing the parameters of the NOMA system, such as beamforming matrix and power allocation coefficients. Whilst, in X-assisted security schemes, X denotes artificial signal, relay, cooperative jamming or something additional. The key idea behind the approaches is to deliberately improve the legitimated communication channel and/or degrade the eavesdropping channel.
Nevertheless, most of the existing studies on secure transmission in NOMA are conducted from the perspective of legitimate communicators, and fail to reflect the confrontation relationship between eavesdroppers and legitimate communicators. In other words, they assume the precondition that the eavesdropper keeps wiretapping regardless of the radio environment. As a matter of fact, eavesdroppers may incur more costs than benefits when faced with harsh eavesdropping channel conditions, and have no intent to eavesdrop in this situation, which makes the precondition more conservative. Therefore, it is of great significance to comprehensively study the interaction strategies between the two sides considering the channel conditions. However, the various and variable channel state information in radio environment complicates the dynamic secure transmission and eavesdropping process, and further affects their optimal strategy selection for both sides, which poses a huge challenge to studying the secure transmission in NOMA system from the interaction perspective.
Fortunately, game theory, as a mathematical theory and tool to study competitive or cooperative behaviors, provides a powerful framework with which the optimal strategies for both/all sides under various solution concepts of equilibrium can be found. In the secure transmission strategy selections of NOMA systems, we study the interaction between the legitimate communicators and the eavesdropper based on game theory. Specifically, both sides will pay the cost and receive the corresponding benefits in the light of the strategy profile comprised of strategies they select, respectively. That is to say, one’s gain is influenced not only by his/her strategy, but also by the other’s. The advantage of doing so is that the optimal secure transmission strategy can be selected by analyzing the opponent’s strategy, and its conservativeness can be reduced to some extent.
Motivated by this, for a NOMA system with external eavesdroppers, we focus on two typical security schemes, artificial-signal-assisted scheme (AS scheme) and relay-station-assisted scheme (RS scheme). Specifically, artificial signals are superimposed in the orthogonal subspace of weak users’ transmission directions in AS scheme and relays are employed in weak users’ transmission links in RS scheme, to impair the eavesdropping capability. In both schemes, the external active eavesdropper can impose interference signals while eavesdropping to reduce the quality of legitimate communication. In this paper, we first establish the system models, including channel models and signal models, and formulate the information transmission rate for each legitimate communicator and eavesdropper in AS and RS schemes, respectively. Then, the interactions around secure transmission rate, i.e., secrecy rate, are modeled as two-person zero-sum security games. For each security game model, the existence of Nash equilibrium is proved, and the pure strategy Nash equilibrium and mixed-strategy the Nash equilibrium profile are solved and analyzed. Finally, numerical simulations are conducted to validate the theoretical results, and show that AS and RS schemes can improve the secrecy rate and further enhance the physical layer security performance of NOMA systems. By analyzing the Nash equilibrium of the proposed game model, we can shed some light on the decision-making motives, which is of great significance in the design of security schemes.
The main contributions of this paper can be summarized as follows:
• We are the first to investigate artificial-signal-assisted and relay-station-assisted secure downlink transmission schemes for NOMA systems against external active eavesdropping within the framework of game theory, which integrates eavesdropper’s strategy in the design of secure transmission scheme, improves secrecy rate and further enhances physical layer security performance accordingly.
• We model the confrontational interaction between them as a two-person zero-sum game with secrecy rate as utilities to characterize the impact mechanism of legitimate communicators and active eavesdropper’s strategies on the security performance of the Nash system, prove the existence of the Nash equilibrium, and give the optimal (equilibrium) strategy profile which sheds some light on the design of secure NOMA downlink transmission.
• Through numerical simulations, we demonstrate that legitimate communicators can improve the security performance in terms of secrecy rate by with the help of artificial signals or relay stations, while the active eavesdropper choose to eavesdrop and impose interference signal simultaneously in AS scheme and only eavesdrop in RS scheme.
The rest of the paper is organized as follows. In Section 2, a detailed literature survey of physical layer security issues in NOMA system are discussed. Section 3 describes the system model, including channel model and signal model, in artificial-signal-assisted scheme and relay-assisted scheme, respectively. In Section 4, the interactions between the utility of the legitimate communication party and eavesdropper are modeled as two-person zero-sum game, the utilities are expressed in terms of secrecy rate, the existence of the Nash equilibrium of the proposed game models is proved, and the pure strategy the Nash equilibrium and the mixed-strategy Nash equilibrium profiles are solved and analyzed respectively. In Section 5, the proposed game models are evaluated and verified through numerical simulations. Finally, a conclusion is given in Section 6.
In the pioneering works on secure communication in NOMA system from the perspective of physical layer security, existing studies in this field can be classified into two categories: the security-oriented system optimization and X-assisted security scheme. In this section, we introduce the security solutions for NOMA communication systems according to the above taxonomy.
2.1 Security-Oriented NOMA System Design
Security-oriented NOMA system design aims to achieve better security performance by optimizing the NOMA communication system in normal operation mode, such as beamforming, power allocation, user pairing, etc. In [11], the authors investigated the physical layer security problem of mm-Wave NOMA network, proposed an analysis framework of security outage probability, develop a minimal angle-difference user pairing scheme and two maximum ratio transmission beamforming schemes to further enhance the secrecy performance. The authors of [12] considered the application of NOMA to a multi-user network with mixed multicasting and unicasting traffic and proposed a design of beamforming and power allocation ensures that the unicasting performance is improved and maintaining the reception reliability of multicasting. In [13], a low-complexity subcarrier assignment scheme was proposed to maximize the achievable secrecy energy efficiency. In [14], the authors investigated the reliable and secure transmission problem of NOMA systems with untrusted near users, and proposed a joint beamforming and power allocation scheme to achieve reliable and secure transmission. The authors of [15] designed a secure transmission scheme based on beamforming optimization to guard against both internal and external eavesdropping of downlink MISO NOMA networks. In [16], the authors considered the PLS against internal eavesdropping and gave the beamforming design and optimal power allocation problems to guarantee the positive secrecy rate of the system.
2.2 X-Assisted Security Solution
Different from security-oriented NOMA system design, X-assisted security solution enhance security by utilizing external “X”, such as artificial signals, relays, etc. We mainly introduce the two mainstream techniques, artificial-signal (AS) and relay-station (RS)-assisted security solutions, respectively.
2.2.1 AS-Assisted Security Solution
The authors of [17] proposed the method of combining weak user information bearing signal and artificial signal in NOMA system to improve the security performance of the system. The security outage performance of artificial noise assisted full duplex downlink NOMA transmission in large-scale networks was investigated in [18]. In [19], the authors proposed a new hierarchical PLS model to ensure the security of the transmitted information. And an auxiliary optimal beamforming scheme was proposed to ensure the layered information security. In [20], a new frequency domain artificial noise assisted transmission strategy was proposed to improve the physical layer security of the information receiver and satisfied the energy acquisition requirements of the energy receiver. The authors investigated the problem for the design of artificial noise assisted beamforming in MISO channels from the perspective of security outage. The optimal structure was found by solving the security rate maximization problem constrained by the security outage in [21].
2.2.2 RS-Assisted Security Solution
In [22], the security communication problem in multi hop relay systems was considered, the authors proposed to use full duplex relay to enhance the security of the wireless physical layer. The authors of [23] proposed a new two-level secure relay selection scheme in order to protect legitimate communication from eavesdropping. In [24], the authors considered a NOMA network with a half-duplex decode-and-forward relay to improve the physical layer security of two users. Two relay selection schemes termed decode-and-forward and amplify-and-forward protocols based optimal relay selection was proposed in [25]. In [26], the authors proposed a novel cooperative NOMA scheme to guarantee the secure transmission of a specific user via two time slots.
Although scholars have provided many security schemes in the research of NOMA physical layer security, they rarely consider the dynamic confrontational interaction between the two parties. Using the method of game theory, this paper comprehensively considers the confrontation game relationship between the eavesdropper and the legitimate communicator, establishes the interaction behavior of the two sides as a zero-sum game model, and finally realizes the secure transmission of the legitimate communicator.
Consider the standard downlink transmission of a typical NOMA system, consisting of a base station (BS) equipped with N antennas, an external active eavesdropper (E), and two paired legitimate users (
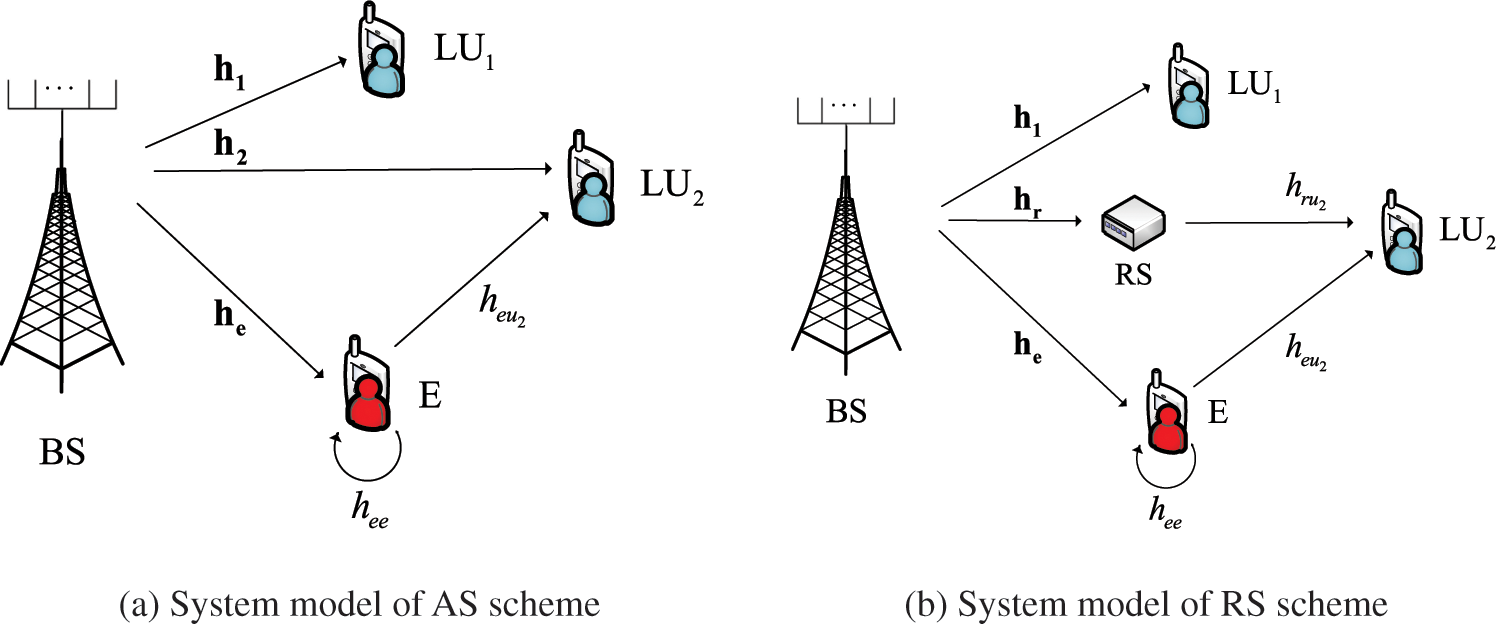
Figure 1: System model in AS and RS schemes
Assume that all channels experience independent quasi-static flat Rayleigh fading, where the channel coefficients remain unchanged within one time-frequency block but change independently between different time-frequency blocks, and suffer from additive white Gaussian noise (AWGN) [27,28]. The
3.2.1 Signal Model of AS Scheme
In the system model of the AS scheme, the base station transmits superimposed signal to users. To protect the weak user from eavesdropping, the artificial signal is superimposed in the orthogonal null space of the transmission direction. The superimposed signal transmitted from BS to
where
Then, the signals received at
and
where
Since the artificial signal is allocated into the orthogonal null space of the channel for NOMA users, we have
and
According to the power-domain NOMA principle, the strong user decodes his message by employing SIC after decoding the message of the weak user, and the weak user directly decodes his message by treating the signal of the strong user as noise. As a result, the signal-to-interference-to-noise ratio (SINR) at
and
where
Similarly,
where
For the eavesdropper E, the received signal can be expressed as
where
The SINR at the eavesdropper E to decode the message for
where
Similarly, when the eavesdropper E does not emit interference signals, i.e.,
3.2.2 Signal Model of RS Scheme
In this scheme, the relay RS works in full duplex mode, and can decode and forward at the same time. In the transmission process, the base station BS first transmits a superimposed signal to the legitimate user
In the system model of the RS scheme, the superimposed signal transmitted to
The signals received at
and
where
The SINR at RS to decode the message for
where
The legitimate user
where
The SINR at
For such a link from the BS to
then the data rate for
For the eavesdropper E, the received signal can be given as
and the SINR at the eavesdropper E to decode the message for
where
Similarly, when the eavesdropper E does not emit interference signals, i.e.,
In this article, we assume that the eavesdropper E only eavesdrops on
where
In the downlink NOMA transmission system with external eavesdropper E, the legitimate user
4.1.1 Game Modeling for the AS Scheme
In the AS scheme, we regard the base station BS and users
Definition 4.1. In the AS scheme, the zero-sum game
•
•
•
According to Definition 4.1, we can further formulate the utility matrix for the zero-sum game, as shown in Table 1. In the utility matrix, there are four strategy profiles in all, and they are
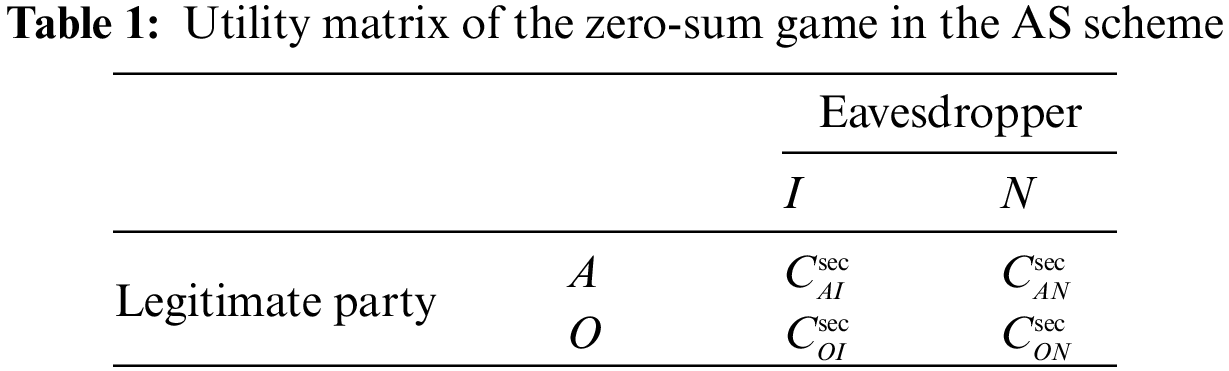
For the profile
For the profile
For the profile
For the profile
4.1.2 Game Modeling for the RS Scheme
In the system model of the RS scheme, the legitimate party L can choose to use the relay transmission strategy or the direct link transmission strategy. The eavesdropper E can choose from the strategies of eavesdropping strategy with or without emitting interference signal. We can establish the game model for the RS scheme as follows.
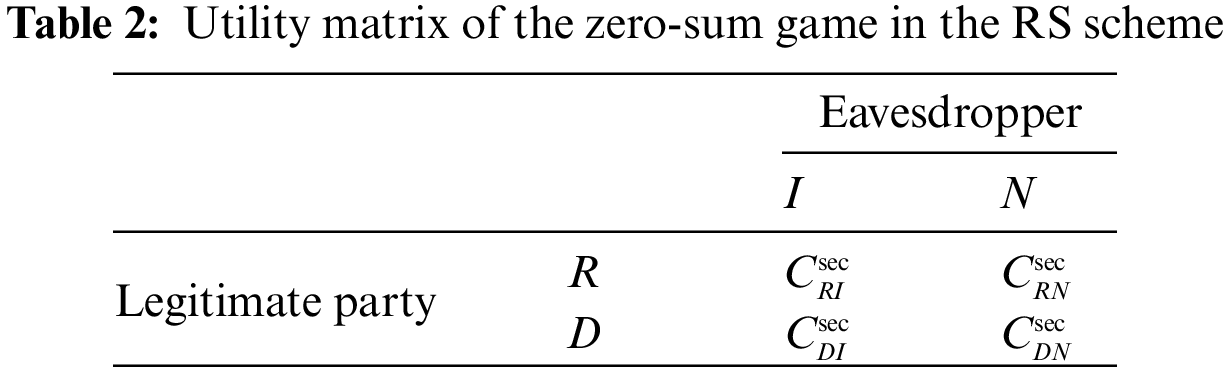
Definition 4.2. In the RS scheme, the zero-sum game
•
•
•
Similarly, we can formulate the utility matrix as shown in Table 2, and the utility functions can be expressed as follows:
where
4.2 Analysis of Game Equilibrium
In this subsection, we will first prove the existence of the Nash equilibrium for the zero-sum game in both AS and RS schemes, and then solve and analyze the pure strategy Nash equilibrium and the mixed strategy Nash equilibrium, respectively.
We give the results of Nash Equilibrium of the games
Theorem 4.1. There is at least one Nash equilibrium in the zero-sum game
Proof. In the zero-sum game
Theorem 4.2. There is at least one Nash equilibrium in the zero-sum game
The proof is similar to that of Theorem 4.1 and thus omitted for simplicity.
4.2.2 Pure-strategy Nash Equilibrium
In this subsection, we solve the pure-strategy Nash equilibrium of the game
Theorem 4.3. The pure-strategy Nash equilibrium (A,I) exists in the game
Proof. According to the analysis aforementioned and Eqs. (28), (30), (32) and (34), it is easy to find that the utility functions in Table 1 satisfy the following conditions:
Thus, the strategy A is the dominating strategy for the legitimate party in the game
First, if
Second, if
This completes the proof.
Theorem 4.4. The pure-strategy Nash equilibrium (R,N) exists in the game
Proof. Since we have assumed
Thus, the strategy R is the dominating strategy for the legitimate party in the game
First, if
Second, if
This completes the proof.
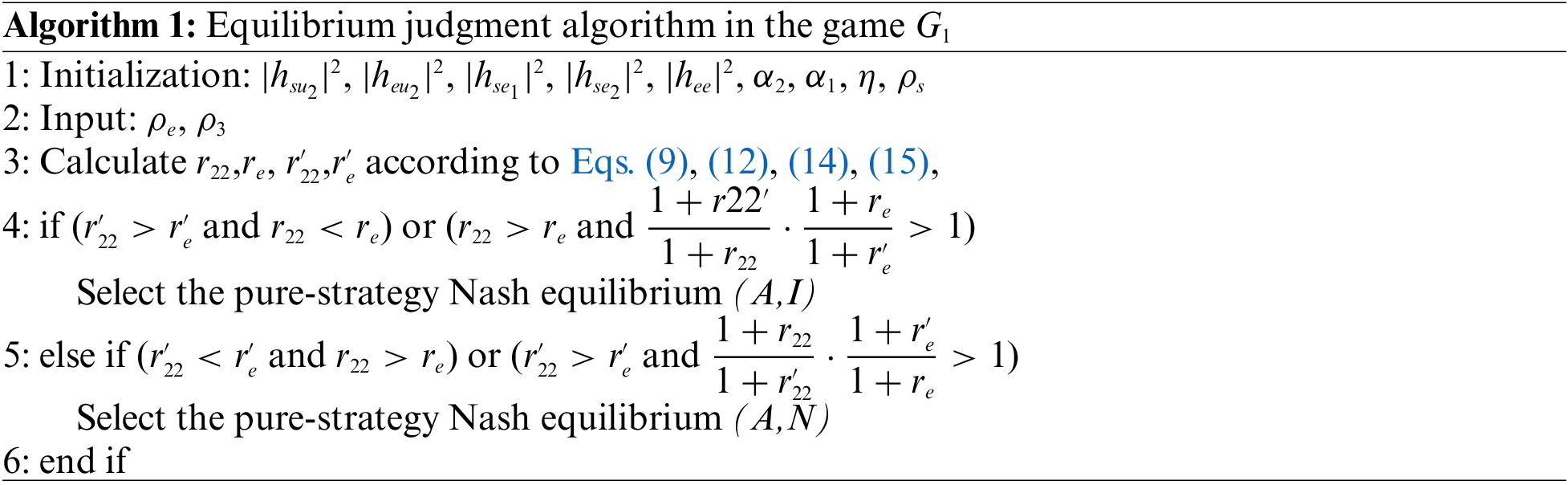
4.2.3 Algorithms for Pure Strategy Nash Equilibrium Strategy
According to the analysis in the previous section, there are two situations in the pure strategy Nash equilibrium of the game
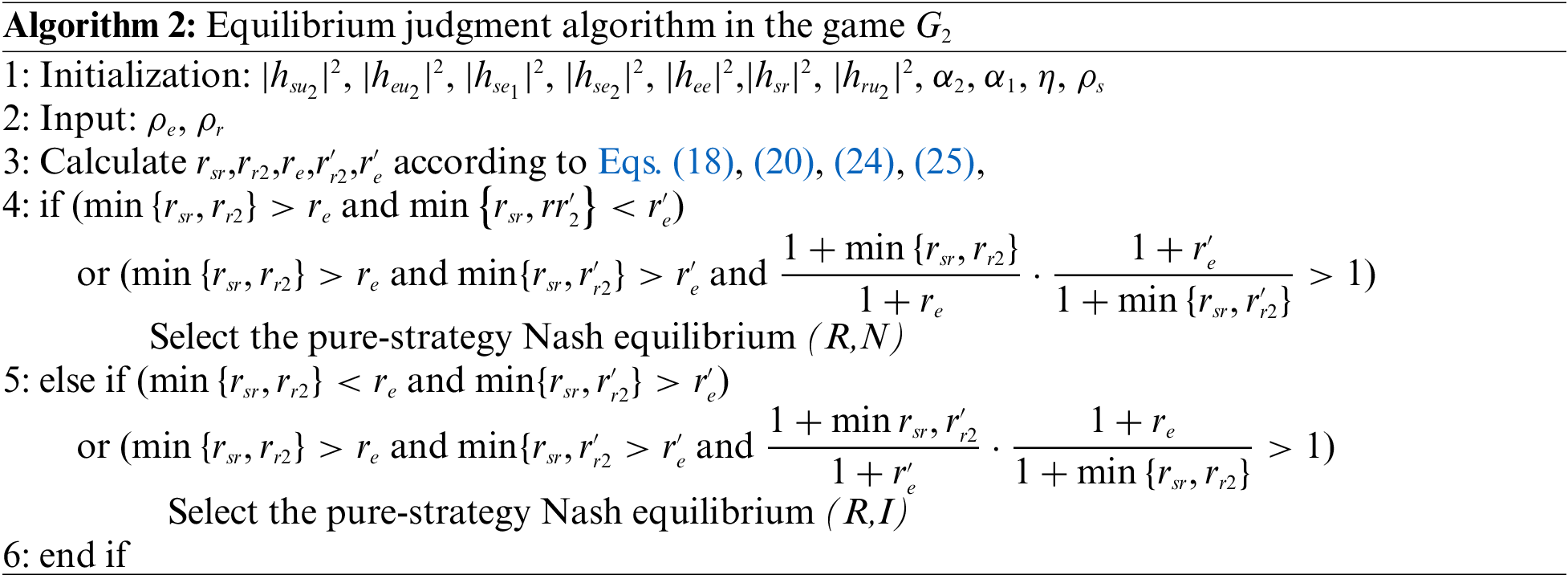
4.2.4 Mixed-Strategy Nash Equilibrium
Different from the deterministic selection of a strategy in pure-strategy Nash equilibrium, a player may select each pure strategy with a certain probability, which leads to the concept of a mixed strategy. For each player, a mixed strategy consists of a number of possible actions and a probability distribution which corresponds to how frequently each action would be selected by the player. In this subsection, we will discuss the mixed-strategy Nash equilibrium of the game
The mixed strategy Nash equilibrium in AS and RS schemes are given by the following two theorems.
Theorem 4.5. The utility of the mixed strategy Nash equilibrium
where
Proof. In the AS scheme, we define the probability distribution
The legitimate party L can find his optimal strategy by solving the following optimization problem:
Solving the above two optimization problem yields the optimal probability value of each strategy selected by L and E as
Then substitute
This completes the proof.
Theorem 4.6. The utility of the mixed strategy Nash equilibrium
where
The proof is similar to Theorem 4.5, and thus omitted for simplicity.
5 Numerical Simulation and Result Analysis
The main parameter settings in the simulation of AS and RS scheme are as follows. The power allocation coefficients of strong users and weak users in the NOMA system are
5.2 Result Analysis in the AS Scheme
This subsection mainly analyzes the data rate of the weak user and the eavesdropper, as well as the gains of the pure and mixed strategy in the AS scheme.
The curves in Fig. 2a show the data rate
Fig. 2b shows the change of the data rate of E with
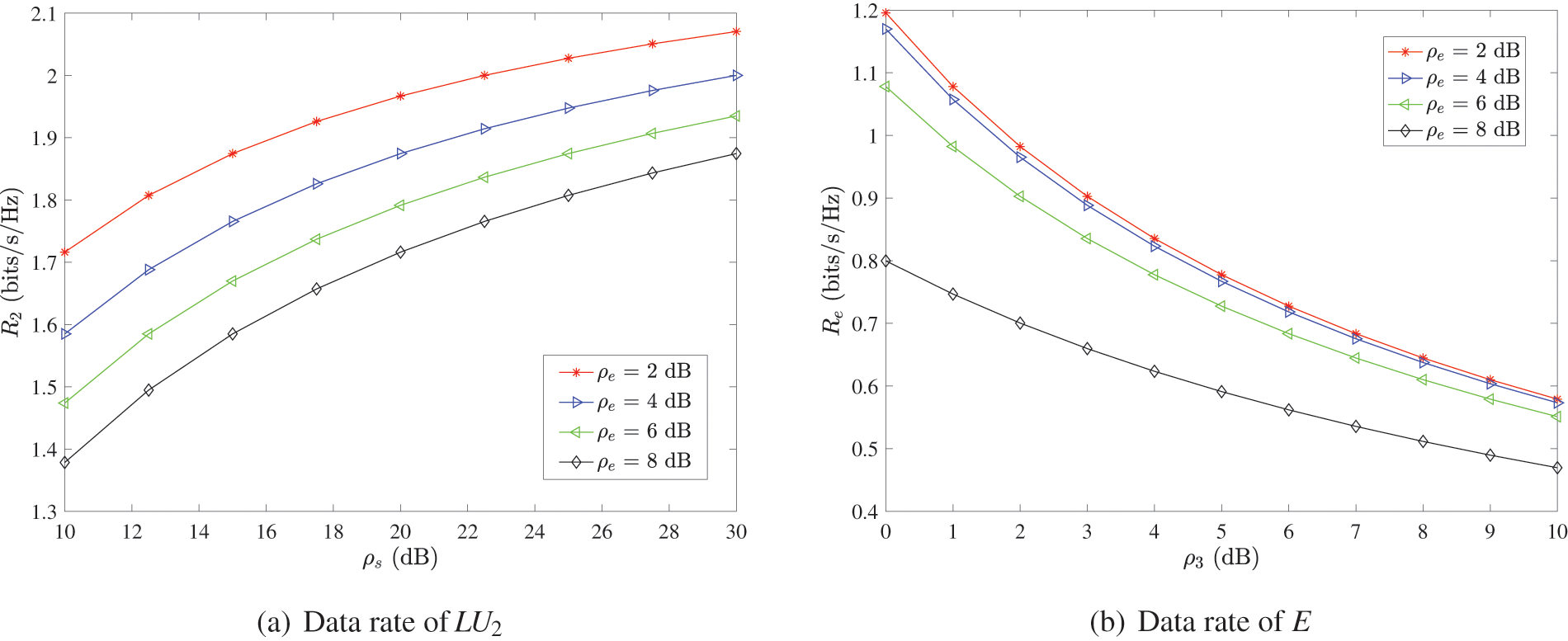
Figure 2: Data rate in the AS scheme
5.2.2 Analysis of the Pure Strategy Nash Equilibrium and Benefits
According to the aforementioned analysis, the pure strategy Nash equilibrium depends on the parameter
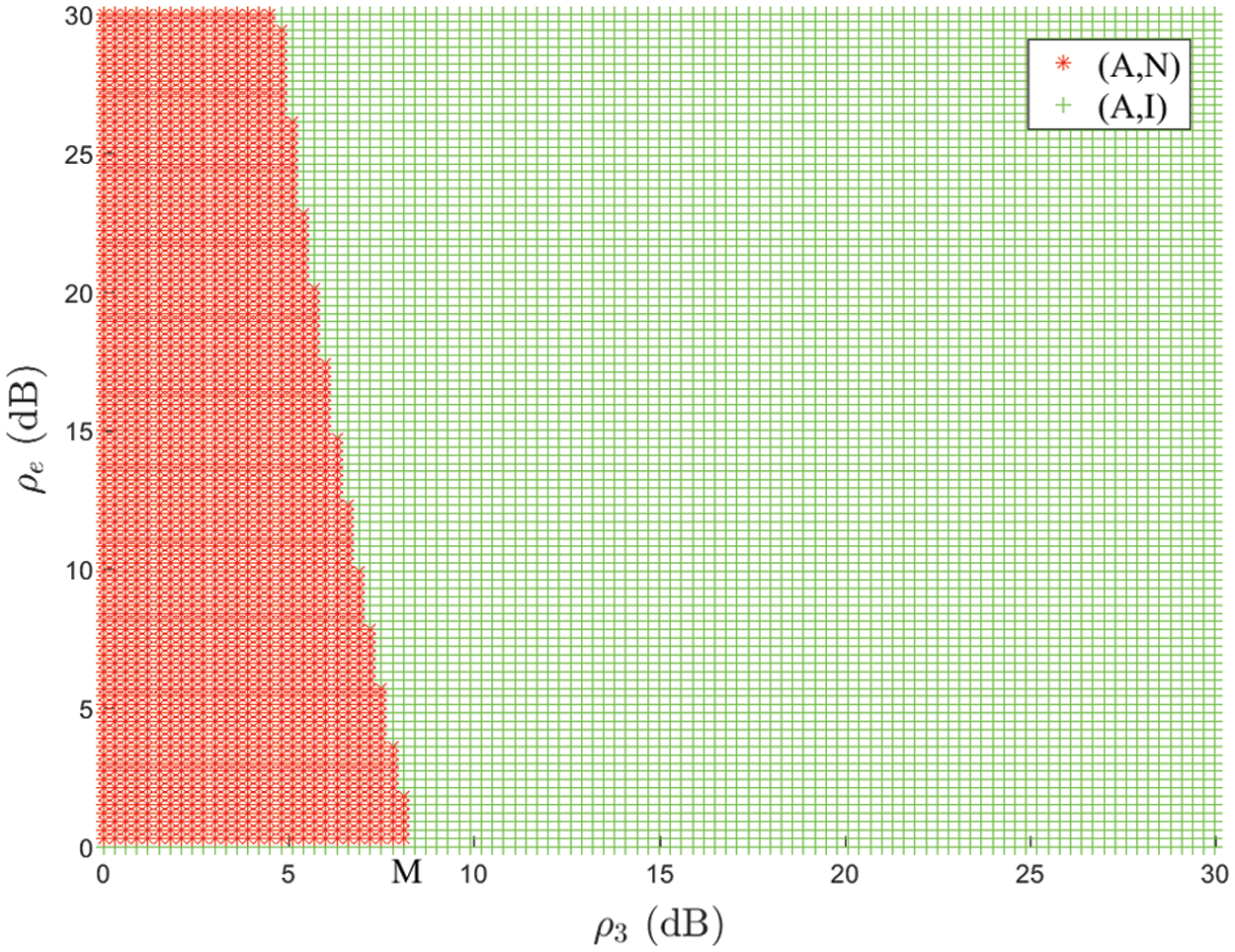
Figure 3: Effect of
The curves in Fig. 4 show the benefits (
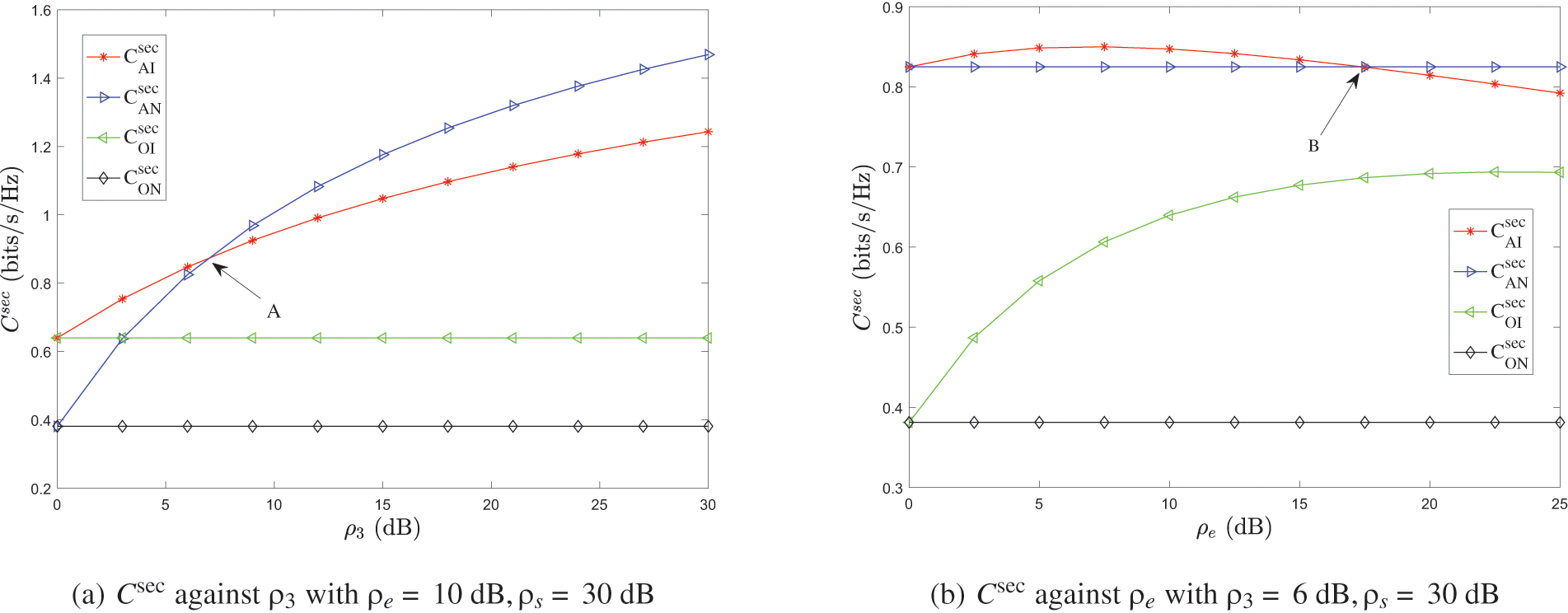
Figure 4: The benefits of pure strategy in the AS scheme
Likewise, from Fig. 4b, we can get similar results that the equilibrium strategy and the corresponding benefit is
5.2.3 Analysis of the Mixed Strategy Benefits
Fig. 5 shows the benefit variation of the mixed strategy in the AS scheme with respect to
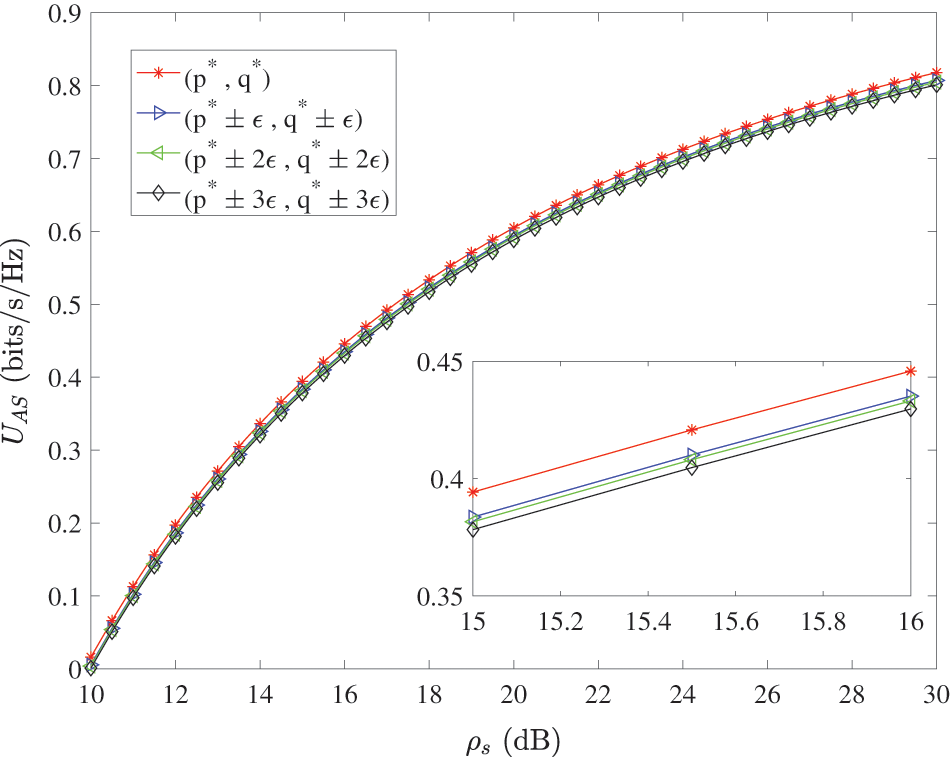
Figure 5: Benefits of mixed strategies in the AS scheme
Fig. 6 shows the comparison of benefits between the pure strategy Nash equilibrium and the mixed strategy Nash equilibrium in the AS scheme. From the local enlarged subplot, we can clearly find that the benefit curves of potential pure strategy Nash equilibrium profiles
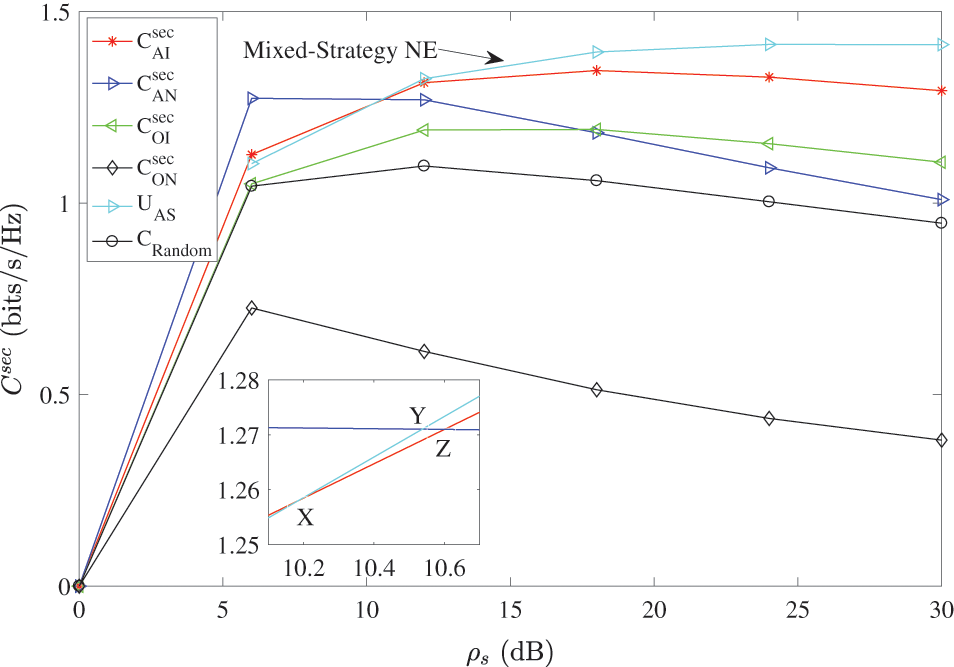
Figure 6: Comparison of the benefits between pure and mixed strategy NE in the AS scheme
Additionally, from Fig. 6, we can see that the curve of random-selection method is always below the curves of pure and mixed strategy NE. This is not good for legitimate communicators. Therefore, the legitimate communication party will not select the random-selection strategy to increase the secrecy rate, i.e., the random-selection strategy is unstable in the AS scheme.
5.3 Result Analysis in the RS Scheme
This subsection mainly analyzes the data rate of the weak user and the eavesdropper, as well as the benefits of the pure and mixed strategy in the RS schemes.
Fig. 7a shows the relationship between the information transmission rate of
Fig. 7b shows the relationship between the information transmission rate of E and
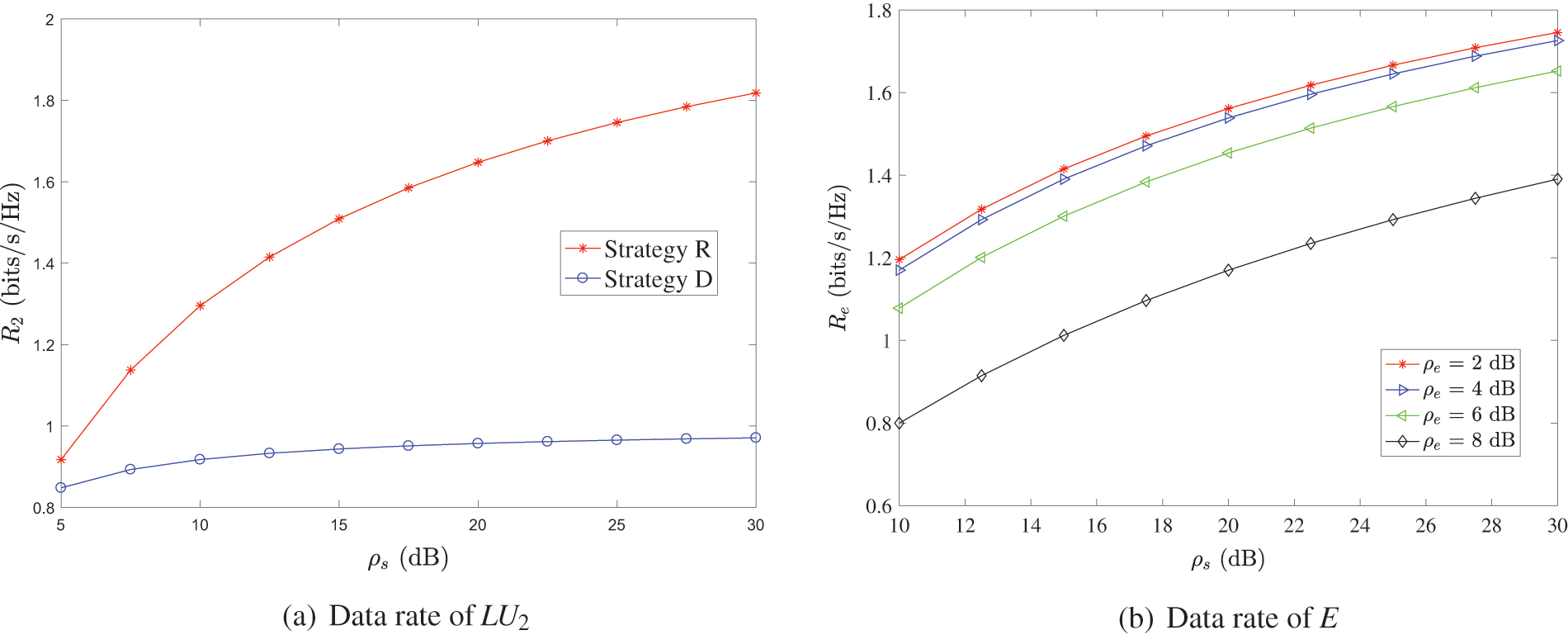
Figure 7: Data rate in the RS scheme
5.3.2 Analysis of the Pure Strategy Nash Equilibrium and Benefits
According to the analysis, the pure strategy Nash equilibrium depends on the parameter
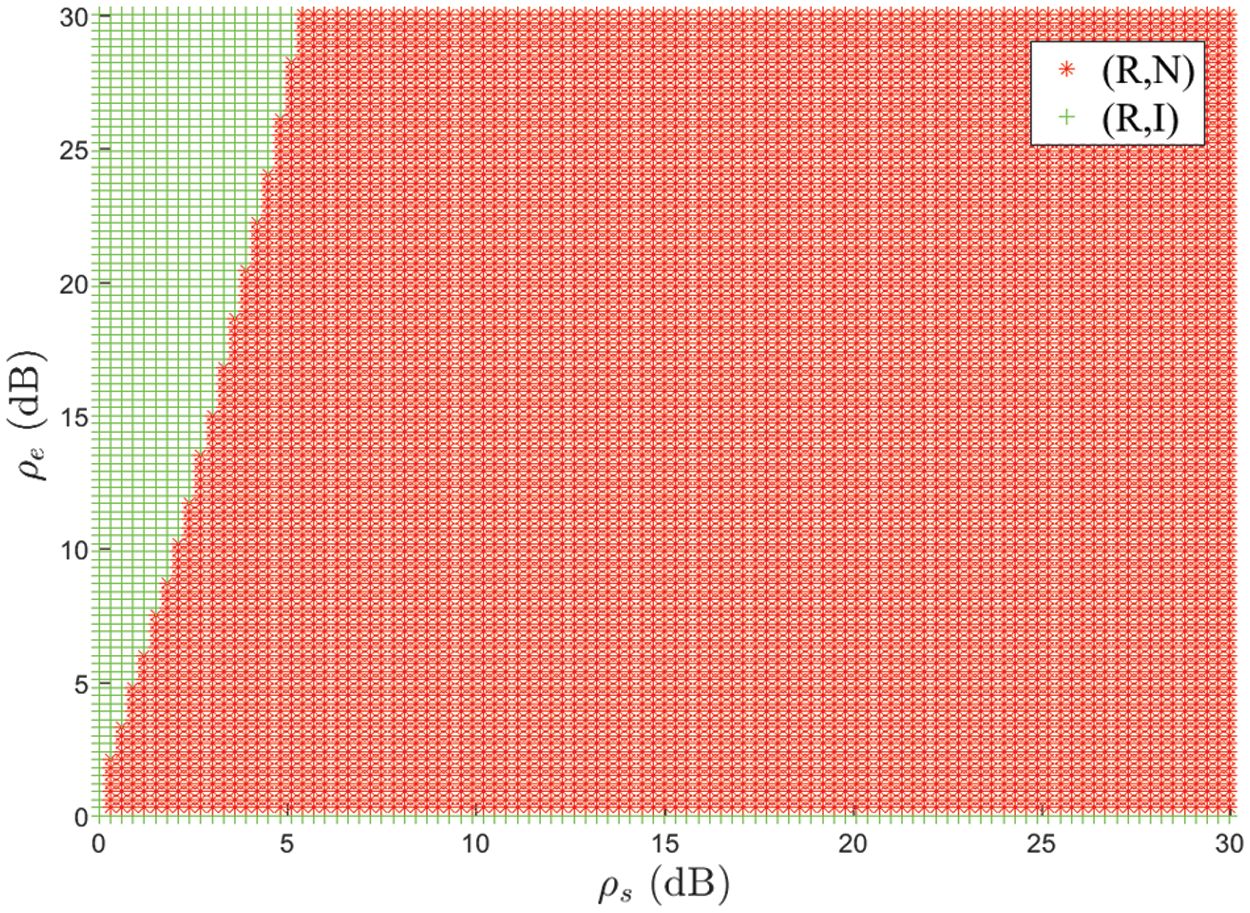
Figure 8: Effect of
Fig. 9 shows the pure strategy benefits under different conditions in the zero sum game of RS scheme. Fig. 9a shows the change of pure strategy benefits with
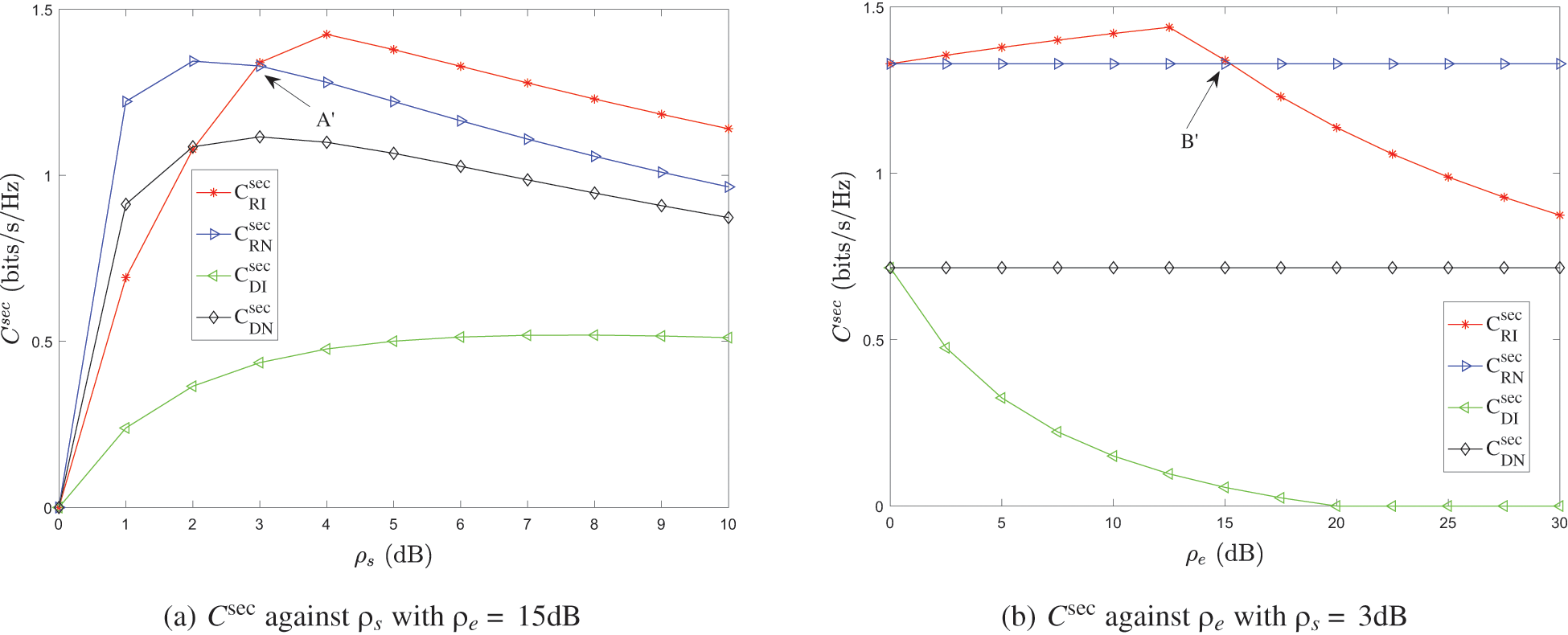
Figure 9: The benefits of pure strategy in the RS scheme
5.3.3 Analysis of the Mixed Strategy Benefits
Fig. 10 shows the change of the mixed strategy benefits of the zero sum game of RS scheme with
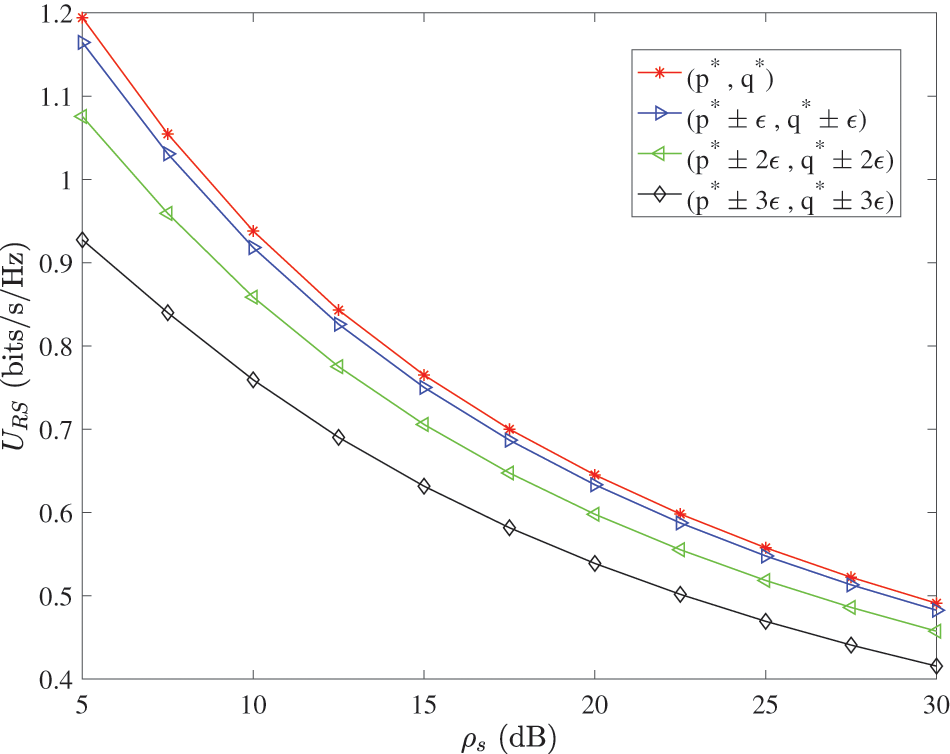
Figure 10: Benefits of mixed strategies in the RS scheme
Fig. 11 shows the comparison of benefits between the pure strategy Nash equilibrium and the mixed strategy Nash equilibrium in the RS scheme. It can be seen that the benefits of the mixed strategy Nash equilibrium are always smaller than that of the pure strategy Nash equilibrium. Therefore, both sides of the game will always choose a pure strategy. That is to say, in the zero-sum game of the RS scheme, both sides will choose the pure strategy NE profile
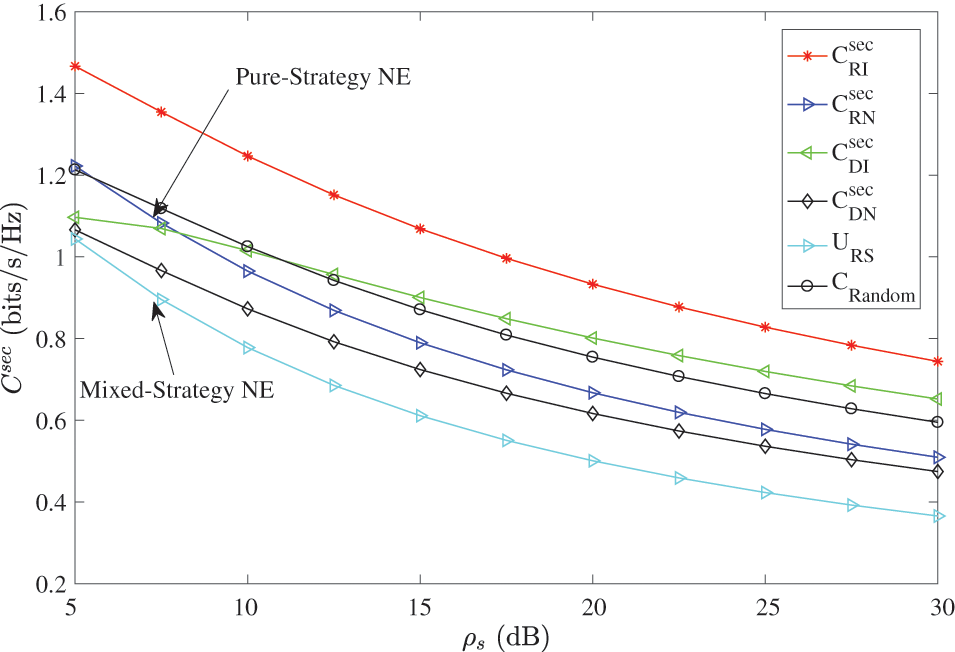
Figure 11: Comparison of the benefits between pure and mixed strategy NE in the RS scheme
Additionally, from Fig. 11, we can observe that the curve of random-selection method is always above the curves of pure and mixed strategy NE. This is not good for the active eavesdropper. Therefore, the active eavesdropper will not select the random-selection strategy to decrease the secrecy rate, i.e., the random-selection strategy is also unstable in the RS scheme.
In the scenario of the standard downlink NOMA transmission system, this paper considers two typical physical layer security design schemes based on artificial signals and relay assistance. The non-cooperative behavior between the legitimate communication party and the eavesdropping party under the two schemes is modeled as a two-person zero-sum game. The game is used to characterize the confrontational behavior relationship between the two parties and the process of mutual influence, and prove the existence of the game Nash equilibrium. Through the solution and analysis of the pure strategy and mixed strategy Nash equilibrium of the security game model, the best strategy profile of the two parties in the confrontation environment is given. Numerical simulation results show that both solutions can improve the physical layer security of the NOMA system. The physical layer security game model proposed in this paper can be extended to other scenarios (such as the combination of relay and artificial signals) and can be used to guide the analysis and design of security solutions. However, the cases where there are multiple eavesdroppers and multi-user pairs have not been considered in this paper, and need to be studied in the future.
Acknowledgement: The authors wish to express their appreciation to the reviewers for their helpful suggestions which greatly improved the presentation of this paper.
Funding Statement: This research was supported by the National Natural Science Foundation of China under Grants U1836104, 61801073, 61931004, 62072250, National Key Research and Development Program of China under Grant 2021QY0700, and The Startup Foundation for Introducing Talent of NUIST under Grant 2021r039.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. Dai, L., Wang, B., Yuan, Y., Han, S., Chih-Lin, I. et al. (2015). Non-orthogonal multiple access for 5G: Solutions, challenges, opportunities, and future research trends. IEEE Communications Magazine, 53(9), 74–81. DOI 10.1109/MCOM.35. [Google Scholar] [CrossRef]
2. Ding, Z. G., Lei, X. F., Karagiannidis, G. K., Schober, R., Yuan, J. H. et al. (2017). A survey on non-orthogonal multiple access for 5G networks: Research challenges and future trends. IEEE Journal on Selected Areas in Communications, 35(10), 2181–2195. DOI 10.1109/JSAC.49. [Google Scholar] [CrossRef]
3. Liu, Y., Pan, G. F., Zhang, H. T., Song, M. (2016). On the capacity comparison between mimo-noma and mimo-oma. IEEE Access, 4, 2123–2129. DOI 10.1109/ACCESS.2016.2563462. [Google Scholar] [CrossRef]
4. Wu, Y. P., Khisti, A., Xiao, C. S., Caire, G., Wong, K. K. et al. (2018). A survey of physical layer security techniques for 5G wireless networks and challenges ahead. IEEE Journal on Selected Areas in Communications, 36(4), 679–695. DOI 10.1109/JSAC.2018.2825560. [Google Scholar] [CrossRef]
5. Yang, N., Wang, L. F., Geraci, G., Elkashlan, M., Yuan, J. H. et al. (2015). Safeguarding 5G wireless communication networks using physical layer security. IEEE Communications Magazine, 53(4), 20–27. DOI 10.1109/MCOM.35. [Google Scholar] [CrossRef]
6. Wang, Y., Zhou, X., Zhuang, Z., Sun, L., Qian, Y. et al. (2020). UAV-enabled secure communication with finite blocklength. IEEE Transactions on Vehicular Technology, 69(12), 16309–16313. DOI 10.1109/TVT.2020.3042791. [Google Scholar] [CrossRef]
7. Xia, G., Jia, L., Qian, Y., Shu, F., Zhuang, Z. et al. (2019). Power allocation strategies for secure spatial modulation. IEEE Systems Journal, 13(4), 3869–3872. DOI 10.1109/JSYST.2019.2918168. [Google Scholar] [CrossRef]
8. Shiu, Y. S., Chang, S. Y., Wu, H. C., Huang, S. C. H., Chen, H. H. (2011). Physical layer security in wireless networks: A tutorial. IEEE Wireless Communications, 18(2), 66–74. DOI 10.1109/MWC.2011.5751298. [Google Scholar] [CrossRef]
9. Liu, Y. W., Qin, Z. J., Elkashlan, M., Gao, Y., Hanzo, L. (2017). Enhancing the physical layer security of non-orthogonal multiple access in large-scale networks. IEEE Transactions on Wireless Communications, 16(3), 1656–1672. DOI 10.1109/TWC.2017.2650987. [Google Scholar] [CrossRef]
10. Li, A. (2019). Enhancing the physical layer security of cooperative noma system. 2019 IEEE 3rd Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Chengdu, China. [Google Scholar]
11. Huang, S. C., Xiao, M., Poor, H. V. (2020). On the physical layer security of millimeter wave noma networks. IEEE Transactions on Vehicular Technology, 69(10), 11697–11711. DOI 10.1109/TVT.25. [Google Scholar] [CrossRef]
12. Ding, Z. G., Zhao, Z. Y., Peng, M. G., Poor, H. V. (2017). On the spectral efficiency and security enhancements of noma assisted multicast-unicast streaming. IEEE Transactions on Communications, 65(7), 3151–3163. DOI 10.1109/TCOMM.2017.2696527. [Google Scholar] [CrossRef]
13. Zhang, H. J., Yang, N., Long, K. P., Pan, M., Karagiannidis, G. K. et al. (2018). Secure communications in noma system: Subcarrier assignment and power allocation. IEEE Journal on Selected Areas in Communications, 36(7), 1441–1452. DOI 10.1109/JSAC.2018.2825559. [Google Scholar] [CrossRef]
14. Cao, K. R., Wang, B. H., Ding, H. Y., Li, T. Y., Tian, J. W. et al. (2020). Secure transmission designs for noma systems against internal and external eavesdropping. IEEE Transactions on Information Forensics and Security, 15, 2930–2943. DOI 10.1109/TIFS.10206. [Google Scholar] [CrossRef]
15. Cao, Y., Zhao, N., Chen, Y. F., Jin, M. L., Ding, Z. G. et al. (2020). Secure transmission via beamforming optimization for noma networks. IEEE Wireless Communications, 27(1), 193–199. DOI 10.1109/MWC.7742. [Google Scholar] [CrossRef]
16. Jia, F., Zhang, C. S., Jiang, C. J., Li, M. D., Ge, J. H. (2021). Guaranteeing positive secrecy rate for noma system against internal eavesdropping. IEEE Communications Letters, 25(6), 1805–1809. DOI 10.1109/LCOMM.2021.3062832. [Google Scholar] [CrossRef]
17. Alsaba, Y., Leow, C. Y., Abdul Rahim, S. K. (2018). A zero-sum game approach for non-orthogonal multiple access systems: Legitimate eavesdropper case. IEEE Access, 6, 58764–58773. DOI 10.1109/ACCESS.2018.2874215. [Google Scholar] [CrossRef]
18. Gong, C. H., Yue, X. W., Zhang, Z. Y., Wang, X. Y., Dai, X. M. (2021). Enhancing physical layer security with artificial noise in large-scale noma networks. IEEE Transactions on Vehicular Technology, 70(3), 2349–2361. DOI 10.1109/TVT.2021.3057661. [Google Scholar] [CrossRef]
19. Zhang, W., Chen, J., Kuo, Y. H., Zhou, Y. C. (2019). Artificial-noise-aided optimal beamforming in layered physical layer security. IEEE Communications Letters, 23(1), 72–75. DOI 10.1109/LCOMM.2018.2881182. [Google Scholar] [CrossRef]
20. Zhang, M., Liu, Y., Zhang, R. (2016). Artificial noise aided secrecy information and power transfer in ofdma systems. IEEE Transactions on Wireless Communications, 15(4), 3085–3096. DOI 10.1109/TWC.2016.2516528. [Google Scholar] [CrossRef]
21. Wang, B., Mu, P. C., Li, Z. Z. (2017). Artificial-noise-aided beamforming design in the misome wiretap channel under the secrecy outage probability constraint. IEEE Transactions on Wireless Communications, 16(11), 7207–7220. DOI 10.1109/TWC.2017.2742954. [Google Scholar] [CrossRef]
22. Lee, J. (2015). Full-duplex relay for enhancing physical layer security in multi-hop relaying systems. IEEE Communications Letters, 19(4), 525–528. DOI 10.1109/LCOMM.2015.2401551. [Google Scholar] [CrossRef]
23. Feng, Y. H., Yan, S. H., Liu, C. X., Yang, Z., Yang, N. (2019). Two-stage relay selection for enhancing physical layer security in non-orthogonal multiple access. IEEE Transactions on Information Forensics and Security, 14(6), 1670–1683. DOI 10.1109/TIFS.2018.2883273. [Google Scholar] [CrossRef]
24. Chen, B., Li, R., Ning, Q., Lin, K., Han, C. et al. (2022). Security at physical layer in noma relaying networks with cooperative jamming. IEEE Transactions on Vehicular Technology, 71(4), 3883–3888. DOI 10.1109/TVT.2022.3144531. [Google Scholar] [CrossRef]
25. Cao, K., Wang, B., Ding, H., Li, T., Gong, F. (2020). Optimal relay selection for secure noma systems under untrusted users. IEEE Transactions on Vehicular Technology, 69(2), 1942–1955. DOI 10.1109/TVT.2019.2962860. [Google Scholar] [CrossRef]
26. Chen, B., Chen, Y., Cao, Y., Chen, Y., Zhao, N. et al. (2020). Security enhancement using a novel two-slot cooperative noma scheme. IEEE Transactions on Vehicular Technology, 69(3), 3470–3475. DOI 10.1109/TVT.2020.2966996. [Google Scholar] [CrossRef]
27. Zhao, R., Huang, Y. M., Wang, W., Lau, V. N. (2016). Ergodic achievable secrecy rate of multiple-antenna relay systems with cooperative jamming. IEEE Transactions on Wireless Communications, 15(4), 2537–2551. DOI 10.1109/TWC.2015.2504526. [Google Scholar] [CrossRef]
28. Lv, L., Zhou, F. H., Chen, J., Al-Dhahir, N. (2019). Secure cooperative communications with an untrusted relay: A noma-inspired jamming and relaying approach. IEEE Transactions on Information Forensics and Security, 14(12), 3191–3205. DOI 10.1109/TIFS.10206. [Google Scholar] [CrossRef]
29. Zheng, G. (2015). Joint beamforming optimization and power control for full-duplex mimo two-way relay channel. IEEE Transactions on Signal Processing, 63(3), 555–566. DOI 10.1109/TSP.2014.2376885. [Google Scholar] [CrossRef]
30. Kang, Y. Y., Kwak, B., Cho, J. H. (2014). An optimal full-duplex af relay for joint analog and digital domain self-interference cancellation. IEEE Transactions on Communications, 62(8), 2758–2772. DOI 10.1109/TCOMM.2014.2342230. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools