 Open Access
Open Access
ARTICLE
Application of Zero-Watermarking for Medical Image in Intelligent Sensor Network Security
Medical Data Science Academy, College of Medical Informatics, Chongqing Medical University, Chongqing, 400016, China
* Corresponding Authors: Jinglong Du. Email: ; Baoru Han. Email:
Computer Modeling in Engineering & Sciences 2023, 136(1), 293-321. https://doi.org/10.32604/cmes.2023.022308
Received 03 March 2022; Accepted 30 August 2022; Issue published 05 January 2023
Abstract
The field of healthcare is considered to be the most promising application of intelligent sensor networks. However, the security and privacy protection of medical images collected by intelligent sensor networks is a hot problem that has attracted more and more attention. Fortunately, digital watermarking provides an effective method to solve this problem. In order to improve the robustness of the medical image watermarking scheme, in this paper, we propose a novel zero-watermarking algorithm with the integer wavelet transform (IWT), Schur decomposition and image block energy. Specifically, we first use IWT to extract low-frequency information and divide them into non-overlapping blocks, then we decompose the sub-blocks by Schur decomposition. After that, the feature matrix is constructed according to the relationship between the image block energy and the whole image energy. At the same time, we encrypt watermarking with the logistic chaotic position scrambling. Finally, the zero-watermarking is obtained by XOR operation with the encrypted watermarking. Three indexes of peak signal-to-noise ratio, normalization coefficient (NC) and the bit error rate (BER) are used to evaluate the robustness of the algorithm. According to the experimental results, most of the NC values are around 0.9 under various attacks, while the BER values are very close to 0. These experimental results show that the proposed algorithm is more robust than the existing zero-watermarking methods, which indicates it is more suitable for medical image privacy and security protection.Keywords
With the increasing maturity of intelligent sensor network technology and the continuous improvement of hospital information construction, intelligent sensor network technology is more and more widely used in hospital information systems by combining wide area networks (WAN), wireless networks and other network fields [1]. Most of the data collected by the hospital intelligent sensor network terminal itself belongs to sensitive medical information. Once the information is leaked or maliciously modified, it will bring irreparable losses to the hospital. At the same time, medical information will involve patient information in the process of network transmission. If patient information is leaked, it will bring a huge threat to the patient’s personal privacy, property security, and information security [2]. Therefore, it is necessary to ensure the security of patient information.
In the current field of healthcare, more and more medical information is collected and transmitted through intelligent sensor networks. Among them, medical images provide a visual way for clinicians to diagnose the condition of patients. An increasing number of medical images are transmitted among different positions through the network. Most of these medical images contain personal privacy details, which may be maliciously intercepted and tampered with by some illegal elements during the transmission. Therefore, the digital watermarking technique has been gradually applied to protect the security of the medical image [3]. It embeds specified information that cannot be visually detected and in the digital carrier without affecting the transmission, which plays a role in copyright protection [4]. The digital watermarking method can be implemented in spatial and transform domains. The spatial domain algorithm is simple and lightweight. In contrast, the transform-based method has better transparency and robustness, so it has become mainstream in the field of digital watermarking.
In the spatial domain, the least significant bit (LSB) is a commonly-used technique [5,6]. For example, Wang et al. proposed a fragile watermarking method based on the LSB, hash functions and chaotic sequences [7]. The commonly-used method in the transform domain is discrete cosine transform (DCT), discrete wavelet transform (DWT), discrete Fourier transform (DFT) and so on [8–10]. In addition, many techniques based on the geometric moment of image watermarking are also widely used [11]. A technique of embedding the scrambled binary watermarking into a host color image by adapting the fractional-order multi-channel orthogonal exponent moments (MFrEMs) magnitudes was proposed by Hosny et al. [12]. Besides, some algorithms divide medical images into regions of interest (ROI) and regions of non-interest (RONI) to accurately extract the features matrix [13–15]. However, the division of ROI regions often requires manual evaluation and distinguishing, which limits the application situation of these algorithms. However, most of the above methods construct the watermarking by making some changes to the original image [16].
To solve this problem, Wen et al. proposed a zero-watermarking algorithm to construct the watermarking according to the characteristic information of the image itself, which could solve the contradiction between the perceptibility and robustness of digital watermarking [17]. This type of zero-watermarking algorithm is widely used in the copyright protection of medical images. Aditi et al. designed a multiple watermarking algorithm using DWT, DCT and singular value decomposition (SVD) which used medical block image watermarking, doctor signature and patient diagnosis information as text watermarking [18]. Similarly, Liu et al. [19] proposed a medical image zero-watermarking algorithm based on dual-tree complex wavelet transform and discrete cosine transform. Then, the zero-watermarking was encrypted by a Logistic map. Hu et al. [20] proposed a robust medical image zero-watermarking algorithm combining bi-dimensional empirical mode decomposition (BEMD) with SVD, which could effectively detect image tampering and protect the copyright of medical images. Xia et al. [21] extended the integer-order radial harmonic Fourier moments (IoRHFMs) to fractional-order radial harmonic Fourier moments (FoRHFMs), and then proposed a FoRHFM-based medical image zero-watermarking algorithm, which improved the calculation accuracy of IoRHFMs and effectively alleviated the problem of numerical instability. Dai et al. [22] proposed a hybrid reversible zero-watermarking (HRZW), in which the authors combined the zero-watermarking and reversible watermarking to generate the ownership shares through the characteristics and watermarking information of the nearest neighbor gray residue (NNGR), and then reversibly embed the generated ownership shares based on slantlet transform, singular value decomposition and quantization index modulation (SLT-SVD-QIM). For medical images, a robust zero-watermarking algorithm by fusing Dual-Tree Complex Wavelet Transform (DTCWT), Hessenberg decomposition, and Multi-level Discrete Cosine Transform (MDCT) was proposed by Huang et al. [23].
The current focus of the watermarking algorithm research is on the robustness of this algorithm under various attacks. However, these algorithms are less robust against high-intensity conventional and geometric attacks, especially Gaussian noise, scaling attacks, and cropping attacks. And most algorithms do not test the robustness of multiple attacks.
To address these issues, in this paper, we propose a zero-watermarking algorithm based on IWT, Schur decomposition and image block energy. Specifically, we use IWT to extract low-frequency regions from the original medical image and divide them into non-overlapping blocks, which are subsequently decomposed by the Schur decomposition. Then, we extract the feature matrix by comparing the energy of the image block and the whole image. Finally, we adopt the XOR operation on the encrypted watermarking image and the feature matrix to generate the zero-watermarking. To summarize, we make the following contributions in this work:
(1) We use IWT to avoid the defect of quantization error introduced in the medical image calculation process;
(2) We improve the robustness and stability using the Schur decomposition with vector scale invariance and quantum space invariance;
(3) We utilize the relationship between the block energy of the transform domain and the average energy of medical images to construct the zero-watermarking, which can achieve good robustness against various attacks even with multiple attacks.
2.1 Integer Wavelet Transform (IWT)
Sweldens et al. proposed a lifting scheme which accelerates the speed of fast wavelet transform [24]. Afterward, Calderbank et al. proposed IWT on the basis of a lifting scheme [25]. The coefficients of this algorithm are all integers after transformation, so IWT not only retains the characteristics of wavelet transform but also speeds up the operation. The transformation process of the algorithm includes the following three steps: (1) Splitting: splitting the original data set into two disjoint subsets, an even subset and an odd subset. (2) Prediction: on the basis of the original data and based on the relationship between the data, a prediction operator is constructed, and the even subset sequence is used to predict the odd subset sequence. The error between the predicted value and the original odd subset will generate error data. (3) Update: to make the even subset generated in the splitting step always retain some characteristics of the original data set, an update operator is constructed to update the even subset.
The IWT is the same as the traditional wavelet transform. The original image is still decomposed into four sub-bands after a wavelet transform. A schematic diagram of the 2-level IWT decomposition is shown in Fig. 1. It is the low-frequency component LL of the original image in the horizontal and vertical direction; LH is the low frequency in the horizontal direction and the high frequency in the vertical direction; HL is the high frequency in the horizontal direction and the low frequency in the vertical direction; and HH is the high-frequency component in the horizontal and vertical directions. Among them, the LL sub-band is the low-frequency sub-band containing the features of the original image. If the multi-level transformation is to be carried out, only the low-frequency sub-band is further decomposed. Compared with the traditional wavelet transform, the IWT algorithm is faster and simpler, suitable for parallel processing and takes up less memory.

Figure 1: Schematic diagram of the 2-level IWT decomposition
Schur decomposition is a common matrix decomposition, which is similar to SVD. SVD can be derived from Schur decomposition. Schur decomposition’s theorem is as follows:
For any matrix
The time complexity of SVD is bigger than the time complexity of Schur decomposition [27]. Thus, it can be seen that Schur decomposition can reduce the computational complexity and save a lot of computing time compared with SVD.
Each image has its overall energy, but in the zero-watermarking algorithm, the fact that the original image can effectively resist all kinds of attacks shows that the features constructed by the algorithm are very robust. So, on the basis of the overall image energy, choose to block the image to calculate the energy of the block image. The original image is divided into
where
In [28], the natural image is used to test the relationship between the overall average energy and the average energy when the original image is attacked by different attacks. While this paper studies the medical image, there are some differences in imaging principles and inherent characteristics between medical images and natural images. Therefore, this paper chooses the MRI image with a size of 128 × 128 as the original image and divides it into 2 × 2 blocks for testing. When the original image is attacked by Gaussian noise (10%), JEPG compression (50%), median filtering (3 × 3), counterclockwise rotation (5°) and scaling (0.25), the relationship between the overall average energy of the medical image and the block average energy is shown in Table 1.

As shown in Table 1, T0 represents the number of blocks whose average energy is greater than the overall average energy, while T1 indicates that the average energy of blocks is less than the number of blocks with overall average energy. And peak signal-to-noise ratio (PSNR) is an objective index to evaluate image quality. After different attacks, except that the value of PSNR fluctuates greatly, but the ratio between T0 and T1 is not large, so it has strong robustness. It can be seen that this feature extraction method is also suitable for the construction of zero-watermarking in medical images.
The medical image watermarking algorithm proposed in this paper can be divided into the process of zero-watermarking construction and extraction, as shown in Fig. 2.

Figure 2: The flow chart of the proposed zero-watermarking construction and extraction process
3.1 Zero-Watermarking Construction
The collected medical images are transmitted to the data center by an intelligent sensor network. Then upload the medical image to the medical cloud platform according to the requirements of medical information management. In order to protect patient information disclosure or authentication, the medical image stored in the data center is used as the original image to construct a zero-watermarking.
We use the logistic chaotic scrambling method to encrypt the binary watermarking image
where
To construct the zero-watermarking, we adopt the IWT to extract the feature matrix from the original image features [29]. The IWT not only retains the characteristics of the wavelet transform but also is faster, which meets the requirements of accuracy and accurate decomposition of medical images. Therefore, we utilize the 2-level IWT to extract the low-frequency part of the original medical image
where
Schur decomposition is a commonly-used matrix decomposition method, which is similar to SVD operation [27]. Compared with SVD, it can reduce computational complexity and save a lot of computing time. In addition, Schur decomposition also has vector scaling invariance and quantum space invariance, so it can effectively resist scaling attacks. These important characteristics make the zero-watermarking algorithm faster, more robust and stable. The low-frequency part of the original medical image is divided into non-overlapping blocks. Then decomposes the blocks by the Schur decomposition. The specific realization process can be written as:
where
Each image has its overall energy, but in the zero-watermarking algorithm, the fact that the original image can effectively resist all kinds of attacks shows that the features constructed by the algorithm are very robust. Because the relationship between the overall average energy of the medical image and the average energy of each block has strong robustness. The calculation of the overall original medical image I energy is given by:
On the basis of the overall image energy, we choose to block the image to calculate the energy of the split image. The original image is divided into
Based on the overall average energy and block average energy of the carrier image calculated in the above steps, the method of constructing the feature matrix can be represented as:
Finally, the zero-watermarking Z is generated by the exclusive XOR operation of the feature matrix T and the scrambled watermarking image
The final zero-watermarking Z is registered in the copyright authentication center. The construction process is shown in Fig. 2. The specific steps are as Algorithm 1.
3.2 Zero-Watermarking Extraction
The zero-watermarking extraction is similar to the above-described construction process. The difference is that the feature matrix obtained from the attacked medical image is XOR with the zero-watermarking from the copyright authentication center, and then inverse scrambling is carried out to the extraction watermarking image
In formula (10) and formula (11), M is the length and width of the original medical image, N is the length and width of the watermarking image. In formula (12),
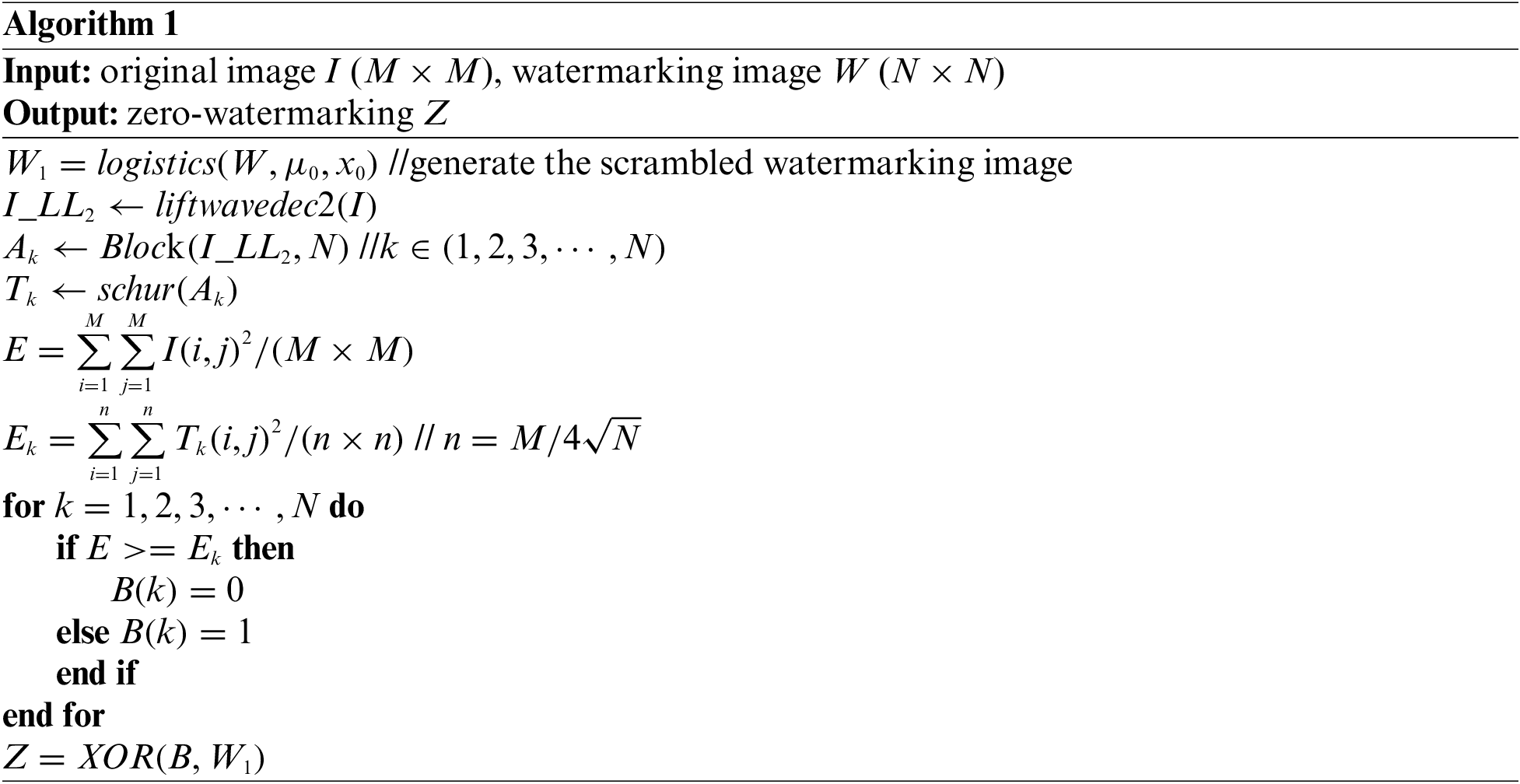
In the experiment, we implement the construction and extraction of zero-watermarking using the MATLAB R2018a platform. The original medical images include the brain, lung, chest and hand with the size of 128 × 128 are used as the original carrier images, as shown in Figs. 3a–3d. The original watermarking images with the size of 64 × 64 are given in Figs. 3e–3f.

Figure 3: The original carrier medical image and the watermarking image used in the experiment
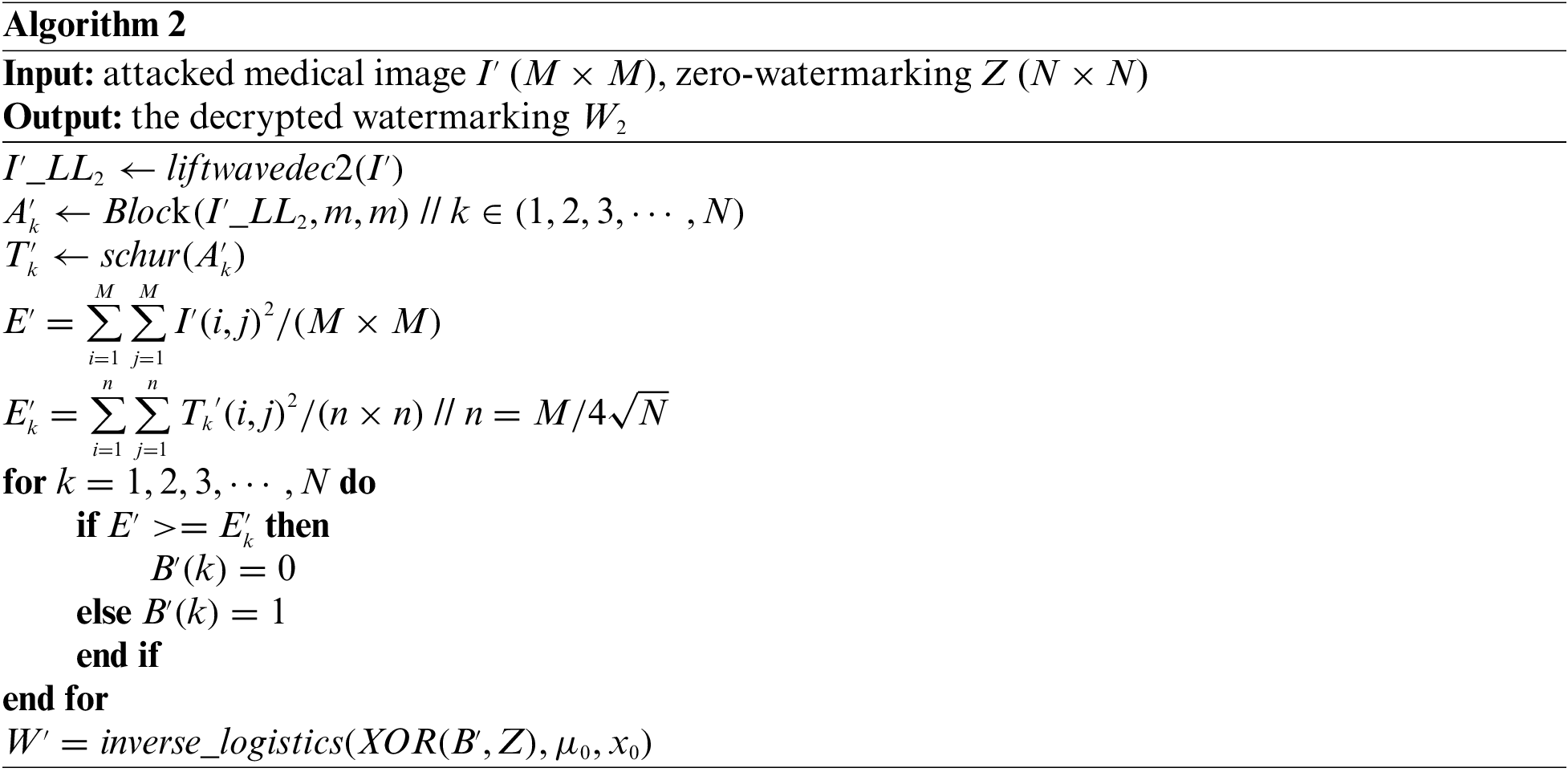
In this paper, we simulate conventional attacks (Gaussian noise, salt & pepper noise, speckle noise, JPEG compression and median filtering, average filtering and Gaussian filtering), geometric attacks (scaling, cropping, rotation, and translation) and combination attacks to evaluate our proposed medical watermarking algorithm. Here, PSNR is used to measure the distortion of the original medical image after being attacked. Besides, we use the NC value given in formula (11) and the BER given in formula (12) to measure the similarity between the extracted watermarking image and the original watermarking image. Due to a large amount of data in the experimental results, only the experimental data of watermarking image Fig. 3e are listed in Tables 2–4.



The first is to carry out some kinds of noise attacks. In this paper, Gaussian noise, salt & pepper noise and speckle noise with different intensities (5%, 10%, 15%, 20% and 25%) are selected to attack the four original medical images. The NC values of all four medical images under the Gaussian noise attack are above 0.88 with the increasing noise intensity as shown in Table 2. Under salt & pepper noise and speckle noise, the NC values of four medical images are greater than 0.9 under an intensity of 25%. Especially under speckle noise attacks, the NC values are always greater than 0.91. And under all three types of noise attacks, the BER values of the images are less than 0.15. As shown in Figs. 4–6, when all kinds of medical images are attacked by three noises of intensity 15%, the NC values are greater than 0.95 despite the serious distortion of the original images. It indicates that the proposed algorithm is robust to noise attacks.
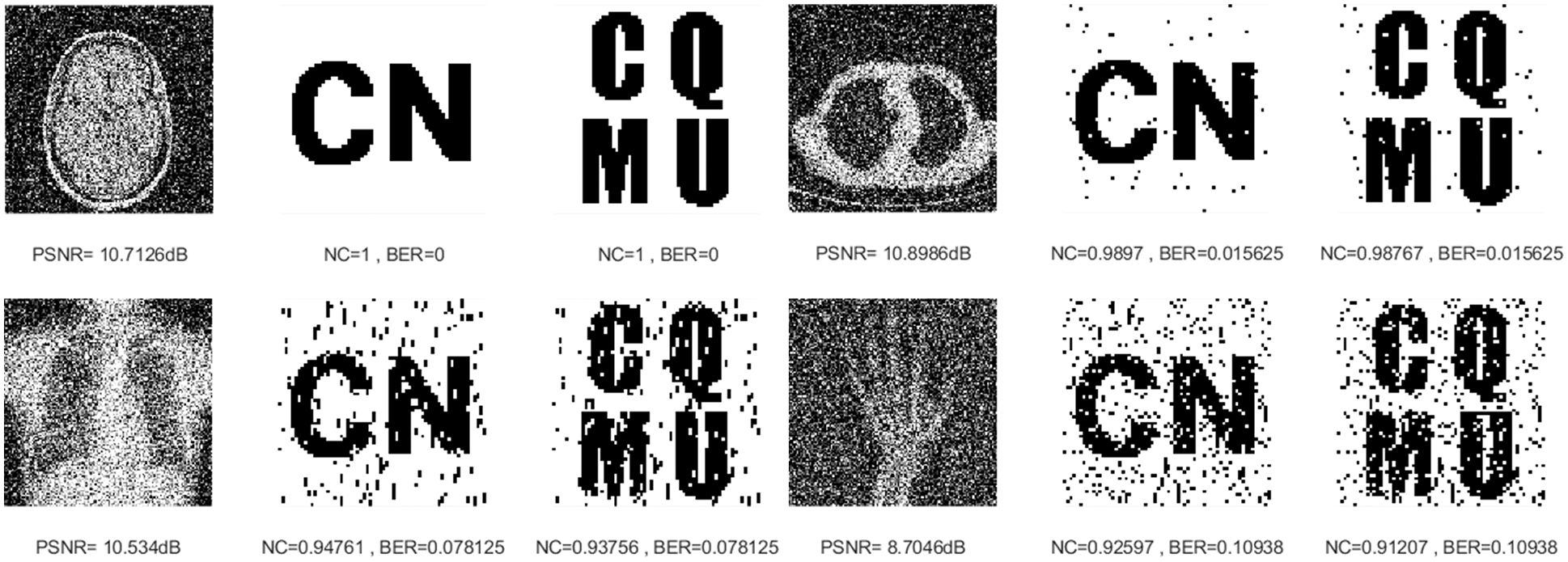
Figure 4: Four medical images and extracted watermarking images with Gaussian noise attack intensity of 15%

Figure 5: Four medical images and extracted watermarking images with salt & pepper noise attack intensity of 15%
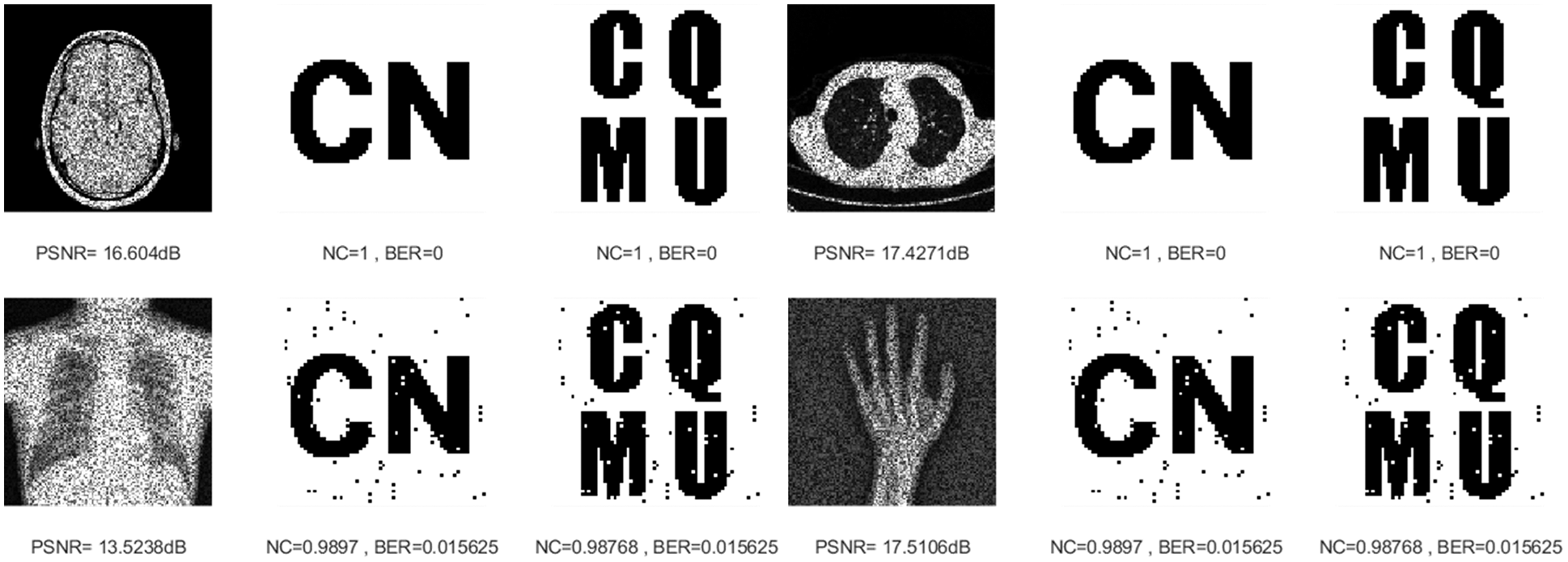
Figure 6: Four medical images and extracted watermarking images with speckle noise attack intensity of 15%
Similarly, the NC values of all four medical images are maintained above 0.97 and their BER values are less than 0.04 through JPEG compression attacks of different intensities. When the strength is 15%, the attack results of the four images are shown in Fig. 7, and we can still see the watermarking pattern clearly through the naked eye. This demonstrates that our algorithm can effectively resist JPEG compression attacks.
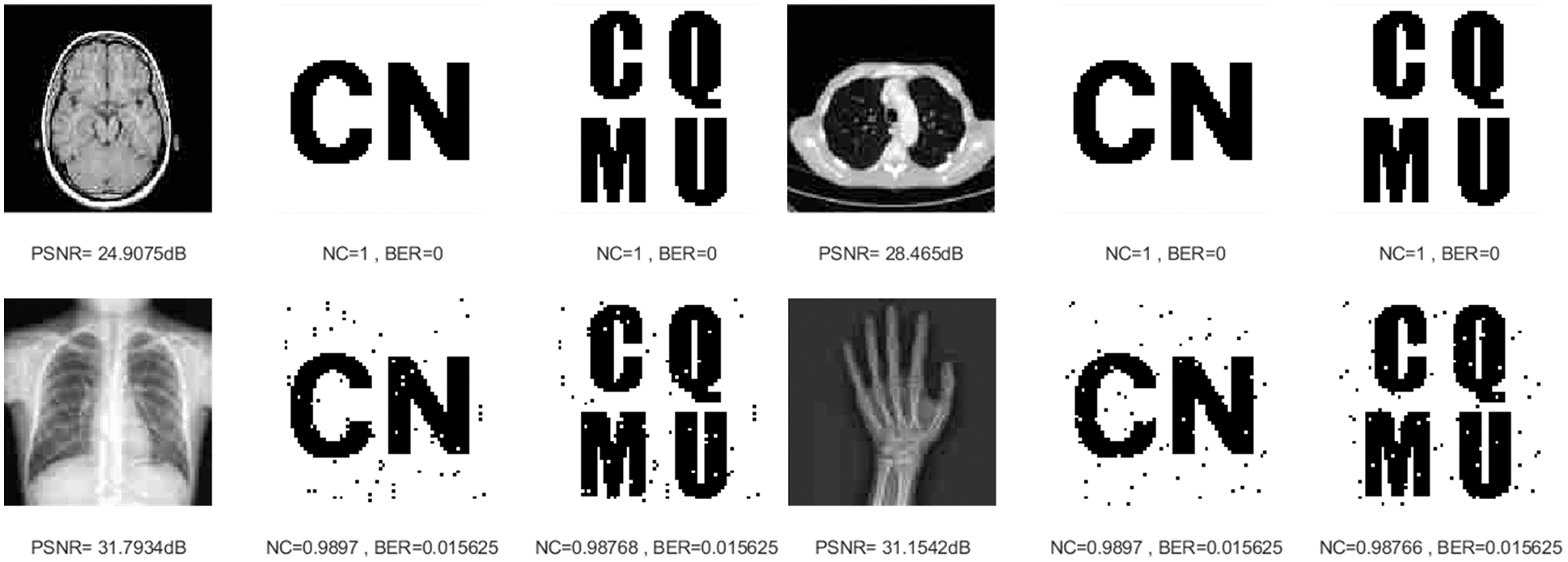
Figure 7: Four medical images and extracted watermarking images with JPEG compression attack intensity of 15%
Three kinds of filtering attacks are also selected in this paper, namely, median filtering, average filtering, and Gaussian filtering. As can be seen from Table 2, as the attack intensity increases, the NC values of the brain image and lung image are almost 1, while the other two images have NC values above 0.96, and the BER values are also very close to 0. As shown in Figs. 8–10, we can see that the median filtering intensity and the mean filtering intensity are 7 × 7, and the Gaussian filtering intensity is 7 × 3. The images have been very blurred, but the watermarking image is still relatively complete, even the NC values of brain image and lung image are still equal to 1. The two observations mentioned above verify the good performance against various filtering attacks. Overall, these results shown in Table 2 demonstrated that the proposed algorithm has strong resistance to conventional attacks.

Figure 8: Four medical images and extracted watermarking images with median filtering attack intensity of 7 × 7
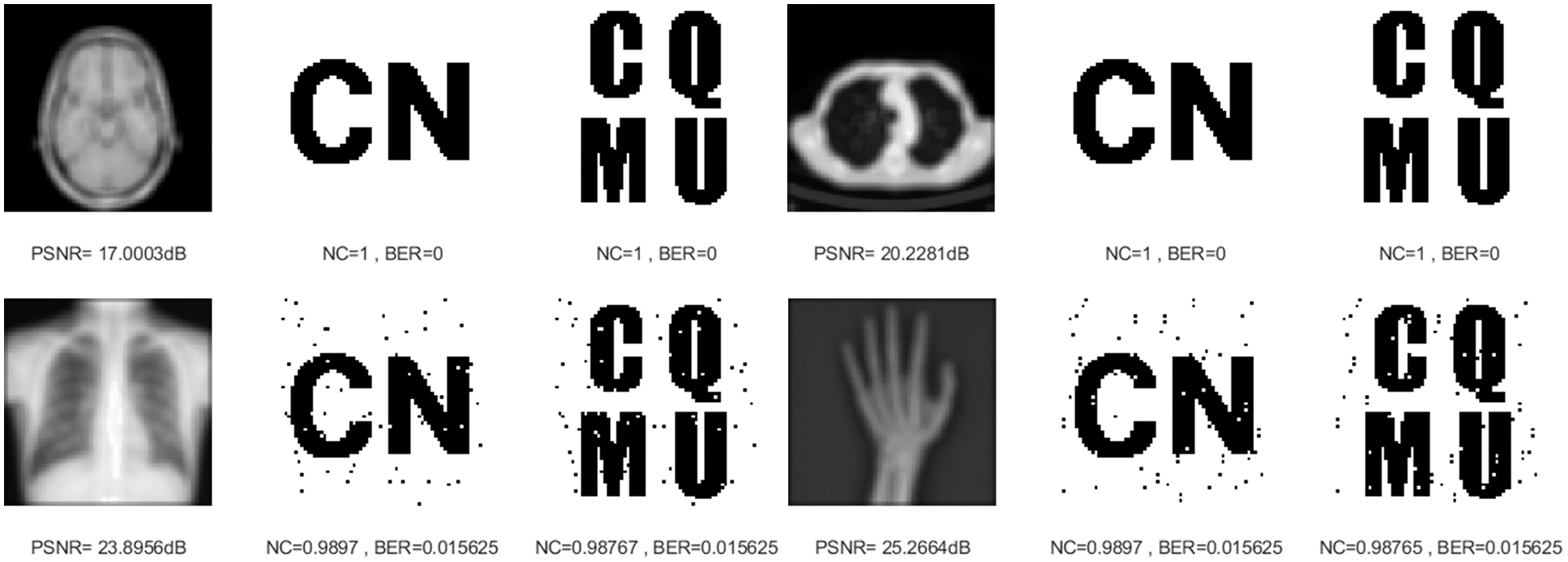
Figure 9: Four medical images and extracted watermarking images with average filtering attack intensity of 7 × 7

Figure 10: Four medical images and extracted watermarking images with Gaussian filtering attack intensity of 7 × 3
Table 3 shows the results of our proposed method against geometric attacks. As the scaling attack intensity increases, the NC and PSNR value increases gradually. Besides, no matter what the scaling factor, the NC values of the brain image and lung image are always equal to 1.0 and the BER values are almost always 0. Fig. 11 shows the experimental results when the scaling factors are 0.5 and 2. This shows that the proposed algorithm has strong robustness under scaling attacks.
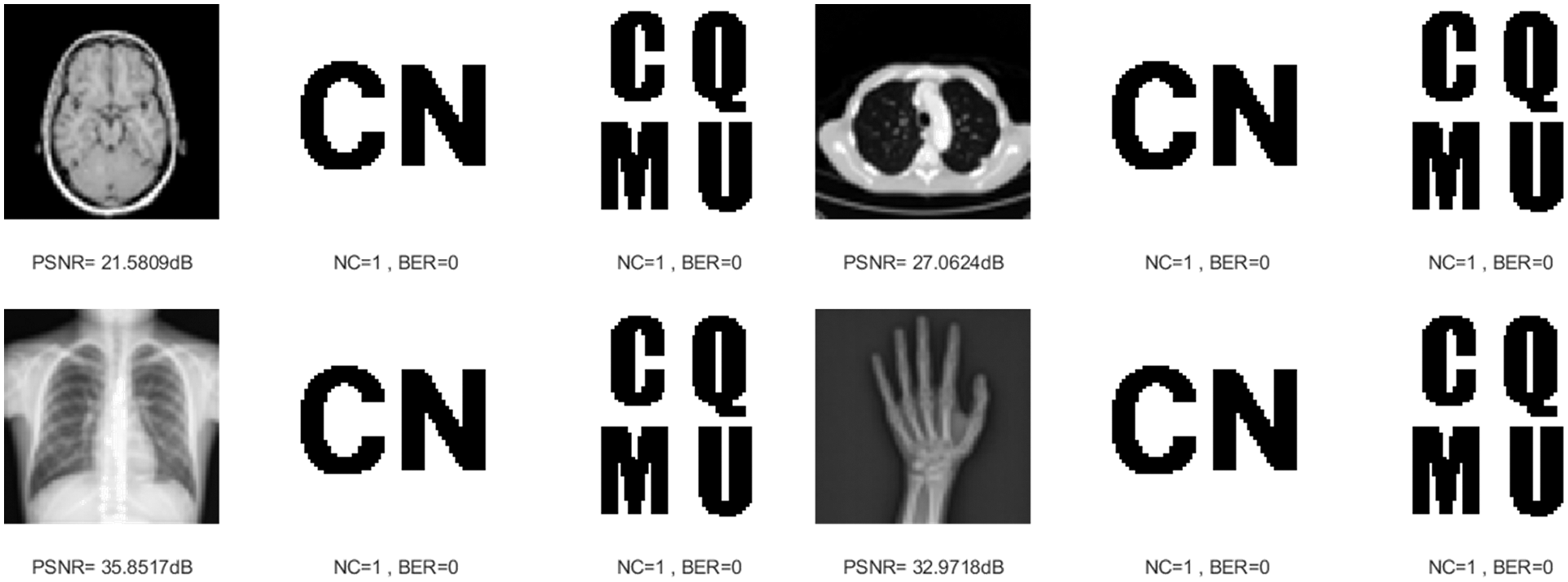
Figure 11: Four medical images and extracted watermarking images with scaling attack intensity of 0.5 and 2
For medical images such as the chest radiograph, when subjected to a slightly stronger cropping attack, the pixels of the extracted watermarking image are somewhat distorted, but the average value of NC is still higher than 0.86. Fig. 12 shows the experimental results after cropping 15% along the X-axis direction. Their NC values are greater than 0.88. It shows that this proposed algorithm can effectively resist cropping attacks.
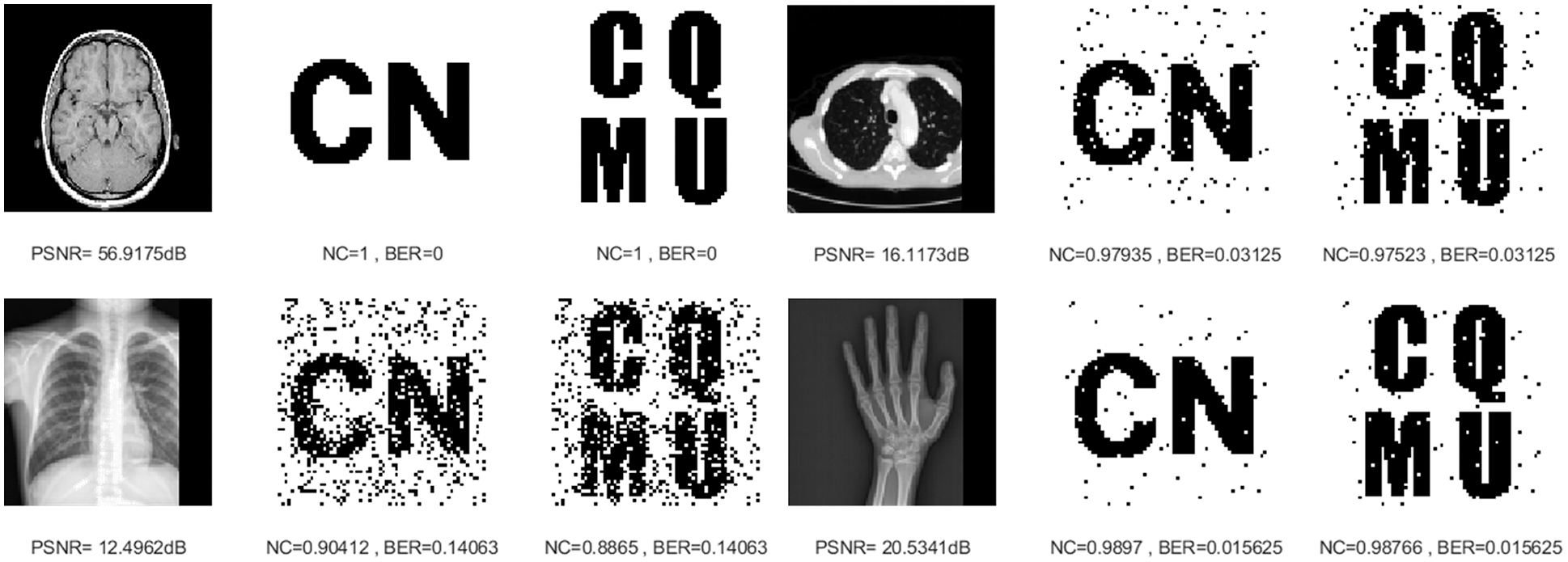
Figure 12: Four medical images and extracted watermarking images with cropping attack intensity of 15%
Image rotation is a common geometric attack that changes the position of image pixels. After rotating 10 degrees counterclockwise, as shown in Fig. 13, the smallest NC value is 0.8993. The rotation attack experimental data in Table 3 further verify that the proposed algorithm has a strong ability to resist counterclockwise rotation attacks.
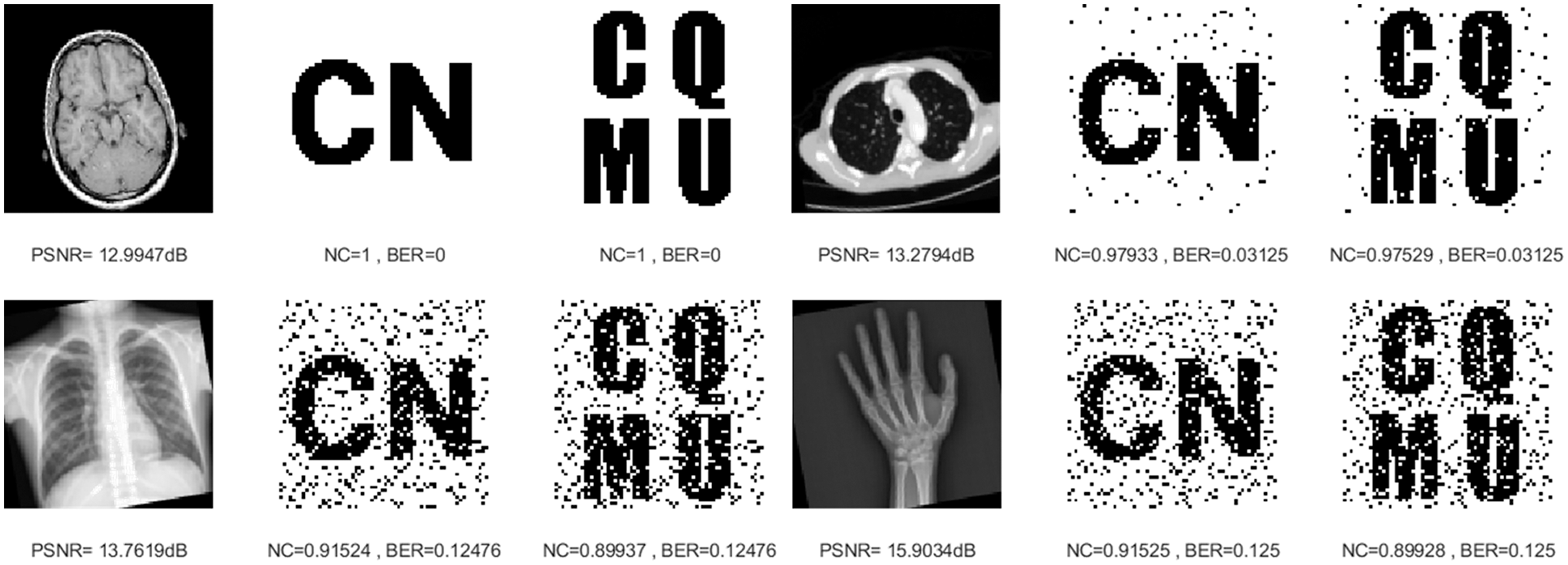
Figure 13: Four medical images and extracted watermarking images with rotation attack intensity of 10°
In the process of downward translation, the PSNR obtained from the original medical image decreases gradually, but the NC values are high enough and the BER values are also close to 0. In Fig. 14, when the translation attack intensity is 5%, their NC values are much greater than 0.84. Therefore, for geometric attacks (scaling, cropping, rotation and translation downward), this proposed algorithm also shows attractive robustness.
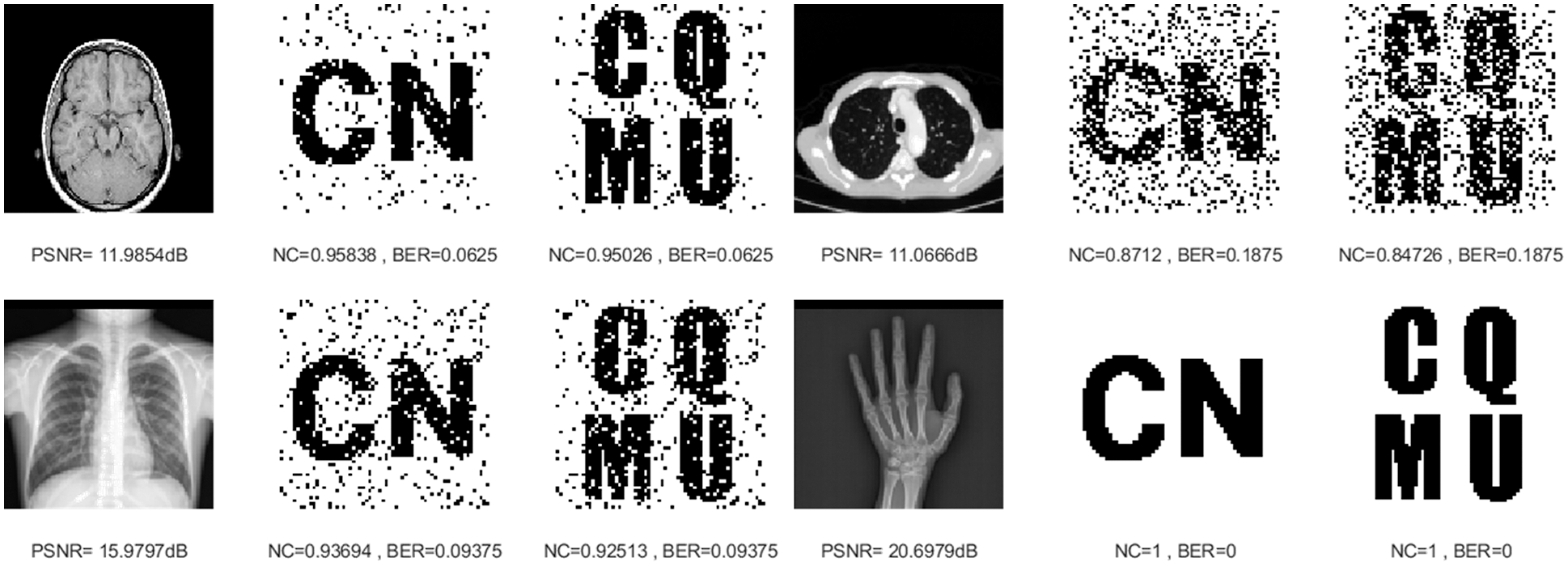
Figure 14: Four medical images and extracted watermarking images with translation attack intensity of 5%
Six combined attacks are selected in this paper. The first is the combination of two conventional attacks. The first kind is the Gaussian noise attack on the medical image and then the median filtering attack, and the second is the JPEG compression attack on the medical image and then the median filtering attack. As can be seen in Table 4, under both attacks, despite the gradually decreasing PSNR values of the four medical images, their NC values are consistently greater than 0.96. From Figs. 15 and 16, the NC values of the brain image and lung image are maintained at 1 under both attacks. In addition, the overall BER values are below 0.05 for both attacks.
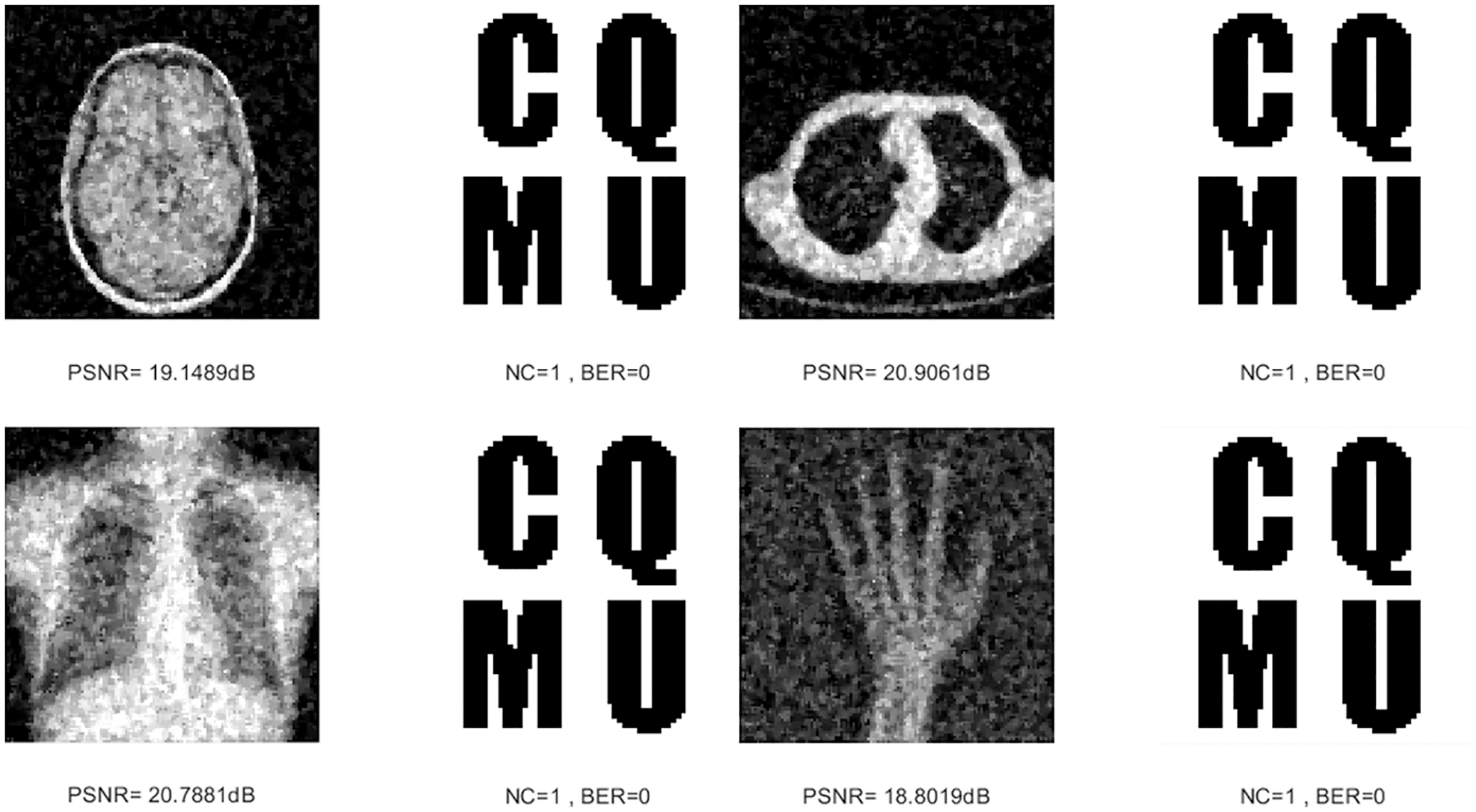
Figure 15: Four medical images and extracted watermarking images with Gaussian noise attack intensity of 5% and median filtering attack intensity of 3 × 3

Figure 16: Four medical images and extracted watermarking images with JPEG compression attack intensity of 5% and median filtering attack intensity of 3 × 3
The second major category is the combination of conventional attacks and geometric attacks. The first one cuts the image along the X-axis and then performs the median filtering attack. Compared with the four images, the NC values of the chest image are slightly lower but still above 0.85, and the NC values of the other three images remain above 0.9. The second attack is the JPEG compression attack on the image and then the scaling attack. In Figs. 17 and 18, when the medical images become very blurred and distorted, the NC values of the four images are greater than 0.96, and the BER values are also close to 0.

Figure 17: Four medical images and extracted watermarking images with cropping attack intensity of 5% and median filtering attack intensity of 3 × 3

Figure 18: Four medical images and extracted watermarking images with JPEG compression attack intensity of 5% and scaling attack intensity of 0.125
The third category of attacks is two geometric attacks on images, namely, scaling attack combined with cropping attack, and rotation attack combined with scaling attack. From the data in Table 4, only the chest image has the lowest NC value of 0.7277 under both attacks, while the other three images have NC values above 0.83 under both attacks. In Figs. 19 and 20, under both attacks, it is obvious that even if the image distortion is serious, the extracted watermarking image is very clearly visible. From the overall results of these three types of attacks, the proposed algorithm can effectively resist the attacks of different combinations.

Figure 19: Four medical images and extracted watermarking images with scaling attack intensity of 0.125 and cropping attack intensity of 5%

Figure 20: Four medical images and extracted watermarking images with rotation attack intensity of 3° and scaling attack intensity of 0.125
4.3 Comparisons with Other Algorithms
To verify the advantage of our proposed algorithm, we used the same experiment condition to compare it with other representative works [23,28,30,31]. In the contrast experiment, the 128 × 128 brain image shown Fig. 3a is selected as the original medical image, and the watermarking image is shown in Fig. 3e. The specific experimental results are shown in Tables 5–9.





When carrying out conventional attacks, as shown in Tables 5 and 6, in the attack of Gaussian noise, the NC value of both algorithm [30] and algorithm [31] is lower than 0.7. According to the JPEG compression attack, the NC value of algorithm [30] appears below the value of 0.6. Under the median filtering attack, except that the value of algorithm [30] is lower than 0.8, the NC value of the other algorithms is greater than 0.9. Only in the algorithm [23,28] and the proposed algorithm, the NC value is always above 0.9 under different degrees of three attacks, and the NC value of the proposed algorithm is always equal to 1. Moreover, the BER values of the algorithm under different conventional attack intensities are equal to 0, while other algorithms have BER values greater than 0, or even have values greater than 0.5. So far, it can be seen that under conventional attack, the proposed algorithm has stronger stability and robustness than the compared algorithms [23,28,30,31].
As shown on the right in Table 7, when faced with the increased intensity of different geometric attacks, the NC values of the algorithms showed in [23,28,30,31] all decrease, while the proposed algorithm is almost maintained at 1.0 in terms of NC metric. When facing different degrees of translation attacks, the NC values of the algorithms in [28,30,31] are lower than 0.9, and the algorithm in [30] is even lower than 0.8, but the proposed algorithm and the algorithm [23] are still above 0.9. Under the geometric attack, in Table 8, the largest BER value of the proposed algorithm is 0.1094, and the remaining BER values are equal to 0, which are much smaller than the BER values of other algorithms. From these observations, we can obviously see that the proposed algorithm is more robust when it is subjected to geometric attack compared with the other algorithms [23,28,30,31].
To more comprehensively detect the algorithm’s performance, under the same experimental environment, the computing time of the proposed algorithm and the literature [23,28,30,31] for comparison, the average time for the 20 runs is displayed in Table 9. Table 9 shows that the computing time of the proposed algorithm to construct zero-watermarking is low relative to the literature [23,28,30,31]. This is because the IWT has high computational efficiency, and the computational complexity of the Schur decomposition is lower than that of the SVD in [30,31], which effectively enhances the algorithm’s execution efficiency.
Aiming to protect the security of the medical image and not damage original information, we have proposed a new zero-watermarking algorithm in this work. Specifically, we used the IWT to extract low-frequency information from the original medical image, which was then divided into blocks by the Schur decomposition. After that, we constructed the feature matrix according to the relation between image block energy. Meanwhile, we encrypted the watermarking information using logistic position scrambling. Finally, zero-watermarking is generated via the XOR operation between the scrambled watermarking information and the feature matrix. We compared our algorithm with other representative works under a series of conventional attacks and geometric attacks in the experiment. Experimental results show that the proposed algorithm could improve the robustness of the medical image zero-watermarking, especially for the high-intensity of conventional attacks and geometric attacks. This algorithm can efficiently ensure the safety and privacy of patients and the confidentiality and reliability of medical images. However, this algorithm in this paper is aimed at 2D medical images. It has not been applied to 3D medical images, our future work will consider applying the proposed algorithm to the protection of 3D medical images, and we will attempt to design a robust zero-watermarking algorithm that can protect 2D and 3D medical images.
Funding Statement: This work was supported in part by the Hainan Provincial Natural Science Foundation of China (No. 620MS067), the Intelligent Medical Project of Chongqing Medical University (ZHYXQNRC202101), and the Student Scientific Research and Innovation Experiment Project of the Medical Information College of Chongqing Medical University (No. 2020C006).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. Xun, Y., Bouguettaya, A., Georgakopoulos, D., Song, A., Willemson, J. (2016). Privacy protection for wireless medical sensor data. IEEE Transactions on Dependable and Secure Computing, 13(3), 369–380. DOI 10.1109/TDSC.2015.2406699. [Google Scholar] [CrossRef]
2. Rault, T., Bouabdallah, A., Challal, Y. (2014). Energy efficiency in wireless sensor networks: A top-down survey. Computer Networks, 67, 104–122. DOI 10.1016/j.comnet.2014.03.027. [Google Scholar] [CrossRef]
3. Qasim, A. F., Meziane, F., Aspin, R. (2018). Digital watermarking: Applicability for developing trust in medical imaging workflows state of the art review. Computer Science Review, 27, 45–60. DOI 10.1016/j.cosrev.2017.11.003. [Google Scholar] [CrossRef]
4. Makbol, N. M., Khoo, B. E., Rassem, T. H. (2015). Block-based discrete wavelet transform-singular value decomposition image watermarking scheme using human visual system characteristics. IET Image Processing, 10(1), 34–52. DOI 10.1049/iet-ipr.2014.0965. [Google Scholar] [CrossRef]
5. Hussain, M., Wahab, A. W. A., Idris, B. Y. I., Ho, A. T. S., Jung, K. H. (2018). Image steganography in spatial domain: A survey. Signal Processing: Image Communication, 65, 46–66. DOI 10.1016/j.image.2018.03.012. [Google Scholar] [CrossRef]
6. Xia, Z., Wang, X., Sun, X., Liu, Q., Xiong, N. (2016). Steganalysis of LSB matching using differences between nonadjacent pixels. Multimedia Tools and Applications, 75(4), 1947–1962. DOI 10.1007/s11042-014-2381-8. [Google Scholar] [CrossRef]
7. Wang, G., Rao, N. N. (2005). A fragile watermarking scheme for medical image. IEEE Engineering in Medicine and Biology 27th Annual Conference, pp. 3406–3409. Shanghai, China. [Google Scholar]
8. Singh, S. P., Bhatnagar, G. (2018). A new robust watermarking system in integer DCT domain. Journal of Visual Communication and Image Representation, 53, 86–101. DOI 10.1016/j.jvcir.2018.03.006. [Google Scholar] [CrossRef]
9. Atawneh, S., Almomani, A., Bazar, H. A., Sumari, P., Gupta, B. (2017). Secure and imperceptible digital image steganographic algorithm based on diamond encoding in DWT domain. Multimedia Tools and Applications, 76(18), 18451–18472. DOI 10.1007/s11042-016-3930-0. [Google Scholar] [CrossRef]
10. Hamidi, M., Haziti, M. E., Cherifi, H., Hassouni, M. E. (2018). Hybrid blind robust image watermarking technique based on DFT-DCT and Arnold transform. Multimedia Tools and Applications, 77(20), 27181–27214. DOI 10.1007/s11042-018-5913-9. [Google Scholar] [CrossRef]
11. Hosny, K. M., Darwish, M. M., Li, K., Salah, A. (2018). Parallel multi-core CPU and GPU for fast and robust medical image watermarking. IEEE Access, 6, 77212–77225. DOI 10.1109/ACCESS.2018.2879919. [Google Scholar] [CrossRef]
12. Hosny, K. M., Darwish, M. M., Fouda, M. M. (2021). Robust color images watermarking using new fractionalorder exponent moments. IEEE Access, 9, 47425–47435. DOI 10.1109/ACCESS.2021.3068211. [Google Scholar] [CrossRef]
13. Al-Haj, A., Mohammad, A., Amer, A. (2017). Crypto-watermarking of transmitted medical images. Journal of Digital Imaging, 30(1), 26–38. DOI 10.1007/s10278-016-9901-1. [Google Scholar] [CrossRef]
14. Khor, H. L., Liew, S. C., Zain, J. M. (2017). Region of interest-based tamper detection and lossless recovery watermarking scheme (ROI-DR) on ultrasound medical images. Journal of Digital Imaging, 30(3), 328–349. DOI 10.1007/s10278-016-9930-9. [Google Scholar] [CrossRef]
15. Gao, G., Wan, X., Yao, S., Cui, Z., Zhou, C. et al. (2017). Reversible data hiding with contrast enhancement and tamper localization for medical images. Information Sciences, 385, 250–265. DOI 10.1016/j.ins.2017.01.009. [Google Scholar] [CrossRef]
16. Priyanka, S., Maheshkar, S. (2017). Region-based hybrid medical image watermarking for secure telemedicine applications. Multimedia Tools and Applications, 76(3), 3617–3647. DOI 10.1007/s11042-016-3913-1. [Google Scholar] [CrossRef]
17. Wen, Q., Sun, T., Wang, S. (2003). Concept and application of zero-watermark. ACTA Electonica Sinica, 31(2), 214–216. [Google Scholar]
18. Zear, A., Singh, A. K., Kumar, P. (2018). A proposed secure multiple watermarking technique based on dwt, dct and svd for application in medicine. Multimedia Tools and Applications, 77(4), 4863–4882. DOI 10.1007/s11042-016-3862-8. [Google Scholar] [CrossRef]
19. Liu, J., Li, J., Ma, J., Sadiq, N., Bhatti, U. A. et al. (2019). A robust multi-watermarking algorithm for medical images based on DTCWT-DCT and henon map. Applied Sciences, 9(4), 700. DOI 10.3390/app9040700. [Google Scholar] [CrossRef]
20. Hu, K., Wang, X., Hu, J., Wang, H., Qin, H. (2021). A novel robust zero-watermarking algorithm for medical images. The Visual Computer, 37(9), 2841–2853. DOI 10.1007/s00371-021-02168-5. [Google Scholar] [CrossRef]
21. Xia, Z., Wang, X., Wang, C., Wang, C., Ma, B. et al. (2022). A robust zero-watermarking algorithm for lossless copyright protection of medical images. Applied Intelligence, 52(1), 607–621. DOI 10.1007/s10489-021-02476-2. [Google Scholar] [CrossRef]
22. Dai, Z., Lian, C., He, Z., Jiang, H., Wang, Y. (2022). A novel hybrid reversible-zero watermarking scheme to protect medical image. IEEE Access, 10, 58005–58016. DOI 10.1109/ACCESS.2022.3170030. [Google Scholar] [CrossRef]
23. Huang, T., Xu, J., Yang, Y., Han, B. (2022). Robust zero-watermarking algorithm for medical images using double-tree complex wavelet transform and Hessenberg decomposition. Mathematics, 10(7), 1–19. DOI 10.3390/math10071154. [Google Scholar] [CrossRef]
24. Sweldens, W. (1996). The lifting scheme: A custom-design construction of biorthogonal wavelets. Applied & Computational Harmonic Analysis, 3(2), 186–200. DOI 10.1006/acha.1996.0015. [Google Scholar] [CrossRef]
25. Calderbank, A. R., Daubechies, I., Sweldens, W., Yeo, B. L. (1998). Wavelet transforms that map integers to integers. Applied and Computational Harmonic Analysis, 5(3), 332–369. DOI 10.1006/acha.1997.0238. [Google Scholar] [CrossRef]
26. Liu, W., Sun, S., Qu, H. (2019). Fast zero-watermarking algorithm based on Schur decomposition. Journal of Frontiers of Computer Science & Technology, 13(3), 494–504. DOI 10.3778/j.issn.1673-9418.1712040. [Google Scholar] [CrossRef]
27. Zermi, N., Khaldi, A., Kafi, M. R., Kahlessenane, F., Euschi, S. (2021). A lossless DWT-SVD domain watermarking for medical information security. Multimedia Tools and Applications, 80(16), 24823–24841. DOI 10.1007/s11042-021-10712-7. [Google Scholar] [CrossRef]
28. Li, W., Amandeep, K. X., Deepak, D., Sanjeev, K. (2019). Robust zero-watermarking algorithm based on chaotic and block energy relationship. Microelectronics and Computer, 36(11), 30–36. DOI 10.19304/j.cnki.issn1000-7180.2019.11.007. [Google Scholar] [CrossRef]
29. Durafe, A., Patidar, V. (2022). Development and analysis of IWT-SVD and DWT-SVD steganography using fractal cover. Journal of King Saud University-Computer and Information Sciences, 34(7), 4483–4498. DOI 10.1016/j.jksuci.2020.10.008. [Google Scholar] [CrossRef]
30. Rani, A., Bhullar, A. K., Dangwal, D., Kumar, S. (2015). A zero-watermarking scheme using discrete wavelet transform. Procedia Computer Science, 70, 603–609. DOI 10.1016/j.procs.2015.10.046. [Google Scholar] [CrossRef]
31. Zeng, F., Zhou, A. (2008). Image zero-watermarking algorithm based on contourlet transform and singular value decomposition. Journal of Computer Applications, 28(8), 2033–2035. DOI 10.3724/SP.J.1087.2008.02033. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools