 Open Access
Open Access
ARTICLE
A Novel RFID Localization Approach to Smart Self-Service Borrowing and Returning System
1
Fudan University, Shanghai, 200433, China
2
Commonwealth Scientific and Industrial Research Organization, Sydney, 2122, Australia
3
Zhengzhou University of Industrial Technology, Zhengzhou, 451100, China
* Corresponding Authors: Bochun Wu. Email: ; Yi Gong. Email:
(This article belongs to the Special Issue: Models of Computation: Specification, Implementation and Challenges)
Computer Modeling in Engineering & Sciences 2023, 135(1), 527-538. https://doi.org/10.32604/cmes.2022.022298
Received 09 March 2022; Accepted 25 May 2022; Issue published 29 September 2022
Abstract
The misreading problem of a passive ultra-high-frequency (UHF) radio frequency identification (RFID) tag is a frequent problem arising in the field of librarianship. Unfortunately, existing solutions are something inefficient, e.g., extra resource requirement, inaccuracy, and empiricism. To this end, under comprehensive analysis on the passive UHF RFID application in the librarianship scenario, a novel and judicious approach based on RFID localization is proposed to address such a misreading problem. Extensive simulation results show that the proposed approach can outperform the existing ones and can be an attractive candidate in practice.Keywords
Driven by the great advances of integrated circuits (IC) and wireless communications [1], the applications of Internet-of-Things (IoT) have been infiltrated to each realm of the society [2], e.g., environment surveillance, smart home, remote health care, and smart library. Thousands of devices equipped with sensing modules (e.g., radio frequency identification (RFID)) have been interconnected with each other [3–5]. Specifically, as a critical IoT technology, RFID has been widely adopted and deployed in many fields, e.g., access control, traffic control, retail business, and librarianship, due to its convenience in non-contacted bidirectional data communication [6–8]. As a matter of fact, RFID technology has been applied in librarianship to improve the efficiency of book circulation since the 1990s. Until now, libraries worldwide have typically deployed ultra-high-frequency (UHF) RFID technology to manage books instead of the manual way, which is inefficient and error-prone.
Despite the great convenience of UHF RFID, there still exists some fatal failure in the book circulations of libraries, and the typical ones are concentrated in the tag misreading of the UHF RFID self-service borrowing and returning system (RFID-SBRS). According to [9,10], the detection radius of UHF RFID can be up to 10 m. While this extends the effective operation range of the RFID systems, it is the key cause of the misreading problem encountered by libraries. Although the transmitting power of the UHF RFID readers has been restricted to alleviate the misreading or interference from the other irrelevant passive UHF RFID tags, there inevitably exists quite a few cases caused by tag misreading, especially taking the near-field and far-field effect into consideration. To tackle this, an effective way is urgently needed.
1.1 Basic Framework of UHF RFID-SBRS
First of all, it will be necessary for us to introduce the basic framework of UHF RFID-SBRS briefly. A typical UHF RFID-SBRS is a classic client-server (CS) architecture, whose components mainly include three kinds: the tag, the terminal, and the server [11–14].
Tag: An UHF RFID tag is a physical data carrier for storing the data information of the identified object, and there are two major types of UHF RFID tags: active tags and passive tags. The active tags are generally equipped with built-in batteries to supply the power for transmitting signals, while the passive tags are battery-free, and the power for transmitting signals depends on the electromagnetic induction power transmitted from UHF RFID readers.
Terminal: An UHF RFID-SBRS terminal is equipped with an UHF RFID reader, middleware, operating system, and corresponding RFID application software. The UHF RFID reader can transmit reading signals, receive the backscatter from the passive UHF RFID tag, and demodulate the specific data. The middleware is an interface including drives of hardware, data reading and writing protocol, etc. It can be seen as a bridge for data exchange between RFID software and hardware. The operating system is the software operating on a higher level than middleware and can be seen as a container for running RFID application software. The RFID application software is the special software integrated with all kinds of book-related transactions, e.g., user identity authority service, books information query service, and books borrowing and returning service, etc.
Server: An RFID-SBRS server is a system including both physical hardware and software, and can be used to process the request from the UHF RFID-SBRS terminal for book-related transactions, e.g., process the corresponding borrowing transactions based on the general data interface and integrated library system.
The identification procedure of a general UHF RFID system is listed as follows:
• The UHF RFID reader starts the identification process by sending out radio frequency signals via antennas and keeping the detection in the meantime.
• Whenever a passive UHF RFID tag is in the scope of action of the radio signal by the RFID reader mentioned above, the passive UHF RIFD tag is activated, then powered by the radio frequency signal.
• The stored information is coded, modulated, and then transmitted via embedded antennas by resorting to the electromagnetic induction power collected from the UHF RFID reader.
• The signal transmitted by the passive UHF RFID tag is then received, demodulated, and decoded at the UHF RFID reader side.
• After a series of data format transformations, the output data is delivered to the central control system and further processed.
• The legitimacy of data is double-checked in the central control system. According to the specific instructions embodied in the data, the verified data is then used to control the corresponding transactions.
Specifically, the RFID tag misreading problem mainly relates to the first three steps in the above list, and the details of such failure are discussed in the next section.
1.2 Motivation and Contributions
This paper is motivated to address the misreading problem of a passive UHF RFID tag generally adopted by libraries. A new approach based on RFID localization technology is proposed to determine an adequate threshold to differentiate the misread books from the intended books, specifically, the misread books considered in this paper are referred to the ones in the reading area of UHF RFID reader, but not in the predefined threshold. Given the considerable RFID localization accuracy, the misreading problem of a passive UHF RFID tag can be resolved.
The key contributions of this paper are summarized, as follows:
• A new RFID localization-based solution is proposed to resolve the book misreading failures in libraries, after the cause of failures is comprehensively analyzed.
• The proposed solution can be technically readily and cost-effectively deployed with simple configurations. There is no need for additional hardware or firmware.
• The proposed approach can achieve significant improvements in accuracy, availability, and robustness over existing solutions.
The remainder of this paper is organized as follows. In Section 2, we analyze the misreading failure problem of passive UHF RFID tags, and overview existing solutions and their limitations. In Section 3, we propose a new RFID localization-based approach and provide the detailed procedure of the approach. We conduct extensive simulations to validate the accuracy, availability, and robustness of the approach in Section 4, followed by conclusions in Section 5.
Let us consider a typical scenario. A borrower wants to use the RFID-SBRS to borrow several books and waits in line for his turn. After a long-time waiting, he takes his turn to use RFID-SBRS. He logs in the system to obtain authorization for borrowing service with proper username and password, puts the wanted books in the specific places for RFID tags detection, and then chooses the number of wanted books via the interactive interface. The RFID reader of RFID-SBRS will immediately start the detection process and return a long list of book names for confirmation via the interactive interface. The borrower should carefully check the feedback list at this time. However, the borrower may restrict the number of lines with the number of wanted books and confirm the feedback for efficiency due to long waiting time or the urged pressure from the next borrower. Unfortunately, the RFID tags of the wanted books cannot be guaranteed to be valid all the time. The failures of RFID tags can be easily occurred. A considerable number of funds have been granted to purchase the new tags for the failed/faulted RFID tags in the field of library. It is worth noting that it is not realistic to recover the functionality of faulted RFID tags when considering the expense. Under the practical assumption of considered scenario, we thus unify the failed and faulted tags as the failure tags. In such a case, some of the books he/she just confirms to borrow are not the required ones but the misread ones from the other borrowers, bringing unnecessary troubles to multiple borrowers.
How to efficiently identify the misread books and remind the borrower of the unwanted books in advance is the key to avoid the embarrassing failure problem, e.g., give some tips when the misread books are identified or highlight the misread book names in the feedback list of RFID-SBRS.
2.2 General Solutions Adopted in Librarianship
The technology of tuning coverage distance of the RFID reader according to the actual scenario has been adopted in the field of library. The RFID project engineer has to make subjective decisions to fetch a suitable coverage distance of the deployed RFID reader. Such a case requires an RFID project engineer who has a high comprehensive quality, as well as the upcoming time and economic cost. Furthermore, limited coverage may cause an undesirable effect on the normal function of the RFID reader, e.g., both the size and the material of books have a deep effect on the reliability of the RFID tag [15]. The deeply affixed passive tags cannot be generally detected for too low transmitting power. In contrast, extensive coverage may cause more misreading on the books. One natural idea for tackling this troublesome thing is to locate all the detected books efficiently, and the books far away from RFID-SBRS can be seen as the unrelated books, and vice versa.
2.3 Further Discussion on Direct Solutions
One straightforward and plausible way is to utilize the localization of the active RFID tags to distinguish the wanted books from the misread ones based on the received signal strength (RSS). Typically, according to the classical path loss model, the attenuation of the signal propagated from an active RFID tag is a function of the distance between the RFID reader and the RFID tag, and the distance estimation can thus be translated into the power difference between the RFID reader and the active RFID tag. The transmitting power can be obtained from the specification of the active RFID tag, and the RSS can be directly obtained at the reader side. Yet, the cost of an active RFID tag can be comparatively high, and the size cannot be relatively small with the built-in battery, which consequently limits the life cycle. It is thus impractical for library to deploy thousands of active RFID tags on books. In reality, almost without exception, the RFID tags adopted by libraries to manage books are passive RFID tags for their superior characteristic on low cost and small size [16–18].
3 Approach to Failure Prevention
How to efficiently locate the misread books solely based on existing resources and circumstances of library becomes the key for solving the misreading problem. To this end, inspired by the recent work on RFID indoor localization technology, we develop a novel passive UHF RFID tag localization approach to overcome the failure of books misreading [19–21]. With reasonably good accuracy, any defined threshold can be set according to the actual needs for identifying the right books for the borrower, and the failures on misreading can thus be alleviated.
The main principle of the proposed approach is based on two assumptions:
• The RSS at the RFID reader is a function of the distance between the RFID reader and the passive RFID tag;
• The environment around RFID-SBRS is comparatively static or conforms to the statistically regular environment.
Let us first discuss the rationality of two assumptions. For the first assumption, the communication between the RFID reader and the passive RFID tag is duplex, which includes the signal transmitted from the RFID reader to the passive RFID tag and the backscatter from an activated passive RFID tag to the RFID reader. The channels in both directions are assumed to follow the well-known path loss model. By resorting to the path loss model, it is thus rational to make the assumptions that the distance between the RFID reader and the passive RFID tag has a functional relationship with the RSS at the RFID reader. Based on this assumption, the longer the distance between the RFID reader and the RFID tag is, the more the path loss will be, and the less the RSS received by the RFID reader will be. For the second assumption, the RFID-SBRS is generally placed indoors (e.g., the reading room and the comparatively static environment). In such a case, the effect of multi-path propagation and the interference are tiny. The channel model can thus maintain a steadily statistical state, e.g., the free-space path loss model.
Based on the two assumptions above, we further propose an approach for identifying the justifiably needed books for the borrower.
As shown in Fig. 1, the workplace of RFID-SBRS is a semi-circle area centered at RFID-SBRS with the radius of the semi-circle area denoted as R. The area is divided into
where
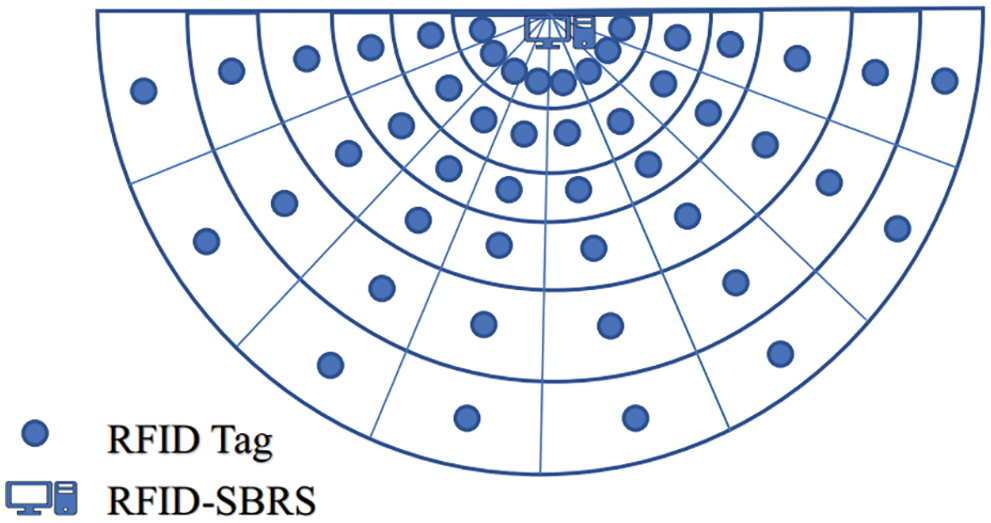
Figure 1: RFID-SBRS scheme
Based on the model, the procedure of the proposed approach mainly includes two parts: the offline part and the online part, whose details are respectively listed below.
• Confirm the scope of the testing area. The test area is centered on the RFID-SBRS with an RFID reader equipped, with the maximum read range as the test radius.
• Divide the test area into a set of grids. The number of the divided grids affects the accuracy of RFID tag identification. Typically, the more grids divided, the more accurate the tag identification can be. An on-site measurement can directly obtain a distance from each center of the grid to the RFID reader.
• Set up a fingerprint set of the environment for RFID tag. In detail, in each center of the divided grids, to deploy a test RFID tag, take 100 times measurements of RSS at RFID reader, and take an average of the measurements as the final measured RSS for this grid. Combining the corresponding measured RSS with the distance be-tween each center of grid and RFID reader, a bijection relationship can be established, a fingerprint set of the test area with RSS as key, and the other data including distances and coordinates value is consequently set up [22,23].
• Define a suitable distance threshold for distinguishing the misread books from the truly needed books, after the fingerprint set has been set up.
• Store all the parameters, including the fingerprint set and the threshold parameter, into the local database of the RFID-SBRS terminal.
• The borrower who carries wanted books equipped with RFID tags enters into the test area of the RFID-SBRS.
• The borrower can confirm the number of the books, the RSS of related books can be obtained at the RFID reader.
• The measured RSS is compared with the aforementioned RSS fingerprint database built in the offline part. The K closest key-value pairs with measured RSS can be chosen from the fingerprint database.
• For each detected book, take a coordinates average of the chosen as the final pre-dicted localization, and compare the localization with the threshold parameter. Any RFID tag exceeding the threshold parameter will be judged as the misread RFID tags. The detection of multiple tags can be generalized to differentiate the tags if the pairwise distance is longer than the resolution of the proposed approach, as discussed in Section 4. The predicted localization can be given by
where x is the horizontal coordinate and y is the vertical coordinate, and
• The location information and the preset book ID information of each detected book are encapsulated into a data pair, inserted into the raw list of detected books, and sent to the RFID-SBRS server for further processing.
• The RFID-SBRS server parses the raw list sent from the RFID-SBRS terminal, and processes the list of tags, e.g., setting the status field of misread tags bonded with specific ID to “1”. Then, the processed list is returned to the RFID-SBRS terminal.
• The RFID-SBRS terminal filters out all the misread books in the feedback list of book names, or highlight the misread books in the feedback list, e.g., all the mis-read book names are highlighted with red color, in contrast to the black color for wanted books.
We conduct simulations using synthetic data generated according to the path loss model in [25]. The RSS at RFID reader is assumed to be corrupted by multiplicative noise for robustness, as given by
where
4.1 Realization of the Proposed Approach
As shown in Fig. 2, we consider a realization of the scenario as discussed in Section 3, where parameters are set up as follows. The radius of the semi-circle area
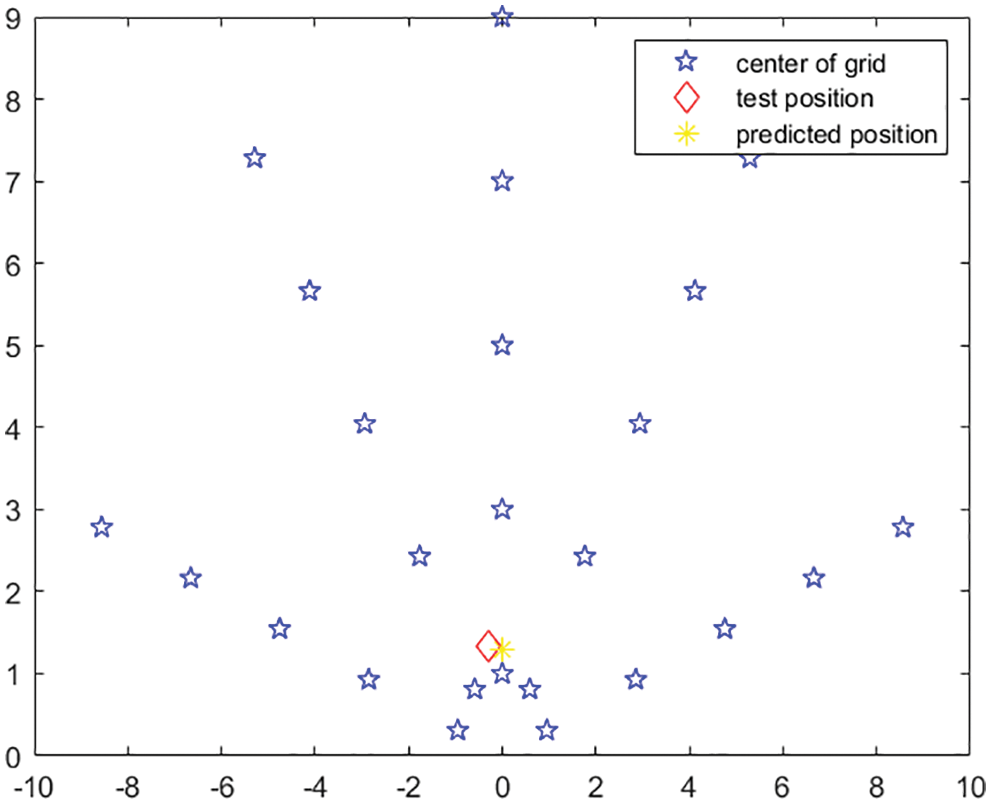
Figure 2: Realization for RFID tag localization using the proposed approach
We consider two metrics to evaluate the proposed approach, as shown in Figs. 3 and 4. All the parameters are the same as in the previous subsection, except
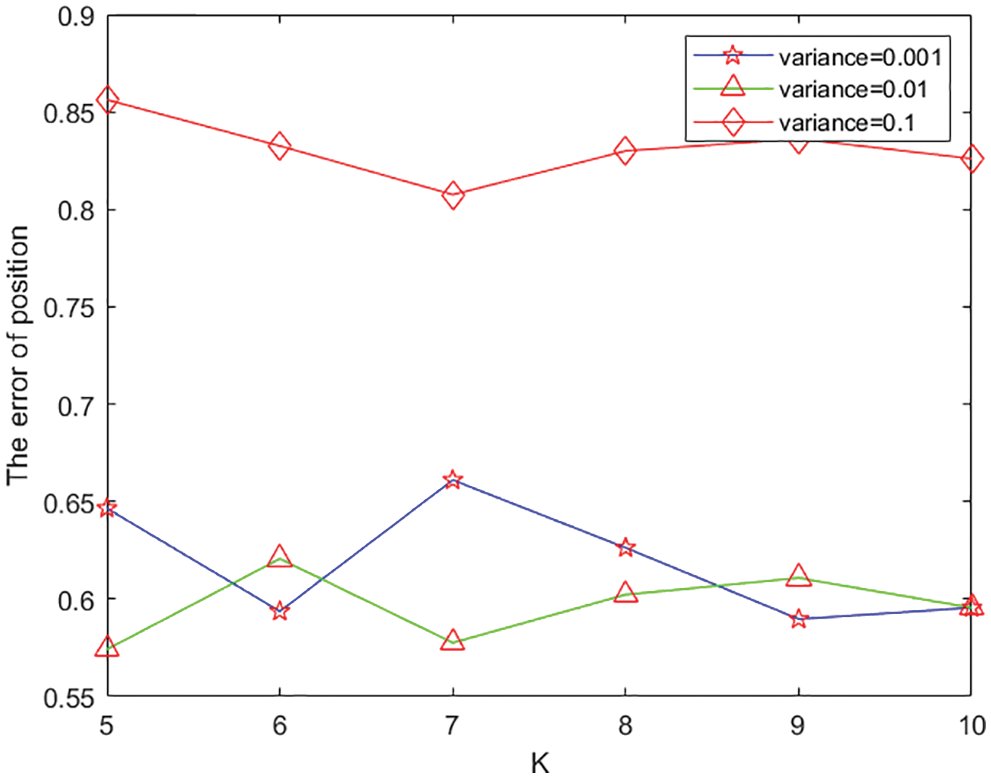
Figure 3: Impact on error of position
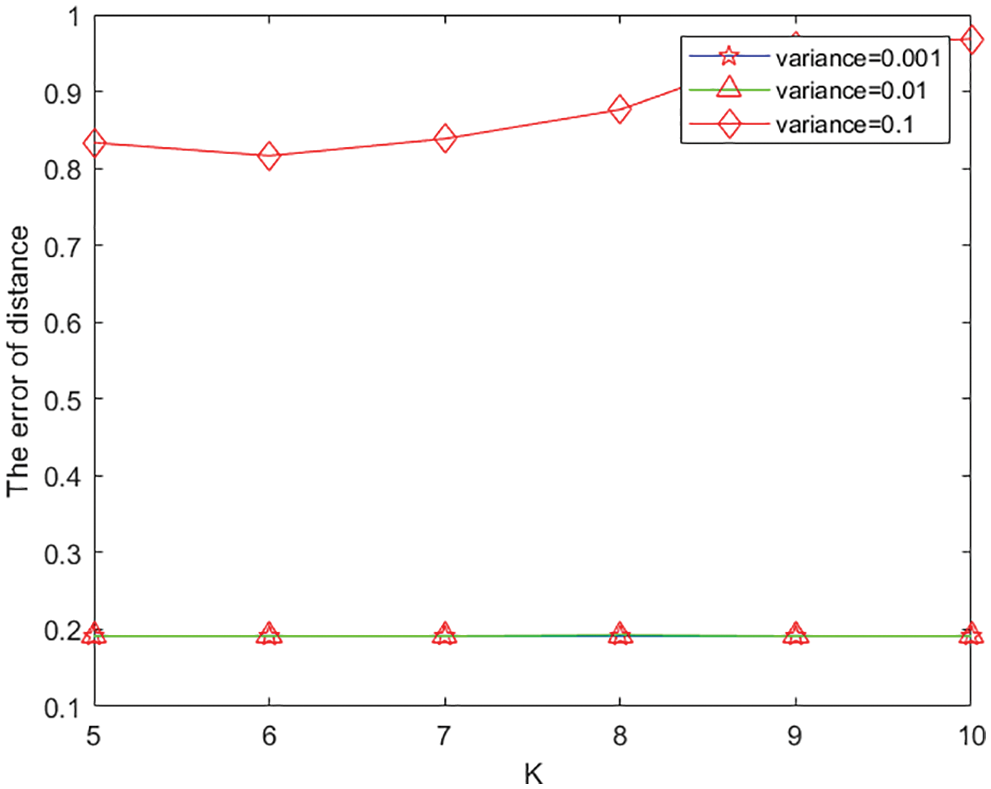
Figure 4: Impact on error of distance
4.3 Discussion of Practical Deployment
We further consider the impact of the scale of grids. All the parameters in Fig. 5 are consistent with the parameters in Fig. 2 except the variation of the scale of grids. Without loss of generality, the number of the divided angels is equal to the number of the divided radius under each realization, and every point of the scale of grids is the average of 100 realizations. We have also considered the cases that the variances of noise are respectively 0.001, 0.01, and 0.1. It can be observed that the error of position decreases geometrically with the increasing scale of grids. This accords with the basic prior knowledge, which can be interpreted that the localization will be more accurate with more accurate neighbors’ information. In practice, deploying more grids implies more overhead in the offline part of the proposed approach. It will be more sensible to have a reasonable trade-off between accuracy and expense. It can also be observed that the proposed approach exhibits fine robustness when the scale of grids is over 5. Under the consideration of combining the expense with the robustness, a suitable the scale of grids can be rationally determined, e.g., the scale of grids is 5.
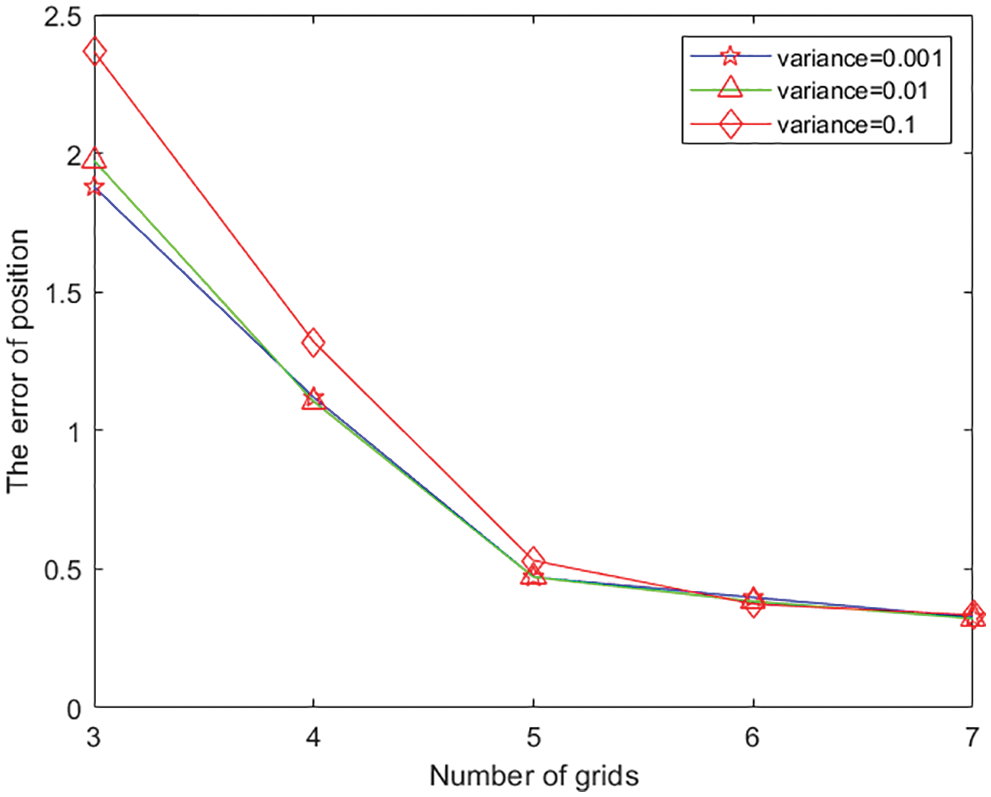
Figure 5: Impact of grid number on the error of position
The RFID readers typically have cross polarization to capture different possible orientations of the RFID tags (due to manual placement). The affected area is typically a semi-hemisphere centered at the RFIS reader in three-dimensional (3D) spaces, and a semi-circular area in the top view. For illustration convenience, we consider horizontally polarized RFID tags and study the horizontal semi-circular area. Nevertheless, the study can be readily extended to a semi-hemispherical area in 3D spaces. We next evaluate the proposed approach in a 3D scenario, where the space is a semi-hemisphere area centered at semi-hemisphere area. Fig. 6 shows a realization of the proposed approach deployed in 3D scenario. All the parameters in Fig. 5 are consistent with the parameters in Fig. 2 except the test space is a 3D space. It can be observed that the predicted position under the proposed approach is almost the same as the true position, even applied in the 3D scenario.
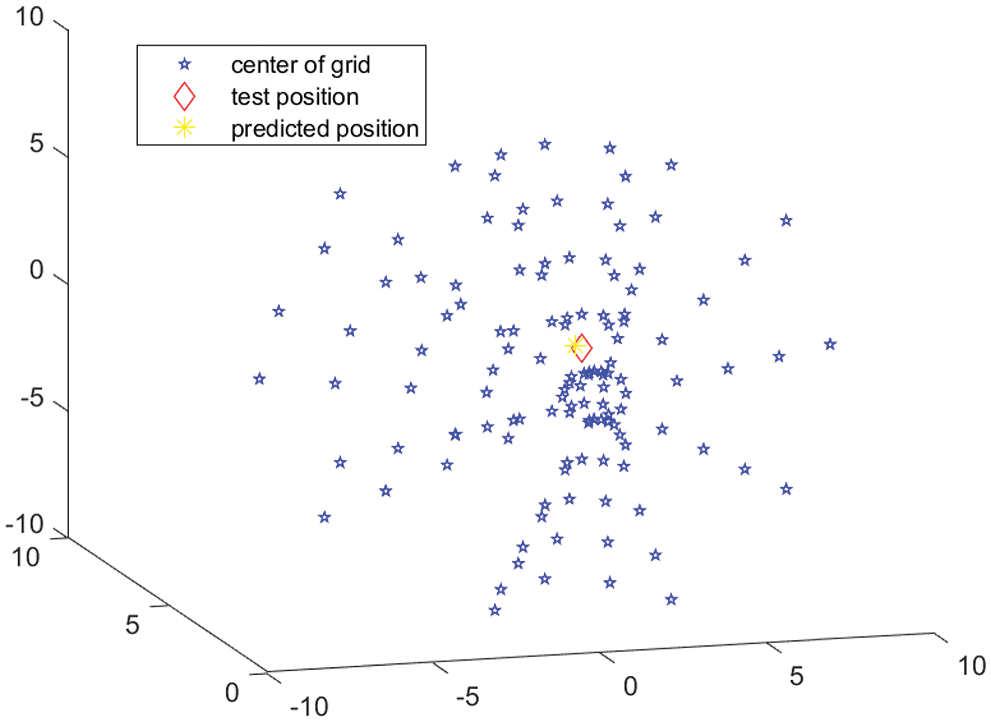
Figure 6: Realization for RFID tag localization using the proposed approach in three dimensional space
The misreading of a passive UHF RFID tag is a critical issue frequently arising in the field of librarianship. We made a comprehensive analysis on such a recurrent problem with an actual scenario as an entry point. We further discussed the existing solutions adopted by most libraries, and developed a novel approach for accurate book localization based on RFID, without needing extra resources. The extensive simulation results show that the proposed approach can achieve significant performance on accuracy, availability, and robustness, and can thus be an attractive candidate in practice.
It is worth noting that in our discussion on the accurate RFID tag localization by the proposed approach applied in the librarianship, the RFID-based misread cases can be readily and efficiently alleviated without extra resources, which can be an attractive engine for any RFID-relied scenarios. For example, considering the RFID-based self-help checkout machine adopted in the supermarket, it apparently can lead to the economic loss of the customers when the RFID tags of commodities are misread. A similar case can be aroused in the scenario of an RFID-based self-help charge for parking. In addition, in the scenario of medical care service, the RFID-based misread cases will cause not only money expense but also personal health even death on the patients. Thus, in our future work, we intend to extend the proposed approach to more passive UHF RFID based scenarios and to take more artificial intelligence (AI)-based ideologies into considerations, aiming to further develop the approach.
Acknowledgement: Part of this work was initially presented at CCIE 2021 [27].
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. Bi, S., Fang, Z., Yuan, X., Wang, X. (2019). Joint base station activation and coordinated downlink beamforming for hetnets: Efficient optimal and suboptimal algorithms. IEEE Transactions on Vehicular Technology, 68(4), 3702–3712. DOI 10.1109/TVT.25. [Google Scholar] [CrossRef]
2. Xu, S., Chen, J., Wu, M., Zhao, C. (2021). E-commerce supply chain process optimization based on whole-process sharing of Internet of Things identification technology. Computer Modeling in Engineering & Sciences, 126(2), 843–854. DOI 10.32604/cmes.2021.014265. [Google Scholar] [CrossRef]
3. Luo, C., Gil, I., Fernandez-Garcia, R. (2020). Wearable textile UHF-RFID sensors: A systematic review. Materials, 13(15), 3292. DOI 10.3390/ma13153292. [Google Scholar] [CrossRef]
4. Zhong, T., Jin, N., Yuan, W., Zhou, C., Gu, W. et al. (2019). Printable stretchable silver ink and application to printed RFID tags for wearable electronics. Materials, 12(18), 3036. DOI 10.3390/ma12183036. [Google Scholar] [CrossRef]
5. Gavalas, D., Stavrakis, M., Chatzimisios, P., Cao, Z., Zheng, X. (2020). Wireless systems and networks in the IoT. Sensors, 20(8), 2279. DOI 10.3390/s20082279. [Google Scholar] [CrossRef]
6. Garcia Oya, J., Martin Clemente, R., Hidalgo Fort, E., Gonzalez Carvajal, R., Munoz Chavero, F. (2018). Passive RFID-based inventory of traffic signs on roads and urban environments. Sensors, 18(7), 2385. DOI 10.3390/s18072385. [Google Scholar] [CrossRef]
7. Cui, L., Zhang, Z., Gao, N., Meng, Z., Li, Z. (2019). Radio frequency identification and sensing techniques and their applications: A review of the state-of-the-art. Sensors, 19(18), 4012. DOI 10.3390/s19184012. [Google Scholar] [CrossRef]
8. Bi, S., Wang, C., Zhang, J., Huang, W., Wu, B. et al. (2022). A survey on artificial intelligence aided Internet-of-Things technologies in emerging smart libraries. Sensors, 22(8), 2991. DOI 10.3390/s22082991. [Google Scholar] [CrossRef]
9. Juels, A. (2006). RFID security and privacy: A research survey. IEEE Journal on Selected Areas in Communications, 24(2), 381–394. DOI 10.1109/JSAC.2005.861395. [Google Scholar] [CrossRef]
10. Ferro, V., Luz, A., Lucrécio, A. (2013). Small long range UHF tag for metal applications. Proceedings of IEEE International Conference on RFID-Technologies and Applications (RFID-TA), Johor Bahru, Malaysia. [Google Scholar]
11. Nayagam, V., Vedullapalli, S., Saikrishna, M., Sivakumar, R. (2017). Radio frequency identification technology for advanced library management. Proceedings of the 3rd International Conference on Science Technology Engineering and Management (ICONSTEM), Chennai, India. [Google Scholar]
12. Ojha, N. (2018). Radio frequency identification (RFID) technology in library: Advantages and issues. Proceedings of the 2nd International Conference on Inventive Systems and Control (ICISC), Coimbatore, India. [Google Scholar]
13. He, H., Liu, T., Wang, E. (2017). Intelligent book positioning system for library based on RFID. Proceedings of the 12th IEEE Conference on Industrial Electronics and Applications (ICIEA), Siem Reap, Cambodia. [Google Scholar]
14. Zhang, J., Wen, C. (2017). The university library management system based on radio frequency identification. Proceedings of the 10th International Congress on Image and Signal Processing, BioMedical Engineering and Informatics (CISP-BMEI), Shanghai, China. [Google Scholar]
15. Toivanen, L., Heino, M., Oksman, A., Vienamo, A., Holopainen, J. et al. (2016). RFID-based book finder [education corner]. IEEE Antennas and Propagation Magazine, 58(3), 72–80. DOI 10.1109/MAP.2016.2541602. [Google Scholar] [CrossRef]
16. Wang, P., Dong, L., Wang, H., Li, G., Di, Y. et al. (2021). Passive wireless dual-tag UHF RFID sensor system for surface crack monitoring. Sensors, 21(3), 882. DOI 10.3390/s21030882. [Google Scholar] [CrossRef]
17. Ando, B., Baglio, S., Castorina, S., Crispino, R., Marletta, V. (2020). An assistive technology solution for user activity monitoring exploiting passive RFID. Sensors, 20(17), 4954. DOI 10.3390/s20174954. [Google Scholar] [CrossRef]
18. Khalid, N., Mirzavand, R., Iyer, A. (2021). A survey on battery-less RFID-based wireless sensors. Micromachines, 12(7), 819. DOI 10.3390/mi12070819. [Google Scholar] [CrossRef]
19. Saad, S., Nakad, Z. S. (2011). A standalone RFID indoor positioning system using passive tags. IEEE Transactions on Industrial Electronics, 58(5), 1961–1970. DOI 10.1109/TIE.41. [Google Scholar] [CrossRef]
20. Ahmad, M., Mohan, A. (2009). RFID reader localization using passive RFID tags. Proceedings of the Asia Pacific Microwave Conference, Singapore. [Google Scholar]
21. Scherhaufl, M., Pichler, M., Stelzer, A. (2015). UHF RFID localization based on evaluation of backscattered tag signals. IEEE Transactions on Instrumentation and Measurement, 64(11), 2889–2899. DOI 10.1109/TIM.2015.2440554. [Google Scholar] [CrossRef]
22. Hatem, E., Fortes, S., Colin, E., Abou-Chakra, S., Laheurte, J. M. et al. (2021). Accurate and low-complexity auto-fingerprinting for enhanced reliability of indoor localization systems. Sensors, 21(16), 5346. DOI 10.3390/s21165346. [Google Scholar] [CrossRef]
23. Galvan-Tejada, C., Zanella-Calzada, L., Garcia-Dominguez, A., Magallanes-Quintanar, R., Luna-Garcia, H. et al. (2021). Estimation of indoor location through magnetic field data: An approach based on convolutional neural networks. ISPRS International Journal of Geo-Information, 9(4), 226. DOI 10.3390/ijgi9040226. [Google Scholar] [CrossRef]
24. Wang, C., Liu, L., Tan, Y. (2020). An efficient content-based image retrieval system using knn and fuzzy mathematical algorithm. Computer Modeling in Engineering & Sciences, 124(3), 1061–1083. DOI 10.32604/cmes.2020.010198. [Google Scholar] [CrossRef]
25. Goldsmith, A. (2005). Wireless communications. Cambridge, UK: Cambridge University Press. [Google Scholar]
26. Hussain, M., Amin, Y., Lee, K. G. (2020). A compact and flexible UHF RFID tag antenna for massive IoT devices in 5G system. Sensors, 20(19), 5713. DOI 10.3390/s20195713. [Google Scholar] [CrossRef]
27. Bi, S., Wang, C., Wu, B., Gong, Y., Ni, W. (2021). An accurate book-localization approach based on passive ultra-high-frequency RFID. Proceedings of 6th International Conference on Computing, Control and Industrial Engineering (CCIE 2021), Hangzhou, China. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools