 Open Access
Open Access
ARTICLE
PSAP-WSN: A Provably Secure Authentication Protocol for 5G-Based Wireless Sensor Networks
1 Shandong University of Science and Technology, Qingdao, 266590, China
2 Department of Mathematics, Chaudhary Charan Singh University, Meerut, 250004, India
* Corresponding Author: Chien-Ming Chen. Email:
Computer Modeling in Engineering & Sciences 2023, 135(1), 711-732. https://doi.org/10.32604/cmes.2022.022667
Received 20 March 2022; Accepted 27 May 2022; Issue published 29 September 2022
Abstract
Nowadays, the widespread application of 5G has promoted rapid development in different areas, particularly in the Internet of Things (IoT), where 5G provides the advantages of higher data transfer rate, lower latency, and widespread connections. Wireless sensor networks (WSNs), which comprise various sensors, are crucial components of IoT. The main functions of WSN include providing users with real-time monitoring information, deploying regional information collection, and synchronizing with the Internet. Security in WSNs is becoming increasingly essential because of the across-the-board nature of wireless technology in many fields. Recently, Yu et al. proposed a user authentication protocol for WSN. However, their design is vulnerable to sensor capture and temporary information disclosure attacks. Thus, in this study, an improved protocol called PSAP-WSN is proposed. The security of PSAP-WSN is demonstrated by employing the ROR model, BAN logic, and ProVerif tool for the analysis. The experimental evaluation shows that our design is more efficient and suitable for WSN environments.Keywords
Historically, communication modes have evolved constantly, progressing through flying pigeons, post stations, wireless telegrams, fixed telephones, and mobile phones. Currently, most countries enjoy excellent Internet communication. Humans can control objects around them, as well as distant objects. Consequently, the Internet of Things (IoT) [1–3] emerged. In 1990, the world’s first IoT device, Xerox’s vending machine, appeared. In 1999, Professor Kevin Ashton of the Massachusetts Institute of Technology first proposed the definition of the IoT [4]. IoT now controls distant things from theory to practice. However, the slow transmission speed of information in the IoT, high latency, and limited support for connected devices are significant problems. 5G has emerged to solve these problems [5,6], providing higher data transfer rates, lower latency, and more connections to facilitate the efficient application of IoT worldwide [7]. Currently, IoT has been deployed in various applications [8–10].
In the last two or three decades, people’s lives have continuously improved with the vigorous development of the Internet. Expectations for quality of life have generally increased. However, traditional electronic devices cannot meet the growing needs of people. With the rapid development of IoT, sensors joined IoT to form wireless sensor networks (WSNs) [11–13], meeting people’s needs for work, production, study, entertainment, and other aspects. Sensors are ubiquitous in everyday life. As shown in Fig. 1, different types of sensors are deployed in homes, hospitals, schools, and other environments. In hospitals, patients are equipped with sensors to self-monitor physiological indicators, and doctors can remotely analyze these data to provide timely medical services to patients. Sensors are placed in schools or homes to collect temperature, carbon monoxide, or pyroelectric data.

Figure 1: Wireless sensor network environment
Although WSNs make people’s lives more efficient and convenient, they also create security problems [14–16]. For example, in 2016, a massive network outage in the eastern United States was caused by hackers who exploited vulnerabilities in communication protocols through a distributed denial-of-service attack [17,18]. Therefore, security is a significant problem that must be solved in WSNs [19,20]. In a typical WSN, two vital security issues must be carefully considered. First, because all sensing data are transmitted through a public channel, the data must be encrypted. Second, all members in a WSN should authenticate each other before sending data [21,22]. Many authentication protocols have been proposed to overcome these two security issues [23–25].
Recently, Yu et al. [26] proposed an authentication protocol called SLUA-WSN, declaring that it is secure against various attacks. Nevertheless, their design remains insecure against temporary information disclosure and sensor capture attacks [26]. To address these vulnerabilities, in this study, a novel authentication protocol, called PSAP-WSN, is proposed. To demonstrate that PSAP-WSN is secure and addresses the vulnerability issues, the ROR model, BAN logic, and ProVerif tools, which are three effective methods for proving the security of an authentication protocol, were employed. In addition, a performance evaluation was conducted to demonstrate that PSAP-WSN is suitable for WSN environments.
The remainder of this paper is organized as follows. In Sections 2 and 3, related work and Yu et al.’s protocol are described, respectively. In Section 4, it is demonstrated that Yu et al.’s protocol is insecure. In Section 5, new solutions are proposed. In Sections 6 and 7, a security analysis and performance evaluation are provided, respectively.
5G requires powerful security and privacy solutions because it connects all aspects of a communication network. Various security mechanisms have been proposed for 5G applications. In 2019, Lu et al. [27] recognized the crucial challenges of security and privacy in 5G vehicle-to-everything. In 2020, Liu et al. [28] proposed a federated learning framework to make 5G environments secure. In 2021, Afaq et al. [29] recognized essential security issues in 5G networks. Then, Yahaya et al. [30] proposed a privacy handover scheme for SDN-based 5G networks. In 2022, Yahaya et al. [30] provided an energy trading model for a 5G-deployed smart community based on blockchain technology.
Various authentication protocols have been proposed for WSNs. In 2015, Chang et al. [31] proposed an authentication protocol for protecting user privacy. However, some parameters of their protocols are not protected. Anonymity and backward confidentiality attacks may occur when users lose their smart cards. In 2017, Lu et al. [32] presented a three-factor authentication protocol with anonymity. In 2019, Mo et al. [33] analyzed Lu et al.’s protocol and concluded that it did not provide three-factor security. Therefore, an improved protocol was proposed. In 2020, Yu et al. [26] indicated that their protocol [33] was insecure against camouflage and session key exposure attacks. In addition, this protocol [33] does not provide anonymity. In 2020, Almuhaideb et al. [34] analyzed Yu et al.’s protocol and noted loopholes. Security problems occur if an adversary obtains both random numbers and sensitive information stored in a smart card. However, we believe that this attack is not reasonable because an adversary should simultaneously obtain two types of secret information.
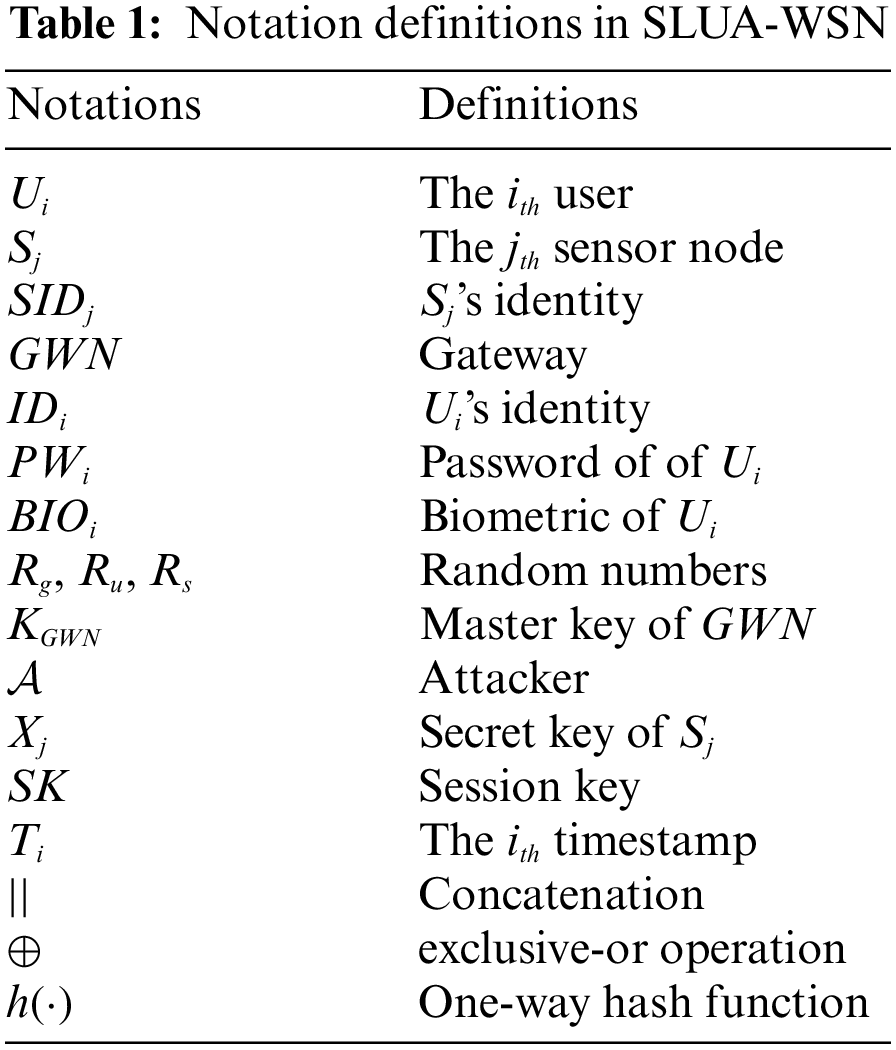
Here, Yu et al.’s design, which consists of sensor registration, user registration, and login and authentication phases, is revisited. The symbols and notations used are listed in Table 1.
Assuming that a sensor
1.
2. GWN generates
3.3 Login and Authentication Phase
1. With the smart card,
2. GWN examines the freshness of
3.
4. GWN calculates
5.
4 Attacks on the SLUA-WSN Protocol
This section analyzes the SLUA-WSN protocol [26]. The adversary model utilized in this study is presented, demonstrating that SLUA-WSN is insecure against sensor node capture and temporary information leakage attacks.
The Dolev-Yao (DY) model [35] is a widely used and reasonable adversary model for analyzing authentication protocols [36]. Under the DY model, the protocol can be thoroughly and reasonably cryptanalyzed. Therefore, the DY model was used as the adversary model with
1.
2.
3.
4.
4.2 Sensor Node Capture Attack
According to the DY model, after capturing a sensor,
Assume that
1.
2.
3.
4. With
5. Now,
6. Eventually,
Evidently, the SLUA-WSN protocol [26] cannot effectively resist sensor node capture attacks.
4.3 Temporary Information Leakage Attack
As mentioned in the adversary model,
Suppose that
1.
2.
3.
4. Eventually,
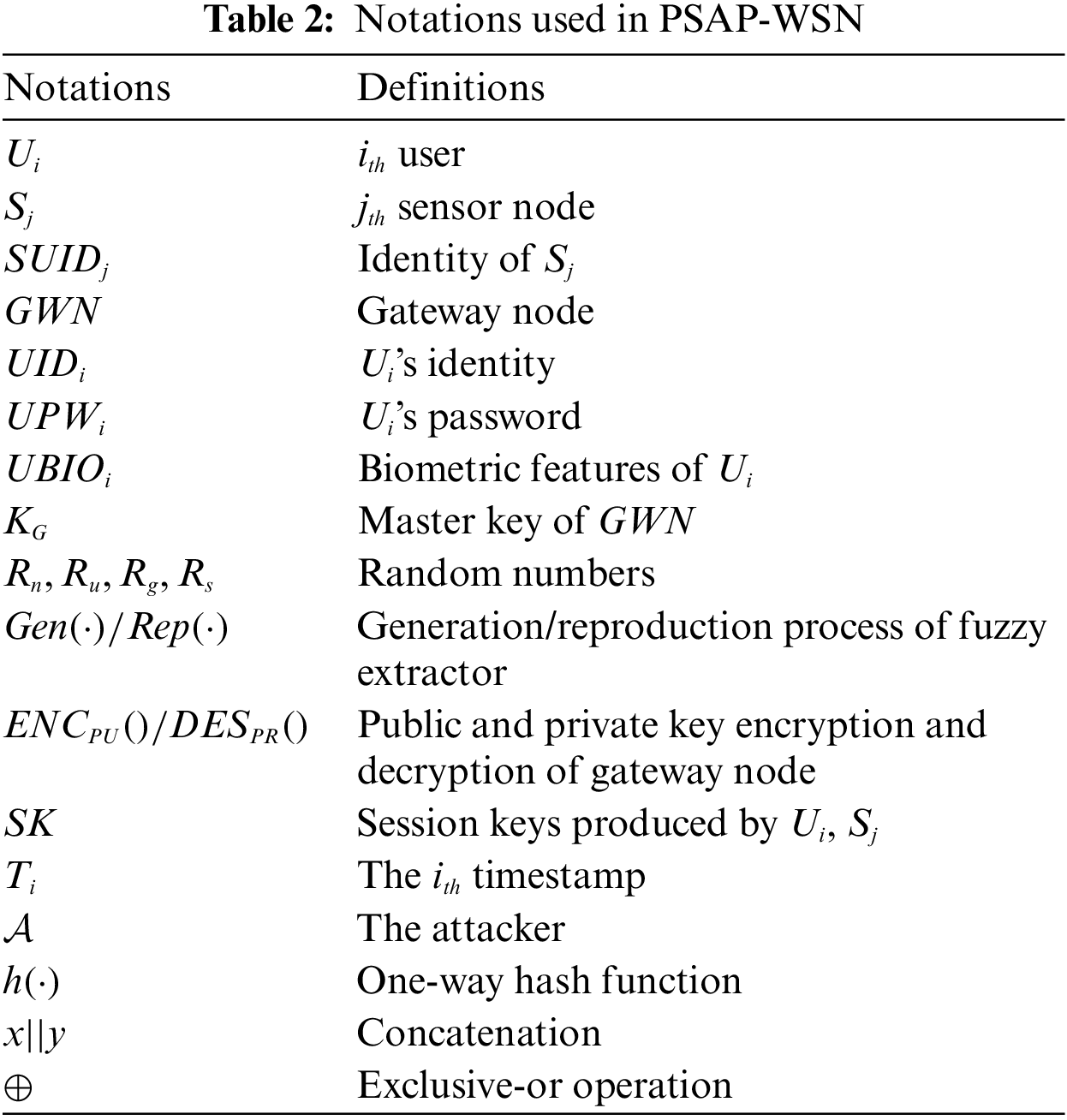
This section describes, in detail, the proposed PSAP-WSN, which consists of the pre-processing, user registration, login, and authentication phases. The symbols used in PSAP-WSN are listed in Table 2.
GWN has to prepare some parameters for the sensors before they are deployed. This phase does not significantly differ from the SLUA-WSN protocol [26]. Fig. 2 illustrates this process. The detailed steps are as follows:
(1) GWN chooses the unique
(2)

Figure 2: Pre-processing phase
All users need to register with GWN before entering the network. Assume that
1.
2. GWN obtains

Figure 3: User registration phase
5.3 Login and Authentication Phase
This phase is performed when the user is expected to connect to a specific sensor. Fig. 4 illustrates this process. Suppose that
(1)
(2) GWN checks the freshness of
(3)
(4) GWN confirms the freshness of
(5)

Figure 4: Login and authentication phase
Finally,
This section demonstrates that PSAP-WSN is provably secure against different attacks, using BAN logic, ROR model, and ProVerif tool.
Ban Logic Rules
Message-meaning rule (R1)
Nonce-verification rule (R2)
Jurisdiction rule (R3)
Freshness rule (R4)
Belief rule (R5)
Session key rule (R6)
Goals
G1
G2
G3
G4
G5
G6
G7
G8
6.1.1 Idealizing Communication
Initial state assumptions
A1
A2
A3
A4
A5
A6
A7
A8
A9
A10
A11
Detailed steps
With
Using S1, R1, and A2, we obtain
Using S2, under the assumption of A3 and nonce verification postulate R2, S3 can be obtained.
With A4, R3, and S3, we obtain
Similarly, we obtain
Because
With A3, A5, and R4, we obtain
In addition, using
By using A1, and R1 we obtain
With S9, A6, and R2, we obtain
Using A7, S9, and R3, we obtain
thus,
Because
With S13, A6, and R4, we obtain
By considering the message
Using S15, R1, and A8, we obtain
Using S16, under the assumption of A10 and the nonce verification postulate R2, S17 can be obtained.
Using A11, R3, and S17, we obtain
Because
Using S19, A10, and R4, we obtain
By considering message
Using S21, R1, and A9, we obtain
Using S22, under the assumption of A3, A5, and nonce verification postulate R2, S23 can be obtained.
Using A4, R3, and S2, we obtain
Because
Using S25, A3, A5, and R4, we obtain
The well-known real-or-random (ROR) model [44] was used to demonstrate that PSAP-WSN is provably secure. The ROR model has been widely used in numerous studies. The PSAP-WSN has three entities:
Theorem 1: Using
Security proof
Proof: To prove Theorem 1, four games
After executing the above four games,
By sorting the above formulae, we obtain
Subsequently, we obtain
To further verify the security of the proposed PSAP-WSN, a well-known verification tool called ProVerif [45,46] was used. In this simulation, we define ch as a public channel and sch as a secure channel. SKi and SKj represent the session keys established by the user and the sensor node, respectively. In addition, PR and KG represent the gateway’s private and master keys, respectively. The simulation contained five events: UserStarted(), UserAuthed(), GatewayAcUser(), SjAcGateway(), and UserAcSj(). The defined parameters and function codes are presented in detail in Fig. 5.

Figure 5: Definition, queries, and events in the ProVerif tool
The results for ProVerif are shown in Fig. 6. We can see “Result not attacker (ski []) is true,” “RESULT not attacker(SKj[]) is true,” “RESULT inj-event(UserAuthed)

Figure 6: Operation results
6.4 Security Requirement Analysis
Next, it is demonstrated that PSAP-WSN is secure against the following attacks.
6.4.1 Sensor Node Capture Attack
Because a sensor node is unattended, it is easily obtained by
6.4.2 Temporary Information Disclosure Attack
This attack assumes that
Suppose
6.4.5 Anonymity and Untraceability
In our design, neither
The proposed PSAP-WSN was compared with similar protocols. The primary attacks included A1: sensor node capture attack; A2: privileged insider attack; A3: temporary information disclosure attack; A4: impersonation attack; A5: replay attack; and A6: anonymity and untraceability attacks. The results in Table 3 confirm that PSAP-WSN provides sufficient security advantages compared with other protocols.

This section evaluates the performance by experimentally calculating the computation and communication overhead.
The three different types of devices used in the comparisons included the OPPO-R9 mobile phone, MI10-UTAR mobile phone, and ASUS-A456U notebook to represent the user, gateway, and sensor, respectively. The running times of the different functions for each device are listed in Table 4. In our experiment, the running times of symmetric encryption and asymmetric encryption were almost the same. In the experiment mentioned in [47], the running time of

The experimental results are presented in Table 5. As shown in the Table 5, the running times of the user, gateway, and sensor node were 15.055, 0.0825, and 0.11 ms, respectively. Although the running time of our design was not always optimal, the overall ranking was relatively high. In addition, the difference was also quite small. Most importantly, these protocols have better running times and are vulnerable to attacks. The results are illustrated in Fig. 7.


Figure 7: Running time
Here, to discuss the communication overhead, the proposed protocol is compared with other related protocols. In the experiment, the settings in [26] were adopted, thereby assuming that the prime number, random nonce, identity, timestamp, and hash function are 160, 128, 32, 32, and 160 bits, respectively. The information exchanged in our proposed protocol includes,

In this paper, first, Yu et al.’s protocol was reviewed and cryptanalyzed, thereby determining that it is vulnerable to sensor node capture attacks and temporary information disclosure attacks. Therefore, the PSAP-WSN protocol was proposed. Subsequently, PSAP-WSN was demonstrated to be provably secure, using BAN logic, the ROR model, and the Proverif tool. In addition, an adversarial attack was simulated against the proposed PSAP-WSN. The performance evaluation indicates that the PSAP-WSN has reasonable communication and computation overhead and is suitable for WSNs.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. Khan, M. A., Salah, K. (2018). IoT security: Review, blockchain solutions, and open challenges. Future Generation Computer Systems, 82, 395–411. DOI 10.1016/j.future.2017.11.022. [Google Scholar] [CrossRef]
2. Gubbi, J., Buyya, R., Marusic, S., Palaniswami, M. (2013). Internet of Things (IoTA vision, architectural elements, and future directions. Future Generation Computer Systems, 29(7), 1645–1660. DOI 10.1016/j.future.2013.01.010. [Google Scholar] [CrossRef]
3. Huang, X., Xiong, H., Chen, J., Yang, M. (2021). Efficient revocable storage attribute-based encryption with arithmetic span programs in cloud-assisted Internet of Things. IEEE Transactions on Cloud Computing. DOI 10.1109/TCC.2021.3131686. [Google Scholar] [CrossRef]
4. Ashton, K. (2009). That ‘Internet of Things’ thing. RFID Journal, 22(7), 97–114. [Google Scholar]
5. Chettri, L., Bera, R. (2019). A comprehensive survey on Internet of Things (IoT) toward 5G wireless systems. IEEE Internet of Things Journal, 7(1), 16–32. DOI 10.1109/JIoT.6488907. [Google Scholar] [CrossRef]
6. Shafique, K., Khawaja, B. A., Sabir, F., Qazi, S., Mustaqim, M. (2020). Internet of Things (IoT) for next-generation smart systems: A review of current challenges, future trends and prospects for emerging 5 G-IoT scenarios. IEEE Access, 8, 23022–23040. DOI 10.1109/Access.6287639. [Google Scholar] [CrossRef]
7. Khan, M. A., Alzahrani, B. A., Barnawi, A., Al-Barakati, A., Irshad, A. et al. (2022). A resource friendly authentication scheme for space–air–ground–sea integrated maritime communication network. Ocean Engineering, 250, 110894. DOI 10.1016/j.oceaneng.2022.110894. [Google Scholar] [CrossRef]
8. Chaudhry, S. A., Irshad, A., Nebhen, J., Bashir, A. K., Moustafa, N. et al. (2021). An anonymous device to device access control based on secure certificate for internet of medical things systems. Sustainable Cities and Society, 75, 103322. DOI 10.1016/j.scs.2021.103322. [Google Scholar] [CrossRef]
9. Xiong, H., Chen, J., Mei, Q., Zhao, Y. (2020). Conditional privacy-preserving authentication protocol with dynamic membership updating for vanets. IEEE Transactions on Dependable and Secure Computing, 19(3), 2089–2104. DOI 10.1109/TDSC.2020.3047872. [Google Scholar]
10. Khan, M. A., Ullah, I., Alkhalifah, A., Rehman, S. U., Shah, J. A. et al. (2021). A provable and privacy-preserving authentication scheme for UAV-enabled intelligent transportation systems. IEEE Transactions on Industrial Informatics, 18(5), 3416–3425. [Google Scholar]
11. Chu, S. C., Dao, T. K., Pan, J. S., Nguyen, T. T. (2020). Identifying correctness data scheme for aggregating data in cluster heads of wireless sensor network based on naive Bayes classification. EURASIP Journal on Wireless Communications and Networking, 2020(1), 52. [Google Scholar]
12. Fan, F., Chu, S. C., Pan, J. S., Lin, C., Zhao, H. (2021). An optimized machine learning technology scheme and its application in fault detection in wireless sensor networks. Journal of Applied Statistics. DOI 10.1080/02664763.2021.1929089. [Google Scholar] [CrossRef]
13. Xue, X., Chen, J. (2019). Using compact evolutionary tabu search algorithm for matching sensor ontologies. Swarm and Evolutionary Computation, 48, 25–30. DOI 10.1016/j.swevo.2019.03.007. [Google Scholar] [CrossRef]
14. Reddy, G. T., Kaluri, R., Reddy, P. K., Lakshmanna, K., Koppu, S. et al. (2019). A novel approach for home surveillance system using IoT adaptive security. Proceedings of International Conference on Sustainable Computing in Science, Technology and Management (SUSCOM), Amity University Rajasthan, Jaipur-India. DOI 10.2139/ssrn.3356525. [Google Scholar] [CrossRef]
15. Kumar, S. A., Vealey, T., Srivastava, H. (2016). Security in Internet of Things: Challenges, solutions and future directions. 2016 49th Hawaii International Conference on System Sciences (HICSS), pp. 5772–5781. Koloa, HI, USA. [Google Scholar]
16. Jian, M. S., Wu, J. M. T. (2021). Hybrid Internet of Things (IoT) data transmission security corresponding to device verification. Journal of Ambient Intelligence and Humanized Computing. [Google Scholar]
17. Abidoye, A. P., Obagbuwa, I. C. (2018). DDOS attacks in WSNS: Detection and countermeasures. IET Wireless Sensor Systems, 8(2), 52–59. DOI 10.1049/iet-wss.2017.0029. [Google Scholar] [CrossRef]
18. Kaushal, K., Sahni, V. (2016). Early detection of DDOS attack in WSN. International Journal of Computer Applications, 134(13), 14–18. DOI 10.5120/ijca2016908117. [Google Scholar] [CrossRef]
19. Soni, P., Pal, A. K., Islam, S. H. (2019). An improved three-factor authentication scheme for patient monitoring using WSN in remote health-care system. Computer Methods and Programs in Biomedicine, 182, 105054. DOI 10.1016/j.cmpb.2019.105054. [Google Scholar] [CrossRef]
20. Modares, H., Salleh, R., Moravejosharieh, A. (2011). Overview of security issues in wireless sensor networks. 2011 Third International Conference on Computational Intelligence, Modelling & Simulation, pp. 308–311. Langkawi, Malaysia. [Google Scholar]
21. Chen, C. M., Li, Z., Chaudhry, S. A., Li, L. (2021). Attacks and solutions for a two-factor authentication protocol for wireless body area networks. Security and Communication Networks, 2021, 3116593. DOI 10.1155/2021/3116593. [Google Scholar] [CrossRef]
22. Azrour, M., Mabrouki, J., Guezzaz, A., Farhaoui, Y. (2021). New enhanced authentication protocol for Internet of Things. Big Data Mining and Analytics, 4(1), 1–9. DOI 10.26599/BDMA.2020.9020010. [Google Scholar] [CrossRef]
23. Wu, T. Y., Yang, L., Lee, Z., Chu, S. C., Kumari, S. et al. (2021). A provably secure three-factor authentication protocol for wireless sensor networks. Wireless Communications and Mobile Computing, 2021, 5537018. DOI 10.1155/2021/5537018. [Google Scholar] [CrossRef]
24. Shafiq, A., Ayub, M. F., Mahmood, K., Sadiq, M., Kumari, S. et al. (2020). An identity-based anonymous three-party authenticated protocol for IoT infrastructure. Journal of Sensors, 2020, 1–17. [Google Scholar]
25. Chen, C. M., Xiang, B., Wang, K. H., Yeh, K. H., Wu, T. Y. (2018). A robust mutual authentication with a key agreement scheme for session initiation protocol. Applied Sciences, 8(10), 1789. DOI 10.3390/app8101789. [Google Scholar] [CrossRef]
26. Yu, S., Park, Y. (2020). SLUA-WSN: Secure and lightweight three-factor-based user authentication protocol for wireless sensor networks. Sensors, 20(15), 4143. DOI 10.3390/s20154143. [Google Scholar] [CrossRef]
27. Lu, R., Zhang, L., Ni, J., Fang, Y. (2019). 5G vehicle-to-everything services: Gearing up for security and privacy. Proceedings of the IEEE, 108(2), 373–389. [Google Scholar]
28. Liu, Y., Peng, J., Kang, J., Iliyasu, A. M., Niyato, D. et al. (2020). A secure federated learning framework for 5G networks. IEEE Wireless Communications, 27(4), 24–31. DOI 10.1109/MWC.7742. [Google Scholar] [CrossRef]
29. Afaq, A., Haider, N., Baig, M. Z., Khan, K. S., Imran, M. et al. (2021). Machine learning for 5G security: Architecture, recent advances, and challenges. Ad Hoc Networks, 123, 102667. DOI 10.1016/j.adhoc.2021.102667. [Google Scholar] [CrossRef]
30. Yahaya, A. S., Javaid, N., Ullah, S., Khalid, R., Javed, M. U. et al. (2022). A secure and efficient energy trading model using blockchain for a 5G-deployed smart community. Wireless Communications and Mobile Computing, 2022, 1–27. [Google Scholar]
31. Chang, I. P., Lee, T. F., Lin, T. H., Liu, C. M. (2015). Enhanced two-factor authentication and key agreement using dynamic identities in wireless sensor networks. Sensors, 15(12), 29841–29854. DOI 10.3390/s151229767. [Google Scholar] [CrossRef]
32. Lu, Y., Xu, G., Li, L., Yang, Y. (2019). Anonymous three-factor authenticated key agreement for wireless sensor networks. Wireless Networks, 25(4), 1461–1475. DOI 10.1007/s11276-017-1604-0. [Google Scholar] [CrossRef]
33. Mo, J., Chen, H. (2019). A lightweight secure user authentication and key agreement protocol for wireless sensor networks. Security and Communication Networks, 2019, 2136506. DOI 10.1155/2019/2136506. [Google Scholar] [CrossRef]
34. Almuhaideb, A. M., Alqudaihi, K. S. (2020). A lightweight three-factor authentication scheme for whsn architecture. Sensors, 20(23), 6860. DOI 10.3390/s20236860. [Google Scholar] [CrossRef]
35. Dolev, D., Yao, A. (1983). On the security of public key protocols. IEEE Transactions on Information Theory, 29(2), 198–208. DOI 10.1109/TIT.1983.1056650. [Google Scholar] [CrossRef]
36. Chen, C. M., Liu, S. (2021). Improved secure and lightweight authentication scheme for next-generation IoT infrastructure. Security and Communication Networks, 2021, 6537678. DOI 10.1155/2021/6537678. [Google Scholar] [CrossRef]
37. Kocher, P., Jaffe, J., Jun, B. (1999). Differential power analysis. Annual International Cryptology Conference, pp. 388–397. Santa Barbara, California, USA. [Google Scholar]
38. Agadakos, I., Chen, C. Y., Campanelli, M., Anantharaman, P., Hasan, M. et al. (2017). Jumping the air gap: Modeling cyber-physical attack paths in the Internet-of-Things. Proceedings of the 2017 Workshop on Cyber-Physical Systems Security and Privacy, pp. 37–48. Dallas, Texas, USA. [Google Scholar]
39. Jokhio, S. H., Jokhio, I. A., Kemp, A. H. (2012). Node capture attack detection and defence in wireless sensor networks. IET Wireless Sensor Systems, 2(3), 161–169. DOI 10.1049/iet-wss.2011.0064. [Google Scholar] [CrossRef]
40. Bharathi, M. V., Tanguturi, R. C., Jayakumar, C., Selvamani, K. (2012). Node capture attack in wireless sensor network: A survey. 2012 IEEE International Conference on Computational Intelligence and Computing Research, pp. 1–3. Tamilnadu, India. [Google Scholar]
41. Wang, C., Wang, D., Tu, Y., Xu, G., Wang, H. (2020). Understanding node capture attacks in user authentication schemes for wireless sensor networks. IEEE Transactions on Dependable and Secure Computing, 19(1), 507–523. [Google Scholar]
42. Jiang, Q., Zeadally, S., Ma, J., He, D. (2017). Lightweight three-factor authentication and key agreement protocol for internet-integrated wireless sensor networks. IEEE Access, 5, 3376–3392. DOI 10.1109/ACCESS.2017.2673239. [Google Scholar] [CrossRef]
43. Abbasinezhad-Mood, D., Ostad-Sharif, A., Nikooghadam, M., Mazinani, S. M. (2019). A secure and efficient key establishment scheme for communications of smart meters and service providers in smart grid. IEEE Transactions on Industrial Informatics, 16(3), 1495–1502. DOI 10.1109/TII.9424. [Google Scholar] [CrossRef]
44. Abdalla, M., Fouque, P. A., Pointcheval, D. (2005). Password-based authenticated key exchange in the three-party setting. International Workshop on Public Key Cryptography, Les Diablerets, Switzerland: Springer. [Google Scholar]
45. Blanchet, B. (2013). Automatic verification of security protocols in the symbolic model: The verifier proverif. Foundations of Security Analysis and Design VII, pp. 54–87. Bertinoro, Italy, Springer. [Google Scholar]
46. Cheval, V., Cortier, V., Turuani, M. (2018). A little more conversation, a little less action, a lot more satisfaction: Global states in proVerif. 2018 IEEE 31st Computer Security Foundations Symposium (CSF), pp. 344–358. Oxford, UK. [Google Scholar]
47. Wu, F., Xu, L., Kumari, S., Li, X. (2018). An improved and provably secure three-factor user authentication scheme for wireless sensor networks. Peer-to-Peer Networking and Applications, 11(1), 1–20. DOI 10.1007/s12083-016-0485-9. [Google Scholar] [CrossRef]
48. Wang, C., Xu, G., Sun, J. (2017). An enhanced three-factor user authentication scheme using elliptic curve cryptosystem for wireless sensor networks. Sensors, 17(12), 2946. DOI 10.3390/s17122946. [Google Scholar] [CrossRef]
49. Li, X., Niu, J., Kumari, S., Wu, F., Sangaiah, A. K. et al. (2018). A three-factor anonymous authentication scheme for wireless sensor networks in Internet of Things environments. Journal of Network and Computer Applications, 103, 194–204. DOI 10.1016/j.jnca.2017.07.001. [Google Scholar] [CrossRef]
50. Li, X., Peng, J., Obaidat, M. S., Wu, F., Khan, M. K. et al. (2019). A secure three-factor user authentication protocol with forward secrecy for wireless medical sensor network systems. IEEE Systems Journal, 14(1), 39–50. DOI 10.1109/JSYST.4267003. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools