
 | Computer Modeling in Engineering & Sciences |  |
DOI: 10.32604/cmes.2022.018749
ARTICLE
A Lightweight and Robust User Authentication Protocol with User Anonymity for IoT-Based Healthcare
1College of Computer Science and Engineering, Shandong University of Science and Technology, Qingdao, 266590, China
2Department of Computer Engineering, Istanbul Gelisim University, Istanbul, 34310, Turkey
3Department of Computer Science, University of California, Davis, CA, 95616, USA
4Department of Electrical Engineering, Hamdard University, Islamabad, 44000, Pakistan
*Corresponding Author: Chien-Ming Chen. Email: chienmingchen@ieee.org
Received: 14 August 2021; Accepted: 09 October 2021
Abstract: With the rise of the Internet of Things (IoT), the word “intelligent medical care” has increasingly become a major vision. Intelligent medicine adopts the most advanced IoT technology to realize the interaction between patients and people, medical institutions, and medical equipment. However, with the openness of network transmission, the security and privacy of information transmission have become a major problem. Recently, Masud et al. proposed a lightweight anonymous user authentication protocol for IoT medical treatment, claiming that their method can resist various attacks. However, through analysis of the protocol, we observed that their protocol cannot effectively resist privileged internal attacks, sensor node capture attacks, and stolen authentication attacks, and their protocol does not have perfect forward security. Therefore, we propose a new protocol to resolve the security vulnerabilities in Masud’s protocol and remove some redundant parameters, so as to make the protocol more compact and secure. In addition, we evaluate the security and performance of the new protocol and prove that the overall performance of the new protocol is better than that of other related protocols.
Keywords: IoT; intelligent medical; user authentication
In the traditional Internet, most of the information exchange and communication took place between computers, where computers operations were manual operations; the traditional Internet realizes the information exchange and communication between people in a certain sense. Now, however, we have forayed into the era of the Internet of Things (IoT) [1,2]. The applicability of the new system goes beyond realizing the mutual exchange of information and communication between people, between people and objects, and between objects. The IoT has a wide range of uses, including intelligent transportation, intelligent fire protection, intelligent home, intelligent power grid, intelligent medical, and other aspects. In short, it facilitates the use of the latest IT technology in all walks of life. Specifically, IoT technology embeds sensors into the power grid, buildings, and other objects [3 –6]. The construction industry is using IoT technology ubiquitously. Architecture is the foundation of a city; the progress of technology promotes the intelligent development of architecture, and intelligent architecture is rapidly gaining people’s attention. The current smart building methods incorporate power lighting and fire monitoring. Sensors are installed on equipment for sensing, transmission, and remote monitoring, which not only saves considerable time but also energy. Among the many applications of the IoT, smart medicine is one of the most promising applications for the future.
The emergence of IoT technology promotes the further development of medical information technology. IoT technology has great potential in the field of medicine and health [7–9]. It can better realize diagnoses and facilitate intelligent management of things. Furthermore, it realizes digital processing and sharing of resource information, equipment information, drug information, and personnel information. The use of intelligent medicine is prominent in two fields: digital hospitals and medical wearables. The digital hospital includes a hospital information system, medical image storage system, transmission system, and doctor workstation. Their function is to realize the collection, storage, processing, and transmission of patient information. Digital hospitals enable zero-distance contact with patients. Doctors can conduct long-distance consultation, intelligent medical support resource sharing, and cross-regional optimal allocation. In addition, digital medicine can also monitor the vital signs of patients by deploying sensor nodes, which will automatically send an alarm in case of emergency, which reduces the nursing cost of seriously ill patients. The digital hospital also includes a clinical decision-making system, implying that doctors can analyze patients’ symptoms while helping formulate the best and effective treatment plan. In addition, digital medicine provides a remote visitation system. When visitors visit patients, they directly do so through the remote visitation system, which can effectively avoid the direct contact between patients and visitors, eliminate the spread of disease, and shorten the recovery process of patients.
Medical wearable technology [10–12] is the deployment of sensor nodes around the patient, through the sensor nodes collecting information and parameters of the user’s patient and the surrounding environment, sending it through the network to the cloud, and then processing to the user. The digital hospital is an improvement over the traditional hospital; it realizes the digital equipment’s access to electronic medical records and the management of equipment. However, with the introduction of the medical system of the IoT, introducing sensor nodes around the patients to collect information and then transmitting it to remote medical staff is made possible, ensuring the safety of the medical staff. However, the introduction of IoT is bound to involve the transmission of information on the network channel. Due to the universality and openness of the transmission channel, privacy and security of transmitted information have become the main concern of the IoT medical systems.
Fig. 1 shows the architecture of communication between three entities in the IoT-based healthcare environment: the doctor (user), IoT devices, and a gateway. All the IoT devices around the patients collect real-time patients’ information and then transmit them to a gateway. An authenticated doctor can access the gateway to obtain effective information from those IoT devices. This means that a gateway can authenticate the identity of doctors. In other words, a gateway is a medium for doctors to communicate with sensors.

Figure 1: System model
In 2012, Chen et al. [13] proposed an efficient and secure dynamic identity authentication protocol for telemedicine information systems, which dynamically authenticates the user’s identity to achieve user anonymity. However, Cao et al. [14] found that the protocol can track users through offline identity guessing attacks. When the user loses possession of a smart card, there is no guarantee of security as Chen’s protocol is also vulnerable to offline password guessing attacks. Therefore, Cao et al. [14] proposed an improved password authentication protocol based on the smart card. In 2015, He et al. [15] proposed a two-factor authentication scheme for wireless medical sensors, which allows medical personnel to access patient information using wireless sensor medical devices. In 2016, Li et al. [16] proposed a network-based electronic medical authentication scheme, which also uses the user’s password and smart card for two-factor authentication. He et al. [17] proposed an authentication protocol that is more suitable for the configuration of telemedicine information systems with low power consumption mobile devices. Wei et al. [18] found that this protocol cannot effectively resist password attacks; they proposed an improved authentication protocol for telemedicine information systems and proved that the protocol meets the security requirements of two-factor authentication. In 2018, Wu et al. [19] proposed a lightweight two-factor medical authentication scheme, and they claimed that their protocol had perfect security; however, after analysis, it was found that their protocol could not effectively resist perfect forward security. Therefore, based on the two-factor authentication protocol, Wazid et al. [20] proposed a three-factor network authentication key scheme, which introduced biological information based on the previous authentication password and smart card. The map area of biological information is mainly completed by a biological extractor. In 2019, Sharma et al. [21] proposed a lightweight user authentication protocol, but Canetti et al. [22] found that their protocol could not effectively resist privilege insider attacks. Recently, Masud et al. [23] proposed a protocol for the security of the IoT medical system. The paper mentioned that their protocol is a lightweight anonymous user authentication protocol. The protocol only uses hash primitives to encrypt the information, which reduces the burden of the processor while resisting replaying attacks, man-in-the-middle attacks, anonymity, and untraceability. However, we find that the protocol mentioned in this paper cannot effectively resist internal privilege attacks, sensor node capture attacks, or stolen verification attacks, and it cannot provide perfect forward security.
In this paper, we first demonstrate that Masud et al.’s protocol [23] is insecure against various kinds of attacks. We then propose a lightweight and robust user authentication protocol for IoT-based healthcare with user anonymity. In our design, we only use a single hash function and successive XOR operations; thus, the proposed protocol retains better performance. Additionally, the proposed protocol has perfect forward security and can effectively resist internal privilege, stolen verification, and sensor node capture attacks. In addition, we delete some redundant parameters in Masud et al.’s protocol [23] to make the entire protocol more concise. Furthermore, we compare the proposed protocol with other related protocols in terms of communication and computation cost. The results show that our design has better performance. Also, we use the real-or-random (ROR) model [24] to further prove that the proposed protocol is indeed secure.
The remainder of this paper is organized as follows. In Section 2, we briefly review Masud et al.’s protocol [23] Section 3 demonstrates that Masud et al.’s protocol [23] is vulnerable to privilege internal attacks, stolen verification attacks, and sensor node capture attacks. The proposed protocol is described in Section 4. Section 5 and Section 6 provide security and performance analyses and comparisons. Finally, Section 7 concludes the paper.
2 Review of Masud et al.’s Protocol
In this section, we briefly describe the protocol [23], which consists of three phases: user registration phase, sensor node registration phase, and login and mutual authentication phase. In the first two phases, user and sensor registration is conducted through the gateway.
1. The user first selects an DID and password PWD, and then generates a registration request Rreq. Then, the user transmits the DID, PWD, and Rreq to the gateway through the secure channel. After the gateway receives the registration request from the user, it generates a random gateway private key
and stores the parameter a,
2. After receiving the parameter from the gateway, the user first calculates the value of the random gateway key
1. Firstly, the sensor selects its own identity SID, generates a random sensor private key
2. After receiving the parameters SID, and
Finally, the gateway stores the values of sensor identity, random sensor private key, random gateway private key, and sensor pseudo-identity in the memory.
2.3 Login and Mutual Authentication Phase
1. First, the user enters the password, then calculates
This is to test whether the value of Q is equal to B stored in the user memory. If these values are equal, the user generates a temporary random number
Finally, the user transmits parameters
2. After receiving the parameter transmitted by the user, the gateway calculates
and verifies the parameter.
After the verification, it calculates
This is done to verify whether it is equal to the parameter value of K. If it is equal, the gateway generates a temporary random number
Finally, the gateway transmits the parameters
3. The sensor receives the parameters
and then verifies
Next, the gateway generates a random number
Then, the sensor updates its identity
Next, the sensor stores the values of
4. The gateway calculates
Then verifies
This verifies whether
5. The user obtains the value of
3 Cryptanalysis of Masud et al.’s Protocol
In this section, we first introduce the attack model used in this paper and then analyze Masud’s protocol [23] according to the attack model. The protocol cannot effectively resist privileged insider, sensor node capture, and stolen verification attacks, and there are loopholes in the perfect forward secrecy.
The attack model briefly describes the capabilities of
1. According to the “Dolev-Yao threat (DY) model” [27] proposed before,
2. Once the sensor is lost and acquired by
3. In most user sensor authentication protocols, users often need to store some parameters in the registration phase for use in the login authentication phase. Usually, this information is stored in the user’s smart card or memory. However, the user’s smart card is often easy to lose. Once the smart card is obtained by
A good protocol must comprise the perfect forward secrecy feature [31,32], which ensures that master key leakage will not lead to session key leakage. Forward secrecy can protect past communication from the threat of key exposure in the future. Even in the case of master key leaks, the historical communication still has good security. However, in Masud’s protocol, we found that if
1. First,
2. Second,
3. The session key between the sensor and the gateway
Privileged insider attack refers to a process in which
1. First,
2. Second,
3. The session key SK can be obtained.
In the second step, the
3.4 Stolen Verification Attack
A stolen verification attack implies that
1. First,
2.
3.
between the user and the gateway. Therefore, this protocol cannot effectively resist the stolen verification attack.
3.5 Sensor Node Capture Attack
The sensor node capture attack refers to the process in which the session key is leaked after
1. During the registration of the sensor with the gateway, the sensor stores the identity STID,
2. In the mutual authentication stage of gateway and sensor, the user transmits the parameter STID to the gateway through the common channel, and the gateway transmits the parameter
3. Session key between sensor and gateway
Once
We have analyzed Masud’s protocol and listed the detailed attack process. A secure protocol must be able to resist some common attacks. We have improved Masud’s protocol, and the improved protocol can successfully repair the aforementioned security vulnerabilities. In addition, we deleted some redundant symbols in the original protocol to make the entire protocol more concise. Our protocol consists of four parts: pre-deployment phase, user registration phase, sensor registration phase, and login authentication phase.
The symbols used in the protocol are shown in Table 1.

For the pre-deployment phase of users and sensors, the gateway first generates a key-value RG and then sends the key value to the users and sensors through the secure channel in advance.
Fig. 2 illustrates the user registration phase. The detailed steps are as follows:

Figure 2: User registration phase
1. First, the user selects id ID and password PW, and a random number N1, calculates
and generates a request Rreq for registration. Finally, the user transmits the information of RID and RPW to the gateway through the secure channel.
2. After receiving the registration request from the user, the gateway calculates
and then generates a random secret value G1. It then calculates
Finally, A1, A2, and DTID are stored in the gateway, and A2 is transmitted to users through a secure channel.
3. According to the transmitted A2, calculate
Finally, G1, DTID, D and X is stored in the user’s memory.
Fig. 3 illustrates the sensor registration phase. The detailed steps are as follows:

Figure 3: Sensor registration phase
1. First, users select an identity SID for themselves and generate a random key value S1 to calculate
and then the user sends SID′, S1 to the gateway through the secure channel for registration.
2. After receiving the message from the sensor, the gateway generates a random key value G2 and encrypts the key value to obtain
and encrypts the identity of the sensor to obtain the pseudo-identity of the sensor
It next stores the parameters O, B, STID in the gateway memory and then sends the parameter O to the sensor through the secure channel.
3. After the sensor receives the message, it first extracts the value of the gateway’s key G2,
and then calculates the sensor’s pseudo-identity
Finally, the sensor stores the parameter value S1 and STID in the sensor memory.
4.5 Login and Authentication Phase
This section introduces the login and mutual authentication process between the user and the sensor through the gateway in detail as in Fig. 4. The following is the detailed description of login and authentication.

Figure 4: Login and authentication phase
1. Before logging in, the user first enters the account id ID and password PW, used in registration. Then, the following is calculated:
Subsequently, D1 is verified to check whether it is equal to the D value previously stored in the user’s memory. If it is, it implies that it is a login operation by a legal user. After successful login, the user calculates
Finally, the user sends the parameter K and SID′ to the gateway through the common channel.
2. When the gateway receives the parameters from a legitimate user, it needs to determine whether the message sent has been tampered with by
to compare K′ with K, and equality implies that it passes verification. Then, the gateway continues to calculate
SKs is the operation in which the gateway distributes the key to the sensor. Finally, the gateway sends the parameter Y1, Y2, STID, SKs to the sensor through the common channel.
3. The sensor receives the message from the gateway, and first calculates the temporary key value G1 of the gateway according to the values of STID and Y1.
then calculates
and compares the S2 value sent by the gateway with Y2′. If it is equal, then
according to the parameter SKs sent by the gateway. Finally, the sensor identity is updated, storing the updated sensor parameter value in memory, and the value of parameter Z is sent to the gateway through the common channel.
4. The gateway receives the parameter from the sensor. First, it checks whether
and compares the value of Z′ with that of Z. If it is equal, it means it passes verification. Next, the gateway obtains the identity value of the updated sensor through the following operation.
Then, it stores the updated sensor identity value in its memory. Next, the gateway allocates the session key and computes
and updates the user’s identity.
The gateway stores the updated user’s identity parameter in the gateway, and sends the value of parameter u, SKu, n to the user through the common channel.
5. The user should first check the parameter value sent,
If the value of G1′ is equal to the value of G1 previously stored in the user memory, thus passing the verification. Next, the user calculates the session key
between the user and gateway through the value of SKu sent by the gateway. Then, before updating the user’s identity, the following is performed
which is compared with the received value of n. The parameter is updated if it is equal.
Finally, the updated identity is stored in the user’s memory.
5.1 Formal Proof of the Proposed Protocol
In this section, we use the ROR model [24] to prove the security of the proposed protocol. In the protocol, we define three entities: user, gateway, and sensor node. For this proof, we assume that Ui, Gj, and Sz are the i-th user, the j-th gateway, and the z-th sensor node, respectively, and the parameter
Execute (T): By performing this operation,
Send (T, M): By executing this query,
CorruptDevice (T): After executing this query,
Hash (string): After entering a fixed-length string,
Test (T): In the initial stage,
Theorem: For the ROR model, if
In the formula, f represents the length of biological information entered by the user in the registration and login stage, and D′ and b′ represent two constants.
Proof: We defined 6 games GM0 to GM5 in the specific proof process, and everyone has different game rules. In the proof process,
GM0: In this game,
GM1: GM1 adds the Execute query operation on the basis of Gm0. That is,
GM2: GM2 adds the Send operation on the basis of GM1, that is,
GM3: GM3 adds Hash query on the basis of GM2.
GM4: In this game, we query the CorruptDevice to obtain the value of long-term key RG and the value of temporary information N1 generated by U to verify whether the protocol has perfect forward security and resists temporary information leakage attacks.
Perfect forward secrecy:
Temporary information leakage attack:
GM5: Different from the GM4 rule, we query the information stored in the user’s memory through CorruptDevice, and then prove that the proposed protocol can resist offline password guessing attacks. The probability that it can successfully guess the user password is 1/2, but in Zipf’s law, when the number of transmitted bits
GM6: In GM6, in order to verify that the protocol we proposed can successfully resist user simulation attacks, unlike GM5,
Because the probabilities of GM6 success and failure are equal,
From the formula calculated above, we can get
Then
According to the above process, we prove that our proposed protocol can effectively resist user simulation, offline password guessing, and temporary information leakage attacks and has perfect forward security.
5.2 Informal Security Analysis
In this section, we describe how the new protocol can resist several common attacks. The following descriptions further prove the security of our proposed protocol.
5.2.1 Withstands Privileged Insider Attack
In this protocol, we assume that
5.2.2 Withstands Sensor Node Capture Attack
If
5.2.3 Withstands Stolen Verification Attack
In a stolen verification attack,
Assuming that
In the user registration stage, we perform the XOR operation on the user’s ID and the long-term key RG of the gateway and then encrypt the user’s identity. Subsequently, communication with the gateway occurs through the secure channel. Therefore, it is not easy for
5.2.6 Withstands Password Guessing Attack
In the user login phase, the system verifies whether the value of D1 is equal to the value of D stored in the user memory.
5.2.7 Withstands Temporary Information Leakage Attack
If
6 Security and Performance Comparisons
In this section, we analyze the security and performance of the new protocol. We compare the new protocol with other related protocols, mainly by comparing the running time, communication cost, and the ability to resist common attacks to show that our proposed protocol has an advantage in security and performance.
In this part, we compare with other related agreements. Finally, other protocols cannot resist all common attacks, but our new protocol can resist all attacks. At present, common network attacks include A1: Identity anonymity of user device, A2: Identity anonymity of IoT sensor node, A3: privileged-insider attack, A4: off-line password guessing attack, A5: Perfect forward secrecy, A6: man-in-the-middle attack, A7: IoT sensor node impersonation attack, A8: Sensor node capture attack, A9: Stolen verification attack. The comparison results are presented in Table 2. A “Yes” implies that the protocol can resist the attack, whereas a “No” means that it cannot.

For performance analysis, we use the same conditions to analyze the protocols in different environments. In the analysis process, because XOR and join operations take less time, we only analyze according to the non-collision hash function used in the protocol. The time required for the hash function is 0.00089 Ms. In addition, in the communication process, the number of bits required for the non-collision hash function is 256 bits.
First, we compare the communication cost between the protocol proposed in this paper and the related protocols proposed earlier. Here, we only consider the communication cost of the non-collision hash function. The communication cost of our protocol is 1,792 bits, lower than those of Masud et al. [23] (4,096 bits), Wazid et al. [40] (2,304 bits), Turkanovi et al. [39] (5,120 bits), Farash et al. [38] (5,888), Zhou et al. [37] (6,144 bits), and Challa et al. [36] (3,840 bits). This result can be observed in Fig. 5.
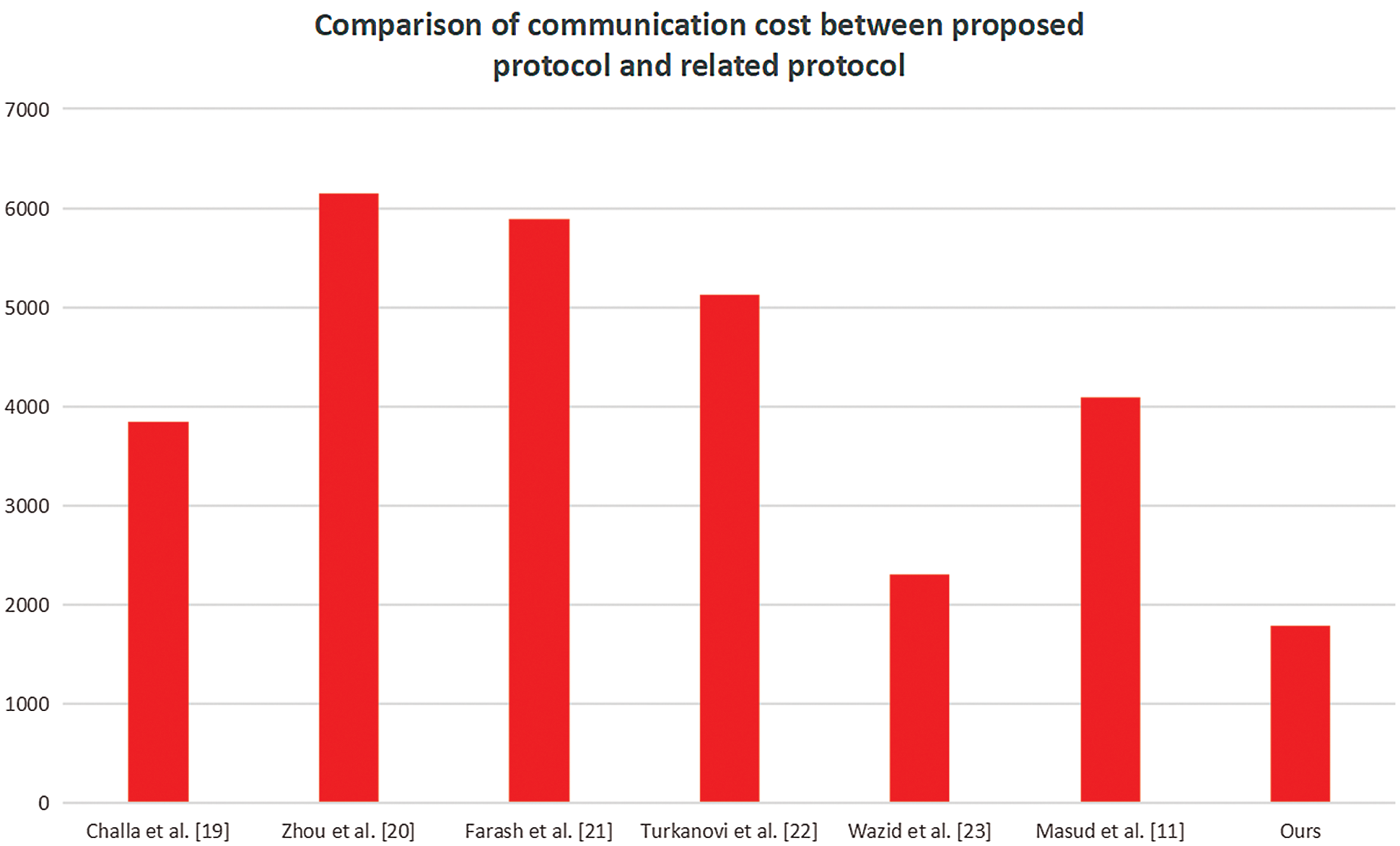
Figure 5: Communication cost
Second, we compare the protocols proposed in this paper with regard to time. Here, we only consider the running time of the non-collision hash function. Table 3 shows the number of hash functions required by the user gateway and sensor nodes during the protocol user registration phase, sensor registration phase, and login authentication phase where H represents the hash function. In Table 4, we compare the proposed protocol with those in other related fields. The results show that the time required for our proposed protocol is 0.00623 ms, and for Masud et al. [23], Wazid et al. [40], Turkanovi et al. [39], Sharma et al. [21], Farash et al. [38], Zhou et al. [37], Challa et al. [36], the times are 0.00712, 0.02848, 0.01513, 0.02047, 0.02848, 0.03204, and 0.01068 ms, respectively. It can be seen more intuitively in Fig. 6 that the running cost of the protocol proposed by us is better than those proposed in other relevant papers.


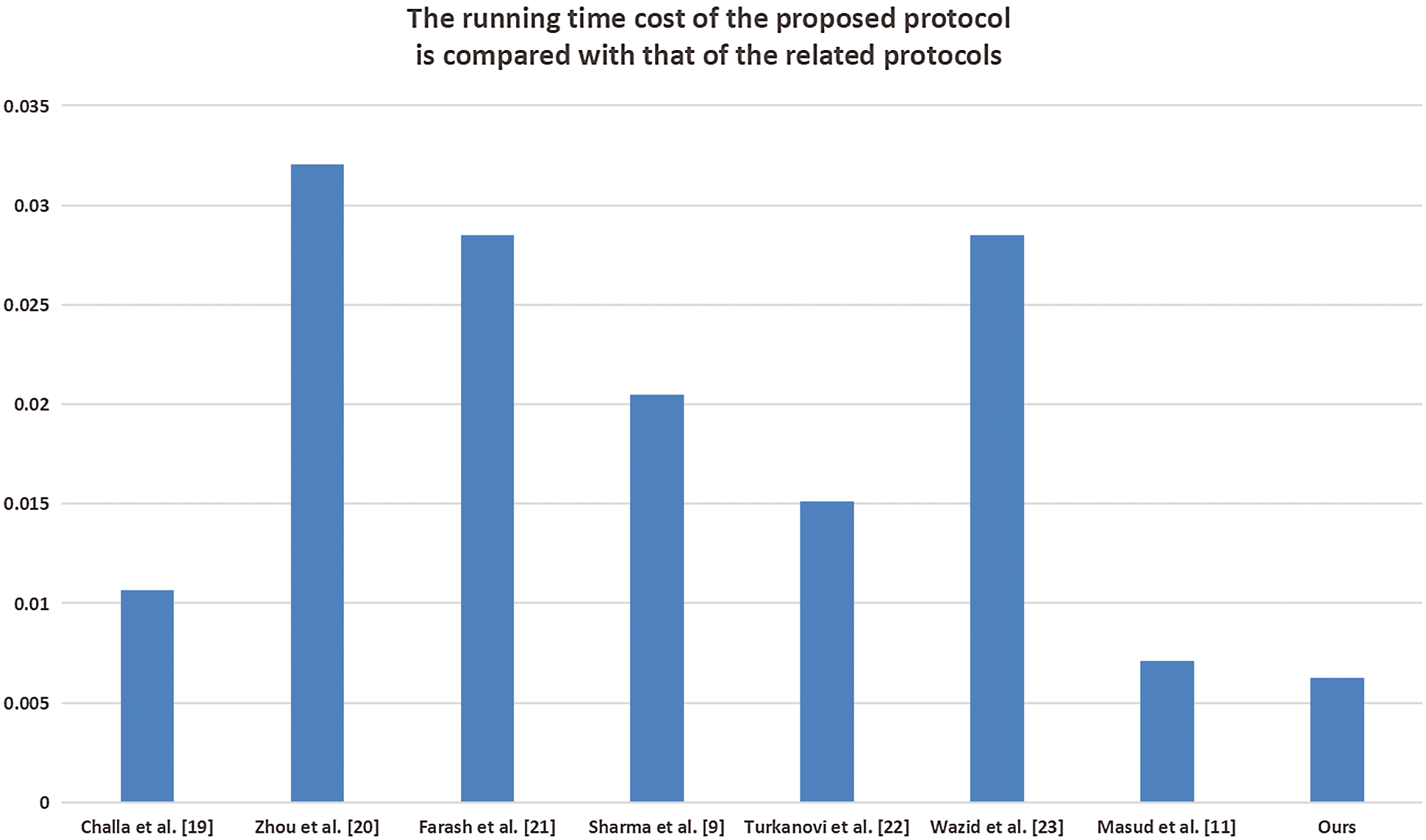
Figure 6: Running time
After comparing our protocol with other related protocols, we can observe that the proposed protocol can effectively resist various attacks, and so we can say that our protocol has perfect security. In addition, our proposed protocol is superior to the existing protocol in terms of communication cost and time running cost. To sum up, the proposed protocol is more suitable for the development of future medical systems and is more convenient and user friendly for future medical staff and patients.
This paper improves Masud’s authentication protocol for the medical system. The improved protocol not only resists the common attacks that the existing protocol was unable to but also removes the redundant symbols in the original protocol, reducing the communication cost. In addition, it retains the lightweight advantage of the original protocol. The improved protocol still adopts a single hash and bit-by-bit XOR operation, which reduces the running time. The protocol is secure against privileged internal attacks, stolen verification attacks, and sensor node capture attacks, thus presenting perfect forward security. This protocol is more suitable for the future medical environment. It preserves the security in the medical system as well as the user privacy, while additionally enhancing the system performance.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. Xiong, H., Huang, X., Yang, M., Wang, L., Yu, S. (2021). Unbounded and efficient revocable attribute-based encryption with adaptive security for cloud-assisted Internet of Things. IEEE Internet of Things Journal. DOI 10.1109/JIOT.2021.3094323. [Google Scholar] [CrossRef]
2. Hou, Y., Xiong, H., Huang, X., Kumari, S. (2021). Certificate-based parallel key-insulated aggregate signature against fully chosen key attacks for industrial Internet of Things. IEEE Internet of Things Journal, 8(11), 8935–8948. DOI 10.1109/JIOT.2021.3056477. [Google Scholar] [CrossRef]
3. Wang, K., Chen, C. M., Liang, Z., Hassan, M. M., Sarné, G. M. et al. (2021). A trusted consensus fusion scheme for decentralized collaborated learning in massive IoT domain. Information Fusion, 72, 100–109. DOI 10.1016/j.inffus.2021.02.011. [Google Scholar] [CrossRef]
4. Wang, P., Chen, C. M., Kumari, S., Shojafar, M., Tafazolli, R. et al. (2021). HDMA: Hybrid D2D message authentication scheme for 5G-enabled vanets. IEEE Transactions on Intelligent Transportation Systems, 22(8), 5071–5080. DOI 10.1109/TITS.2020.3013928. [Google Scholar] [CrossRef]
5. Wang, X., Liu, Y., Choo, K. K. R. (2020). Fault-tolerant multisubset aggregation scheme for smart grid. IEEE Transactions on Industrial Informatics, 17(6), 4065–4072. DOI 10.1109/TII.2020.3014401. [Google Scholar] [CrossRef]
6. Li, C. T., Lee, C. C., Weng, C. Y., Chen, C. M. (2018). Towards secure authenticating of cache in the reader for rfid-based IoT systems. Peer-to-Peer Networking and Applications, 11(1), 198–208. DOI 10.1007/s12083-017-0564-6. [Google Scholar] [CrossRef]
7. Wu, T. Y., Wang, T., Lee, Y. Q., Zheng, W., Kumari, S. et al. (2021). Improved authenticated key agreement scheme for fog-driven IoT healthcare system. Security and Communication Networks, 2021. [Google Scholar]
8. Chen, C. M., Li, C. T., Liu, S., Wu, T. Y., Pan, J. S. (2017). A provable secure private data delegation scheme for mountaineering events in emergency system. IEEE Access, 5, 3410–3422. DOI 10.1109/ACCESS.2017.2675163. [Google Scholar] [CrossRef]
9. Ayub, M. F., Mahmood, K., Kumari, S., Sangaiah, A. K. (2021). Lightweight authentication protocol for e-health clouds in IoT-based applications through 5G technology. Digital Communications and Networks, 7(2), 235–244. DOI 10.1016/j.dcan.2020.06.003. [Google Scholar] [CrossRef]
10. Shahbazi, Z., Byun, Y. C. (2020). Towards a secure thermal-energy aware routing protocol in wireless body area network based on blockchain technology. Sensors, 20(12), 3604. DOI 10.3390/s20123604. [Google Scholar] [CrossRef]
11. Benmansour, T., Ahmed, T., Moussaoui, S., Doukha, Z. (2020). Performance analyses of the IEEE 802.15. 6 wireless body area network with heterogeneous traffic. Journal of Network and Computer Applications, 163, 102651. DOI 10.1016/j.jnca.2020.102651. [Google Scholar] [CrossRef]
12. Hasan, K., Biswas, K., Ahmed, K., Nafi, N. S., Islam, M. S. (2019). A comprehensive review of wireless body area network. Journal of Network and Computer Applications, 143, 178–198. DOI 10.1016/j.jnca.2019.06.016. [Google Scholar] [CrossRef]
13. Chen, H. M., Lo, J. W., Yeh, C. K. (2012). An efficient and secure dynamic ID-based authentication scheme for telecare medical information systems. Journal of Medical Systems, 36(6), 3907–3915. DOI 10.1007/s10916-012-9862-y. [Google Scholar] [CrossRef]
14. Cao, T., Zhai, J. (2013). Improved dynamic ID-based authentication scheme for telecare medical information systems. Journal of Medical Systems, 37(2), 9912. DOI 10.1007/s10916-012-9912-5. [Google Scholar] [CrossRef]
15. He, D., Kumar, N., Chen, J., Lee, C. C., Chilamkurti, N. et al. (2015). Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multimedia Systems, 21(1), 49–60. DOI 10.1007/s00530-013-0346-9. [Google Scholar] [CrossRef]
16. Li, X., Niu, J., Karuppiah, M., Kumari, S., Wu, F. (2016). Secure and efficient two-factor user authentication scheme with user anonymity for network based e-health care applications. Journal of Medical Systems, 40(12), 1–12. DOI 10.1007/s10916-016-0629-8. [Google Scholar] [CrossRef]
17. He, D. B., Chen, J. H., Zhang, R. (2012). A more secure authentication scheme for telecare medicine information systems. Journal of Medical Systems, 36(3), 1989–1995. DOI 10.1007/s10916-011-9658-5. [Google Scholar] [CrossRef]
18. Wei, J., Hu, X., Liu, W. (2012). An improved authentication scheme for telecare medicine information systems. Journal of Medical Systems, 36(6), 3597–3604. DOI 10.1007/s10916-012-9835-1. [Google Scholar] [CrossRef]
19. Wu, F., Li, X., Sangaiah, A. K., Xu, L., Kumari, S. et al. (2018). A lightweight and robust two-factor authentication scheme for personalized healthcare systems using wireless medical sensor networks. Future Generation Computer Systems, 82, 727–737. DOI 10.1016/j.future.2017.08.042. [Google Scholar] [CrossRef]
20. Wazid, M., Das, A. K., Vasilakos, A. V. (2018). Authenticated key management protocol for cloud-assisted body area sensor networks. Journal of Network and Computer Applications, 123, 112–126. DOI 10.1016/j.jnca.2018.09.008. [Google Scholar] [CrossRef]
21. Sharma, G., Kalra, S. (2019). A lightweight user authentication scheme for cloud-IoT based healthcare services. Iranian Journal of Science and Technology, Transactions of Electrical Engineering, 43(1), 619–636. DOI 10.1007/s40998-018-0146-5. [Google Scholar] [CrossRef]
22. Canetti, R., Krawczyk, H. (2002). Universally composable notions of key exchange and secure channels. International Conference on the Theory and Applications of Cryptographic Techniques, Springer, The Netherlands. [Google Scholar]
23. Masud, M., Gaba, G. S., Choudhary, K., Hossain, M. S., Alhamid, M. F. et al. (2021). Lightweight and anonymity-preserving user authentication scheme for IoT-based healthcare. IEEE Internet of Things Journal. DOI 10.1109/JIOT.2021.3080461. [Google Scholar] [CrossRef]
24. Abdalla, M., Fouque, P. A., Pointcheval, D. (2005). Password-based authenticated key exchange in the three-party setting. International Workshop on Public Key Cryptography, Springer. [Google Scholar]
25. Wang, D., He, D., Wang, P., Chu, C. H. (2014). Anonymous two-factor authentication in distributed systems: Certain goals are beyond attainment. IEEE Transactions on Dependable and Secure Computing, 12(4), 428–442. DOI 10.1109/TDSC.2014.2355850. [Google Scholar] [CrossRef]
26. Wang, D., Wang, P. (2016). Two birds with one stone: Two-factor authentication with security beyond conventional bound. IEEE Transactions on Dependable and Secure Computing, 15(4), 708–722. DOI 10.1109/TDSC.2016.2605087. [Google Scholar] [CrossRef]
27. Dolev, D., Yao, A. (1983). On the security of public key protocols. IEEE Transactions on Information Theory, 29(2), 198–208. DOI 10.1109/TIT.1983.1056650. [Google Scholar] [CrossRef]
28. Kocher, P., Jaffe, J., Jun, B. (1999). Differential power analysis. Annual International Cryptology Conference, Springer. California, USA. [Google Scholar]
29. Ren, Y., Wu, L. (2013). Power analysis attacks on wireless sensor nodes using CPU smart card. 22nd Wireless and Optical Communication Conference, IEEE, Chongqing, China. [Google Scholar]
30. Far, H. A. N., Bayat, M., Das, A. K., Fotouhi, M., Pournaghi, S. M. et al. (2021). LAPTAs: Lightweight anonymous privacy-preserving three-factor authentication scheme for WSN-based IIoT. Wireless Networks, 27(2), 1389–1412. DOI 10.1007/s11276-020-02523-9. [Google Scholar] [CrossRef]
31. Li, P., Su, J., Wang, X. (2020). iTLS: Lightweight transport-layer security protocol for IoT with minimal latency and perfect forward secrecy. IEEE Internet of Things Journal, 7(8), 6828–6841. DOI 10.1109/JIoT.6488907. [Google Scholar] [CrossRef]
32. Xu, S., Liu, X., Ma, M., Chen, J. (2020). An improved mutual authentication protocol based on perfect forward secrecy for satellite communications. International Journal of Satellite Communications and Networking, 38(1), 62–73. DOI 10.1002/sat.1309. [Google Scholar] [CrossRef]
33. Ul Haq, I., Wang, J., Zhu, Y., Maqbool, S. (2020). A survey of authenticated key agreement protocols for multi-server architecture. Journal of Information Security and Applications, 55, 102639. DOI 10.1016/j.jisa.2020.102639. [Google Scholar] [CrossRef]
34. Chen, C. M., Ku, W. C. (2002). Stolen-verifier attack on two new strong-password authentication protocols. IEICE Transactions on Communications, 85(11), 2519–2521. [Google Scholar]
35. Xu, G., Wang, F., Zhang, M., Peng, J. (2020). Efficient and provably secure anonymous user authentication scheme for patient monitoring using wireless medical sensor networks. IEEE Access, 8, 47282–47294. DOI 10.1109/Access.6287639. [Google Scholar] [CrossRef]
36. Challa, S., Wazid, M., Das, A. K., Kumar, N., Reddy, A. G. et al. (2017). Secure signature-based authenticated key establishment scheme for future IoT applications. IEEE Access, 5, 3028–3043. DOI 10.1109/ACCESS.2017.2676119. [Google Scholar] [CrossRef]
37. Zhou, L., Li, X., Yeh, K. H., Su, C., Chiu, W. (2019). Lightweight IoT-based authentication scheme in cloud computing circumstance. Future Generation Computer Systems, 91, 244–251. DOI 10.1016/j.future.2018.08.038. [Google Scholar] [CrossRef]
38. Farash, M. S., Turkanovi, M., Kumari, S., Hölbl, M. (2016). An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the Internet of Things environment. Ad Hoc Networks, 36, 152–176. DOI 10.1016/j.adhoc.2015.05.014. [Google Scholar] [CrossRef]
39. Turkanović, M., Brumen, B., Hölbl, M. (2014). A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Networks, 20, 96–112. DOI 10.1016/j.adhoc.2014.03.009. [Google Scholar] [CrossRef]
40. Wazid, M., Das, A. K., Shetty, S., Rodrigues, J. J. P. C., Park, Y. (2019). LDAKM-EIoT: Lightweight device authentication and key management mechanism for edge-based IoT deployment. Sensors, 19(24), 5539. DOI 10.3390/s19245539. [Google Scholar] [CrossRef]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |