
This study presents a comprehensive review of Artificial Intelligence (AI) applications across the diagnostic and prognostic spectrum of urological malignancies,...

Hydrogen is often presented as a clean and universal solution for decarbonization, yet its real sustainability depends on the scale, structure, and coordination...

New research reveals that maternal absence significantly increases loneliness in adolescents. A study of 305 participants (average age 16) in southeast China found...
Tech Science Press is pleased to announce that two additional journals have been selected for inclusion in CAB Abstracts, a leading database produced by CAB International (CABI). This milestone...
Gratitude, Growth, and Global Engagement The Canadian Journal of Urology (CJU) is pleased to share its 2025 annual highlights. Over the past year, the journal has maintained steady growth,...
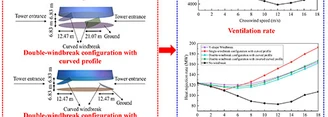
This study aims to mitigate crosswind-induced performance degradation in Natural Draft Dry Cooling Towers used in power plants by developing and assessing...
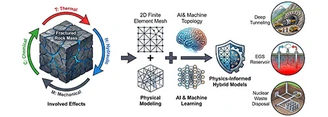
Fluid flow through fractured rock masses is a key process controlling the safety and performance of deep geoengineering systems, shaped by the complex...

Aerodynamic research on road cars was reviewed in this work under the thread of reducing drag, with the awareness that this may succeed in effectively...

In response to the actual demands of the energy storage type organic Rankine power generation cycle, this study proposes a new type of jacketed shell...

Heat exchangers play a crucial role in thermal energy systems, with their performance directly impacting efficiency, cost, and environmental impact. A...
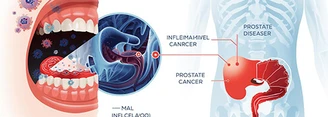
Objective: Current research highlights periodontal disease as a systemic inflammatory condition that may influence extra-oral diseases such as prostatic...

Discussions about the future of energy sources and environmental sustainability are becoming critical on a global scale. The energy sector plays a central...

The increasing integration of electric vehicle (EV) loads into power systems necessitates understanding their impact on stability. Small-magnitude perturbations,...

Objectives: Loneliness among left-behind adolescents is the most frequently reported emotional problem because of parental neglect. The present study...
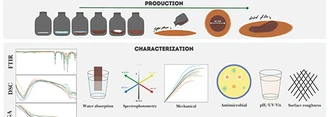
The development of sustainable materials has encouraged the use of biopolymers as alternatives to synthetic polymers. Polymeric films have stood out for...
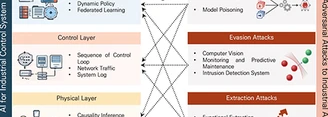
As attack techniques evolve and data volumes increase, the integration of artificial intelligence-based security solutions into industrial control systems...
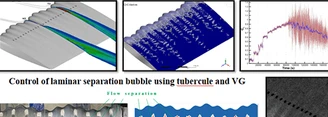
This paper examines a model that combines vortex generators and leading-edge tubercles for controlling the laminar separation bubble (LSB) over an airfoil...

Skin cancer remains the most commonly diagnosed malignancy worldwide, with basal cell carcinoma (BCC), cutaneous squamous cell carcinoma (cSCC), and melanoma...

Classical Hodgkin lymphoma (cHL) is characterized by rare Hodgkin/Reed-Sternberg (HRS) tumor cells that uniformly express cluster of differentiation (CD)30...
Quantitative analysis of aluminum-silicon (Al-Si) alloy microstructure is crucial for evaluating and controlling alloy performance. Conventional analysis...

Internet of Things (IoTs) devices are bringing about a revolutionary change our society by enabling connectivity regardless of time and location. However,...
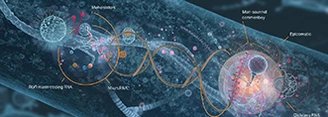
Cancer remains one of the leading causes of morbidity and mortality worldwide, and its onset and progression are closely linked to dysregulated epigenetic...

We propose a special issue titled "Innovative Smart Polymeric Materials for Sustainable Energy Solutions: Bridging Advances in Energy and Biomedical...

Further advancements in the exploitation of unconventional resources, such as tight gas, shale gas, shale oil, coalbed methane, and natural gas hydrate,...

In today’s digital era, patterns are omnipresent, shaping many aspects of our lives. These patterns can be physically observed or computationally identified...

This special issue, “Applied Artificial Intelligence: Advanced Solutions for Engineering Real-World Challenges,” showcases the transformative power of...

This theme captures the essence of advanced technologies (AI, machine learning, big data), modern applications (climate change, smart cities, health research),...

The tumor microenvironment encompasses not only the tumor cells themselves, but also the surrounding fibroblasts, immunological and inflammatory cells,...
This special issue seeks original research and review articles on the roles of γδ T cells and invariant natural killer T (iNKT) cells in malignancies....

This study aims to mitigate crosswind-induced performance degradation in Natural Draft Dry Cooling Towers used in power plants by developing and assessing...

Fluid flow through fractured rock masses is a key process controlling the safety and performance of deep geoengineering systems, shaped by the complex...

Aerodynamic research on road cars was reviewed in this work under the thread of reducing drag, with the awareness that this may succeed in effectively...

In response to the actual demands of the energy storage type organic Rankine power generation cycle, this study proposes a new type of jacketed shell...

Heat exchangers play a crucial role in thermal energy systems, with their performance directly impacting efficiency, cost, and environmental impact. A...

Objective: Current research highlights periodontal disease as a systemic inflammatory condition that may influence extra-oral diseases such as prostatic...

Discussions about the future of energy sources and environmental sustainability are becoming critical on a global scale. The energy sector plays a central...

The increasing integration of electric vehicle (EV) loads into power systems necessitates understanding their impact on stability. Small-magnitude perturbations,...

Objectives: Loneliness among left-behind adolescents is the most frequently reported emotional problem because of parental neglect. The present study...

The development of sustainable materials has encouraged the use of biopolymers as alternatives to synthetic polymers. Polymeric films have stood out for...

As attack techniques evolve and data volumes increase, the integration of artificial intelligence-based security solutions into industrial control systems...

This paper examines a model that combines vortex generators and leading-edge tubercles for controlling the laminar separation bubble (LSB) over an airfoil...

Skin cancer remains the most commonly diagnosed malignancy worldwide, with basal cell carcinoma (BCC), cutaneous squamous cell carcinoma (cSCC), and melanoma...

Classical Hodgkin lymphoma (cHL) is characterized by rare Hodgkin/Reed-Sternberg (HRS) tumor cells that uniformly express cluster of differentiation (CD)30...

Quantitative analysis of aluminum-silicon (Al-Si) alloy microstructure is crucial for evaluating and controlling alloy performance. Conventional analysis...

Internet of Things (IoTs) devices are bringing about a revolutionary change our society by enabling connectivity regardless of time and location. However,...

Cancer remains one of the leading causes of morbidity and mortality worldwide, and its onset and progression are closely linked to dysregulated epigenetic...

We propose a special issue titled "Innovative Smart Polymeric Materials for Sustainable Energy Solutions: Bridging Advances in Energy and Biomedical...

Further advancements in the exploitation of unconventional resources, such as tight gas, shale gas, shale oil, coalbed methane, and natural gas hydrate,...

In today’s digital era, patterns are omnipresent, shaping many aspects of our lives. These patterns can be physically observed or computationally identified...

This special issue, “Applied Artificial Intelligence: Advanced Solutions for Engineering Real-World Challenges,” showcases the transformative power of...

This theme captures the essence of advanced technologies (AI, machine learning, big data), modern applications (climate change, smart cities, health research),...

The tumor microenvironment encompasses not only the tumor cells themselves, but also the surrounding fibroblasts, immunological and inflammatory cells,...

This special issue seeks original research and review articles on the roles of γδ T cells and invariant natural killer T (iNKT) cells in malignancies....
This study aims to mitigate crosswind-induced performance degradation in Natural Draft Dry Cooling Towers used in power plants by developing and assessing windbreak configurations that enhance ventilation while minimizing additional airflow resistance. Three novel windbreak designs, namely single-windbreak configuration with curved profile, double-windbreak configuration with curved profile, and double-windbreak configuration with inverted curved profile, are proposed accordingly and evaluated against conventional solutions. Three-dimensional numerical models of a 120 m high NDDCT equipped with these windbreaks,…
With the maturation of coalbed methane (CBM) exploitation and the transition into the late stages of dewatering and gas production, liquid loading in gathering pipelines has emerged as a major constraint on productivity and operational stability. Based on real-time field data and gas–liquid physicochemical analyses, this study elucidates the mechanisms governing liquid loading formation under varying temperature, pressure, and water saturation conditions. An HYSYS model is employed to determine the water dew point, while the…
Efficient thermal management in porous media is essential for advanced engineering applications, including solar energy systems, electronic cooling, and aerospace thermal control. This study presents a comprehensive analysis of ternary hybrid nanofluids, TiO2–CdTe–MoS2 dispersed in water, flowing over a vertical stretching or shrinking surface in a Darcy–Brinkman porous medium. The investigation accounts for the combined effects of magnetohydrodynamics, thermal radiation, viscous dissipation, and internal heat generation. In contrast to previous studies that predominantly focused on single…
This study investigates in-station pressure drop mechanisms in a shale gas gathering system, providing a quantitative basis for flow system optimization. Computational fluid dynamics (CFD) simulations, based on field-measured parameters related to a representative case (a shale gas platform located in Sichuan, China) are conducted to analyze the flow characteristics of specific fittings and manifolds, and to quantify fitting resistance coefficients and manifold inlet interference. The resulting coefficients are integrated into a full-station gathering network…
Optimizing pyrolysis processes is critical for improving the efficiency of pyrolysis furnaces. This study presents a strategy to enhance heat transfer through agitation, employing Fluent for detailed numerical simulation of the thermal behavior. The simulation results show strong agreement with experimental measurements of localized fluid temperature rise. Forced convection induced by impeller rotation significantly improves heat transfer between the fluid and the furnace walls, effectively reducing thermal stratification. At an impeller speed of 240 RPM,
Fluid flow through fractured rock masses is a key process controlling the safety and performance of deep geoengineering systems, shaped by the complex interactions of thermal, hydraulic, mechanical and chemical (THMC) fields. This paper presents a systematic review of this subject with special emphasis on the multi-physics governing it. First, we elucidate the interdependent mechanisms and governing equations, highlighting the nonlinear, path-dependent, and evolving nature of the relationship between stress and permeability. Next, mainstream modeling…
To clarify fluid flow mechanisms and establish effective development conditions in continental shale oil reservoirs, a high-temperature, high-pressure steady-state flow system integrated with nuclear magnetic resonance (NMR) technology has been developed. The apparatus combines sample evacuation, rapid pressurization and saturation, and controlled displacement, enabling systematic investigation of single-phase shale oil flow under representative reservoir conditions. Related experiments allow proper quantification of the activation thresholds and relative contributions of different pore types to flow. A movable…
Aerodynamic research on road cars was reviewed in this work under the thread of reducing drag, with the awareness that this may succeed in effectively decreasing the carbon footprint of transportation. First, a selection of studies was presented to focus on the most important aerodynamic features of the flow around realistic car body shapes. Then, the discussion was organized around three pillars related to passive flow control, active flow control and active aerodynamics. Both experimental…
During high-speed operation, mixed-flow pumps are susceptible to cavitation, which destabilizes the internal flow, increases energy losses, and degrades hydraulic efficiency. To assess the effectiveness of blade perforation as a cavitation-mitigation strategy, in this study several mixed-flow pump models incorporating perforations were developed. Numerical simulations were performed for configurations with circular holes positioned at different locations along the blade leading edge, and the computational results were validated against experimental measurements. The findings indicate that the…
Deep shale gas reservoirs in the southern Sichuan Basin are typically characterized by significant horizontal stress anisotropy (expressed as stress difference), variable brittleness–ductility in rock mechanics, and strong heterogeneity. These complex geomechanical conditions lead to pronounced differences in hydraulic fracturing outcomes among wells and sections. To investigate hydraulic fracture propagation and fracturing fluid injection behavior under varying geomechanical settings, true triaxial physical simulation tests were performed on 400 × 400 × 400 mm artificial rock…
Moon-based Synthetic Aperture Radar (SAR) is particularly suitable for monitoring polar regions because of its consistent and continuous imaging. It has promising applications in the observation of sea ice by capturing rapid freeze-thaw cycles in the Arctic and Antarctic. However, the long synthetic aperture time inherent in Moon-based SAR may lead to image defocusing due to water fluctuations. Additionally, large incidence angles during observations in polar regions can result in weak backscatter from sea ice,…
Pulse tube cryocoolers are widely employed in cryogenic systems, where gas contamination has become a critical factor limiting both performance and service life. To further investigate the condensation behavior of contaminants, this study develops a two-dimensional axisymmetric model of a linear-type cryocooler to simulate the transport and deposition processes of trace CO2, evaluating the impact of contamination on system pressure drop under various operating conditions. Results indicate that CO2 diffusion is primarily driven by concentration gradients.…
This article presents an adaptive intelligent control strategy applied to a lumped-parameter evaporator model, i.e., a simplified dynamic representation treating the evaporator as a single thermal node with uniform temperature distribution, suitable for control design due to its balance between physical fidelity and computational simplicity. The controller uses a wavelet-based neural proportional, integral, derivative (PID) controller with IIR filtering (infinite impulse response). The dynamic model captures the essential heat and mass transfer phenomena through a…
Based on the Fluent numerical simulation method, this study systematically analyzed the structural parameters of the spiral tube heat exchanger and the influence of the external baffle on its heat transfer performance. The results show that when the equivalent diameter of the spiral tube increased from 16.68 to 21.23 mm, its surface heat transfer coefficient decreased from 22,040 to 17,230 W/m2·K, and the outlet air temperature dropped from 822.3 to 807.3 K. However, the pressure loss…
The proton exchange membrane fuel cell (PEMFC) and the hydrogen hybrid power system are studied by the fuzzy-PID (FPID) control method and the fuzzy-PID control method by Artificial Bee Colony algorithm (ABC-FPID), respectively. The results reveal that compared with the FPID control method, the temperature overshoot of the PEMFC stack under the ABC-FPID control method is decreased by 0.6%. Moreover, the circulating water flow rate within the full operating envelope (about 3 min) is reduced…
In response to the actual demands of the energy storage type organic Rankine power generation cycle, this study proposes a new type of jacketed shell and tube heat exchanger with integrated cold storage and heat exchange. N-tedecane is selected as the phase change material for cold storage, low-temperature water as the cold source, and R134a as the heat source. The phase change material for cold storage is filled inside the jacket tube of the heat…

Guest Editors: Qi Chen; Yunhui Tang Deadline: 31 December 2026
Guest Editors: Dawei Jiang; Miaojun Xu; Bo Jiang; Zijian Wu Deadline: 31 December 2026

Guest Editors: Changhong LINGHU; Hoon Eui Jeong; Ying Jiang; Jiangtao Su; Yangchengyi... Deadline: 30 December 2026

Guest Editors: Fátima Martel Deadline: 30 November 2026

Guest Editors: Wei-Chiang Hong; Yi Liang; Ming-Wei Li; Zhong-Yi Yang Deadline: 30 November 2026

Guest Editors: Emilio Cervantes Deadline: 31 October 2026

Guest Editors: Maria Letizia Motti; Immacolata Belviso Deadline: 31 October 2026

Guest Editors: Batyrkhan Omarov; Daniyar Sultan; Bakhytzhan Kulambayev Deadline: 30 October 2026

Guest Editors: Daniel-Ioan Curiac; Dan Pescaru Deadline: 15 October 2026

Guest Editors: Barmak Honarvar Shakibaei Asli Deadline: 01 October 2026

Guest Editors: Antonella Petrillo; Fabio De Felice Deadline: 30 September 2026

Guest Editors: Sergio Cassese; Giuseppe Gallo Deadline: 30 September 2026

Guest Editors: Wenfeng Zheng; Lirong Yin; Shan Liu Deadline: 31 August 2026

Guest Editors: Mohammad Shokouhifar; Frank Werner Deadline: 31 August 2026

Guest Editors: Dulf Eva-H.; Kovacs Levente; Denes-Fazakas Lehel; Pintea Paul-Andrei Deadline: 31 August 2026

Guest Editors: Ali BOURGI Deadline: 31 July 2026






