
This picture compares the performance of proline dehydrogenase gene-modified wheat with wild-type under drought stress. Under normal conditions, both grow similarly....

This systematic review synthesizes evidence on the determinants and interventions affecting doctoral students’ mental health and well-being. Analysing 56 empirical...

The image illustrates the workflow of artificial intelligence–empowered inverse design for composite materials. At the center of the figure, an AI model integrates...
Bangkok, Thailand | January 26–28, 2026 — Tech Science Press is pleased to share that John Chen, Director of Development, represented the company at the Charleston Asia Conference, where...
2026 10th International Conference on Civil Construction and Structural Engineering (I3CSE 2026)May 29–31, 2026 | Guangzhou, China Structural Durability & Health Monitoring (SDHM) is...

Inverse design of advanced materials represents a pivotal challenge in materials science. Leveraging the latent space of Variational Autoencoders (VAEs)...

Predicting the behavior of renewable energy systems requires models capable of generating accurate forecasts from limited historical data, a challenge...

Neutrophil extracellular trap (NET) formation or NETosis is a specialized innate immune process in which neutrophils release chromatin fibers decorated...
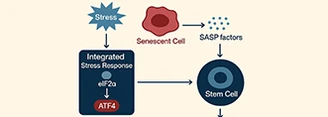
Stem cell fate decisions are increasingly understood through the dynamic interplay of two fundamental stress-adaptive programs: the integrated stress...

Objectives: Immunotherapy based on immune checkpoint blockade (ICB) has become a key treatment for melanoma. However, the increasing number of cases of...

Background: Photodynamic therapy (PDT) may eradicate residual malignant cells following sarcoma resection, through reactive oxygen species (ROS) mediated...

As containerized environments become increasingly prevalent in cloud-native infrastructures, the need for effective monitoring and detection of malicious...

Federated Learning (FL) has become a leading decentralized solution that enables multiple clients to train a model in a collaborative environment without...

Background: Adolescents increasingly engage with social media for connection, self-expression, and identity exploration. This growing digital engagement...

Grape (Vitis vinifera L.) cultivation has progressed from early domestication and clonal propagation to modern, data-driven breeding that is reshaping...
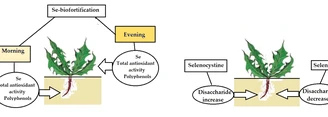
Circadian biorhythms are fundamental in plant adaptability and development. To reveal the effect of organic and inorganic forms of Se, foliar treatments...

Background: While the treatment of metastatic renal cell carcinoma (mRCC) is evolving due to immune checkpoint inhibitors (ICIs), optimal strategies for...
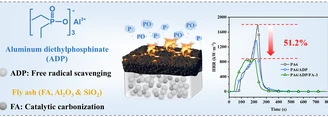
The fabrication of highly flame-retardant polyamide 6 (PA6) composites is of great significance for expanding their practical applications. Herein, a...
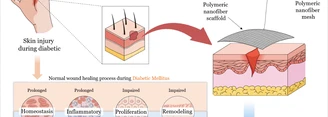
With the global diabetes epidemic, diabetic foot ulcers (DFUs) have become a major health burden, affecting approximately 18 million people worldwide...

Neurodegenerative diseases (NDs) such as Alzheimer’s disease (AD), Parkinson’s disease (PD), Huntington’s disease (HD), and amyotrophic lateral sclerosis...

Precast concrete structures have gained popularity due to their advantages. However, the seismic performance of their connection joints remains an area...
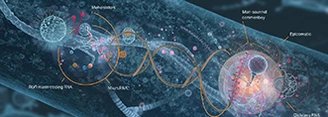
Cancer remains one of the leading causes of morbidity and mortality worldwide, and its onset and progression are closely linked to dysregulated epigenetic...

In today’s digital era, patterns are omnipresent, shaping many aspects of our lives. These patterns can be physically observed or computationally identified...

This theme captures the essence of advanced technologies (AI, machine learning, big data), modern applications (climate change, smart cities, health research),...

The tumor microenvironment encompasses not only the tumor cells themselves, but also the surrounding fibroblasts, immunological and inflammatory cells,...
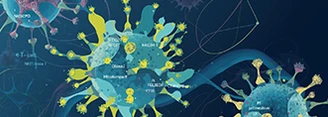
This special issue seeks original research and review articles on the roles of γδ T cells and invariant natural killer T (iNKT) cells in malignancies....

The mobile internet has revolutionized our daily lives, providing continuous connectivity, communication, and access to a wide range of services and applications...

Machine vision detection and intelligent recognition are important research areas in computer vision with wide-ranging applications in manufacturing,...

Object detection and tracking in videos has become an increasingly important area of research due to its potential applications in a variety of domains...

Inverse design of advanced materials represents a pivotal challenge in materials science. Leveraging the latent space of Variational Autoencoders (VAEs)...

Predicting the behavior of renewable energy systems requires models capable of generating accurate forecasts from limited historical data, a challenge...

Neutrophil extracellular trap (NET) formation or NETosis is a specialized innate immune process in which neutrophils release chromatin fibers decorated...

Stem cell fate decisions are increasingly understood through the dynamic interplay of two fundamental stress-adaptive programs: the integrated stress...

Objectives: Immunotherapy based on immune checkpoint blockade (ICB) has become a key treatment for melanoma. However, the increasing number of cases of...

Background: Photodynamic therapy (PDT) may eradicate residual malignant cells following sarcoma resection, through reactive oxygen species (ROS) mediated...

As containerized environments become increasingly prevalent in cloud-native infrastructures, the need for effective monitoring and detection of malicious...

Federated Learning (FL) has become a leading decentralized solution that enables multiple clients to train a model in a collaborative environment without...

Background: Adolescents increasingly engage with social media for connection, self-expression, and identity exploration. This growing digital engagement...

Grape (Vitis vinifera L.) cultivation has progressed from early domestication and clonal propagation to modern, data-driven breeding that is reshaping...

Circadian biorhythms are fundamental in plant adaptability and development. To reveal the effect of organic and inorganic forms of Se, foliar treatments...

Background: While the treatment of metastatic renal cell carcinoma (mRCC) is evolving due to immune checkpoint inhibitors (ICIs), optimal strategies for...

The fabrication of highly flame-retardant polyamide 6 (PA6) composites is of great significance for expanding their practical applications. Herein, a...

With the global diabetes epidemic, diabetic foot ulcers (DFUs) have become a major health burden, affecting approximately 18 million people worldwide...

Neurodegenerative diseases (NDs) such as Alzheimer’s disease (AD), Parkinson’s disease (PD), Huntington’s disease (HD), and amyotrophic lateral sclerosis...

Precast concrete structures have gained popularity due to their advantages. However, the seismic performance of their connection joints remains an area...

Cancer remains one of the leading causes of morbidity and mortality worldwide, and its onset and progression are closely linked to dysregulated epigenetic...

In today’s digital era, patterns are omnipresent, shaping many aspects of our lives. These patterns can be physically observed or computationally identified...

This theme captures the essence of advanced technologies (AI, machine learning, big data), modern applications (climate change, smart cities, health research),...

The tumor microenvironment encompasses not only the tumor cells themselves, but also the surrounding fibroblasts, immunological and inflammatory cells,...

This special issue seeks original research and review articles on the roles of γδ T cells and invariant natural killer T (iNKT) cells in malignancies....

The mobile internet has revolutionized our daily lives, providing continuous connectivity, communication, and access to a wide range of services and applications...

Machine vision detection and intelligent recognition are important research areas in computer vision with wide-ranging applications in manufacturing,...

Object detection and tracking in videos has become an increasingly important area of research due to its potential applications in a variety of domains...
Predicting the precise impacts of climate change on extreme winds remains challenging, yet strong storms are widely expected to occur more frequently in a warming climate. Wind barriers are commonly used on bridges to reduce aerodynamic loads on trains through blocking effects. This study develops a novel wind barrier based on Tesla valves, which not only blocks incoming flow but also dissipates mechanical energy through fluid collision. To demonstrate this energy-dissipation capability, a Tesla plate…
For hypersonic air-breathing vehicles, the V-shaped leading edges (VSLEs) of supersonic combustion ramjet (scramjet) inlets experience complex shock interactions and intense aerodynamic loads. This paper provides a comprehensive review of flow characteristics at the crotch of VSLEs, with particular focus on the transition of shock interaction types and the variation of wall heat flux under different freestream Mach numbers and geometric configurations. The mechanisms governing shock transition, unsteady oscillations, hysteresis, and three-dimensional effects in VSLE
Carbonate gas reservoirs are often characterized by strong heterogeneity, complex inter-well connectivity, extensive edge or bottom water, and unbalanced production, challenges that are also common in many heterogeneous gas reservoirs with intricate storage and flow behavior. To address these issues within a unified, data-driven framework, this study develops a multi-block material balance model that accounts for inter-block flow and aquifer influx, and is applicable to a wide range of reservoir types. The model incorporates inter-well…
Significant differences exist between deep and medium-shallow coalbed methane (CBM) reservoirs. The unclear understanding of flowback and production behavior severely constrains the development of deep CBM resources. To address this challenge, guided by the gas-liquid two-phase flow theory in ultra-low permeability reservoirs, and integrating theoretical analysis, numerical simulation, and insights from production practices, this study classifies the flowback and production stages of deep CBM well considering the Daning-Jixian Block, Eastern Ordos Basin as a representative…
Self-suspended proppants, which enable clear-water fracturing, represent a promising new class of materials for reservoir stimulation. Given the economic limitations associated with their exclusive use, this study investigates proppant transport behavior in hybrid systems combining self-suspended proppants with conventional 40/70 mesh quartz sand at various mixing ratios. A dedicated experimental apparatus was developed to replicate field-relevant complex fracture networks, consisting of a main fracture and two branching fractures with different deflection angles. Using this system,…
The low-pressure and low-density conditions encountered at high altitudes significantly reduce the operating Reynolds number of micro radial-flow turbines, frequently bringing it below the self-similarity critical threshold of 3.5 × 104. This departure undermines the applicability of conventional similarity-based design approaches. In this study, micro radial-flow turbines with rotor diameters below 50 mm are investigated through a combined approach integrating high-fidelity numerical simulations with experimental validation, aiming to elucidate the mechanisms by which low Reynolds numbers…
Weak water-drive offshore reservoirs with complex pore architecture and strong permeability heterogeneity present major challenges, including rapid depletion of formation energy, low waterflood efficiency, and significant lateral and vertical variability in crude oil properties, all of which contribute to limited recovery. To support more effective field development, alternative strategies and a deeper understanding of pore-scale flow behavior are urgently needed. In this work, CT imaging and digital image processing were used to construct a digital…
In this study, a Gaussian Process Regression (GPR) surrogate model coupled with a Bayesian optimization algorithm was employed for the single-objective design optimization of fan-shaped film cooling holes on a concave wall. Fan-shaped holes, commonly used in gas turbines and aerospace applications, flare toward the exit to form a protective cooling film over hot surfaces, enhancing thermal protection compared to cylindrical holes. An initial hole configuration was used to improve adiabatic cooling efficiency. Design variables…
As a controllable power generation method requiring no energy storage, Ocean Thermal Energy Conversion (OTEC) technology demonstrates characteristics of abundant reserves, low pollution, and round-the-clock stable operation. The free-standing cold-water pipe (CWP) in the system withstands various complex loads during operation, posing potential failure risks. To reveal the deformation and stress mechanisms of OTEC CWPs, this study first analyzes wave particle velocity and acceleration to determine wave loads at different water depths. Based on the…
Identifying geohazards such as landslides and methane leakage is crucial during gas extraction from natural gas hydrate (NGH) reservoirs, and understanding reservoir settlement behavior is central to this assessment. Horizontal wells can enlarge the pressure relief zone within the formation, improving single-well productivity, and are therefore considered a promising approach for NGH development. This study examines the settlement response of hydrate-bearing sediments during depressurization using horizontal wells. A fully coupled thermal, hydraulic, mechanical, and chemical…
The expansion of transportation networks, including railways and ports, has been a major force driving urban growth, mobility, and socio-economic transformations since the Industrial Revolution. This study utilizes Historical Geographic Information Systems to examine the global evolution of transportation infrastructure, focusing on railways and ports, from 1880 to 2020. The dataset enables a multidimensional analysis of how transportation systems have shaped cities, influenced regional development, and helped to make possible sustainability efforts. By offering insights…
Climate classification systems are essential tools for analyzing regional climatic behavior, assessing long-term aridity patterns, and evaluating the impacts of climate change on water resources and ecosystem resilience. This study introduces a new Climate Classification Method based on uniform and unitless variables, referred to as the U2 Climate Classification (U2CC). The proposed U2 Index was designed to overcome structural limitations of the classical De Martonne (1942) and Erinç (1949) indices, which rely on raw precipitation–temperature…
The assessment of groundwater quality is crucial for ensuring its safe and sustainable use for domestic and agricultural purposes. The Kurukshetra district in the Indian state of Haryana relies heavily on groundwater to meet household and agricultural needs. Sustainable groundwater management must be assessed in terms of suitability for domestic and agricultural needs in a region. The current study analyzed pre-monsoon geochemical data from groundwater samples in the study area for 1991, 2000, 2010, and…
Rainfall data from four weather stations, quite far from each other, but located in the Zambezian phytogeographic region, were analysed for the research for indices of climate change. Two variables, rainfall and the annual number of rainy days, were considered. The rainfall data examined are 114 years for Luanda (1901–2014), 106 years for Lubumbashi (1916–2021), respectively, 54 and 41 years for Huambo (1961–2014) and Boma (1981–2021); 100 years (1921–2021) for the annual number of rainy…
Cyprus has an extensive record in grape production and winemaking. Grapevine is essential for the economic and environmental sustainability of the agricultural sector, as it is in other Mediterranean regions. Intensive agriculture can overuse and exhaust natural resources, including soil and water. The current study evaluated how conservation strategies, including no tillage and semi-tillage (as a variation of strip tillage), affected grapevine growth and grape quality when compared to conventional tillage application. Two cultivars were…
Achillea species are known for their healing properties since ancient times. There is extensive literature on their pharmacological action due to their bioactive compounds. The present study aimed to investigate the antioxidant and antimicrobial effects of hydroalcoholic extracts from the inflorescences and leaves of the species Achillea crithmifolia Waldst. and Kit., A. grandifolia Friv. and A. millefolium L. The phytochemical profiles of all extracts were evaluated both by NMR spectroscopy and LC-MS analysis, and the results were consistent with…

Guest Editors: Fátima Martel Deadline: 30 November 2026

Guest Editors: Emilio Cervantes Deadline: 31 October 2026

Guest Editors: Maria Letizia Motti; Immacolata Belviso Deadline: 31 October 2026

Guest Editors: Daniel-Ioan Curiac; Dan Pescaru Deadline: 15 October 2026

Guest Editors: Antonella Petrillo; Fabio De Felice Deadline: 30 September 2026

Guest Editors: Mohammad Shokouhifar; Frank Werner Deadline: 31 August 2026

Guest Editors: Dulf Eva-H.; Kovacs Levente; Denes-Fazakas Lehel; Pintea Paul-Andrei Deadline: 31 August 2026

Guest Editors: Hoon Ko; Marek R. Ogiela Deadline: 31 July 2026

Guest Editors: Jevier Bermejo Higuera; Juan Ramón Bermejo Higuera Deadline: 31 July 2026

Guest Editors: Shyi-Chyi Cheng; Naomi A. Ubina Deadline: 31 July 2026

Guest Editors: Wenfeng Zheng; Lirong Yin; Shan Liu Deadline: 30 June 2026

Guest Editors: Consolato M. Sergi Deadline: 30 June 2026

Guest Editors: Snježana Kaštelan; Ivica Lukšić; Jelena Juri Mandić; Matija... Deadline: 30 June 2026

Guest Editors: Ilsun You; Gaurav Choudhary; Philip Virgil Astillo Deadline: 15 June 2026

Guest Editors: Viktor Gribniak; Zdeněk Kala; Constantin E. Chalioris Deadline: 31 March 2026

Guest Editors: Kang-Di Lu; Yun Fu; Yong Xu Deadline: 30 March 2026






